1、step-certificates安装
helm repo add smallstep https://smallstep.github.io/helm-charts
helm repo update
helm repo list smallstep
helm pull repo smallstep/step-certificates --version 1.27.4 --untar
cd step-certificates/
# values.yaml中找到ca这一段
ca:
name: Step Certificates
address: :9000
dns:
url:
password: "xxx" # 填写上去
provisioner:
name: admin
password: "xxx" # 填写上去
db:
enabled: true
persistent: true
storageClass: nfs-data # 填写自己的存储类
bootstrap: # 这个是关键点一定要去添加,将type改为acme,可为服务自动签发证书
postInitHook: |
set -e
step ca provisioner list | grep -q '"type": "ACME"' || step ca provisioner add acme --type ACME
# 安装后检查一下
helm install -n step-certificates -n step-certificates -f values.yaml .
[root@master-11 step-certificates]# kubectl get pods -n step-certificates
NAME READY STATUS RESTARTS AGE
step-certificates-0 1/1 Running 0 83m
step-certificates-srhxk 0/1 Completed 0 85m
2、验证是否开启acme
[root@master-11 step-certificates]# kubectl exec -it -n step-certificates step-certificates-0 bash
kubectl exec [POD] [COMMAND] is DEPRECATED and will be removed in a future version. Use kubectl exec [POD] -- [COMMAND] instead.
Defaulted container "step-certificates" out of: step-certificates, step-certificates-init (init)
step-certificates-0:~$ cat /home/step/config/ca.json
{
"root": "/home/step/certs/root_ca.crt",
"federatedRoots": null,
"crt": "/home/step/certs/intermediate_ca.crt",
"key": "/home/step/secrets/intermediate_ca_key",
"address": ":9000",
"insecureAddress": "",
"dnsNames": [
"step-certificates.step-certificates.svc.cluster.local",
"127.0.0.1"
],
"logger": {
"format": "text"
},
"db": {
"type": "badgerv2",
"dataSource": "/home/step/db",
"badgerFileLoadingMode": ""
},
"authority": {
"provisioners": [
{
"type": "JWK",
"name": "admin",
"key": {
"use": "sig",
"kty": "EC",
"kid": "Y9FZxuw-UEdPp0b-DZRuBMWNblRpE0e1qrhI_mGNsF0",
"crv": "P-256",
"alg": "ES256",
"x": "6QJLOU7mpMoSN_sTtbwNfH0okax6NAdNf5I-r_YG7E0",
"y": "mhm3j6XnFZQfJvFC1BihuoCZSEnfBtsdmVWfMhFctWE"
},
"encryptedKey": "eyJhbGciOiJQQkVTMi1IUzI1NitBMTI4S1ciLCJjdHkiOiJqd2sranNvbiIsImVuYyI6IkEyNTZHQ00iLCJwMmMiOjEwMDAwMCwicDJzIjoiekVYU1lTVUhQcGN0cUtIcWtCSHYyUSJ9.wJtdmKL28QP9kAKkAnjJa-Qdm6B27irxiY390JZQMbnddNnSKvYsWA.f_adssoq7-evDpUy.E4uXy8wYCczeChU260_9GlV4Pr2515FMnj7hpFiZEmnunTh5exSrX4pNtlulUI10KwKm1YPTSRTKd6TzCCgRJTPrR9H2Guy9J_0z9Q2MQkeASMGc7qodFtBJtqrGWGmoGfWYWteGAEQ9DzHpeQKZ5mrbIy3Gar3xyurVd65-s08Cjoqazz6Ndu6fhrE6FXhsijxgicuMNqo9JB-jj27bqzjKql7vH97b-vIuR6YHdlHNxlFu4A0GHck8P5FJv2jBorHkrk-62utKBCkrnu2wyI0Izn99OC-1LZuAGeUXAs7BtEJt5yaAD_GFvV7S_Vx1l8U-Nen3f5DlNttIPOI.FvPV28uv5n1VQ33o6AivkA"
},
{
"type": "ACME", # 确保这个地方是ACME就行
"name": "acme",
"claims": {
"enableSSHCA": true,
"disableRenewal": false,
"allowRenewalAfterExpiry": false
},
"options": {
"x509": {},
"ssh": {}
}
}
],
"template": {},
"backdate": "1m0s"
},
"tls": {
"cipherSuites": [
"TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256",
"TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256"
],
"minVersion": 1.2,
"maxVersion": 1.3,
"renegotiation": false
},
"commonName": "Step Online CA"
}
# 检查一下svc的端口
[root@master-11 step-certificates]# kubectl get svc -n step-certificates # 看他是443还是9000
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
step-certificates ClusterIP 10.200.103.10 <none> 443/TCP 88m
3、更改traefik的配置,让step-certificates去自动申请证书
# values.yaml 我的traefik是使用helm安装的
certificatesResolvers: {}
additionalArguments: # 将下面这一段加上,这个 --certificatesresolvers.stepca.acme.caserver后的地址是svc形式的地址,按你实际的来修改,注意端口是443还是9000
- "--certificatesresolvers.stepca.acme.caserver=https://step-certificates.step-certificates.svc.cluster.local:443/acme/acme/directory"
- "--certificatesresolvers.stepca.acme.email=admin@example.com"
- "--certificatesresolvers.stepca.acme.storage=/data/acme.json"
- "--certificatesresolvers.stepca.acme.tlschallenge=true"
- "--serversTransport.insecureSkipVerify=true"
# -- If hostNetwork is true, runs traefik in the host network namespace
# To prevent unschedulable pods due to port collisions, if hostNetwork=true
# and replicas>1, a pod anti-affinity is recommended and will be set if the
# affinity is left as default.
hostNetwork: false
ports:
websecure:
tls:
enabled: true
options: ""
certResolver: "stepca" # 将这个加上
domains: []
# 随后更新一下traefik的配置,root_ca.crt可以拿出来给windows安装上
[root@master-11 ~]# kubectl exec -it -n step-certificates step-certificates-0 bash
kubectl exec [POD] [COMMAND] is DEPRECATED and will be removed in a future version. Use kubectl exec [POD] -- [COMMAND] instead.
Defaulted container "step-certificates" out of: step-certificates, step-certificates-init (init)
step-certificates-0:~$ ls /home/step/certs/root_ca.crt
/home/step/certs/root_ca.crt
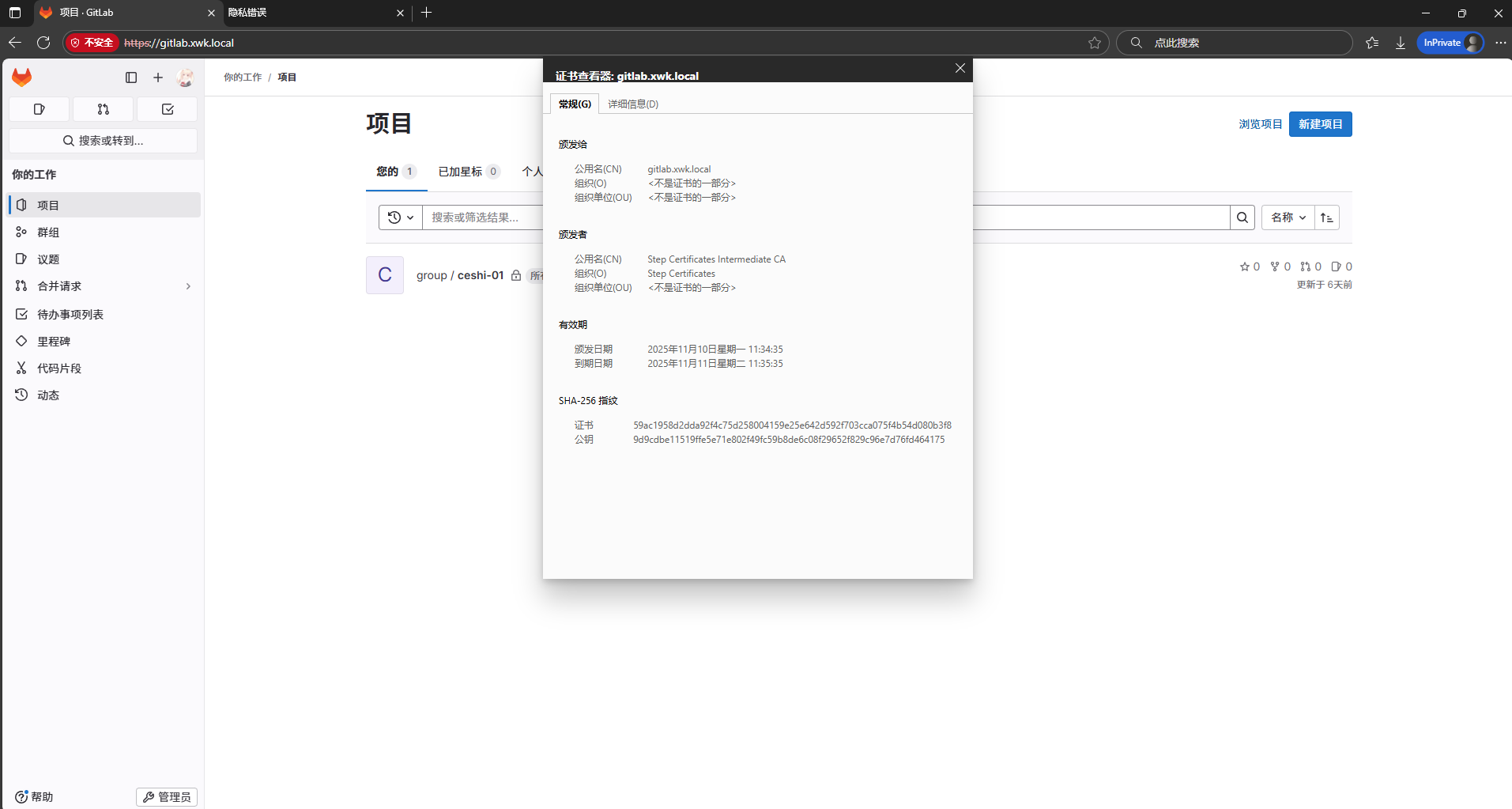
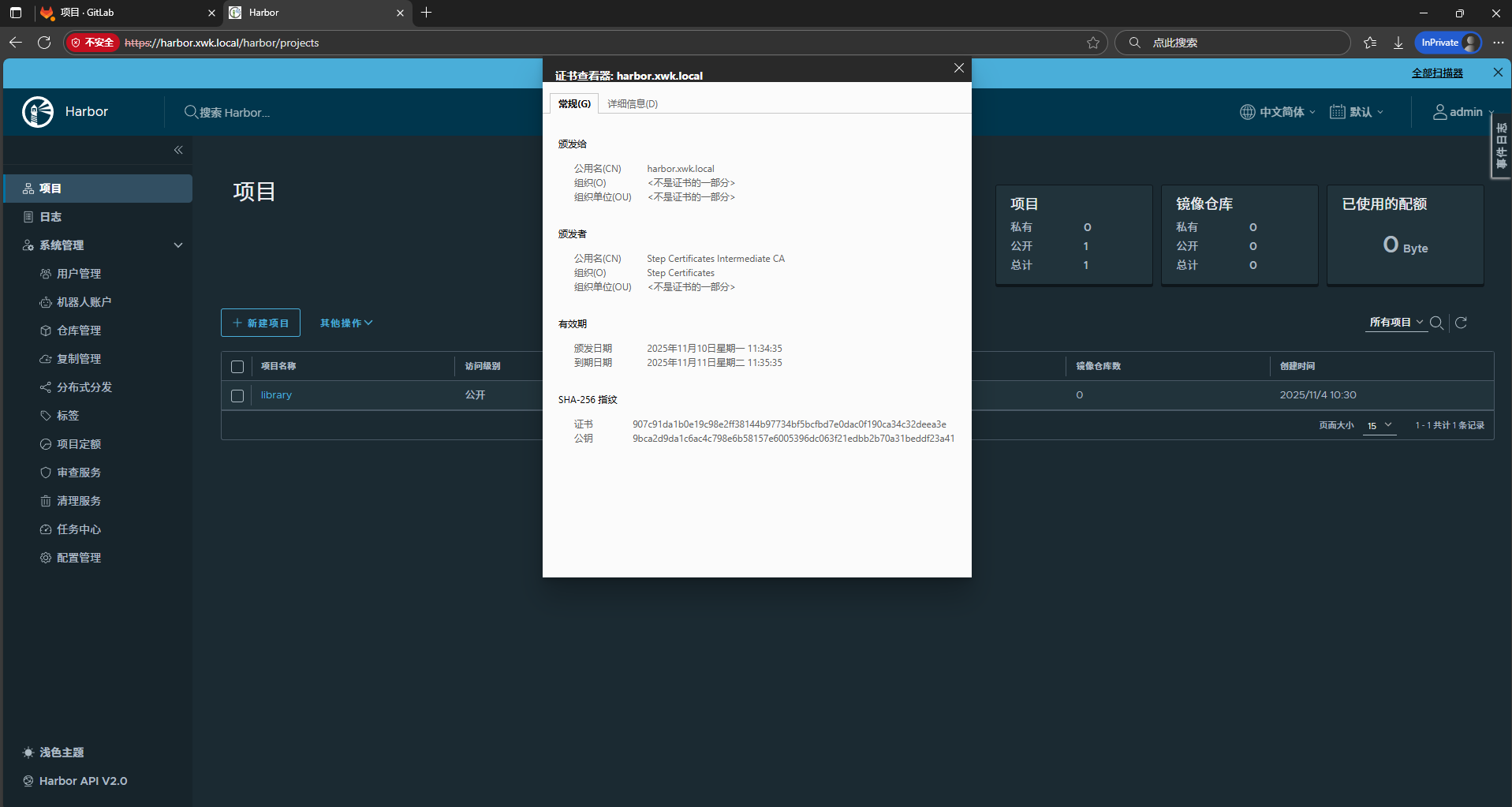
4、拿gitlab和harbor尝试
# 这个是gitlab的ingressroute
apiVersion: traefik.io/v1alpha1
kind: IngressRoute
metadata:
name: gitlab-https
namespace: gitlab
spec:
entryPoints:
- websecure
routes:
- kind: Rule
match: Host(`gitlab.xwk.local`)
services:
- name: svc-gitlab
port: 80
scheme: http
tls:
certResolver: stepca 在这个地方将加上这么一段
# 运行后访问服务查看traefik的日志会不会出现关于证书的报错,如果报了错很可能是因为之前遗留了ingressroute,或者是您的secretName忘记删掉了,导致访问时又去找你老的secret,如果你之前使用过默认的TLSStore/静态证书记得删掉
# harbor服务,helm部署
# values.yaml
# 找到所有的secretName把后面全部留空
expose:
ingress:
annotations: # 将下面这5段全部加上
kubernetes.io/ingress.class: traefik
traefik.ingress.kubernetes.io/router.entrypoints: websecure # 定义websecure 的入口点
traefik.ingress.kubernetes.io/router.tls: "true"
traefik.ingress.kubernetes.io/router.tls.certresolver: stepca # 指定 ACME 证书解析器为stepca
traefik.ingress.kubernetes.io/redirect-entry-point: websecure # 重定向到https
notary:
# notary ingress-specific annotations
annotations: {}
# notary ingress-specific labels
labels: {}
# 更新后访问服务查看traefik的日志会不会出现关于证书的报错,要是有错误就检查一下是否又遗留了secretName忘记删掉了,看看ingress是不是正确的
[root@master-11 harbor]# kubectl get ingresses.networking.k8s.io -n harbor harbor-ingress -oyaml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
annotations:
kubernetes.io/ingress.class: traefik
meta.helm.sh/release-name: harbor
meta.helm.sh/release-namespace: harbor
traefik.ingress.kubernetes.io/redirect-entry-point: websecure
traefik.ingress.kubernetes.io/router.entrypoints: websecure
traefik.ingress.kubernetes.io/router.tls: "true"
traefik.ingress.kubernetes.io/router.tls.certresolver: stepca # 看看这个在不在
········
········
spec:
ingressClassName: traefik
rules:
- host: harbor.xwk.local
http:
paths:
- backend:
service:
name: harbor-core
port:
number: 80
·······
·······
·······
tls:
- hosts:
- harbor.xwk.local
·······
·······




 浙公网安备 33010602011771号
浙公网安备 33010602011771号