iptables面试题
iptabls面试题
基础理论
- 流经防火墙的三种报文:(到防火墙的、让防火墙转发的、防火墙发出的)
- 五链是指哪五链(prerouting、input、forward、output、postrouting)
- 四表是指哪四表(filter、nat、mangle、raw)
- 为什么过滤功能只能在input、output和forward三个地方实现?因为prerouting和postrouting容易发生NAT,报文不稳定。
- NAT功能可以在forward、prerouting和postrouting三个地方做,s-nat发生在postrouting,而d-nat是在pre-routing。
基本练习
- 如果要拒绝本机访问百度,怎么做呢?在两个链上做?用什么表,不用说出具体操作(output和input,用filter表)。
- 拒绝内网某个主机访问百度?只能在forward上做filter
- 给内网做S-NAT在post-routing上做
- 防火墙拒绝别人telnet,在input上做filter。
书写基本理论
iptables的书写分成两部分,一个是匹配,一个是处理动作。匹配又分为基本匹配的扩展匹配(又分为显式和隐式的),而动作又分为基本动作和扩展处理动作。
iptables默认是黑名单,而真实生产环境当中我们最好使用白名单。
iptables - t 表名 /查看/增加/替换/删除/清空 链名 匹配条件 处理动作
查看:iptables -vnL
匹配条件
基础匹配:
- -s 匹配源地址
- -d 匹配目标地址
- -p 匹配协议;tcp/udp/icmp
- -i 匹配流入接口
- -o 匹配流出接口
扩展匹配:
通过基本匹配-p 就相当于已经使用了隐式的匹配,如果要使用显式的,就得使用-m 指定,显示其实就是指明了具体细节而已。
- -p tcp --dport/--sport/ -m multiport
- -p udp --dport/--sport
- -p icmp --icmp-type 8/1
收集
- iptables有几个表以及每个表有几个链?
- 说一说你对四表五链的看法
- 查看iptables
- 禁止来自10.0.0.188 ip地址访问80端口的请求
iptabels -A INPUT -s 10.1.1.18/32 -p tcp --dport 80 -J DROP
- 如何使在命令行执行的iptables规则永久生效 (iptables save)
- 实现把访问10.0.0.3:80的请求转到172.16.1.17:80
iptables -t nat -A PREROUTING -d 10.0.0.3 -p tcp --dport 80 -j DNAT --to-destination 172.16.1.6:80
- 实现172.16.1.0/24段所有主机通过124.32.54.26外网IP共享上网。
iptables -t nat -A POSTROUTING -s 172.16.1.0/24 -j SNAT --to-source 124.32.54.26
- 请描述iptables的常见生产应用场景。
企业应用场景:
1) 把访问外网IP及端口的请求映射到内网某个服务器及端口(企业内部);
2) 硬件防火墙,把访问LVS/nginx外网VIP及80端口的请求映射到IDC 负载均衡服务器内部IP及端口上(IDC机房的操作) ;
3)局域网共享上网
- 请描述下面iptables命令的作用
iptables -N syn-flood
iptables -A INPUT -i eth0 --syn -j syn-flood
iptables -A syn-flood -m limit -limit 5000/s -limit-burst 200 -j RETURN
iptables -A syn-flood -j DROP
- 企业WEB应用较大并发场景如何优化iptables?
net.nf_conntrack_max = 25000000
net.netfilter.nf_conntrack_max = 25000000
net.netfilter.nf_conntrack_tcp_timeout_established = 180
net.netfilter.nf_conntrack_tcp_timeout_time_wait = 120
net.netfilter.nf_conntrack_tcp_timeout_close_wait = 60
net.netfilter.nf_conntrack_tcp_timeout_fin_wait = 120
- 写一个防火墙配置脚本,只允许远程主机访问本机的80端口(奇虎360面试题)
iptables -A INPUT -p tcp --dport 80 -j accept
iptables -A INPUT -p tcp -j DROP
- 请描述如何配置一个linux上网网关?
route add -net 192.168.0.0/24 gw 10.0.0.253 dev eth1
- 请描述如何配置一个专业的安全的WEB服务器主机防火墙?
//先将默认的INPUT链和Forward链关闭,只开放允许进入的端口
iptables -P OUTPUT ACCEPT
iptables -P FORWARD DROP
iptables -P INPUT DROP
- 写一个脚本解决DOS攻击生产案例
提示:根据web日志或者或者网络连接数,监控当某个IP并发连接数达到100,即调用防火墙命令封掉对应的IP,监控频率每隔3分钟。防火墙命令为:iptables -I INPUT -s 10.0.1.10 -j DROP。
//当前目录
[root@nfs-server nginx]# pwd
/var/log/nginx
//日志内容
[root@nfs-server nginx]# cat access.log
192.168.80.136 - - [28/Mar/2020:13:00:47 +0800] "GET /tomcat.css HTTP/1.0" 200 5581 "http://192.168.80.37/" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36" "-"
192.168.80.136 - - [28/Mar/2020:13:00:47 +0800] "GET /bg-nav.png HTTP/1.0" 200 1401 "http://192.168.80.37/tomcat.css" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36" "-"
192.168.80.136 - - [28/Mar/2020:13:00:47 +0800] "GET /bg-upper.png HTTP/1.0" 200 3103 "http://192.168.80.37/tomcat.css" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36" "-"
192.168.80.136 - - [28/Mar/2020:13:00:47 +0800] "GET /bg-middle.png HTTP/1.0" 200 1918 "http://192.168.80.37/tomcat.css" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36" "-"
192.168.80.136 - - [28/Mar/2020:13:01:07 +0800] "GET /testsession.jsp HTTP/1.0" 200 516 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36" "-"
192.168.80.136 - - [28/Mar/2020:13:01:08 +0800] "GET /testsession.jsp HTTP/1.0" 200 516 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36" "-"
192.168.80.136 - - [28/Mar/2020:13:01:08 +0800] "GET /testsession.jsp HTTP/1.0" 200 516 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36" "-"
192.168.80.136 - - [28/Mar/2020:13:01:08 +0800] "GET /testsession.jsp HTTP/1.0" 200 516 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36" "-"
192.168.80.139 - - [28/Mar/2020:13:01:08 +0800] "GET /testsession.jsp HTTP/1.0" 200 516 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36" "-"
192.168.80.133 - - [28/Mar/2020:13:01:08 +0800] "GET /testsession.jsp HTTP/1.0" 200 516 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36" "-"
192.168.80.130 - - [28/Mar/2020:13:01:08 +0800] "GET /testsession.jsp HTTP/1.0" 200 516 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36" "-"
192.168.80.135 - - [28/Mar/2020:13:01:08 +0800] "GET /testsession.jsp HTTP/1.0" 200 516 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36" "-"
192.168.80.131 - - [28/Mar/2020:13:01:08 +0800] "GET /testsession.jsp HTTP/1.0" 200 516 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36" "-"
192.168.80.133 - - [28/Mar/2020:13:01:08 +0800] "GET /testsession.jsp HTTP/1.0" 200 516 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36" "-"
192.168.80.139 - - [28/Mar/2020:13:01:08 +0800] "GET /testsession.jsp HTTP/1.0" 200 516 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36" "-"
192.168.80.137 - - [28/Mar/2020:13:01:08 +0800] "GET /testsession.jsp HTTP/1.0" 200 516 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36" "-"
[root@nfs-server nginx]# awk '{print $1}' access.log | sort | uniq -c
1 192.168.80.130
1 192.168.80.131
2 192.168.80.133
1 192.168.80.135
8 192.168.80.136
1 192.168.80.137
2 192.168.80.139
[root@nfs-server nginx]# vim ddos.sh
#!/bin/bash
#定义一个变量接收命令行参数,参数为日志文件类型,就用上面的access.log
while true
do
#分析传入的日志文件,并在排序去重之后追加到一个临时文件里面
awk '{print $1}' $1 | sort | uniq -c > /tmp/tmp.log
exec < /tmp/tmp.log
while read line
do
#取出IP地址
ip=`echo $line | awk '{print $2}'`
#取出每个IP地址对应的次数,相同于PV
count=`echo $line | awk '{print $1}'`
#如果PV大于500,并且防火墙里面没有封这个IP
if [ $count -gt 100 ] && [ `iptables -L -n|grep "$ip" | wc -l` -lt 1 ]
then
iptables -I INPUT -s $ip -j DROP
echo "$line is dropped " >> /tmp/droplist_$(date +%F).log
fi
done
sleep 1800
done
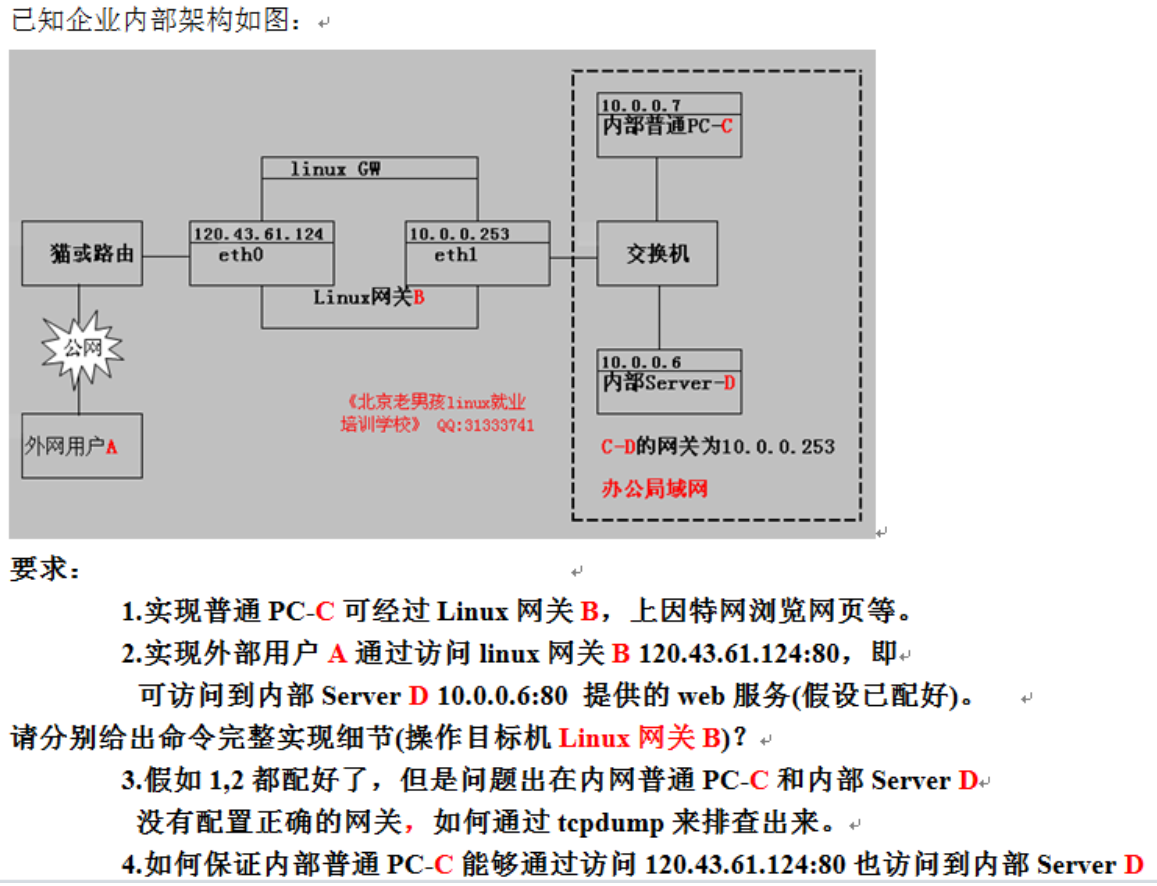
iptables -t nat -A POSTROUTING -s 10.0.0.253 -j SNAT -o eth0 --to-source 120.43.61.124
iptables -A INPUT -p tcp --dport 80 -j ACCEPT
tcpdump ip host 10.0.0.253 and 10.0.0.6 或 tcpdump ip host 10.0.0.253 and 10.0.0.7
iptables -t nat -A PREROUTING -d 120.43.61.124 -p tcp --dport 80 -j DNAT --to-destination 172.16.1.6:80

