k8s集群的扩容实战案例
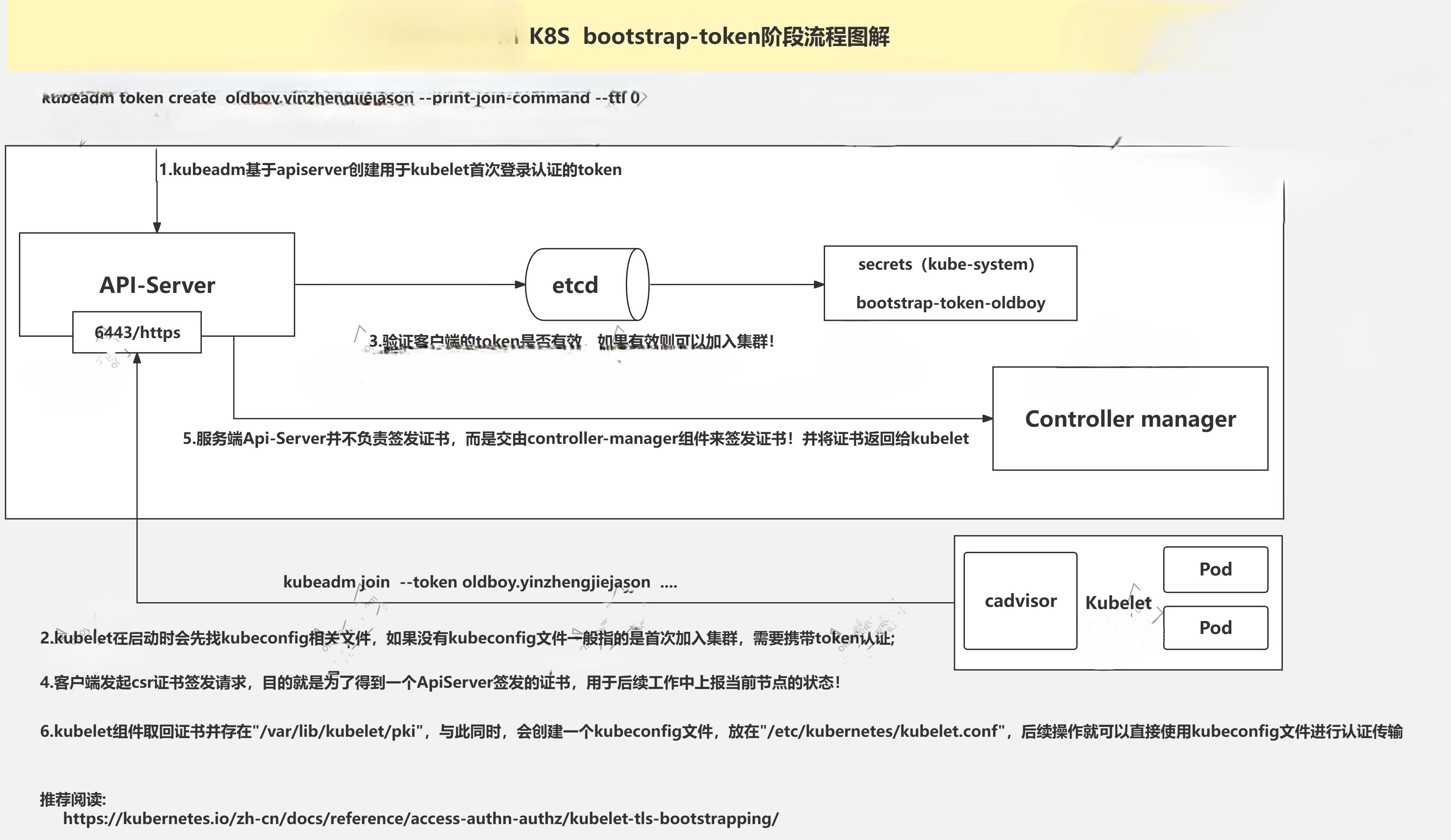
1.扩容流程
A.创建token;
B.待加入节点安装docker,kubectl,kubeadm,kubelet等相关组件;
C.kubeadm join即可
2.实战案例
2.1 master节点创建token
[root@master231 18-scheduler]# kubeadm token create oldboy.yinzhengjiejason --print-join-command --ttl 0
kubeadm join 10.0.0.231:6443 --token oldboy.yinzhengjiejason --discovery-token-ca-cert-hash sha256:2e59d5d84d2fad847601a21917719c93efce1620746da1f48e358a9174c1c152
[root@master231 18-scheduler]#
[root@master231 18-scheduler]# kubeadm token list
TOKEN TTL EXPIRES USAGES DESCRIPTION EXTRA GROUPS
oldboy.yinzhengjiejason <forever> <never> authentication,signing <none> system:bootstrappers:kubeadm:default-node-token
[root@master231 18-scheduler]#
2.2 客户端安装相关软件包
主要安装docker,kubectl,kubeadm,kubelet等相关组件。
2.3 待加入节点假如集群【使用第一步生成的token】
[root@worker233 ~]# kubeadm join 10.0.0.231:6443 --token oldboy.yinzhengjiejason --discovery-token-ca-cert-hash sha256:2e59d5d84d2fad847601a21917719c93efce1620746da1f48e358a9174c1c152
[preflight] Running pre-flight checks
[preflight] Reading configuration from the cluster...
[preflight] FYI: You can look at this config file with 'kubectl -n kube-system get cm kubeadm-config -o yaml'
W0722 16:54:18.692995 335932 utils.go:69] The recommended value for "resolvConf" in "KubeletConfiguration" is: /run/systemd/resolve/resolv.conf; the provided value is: /run/systemd/resolve/resolv.conf
[kubelet-start] Writing kubelet configuration to file "/var/lib/kubelet/config.yaml"
[kubelet-start] Writing kubelet environment file with flags to file "/var/lib/kubelet/kubeadm-flags.env"
[kubelet-start] Starting the kubelet
[kubelet-start] Waiting for the kubelet to perform the TLS Bootstrap...
This node has joined the cluster:
* Certificate signing request was sent to apiserver and a response was received.
* The Kubelet was informed of the new secure connection details.
Run 'kubectl get nodes' on the control-plane to see this node join the cluster.
2.4 master节点验证
[root@master231 18-scheduler]# kubectl get nodes
NAME STATUS ROLES AGE VERSION
master231 Ready control-plane,master 13d v1.23.17
worker232 Ready <none> 13d v1.23.17
worker233 Ready <none> 29s v1.23.17
[root@master231 18-scheduler]#
2.5 验证客户端证书信息
[root@worker233 ~]# ll /var/lib/kubelet
total 48
drwxr-xr-x 8 root root 4096 Jul 22 16:54 ./
drwxr-xr-x 65 root root 4096 Jul 15 15:06 ../
-rw-r--r-- 1 root root 1016 Jul 22 16:54 config.yaml
-rw------- 1 root root 62 Jul 22 16:54 cpu_manager_state
drwxr-xr-x 2 root root 4096 Jul 22 16:54 device-plugins/
-rw-r--r-- 1 root root 122 Jul 22 16:54 kubeadm-flags.env
-rw------- 1 root root 61 Jul 22 16:54 memory_manager_state
drwxr-xr-x 2 root root 4096 Jul 22 16:54 pki/
drwxr-x--- 2 root root 4096 Jul 22 16:54 plugins/
drwxr-x--- 2 root root 4096 Jul 22 16:54 plugins_registry/
drwxr-x--- 2 root root 4096 Jul 22 16:54 pod-resources/
drwxr-x--- 8 root root 4096 Jul 22 16:54 pods/
[root@worker233 ~]#
[root@worker233 ~]# ll /var/lib/kubelet/pki/
total 20
drwxr-xr-x 2 root root 4096 Jul 22 16:54 ./
drwxr-xr-x 8 root root 4096 Jul 22 16:54 ../
-rw------- 1 root root 1114 Jul 22 16:54 kubelet-client-2025-07-22-16-54-19.pem
lrwxrwxrwx 1 root root 59 Jul 22 16:54 kubelet-client-current.pem -> /var/lib/kubelet/pki/kubelet-client-2025-07-22-16-54-19.pem
-rw-r--r-- 1 root root 2258 Jul 22 16:54 kubelet.crt
-rw------- 1 root root 1675 Jul 22 16:54 kubelet.key
2.6 master节点查看证书签发请求
[root@master231 18-scheduler]# kubectl get csr
NAME AGE SIGNERNAME REQUESTOR REQUESTEDDURATION CONDITION
csr-szn6d 83s kubernetes.io/kube-apiserver-client-kubelet system:bootstrap:oldboy <none> Approved,Issued
[root@master231 18-scheduler]#
[root@master231 18-scheduler]#
[root@master231 18-scheduler]# kubectl get csr csr-szn6d -o yaml
apiVersion: certificates.k8s.io/v1
kind: CertificateSigningRequest
metadata:
creationTimestamp: "2025-07-22T08:54:19Z"
generateName: csr-
name: csr-szn6d
resourceVersion: "216756"
uid: 1e600d47-0c23-4736-8322-ec00a5881a06
spec:
groups:
- system:bootstrappers
- system:bootstrappers:kubeadm:default-node-token
- system:authenticated
request: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0KTUlIeU1JR1pBZ0VBTURjeEZUQVRCZ05WQkFvVERITjVjM1JsYlRwdWIyUmxjekVlTUJ3R0ExVUVBeE1WYzNsegpkR1Z0T201dlpHVTZkMjl5YTJWeU1qTXpNRmt3RXdZSEtvWkl6ajBDQVFZSUtvWkl6ajBEQVFjRFFnQUU1QitECi9QeG5qZkVnVWVJZi94NlMzTWVuYzQyZ3RQZkRHZzIzMmpPMEIvMGR1d2k5QlVBNW1hcGFlL3hmUUlKV1kzdHQKTmNnRW54RzZZRDVzR1B6alVhQUFNQW9HQ0NxR1NNNDlCQU1DQTBnQU1FVUNJUUNoSTRPbTNueTVLRjU5K3BDSApNaENhREQwQ1F2MFMyVDU5T0owNHowNEQwZ0lnRE5JN1RmZTF3QmFlbjRsSSt3VmZZeGxkSE9yUFRsaFlpcWZXCnBkWXRjeGM9Ci0tLS0tRU5EIENFUlRJRklDQVRFIFJFUVVFU1QtLS0tLQo=
signerName: kubernetes.io/kube-apiserver-client-kubelet
usages:
- digital signature
- key encipherment
- client auth
username: system:bootstrap:oldboy
status:
certificate: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUNZakNDQVVxZ0F3SUJBZ0lSQU16dFFHeEdJVU5HN2kzWThMNkFFQXd3RFFZSktvWklodmNOQVFFTEJRQXcKRlRFVE1CRUdBMVVFQXhNS2EzVmlaWEp1WlhSbGN6QWVGdzB5TlRBM01qSXdPRFE1TVRsYUZ3MHlOakEzTWpJdwpPRFE1TVRsYU1EY3hGVEFUQmdOVkJBb1RESE41YzNSbGJUcHViMlJsY3pFZU1Cd0dBMVVFQXhNVmMzbHpkR1Z0Ck9tNXZaR1U2ZDI5eWEyVnlNak16TUZrd0V3WUhLb1pJemowQ0FRWUlLb1pJemowREFRY0RRZ0FFNUIrRC9QeG4KamZFZ1VlSWYveDZTM01lbmM0Mmd0UGZER2cyMzJqTzBCLzBkdXdpOUJVQTVtYXBhZS94ZlFJSldZM3R0TmNnRQpueEc2WUQ1c0dQempVYU5XTUZRd0RnWURWUjBQQVFIL0JBUURBZ1dnTUJNR0ExVWRKUVFNTUFvR0NDc0dBUVVGCkJ3TUNNQXdHQTFVZEV3RUIvd1FDTUFBd0h3WURWUjBqQkJnd0ZvQVVPVGxjOFJGWlV3b3pOdHBMaDhmd1BwNHkKZCtZd0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFJVGh2cDAzcS9zK2hSZkdFaCtVK0xmd2JtSU9lZkxCOVZYZAp0QW1zZnVCMmF4VVdOOWU2MCsxVzJMdHRYVzV6RC9FS1NpcFNlYUtBRGI5aTJvWDVka3RqVzRKMVNscC8wallPClhIWmh0VWUrcndOdk53ZXdBMHFsbVY0YTlZZnpqSUo5bmlhazh5NEhlamNpczdHZ1BsaFJKSCswL0ZqcGdja0sKa3BFNTlEV0MxVE1KRU1XNVdlRUlEcHpUK01oVW9yZkhnV1JCaTFvMTRxN0c1SHdOcmJ1VWNMc0pkYTV1a0x5WQpIbkRBNWJRRzFlQ21WYTZHUkVQQnBESTM3bVh2TVN5Wm1Ud3RoSE1UbzJuSHI3eXpSS1ZRbnI5aWttTk51WUYrCnJTUEJ2Snc5QTk1YUdKN3JkR3ZTSnk5cmVvalFCUm1UZ1pnVitzQmZ2aXVhNVlqSG5kQT0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=
conditions:
- lastTransitionTime: "2025-07-22T08:54:19Z"
lastUpdateTime: "2025-07-22T08:54:19Z"
message: Auto approving kubelet client certificate after SubjectAccessReview.
reason: AutoApproved
status: "True"
type: Approved
[root@master231 18-scheduler]#
2.7 移除token
[root@master231 18-scheduler]# kubeadm token list
TOKEN TTL EXPIRES USAGES DESCRIPTION EXTRA GROUPS
oldboy.yinzhengjiejason <forever> <never> authentication,signing <none> system:bootstrappers:kubeadm:default-node-token
[root@master231 18-scheduler]#
[root@master231 18-scheduler]# kubeadm token delete oldboy
bootstrap token "oldboy" deleted
[root@master231 18-scheduler]#
[root@master231 18-scheduler]# kubeadm token list
[root@master231 18-scheduler]#
[root@master231 18-scheduler]#
[root@master231 18-scheduler]# kubectl get secrets -n kube-system bootstrap-token-oldboy
Error from server (NotFound): secrets "bootstrap-token-oldboy" not found
[root@master231 18-scheduler]#
[root@master231 18-scheduler]#




 浙公网安备 33010602011771号
浙公网安备 33010602011771号