NetDream wp
reverse
ezre
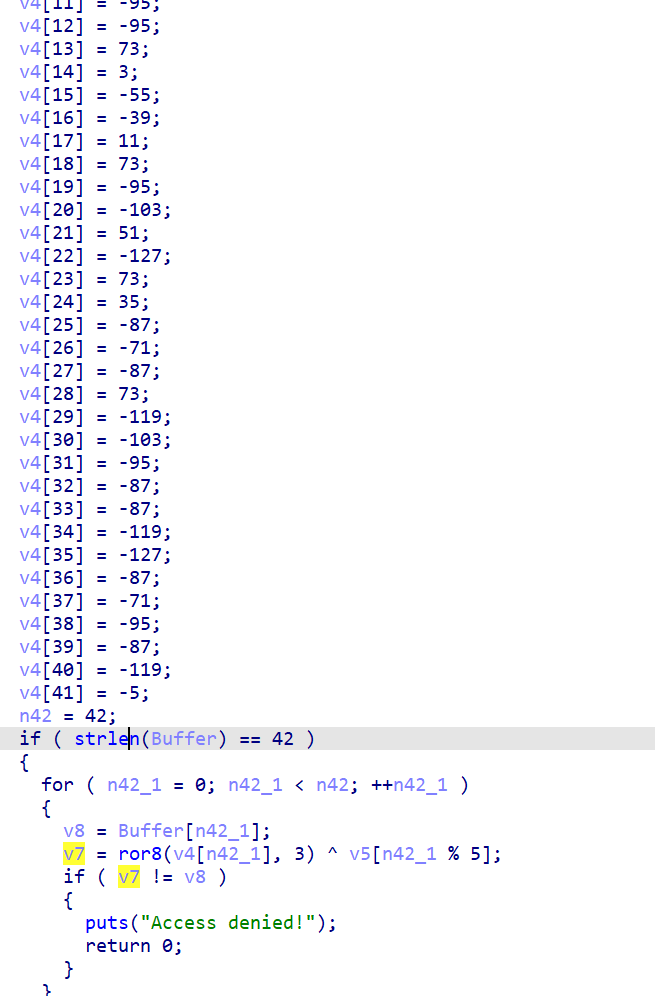
这里是正向求出flag在与输入flag作比较
#include <stdint.h>
#include <stdio.h>
#include <string.h>
#include <stdlib.h>
int ror8(unsigned __int8 a1, char n3)
{
return (a1 >> n3) | (a1 << (8 - n3));
}
int main()
{
char flag[42]={0};
int v6[]={1,2,3,4,5};
int v5[]={0x3B,0x73,0x13,0x1B,0xF3,0x81,0x81,0x81,0xB,0x89,0xA1,0xA1,0xA1,0x49,0x3,0xC9,0xD9,0xB,0x49,0xA1,0x99,0x33,0x81,0x49,0x23,0xA9,0xB9,0xA9,0x49,0x89,0x99,0xA1,0xA9,0xA9,0x89,0x81,0xA9,0xB9,0xA1,0xA9,0x89,0xFB};
for(int i=0;i<42;i++){
int v9=flag[i];
int v4=ror8(v5[i],3);
int v8 = v4 ^ v6[i%5];
v9=v8;
printf("%c",v9);
}
printf("%s",flag);
return 0;
}//flag{123e4567-e89b-12d3-a456-426614174000}
NMTZ_LIKE_RE
直接将anti_debug的调用nop掉
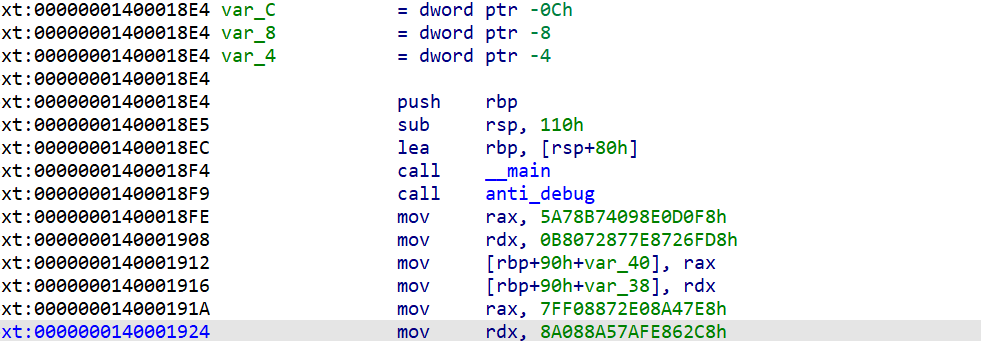
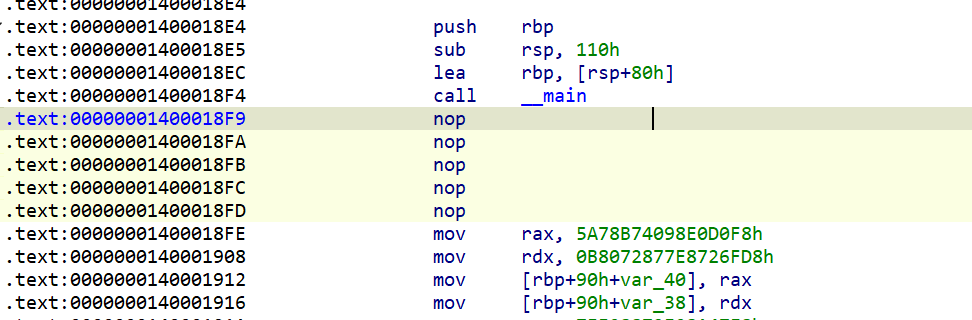
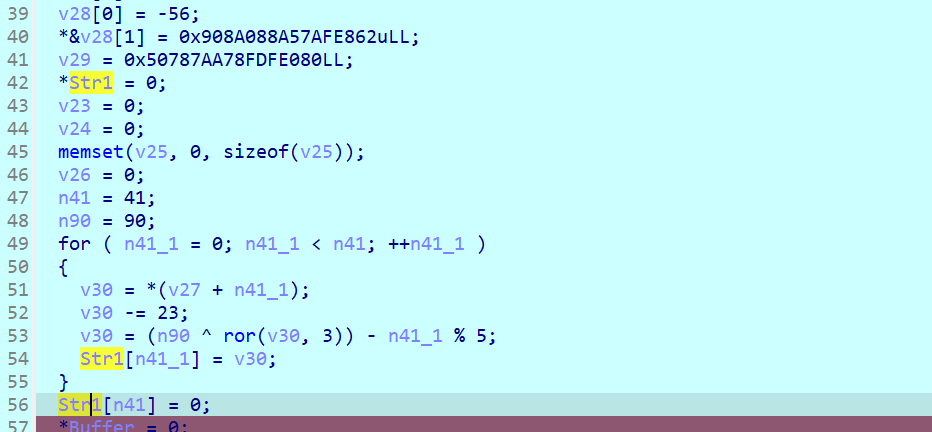
这里也是在计算flag,直接动调
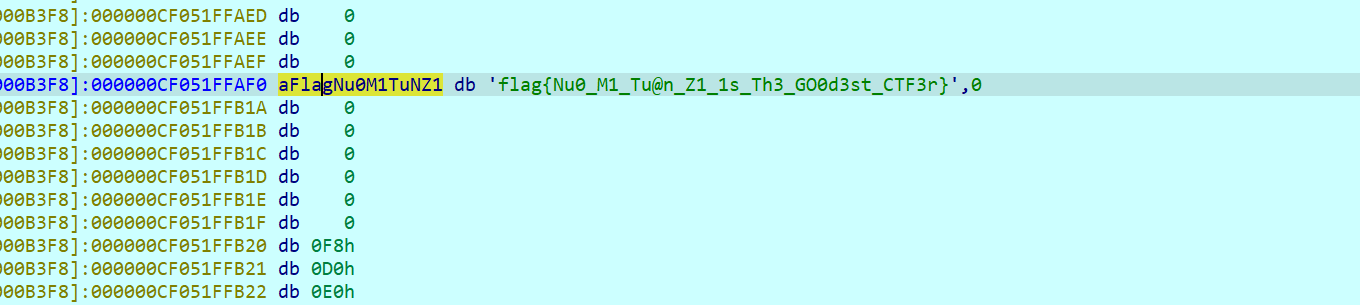
MISC
I_AM_K
import base64
def decrypt(ciphertext_hex):
# Step 1: Convert hex to bytes and then to string (Caesar-shifted Base64)
caesar_shifted_base64 = bytes.fromhex(ciphertext_hex).decode('utf-8')
# Step 2: Brute-force Caesar shift (0 to 25)
for shift in range(26):
reversed_caesar = ""
for char in caesar_shifted_base64:
if char.isalpha():
if char.isupper():
reversed_char = chr(((ord(char) - ord('A') - shift) % 26 + ord('A')))
else:
reversed_char = chr(((ord(char) - ord('a') - shift) % 26 + ord('a')))
reversed_caesar += reversed_char
else:
reversed_caesar += char
# Step 3: Base64 decode
try:
encrypted_bytes = base64.b64decode(reversed_caesar)
except:
continue # Skip if Base64 decoding fails
# Step 4: Brute-force key_sum (0 to 255)
for key_sum in range(256):
decrypted = []
for byte in encrypted_bytes:
decrypted_char = (byte - key_sum) % 256
decrypted.append(decrypted_char)
# Step 5: Convert to string and check for "flag{...}"
try:
decrypted_text = bytes(decrypted).decode('utf-8')
if decrypted_text.startswith("flag{") and decrypted_text.endswith("}"):
print(f"Shift: {shift}, Key Sum: {key_sum}, Decrypted: {decrypted_text}")
except:
continue # Skip if decoding fails
ciphertext_hex = "686545356839417466377a5266364133695a54556a376857696f6c4e67377a5166364248"
decrypt(ciphertext_hex)
ezimg
图片最下面有base64
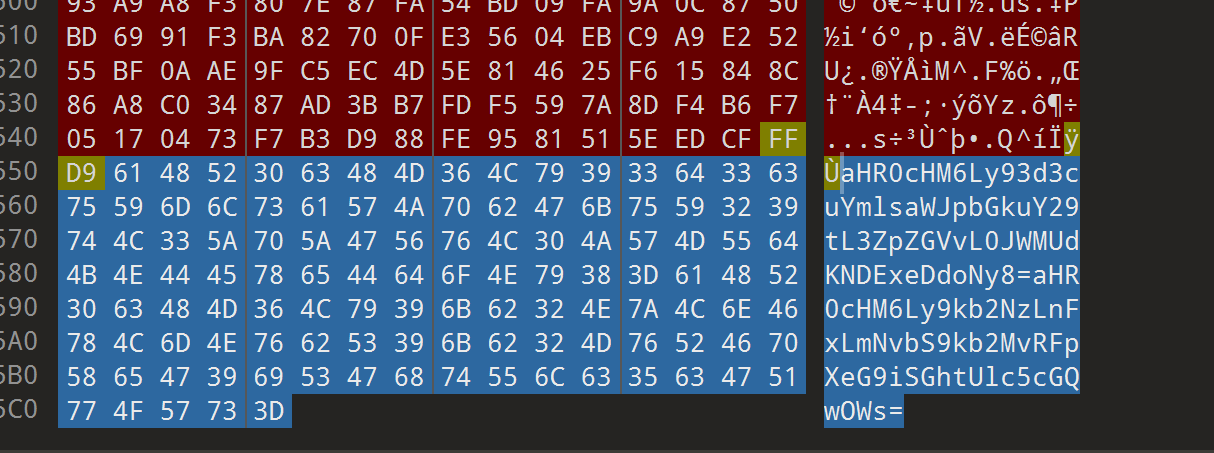
解出来是两个网址
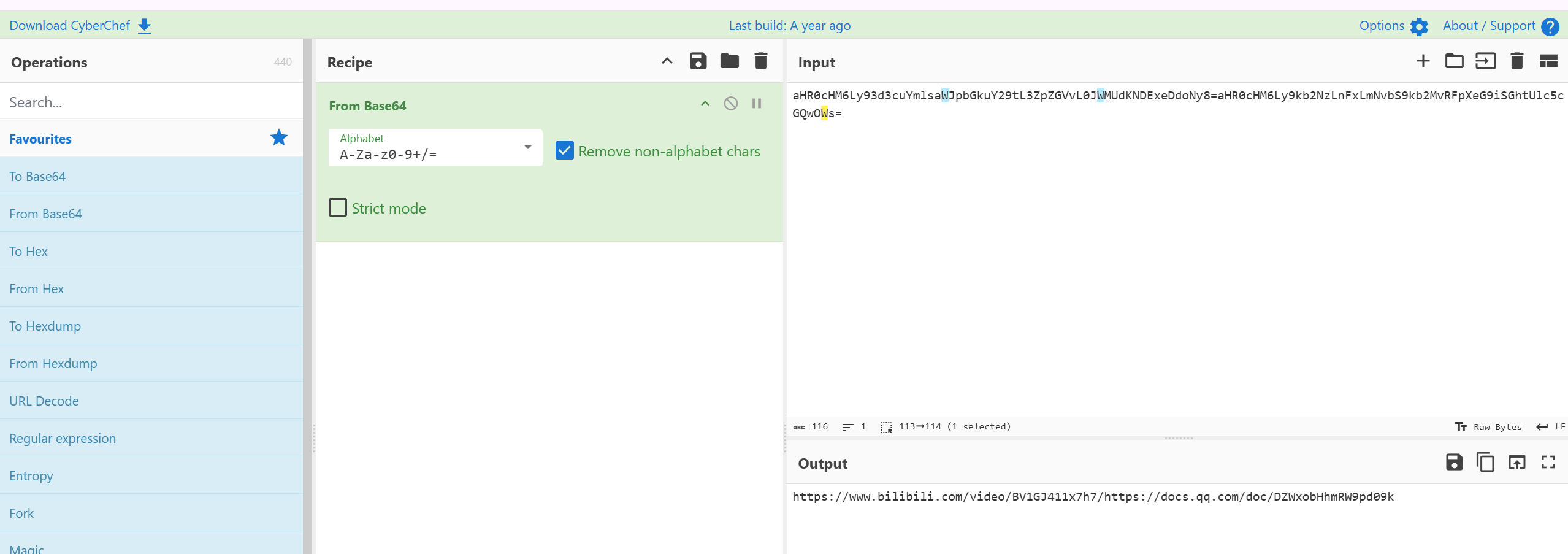
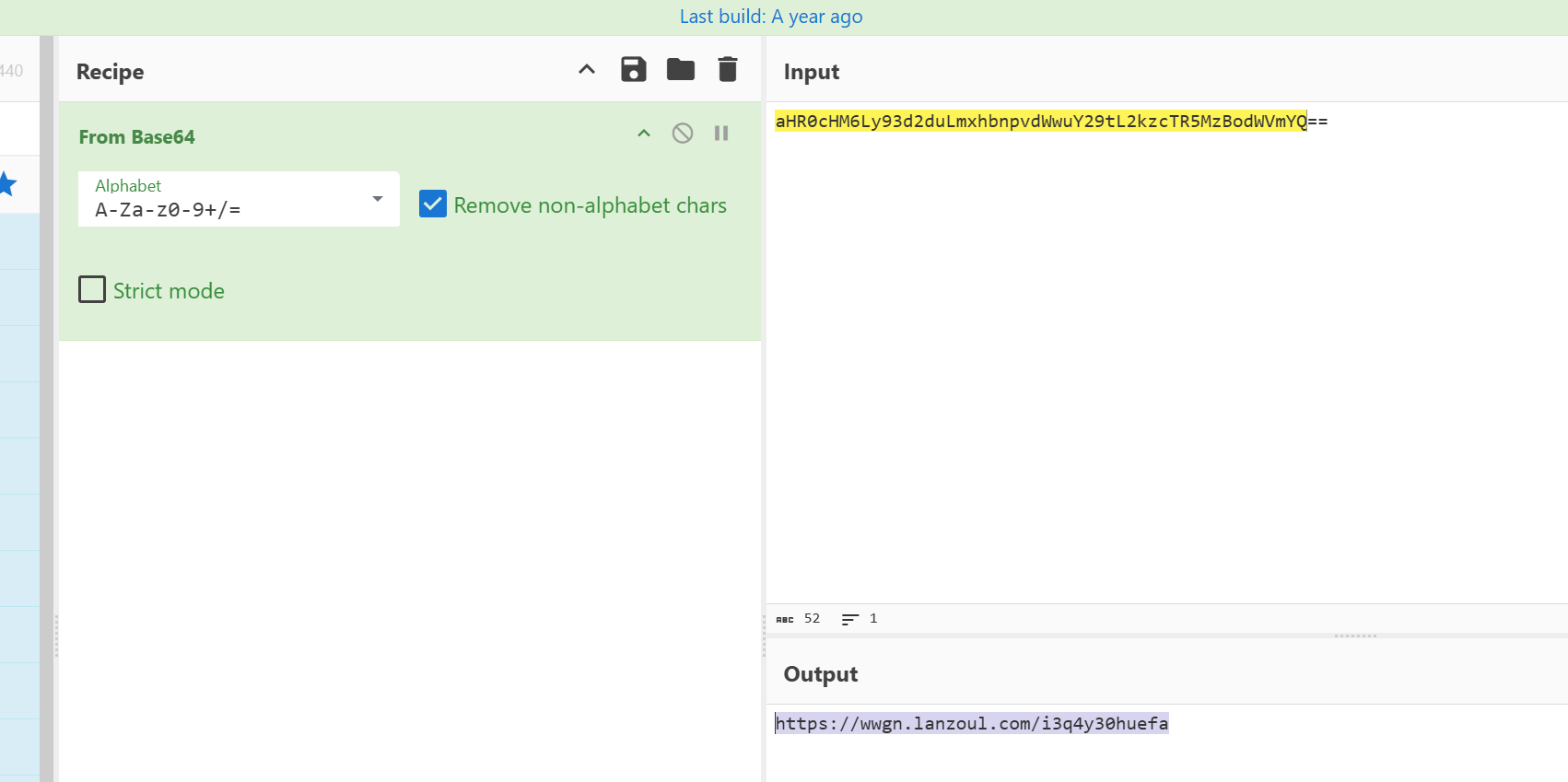
文档的图片下面还有base64,网址下载zip
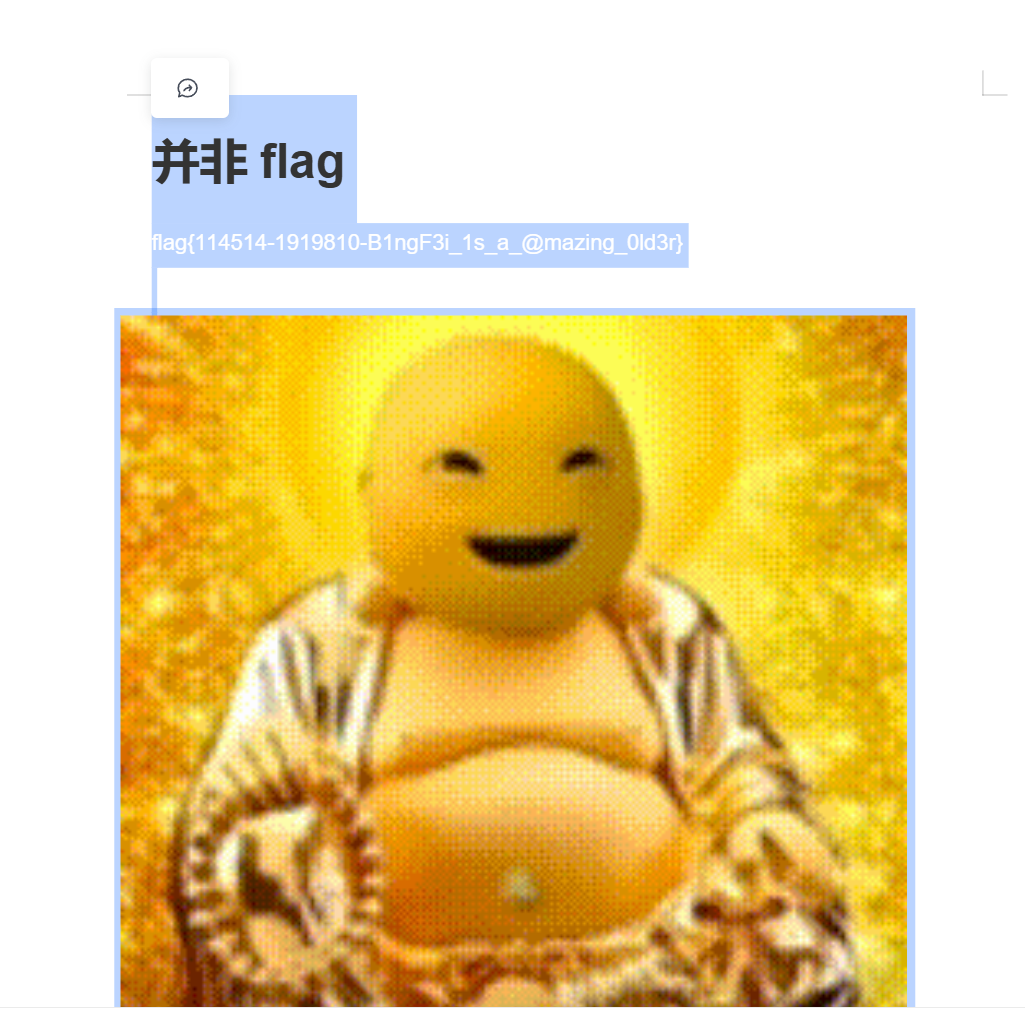
看下面进度条应该有隐藏,ctrl+A ctrl+C ctrl+V到记事本看到内容,fernet加密,key就是文档里面的flag{……}
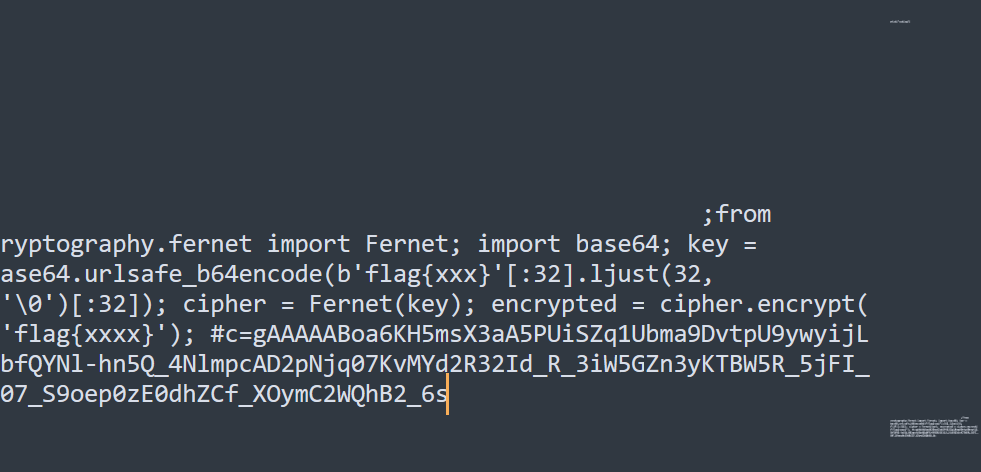
from cryptography.fernet import Fernet
import base64
# 已知的完整密钥
full_key = "flag{114514-1919810-B1ngF3i_1s_a_@mazing_0ld3r}"
# 转换为字节并处理成32字节
key_bytes = full_key.encode()[:32] # 取前32字节
key_bytes = key_bytes.ljust(32, b'\0') # 不足32字节则用空字节填充
# 生成Fernet密钥
fernet_key = base64.urlsafe_b64encode(key_bytes)
# 创建Fernet实例
cipher = Fernet(fernet_key)
# 给定的密文
encrypted_message = b'gAAAAABoa6KH5msX3aA5PUiSZq1Ubma9DvtpU9ywyijLEbfQYNl-hn5Q_4NlmpcAD2pNjq07KvMYd2R32Id_R_3iW5GZn3yKTBW5R_5jFI_307_S9oep0zE0dhZCf_XOymC2WQhB2_6s'
# 解密
try:
decrypted_message = cipher.decrypt(encrypted_message)
print("解密成功!")
print("解密结果:", decrypted_message.decode())
except Exception as e:
print("解密失败:", e)
osint
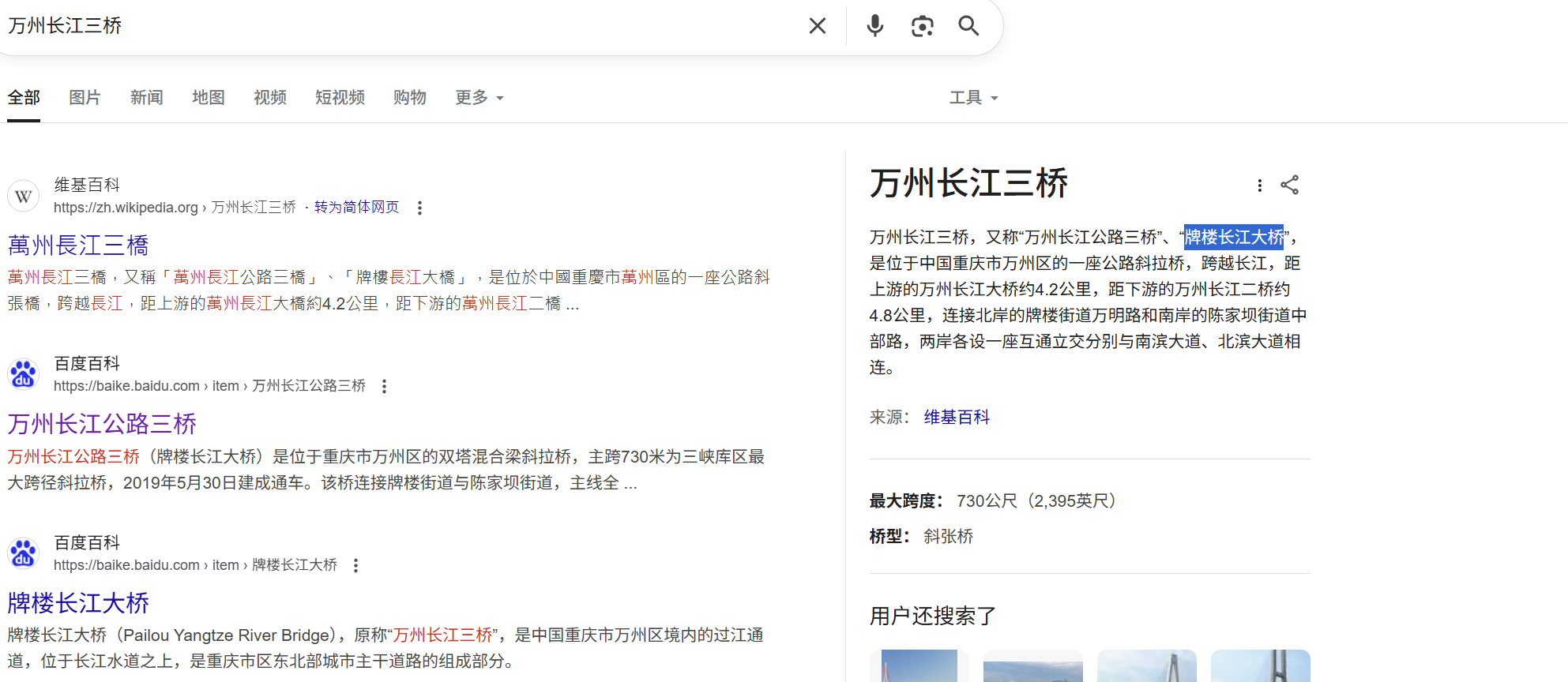
Bridge
谷歌搜索
尝试不同的名字
Where_am_i
依旧谷歌

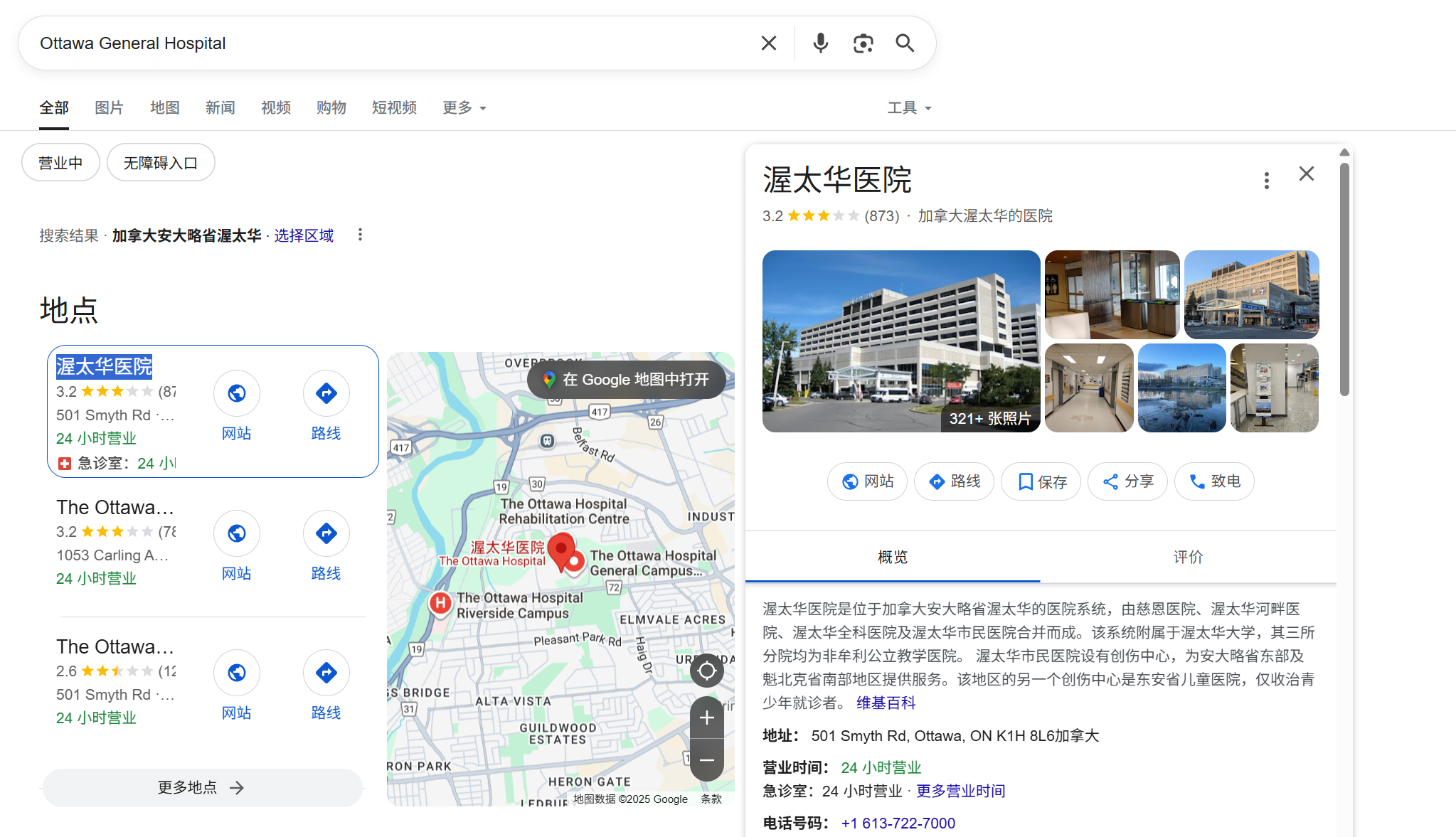
比桥简单
crypto
EzRSA
e=3,特别小,直接用脚本
#python3
## -*- coding: utf-8 -*-#
from gmpy2 import iroot
import libnum
e = 3
n = 3256593900815599638610948588846270419272266309072355018531019815816383416972716648196614202756266923662468043040766972587895880348728177684427108179441398076920699534139836200520410133083399544975367893285080239622582380507397956076038256757810824984700446326253944197017126171652309637891515864542581815539
c = 1668144786169714702301094076704686642891065952249900945234348491495868262367689770718451252978033214169821458376529832891775500377565608075759008139982766645172498702491199793075638838575243018129218596030822468832530007275522627172632933
k = 0
while 1:
res = iroot(c+k*n,e) #c+k*n 开3次方根 能开3次方即可
#print(res)
#res = (mpz(13040004482819713819817340524563023159919305047824600478799740488797710355579494486728991357), True)
if(res[1] == True):
print(libnum.n2s(int(res[0]))) #转为字符串
break
k=k+1
Quaternion_Lock
ai解的
# -*- coding: utf-8 -*-
import sys
p = 9223372036854775783
e = 65537
subgroup_order = 60480
X = (7380380986429696832, 34163292457091182, 3636630423226195928, 3896730209645707435)
Y = (1015918725738180802, 4456058114364993854, 0, 0)
def qmul(q1, q2, p):
a1, b1, c1, d1 = q1
a2, b2, c2, d2 = q2
return (
(a1*a2 - b1*b2 - c1*c2 - d1*d2) % p,
(a1*b2 + b1*a2 + c1*d2 - d1*c2) % p,
(a1*c2 - b1*d2 + c1*a2 + d1*b2) % p,
(a1*d2 + b1*c2 - c1*b2 + d1*a2) % p
)
def qconj(q, p):
a,b,c,d = q
return (a % p, (-b) % p, (-c) % p, (-d) % p)
def qnorm(q, p):
a,b,c,d = q
return (a*a + b*b + c*c + d*d) % p
def qinv(q, p):
n = qnorm(q, p)
inv_n = pow(n, -1, p)
a,b,c,d = qconj(q, p)
return (a*inv_n % p, b*inv_n % p, c*inv_n % p, d*inv_n % p)
def qpow(q, exp, p):
res = (1,0,0,0)
base = q
while exp:
if exp & 1:
res = qmul(res, base, p)
base = qmul(base, base, p)
exp >>= 1
return res
def decode_flag_tuple(F):
# 对应 encode_flag 的切片长度:8,7,7,7
lens = [8,7,7,7]
bs = b''.join(int(x).to_bytes(L, 'big') for x, L in zip(F, lens))
try:
return bs.decode()
except:
return bs
def main():
g = (2,1,0,0)
h = qpow(g, ((p*p - 1) // subgroup_order), p)
# Y = (h^r)^e = (h^e)^r
he = qpow(h, e, p)
acc = (1,0,0,0)
r = None
for i in range(1, subgroup_order):
acc = qmul(acc, he, p)
if acc == Y:
r = i
break
if r is None:
print("r not found")
sys.exit(1)
K = qpow(h, r, p)
K_inv = qinv(K, p)
# X = K * F * K^{-1} => F = K^{-1} * X * K
F = qmul(qmul(K_inv, X, p), K, p)
flag = decode_flag_tuple(F)
print("[+] r =", r)
print("[+] K =", K)
print("[+] F (tuple) =", F)
print("[+] flag =", flag)
if __name__ == "__main__":
main()


 浙公网安备 33010602011771号
浙公网安备 33010602011771号