攻防世界-lgniteMe
放进IDA里,然后看看伪代码,注意到几个关键的地方
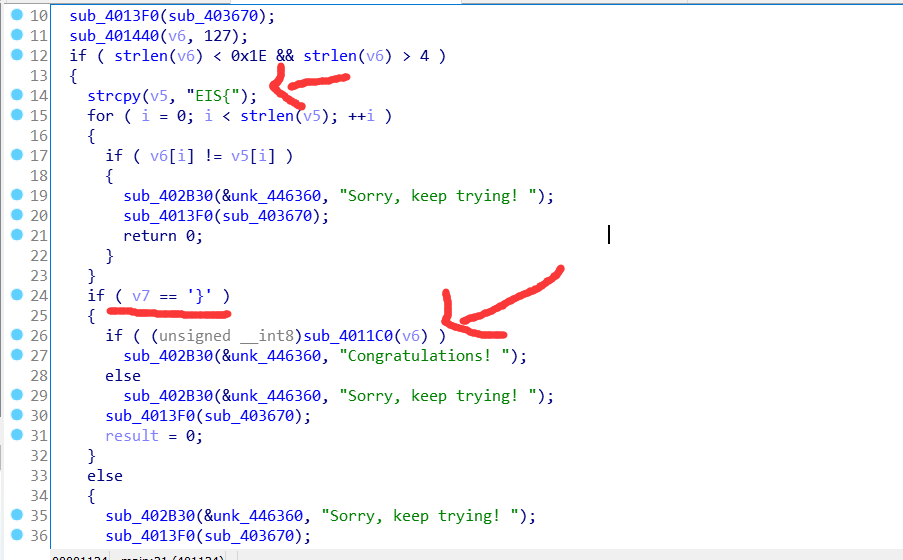
所以flag应该是EIS{}的形式,接着看看congratulations上面的if,里面的4011C0函数
bool __cdecl sub_4011C0(char *a1)
{
size_t v2; // eax
signed int v3; // [esp+50h] [ebp-B0h]
char v4[32]; // [esp+54h] [ebp-ACh]
int v5; // [esp+74h] [ebp-8Ch]
int v6; // [esp+78h] [ebp-88h]
size_t i; // [esp+7Ch] [ebp-84h]
char v8[128]; // [esp+80h] [ebp-80h]
if ( strlen(a1) <= 4 )
return 0;
i = 4;
v6 = 0;
while ( i < strlen(a1) - 1 )
v8[v6++] = a1[i++];
v8[v6] = 0;
v5 = 0;
v3 = 0;
memset(v4, 0, 0x20u);
for ( i = 0; ; ++i )
{
v2 = strlen(v8);
if ( i >= v2 )
break;
if ( v8[i] >= 'a' && v8[i] <= 'z' )
{
v8[i] -= 32;
v3 = 1;
}
if ( !v3 && v8[i] >= 'A' && v8[i] <= 'Z' )
v8[i] += 32;
v4[i] = byte_4420B0[i] ^ sub_4013C0(v8[i]);
v3 = 0;
}
return strcmp("GONDPHyGjPEKruv{{pj]X@rF", v4) == 0;
}
可以看到,应该是对v8首先大写字母转小写,小写字母转大写,接着对v8进行sub_4013C0这个函数操作,再进行异或放入v4中,再进行比较
int __cdecl sub_4013C0(int a1)
{
return (a1 ^ 0x55) + 72;
}
至于byte_4420B0[i]
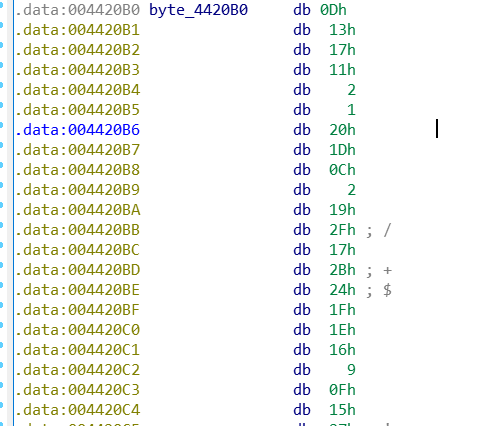
byt=[0x0d,0x13,0x17,0x11,0x2,0x1,0x20,0x1d,0x0c,0x2,0x19,0x2f,0x17,0x2b,0x24,0x1f,0x1e,0x16,0x9,0x0f,0x15,0x27,0x13,0x26,0x0a,0x2f,0x11,0x1a,0x2d,0x0c,0x22,0x4]
所以要还原v8,只需要对"GONDPHyGjPEKruv{{pj]X@rF"这个字符串进行逆向操作就可以了
用python写一下写的很乱
s=['G','O','N','D','P','H','y','G','j','P','E','K','r','u','v','{','{','p','j',']','X','@','r','F']
byt=[0x0d,0x13,0x17,0x11,0x2,0x1,0x20,0x1d,0x0c,0x2,0x19,0x2f,0x17,0x2b,0x24,0x1f,0x1e,0x16,0x9,0x0f,0x15,0x27,0x13,0x26,0x0a,0x2f,0x11,0x1a,0x2d,0x0c,0x22,0x4]
print(len(byt))
print(len(s))
for i in range(24):
s[i]=ord(s[i])^byt[i]
s[i]-=72
s[i]=s[i]^0x55
print(chr(s[i]),end="")
print(s)
#unknowstr=['J', '\', 'Y' , 'U' , 'R' , 'I' ,'Y','Z','f','R','\','d','e','^','R','d','e','f','c','R','M','g','a','`']
#print(unknowstr)
ununstr=[87, 65, 68, 88, 95, 84, 68, 71, 75, 95, 65, 73, 72, 67, 95, 73, 72, 75, 78, 95, 80, 74, 76, 77]
uninstr=""
for i in range(24):
uninstr+=chr(ununstr[i])
for j in range(24):
print(chr(s[i]),end="")
print(uninstr)
a="WADX_TDGK_AIHC_IHKN_PJLM"
a=a.lower()
print(a)
最后加上EIS{}

 浙公网安备 33010602011771号
浙公网安备 33010602011771号