Frida反调试与脱壳
方法一
1.启动frida服务
adb shell
su
./frida-server-16.0.19-android-arm64
2.转发端口
cmd
adb forward tcp:27042 tcp:27042
adb forward tcp:27043 tcp:27043
python代码
import subprocess subprocess.getoutput("adb forward tcp:27042 tcp:27042") subprocess.getoutput("adb forward tcp:27043 tcp:27043")
3.运行frida进行hook
import frida import sys rdev = frida.get_remote_device() pid = rdev.spawn(["com.shizhuang.duapp"]) session = rdev.attach(pid) scr = """ Java.perform(function () { var dlopen = Module.findExportByName(null, "dlopen"); var android_dlopen_ext = Module.findExportByName(null, "android_dlopen_ext"); Interceptor.attach(dlopen, { onEnter: function (args) { var path_ptr = args[0]; var path = ptr(path_ptr).readCString(); console.log("[dlopen:]", path); }, onLeave: function (retval) { } }); Interceptor.attach(android_dlopen_ext, { onEnter: function (args) { var path_ptr = args[0]; var path = ptr(path_ptr).readCString(); console.log("[dlopen_ext:]", path); }, onLeave: function (retval) { } }); }); """ script = session.create_script(scr) def on_message(message, data): print(message, data) script.on("message", on_message) script.load() rdev.resume(pid) sys.stdin.read()
运行结果如图所示:
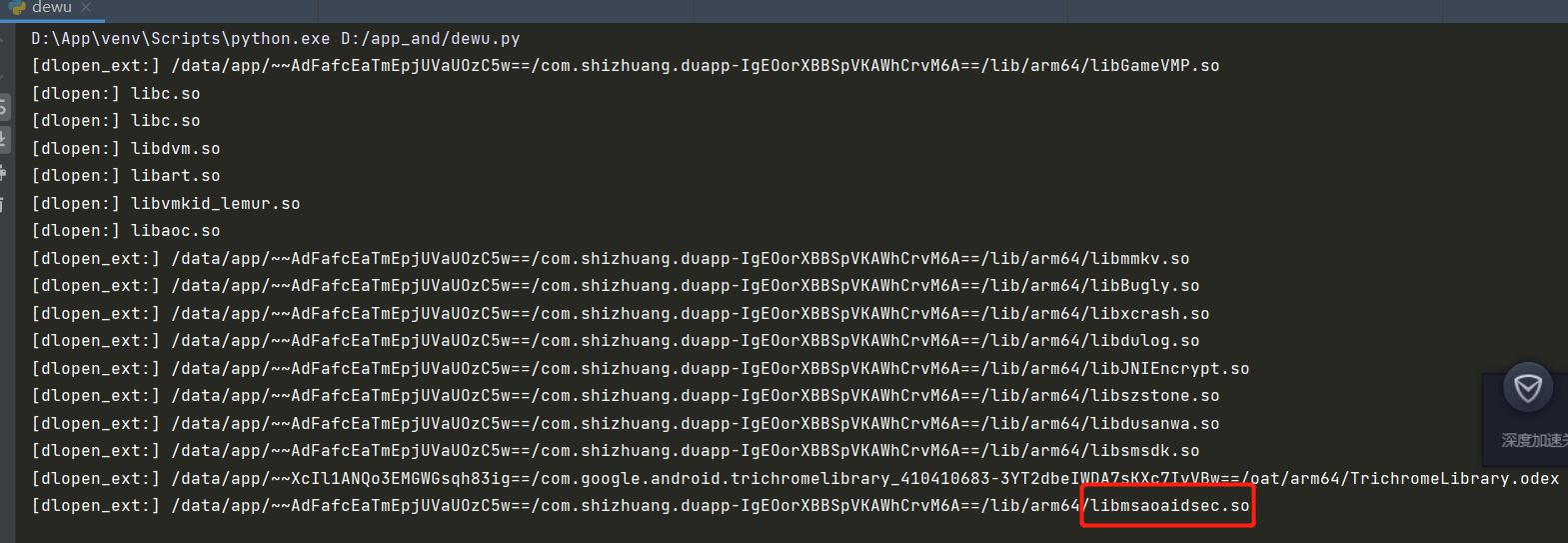
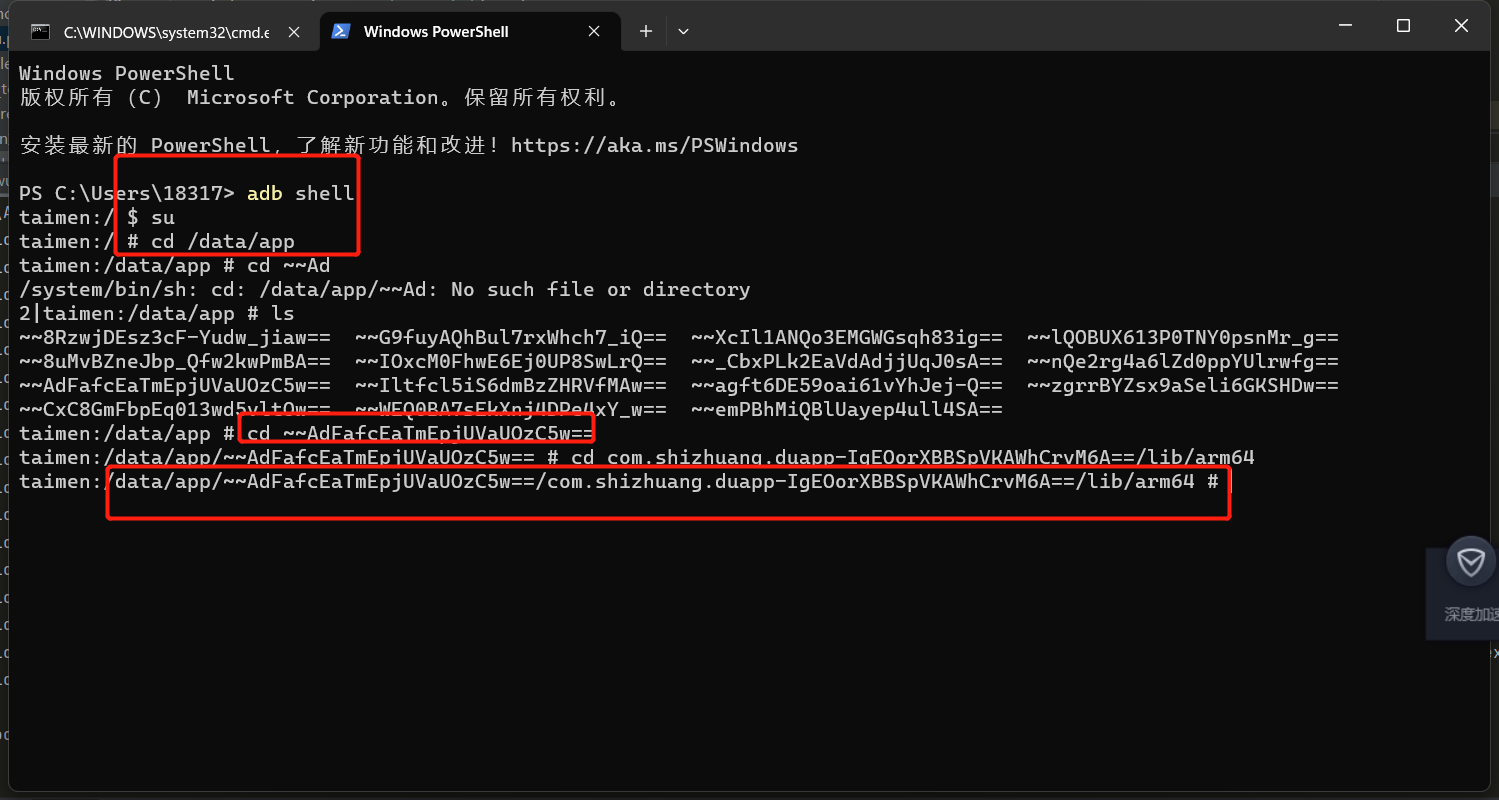
在终端找到如图所示哪个路径,删除 libmsaoaidsec.so
方法二
有些app运行时会监测frida的相关特征,监测到之后就会直接闪退。
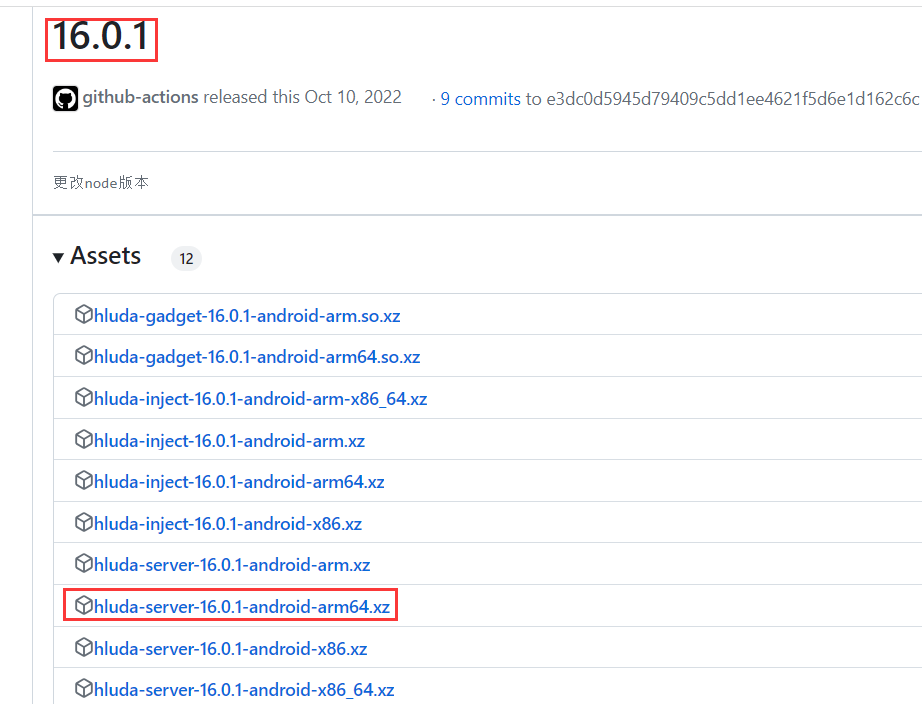
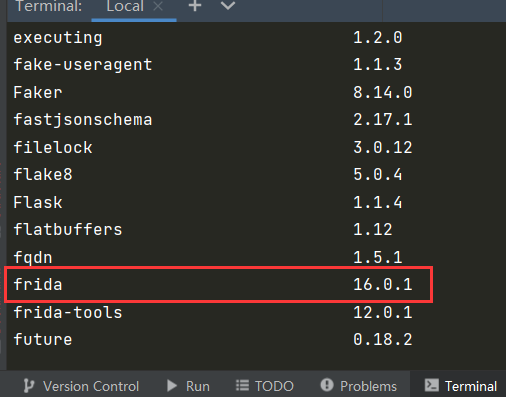
上传
>>>adb push C:\soft\frida-server-16.0.1-arm64 /data/local/tmp/
赋予可执行权限
>>>adb shell >>>su >>>cd /data/local/tmp/ >>>chmod 755 frida-server-16.0.1-android-arm64
脱壳
下载模块
pip install frida-dexdump
-
-
电脑端
-
端口转发
-
-
frida-dexdump -U -f 包名称
-
脱壳后,会生成相应的dex文件,例如:
frida-dexdump -U -f com.jiuxianapk.ui
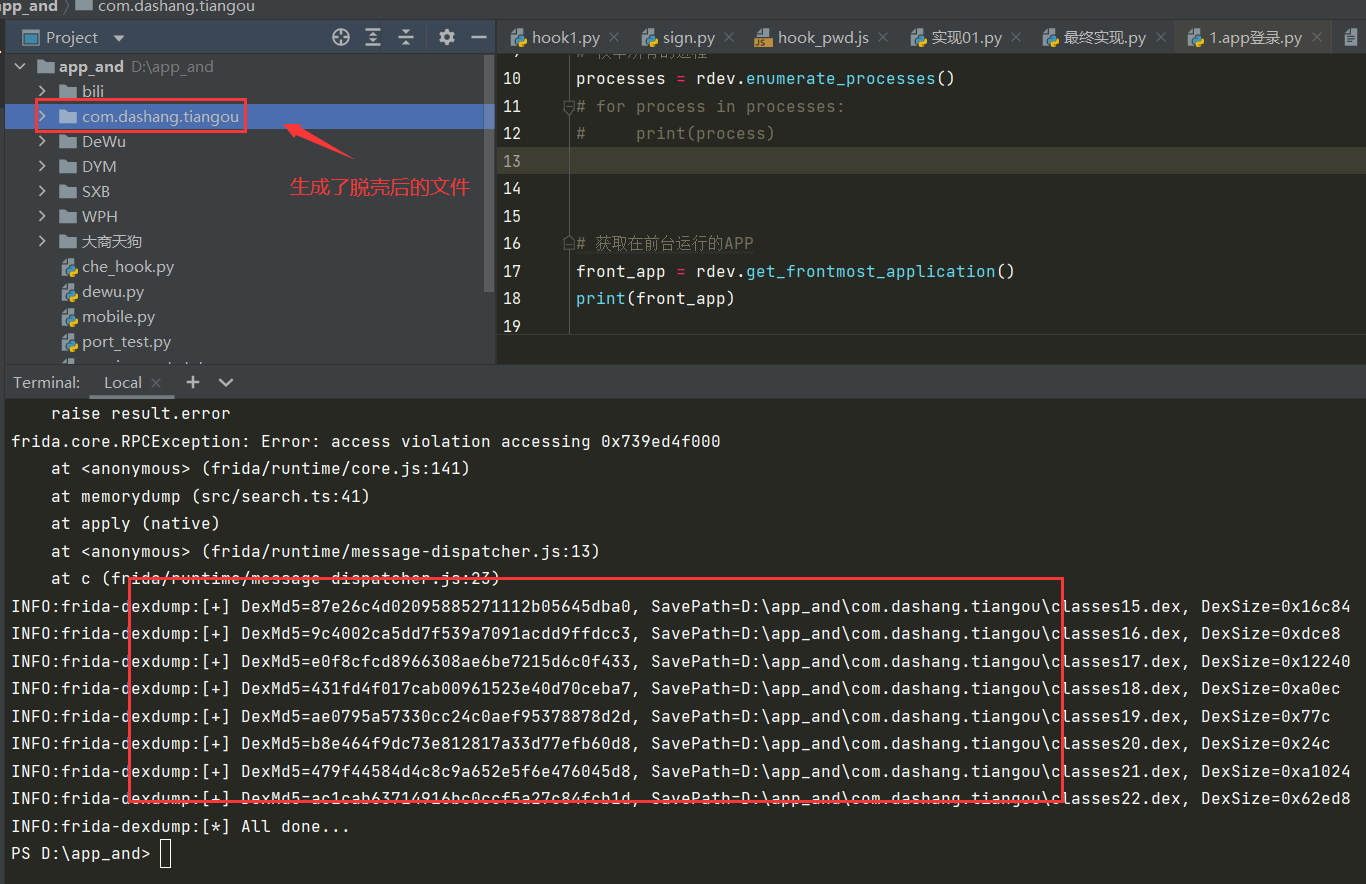
然后将该文件拖入运行的jadx中反编译即可

 浙公网安备 33010602011771号
浙公网安备 33010602011771号