第17周作业
#在samba服务器上安装samba包 yum install -y samba #创建samba用户和用户组 groupadd -r admins useradd -s /sbin/nologin -G admins wang #添加用户到samba服务 smbpasswd -a wang New SMB password: #设置密码 Retype new SMB password: #确认密码 Added user wang. #创建samba共享目录,并设置selinux、关闭防火墙 mkdir /testdir/smbshare -pv chgrp admins /testdir/smbshare chmod 2775 /testdir/smbshare/ #samba服务器配置 vi /etc/samba/smb.conf [share] path = /testdir/smbshare write list = @admins
samba客户端访问
yum install -y samba-client;yum install -y cifs-utils #wang用户挂载并访问 mkdir /mnt/smb mount -o user=wang,password=magedu //10.0.0.8/share /mnt/smb #此处入坑 [root@centos7 ~]#mount -o user=wang,password=magedu //10.0.0.8/share /mnt/smb mount error(95): Operation not supported #报错 Refer to the mount.cifs(8) manual page (e.g. man mount.cifs) #经网上查询得知由于内核版本所致,需要加选项vers=1.0,但经过测试这里必须是vers=2.0才可以 [root@centos7 ~]#mount -o user=wang,password=magedu,vers=2.0 //10.0.0.8/share /mnt/smb [root@centos7 ~]#df -Th Filesystem Type Size Used Avail Use% Mounted on /dev/sda3 xfs 38G 1.7G 37G 5% / devtmpfs devtmpfs 479M 0 479M 0% /dev tmpfs tmpfs 489M 0 489M 0% /dev/shm tmpfs tmpfs 489M 13M 476M 3% /run tmpfs tmpfs 489M 0 489M 0% /sys/fs/cgroup /dev/sda1 xfs 297M 102M 195M 35% /boot tmpfs tmpfs 98M 0 98M 0% /run/user/0 //10.0.0.8/share cifs 26G 1.7G 24G 7% /mnt/smb
配置开机自动挂载
[root@centos7 ~]#vi /etc/fstab # # /etc/fstab # Created by anaconda on Sat Jun 13 21:31:32 2020 # # Accessible filesystems, by reference, are maintained under '/dev/disk' # See man pages fstab(5), findfs(8), mount(8) and/or blkid(8) for more info # UUID=86315d10-d0e2-467a-aeca-da2d3bb7188b / xfs defaults 0 0 UUID=2453dcf9-bf84-41f1-a05c-b615d8dc6250 /boot xfs defaults 0 0 UUID=ce33b4de-ea28-4d49-9ded-de3a8a661735 swap swap defaults 0 0 //10.0.0.8/share /mnt/smb cifs user=wang,password=magedu,vers=2.0 0 0
#创建3个用户,并设置密码为magedu useradd -s /sbin/nologin user1 useradd -s /sbin/nologin user2 useradd -s /sbin/nologin user3 smbpasswd -a user1 smbpasswd -a user2 smbpasswd -a user3 mkdir /data/dir{1,2,3} -pv #修改samba配置文件 vi /etc/samba/smb.conf #在workgroup下加一行 config file= /etc/samba/conf.d/%U [share] path = /data/dir1 read only= no Guset ok=yes #针对user2,user3用户创建单独配置文件 mkdir /etc/samba/conf.d vi /etc/samba/conf.d/user2 [share] path=/data/dir2 read only=no create mask=0644 vi /etc/samba/conf.d/user3 [share] path=/data/dir3 systemctl restart nmb smb #用户user1,user2,user3访问share共享目录,看到目录是不同目录 smbclient //10.0.0.8/share -U user1%magedu smbclient //10.0.0.8/share -U user2%magedu smbclient //10.0.0.8/share -U user3%magedu
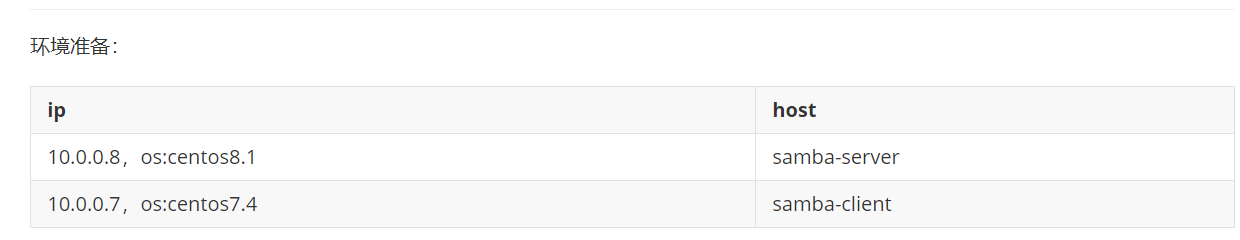
共四台主机 1 openvpn server: CentOS 8.2 eth0:10.0.0.8/24 NAT模式 eth1:172.30.0.1/24 仅主机模式 2 内网主机两台 第一台主机 eth0:172.30.0.100/24 仅主机模式 第二台主机 eth0:172.30.0.200/24 仅主机模式 3 Windows 客户端 Windows 10
yum install -y openvpn yum install -y easy-rsa
#生成服务器配置文件 [root@vpn-server ~]#cp /usr/share/doc/openvpn/sample/sample-config-files/server.conf /etc/openvpn/ [root@vpn-server ~]#ll /etc/openvpn/ total 12 drwxr-x---. 2 root openvpn 6 Apr 25 05:27 client drwxr-x---. 2 root openvpn 6 Apr 25 05:27 server -rw-r--r--. 1 root root 10785 Sep 23 14:31 server.conf #准备证书签发相关文件 [root@vpn-server ~]#cp -r /usr/share/easy-rsa/ /etc/openvpn/easy-rsa-server [root@vpn-server ~]#ll /etc/openvpn/ total 12 drwxr-x---. 2 root openvpn 6 Apr 25 05:27 client drwxr-xr-x. 3 root root 39 Sep 23 14:34 easy-rsa-server drwxr-x---. 2 root openvpn 6 Apr 25 05:27 server -rw-r--r--. 1 root root 10785 Sep 23 14:31 server.conf #准备签发证书相关变量的配置文件 [root@vpn-server ~]#cp /usr/share/doc/easy-rsa/vars.example /etc/openvpn/easy-rsa-server/3/vars [root@vpn-server ~]#vi /etc/openvpn/easy-rsa-server/3/vars #建议修改给CA和OpenVPN服务器颁发的证书的有效期,可适当加长,比如:3650天 #CA的证书有效期默为为10年 #set_var EASYRSA_CA_EXPIRE 3650 #服务器证书默为为825天 #set_var EASYRSA_CERT_EXPIRE 825 #将上面行修改为下面 set_var EASYRSA_CERT_EXPIRE 3650 [root@vpn-server ~]#tree /etc/openvpn/ /etc/openvpn/ ├── client ├── easy-rsa-server │ ├── 3 -> 3.0.7 │ ├── 3.0 -> 3.0.7 │ └── 3.0.7 │ ├── easyrsa │ ├── openssl-easyrsa.cnf │ ├── vars │ └── x509-types │ ├── ca │ ├── client │ ├── code-signing │ ├── COMMON │ ├── email │ ├── kdc │ ├── server │ └── serverClient ├── server └── server.conf 7 directories, 12 files
#脚本easyrsa帮助用法 [root@vpn-server ~]#cd /etc/openvpn/easy-rsa-server/3 [root@vpn-server 3]#./easyrsa Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-server/3.0.7/vars Easy-RSA 3 usage and overview USAGE: easyrsa [options] COMMAND [command-options] A list of commands is shown below. To get detailed usage and help for a command, run: ./easyrsa help COMMAND For a listing of options that can be supplied before the command, use: ./easyrsa help options Here is the list of commands available with a short syntax reminder. Use the 'help' command above to get full usage details. init-pki build-ca [ cmd-opts ] gen-dh gen-req <filename_base> [ cmd-opts ] sign-req <type> <filename_base> build-client-full <filename_base> [ cmd-opts ] build-server-full <filename_base> [ cmd-opts ] revoke <filename_base> [cmd-opts] renew <filename_base> [cmd-opts] build-serverClient-full <filename_base> [ cmd-opts ] gen-crl update-db show-req <filename_base> [ cmd-opts ] show-cert <filename_base> [ cmd-opts ] show-ca [ cmd-opts ] import-req <request_file_path> <short_basename> export-p7 <filename_base> [ cmd-opts ] export-p12 <filename_base> [ cmd-opts ] set-rsa-pass <filename_base> [ cmd-opts ] set-ec-pass <filename_base> [ cmd-opts ] upgrade <type> DIRECTORY STATUS (commands would take effect on these locations) EASYRSA: /etc/openvpn/easy-rsa-server/3.0.7 PKI: /etc/openvpn/easy-rsa-server/3/pki
[root@vpn-server 3]#cd /etc/openvpn/easy-rsa-server/3/ [root@vpn-server 3]#./easyrsa init-pki Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-server/3.0.7/vars init-pki complete; you may now create a CA or requests. Your newly created PKI dir is: /etc/openvpn/easy-rsa-server/3/pki [root@vpn-server 3]#tree . ├── easyrsa ├── openssl-easyrsa.cnf ├── pki #生成一个新目录及相关文件 │ ├── openssl-easyrsa.cnf │ ├── private │ ├── reqs │ └── safessl-easyrsa.cnf ├── vars └── x509-types ├── ca ├── client ├── code-signing ├── COMMON ├── email ├── kdc ├── server └── serverClient 4 directories, 13 files
[root@vpn-server 3]#tree pki pki ├── openssl-easyrsa.cnf ├── private ├── reqs └── safessl-easyrsa.cnf 2 directories, 2 files [root@vpn-server 3]#./easyrsa build-ca nopass Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-server/3.0.7/vars Using SSL: openssl OpenSSL 1.1.1c FIPS 28 May 2019 Generating RSA private key, 2048 bit long modulus (2 primes) .........................+++++ ......................................+++++ e is 65537 (0x010001) You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Common Name (eg: your user, host, or server name) [Easy-RSA CA]: #直接回车 CA creation complete and you may now import and sign cert requests. Your new CA certificate file for publishing is at: /etc/openvpn/easy-rsa-server/3/pki/ca.crt #生成自签名证书文件 [root@vpn-server 3]#tree pki pki ├── ca.crt #生成自签名的证书文件 ├── certs_by_serial ├── index.txt ├── index.txt.attr ├── issued ├── openssl-easyrsa.cnf ├── private │ └── ca.key #生成私钥文件 ├── renewed │ ├── certs_by_serial │ ├── private_by_serial │ └── reqs_by_serial ├── reqs ├── revoked │ ├── certs_by_serial │ ├── private_by_serial │ └── reqs_by_serial ├── safessl-easyrsa.cnf └── serial 12 directories, 7 files #生成CA相关文件 [root@vpn-server 3]#cat pki/serial 01 [root@vpn-server 3]#ll pki/index.txt -rw-------. 1 root root 0 Sep 23 14:59 pki/index.txt [root@vpn-server 3]#ll pki/ca.crt pki/private/ca.key -rw-------. 1 root root 1204 Sep 23 14:59 pki/ca.crt -rw-------. 1 root root 1675 Sep 23 14:59 pki/private/ca.key
[root@vpn-server ~]#cd /etc/openvpn/easy-rsa-server/3 [root@vpn-server 3]#./easyrsa gen-req server nopass Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-server/3.0.7/vars Using SSL: openssl OpenSSL 1.1.1c FIPS 28 May 2019 Generating a RSA private key ............................................+++++ .+++++ writing new private key to '/etc/openvpn/easy-rsa-server/3/pki/easy-rsa-14307.KtQvlk/tmp.U8Q0WF' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Common Name (eg: your user, host, or server name) [server]: #接受默认值,直接回车 Keypair and certificate request completed. Your files are: req: /etc/openvpn/easy-rsa-server/3/pki/reqs/server.req #生成请求文件 key: /etc/openvpn/easy-rsa-server/3/pki/private/server.key #生成私钥文件 [root@vpn-server 3]#tree pki pki ├── ca.crt ├── certs_by_serial ├── index.txt ├── index.txt.attr ├── issued ├── openssl-easyrsa.cnf ├── private │ ├── ca.key │ └── server.key #生成私钥文件 ├── renewed │ ├── certs_by_serial │ ├── private_by_serial │ └── reqs_by_serial ├── reqs │ └── server.req #生成请求文件 ├── revoked │ ├── certs_by_serial │ ├── private_by_serial │ └── reqs_by_serial ├── safessl-easyrsa.cnf └── serial 12 directories, 9 files
[root@vpn-server 3]#./easyrsa help sign Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-server/3.0.7/vars sign-req <type> <filename_base> Sign a certificate request of the defined type. <type> must be a known type such as 'client', 'server', 'serverClient', or 'ca' (or a user-added type.) This request file must exist in the reqs/ dir and have a .req file extension. See import-req below for importing reqs from other sources.
颁发服务端证书
[root@vpn-server 3]#./easyrsa sign server server Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-server/3.0.7/vars Using SSL: openssl OpenSSL 1.1.1c FIPS 28 May 2019 You are about to sign the following certificate. Please check over the details shown below for accuracy. Note that this request has not been cryptographically verified. Please be sure it came from a trusted source or that you have verified the request checksum with the sender. Request subject, to be signed as a server certificate for 3650 days: #可以看到vars文件指定的有效期 subject= commonName = server Type the word 'yes' to continue, or any other input to abort. Confirm request details: yes #输入yes,回车 Using configuration from /etc/openvpn/easy-rsa-server/3/pki/easy-rsa-14490.1zp9vh/tmp.hxCtCm Check that the request matches the signature Signature ok The Subject's Distinguished Name is as follows commonName :ASN.1 12:'server' Certificate is to be certified until Sep 21 07:28:08 2030 GMT (3650 days) Write out database with 1 new entries Data Base Updated Certificate created at: /etc/openvpn/easy-rsa-server/3/pki/issued/server.crt #生成服务器证书文件
验证结果
[root@vpn-server 3]#tree pki pki ├── ca.crt ├── certs_by_serial │ └── 7A07579ED933C60BA4C6E548AB001053.pem #服务器证书文件 ├── index.txt ├── index.txt.attr ├── index.txt.attr.old ├── index.txt.old ├── issued │ └── server.crt #服务器证书文件 ├── openssl-easyrsa.cnf ├── private │ ├── ca.key │ └── server.key ├── renewed │ ├── certs_by_serial │ ├── private_by_serial │ └── reqs_by_serial ├── reqs │ └── server.req ├── revoked │ ├── certs_by_serial │ ├── private_by_serial │ └── reqs_by_serial ├── safessl-easyrsa.cnf ├── serial └── serial.old 12 directories, 14 files [root@vpn-server 3]#diff pki/certs_by_serial/7A07579ED933C60BA4C6E548AB001053.pem pki/issued/server.crt [root@vpn-server 3]#ll !* ll pki/certs_by_serial/7A07579ED933C60BA4C6E548AB001053.pem pki/issued/server.crt -rw-------. 1 root root 4608 Sep 23 15:28 pki/certs_by_serial/7A07579ED933C60BA4C6E548AB001053.pem -rw-------. 1 root root 4608 Sep 23 15:28 pki/issued/server.crt #证书相关文件 [root@vpn-server 3]#cat pki/serial 7A07579ED933C60BA4C6E548AB001054 [root@vpn-server 3]#cat pki/index.txt V 300921072808Z 7A07579ED933C60BA4C6E548AB001053 unknown /CN=server
[root@vpn-server 3]#cd /etc/openvpn/easy-rsa-server/3 [root@vpn-server 3]#./easyrsa gen-dh .... DH parameters of size 2048 created at /etc/openvpn/easy-rsa-server/3/pki/dh.pem [root@vpn-server 3]#ll pki/dh.pem -rw-------. 1 root root 424 Sep 23 16:38 pki/dh.pem
准备客户端证书环境
上面服务端证书配置完成,下面是配置客户端证书
[root@vpn-server ~]#cp -r /usr/share/easy-rsa/ /etc/openvpn/easy-rsa-client [root@vpn-server ~]#cp /usr/share/doc/easy-rsa/vars.example /etc/openvpn/easy-rsa-client/3/vars [root@vpn-server ~]#cd /etc/openvpn/easy-rsa-client/3 [root@vpn-server 3]#ls easyrsa openssl-easyrsa.cnf vars x509-types [root@vpn-server 3]#tree . ├── easyrsa ├── openssl-easyrsa.cnf ├── vars └── x509-types ├── ca ├── client ├── code-signing ├── COMMON ├── email ├── kdc ├── server └── serverClient 1 directory, 11 files [root@vpn-server 3]#./easyrsa init-pki Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-client/3.0.7/vars init-pki complete; you may now create a CA or requests. Your newly created PKI dir is: /etc/openvpn/easy-rsa-client/3/pki #生成新目录 [root@vpn-server 3]#tree . ├── easyrsa ├── openssl-easyrsa.cnf ├── pki #生成新目录 │ ├── openssl-easyrsa.cnf │ ├── private │ ├── reqs │ └── safessl-easyrsa.cnf ├── vars └── x509-types ├── ca ├── client ├── code-signing ├── COMMON ├── email ├── kdc ├── server └── serverClient 4 directories, 13 files
[root@vpn-server 3]#pwd /etc/openvpn/easy-rsa-client/3 [root@vpn-server 3]#./easyrsa gen-req wangxiaochun nopass Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-client/3.0.7/vars Using SSL: openssl OpenSSL 1.1.1c FIPS 28 May 2019 Generating a RSA private key ........................................+++++ .........+++++ writing new private key to '/etc/openvpn/easy-rsa-client/3/pki/easy-rsa-14760.c3QZ9E/tmp.dBSzGc' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Common Name (eg: your user, host, or server name) [wangxiaochun]: #接受默认值,直接回车 Keypair and certificate request completed. Your files are: req: /etc/openvpn/easy-rsa-client/3/pki/reqs/wangxiaochun.req #证书申请文件 key: /etc/openvpn/easy-rsa-client/3/pki/private/wangxiaochun.key #私钥文件 #生成两个新文件 [root@vpn-server 3]#tree . ├── easyrsa ├── openssl-easyrsa.cnf ├── pki │ ├── openssl-easyrsa.cnf │ ├── private │ │ └── wangxiaochun.key #私钥文件 │ ├── reqs │ │ └── wangxiaochun.req #证书申请文件 │ └── safessl-easyrsa.cnf ├── vars └── x509-types ├── ca ├── client ├── code-signing ├── COMMON ├── email ├── kdc ├── server └── serverClient 4 directories, 15 files
[root@vpn-server 3]#cd /etc/openvpn/easy-rsa-server/3 [root@vpn-server 3]#pwd /etc/openvpn/easy-rsa-server/3 #将客户端证书请求文件复制到CA的工作目录 [root@vpn-server 3]#./easyrsa import-req /etc/openvpn/easy-rsa-client/3/pki/reqs/wangxiaochun.req wangxiaochun [root@vpn-server 3]#ll pki/reqs/wangxiaochun.req /etc/openvpn/easy-rsa-client/3/pki/reqs/wangxiaochun.req -rw-------. 1 root root 891 Sep 23 16:50 /etc/openvpn/easy-rsa-client/3/pki/reqs/wangxiaochun.req -rw-------. 1 root root 891 Sep 23 16:34 pki/reqs/wangxiaochun.req #修改给客户端颁发的证书的有效期 [root@vpn-server 3]#vi vars #建议修改给客户端颁发证书的有效期,可适当减少,比如:90天 #set_var EASYRSA_CERT_EXPIRE 825 #将上面行修改为下面 set_var EASYRSA_CERT_EXPIRE 90 #签发客户端证书 [root@vpn-server 3]#./easyrsa sign client wangxiaochun Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa-server/3.0.7/vars Using SSL: openssl OpenSSL 1.1.1c FIPS 28 May 2019 You are about to sign the following certificate. Please check over the details shown below for accuracy. Note that this request has not been cryptographically verified. Please be sure it came from a trusted source or that you have verified the request checksum with the sender. Request subject, to be signed as a client certificate for 3650 days: subject= commonName = wangxiaochun Type the word 'yes' to continue, or any other input to abort. Confirm request details: yes Using configuration from /etc/openvpn/easy-rsa-server/3/pki/easy-rsa-15080.Zz4NcM/tmp.fy6vve Check that the request matches the signature Signature ok The Subject's Distinguished Name is as follows commonName :ASN.1 12:'wangxiaochun' Certificate is to be certified until Sep 21 08:58:17 2030 GMT (3650 days) Write out database with 1 new entries Data Base Updated Certificate created at: /etc/openvpn/easy-rsa-server/3/pki/issued/wangxiaochun.crt [root@vpn-server 3]#tree pki pki ├── ca.crt ├── certs_by_serial │ ├── 7A07579ED933C60BA4C6E548AB001053.pem │ └── A1ED0D2BF06C06372BD25478E6D21AA5.pem ├── dh.pem ├── index.txt ├── index.txt.attr ├── index.txt.attr.old ├── index.txt.old ├── issued │ ├── server.crt │ └── wangxiaochun.crt ├── openssl-easyrsa.cnf ├── private │ ├── ca.key │ └── server.key ├── renewed │ ├── certs_by_serial │ ├── private_by_serial │ └── reqs_by_serial ├── reqs │ ├── server.req │ └── wangxiaochun.req ├── revoked │ ├── certs_by_serial │ ├── private_by_serial │ └── reqs_by_serial ├── safessl-easyrsa.cnf ├── serial └── serial.old 12 directories, 18 files [root@vpn-server 3]#cat pki/index.txt V 300921072808Z 7A07579ED933C60BA4C6E548AB001053 unknown /CN=server V 300921085817Z A1ED0D2BF06C06372BD25478E6D21AA5 unknown /CN=wangxiaochun [root@vpn-server 3]#ll pki/issued/ total 16 -rw-------. 1 root root 4608 Sep 23 15:28 server.crt -rw-------. 1 root root 4500 Sep 23 16:58 wangxiaochun.crt [root@vpn-server 3]# ll pki/certs_by_serial/ total 16 -rw-------. 1 root root 4608 Sep 23 15:28 7A07579ED933C60BA4C6E548AB001053.pem -rw-------. 1 root root 4500 Sep 23 16:58 A1ED0D2BF06C06372BD25478E6D21AA5.pem
[root@vpn-server ~]#mkdir /etc/openvpn/certs [root@vpn-server ~]#cp /etc/openvpn/easy-rsa-server/3/pki/ca.crt /etc/openvpn/certs/ [root@vpn-server ~]#cp /etc/openvpn/easy-rsa-server/3/pki/issued/server.crt /etc/openvpn/certs/ [root@vpn-server ~]#cp /etc/openvpn/easy-rsa-server/3/pki/private/server.key /etc/openvpn/certs/ [root@vpn-server ~]#cp /etc/openvpn/easy-rsa-server/3/pki/dh.pem /etc/openvpn/certs/ [root@vpn-server ~]#ll /etc/openvpn/certs/ total 20 -rw-------. 1 root root 1204 Sep 24 10:25 ca.crt -rw-------. 1 root root 424 Sep 24 10:32 dh.pem -rw-------. 1 root root 4608 Sep 24 10:29 server.crt -rw-------. 1 root root 1704 Sep 24 10:30 server.key
[root@vpn-server 3]#mkdir /etc/openvpn/client/wangxiaochun/ [root@vpn-server 3]#find /etc/openvpn/ -name "wangxiaochun.key" -o -name "wangxiaochun.crt" -o -name ca.crt /etc/openvpn/easy-rsa-server/3.0.7/pki/issued/wangxiaochun.crt /etc/openvpn/easy-rsa-server/3.0.7/pki/ca.crt /etc/openvpn/easy-rsa-client/3.0.7/pki/private/wangxiaochun.key /etc/openvpn/certs/ca.crt [root@vpn-server 3]#find /etc/openvpn/ \( -name "wangxiaochun.key" -o -name "wangxiaochun.crt" -o -name ca.crt \) -exec cp {} /etc/openvpn/client/wangxiaochun \; [root@vpn-server 3]#ll /etc/openvpn/client/wangxiaochun/ total 16 -rw-------. 1 root root 1204 Sep 24 11:36 ca.crt -rw-------. 1 root root 4500 Sep 24 11:36 wangxiaochun.crt -rw-------. 1 root root 1708 Sep 24 11:36 wangxiaochun.key
[root@vpn-server 3]#vi /etc/openvpn/server.conf [root@vpn-server 3]#grep '^[a-Z].*' /etc/openvpn/server.conf port 1194 proto tcp dev tun ca /etc/openvpn/certs/ca.crt cert /etc/openvpn/certs/server.crt key /etc/openvpn/certs/server.key # This file should be kept secret dh /etc/openvpn/certs/dh.pem server 10.8.0.0 255.255.255.0 push "route 192.168.20.0 255.255.255.0" keepalive 10 120 cipher AES-256-CBC compress lz4-v2 push "compress lz4-v2" max-clients 100 user nobody group nobody persist-key persist-tun status /var/log/openvpn/openvpn-status.log log-append /var/log/openvpn/openvpn.log verb 3 mute 200 #准备日志相关目录 [root@vpn-server 3]#getent passwd openvpn openvpn:x:995:990:OpenVPN:/etc/openvpn:/sbin/nologin [root@vpn-server 3]#mkdir /var/log/openvpn [root@vpn-server ~]#chown openvpn.openvpn /var/log/openvpn [root@vpn-server ~]#ll -d /var/log/openvpn drwxr-xr-x. 2 openvpn openvpn 6 Sep 24 14:55 /var/log/openvpn
#在服务器开启ip_forward转发功能 [root@vpn-server ~]#echo net.ipv4.ip_forward=1 >> /etc/sysctl.conf [root@vpn-server ~]#sysctl -p net.ipv4.ip_forward = 1 #添加SNAT规则 [root@vpn-server ~]#echo 'iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -j MASQUERADE' >> /etc/rc.d/rc.local [root@centos8 3]#chmod +x /etc/rc.d/rc.local [root@centos8 3]#/etc/rc.d/rc.local [root@vpn-server ~]#iptables -vnL -t nat Chain PREROUTING (policy ACCEPT 215 packets, 27276 bytes) pkts bytes target prot opt in out source destination Chain INPUT (policy ACCEPT 1 packets, 52 bytes) pkts bytes target prot opt in out source destination Chain POSTROUTING (policy ACCEPT 104 packets, 16846 bytes) pkts bytes target prot opt in out source destination 0 0 MASQUERADE all -- * * 10.8.0.0/24 0.0.0.0/0 Chain OUTPUT (policy ACCEPT 104 packets, 16846 bytes) pkts bytes target prot opt in out source destination
[root@centos7 ~]#rpm -ql openvpn|grep systemd /usr/lib/systemd/system/openvpn-client@.service /usr/lib/systemd/system/openvpn-server@.service /usr/lib/systemd/system/openvpn@.service /usr/share/doc/openvpn-2.4.9/README.systemd #CentOS8 缺失unit文件,从CentOS7复制文件 [root@vpn-server ~]#rpm -ql openvpn|grep systemd /usr/lib/systemd/system/openvpn-client@.service /usr/lib/systemd/system/openvpn-server@.service /usr/share/doc/openvpn/README.system [root@centos7 ~]#cat /usr/lib/systemd/system/openvpn@.service [Unit] Description=OpenVPN Robust And Highly Flexible Tunneling Application On %I After=network.target [Service] Type=notify PrivateTmp=true ExecStart=/usr/sbin/openvpn --cd /etc/openvpn/ --config %i.conf [Install] WantedBy=multi-user.target [root@centos7 ~]#scp /lib/systemd/system/openvpn@.service 10.0.0.8:/lib/systemd/system/ [root@vpn-server ~]#systemctl daemon-reload [root@vpn-server ~]#systemctl enable --now openvpn@server [root@vpn-server ~]#ss -tnlp State Recv-Q Send-Q Local Address:Port Peer Address:Port LISTEN 0 128 0.0.0.0:22 0.0.0.0:* users:(("sshd",pid=839,fd=5)) LISTEN 0 50 0.0.0.0:445 0.0.0.0:* users:(("smbd",pid=1265,fd=37)) LISTEN 0 32 0.0.0.0:1194 0.0.0.0:* users:(("openvpn",pid=2362,fd=8)) LISTEN 0 50 0.0.0.0:139 0.0.0.0:* users:(("smbd",pid=1265,fd=38)) LISTEN 0 128 [::]:22 [::]:* users:(("sshd",pid=839,fd=7)) LISTEN 0 50 [::]:445 [::]:* users:(("smbd",pid=1265,fd=35)) LISTEN 0 50 [::]:139 [::]:* users:(("smbd",pid=1265,fd=36))
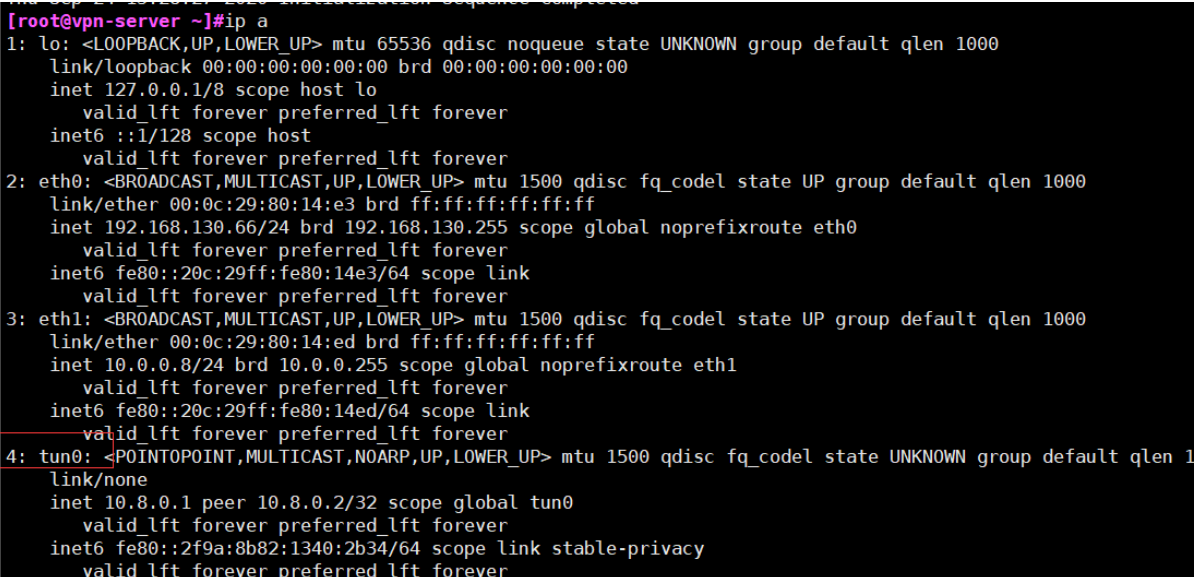
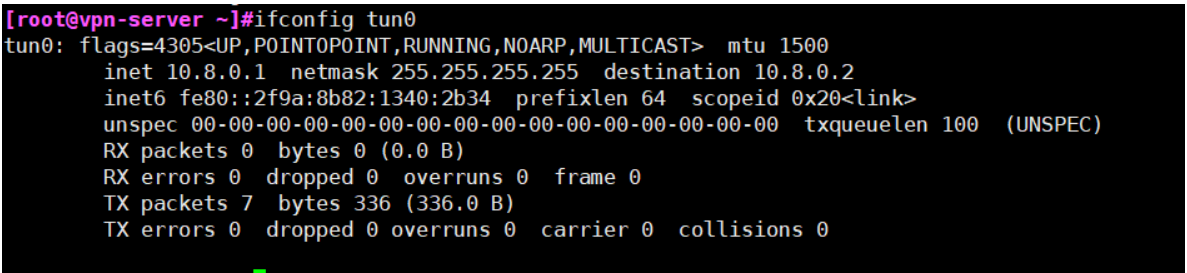
验证 tun 网卡设备:
#生成客户端配置文件,文件名后缀必须为.ovpn [root@vpn-server ~]#grep '^[[:alpha:]].*' /usr/share/doc/openvpn/sample/sample-config-files/client.conf client dev tun proto udp remote my-server-1 1194 resolv-retry infinite nobind persist-key persist-tun ca ca.crt cert client.crt key client.key remote-cert-tls server tls-auth ta.key 1 cipher AES-256-CBC verb 3 [root@vpn-server ~]#grep '^[[:alpha:]].*' /usr/share/doc/openvpn/sample/sample-config-files/client.conf > /etc/openvpn/client/wangxiaochun/client.ovpn [root@vpn-server ~]#cat /etc/openvpn/client/wangxiaochun/client.ovpn client dev tun proto tcp remote 10.0.0.8 1194 resolv-retry infinite nobind #persist-key #persist-tun ca ca.crt cert wangxiaochun.crt key wangxiaochun.key remote-cert-tls server #tls-auth ta.key 1 cipher AES-256-CBC verb 3 compress lz4-v2
官方客户端下载地址:
https://openvpn.net/community-downloads/
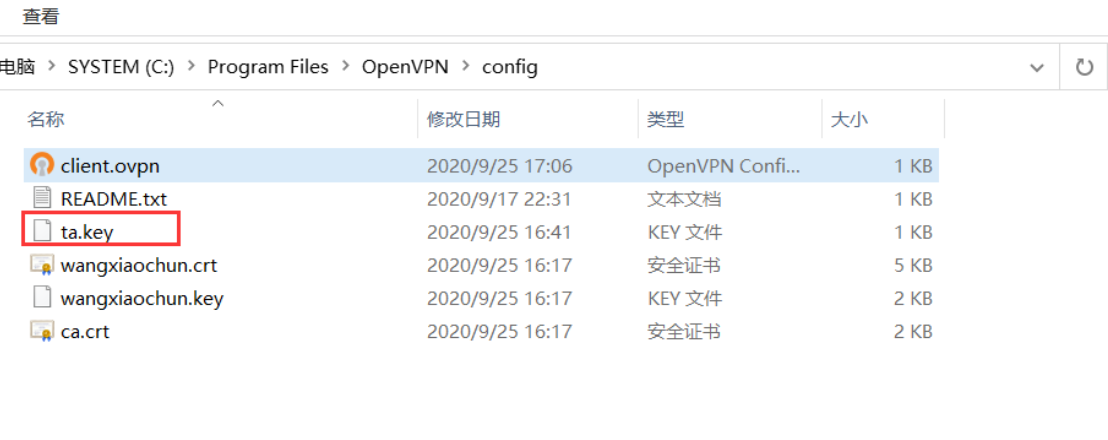
#在服务器打包证书并下载发送给windows客户端 [root@centos8 ~]#cd /etc/openvpn/client/wangxiaochun/ [root@centos8 wangxiaochun]#ll total 20 -rw------- 1 root root 1204 Sep 25 16:17 ca.crt -rw-r--r-- 1 root root 238 Sep 25 16:33 client.ovpn -rw------- 1 root root 4506 Sep 25 16:17 wangxiaochun.crt -rw------- 1 root root 1704 Sep 25 16:17 wangxiaochun.key #下载上面4个文件传至C:\Program Files\OpenVPN\config openvpn客户端安装目
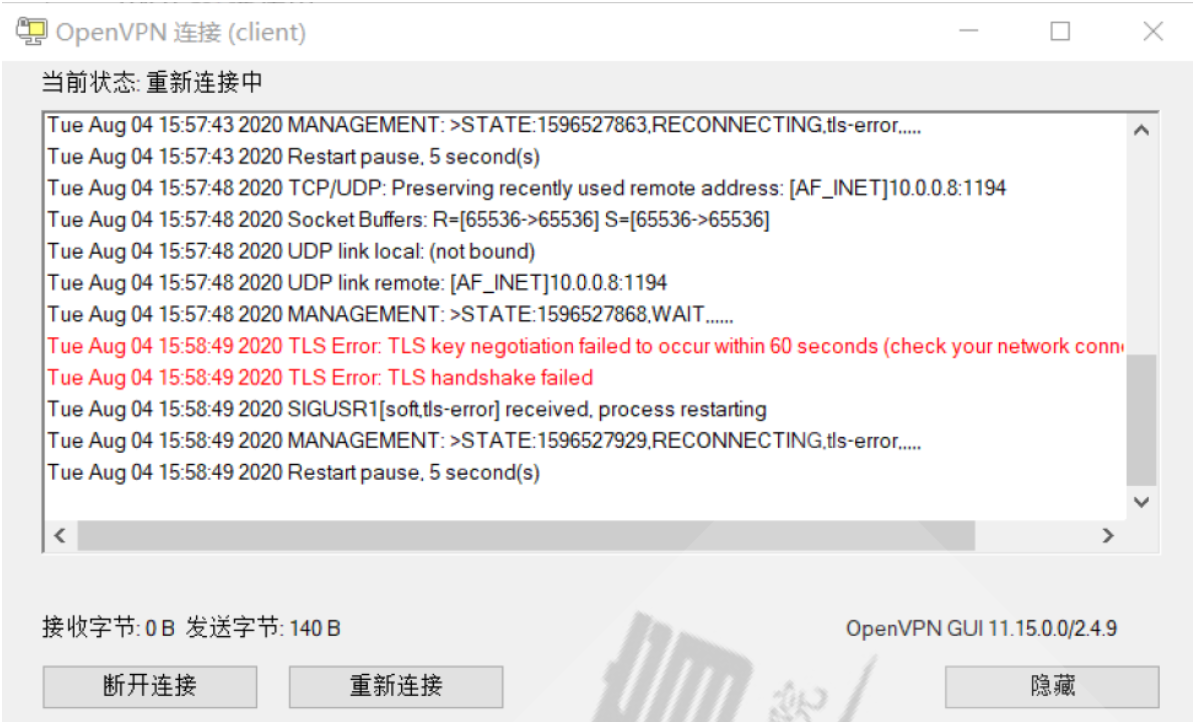
在Windows上启动客户端测试报错如下:
(10) 启用安全增强功能
启用防止DoS攻击的安全增强配置
[root@centos8 ~]#openvpn --genkey --secret /etc/openvpn/certs/ta.key [root@centos8 certs]#ll /etc/openvpn/certs total 24 -rw------- 1 root root 1204 Sep 25 16:16 ca.crt -rw------- 1 root root 424 Sep 25 16:16 dh.pem -rw------- 1 root root 4608 Sep 25 16:16 server.crt -rw------- 1 root root 1704 Sep 25 16:16 server.key -rw------- 1 root root 636 Sep 25 16:41 ta.key [root@centos8 ~]#vim /etc/openvpn/server.conf #tls-auth ta.key 0 # This file is secret tls-auth /etc/openvpn/certs/ta.key 0 #客户端为1,服务器端为0 [root@centos8 ~]#systemctl restart openvpn@server.service
将ta.key 传到客户端相关目录下
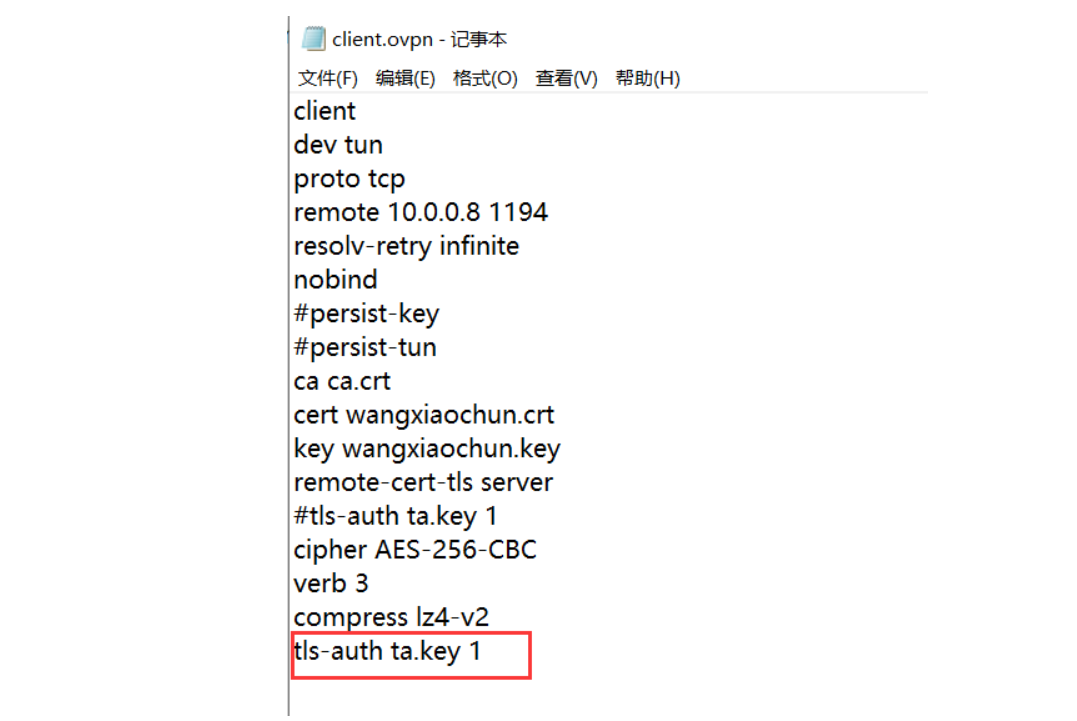
修改客户端配置文件clent.ovpn,添加一行
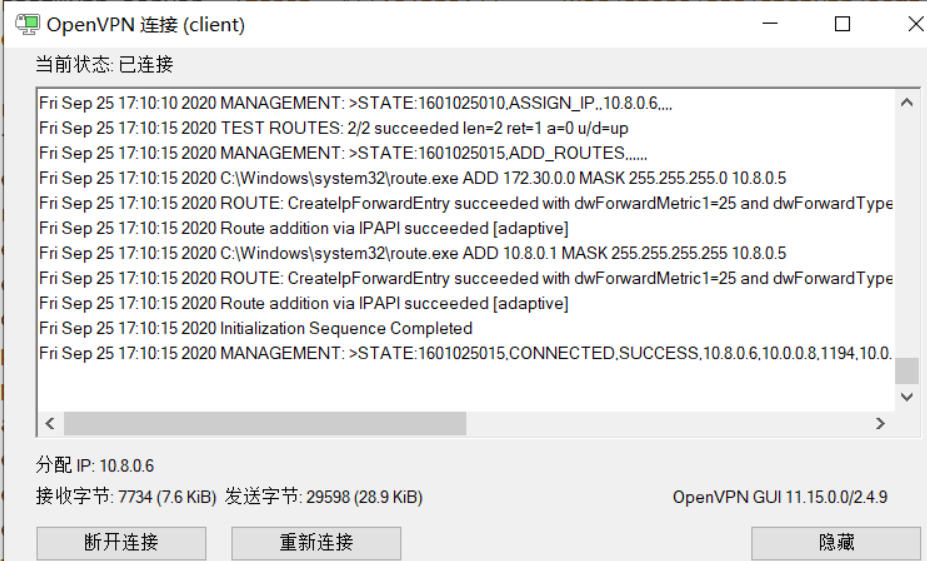
客户端重新连接成功



 浙公网安备 33010602011771号
浙公网安备 33010602011771号