随笔分类 - Cyber Security
摘要:Today, we are going to talk briefly about web browser tracking so what sites can view to track your web browser and track who you are? Cookies Text ta
阅读全文
摘要:Now that we have constructed a port scanner to find targets, we can begin the task of exploiting the vulnerabilities of each service. The Morris Worm
阅读全文
摘要:PHP's unserialize() function In a nutshell, PHP's unserialize() function takes a string(representing a serialized object) and converts it back to a PH
阅读全文
摘要:What is insecure deserialization? To understand insecure deserialization, we must first understand what serialization is and how it is used in applica
阅读全文
摘要:A reverse shell is a shell session established on a connection that is initiated from a remote machine, not from the localhost. Attackers who successf
阅读全文
摘要:Nmap is used to enumerate network host inventories, manage service escalation schedules, and monitor host or service health. Nmap can detect whether t
阅读全文
摘要:Access Database Introduction Microsoft Access is a database management system (DBMS) from Microsoft that combines the relational Microsoft Jet Databas
阅读全文
摘要:TCP Full Connect Scan An attacker routinely performs a port scan in the opening salvo of any successful cyber assault. One type of port scan includes
阅读全文
摘要:SQLI DUMB SERIES-1 Step 1: Find the Injection point. This obviously is parameter Injection since the hint said, Please input the ID as parameter with
阅读全文
摘要:Intro to Metasploit First, Metasploit uses PostgreSQL as its database so it needs to be launched first. sudo service postgresql start Second, With Pos
阅读全文
摘要:Evil Twin Attack's sole purpose is to evaesdrop on WiFi users to steal personal or corporate information without user's knowledge. Step 1: Attacker sc
阅读全文
摘要: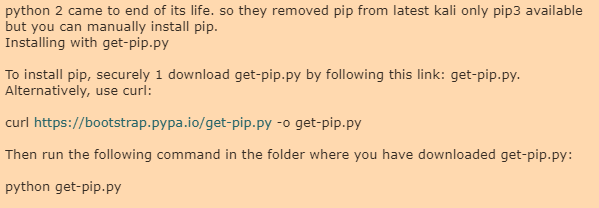 
阅读全文
摘要:Step 1:Set our network wireless card into monitor mode Step 2: Use these commands below, and make sure they will not disturb u. Step 3: spying the net
阅读全文
摘要:Because In the next few sections, we will study wireless pen-testing. So today, In this tutorial, I will write about how to set up your external USB n
阅读全文
摘要:Our task is a spoofing exercise by setting up a fake login website. Step 1: Open your terminal and run setoolkit Step 2: Select Social-Engineering Att
阅读全文
摘要:~/.config/qterminal.org/qterminal.ini fontFamily = Fira Code fontSize = 15
阅读全文
摘要:Our target: scanme.nmap.org Tools: nslookup、nmap nslookup nslookup is a network administration command-line tool for querying the Domain Name System(D
阅读全文
摘要:Using proxychains with Tor or VPN to hide real IP https://www.cnblogs.com/gufana/p/13856116.html Prevent DNS Leak Vim /etc/resolv.conf and change the
阅读全文
摘要:RESULT: 1. In ~ directory, input ls -a, there exist a .bashrc file. 2. Delete all of them, then go to https://gist.github.com/rickdaalhuizen90/d1df7f6
阅读全文
摘要:Pros: * Anonymous Cons: * Low Speed * Informations are not secure Suitable application scenarios: 1. Scanning 2. Nmapping 3. Bypass firewall setting o
阅读全文

 浙公网安备 33010602011771号
浙公网安备 33010602011771号