CryptoHack Symmetry
题目脚本
from Crypto.Cipher import AES
KEY = ?
FLAG = ?
@chal.route('/symmetry/encrypt/<plaintext>/<iv>/')
def encrypt(plaintext, iv):
plaintext = bytes.fromhex(plaintext)
iv = bytes.fromhex(iv)
if len(iv) != 16:
return {"error": "IV length must be 16"}
cipher = AES.new(KEY, AES.MODE_OFB, iv)
encrypted = cipher.encrypt(plaintext)
ciphertext = encrypted.hex()
return {"ciphertext": ciphertext}
@chal.route('/symmetry/encrypt_flag/')
def encrypt_flag():
iv = os.urandom(16)
cipher = AES.new(KEY, AES.MODE_OFB, iv)
encrypted = cipher.encrypt(FLAG.encode())
ciphertext = iv.hex() + encrypted.hex()
return {"ciphertext": ciphertext}
这是一个冷门加密算法,现在已经不常见了,加密算法名字为 Output Feedback(OFB),该算法主要用于产生流密码,具体流程如下:
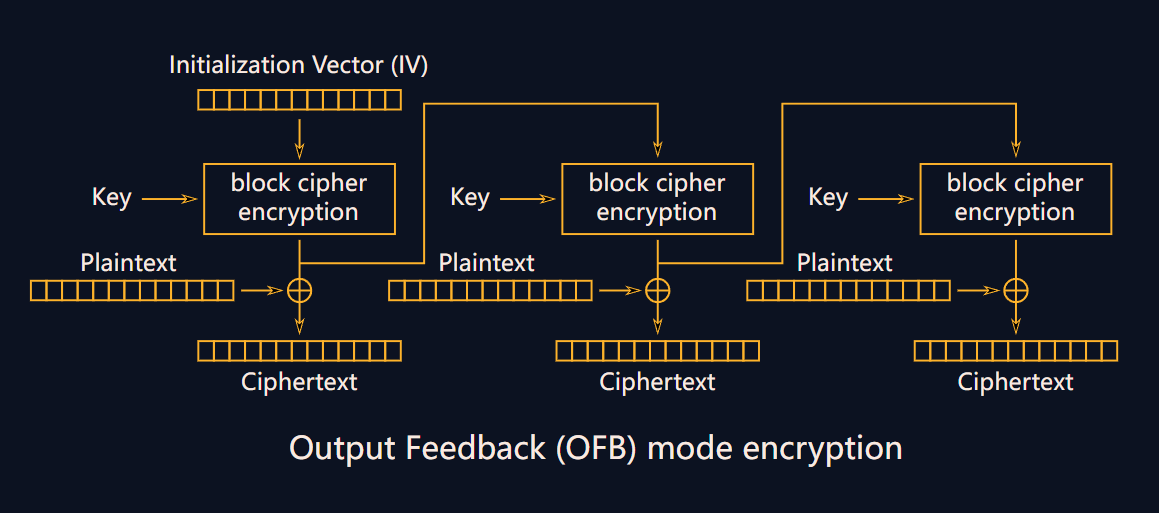
根据流程,我们发现,明文通过加密后得到密文时,所异或的 KEY 是按照顺序加密生成的密钥流,根据异或的对称性,我们可以通过对密文加密,由此得到我们的明文。
脚本如下
import requests
from tqdm import *
from Crypto.Util.number import *
from pwn import *
requests.adapters.DEFAULT_RETRIES = 100000
s = requests.Session()
s.timeout = (1000.0, 1000.0)
real_c1 = b'admin=False;expi'
fake_c1 = b'admin=True;00000'
encrypt_flag = requests.get(f'http://aes.cryptohack.org/symmetry/encrypt_flag')
result = encrypt_flag.text[15:][:-3]
iv = result[0:32]
ciphertext = result[32:]
print(iv)
print(ciphertext)
encrypt = requests.get(f'http://aes.cryptohack.org/symmetry/encrypt/{ciphertext}/{iv}')
result = bytes.fromhex(encrypt.text[15:][:-3])
print(result)


 浙公网安备 33010602011771号
浙公网安备 33010602011771号