Debian12自动安全更新升级操作部署
目录
目标说明
实现一套自动、安全、稳定的 Debian 12 安全更新机制,并在升级失败时将通知发送到外部邮箱,适用于硬盘加密场景,不允许自动重启
如在部署当中出现报错,请看 这里
操作
配置apt软件源(含安全更新)
rambo@debian-3:~$ sudo cp /etc/apt/sources.list{,-bak}
rambo@debian-3:~$ sudo vim /etc/apt/sources.list
deb http://ftp.debian.org/debian/ bookworm main contrib non-free non-free-firmware
deb http://ftp.debian.org/debian/ bookworm-updates main contrib non-free non-free-firmware
deb http://security.debian.org/debian-security bookworm-security main contrib non-free non-free-firmware
rambo@debian-3:~$ sudo apt update
安装并配置自动升级工具
# 安装自动升级相关组件
rambo@debian-3:~$ sudo apt install -y unattended-upgrades apt-listchanges
rambo@debian-3:~$ sudo vim /etc/apt/apt.conf.d/50unattended-upgrades
Unattended-Upgrade::Mail "xxxx@126.com"; // 替换为接收通知的邮箱(收件箱)
Unattended-Upgrade::MailOnlyOnError "false"; // true只在升级失败时发送邮件
Unattended-Upgrade::Automatic-Reboot "false"; // 成功升级后不自动重启,防止加密盘未解锁
Unattended-Upgrade::Automatic-Reboot-Time "02:00"; // 即使启用重启,也只会在该时间重启
注:如不加 Automatic-Reboot "false",系统可能在你不知情的情况下重启,导致因加密盘未解锁而卡死
# 启用自动升级功能
rambo@debian-3:~$ sudo dpkg-reconfigure --priority=low unattended-upgrades
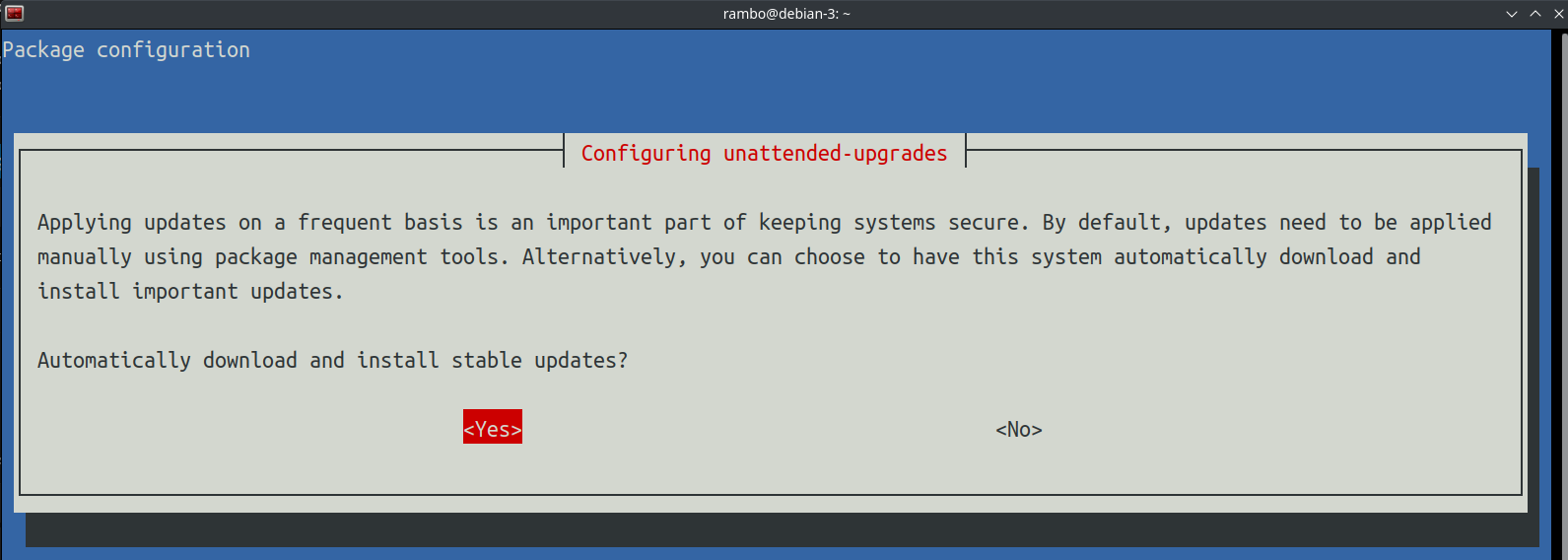
配置邮件系统(支持发送到外部邮箱)
# 安装邮件工具:msmtp + mailx
rambo@debian-3:~$ sudo apt install -y msmtp msmtp-mta bsd-mailx
===================================================
注:这里仅作说明,安装好上述的包后不会是这样,除非手动修改过
rambo@debian1:~$ ls -alh /usr/sbin/sendmail
lrwxrwxrwx 1 root root 12 Feb 5 2023 /usr/sbin/sendmail -> ../bin/msmtp
这这表示 apt、cron、unattended-upgrades 等使用 sendmail 的程序都会走 msmtp
===================================================
# 创建邮件日志文件,下面会用到
rambo@debian-3:~$ sudo touch /var/log/msmtp.log
rambo@debian-3:~$ sudo chown root:msmtp /var/log/msmtp.log
rambo@debian-3:~$ sudo chmod 664 /var/log/msmtp.log
rambo@debian-3:~$ sudo vim /etc/msmtprc
defaults
auth on
tls on
tls_trust_file /etc/ssl/certs/ca-certificates.crt
logfile /var/log/msmtp.log
account 126
host smtp.126.com
port 587
from zhangsan@126.com # 发件人邮箱
user zhangsan@126.com # 发件人邮箱
passwordeval "cat /etc/msmtp-pass"
account default : 126
rambo@debian-3:~$ sudo chmod 644 /etc/msmtprc
# 测试给另一个用户发送一个邮件
rambo@debian1:~$ echo -e "Subject: Test\n\nThis is a secure test email from msmtp." | msmtp --debug --from=default lisi@126.com
ignoring user configuration file /home/zhangsan/.msmtprc: No such file or directory
falling back to default account
using account default from /etc/msmtprc
host = smtp.126.com
port = 587
source ip = (not set)
proxy host = (not set)
proxy port = 0
socket = (not set)
timeout = off
protocol = smtp
domain = localhost
auth = choose
user = <发件人邮件>@126.com
password = *
passwordeval = *
ntlmdomain = (not set)
tls = on
tls_starttls = on
tls_trust_file = /etc/ssl/certs/ca-certificates.crt
tls_crl_file = (not set)
tls_fingerprint = (not set)
tls_key_file = (not set)
tls_cert_file = (not set)
tls_certcheck = on
tls_min_dh_prime_bits = (not set)
tls_priorities = (not set)
tls_host_override = (not set)
auto_from = off
maildomain = (not set)
from = default
allow_from_override = on
set_from_header = auto
set_date_header = auto
remove_bcc_headers = on
undisclosed_recipients = off
dsn_notify = (not set)
dsn_return = (not set)
logfile = /var/log/msmtp.log
logfile_time_format = (not set)
syslog = (not set)
aliases = (not set)
reading recipients from the command line
<-- 220 smtp.126.com ESMTP d9443c01ac2sm2712715ad.29 - 126
--> EHLO localhost
<-- 250-smtp.126.com at your service, [1xx.1xx.4x.11]
<-- 250-SIZE 35882577
<-- 250-8BITMIME
<-- 250-STARTTLS
<-- 250-ENHANCEDSTATUSCODES
<-- 250-PIPELINING
<-- 250-CHUNKING
<-- 250 SMTPUTF8
--> STARTTLS
<-- 220 2.0.0 Ready to start TLS
TLS session parameters:
(TLS1.3)-(ECDHE-X25519)-(ECSA-SEC256R1-SHA256)-(AES-256-GCM)
TLS certificate information:
Subject:
CN=smtp.126.com
Issuer:
C=US,O=Google Trust Services,CN=WR2
Validity:
Activation time: Mon 12 May 2025 04:43:59 AM EDT
Expiration time: Mon 04 Aug 2025 04:43:58 AM EDT
Fingerprints:
SHA256: 6E:71:18:EC:C3:0C:EB:7F:2D:F6:CD:4F:8C:AA:7D:53:83:1C:AF:13:50:14:A3:E6:7C:DA:55
SHA1 (deprecated): 5E:7F:1C:2E:7D:79:9A:D4:3F:E8:DB:14:E7:60:44:30
--> EHLO localhost
<-- 250-smtp.126.com at your service, [1xx.1xx.4x.11]
<-- 250-SIZE 35882577
<-- 250-8BITMIME
<-- 250-AUTH LOGIN PLAIN XOAUTH2 PLAIN-CLIENTTOKEN OAUTHBEARER XOAUTH
<-- 250-ENHANCEDSTATUSCODES
<-- 250-PIPELINING
<-- 250-CHUNKING
<-- 250 SMTPUTF8
--> AUTH PLAIN AHpoYW5ncGVuZ3poYW40NTZAZ21haWnp2enB2l0bWdvZG4=
<-- 235 2.7.0 Accepted
--> MAIL FROM:<default>
--> RCPT TO:<收件人地址@126.com>
--> DATA
<-- 250 2.1.0 OK d9443c01a7336-236030sm2712715ad.29 - gsmtp
<-- 250 2.1.5 OK d9443c01a7336-236030sm2712715ad.29 - gsmtp
<-- 354 Go ahead d9443c01a7336-236030sm2712715ad.29 - gsmtp
--> From: default
--> Date: Thu, 05 Jun 2025 22:24:37 -0400
--> Message-ID: <caa07a9769cc04d347d80cfee2.default@debian1>
--> Subject: Test
-->
--> This is a secure test email from 126.
--> .
<-- 250 2.0.0 OK 1749176681 d9443c01a7336-236030789c2sm2712715ad.29 - gsmtp
--> QUIT
<-- 221 2.0.0 closing connection d9443c01a7336-236030789c2sm2712715ad.29 - gsmtp
msmtp: cannot log to /var/log/msmtp.log: cannot open: Permission denied
msmtp: log info was: host=smtp.126.com tls=on auth=on user=发件人邮箱@126.com from=default recipients=收件人邮箱@126.com mailsize=170 smtpstatus=250 smtpmsg='250 2.0.0 OK 1749176681 d9443c01a7336-2360c2sm2712715ad.29 - 126' exitcode=EX_OK
邮箱和Unattended-Upgrade集成
rambo@debian1:~$ sudo vim /etc/apt/apt.conf.d/50unattended-upgrades
Unattended-Upgrade::Mail "lisi@126.com"; # 收件邮箱
Unattended-Upgrade::Sender "zhangsan@126.com"; # 发件邮箱地址(必须和msmtp账户匹配)
Unattended-Upgrade::MailCommandLine "/usr/bin/msmtp -t"; # 只让Unattended-Upgrade走msmtp
Unattended-Upgrade::Automatic-Reboot-Time "02:00"; # 即使启用重启,也只会在该时间重启,该命令只有在Automatic-Reboot为true时才生效
# 测试是否能通过 unattended-upgrades 发送邮件
1、执行一次模拟更新并触发邮件发送
rambo@debian1:~$ sudo unattended-upgrade -d
注:也可把sources.list改名后执行这条命令
2、实际更新:
rambo@debian1:~$ sudo unattended-upgrades
注:如果没有错误,默认不会发邮件;你可临时把:
Unattended-Upgrade::MailOnlyOnError "true";
改为:
Unattended-Upgrade::MailOnlyOnError "false";
来验证邮件是否会发送
# 查看unattended-upgrades的日志(确认是否触发邮件)
rambo@debian1:~$ cat /var/log/unattended-upgrades/unattended-upgrades.log
确认其中有:
Packages that will be upgraded:
...
Sending mail to: your_email@126.com
3、如果没有发生任何更新或错误,即它只有真正发生了升级操作(或错误)才发送邮件,像下面的情况它就不发送邮件
rambo@debian1:~$ sudo unattended-upgrade -d
Checking if system is running on battery is skipped. Please install powermgmt-base package to check power status and skip installing updates when the system is running on battery.
Starting unattended upgrades script
Allowed origins are: o=Debian,a=bookworm-security, o=Debian,a=bookworm-updates, origin=Debian,codename=bookworm,label=Debian, origin=Debian,codename=bookworm,label=Debian-Security, origin=Debian,codename=bookworm-security,label=Debian-Security
Initial blacklist:
Initial whitelist (not strict):
Marking not allowed <apt_pkg.PackageFile object: filename:'/var/lib/apt/lists/ftp.debian.org_debian_dists_bookworm-updates_main_i18n_Translation-en' a=stable-updates,c=main,v=12-updates,o=Debian,l=Debian arch='' site='ftp.debian.org' IndexType='Debian Translation Index' Size=398 ID:9> with -32768 pin
Marking not allowed <apt_pkg.PackageFile object: filename:'/var/lib/apt/lists/ftp.debian.org_debian_dists_bookworm-updates_main_binary-amd64_Packages' a=stable-updates,c=main,v=12-updates,o=Debian,l=Debian arch='amd64' site='ftp.debian.org' IndexType='Debian Package Index' Size=602 ID:8> with -32768 pin
Applying pinning: PkgFilePin(id=9, priority=-32768)
Applying pin -32768 to package_file: <apt_pkg.PackageFile object: filename:'/var/lib/apt/lists/ftp.debian.org_debian_dists_bookworm-updates_main_i18n_Translation-en' a=stable-updates,c=main,v=12-updates,o=Debian,l=Debian arch='' site='ftp.debian.org' IndexType='Debian Translation Index' Size=398 ID:9>
Applying pinning: PkgFilePin(id=8, priority=-32768)
Applying pin -32768 to package_file: <apt_pkg.PackageFile object: filename:'/var/lib/apt/lists/ftp.debian.org_debian_dists_bookworm-updates_main_binary-amd64_Packages' a=stable-updates,c=main,v=12-updates,o=Debian,l=Debian arch='amd64' site='ftp.debian.org' IndexType='Debian Package Index' Size=602 ID:8>
Using (^linux-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^kfreebsd-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^gnumach-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^.*-modules-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^.*-kernel-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^linux-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^kfreebsd-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^gnumach-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^.*-modules-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^.*-kernel-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$) regexp to find kernel packages
Using (^linux-.*-6\.1\.0\-30\-amd64$|^linux-.*-6\.1\.0\-30$|^kfreebsd-.*-6\.1\.0\-30\-amd64$|^kfreebsd-.*-6\.1\.0\-30$|^gnumach-.*-6\.1\.0\-30\-amd64$|^gnumach-.*-6\.1\.0\-30$|^.*-modules-6\.1\.0\-30\-amd64$|^.*-modules-6\.1\.0\-30$|^.*-kernel-6\.1\.0\-30\-amd64$|^.*-kernel-6\.1\.0\-30$|^linux-.*-6\.1\.0\-30\-amd64$|^linux-.*-6\.1\.0\-30$|^kfreebsd-.*-6\.1\.0\-30\-amd64$|^kfreebsd-.*-6\.1\.0\-30$|^gnumach-.*-6\.1\.0\-30\-amd64$|^gnumach-.*-6\.1\.0\-30$|^.*-modules-6\.1\.0\-30\-amd64$|^.*-modules-6\.1\.0\-30$|^.*-kernel-6\.1\.0\-30\-amd64$|^.*-kernel-6\.1\.0\-30$) regexp to find running kernel packages
pkgs that look like they should be upgraded:
Fetched 0 B in 0s (0 B/s)
fetch.run() result: 0
Packages blacklist due to conffile prompts: []
No packages found that can be upgraded unattended and no pending auto-removals
Extracting content from /var/log/unattended-upgrades/unattended-upgrades-dpkg.log since 2025-06-05 23:58:30
# 手动测试发送邮件
rambo@debian1:~$ echo -e "Subject: test321\n\nfrom root" | msmtp -t lisi@126.com
FAQ
Cache has broken packages, exiting
报错原因:apt缓存问题导致的升级中止
解决:先清理缓存和可能存在的锁文件,确保 apt 状态干净:
sudo rm /var/lib/apt/lists/lock
sudo rm /var/cache/apt/archives/lock
sudo rm /var/lib/dpkg/lock-frontend
sudo rm /var/lib/dpkg/lock




 浙公网安备 33010602011771号
浙公网安备 33010602011771号