moectf2025 reverse wp
逆向工程入门指北
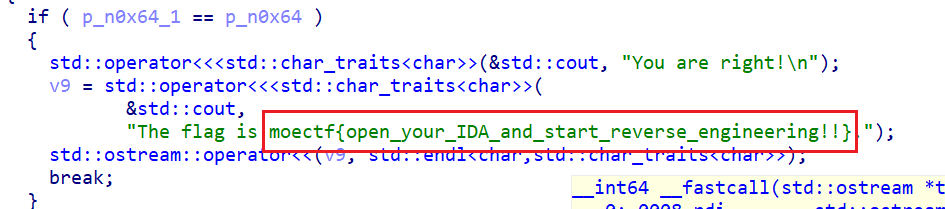
ida里面的明文
upx
没有修改的upx,直接upx -d
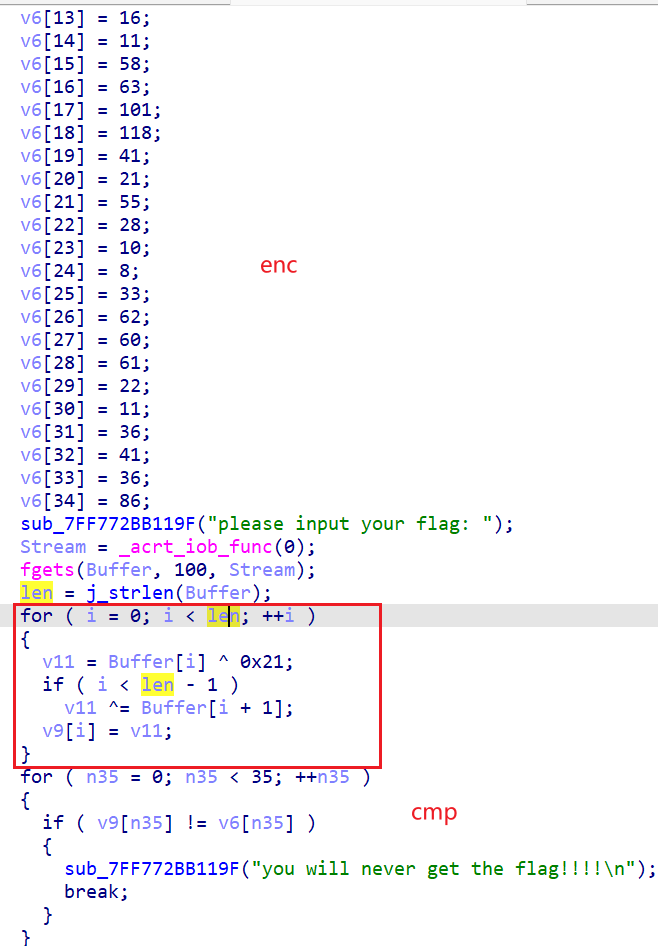
逻辑也很简单,但是我先一直没有解出来,看到提示说小心fgets,fgets会读取'\n',在计算strlen的时候会将'\n'也算上,所以最后一个字符不是'}'而是'\n'
#include <stdio.h>
#include <string.h>
#include <stdlib.h>
#include<stdint.h>
int main()
{
unsigned char v6[35]={0};
v6[0] = 35;
v6[1] = 43;
v6[2] = 39;
v6[3] = 54;
v6[4] = 51;
v6[5] = 60;
v6[6] = 3;
v6[7] = 72;
v6[8] = 100;
v6[9] = 11;
v6[10] = 29;
v6[11] = 118;
v6[12] = 123;
v6[13] = 16;
v6[14] = 11;
v6[15] = 58;
v6[16] = 63;
v6[17] = 101;
v6[18] = 118;
v6[19] = 41;
v6[20] = 21;
v6[21] = 55;
v6[22] = 28;
v6[23] = 10;
v6[24] = 8;
v6[25] = 33;
v6[26] = 62;
v6[27] = 60;
v6[28] = 61;
v6[29] = 22;
v6[30] = 11;
v6[31] = 36;
v6[32] = 41;
v6[33] = 36;
v6[34] = 86;
int flag[36] = {0};
flag[35] = '\n';
for(int i=34;i>=0;i--){
flag[i] = v6[i] ^ flag[i+1] ^ 0x21;
}
for(int i=0;i<36;i++){
printf("%c",flag[i]);
}
}
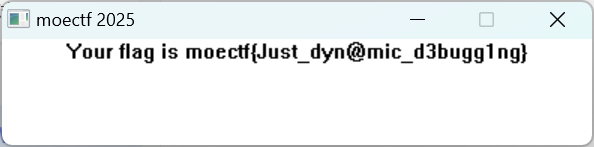
speed
运行之后屏幕闪了一下,不太明显,看到main函数是操作 windows窗口
在窗口销毁前断点
base
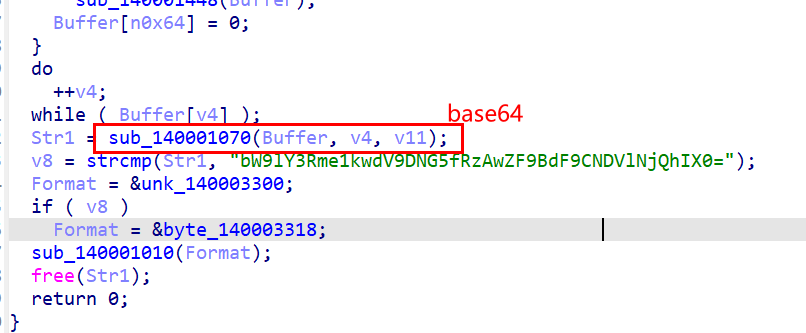
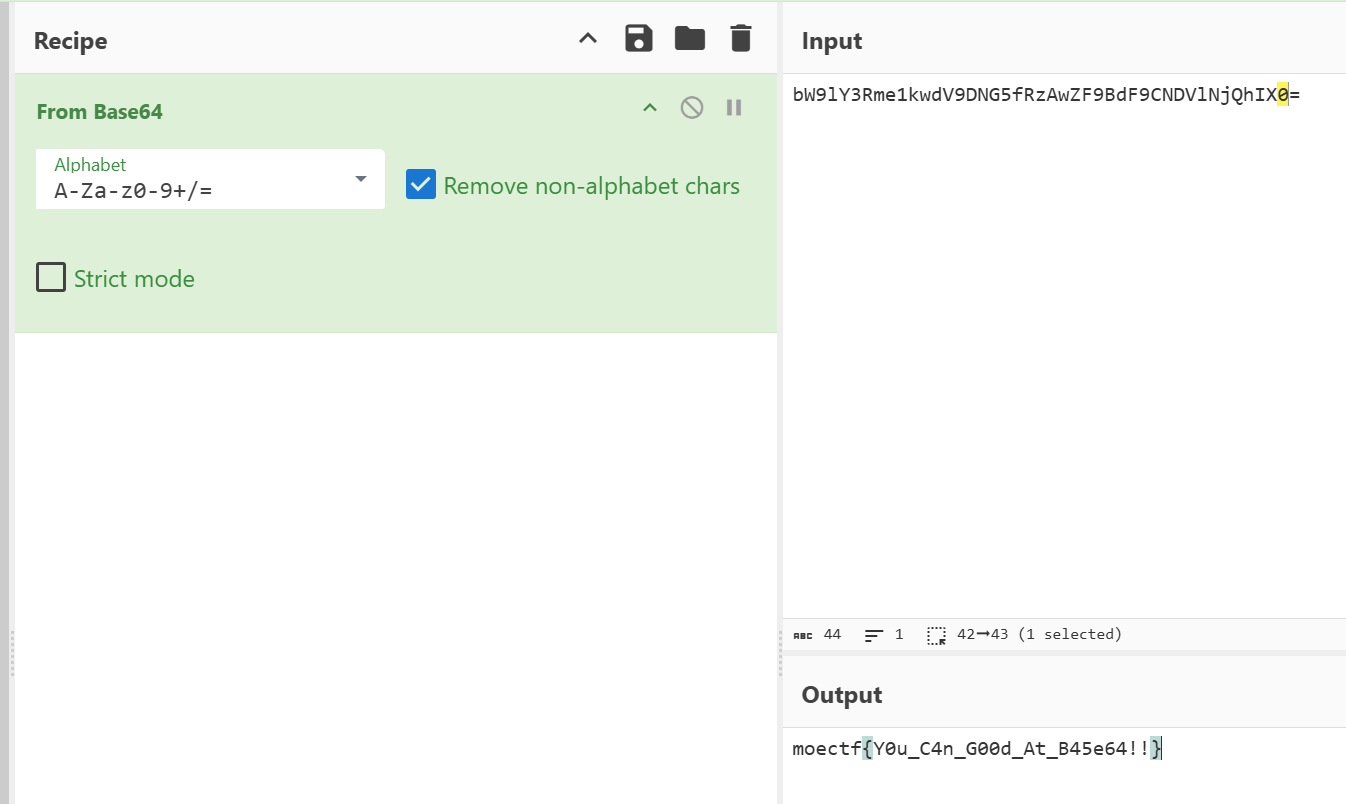
标准base64
mazegame
迷宫题,shift+f12直接看到迷宫,尝试走一下1是墙壁
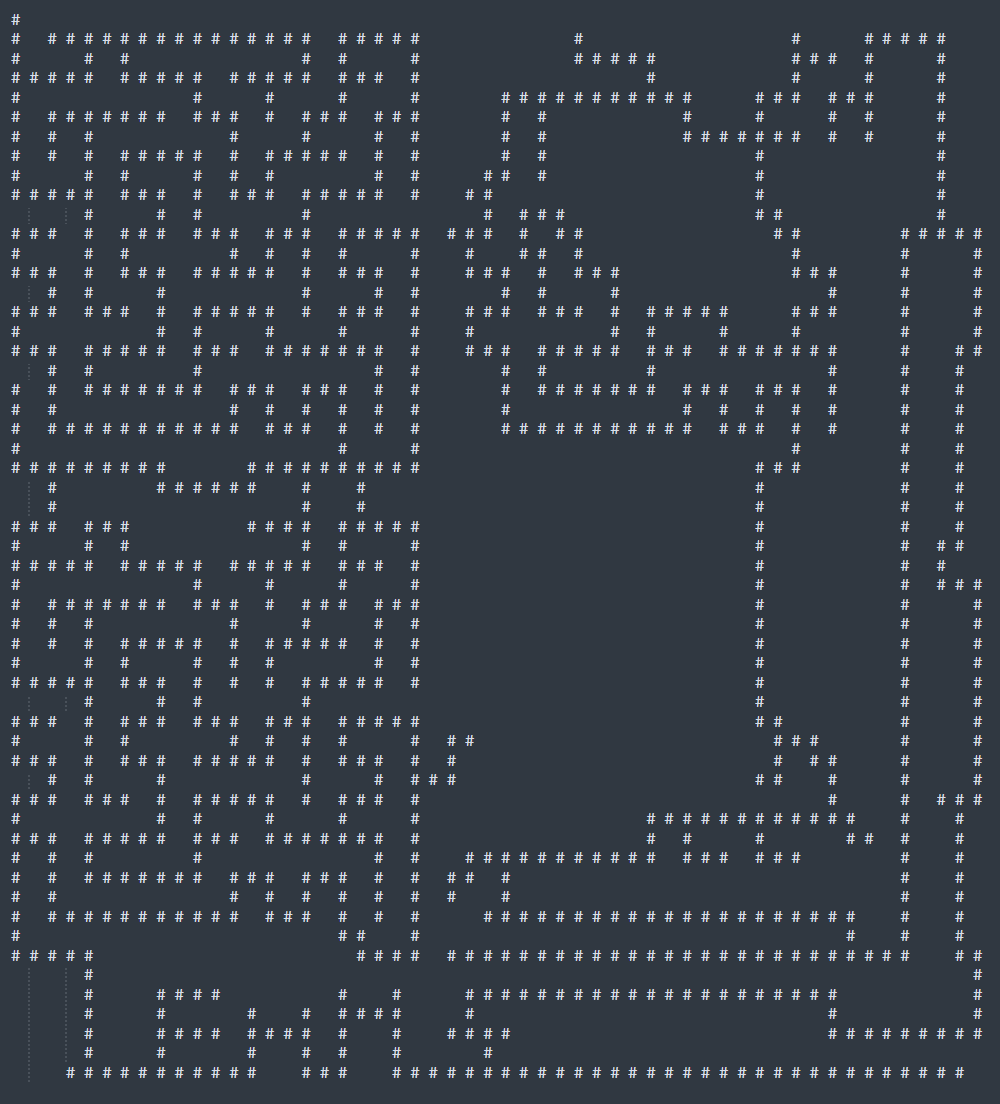
迷宫长这样,猜测(1,1)是S
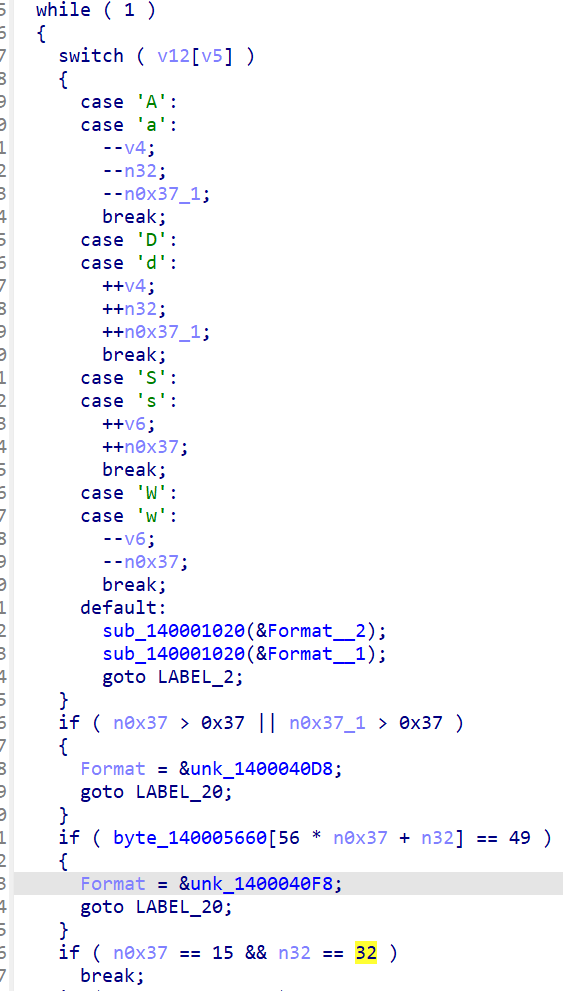
n0x37是控制上下的,n32是控制左右的,那么(15,32)就是E
from collections import deque
# 设置二维四向迷宫, 如果题目是多个小迷宫问题, 拆分多次调用脚本获取路径即可
# 每一排后面要逗号隔开,对齐++++++++++++++++++++++++++
maze = [
[1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1,
1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1],
[1, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 1, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 1,
1, 1, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 0, 0, 0, 0, 1, 1, 1],
[1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0,
1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1],
[1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0,
1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1],
[1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0,
0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 1, 1, 0, 1, 1, 1],
[1, 0, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 1, 0, 1, 0, 1, 0, 1, 1, 1, 1, 1, 1,
1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1],
[1, 0, 1, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 0, 1, 0, 1, 0, 1, 0, 0, 0, 0, 0,
1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1],
[1, 0, 1, 0, 1, 0, 1, 0, 0, 0, 0, 0, 1, 0, 1, 0, 0, 0, 0, 0, 1, 0, 1, 0, 1, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0,
1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1],
[1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1, 1, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0,
0, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1],
[1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 1, 0, 1, 1, 0, 0, 1, 1, 1, 1, 0, 1, 1, 1, 1,
1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1],
[1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0,
0, 1, 0, 1, 1, 0, 0, 1, 0, 1, 0, 0, 1, 1, 1, 0, 1, 1, 1],
[1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 1, 1, 0, 0,
0, 1, 0, 0, 0, 1, 0, 0, 1, 0, 0, 1, 1, 0, 0, 0, 0, 0, 1],
[1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 0, 1, 1, 0, 0, 1, 0, 1, 1, 1, 1,
1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1],
[1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0,
0, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1],
[1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1,
1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1],
[1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0,
0, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1],
[1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0,
1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1],
[1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 1, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 1, 0,
0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 1, 0, 1, 1, 0, 0, 1],
[1, 1, 1, 0, 1, 0, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 1, 1, 1, 0, 1, 0, 1, 1, 1, 1, 1, 0,
1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 1, 0, 1, 1],
[1, 0, 1, 0, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 1, 0, 1, 0, 1, 0, 0, 0, 0, 0, 0, 0,
1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 1, 1, 0, 1, 1],
[1, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1,
1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 0, 1, 1],
[1, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 1, 1, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0,
0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 0, 1, 1],
[1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1,
1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 0, 1, 1],
[1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 1, 1, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 0, 0, 0,
0, 1, 1, 1, 1, 0, 0, 0, 1, 1, 1, 1, 1, 0, 1, 1, 0, 1, 1],
[1, 1, 1, 0, 1, 1, 1, 1, 1, 0, 0, 0, 0, 0, 0, 1, 1, 0, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 1, 0, 1, 1,
1, 0, 1, 1, 1, 0, 1, 1, 0, 0, 0, 0, 1, 0, 1, 1, 0, 1, 1],
[1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1,
1, 1, 0, 1, 1, 0, 1, 1, 0, 0, 0, 0, 1, 0, 1, 1, 0, 1, 1],
[1, 0, 0, 0, 1, 0, 0, 0, 1, 1, 1, 1, 1, 1, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 1, 1, 1, 1, 1, 0, 1, 0, 1, 1, 0, 1, 1,
1, 0, 1, 1, 1, 0, 1, 1, 0, 0, 0, 0, 1, 0, 1, 1, 0, 1, 1],
[1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 0, 0, 0,
0, 1, 1, 1, 1, 0, 1, 1, 0, 0, 0, 0, 1, 0, 1, 0, 0, 1, 1],
[1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1,
1, 1, 1, 1, 1, 0, 1, 1, 0, 0, 0, 0, 1, 0, 1, 0, 1, 1, 1],
[1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 0, 0, 0, 1, 0, 0, 0, 1, 1,
0, 0, 0, 1, 1, 0, 1, 1, 0, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1],
[1, 0, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0,
1, 1, 1, 1, 1, 0, 1, 1, 0, 0, 0, 0, 1, 0, 1, 1, 1, 0, 1],
[1, 0, 1, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0,
1, 1, 1, 1, 1, 0, 1, 1, 0, 0, 0, 0, 1, 0, 1, 1, 1, 0, 1],
[1, 0, 1, 0, 1, 0, 1, 0, 0, 0, 0, 0, 1, 0, 1, 0, 0, 0, 0, 0, 1, 0, 1, 0, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0,
1, 1, 1, 1, 1, 0, 1, 1, 0, 0, 0, 0, 1, 0, 1, 1, 1, 0, 1],
[1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1, 1, 1, 1, 1, 0, 1, 0, 1, 1, 1, 1, 0, 0, 0, 1, 0, 0, 0, 1, 1,
0, 0, 0, 1, 1, 0, 1, 1, 0, 0, 0, 0, 1, 0, 1, 1, 1, 0, 1],
[1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 0, 0, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1,
1, 1, 1, 1, 1, 0, 1, 1, 0, 0, 0, 0, 1, 0, 1, 1, 1, 0, 1],
[1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0,
0, 0, 0, 1, 1, 0, 1, 1, 0, 0, 0, 0, 1, 0, 1, 1, 1, 0, 1],
[1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1,
1, 1, 1, 1, 1, 0, 0, 1, 1, 0, 0, 1, 1, 0, 1, 1, 1, 0, 1],
[1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 1,
1, 1, 1, 1, 1, 1, 0, 0, 0, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1],
[1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 1, 0, 1, 1, 1, 0, 0, 0, 0, 0,
1, 1, 1, 1, 1, 1, 0, 1, 0, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1],
[1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 0, 0, 0, 1, 1, 0, 0, 1, 1, 0, 0, 1, 1, 1,
1, 1, 1, 1, 1, 0, 0, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1],
[1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1,
1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 0, 0, 0, 1],
[1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 0, 0, 0, 1, 0, 0, 1, 1, 0,
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 1, 0, 1, 1, 0, 1, 1],
[1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0,
1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 0, 0, 1, 0, 1, 1, 0, 1, 1],
[1, 0, 1, 0, 1, 0, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0,
1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 1, 1, 0, 1, 1, 0, 1, 1],
[1, 0, 1, 0, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1,
1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 0, 1, 1],
[1, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1,
1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 1, 0, 1, 1],
[1, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0,
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 1, 0, 1, 1, 0, 1, 1],
[1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 0, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1,
1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 0, 1, 1, 0, 1, 1],
[1, 0, 0, 0, 0, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0,
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 1, 0, 0, 1],
[1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1,
1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1],
[1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 0, 0, 0, 1, 1, 0, 0, 1, 1, 0, 1, 1, 0, 1, 1, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0,
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1],
[1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 0, 1, 1, 0, 1, 0, 0, 0, 0, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1,
1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1],
[1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 0, 0, 0, 1, 0, 0, 0, 0, 1, 0, 1, 1, 0, 1, 1, 0, 0, 0, 0, 1, 1, 1, 1, 1, 1, 1, 1,
1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1],
[1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 0, 1, 1, 0, 1, 0, 1, 1, 0, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1,
1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 1, 0, 0, 0, 1, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0,
0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1,
1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1]
]
path_len = 0x7fffffff # 如果题目未给出终点坐标,则一定会指定路径的长度,在此处修改路径长度,否则请保留path_len的极大值
#已知步长时更改,否则不管+++++++++++++++++++++++++++++++++
# 进行BFS寻找路径
def bfs(start, end, barrier):
directions = [(0, 1), (1, 0), (0, -1), (-1, 0)] # 定义四个方向的移动
for i in range(len(maze)): # 获取起点和终点在列表中的索引
for j in range(len(maze[i])):
if (maze[i][j] == start):
start = (i, j)
if (maze[i][j] == end):
end = (i, j)
# 以下均是bfs算法套路
queue = deque()
queue.append((start, [start])) # (当前位置, 路径)
visited = set()
visited.add(start)
while queue:
position, path = queue.popleft()
if position == end:
return path
elif len(path) == path_len:
return path
for d in directions:
next_position = (position[0] + d[0], position[1] + d[1])
if 0 <= next_position[0] < len(maze) and 0 <= next_position[1] < len(maze[0]) and \
maze[next_position[0]][next_position[1]] != barrier and next_position not in visited:
queue.append((next_position, path + [next_position]))
visited.add(next_position)
return None
# 执行BFS搜索并打印结果
if __name__ == '__main__':
#更改起点和终点的坐标,如果知道path而坐标未知则注释掉+++++++++++++++++++++++++++++
maze[1][1] = 'S' #如果题目给了起点终点的坐标,在这里直接给起点和终点添加特征
maze[15][32] = 'E'#前为横坐标,后为纵坐标
path = bfs('S', 'E', 1) # bfs函数传入参数代表起点、终点、障碍的特征(若题目给出的数据无特征, 手动添加特征即可, 通常障碍是1也有可能是0或其它字符如'#')
print("移动路径坐标:", path)
print("移动路径方位:{", end='')
for i in range(1, len(path)):
x1, y1, x2, y2 = path[i - 1][0], path[i - 1][1], path[i][0], path[i][1]
if (x1 > x2): # 上
print("w", end='')
elif (x1 < x2): # 下
print("s", end='')
elif (y1 > y2): # 左
print("a", end='')
elif (y1 < y2): # 右
print("d", end='')
print('}')
A cup of tea
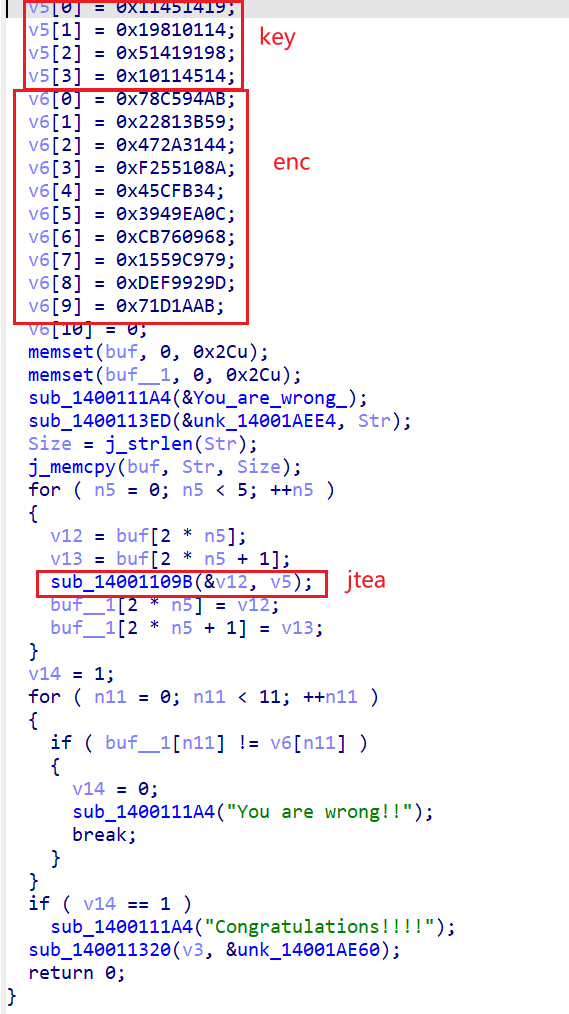
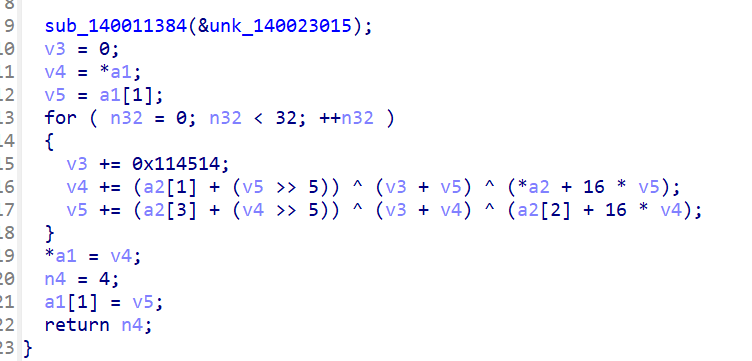
只换了delta的魔改tea
#include <stdio.h>
#include <stdint.h>
void decrypt (uint32_t *v,uint32_t *k){
uint32_t delta=0x114514;
uint32_t v0=v[0],v1=v[1],sum=delta * 32,i;
uint32_t k0=k[0],k1=k[1],k2=k[2],k3=k[3];
for (i=0;i<32;i++){
v1-=((v0<<4)+k2)^(v0+sum)^((v0>>5)+k3);
v0-=((v1<<4)+k0)^(v1+sum)^((v1>>5)+k1);
sum-=delta;
}
v[0]=v0;v[1]=v1;
}
int main()
{
uint32_t v[10]={0x78c594ab,0x22813b59,0x472a3144,0xf255108a,0x45cfb34,0x3949ea0c,0xcb760968,0x1559c979,0xdef9929d,0x71d1aab},
k[4]={289739801,427884820,1363251608,269567252};
for(int i=0;i<5;i++){
uint32_t temp[2] = {v[i*2],v[i*2+1]};
decrypt(temp,k);
printf("%s\n",temp);
}
return 0;
}
flag:moectf{h3r3_4_cuP_0f_734_f0R_y0U!!!!!!}
flower
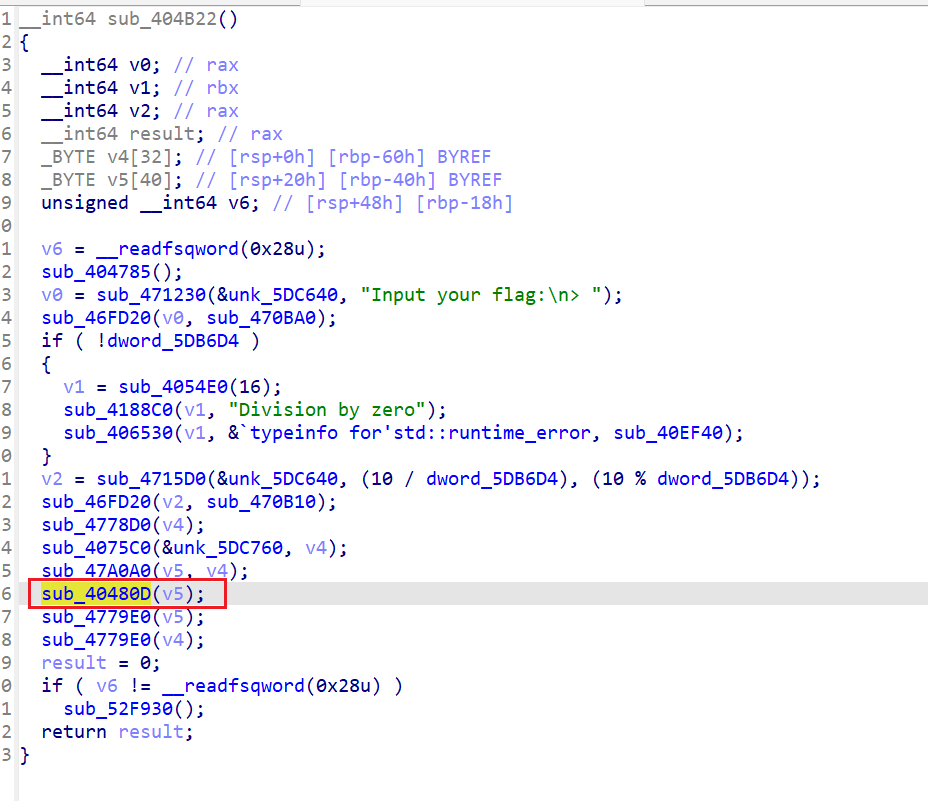
该函数无法反汇编
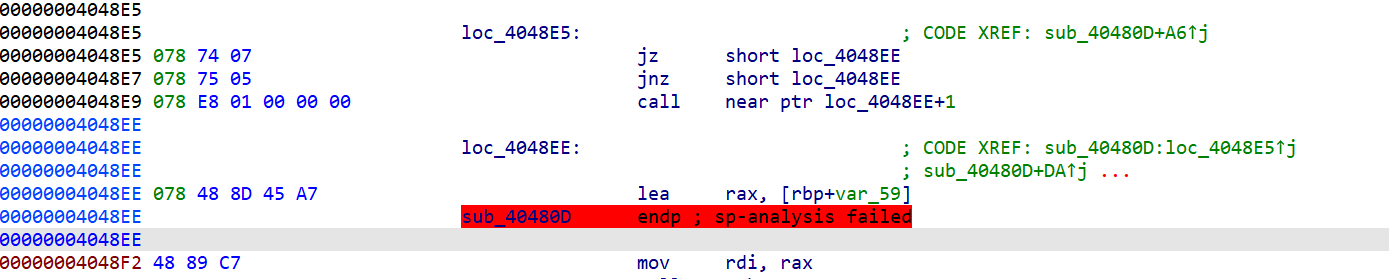
只有这一处jz/jnz强制跳转
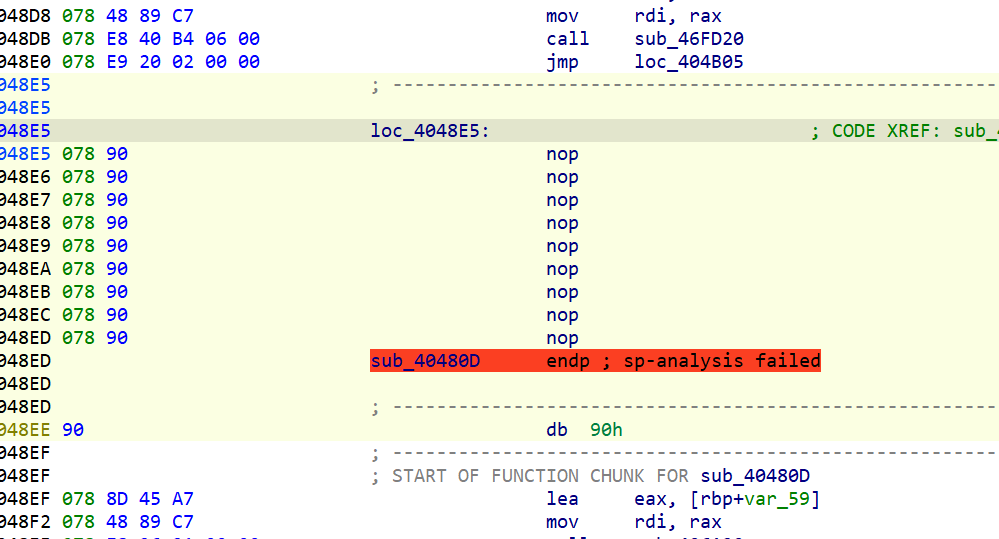
nop掉
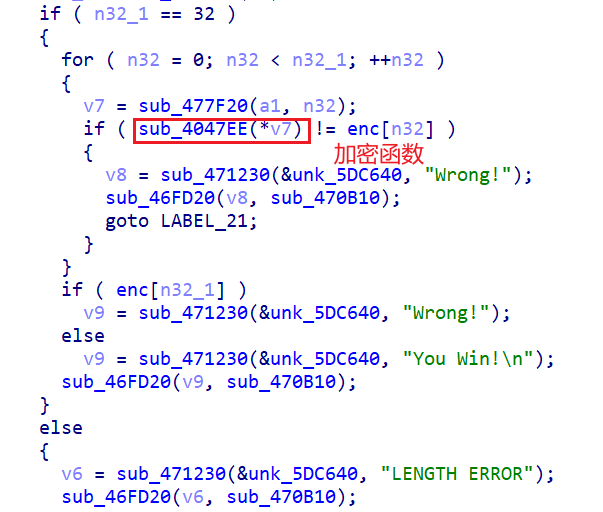
可以反汇编了
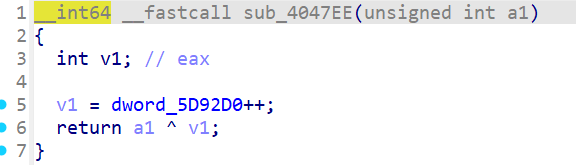
是异或,动调看怎么异或
有反调试
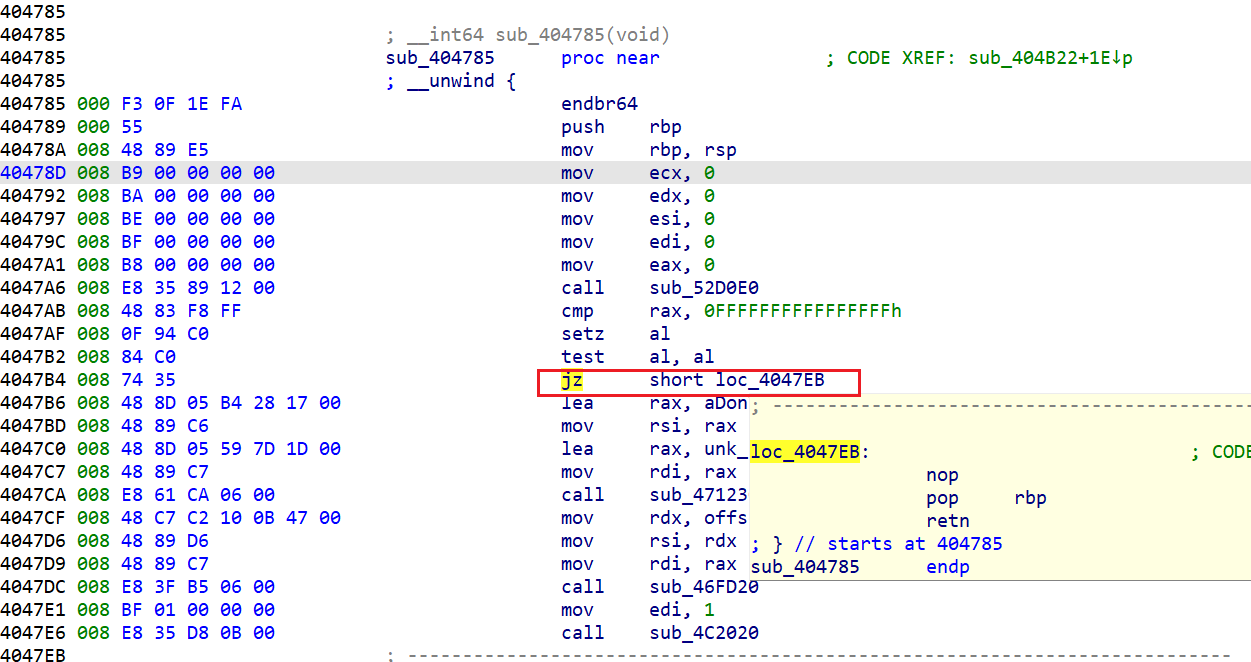
改为jnz
调试发现v1为0x29,每次异或后加1
#include <stdio.h>
#include <stdint.h>
int main()
{
int a[]={0x4F,0x1A,0x59,0x1F,0x5B,0x1D,0x5D,0x6F,0x7B,0x47,0x7E,0x44,0x6A,0x7,0x59,0x67,0xE,0x52,0x8,0x63,0x5C,0x1A,0x52,0x1F,0x20,0x7B,0x21,0x77,0x70,0x25,0x74,0x2B};
// int b[]={0x29,0x2a,0x2b,};
for(int i=0;i<32;i++){
printf("%c",a[i] ^ (0x29+i));
}
return 0;
}
//f0r3v3r_JuMp_1n_7h3_a$m_a9b35c3c
ezpy
凯撒加密
# Decompiled with PyLingual (https://pylingual.io)
# Internal filename: ezpy.py
# Bytecode version: 3.8.0rc1+ (3413)
# Source timestamp: 2025-06-24 08:38:00 UTC (1750754280)
def caesar_cipher_encrypt(text, shift):
result = []
for char in text:
if char.isalpha():
if char.islower():
new_char = chr((ord(char) - ord('a') - shift) % 26 + ord('a'))
elif char.isupper():
new_char = chr((ord(char) - ord('A') - shift) % 26 + ord('A'))
result.append(new_char)
else:
result.append(char)
return ''.join(result)
user_input = input('please input your flag:')
a = 1
if a == 1:#不等改为等于,实现解密
plaintext = user_input
shift = 114514
encrypted_text = caesar_cipher_encrypt(plaintext, shift)
print(encrypted_text)
# if encrypted_text == 'wyomdp{I0e_Ux0G_zim}':
# print('Correct!!!!')
catch
try catch就是一种win的异常处理
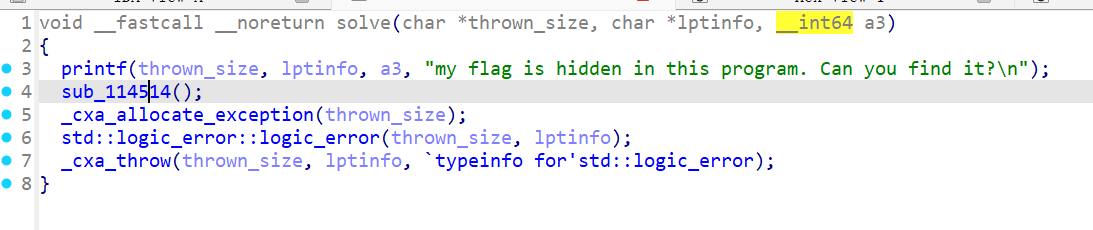
solve函数看到CTF常数
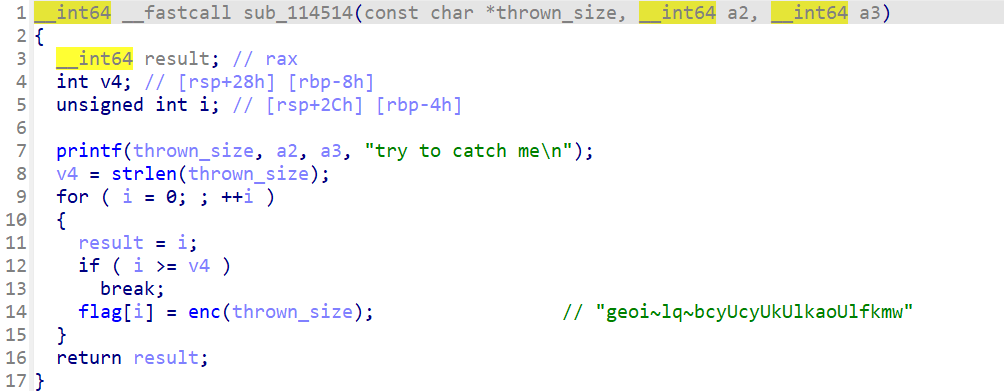
enc函数是异或,但是解不出来,是假的
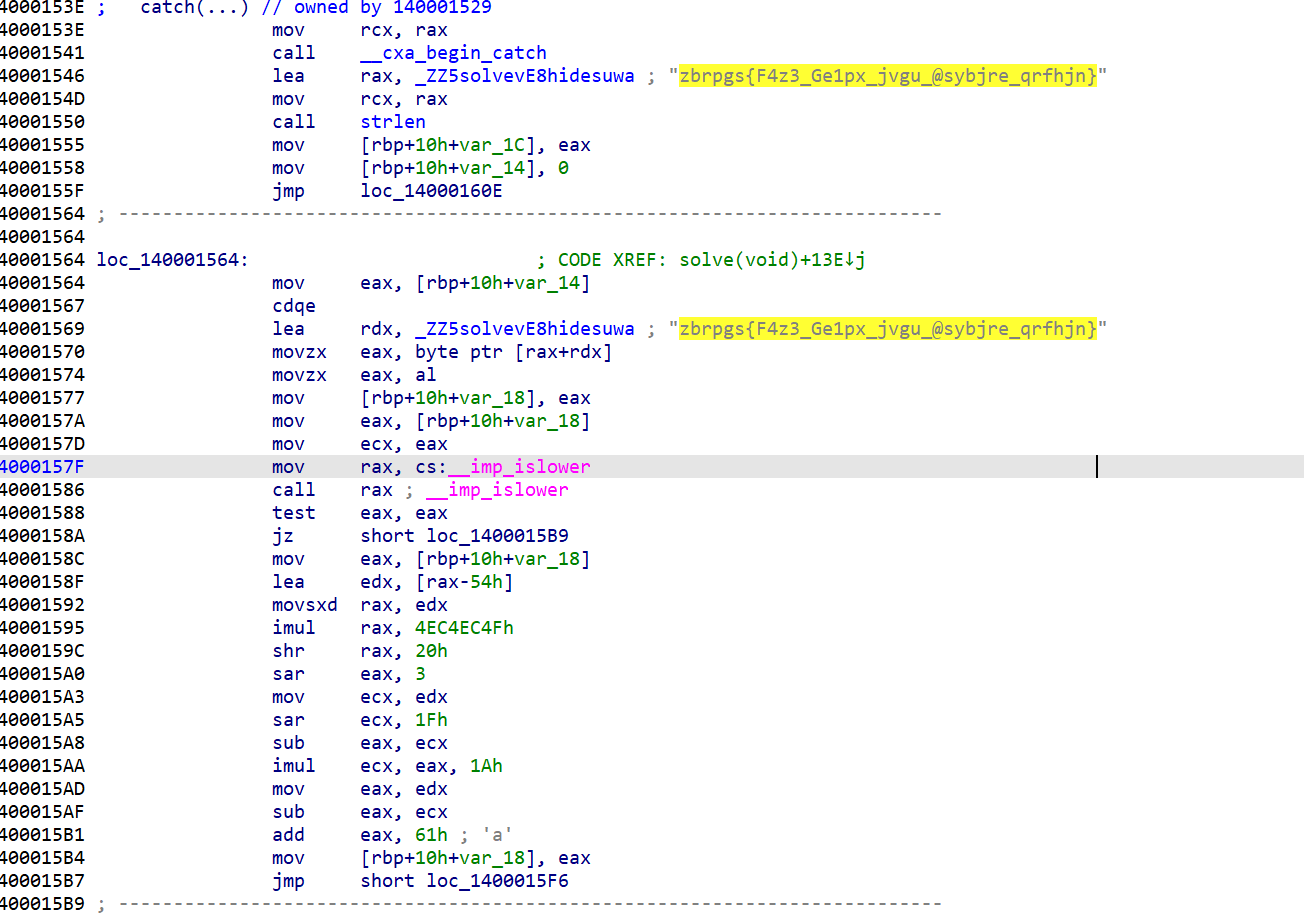
返回去看汇编,有另一串字符串和对应的处理,应该就是try catch导致报异常没有被反汇编
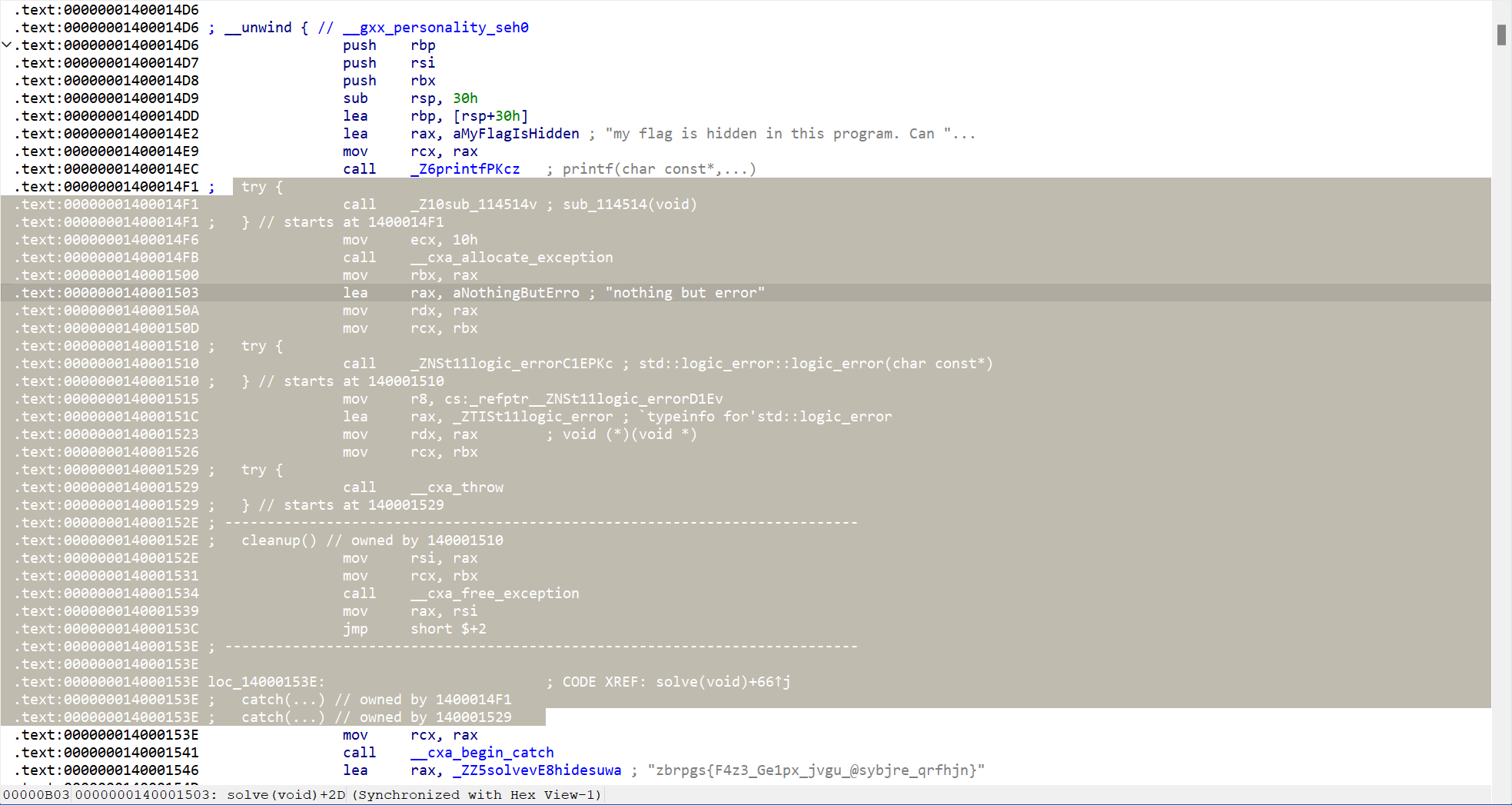
直接将try catch全部nop掉
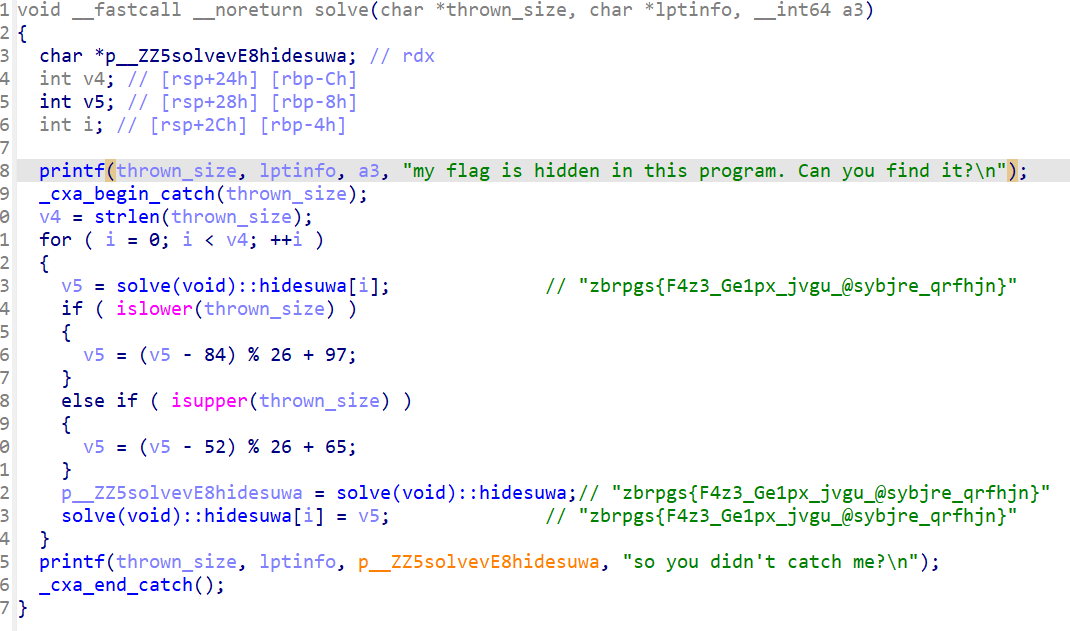
solve函数变了,直接解密
#include <stdint.h>
#include <stdio.h>
#include <string.h>
#include <stdlib.h>
int main(){
char v5[]="zbrpgs{F4z3_Ge1px_jvgu_@sybjre_qrfhjn}";
for(int i=0;i<strlen(v5);i++)
{
if ( 'a'<=v5[i]&&v5[i]<='z' )
{
v5[i] = (v5[i] - 84) % 26 + 97;
}
else if ( 'A'<=v5[i]&&v5[i]<='Z' )
{
v5[i] = (v5[i] - 52) % 26 + 65;
}
}
printf("%s",v5);
}//moectf{S4m3_Tr1ck_with_@flower_desuwa}
rusty_sudoku
虽然是rust写的,但是不存在干扰,直接看字符串
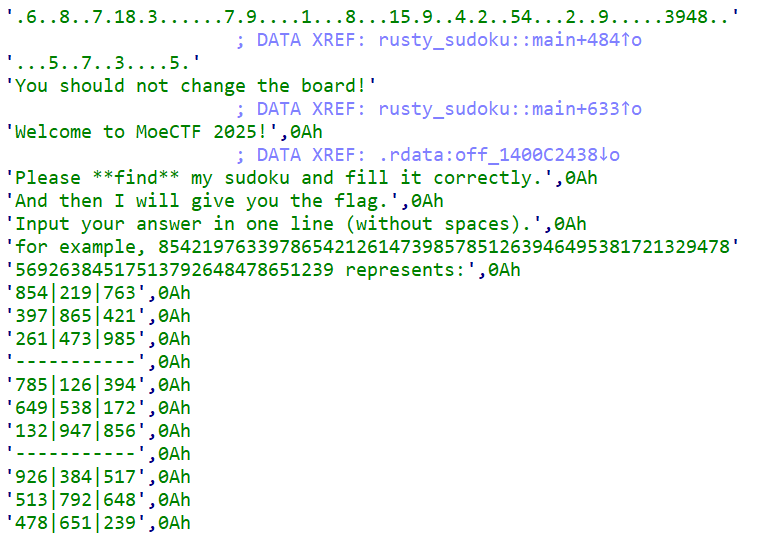
直接看到数独题目,导入在线网站就能解了
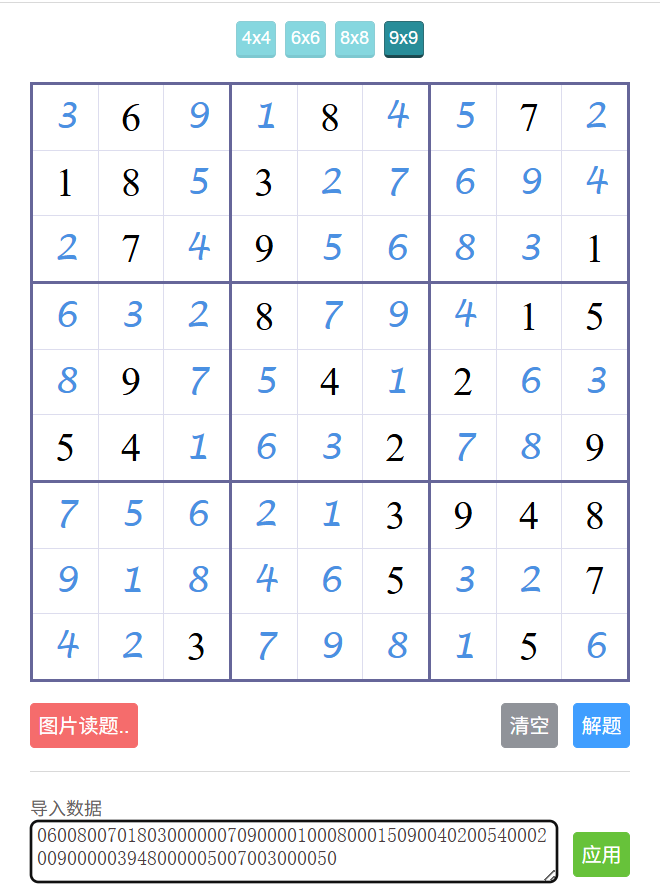
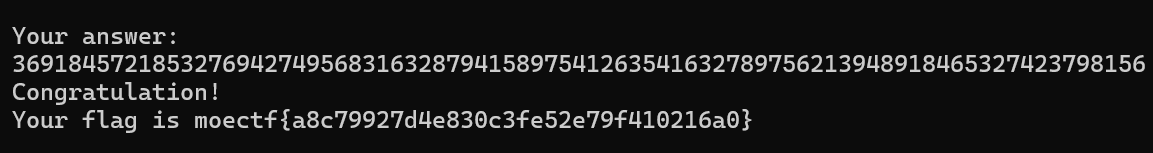
have_fun
MFC?但是xspy分析出来不是MFC窗口,不太理解,那就硬看,无法搜索到字符串
WinMain函数没有对输入的处理,大概是在布置界面
观察函数名字看到DialogFunc函数,上面很陌生,但是下面的内容一见如故
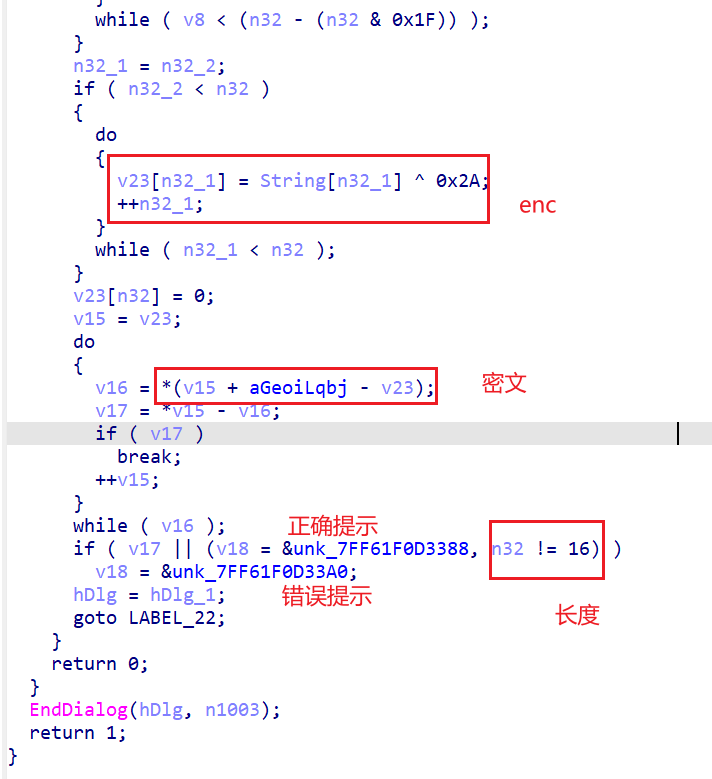
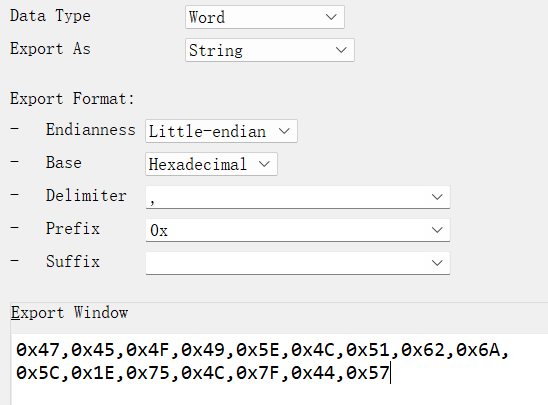
提取word格式的密文
#include <stdint.h>
#include <stdio.h>
#include <string.h>
#include <stdlib.h>
int main(){
char v5[]={0x47,0x45,0x4F,0x49,0x5E,0x4C,0x51,0x62,0x6A,0x5C,0x1E,0x75,0x4C,0x7F,0x44,0x57};
for(int i=0;i<16;i++)
{
printf("%c",v5[i]^0x2a);
}
}//moectf{H@v4_fUn}
ez3
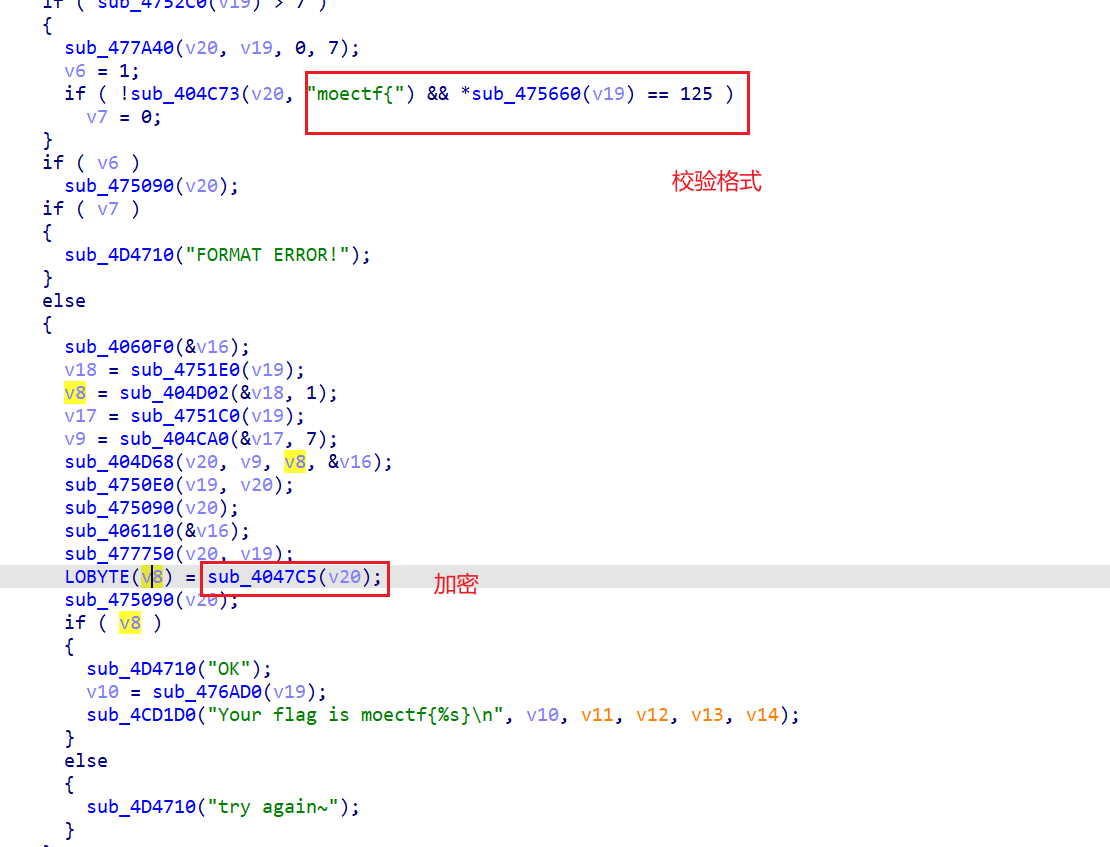
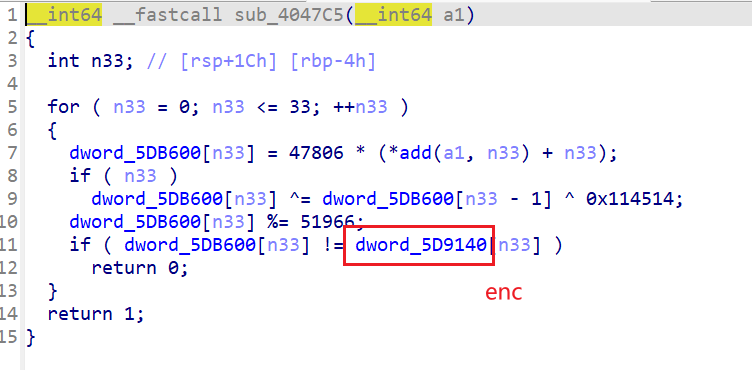
现在可以直接用z3求解,
from z3 import *
check = [0xB1B0,0x5678,0x7FF2,0xA332,0xA0E8,0x364C,0x2BD4,0xC8FE,0x4A7C,0x18,0x2BE4,0x4144,0x3BA6,0xBE8C,0x8F7E,0x35F8,0x61AA,0x2B4A,0x6828,0xB39E,0xB542,0x33EC,0xC7D8,0x448C,0x9310,0x8808,0xADD4,0x3CC2,0x796,0xC940,0x4E32,0x4E2E,0x924A,0x5B5C,0x405740]
s = Solver() # 创建了一个 Solver 对象 s
a = [BitVec('a%d'%i,32) for i in range(34)] # 变量
for i in range(34):
enc = 0xbabe * (a[i]+i)
if i>0:
enc ^= check[i-1] ^ 0x114514#dword_5DB600[i - 1] == check[i] ,已经经过验证了
enc %= 51966
s.add(enc == check[i])
for i in range(34):
s.add(32<=a[i],a[i]<=126)
solutions=0
max_soltions = 10
while s.check() == sat and solutions < max_soltions:
m=s.model()
result = [m[a[i]].as_long() % 0xff for i in range(34)]
print(''.join([chr(x) for x in result]))
not_current = [a[i] != m[a[i]] for i in range(34)]#约束列表
s.add(Or(not_current))#Or() 是 Z3 提供的逻辑或操作,它将列表中的 34 个约束条件组合起来,这个组合约束的意思是:至少有一个变量的值要和当前解不同
solutions += 1
存在多解,但是z3默认只打印一个解,循环打印,共四个解,一个个尝试
upx_revenge
魔改的,但是没想是把UPX!给删了
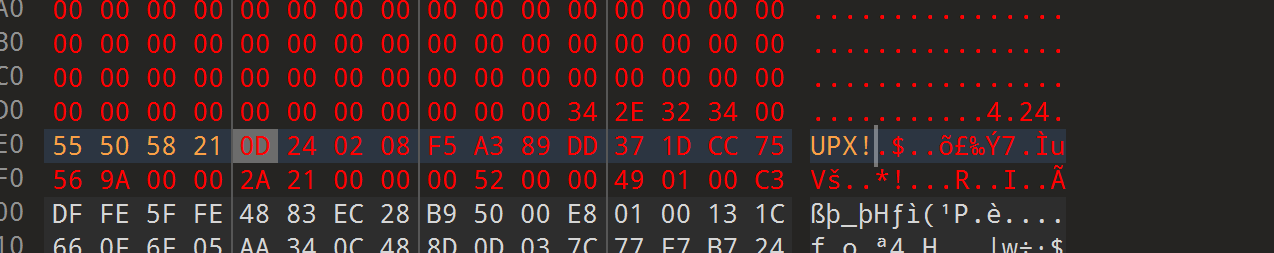
补上之后就能正常脱壳了
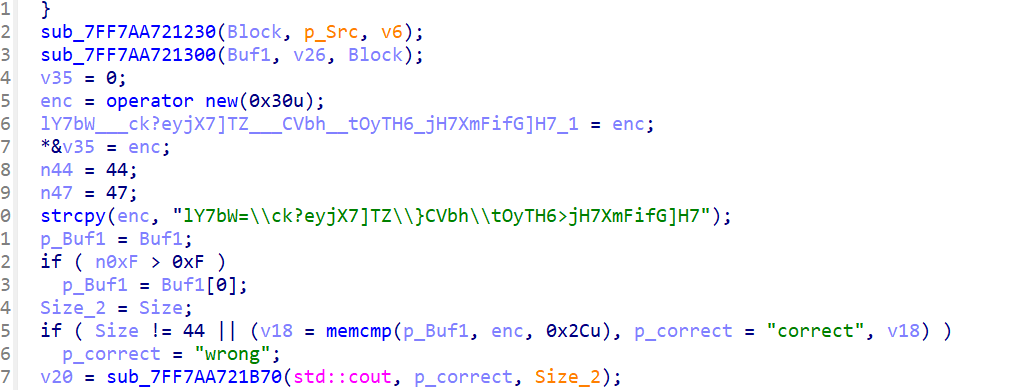
main函数里面看到密文
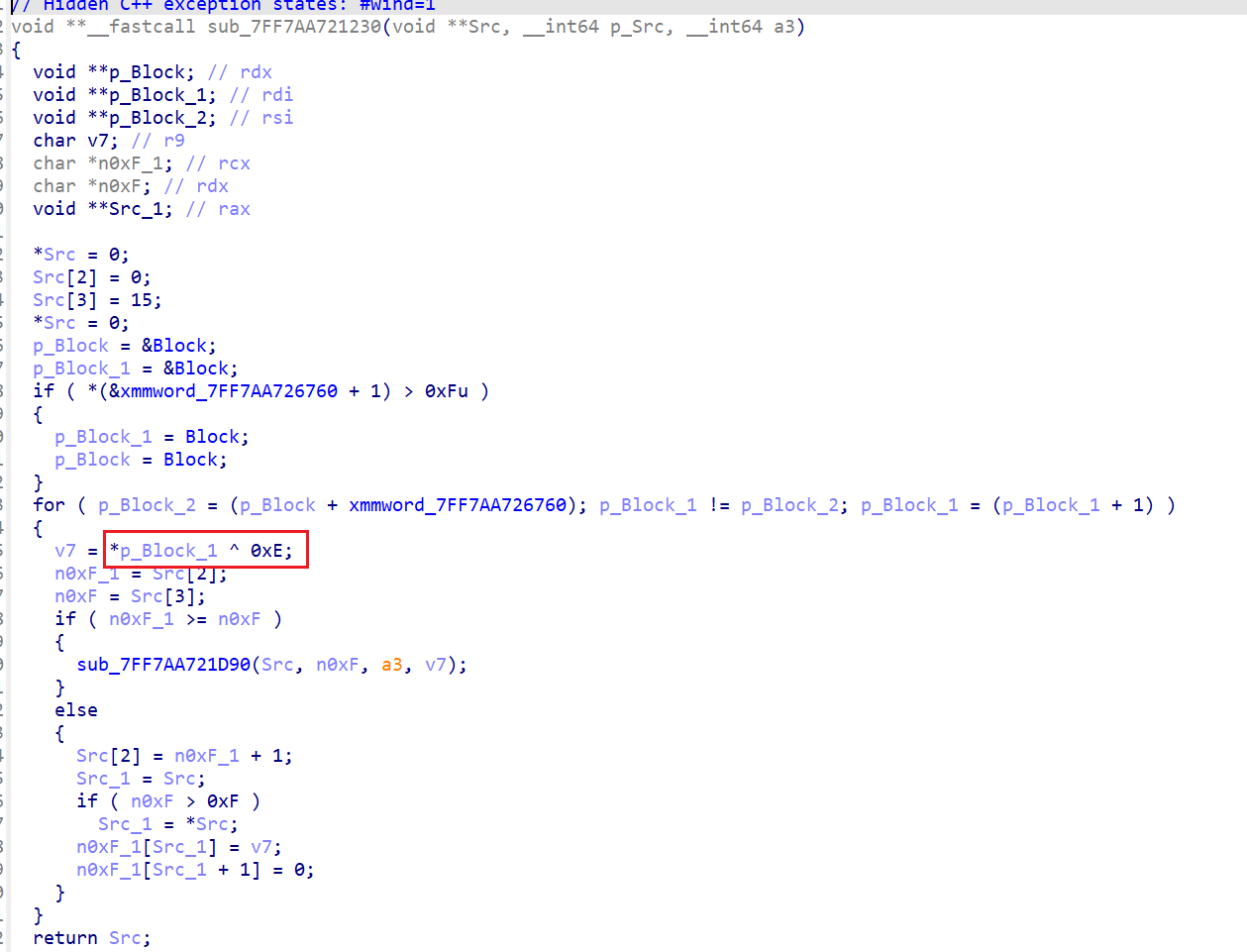
sub_7FF7AA721230是异或0xe
sub_7FF7AA721300看着像是base64,但是没有看到编码表
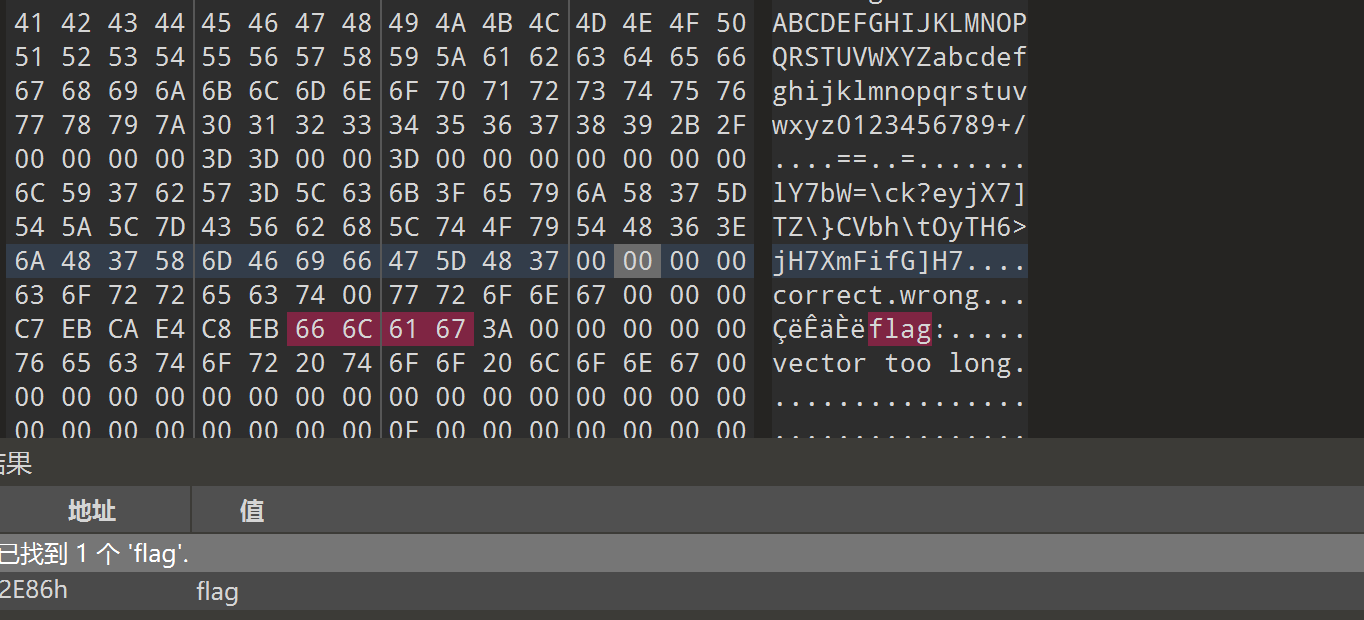
010搜索flag的时候看到是标准的编码表
因为是猜的,所以验证一下
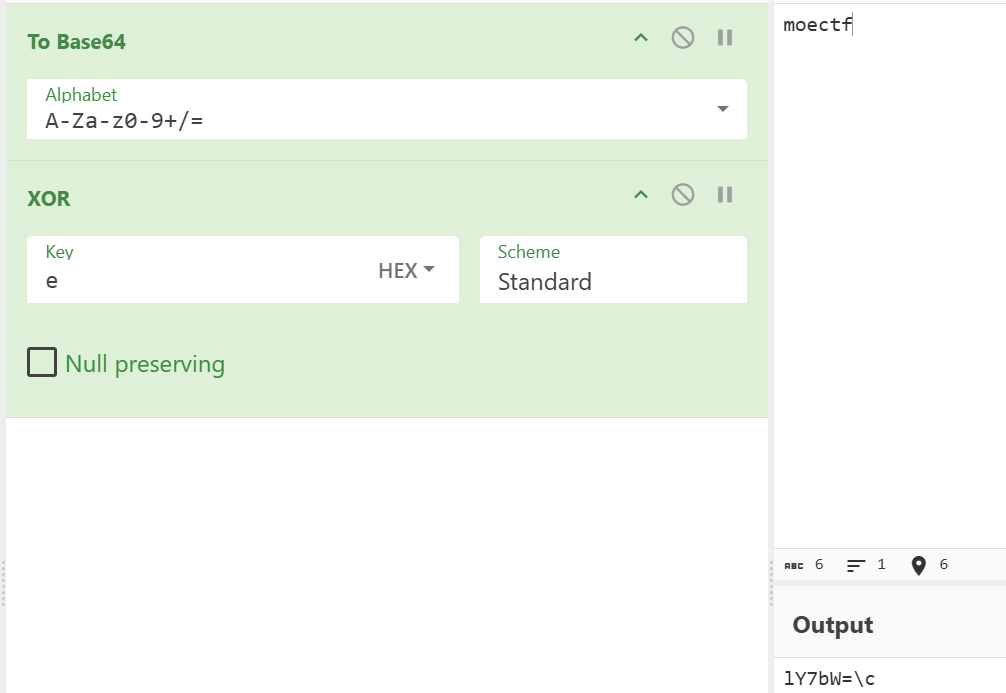
猜测正确
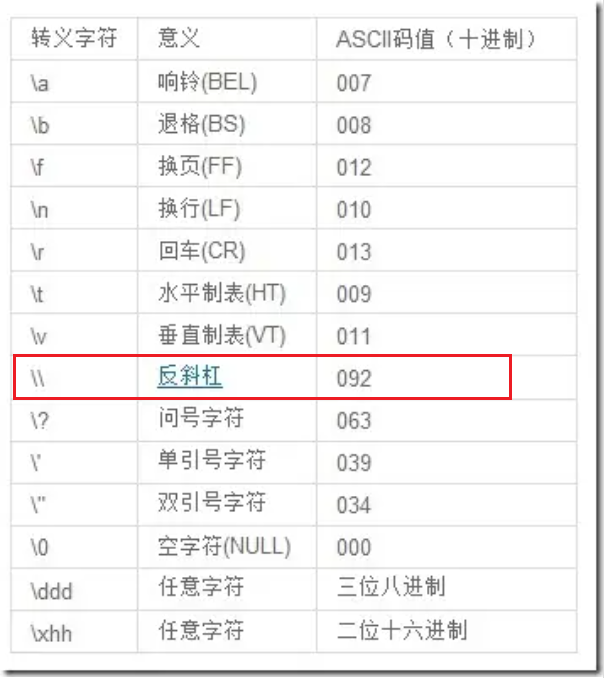
ida里面的\\其实是转义字符,表示的是\
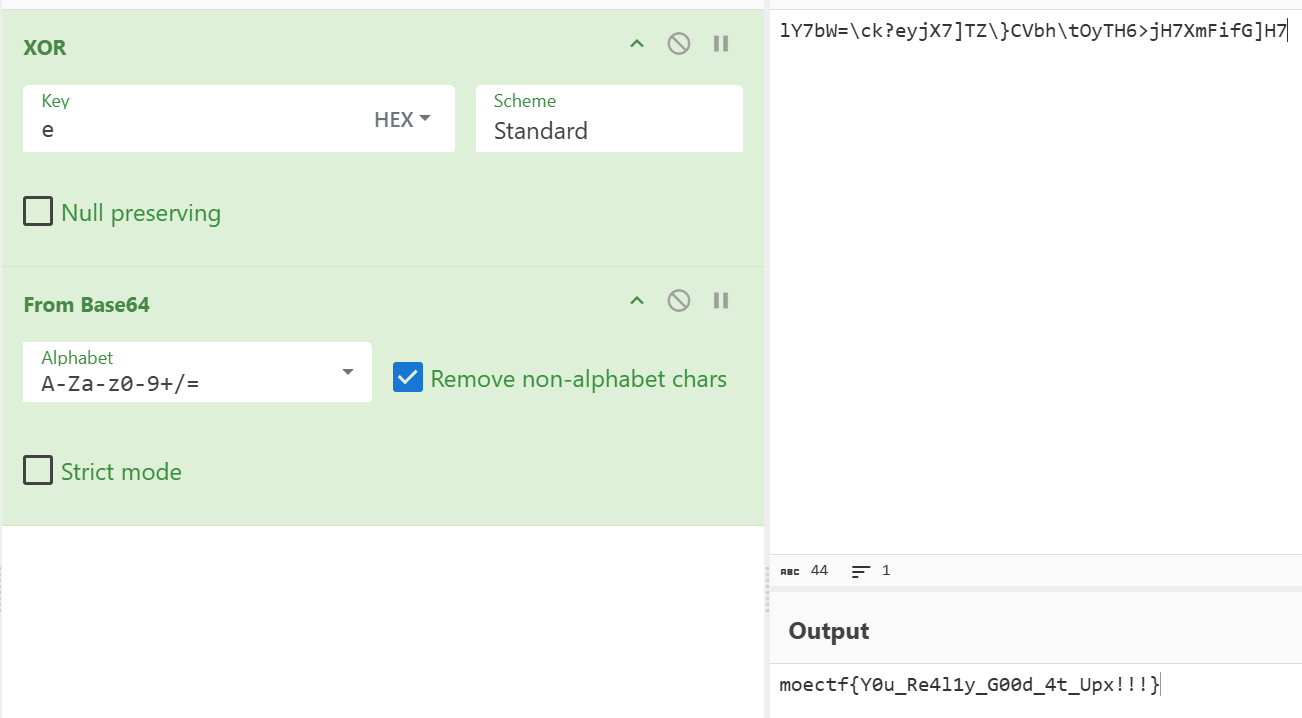
guess
因为说的是如果猜对的话就会输出flag,那么程序可以直接计算flag
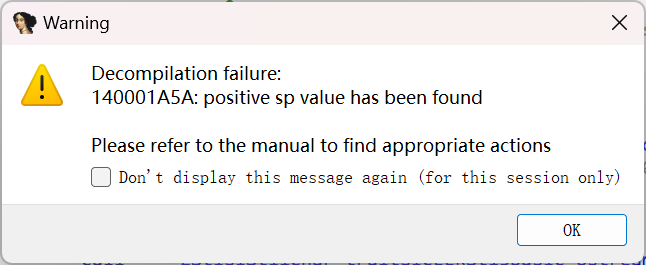
对main函数f5有报错,看0x140001A5A
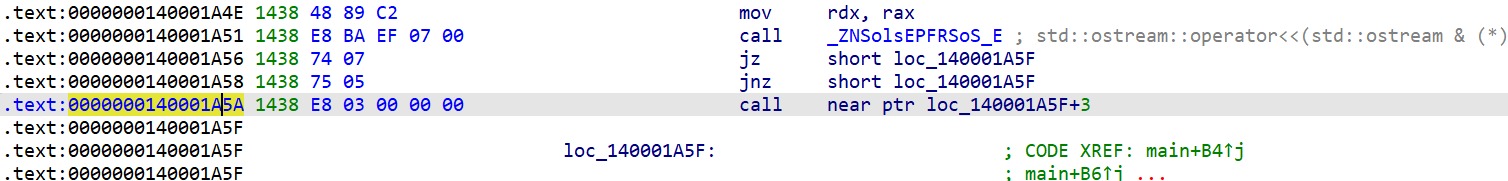
永恒跳转花指令
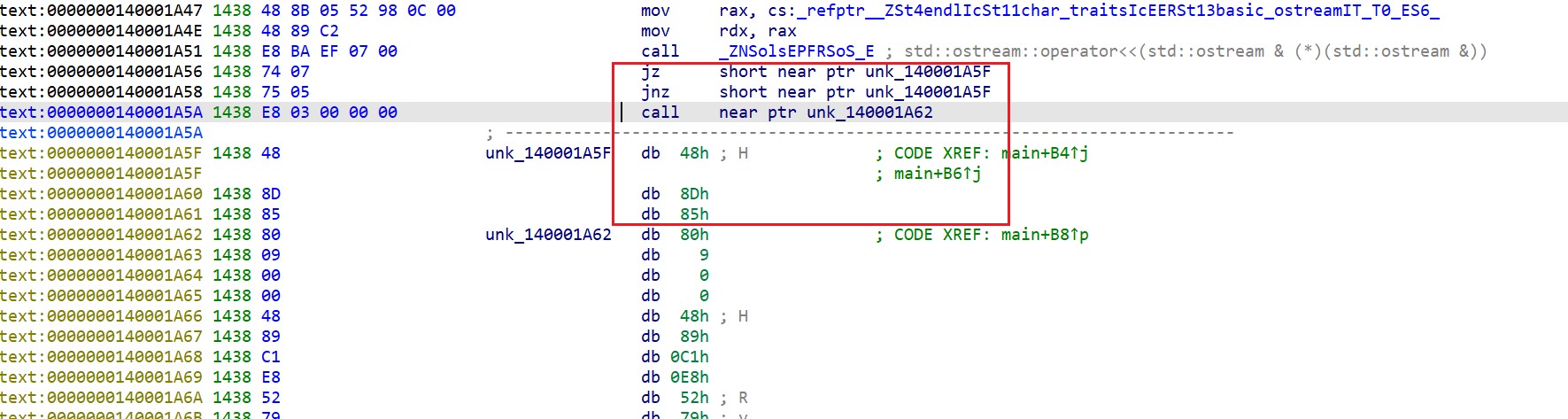
nop后f5正常
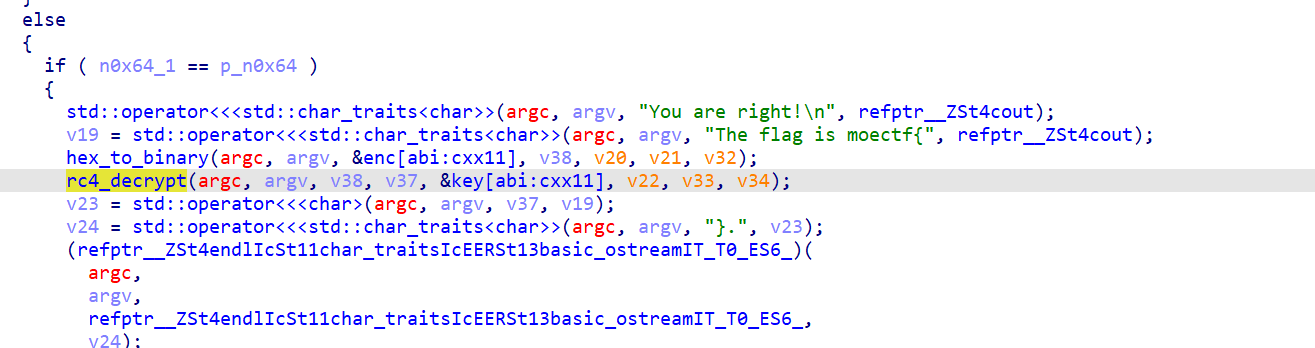
当输入正确会调用rc4_decrypt函数,那么就可以改跳转,在输入的时候断点动调
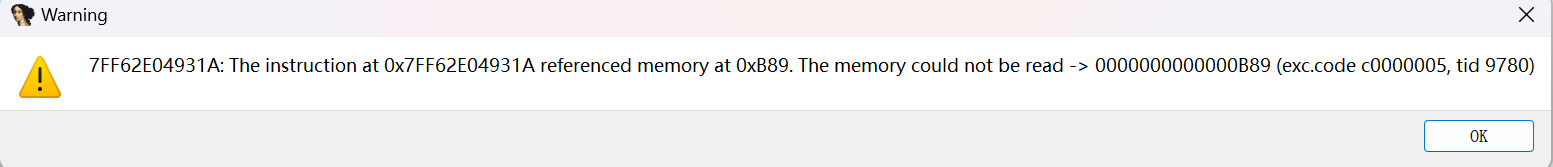
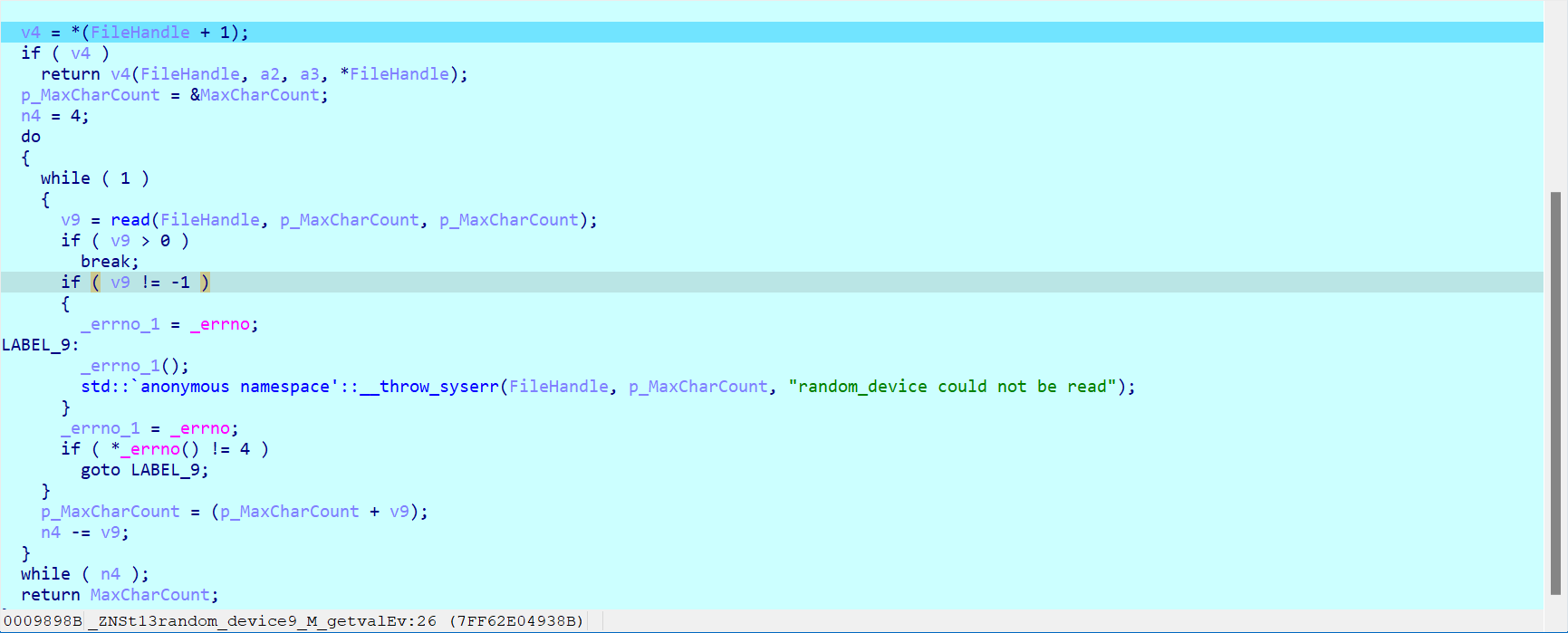
报错,应该是反调试,是random_device函数
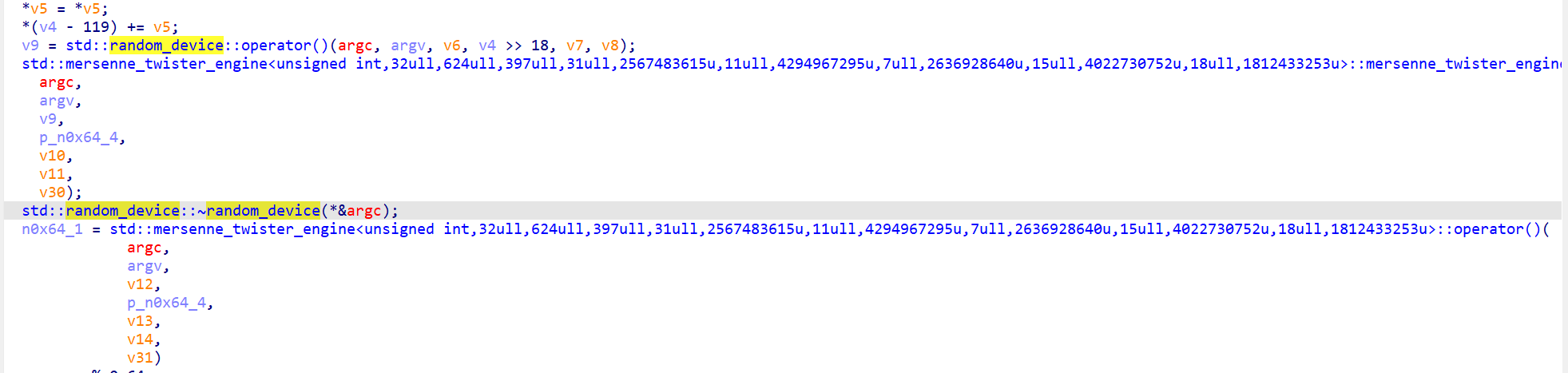
该函数出现位置集中在这里
在前面断点
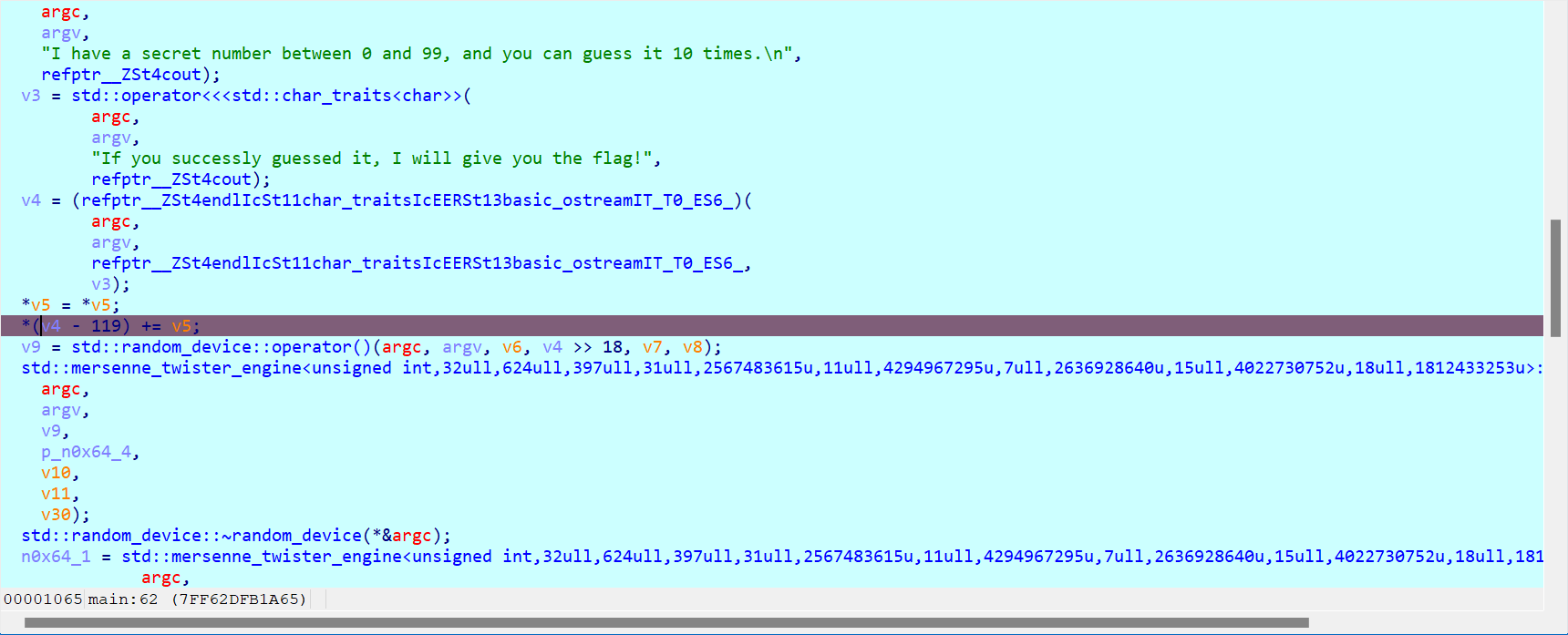
这样就可以了,如果直接f8运行的话依旧会进入random_device,我们找到输入提示处
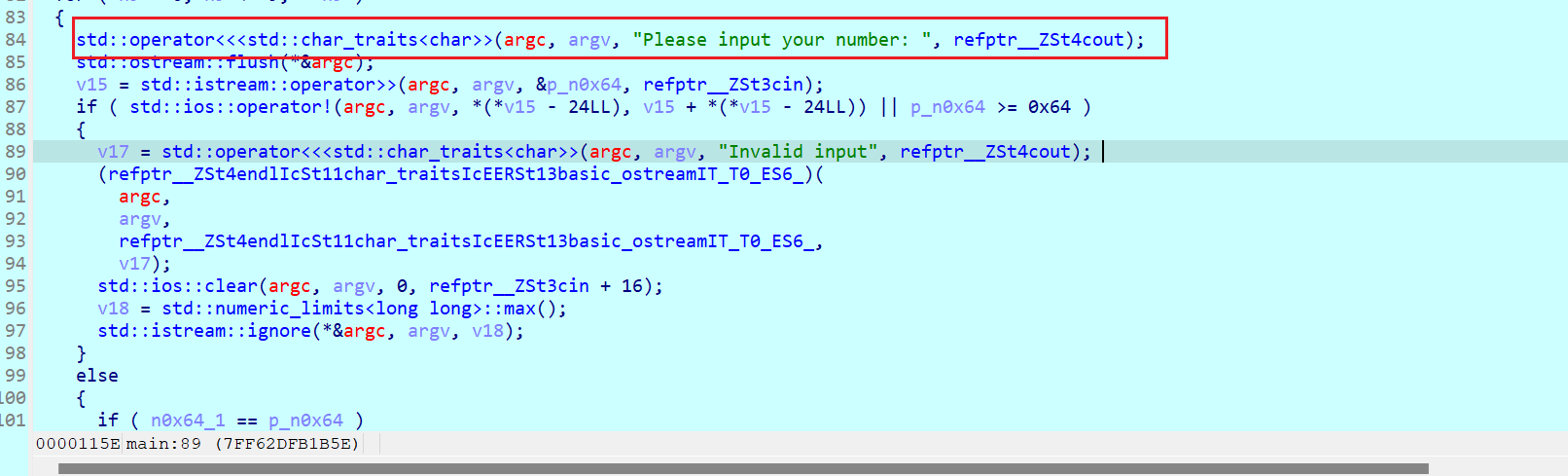
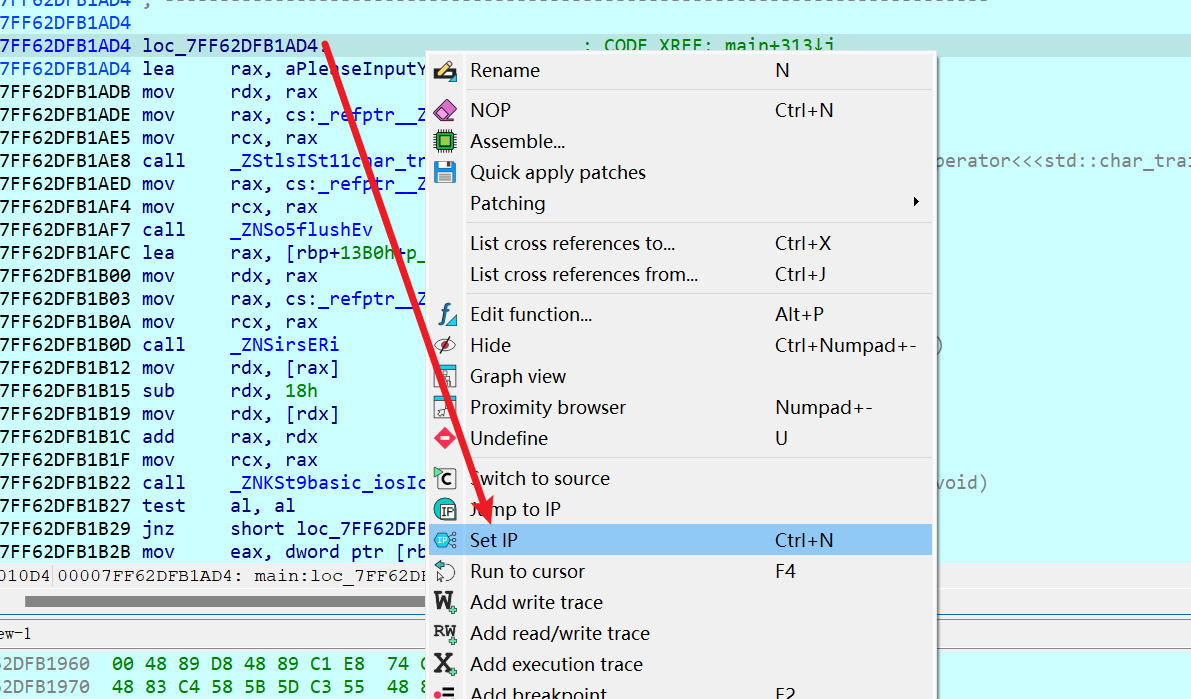
右键set ip(一般是在一个块的开头设置)就会跳过前面部分直接到这
当输入了一个数之后
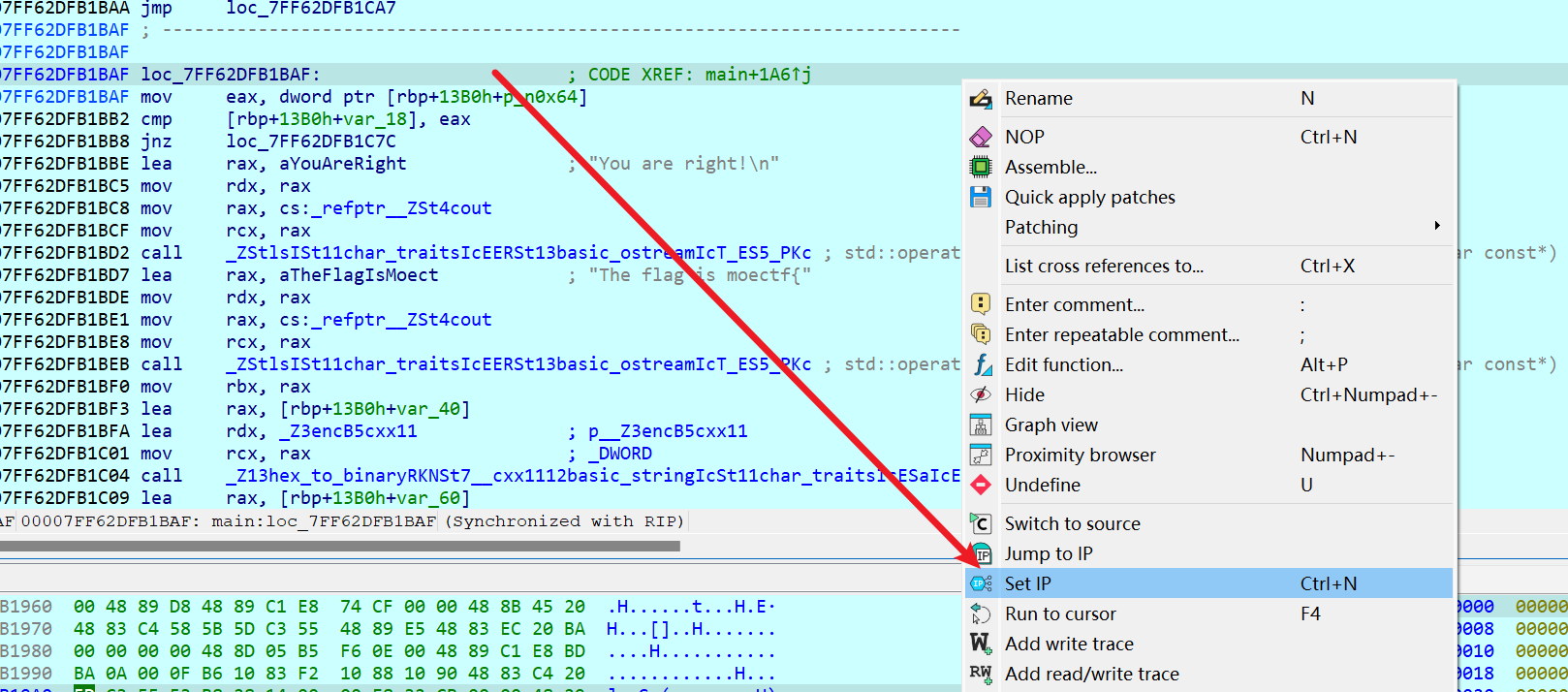
在提示正确的位置set ip
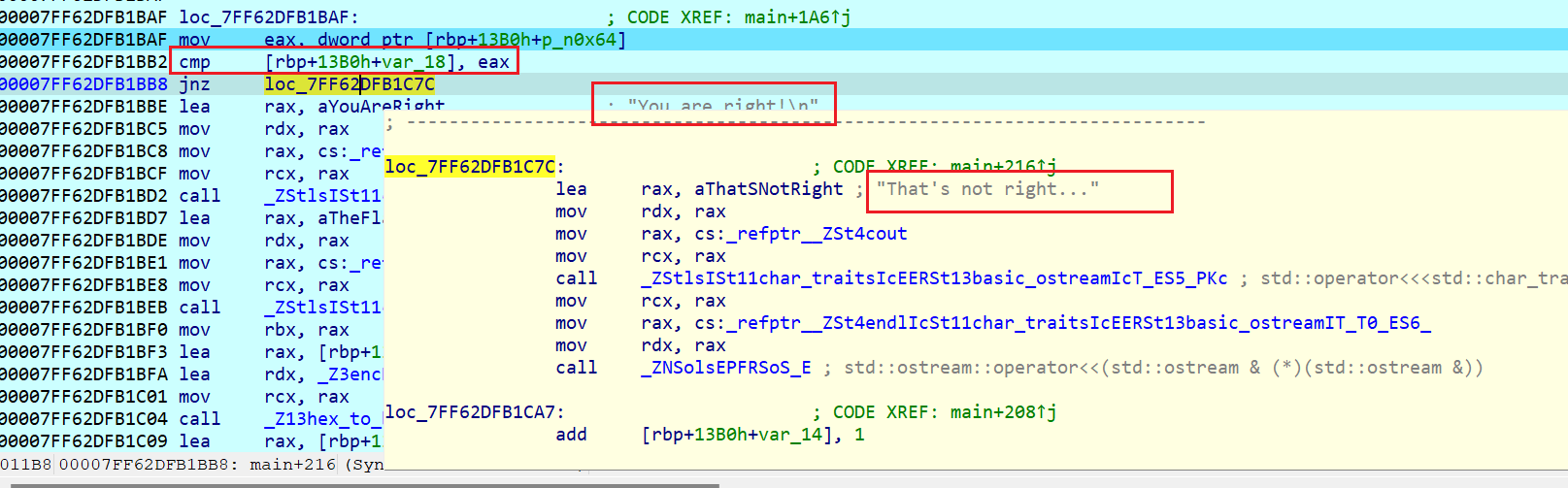
看到这里有一个cmp,jnz到错误提示,所以改为jz
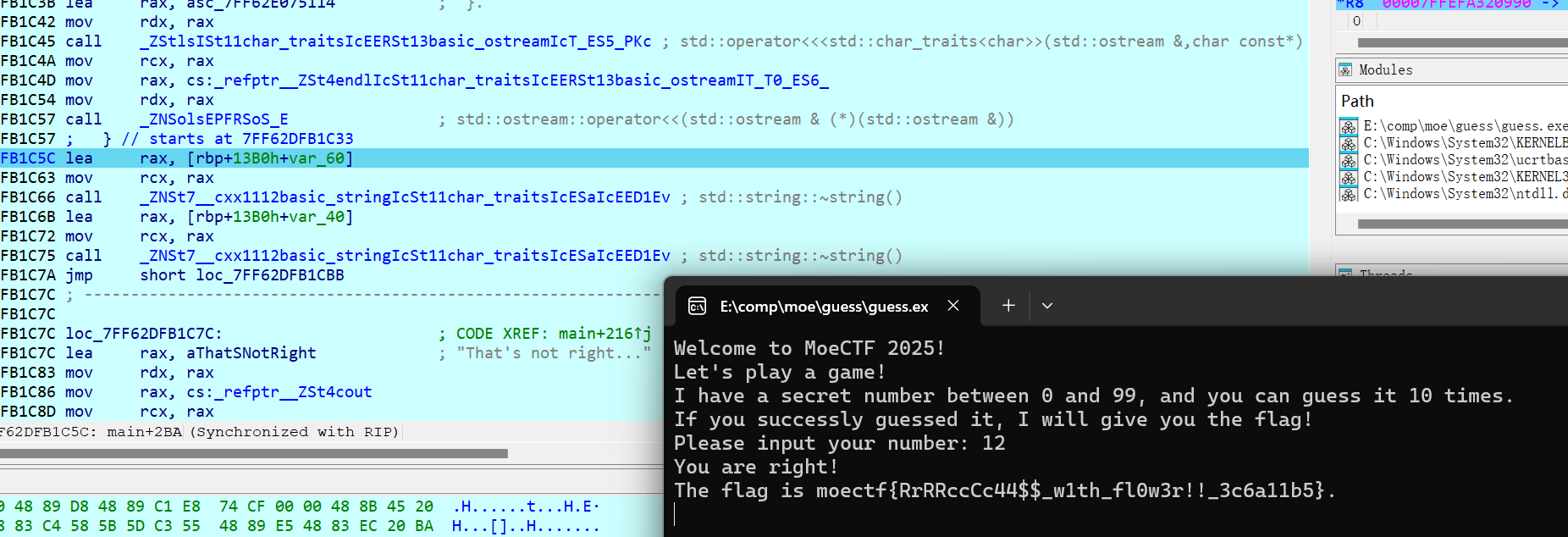
A simple program
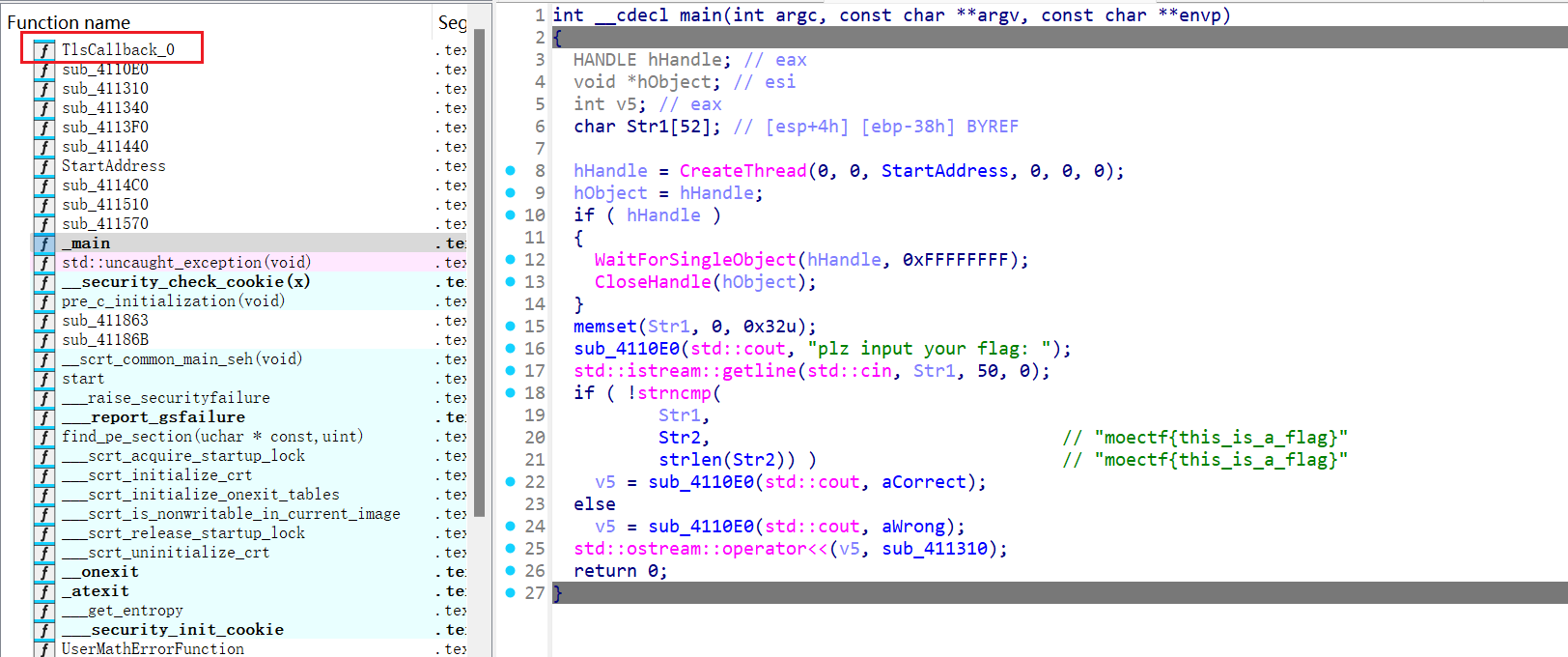
main函数里面看到有明文flag,但是是假的,看函数名有回调函数,看看
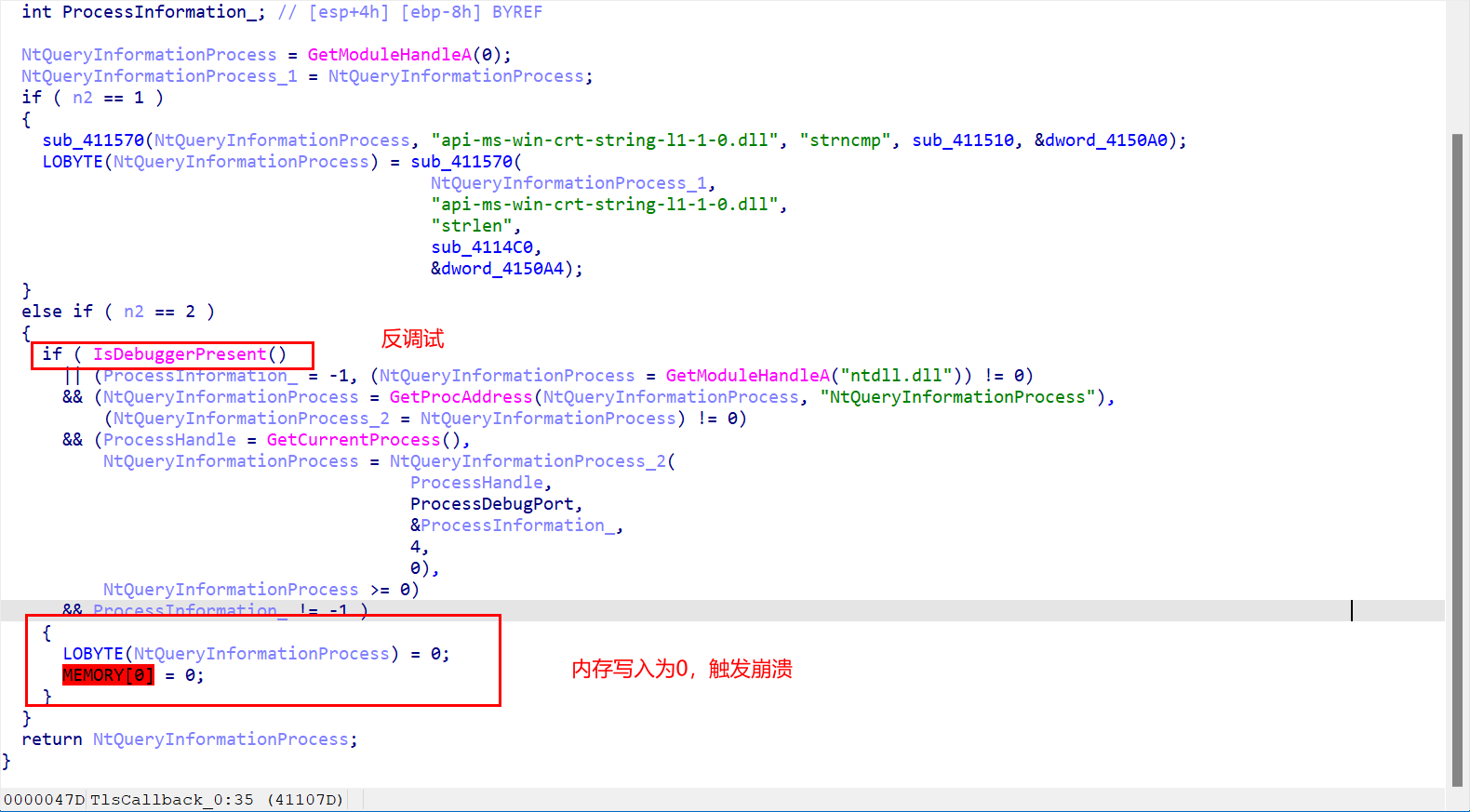
对strlen和strncmp函数进行了替换
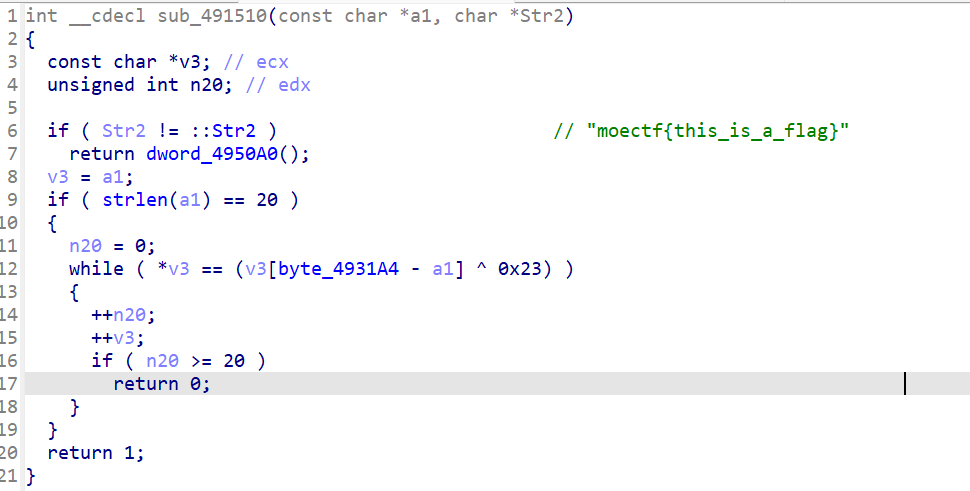
异或加密
#include<stdio.h>
#include<string.h>
#include "windows.h"
int main()
{
int a[]={0x4E,0x4C,0x46,0x40,0x57,0x45,0x58,0x7A,0x13,0x56,0x7C,0x73,0x17,0x50,0x50,0x66,0x47,0x2,0x2,0x5E,0x0,0x0,0x0,0x0};
for(int i=0;i<20;i++){
printf("%c",a[i]^=0x23);
}
}
但是我感觉前面那个函数替换还能再看看
ezandroid
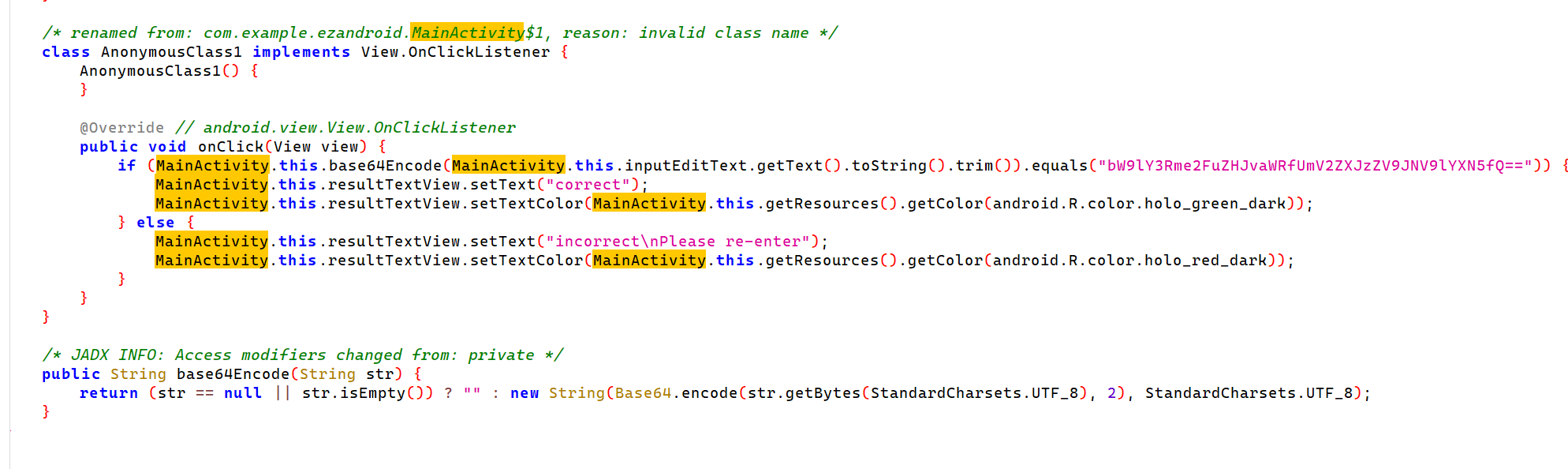
java层base64
ezandroid.pro
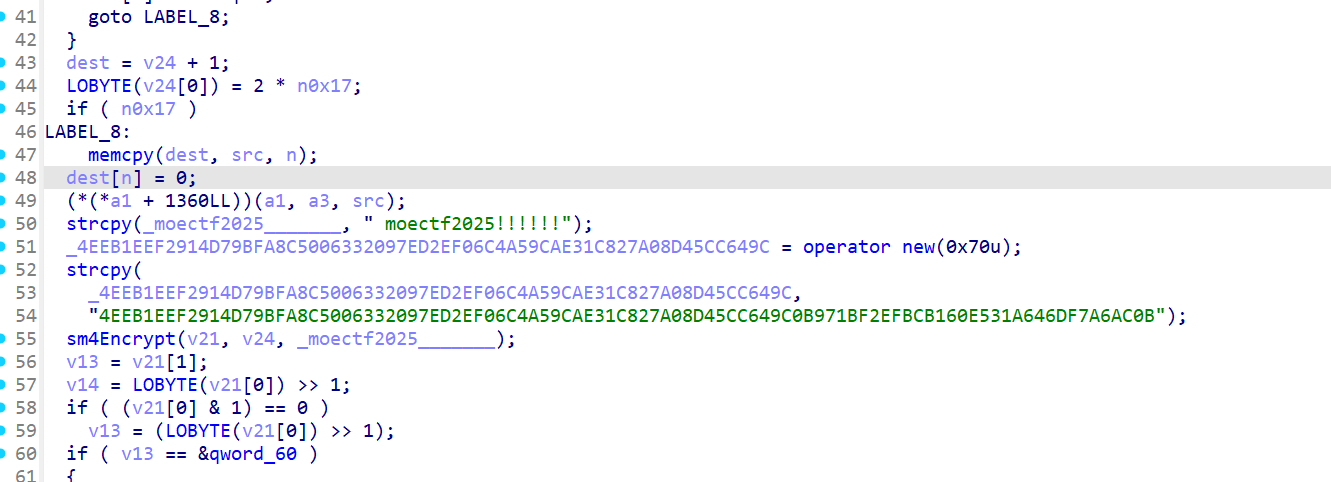
so层check函数sm4 ecb加密
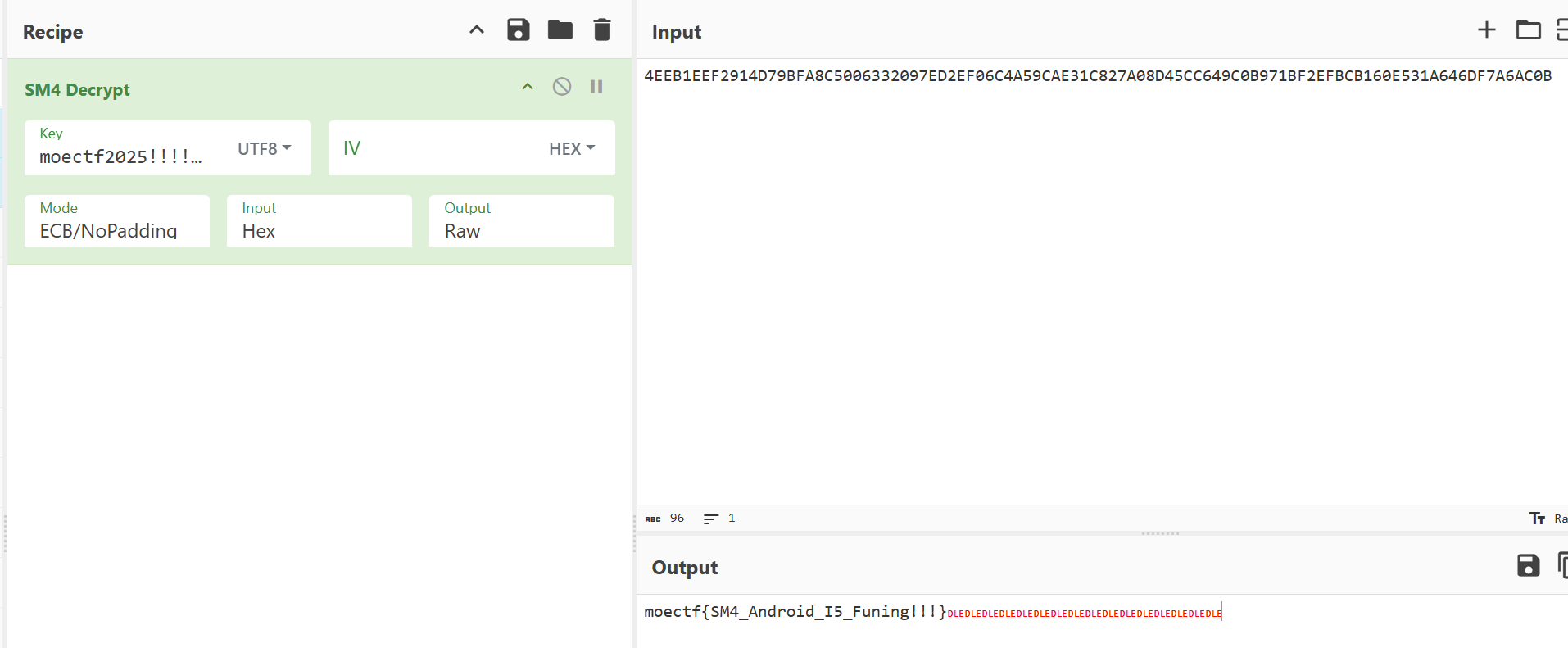
2048_master_re
tips没有用吧,修改数据没有爆flag
那就再ida里面看
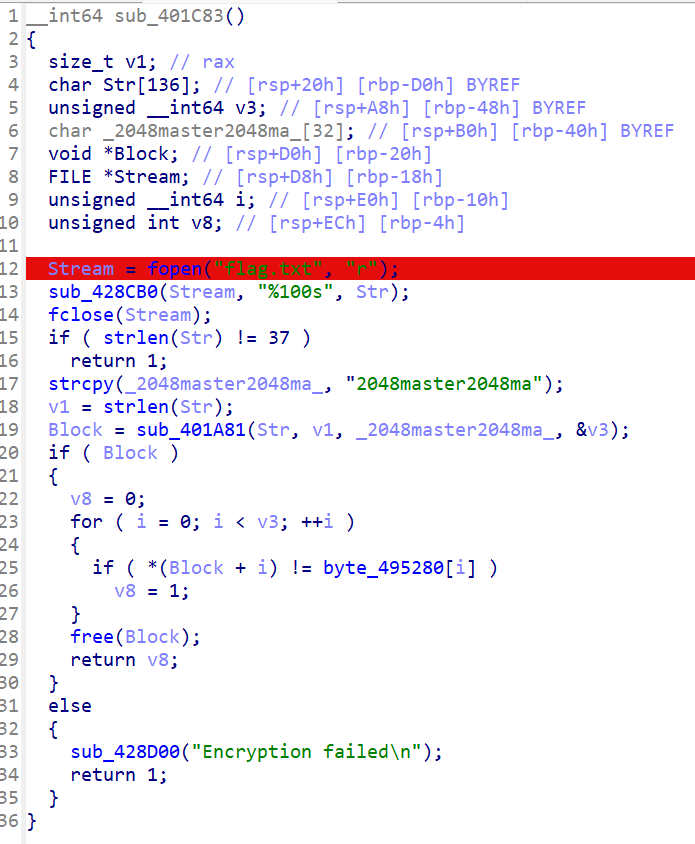
查看strings看到flag.txt,运行时会生成layout.dat文件,但是没有flag.txt,所以创建一个flag.txt,因为会读取37个字符,所以我写入37个a,很明显的cmp
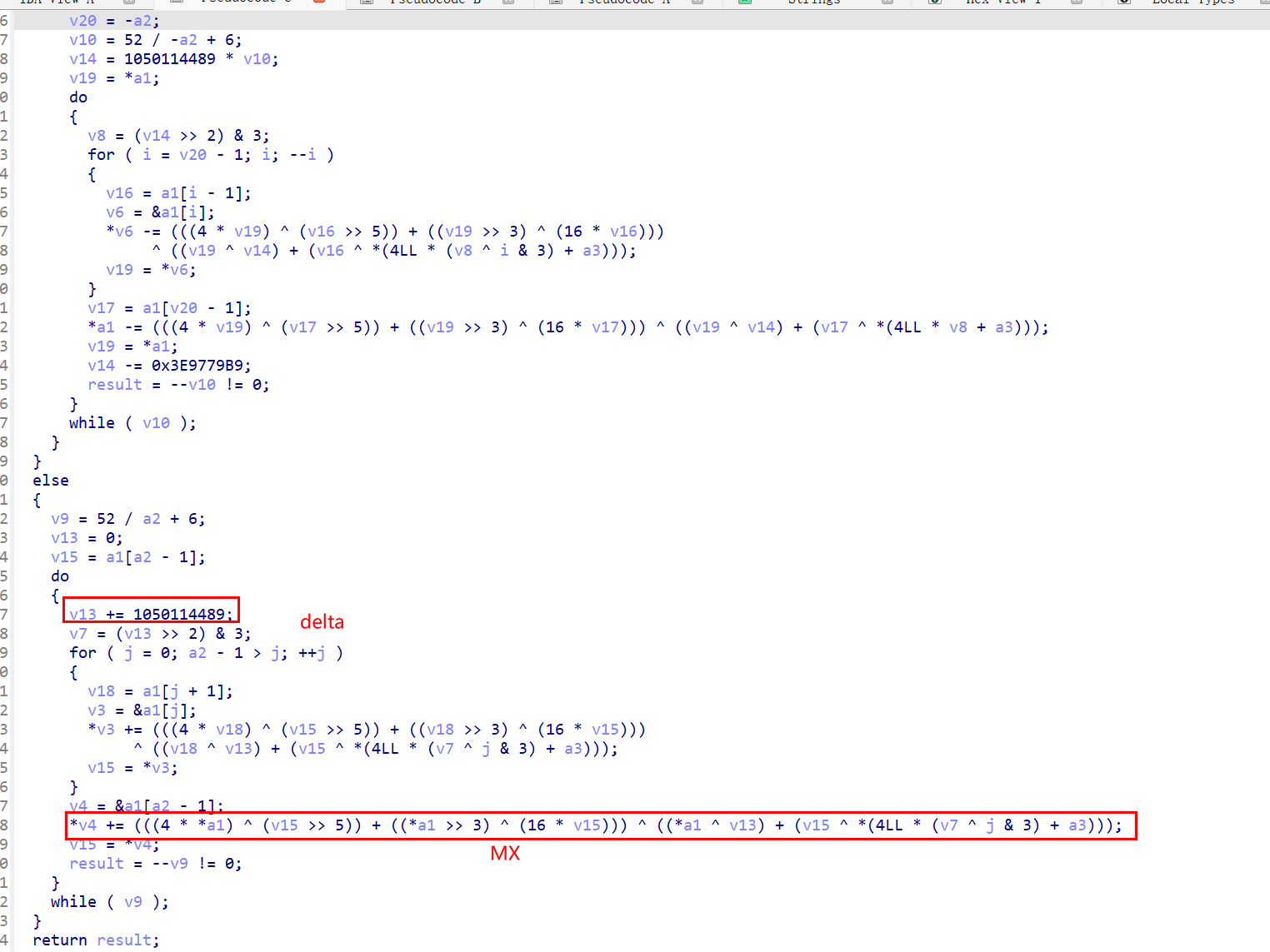
sub_401A81里面的sub_401530函数很明显的xxtea
#include <stdint.h>
#include <stdio.h>
#define DELTA 0x3E9779B9
#define MX (((z>>5^y<<2) + (y>>3^z<<4)) ^ ((sum^y) + (key[(p&3)^e] ^ z)))
void btea(uint32_t* v, int n, uint32_t const key[4])
{
uint32_t y, z, sum;
unsigned p, rounds, e;
if (n > 1) //加密算法
{
rounds = 6 + 52 / n;
sum = 0;
z = v[n - 1];
do
{
sum += DELTA;
e = (sum >> 2) & 3;
for (p = 0; p < n - 1; p++)
{
y = v[p + 1];
z = v[p] += MX;
}
y = v[0];
z = v[n - 1] += MX;
} while (--rounds);
}
else if (n < -1) //解密算法
{
n = -n;
rounds = 6 + 52 / n;
sum = rounds * DELTA;
y = v[0];
do
{
e = (sum >> 2) & 3;
for (p = n - 1; p > 0; p--)
{
z = v[p - 1];
y = v[p] -= MX;
}
z = v[n - 1];
y = v[0] -= MX;
sum -= DELTA;
} while (--rounds);
}
}
// 可用的解密main函数实例
int main()
{
uint32_t v[10] = { 0xCC777935,0x3441131B,0x919FFFF9,0x78945BFF,0xAEAF2A86,0x4D319ED7,0x51A5C47A,0x446ED9D1,0x1B865218,0x63C98A42};
char const k[] = "2048master2048ma";
int n = 10;
btea(v, -n, k);
for (int i = 0; i < n; i++)
{
for (int j = 0; j < sizeof(uint32_t) / sizeof(uint8_t); j++)
{
printf("%c", (v[i] >> (j * 8)) & 0xFF);
}
}
return 0;
}
k的另一种赋值 uint32_t const k[4] = {0x38343032,0x7473616d,0x30327265,0x616d3834};
Two cups of tea
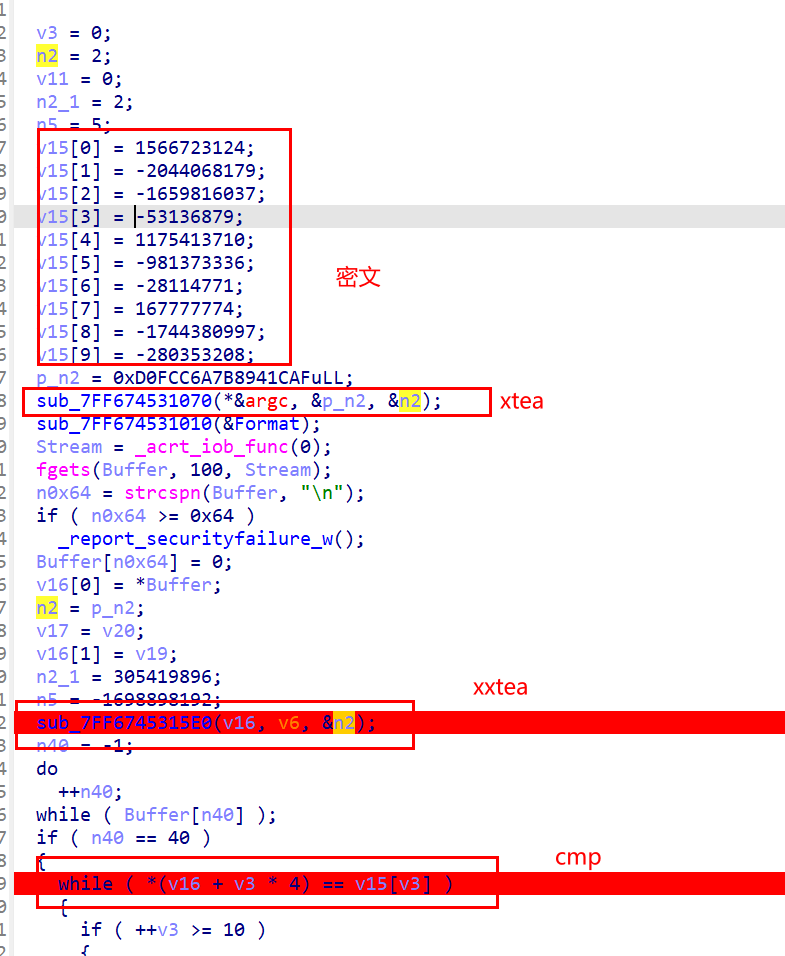
前面的xtea利用p_n2来生成新的key
其中xtea的key为2,0,2,5,delta为0x61C88647,32轮(但是脚本不知道哪里出问题了)
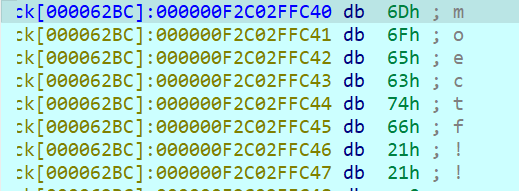
经过xtea加密后p_n2变为moectf!!
所以xxtea的key为0x63656F6D,0x21216674,0x12345678,0x9ABCDEF0
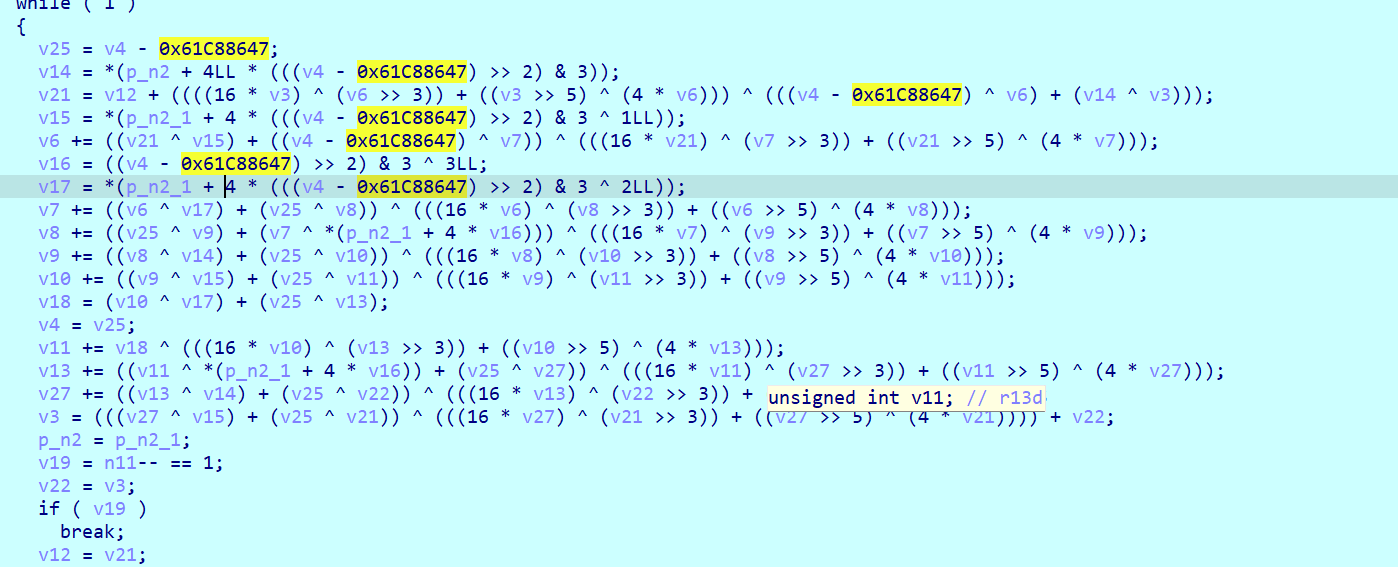
这里看到xxtea的delta运算为- 0x61C88647,但这是加密,应该+,所以这里应该用其补码
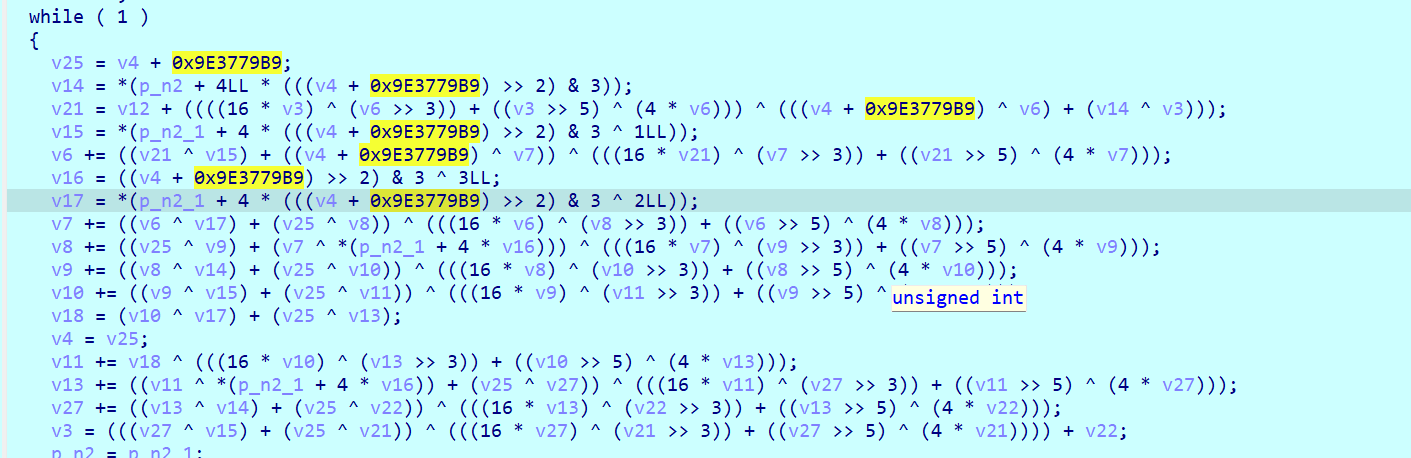
所以delta为0x9E3779B9
#include <stdint.h>
#include <stdio.h>
#define DELTA 0x9E3779B9
#define MX (((z>>5^y<<2) + (y>>3^z<<4)) ^ ((sum^y) + (key[(p&3)^e] ^ z)))
void btea(uint32_t* v, int n, uint32_t const key[4])
{
uint32_t y, z, sum;
unsigned p, rounds, e;
if (n > 1) //加密算法
{
rounds = 6 + 52 / n;
sum = 0;
z = v[n - 1];
do
{
sum += DELTA;
e = (sum >> 2) & 3;
for (p = 0; p < n - 1; p++)
{
y = v[p + 1];
z = v[p] += MX;
}
y = v[0];
z = v[n - 1] += MX;
} while (--rounds);
}
else if (n < -1) //解密算法
{
n = -n;
rounds = 6 + 52 / n;
sum = rounds * DELTA;
y = v[0];
do
{
e = (sum >> 2) & 3;
for (p = n - 1; p > 0; p--)
{
z = v[p - 1];
y = v[p] -= MX;
}
z = v[n - 1];
y = v[0] -= MX;
sum -= DELTA;
} while (--rounds);
}
}
// 可用的解密main函数实例
int main()
{
uint32_t v[10] = { 0x5d624c34,0x8629fead,0x9d11379b,0xfcd53211,0x460f63ce,0xc5816e68,0xfe5300ad,0xa0015ee,0x9806dbbb,0xef4a2648};
uint32_t k[] = {0x63656F6D,0x21216674,0x12345678,0x9ABCDEF0};
int n = 10;
btea(v, -n, k);
for (int i = 0; i < n; i++)
{
for (int j = 0; j < sizeof(uint32_t) / sizeof(uint8_t); j++)
{
printf("%c", (v[i] >> (j * 8)) & 0xFF);
}
}
return 0;
}
//moectf{X7e4_And_xx7EA_I5_BeautifuL!!!!!}


 浙公网安备 33010602011771号
浙公网安备 33010602011771号