HeroCTF v3 web wp
PwnQL #1
Login as admin to get the flag.
进入靶场,看见需要输入用户名和密码
查看源代码
看见一条提示
<!-- Hello dev, do not forget to remove login.php.bak before committing your code. -->
访问:
http://chall1.heroctf.fr:8080/login.php.bak
得到源代码
require_once(__DIR__ . "/config.php"); if (isset($_POST['username']) && isset($_POST['password'])) { $username = $_POST['username']; $password = $_POST['password']; $sql = "SELECT * FROM users WHERE username = :username AND password LIKE :password;"; $sth = $db->prepare($sql, array(PDO::ATTR_CURSOR => PDO::CURSOR_FWDONLY)); $sth->execute(array(':username' => $username, ':password' => $password)); $users = $sth->fetchAll(); if (count($users) === 1) { $msg = 'Welcome back admin ! Here is your flag : ' . FLAG; } else { $msg = 'Wrong username or password.'; } }
开始的时候我也为是需要绕过count函数,结过查了一顿资料没找到什么办法
后来看了wp,关键在于
$sql = "SELECT * FROM users WHERE username = :username AND password LIKE :password;";
LIKE 操作符用于在 WHERE 子句中搜索列中的指定模式。
SELECT column_name(s)
FROM table_name
WHERE column_name LIKE pattern
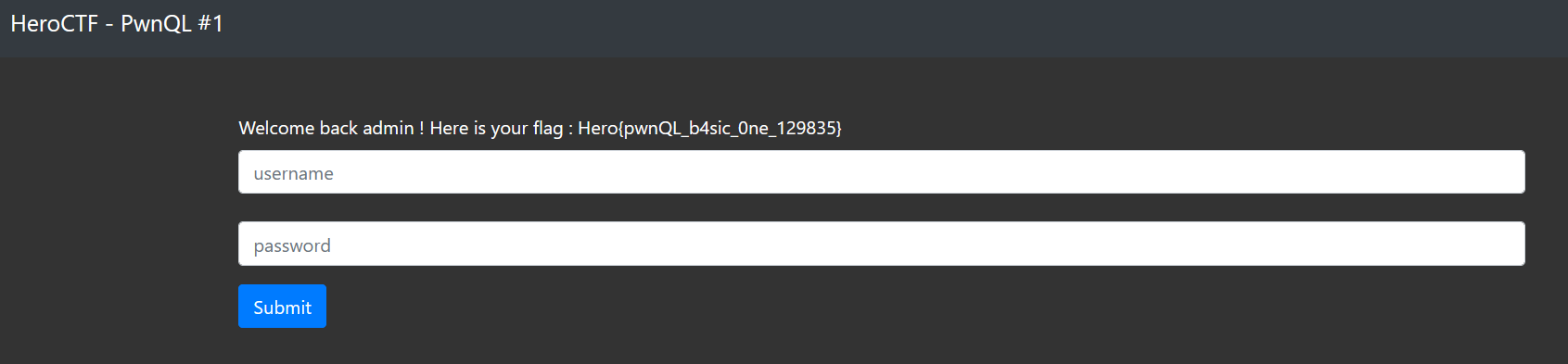
加上提示为 Login as admin to get the flag.
用户名:admin
密码:%
% 替代 0 个或多个字符
得到flag



 浙公网安备 33010602011771号
浙公网安备 33010602011771号