iptables
防火墙种类及使用说明
种类
- 硬件: 整个企业入口
- 三层路由: H3C 华为 Cisco(思科)
- 深信服
Juniper
- 软件: 开源软件 网站内部 封ip 封ip
- iptables 写入到Linux内核中 以后服务docker
- firewalld C7
- 云防火墙
- 阿里云:安全组
必须熟悉的名称
- 容器: 瓶子 罐子 存放东西
- 表(table): 存放链的容器
- 链(chain): 存放规则的容器
- 规则(policy): 准许或拒绝规则

| Netfilter | 表(tables) | 链(chains) | 规则(Policy) |
|---|---|---|---|
| 一栋楼 | 楼里的房子 | 房子里的柜子 | 柜子里衣服,摆放规则 |
iptables
iptables执行过程




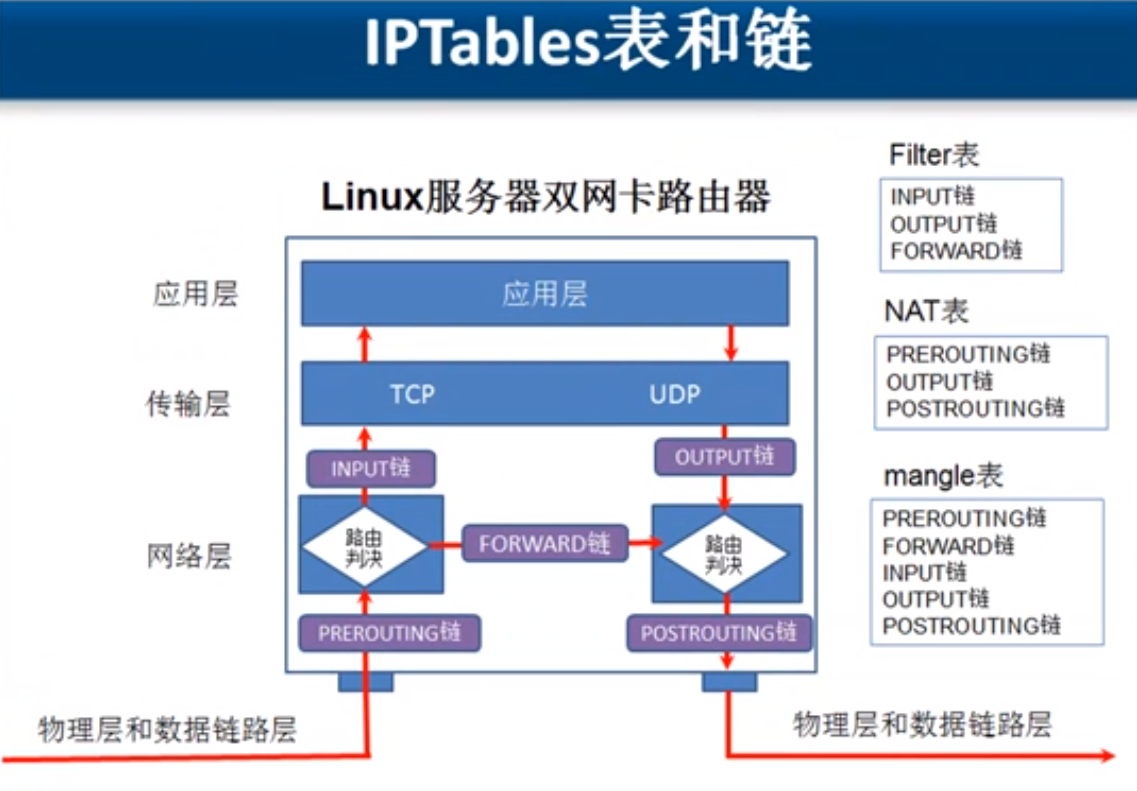
表与链
简介
- iptables 是 4表五链
- 4表: filter 表 nat表 raw表 mangle表
- 伍链: INPUT OUTPUT FORWARD PREROUTING POSTROUTING
每个表说明
filter表
- 防火墙: 屏蔽或准许 端口 ip
| filter表 | 强调:主要和主机自身相关,真正负责主机防火墙功能的(过滤流入流出主机的数据包) filter表示iptables默认使用的表,这个表定义了三个链(chains) 企业工作场景:主机防火墙 |
|---|---|
| INPUT | 负责过滤所有目标地址是本机地址的数据包 通俗来说:就是过滤进入主机的数据包 |
| FORWARD | 负责转发流经主机的数据包。起转发的作用,和NAT关系很大,后面会详细介绍 LVS NAT模式,net.ipv4.ip_forward=0 |
| OUTPUT | 处理所有源地址是本机地址的数据包 通俗的讲:就是处理从主机发出去的数据包 |
nat表
-
实现nat功能
- 实现共享上网(内网服务器上外网)
- 端口映射和ip映射
-
| nat | 负责网络地址转换的,即来源与目的IP地址和port的转换。 应用:和主机本身无关,一般用于局域网共享上网或者特殊的端口转换服务相关。 工作场景: 1. 用于企业路由(zebra)或网关(iptables),共享上网(POSTROUTING) 2. 做内部外部IP地址一对一映射(dmz),硬件防火墙映射IP到内部服务器,ftp服务(PREROUTING) 3. WEB,单个端口的映射,直接映射80端口(PREROUTING) 这个表定义了3个链,nat功能相当于网络的acl控制。和网络交换机acl类似。 |
|---|---|
| OUTPUT | 和主机放出去的数据包有关,改变主机发出数据包的目的地址。 |
| PREROUTING | 在数据包到达防火墙时,进行路由判断之前执行的规则,作用是改变数据包的目的地址、目的端口等 就是收信时,根据规则重写收件人的地址。 例如:把公网IP:xxx.xxx.xxx.xxx映射到局域网的xx.xx.xx.xx服务器上。 如果是web服务,可以报80转换为局域网的服务器9000端口上 10.0.0.61 8080(目标端口) ----nat---à 10.0.0.7 22 |
| POSTROUTING | 在数据包离开防火墙时进行路由判断之后执行的规则,作用改变数据包的源地址,源端口等。 写好发件人的地址,要让家人回信时能够有地址可回。 例如。默认笔记本和虚拟机都是局域网地址,在出网的时候被路由器将源地址改为了公网地址。 生产应用:局域网共享上网。 |
环境准备及命令
首先需要停止firewalld
systemctl stop firewalld
systemctl disable firewalld
# 安装iptables
[root@web01 ~]# yum install -y iptables-services
[root@web01 ~]# rpm -qa | grep iptable
iptables-help-1.8.5-2.ky10.noarch
iptables-1.8.5-2.ky10.x86_64
iptables-libs-1.8.5-2.ky10.x86_64
# 加载相关模块
# 临时加载
modprobe ip_tables
modprobe iptable_filter
modprobe iptable_nat
modprobe ip_conntrack
modprobe ip_conntrack_ftp
modprobe ip_nat_ftp
modprobe ipt_state
# 写入配置文件
cat >>/etc/rc.local<<EOF
modprobe ip_tables
modprobe iptable_filter
modprobe iptable_nat
modprobe ip_conntrack
modprobe ip_conntrack_ftp
modprobe ip_nat_ftp
modprobe ipt_state
EOF
[root@web01 ~]# chmod +x /etc/rc.d/rc.local
# 查看模块
[root@web01 ~]# lsmod |egrep 'filter|nat|ipt'
nf_nat_ftp 16384 0
nf_conntrack_ftp 20480 1 nf_nat_ftp
iptable_nat 16384 0
nf_nat 45056 2 nf_nat_ftp,iptable_nat
nf_conntrack 159744 4 nf_nat,nf_nat_ftp,xt_state,nf_conntrack_ftp
iptable_filter 16384 0
ip_tables 28672 2 iptable_filter,iptable_nat
libcrc32c 16384 3 nf_conntrack,nf_nat,xfs
# 开启服务,并设置开机自启
[root@web01 ~]# systemctl enable iptables.service --now
Created symlink /etc/systemd/system/basic.target.wants/iptables.service → /usr/lib/systemd/system/iptables.service.
[root@web01 ~]# systemctl status iptables.service
● iptables.service - IPv4 firewall with iptables
Loaded: loaded (/usr/lib/systemd/system/iptables.service; enabled; vendor preset: disabled)
Active: active (exited) since Thu 2025-01-16 13:54:02 CST; 6s ago
Process: 1686 ExecStart=/usr/libexec/iptables/iptables.init start (code=exited, status=0/SUCCESS)
Main PID: 1686 (code=exited, status=0/SUCCESS)
Jan 16 13:54:02 web01 systemd[1]: Starting IPv4 firewall with iptables...
Jan 16 13:54:02 web01 iptables.init[1686]: iptables: Applying firewall rules: [ OK ]
Jan 16 13:54:02 web01 systemd[1]: Started IPv4 firewall with iptables.
# 查看防火墙默认规则,默认是看filter表
[root@web01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT)
target prot opt source destination
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@web01 ~]# iptables -t filter -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT)
target prot opt source destination
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT)
target prot opt source destination

相关参数
| 参数 | 含义 |
|---|---|
| -L | 显示表中的所有规则 |
| -n | 不要把端口 或ip反向解析为 名字 |
| -t | 指定表 不指定默认是filter表 |
| -A | append 追加 加入准许类规则 使用-A 将规则追加在最后 |
| -D | delete 删除 -D INPUT 1 |
| -I | insert 拒绝类规则放在所有规则最上面 拒绝类 -I |
| --line-numbers | 显示行号 |
| 参数 | 含义 | |
|---|---|---|
| -p | 协议 protocal tcp/udp/icmp/all | |
| --dport | 目标端口 dest destination 指定端口 加上协议 -p tcp | |
| --sport | 源端口 source 源 | |
| -s | --source 源ip | |
| -d | --destination 目标ip | |
| -m | 指定模块 multiport(一次性写多个端口) | |
| -i | input 输入的时候 从哪个网卡进来 | |
| -o | ouput 输出的时候 从哪个网卡出去 |
| 参数 | 含义 | |
|---|---|---|
| -j | 满足条件后的动作 : DROP/ACCEPT/REJECT | |
| DROP REJECT拒绝 DROP把数据丢掉 不会返回信息给用户 REJECT 拒绝 返回拒绝信息 |
||
| 参数 | 含义 | |
|---|---|---|
| -F flush | 清除所有规则,不会处理默认的规则 | |
| -X | 删除用户自定义的链 | |
| -Z | 链的计数器清零(数据包计数器与数据包字节计数器) |
配置filter表规则
禁止22端口
iptables -t filter -I INPUT -p tcp --dport 22 -j DROP
删除 规则 -D

删除规则
查看序号
[root@m01 ~]# iptables -nL --line
Chain INPUT (policy ACCEPT)
num target prot opt source destination
1 DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
根据序号删除规则
[root@m01 ~]# iptables -D INPUT 1
第二种删除方式:
添加
[root@m01 ~]# iptables -t filter -I INPUT -p tcp --dport 80 -j DROP
删除
[root@m01 ~]# iptables -t filter -D INPUT -p tcp --dport 80 -j DROP
禁止80端口
# 我们在web01上写一个默认网页
[root@web01 ~]# vim /etc/nginx/conf.d/wp.conf
server {
listen 80 default;
server_name _;
root /code/test;
index index.html;
}
[root@web01 ~]# nginx -t
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
[root@web01 ~]# mkdir /code/test
[root@web01 ~]# echo 11 > /code/test/index.html
[root@web01 ~]# systemctl restart nginx
[root@web01 ~]# curl 192.168.121.7
11
# 写规则
[root@web01 ~]# iptables -t filter -I INPUT -p tcp --dport 80 -j DROP
[root@web01 ~]# iptables -t filter -I INPUT -p tcp --dport 443 -j DROP
[root@web01 ~]# iptables -nL --line-num
Chain INPUT (policy ACCEPT)
num target prot opt source destination
1 DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:443
2 DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
Chain FORWARD (policy ACCEPT)
num target prot opt source destination
Chain OUTPUT (policy ACCEPT)
num target prot opt source destination
# -A和-I的区别
[root@web01 ~]# iptables -t filter -A INPUT -p tcp --dport 10050 -j DROP
[root@web01 ~]# iptables -I INPUT -p tcp --dport 10051 -j DROP
[root@web01 ~]# iptables -nL --line-n
Chain INPUT (policy ACCEPT)
num target prot opt source destination
1 DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:10051
2 DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:443
3 DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
4 DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:10050
Chain FORWARD (policy ACCEPT)
num target prot opt source destination
Chain OUTPUT (policy ACCEPT)
num target prot opt source destination
删除规则
有两种方式
- 根据序号删除规则
- 根据创建规则的命令删除规则
# 当前iptables规则
[root@web01 ~]# iptables -nL --line-n
Chain INPUT (policy ACCEPT)
num target prot opt source destination
1 DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:10051
2 DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:443
3 DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
4 DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:10050
Chain FORWARD (policy ACCEPT)
num target prot opt source destination
Chain OUTPUT (policy ACCEPT)
num target prot opt source destination
# 根据创建规则的命令删除规则
[root@web01 ~]# iptables -D INPUT -p tcp --dport 10051 -j DROP
[root@web01 ~]# iptables -nL --line-n
Chain INPUT (policy ACCEPT)
num target prot opt source destination
1 DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:443
2 DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
3 DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:10050
Chain FORWARD (policy ACCEPT)
num target prot opt source destination
Chain OUTPUT (policy ACCEPT)
num target prot opt source destination
# 根据序号删除规则
[root@web01 ~]# iptables -nL --line-n
Chain INPUT (policy ACCEPT)
num target prot opt source destination
1 DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:443
2 DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
Chain FORWARD (policy ACCEPT)
num target prot opt source destination
Chain OUTPUT (policy ACCEPT)
num target prot opt source destination
封IP
禁止某个IP访问
一般会用在恶意访问,通过日志查询到在某一个时间段内的大量访问,进而禁止IP
# 清空规则
[root@web01 ~]# iptables -F
[root@web01 ~]# iptables -nL --line-num
Chain INPUT (policy ACCEPT)
num target prot opt source destination
Chain FORWARD (policy ACCEPT)
num target prot opt source destination
Chain OUTPUT (policy ACCEPT)
num target prot opt source destination
[root@web01 ~]# iptables -I INPUT -s 192.168.121.8 -j DROP
[root@web01 ~]# iptables -nL --line-num
Chain INPUT (policy ACCEPT)
num target prot opt source destination
1 DROP all -- 192.168.121.8 0.0.0.0/0
Chain FORWARD (policy ACCEPT)
num target prot opt source destination
Chain OUTPUT (policy ACCEPT)
num target prot opt source destination
[root@web02 ~]# ping 192.168.121.7
PING 192.168.121.7 (192.168.121.7) 56(84) bytes of data.
^C
--- 192.168.121.7 ping statistics ---
22 packets transmitted, 0 received, 100% packet loss, time 21502ms
# 由于机器存在两个网卡,另外一张网卡还是能访问的
[root@web02 ~]# ping 172.16.1.7
PING 172.16.1.7 (172.16.1.7) 56(84) bytes of data.
64 bytes from 172.16.1.7: icmp_seq=1 ttl=64 time=1.23 ms
^C
--- 172.16.1.7 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 1.226/1.226/1.226/0.000 ms
# 将另外一张网卡也禁止
[root@web01 ~]# iptables -I INPUT -s 172.16.1.8 -j DROP
[root@web01 ~]# iptables -nL --line-num
Chain INPUT (policy ACCEPT)
num target prot opt source destination
1 DROP all -- 172.16.1.8 0.0.0.0/0
2 DROP all -- 192.168.121.8 0.0.0.0/0
Chain FORWARD (policy ACCEPT)
num target prot opt source destination
Chain OUTPUT (policy ACCEPT)
num target prot opt source destination
[root@web02 ~]# ping 172.16.1.7
PING 172.16.1.7 (172.16.1.7) 56(84) bytes of data.
^C
--- 172.16.1.7 ping statistics ---
2 packets transmitted, 0 received, 100% packet loss, time 1055ms
禁止网段连入
# 清空规则
[root@web01 ~]# iptables -F
[root@web01 ~]# iptables -I INPUT -s 192.168.121.0/24 -p tcp --dport 80 -j DROP
[root@web01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
DROP tcp -- 192.168.121.0/24 0.0.0.0/0 tcp dpt:80
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Linux中开放监听端口
nc ncat netcat
nc -l
-l 使用监听模式,管控传入的资料
-v 显示指令执行过程。
-k 接受多个连接请求
telnet
# 首先在服务端监听5000端口
[root@web01 ~]# nc -l 5000
cccccc
# 模拟客户端访问服务器的5000端口
[C:\~]$ telnet 192.168.121.7 5000
Connecting to 192.168.121.7:5000...
Connection established.
To escape to local shell, press Ctrl+Alt+].
cccccc
通过tcpdump抓包
# 在服务端开启12345端口
[root@web01 ~]# nc -lv 12345
Ncat: Version 7.92 ( https://nmap.org/ncat )
Ncat: Listening on :::12345
Ncat: Listening on 0.0.0.0:12345
Ncat: Connection from 192.168.121.1.
Ncat: Connection from 192.168.121.1:36171.
# 在服务器端开启抓包
[root@web01 ~]# tcpdump -nni ens33 port 12345
# 在客户端进行测试
[C:\~]$ telnet 192.168.121.7 12345
Connecting to 192.168.121.7:12345...
Connection established.
To escape to local shell, press Ctrl+Alt+].
1111
# 查看数据包
15:41:00.657068 IP 192.168.121.1.36171 > 192.168.121.7.12345: Flags [.], ack 1, win 4100, length 0
15:41:06.362868 IP 192.168.121.1.36171 > 192.168.121.7.12345: Flags [P.], seq 1:5, ack 1, win 4100, length 4
15:41:06.362905 IP 192.168.121.7.12345 > 192.168.121.1.36171: Flags [.], ack 5, win 502, length 0
15:41:06.362974 IP 192.168.121.1.36171 > 192.168.121.7.12345: Flags [P.], seq 5:7, ack 1, win 4100, length 2
15:41:06.362981 IP 192.168.121.7.12345 > 192.168.121.1.36171: Flags [.], ack 7, win 502, length 0
15:42:00.637781 IP 192.168.121.1.36171 > 192.168.121.7.12345: Flags [P.], seq 7:9, ack 1, win 4100, length 2
15:42:00.637824 IP 192.168.121.7.12345 > 192.168.121.1.36171: Flags [.], ack 9, win 502, length 0
# 现在我们将12345端口禁止
[root@web01 ~]# iptables -I INPUT -p tcp --dport 12345 -j DROP
[root@web01 ~]# iptables -nL --line-num
Chain INPUT (policy ACCEPT)
num target prot opt source destination
1 DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:12345
2 DROP tcp -- 192.168.121.0/24 0.0.0.0/0 tcp dpt:80
Chain FORWARD (policy ACCEPT)
num target prot opt source destination
Chain OUTPUT (policy ACCEPT)
num target prot opt source destination
# 再重复上面的抓包操作,我们会发现所有的数据包都是单向的了
15:43:42.810012 IP 192.168.121.1.36319 > 192.168.121.7.12345: Flags [S], seq 3866319899, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
15:43:44.813165 IP 192.168.121.1.36319 > 192.168.121.7.12345: Flags [S], seq 3866319899, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
15:43:48.817855 IP 192.168.121.1.36319 > 192.168.121.7.12345: Flags [S], seq 3866319899, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
只允许指定网段连入
实现阿里云白名单功能 :默认是拒绝所有 开放端口 网段
allow 10.0.0.0/24;
deny all;
有两种方式
- 利用 ! 进行排除
- 修改链默认规则 修改为拒绝 添加准许
# 利用 ! 进行排除
[root@web01 ~]# iptables -I INPUT ! -s 192.168.121.0/24 -j DROP
[root@web01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
DROP all -- !192.168.121.0/24 0.0.0.0/0
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
# 修改链默认规则 修改为拒绝 添加准许
先配置好规则 准许规则
修改默认规则为拒绝所有
# 清空规则
[root@web01 ~]# iptables -F
[root@web01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
# 设置准许规则
[root@web01 ~]# iptables -I INPUT -s 192.168.121.1 -j ACCEPT
[root@web01 ~]# iptables
[root@web01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 192.168.121.1 0.0.0.0/0
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
# 设置默认规则为DROP
[root@web01 ~]# iptables -P INPUT DROP
[root@web01 ~]# iptables -nL
Chain INPUT (policy DROP)
target prot opt source destination
ACCEPT all -- 192.168.121.1 0.0.0.0/0
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
# 测试完成后修改默认规则为ACCEPT
[root@web01 ~]# iptables -P INPUT ACCEPT
[root@web01 ~]#
[root@web01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 192.168.121.1 0.0.0.0/0
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
指定多个端口
如果多个端口之间是连续的,那么可以直接通过 : 连接
如果多个端口之间不连续,需要引入multiport模块
[root@web01 ~]# iptables -I INPUT -p tcp --dport 10000:20000 -j DROP
[root@web01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpts:10000:20000
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@web01 ~]# iptables -I INPUT -p tcp -m multiport --dport 80,443 -j DROP
[root@web01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
DROP tcp -- 0.0.0.0/0 0.0.0.0/0 multiport dports 80,443
DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpts:10000:20000
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
匹配ICMP类型
- ICMP(Internet Control Message Protocol)Internet控制报文协议 ping
- 整个网站核心
- icmp类型
- 0:回显应答,表示回显自己对别人的请求,自己ping别人
- 8:回显请求,表示回显别人对自己的请求,别人ping自己
通过防火墙规则 控制是否可以ping
[root@web01 ~]# iptables -I INPUT -p icmp --icmp-type 8 -j DROP
[root@web01 ~]# iptables -nL --line-num
Chain INPUT (policy ACCEPT)
num target prot opt source destination
1 DROP icmp -- 0.0.0.0/0 0.0.0.0/0 icmptype 8
2 DROP tcp -- 0.0.0.0/0 0.0.0.0/0 multiport dports 80,443
3 DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpts:10000:20000
Chain FORWARD (policy ACCEPT)
num target prot opt source destination
Chain OUTPUT (policy ACCEPT)
num target prot opt source destination
# icmp类型8允许我ping别人,不能让别人ping我
[root@web01 ~]# ping 192.168.121.8
PING 192.168.121.8 (192.168.121.8) 56(84) bytes of data.
64 bytes from 192.168.121.8: icmp_seq=1 ttl=64 time=0.612 ms
64 bytes from 192.168.121.8: icmp_seq=2 ttl=64 time=0.488 ms
^C
--- 192.168.121.8 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1005ms
rtt min/avg/max/mdev = 0.488/0.550/0.612/0.062 ms
[root@web02 ~]# ping 192.168.121.7
PING 192.168.121.7 (192.168.121.7) 56(84) bytes of data.
^C
--- 192.168.121.7 ping statistics ---
2 packets transmitted, 0 received, 100% packet loss, time 1011ms
也可以通过Linux的内核参数来管理是否可以被ping
[root@web01 ~]# cat /proc/sys/net/ipv4/icmp_echo_ignore_all
0
# net.ipv4.icmp_echo_ignore_all=1 写入到 /etc/sysctl.conf
[root@web01 ~]# tail -1 /etc/sysctl.conf
net.ipv4.icmp_echo_ignore_all=1
sysctl -p
[root@web01 ~]# cat /proc/sys/net/ipv4/icmp_echo_ignore_all
1
0:可以被ping
1:不能被ping
匹配网络状态(TCP连接状态)
-m state --state
NEW:已经或将启动新的连接
ESTABLISHED:已建立的连接
RELATED:正在启动的新连接
INVALID:非法或无法识别的
iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
iptables -A OUTPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
限制并发及速率
-m limit 限制模块
-m limit --limit 10/minute #每分钟只能有10个数据包 每6秒生成
-m limit --limit n/{second/minute/hour}:
解释:指定时间内的请求速率”n”为速率,后面为时间分别为:秒 分 时
-m limit --limit 10/minute --limit-burst 5 每6秒释放工牌 给别人使用
#10个数据包
前5个 1s1个工牌 从第6个开始 每6秒 才能释放1个工牌
--limit-burst [n]
解释:在同一时间内允许通过的请求”n”为数字,不指定默认为5
- 测试 演示
#ping icmp 协议 进行测试
iptables -F
iptables -I INPUT -p icmp -m limit --limit 10/minute --limit-burst 5 -j ACCEPT
iptables -A INPUT -p tcp --dport 22 -j ACCEPT
iptables -P INPUT DROP

- web01 进行ping测试
ping 10.0.0.61
[root@web01 ~]# ping 10.0.0.61
PING 10.0.0.61 (10.0.0.61) 56(84) bytes of data.
64 bytes from 10.0.0.61: icmp_seq=1 ttl=64 time=0.240 ms
64 bytes from 10.0.0.61: icmp_seq=2 ttl=64 time=0.376 ms
64 bytes from 10.0.0.61: icmp_seq=3 ttl=64 time=0.474 ms
64 bytes from 10.0.0.61: icmp_seq=4 ttl=64 time=0.693 ms
64 bytes from 10.0.0.61: icmp_seq=5 ttl=64 time=2.43 ms
64 bytes from 10.0.0.61: icmp_seq=7 ttl=64 time=0.351 ms #7与1比 就是间隔6秒
64 bytes from 10.0.0.61: icmp_seq=13 ttl=64 time=0.869 ms #7 13 间隔6秒
64 bytes from 10.0.0.61: icmp_seq=19 ttl=64 time=0.482 ms
64 bytes from 10.0.0.61: icmp_seq=25 ttl=64 time=0.378 ms
64 bytes from 10.0.0.61: icmp_seq=31 ttl=64 time=0.329 ms
64 bytes from 10.0.0.61: icmp_seq=37 ttl=64 time=0.857 ms
64 bytes from 10.0.0.61: icmp_seq=43 ttl=64 time=0.314 ms
64 bytes from 10.0.0.61: icmp_seq=49 ttl=64 time=0.360 ms
64 bytes from 10.0.0.61: icmp_seq=55 ttl=64 time=0.349 ms
64 bytes from 10.0.0.61: icmp_seq=61 ttl=64 time=0.552 ms
64 bytes from 10.0.0.61: icmp_seq=67 ttl=64 time=0.283 ms
64 bytes from 10.0.0.61: icmp_seq=73 ttl=64 time=0.407 ms
64 bytes from 10.0.0.61: icmp_seq=79 ttl=64 time=0.297 ms
64 bytes from 10.0.0.61: icmp_seq=85 ttl=64 time=0.428 ms
64 bytes from 10.0.0.61: icmp_seq=91 ttl=64 time=0.390 ms
64 bytes from 10.0.0.61: icmp_seq=97 ttl=64 time=0.691 ms
64 bytes from 10.0.0.61: icmp_seq=103 ttl=64 time=0.537 ms
64 bytes from 10.0.0.61: icmp_seq=109 ttl=64 time=0.546 ms
64 bytes from 10.0.0.61: icmp_seq=115 ttl=64 time=0.382 ms
64 bytes from 10.0.0.61: icmp_seq=121 ttl=64 time=0.337 ms
防火墙规则的保存与恢复
- iptables-save 默认输出到屏幕
- iptables-restore < iptables规则文件
- 写入到/etc/sysconfig/iptables
# 保存
[root@web01 ~]# iptables-save > /etc/sysconfig/iptables
# 恢复
[root@web01 ~]# iptables-restore < /etc/sysconfig/iptables
filter表的实际用法
- iptables配置方式
- 逛公园模式: 默认规则是 ACCEPT
- 看电影模式: 默认规则是 DROP
- 默认是拒绝 去电影院
准许ssh接入
[root@web01 ~]# iptables -F
[root@web01 ~]#
[root@web01 ~]#
[root@web01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@web01 ~]# iptables -I INPUT -p tcp --dport 22 -j ACCEPT
[root@web01 ~]# iptables -nL --line-num
Chain INPUT (policy ACCEPT)
num target prot opt source destination
1 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
Chain FORWARD (policy ACCEPT)
num target prot opt source destination
Chain OUTPUT (policy ACCEPT)
num target prot opt source destination
允许本机lo口的规则
# 允许本机回环lo接口数据流量流出与流入
iptables -A INPUT -i lo -j ACCEPT
iptables -A OUTPUT -o lo -j ACCEPT
配置默认规则及 放行 80 443端口
[root@m01 ~]# iptables -P INPUT DROP
[root@m01 ~]# iptables -P FORWARD DROP
[root@m01 ~]# iptables -P OUTPUT ACCEPT
[root@m01 ~]# iptables -A INPUT -m multiport -p tcp --dport 443,80 -j ACCEPT
[root@m01 ~]# iptables -nL
Chain INPUT (policy DROP)
target prot opt source destination
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 multiport dports 443,80
Chain FORWARD (policy DROP)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
[root@m01 ~]# iptables -A INPUT -s 10.0.0.0/24 -j ACCEPT
[root@m01 ~]# iptables -A INPUT -s 172.16.1.0/24 -j ACCEPT
#此处还可以添加 vpn网段 比如说 10.7.1.0/24
[root@m01 ~]# iptables -nL
Chain INPUT (policy DROP)
target prot opt source destination
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 multiport dports 443,80
ACCEPT all -- 10.0.0.0/24 0.0.0.0/0
ACCEPT all -- 172.16.1.0/24 0.0.0.0/0
Chain FORWARD (policy DROP)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
[root@m01 ~]# iptables-save
# Generated by iptables-save v1.4.21 on Wed Jul 24 23:42:00 2019
*filter
:INPUT DROP [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [24:3008]
-A INPUT -p tcp -m tcp --dport 22 -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -p tcp -m multiport --dports 443,80 -j ACCEPT
-A INPUT -s 10.0.0.0/24 -j ACCEPT
-A INPUT -s 172.16.1.0/24 -j ACCEPT
-A OUTPUT -o lo -j ACCEPT
COMMIT
# Completed on Wed Jul 24 23:42:00 2019
保存和恢复规则
iptables-save > /etc/sysconfig/iptables
iptables-restore < /etc/sysconfig/iptables
配置NAT表
- 共享上网
- 端口转发/端口映射
- ip映射
SNAT:我们访问外网
DNAT:目标地址转换,用户通过访问路由器的公网IP,转发到内网服务器上
实现共享上网
DNAT
我们将web02的公网网卡关掉,此时只有内网网卡了,是无法访问外网的,我们可以给内网网卡设置网关,然后给web01的iptables设置规则
同时开启内核转发功能
防火墙配置
# nat表的默认规则
[root@web01 ~]# iptables -t nat -nL --line-num
Chain PREROUTING (policy ACCEPT)
num target prot opt source destination
Chain INPUT (policy ACCEPT)
num target prot opt source destination
Chain OUTPUT (policy ACCEPT)
num target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
num target prot opt source destination
[root@web01 ~]# iptables -t nat -I POSTROUTING -s 172.16.1.8 -j SNAT --to-source 192.168.121.7
[root@web01 ~]# iptables -t nat -nL --line-num
Chain PREROUTING (policy ACCEPT)
num target prot opt source destination
Chain INPUT (policy ACCEPT)
num target prot opt source destination
Chain OUTPUT (policy ACCEPT)
num target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
num target prot opt source destination
1 SNAT all -- 172.16.1.8 0.0.0.0/0 to:192.168.121.7
关闭网卡
[root@web02 ~]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:0c:29:85:61:90 brd ff:ff:ff:ff:ff:ff
3: ens36: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:0c:29:85:61:9a brd ff:ff:ff:ff:ff:ff
inet 172.16.1.8/24 brd 172.16.1.255 scope global noprefixroute ens36
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe85:619a/64 scope link
valid_lft forever preferred_lft forever
# 设置网关,dns
[root@web02 ~]# nmcli connection modify ens36 ipv4.gateway 172.16.1.7 ipv4.dns 114.114.114.114
[root@web02 ~]# nmcli connection reload
[root@web02 ~]# nmcli connection up ens36
Connection successfully activated (D-Bus active path: /org/freedesktop/NetworkManager/ActiveConnection/5)
开启路由转发
[root@web01 ~]# echo 'net.ipv4.ip_forward = 1' >> /etc/sysctl.conf
[root@web01 ~]# sysctl -p
# 测试
[root@web02 ~]# ping www.baidu.com
PING www.a.shifen.com (220.181.38.149) 56(84) bytes of data.
64 bytes from 220.181.38.149 (220.181.38.149): icmp_seq=1 ttl=127 time=19.6 ms
64 bytes from 220.181.38.149 (220.181.38.149): icmp_seq=2 ttl=127 time=20.4 ms
如果公网IP不固定
假如使用的ASDL拨号上网,每一个的公网IP是不固定的,我们就不能使用--to-source参数去指定确定的公网IP
iptables -t nat -A POSTROUTING -s 172.16.1.0/24 -j MASQUERADE
实现端口转发
这里的端口转发也就是我们说的SNAT,和四层负载类似
[root@web01 ~]# iptables -t nat -I PREROUTING -d 192.168.121.7 -p tcp --dport 9000 -j DNAT --to-destination 172.16.1.8:22
[root@web01 ~]# iptables -t nat -nL --line-num
Chain PREROUTING (policy ACCEPT)
num target prot opt source destination
1 DNAT tcp -- 0.0.0.0/0 192.168.121.7 tcp dpt:9000 to:172.16.1.8:22
Chain INPUT (policy ACCEPT)
num target prot opt source destination
Chain OUTPUT (policy ACCEPT)
num target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
num target prot opt source destination
1 SNAT all -- 172.16.1.8 0.0.0.0/0 to:192.168.121.7
C:\Users\HP-MY>ssh root@192.168.121.7 -P 9999
Authorized users only. All activities may be monitored and reported.
root@192.168.121.7's password:
Authorized users only. All activities may be monitored and reported.
Activate the web console with: systemctl enable --now cockpit.socket
Last login: Fri Jan 17 16:37:18 2025 from 192.168.121.1
[root@web01 ~]#
实现IP映射
[root@m01 ~]# iptables -t nat -A PREROUTING -d 10.0.0.62 -j DNAT --to-destination 172.16.1.7
[root@m01 ~]# iptables -nL -t nat
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
DNAT tcp -- 0.0.0.0/0 10.0.0.61 tcp dpt:9000 to:172.16.1.7:22
DNAT all -- 0.0.0.0/0 10.0.0.62 to:172.16.1.7
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
SNAT all -- 172.16.1.0/24 0.0.0.0/0 to:10.0.0.61
本文来自博客园,作者:Linux小菜鸟,转载请注明原文链接:https://www.cnblogs.com/xuruizhao/p/18689766


 浙公网安备 33010602011771号
浙公网安备 33010602011771号