MJUCTF(2)
Web
1. ascll你知道怎么解吗
打开靶场查看页面源码发现有666C6167, 明显flag头, 直接url解码即可
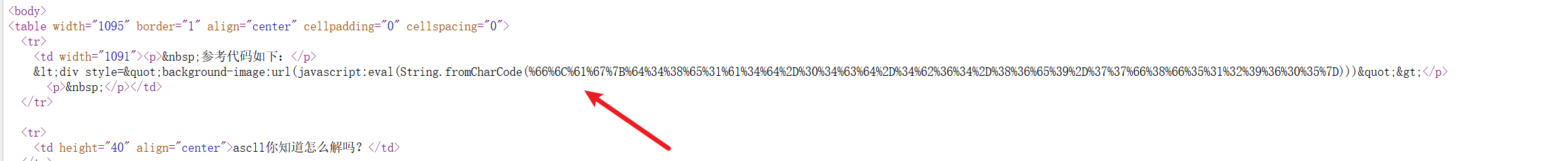

#flag{d48e1a4d-04cd-4b64-86e9-77f8f5129605}
2. 好像是
将指向的数据直接进行html解码即可
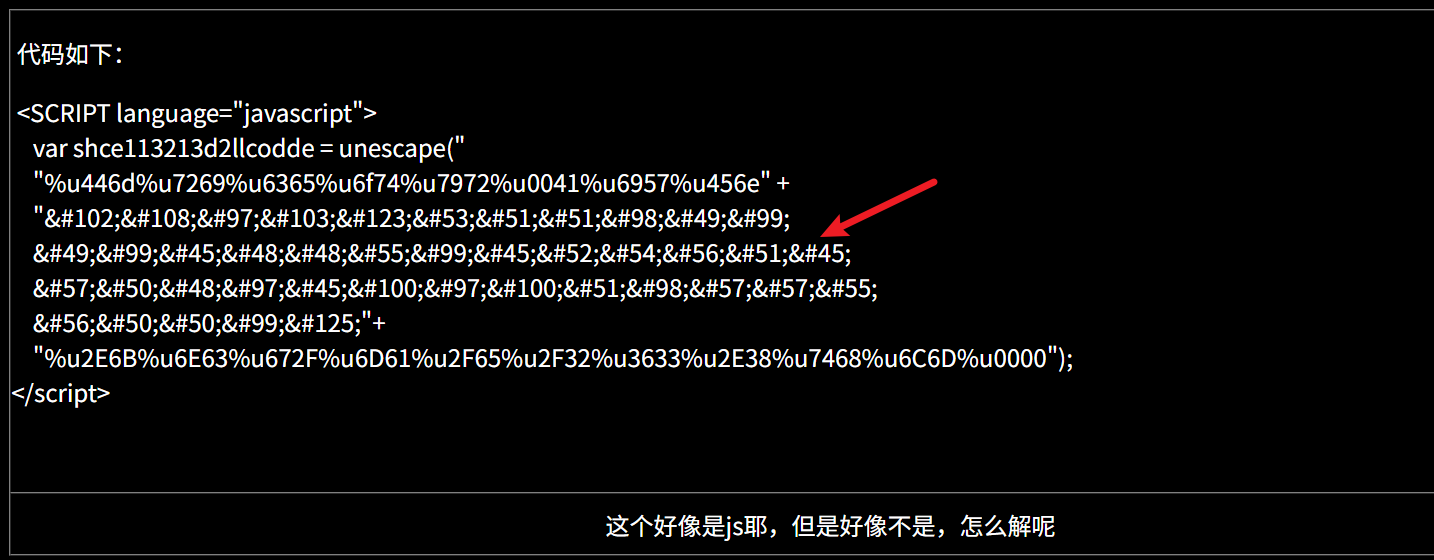
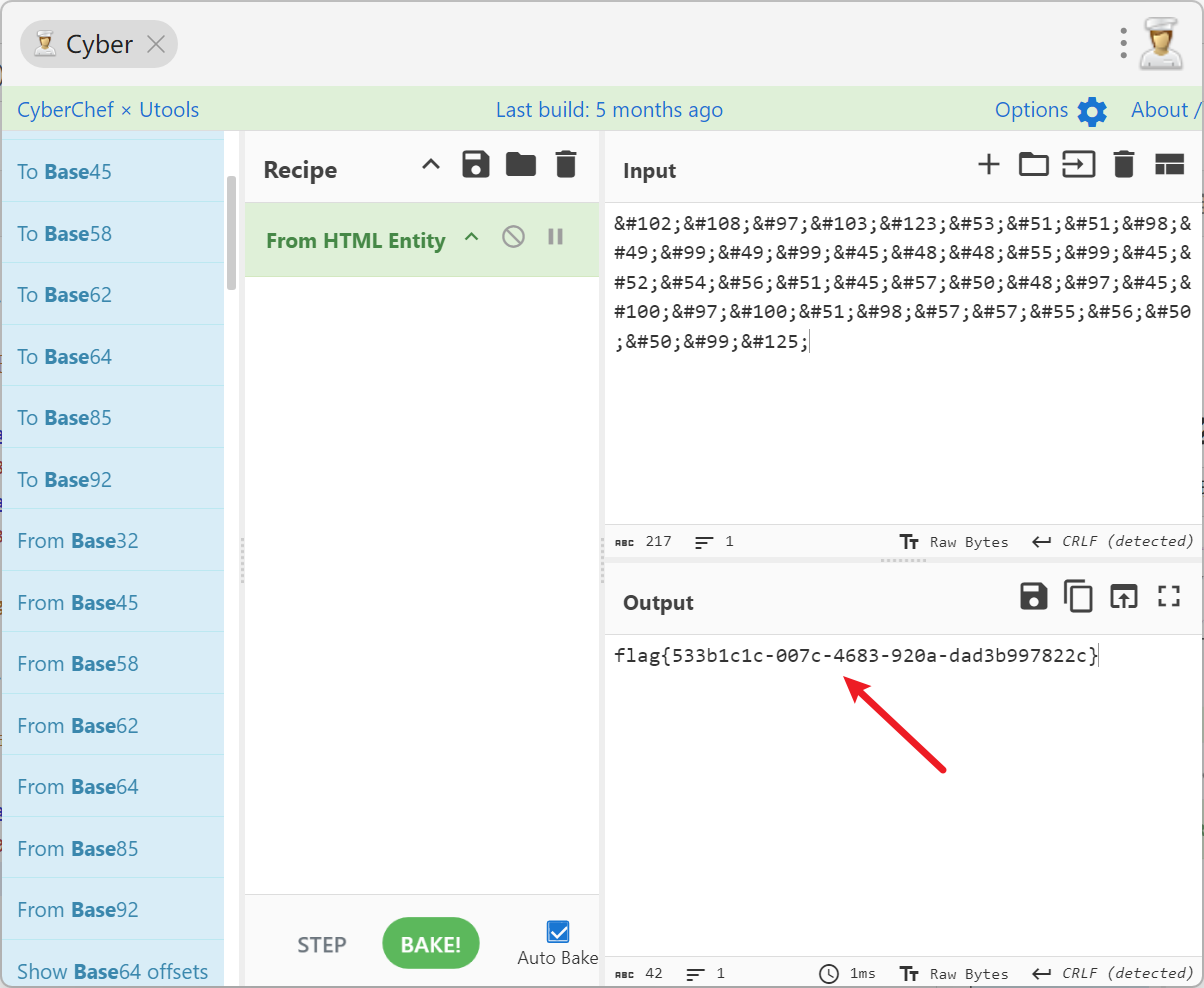
#flag{533b1c1c-007c-4683-920a-dad3b997822c}
3. 正确的密码
将框选中的数据进行md5解密
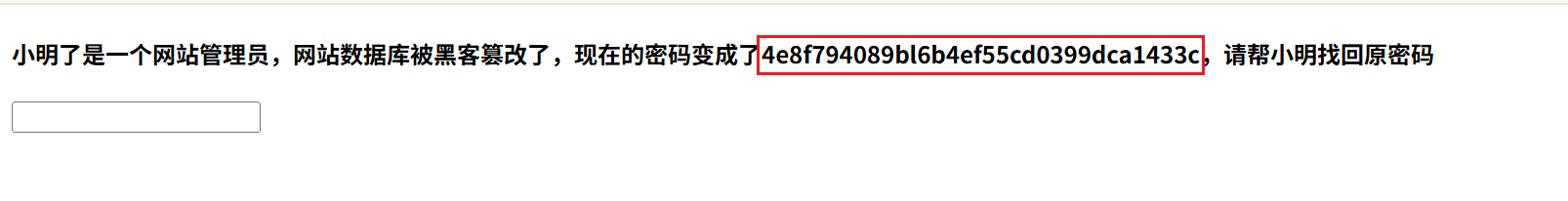
发现没办法解密
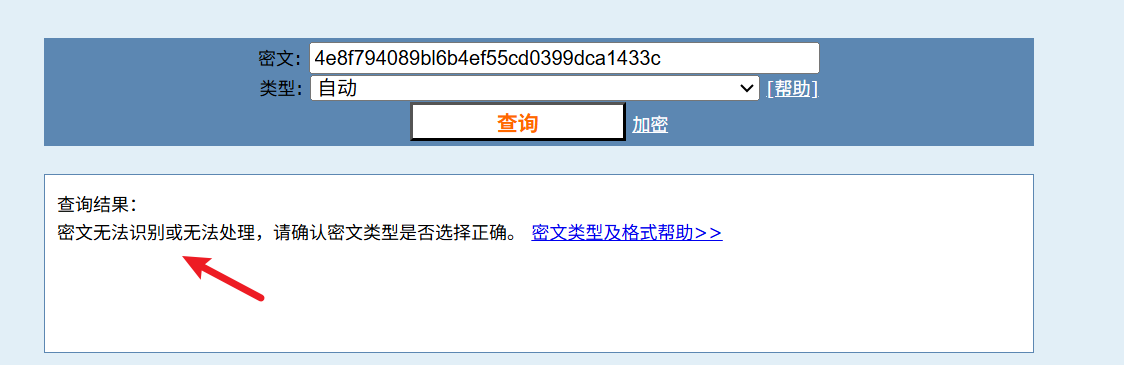
由于32位md5由数字0-9和字母a-f组成, 所以我们可以看到l是多余的, 将其删除再次进行md5解密
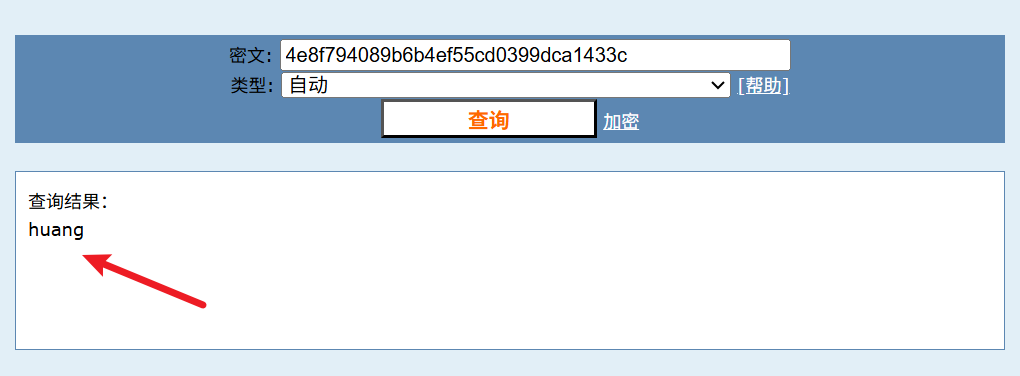
成功得到huang, 直接输入huang得到flag
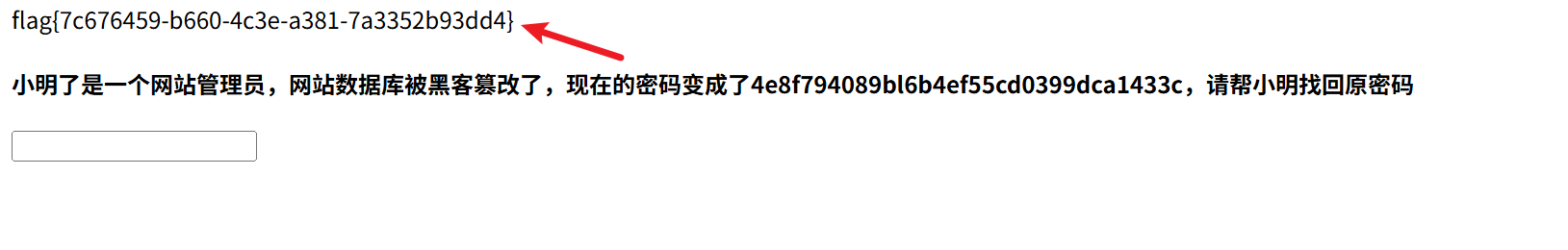
#flag{7c676459-b660-4c3e-a381-7a3352b93dd4}
4. CTF发源地
直接百度搜索CTF发源地
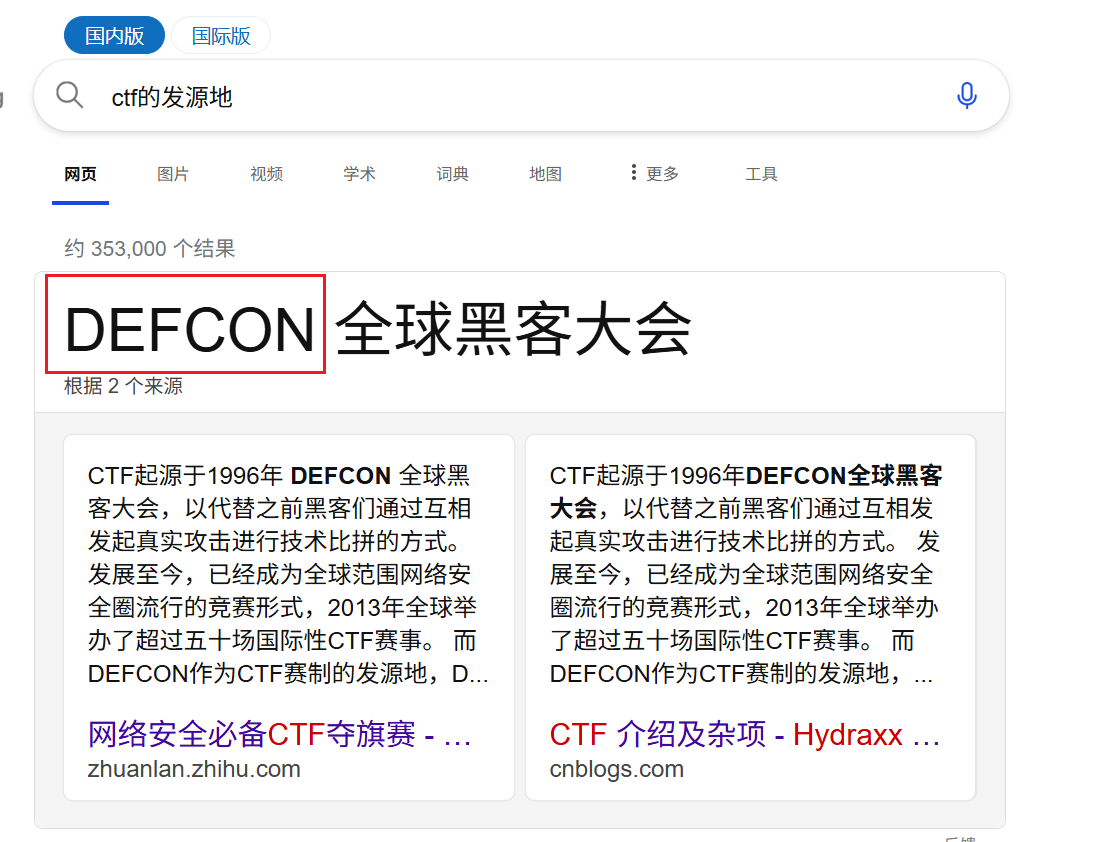
将DEFCON提交即可得到flag
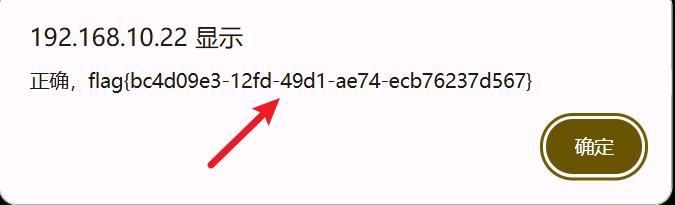
#flag{bc4d09e3-12fd-49d1-ae74-ecb76237d567}
5. 躲猫猫
进入靶场直接查看页面源码, 拿到flag

#flag{6a0c1f8c-d7b3-4b12-8751-54edc2254700}
6. Document
进入靶场F12大法, 发现存在一个ef5pb.html
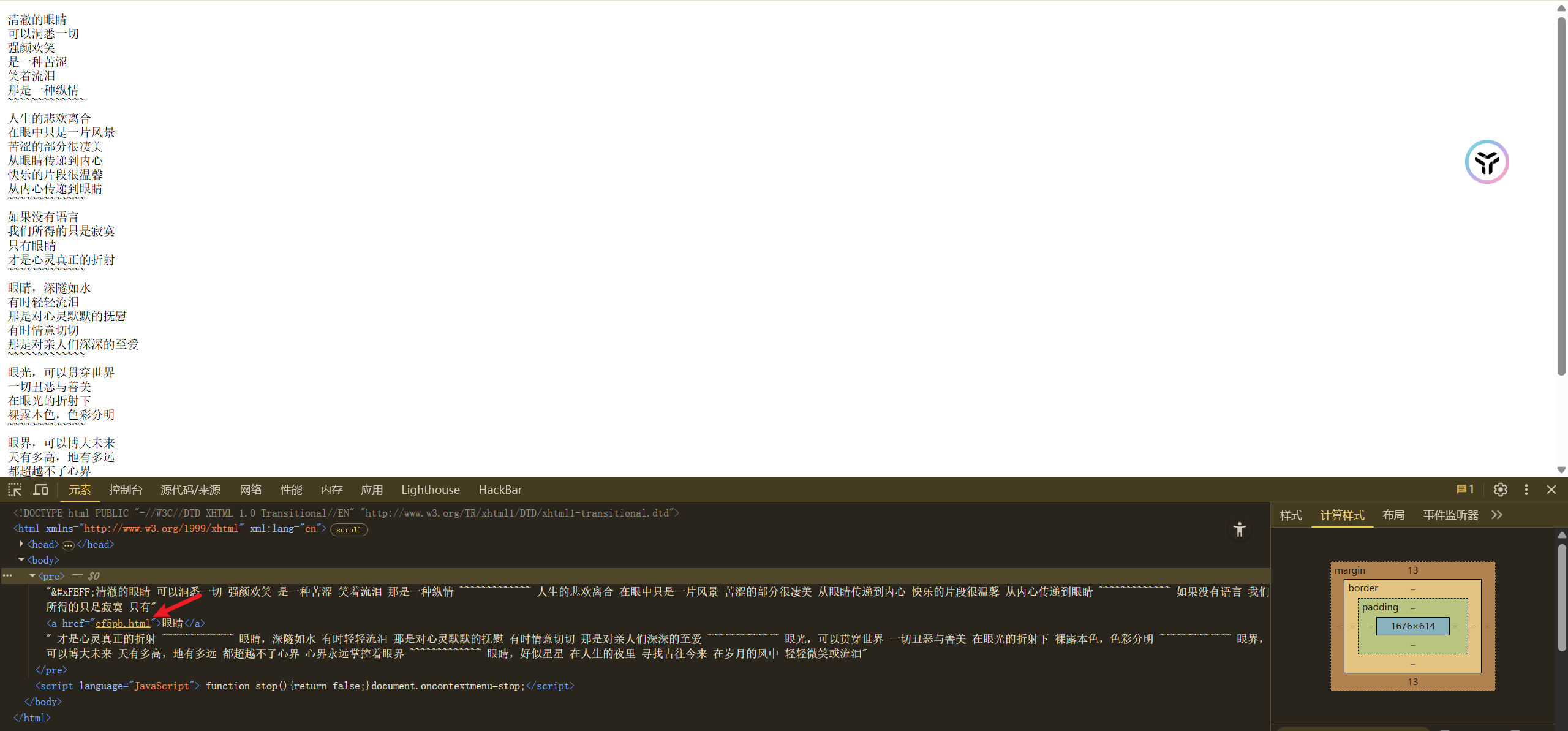
双击查看该页面拿到flag
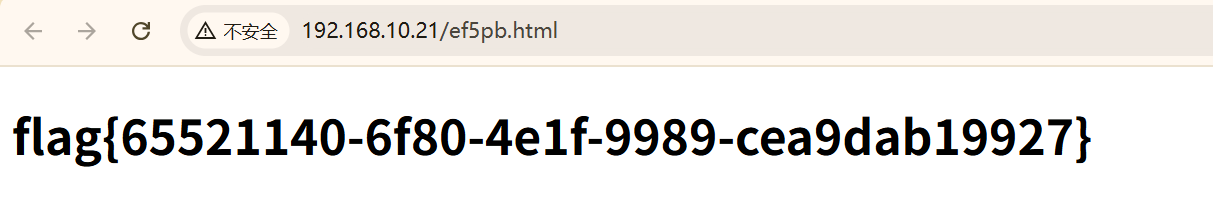
#flag{65521140-6f80-4e1f-9989-cea9dab19927}
Reverse
1. ezre
查看程序是否有加壳
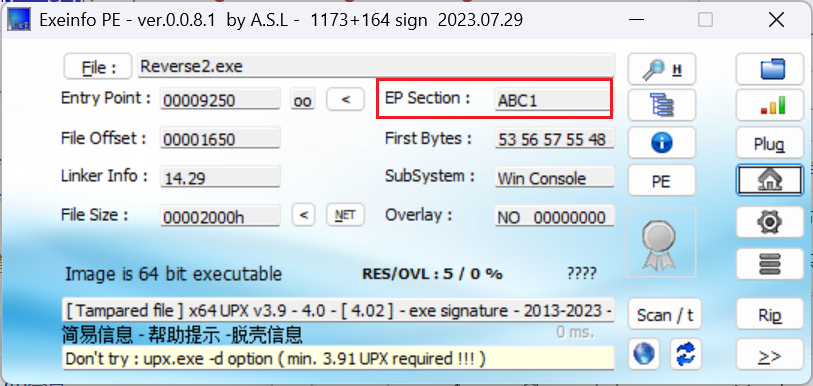
发现upx加壳, 但是UPX特征码不对, 拖入到010中进行修改
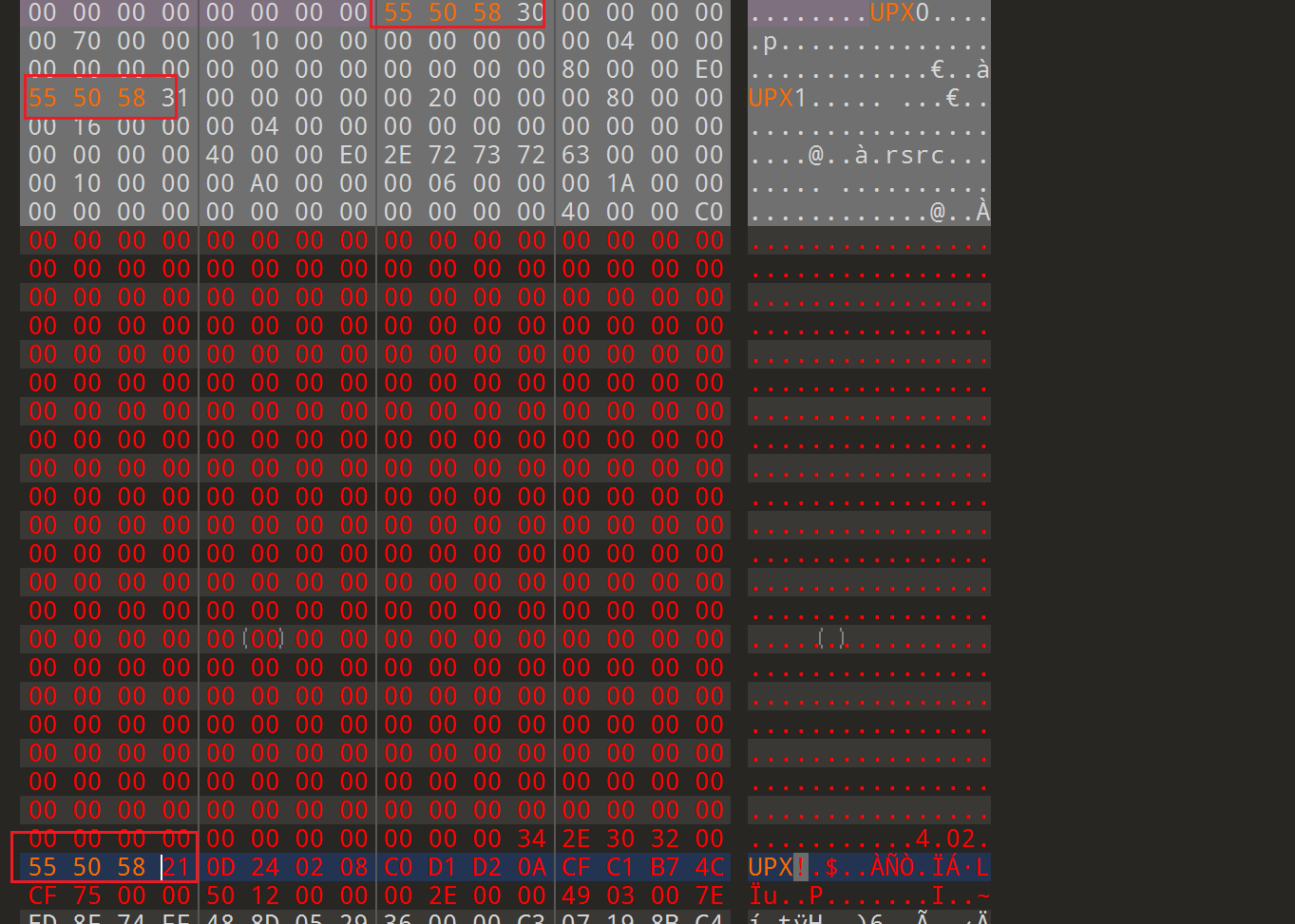
使用upx脱壳工具进行脱壳, 指令-d
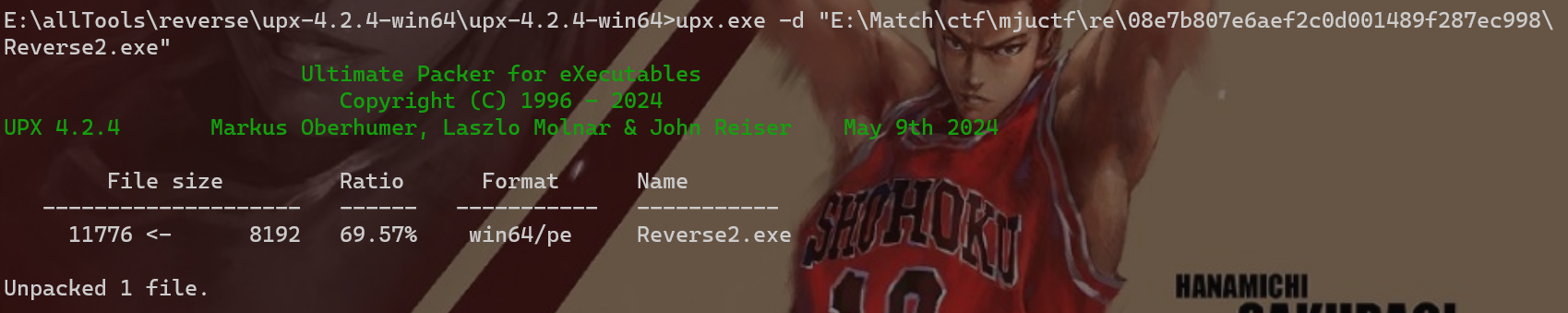
脱壳成功, 再次查看程序
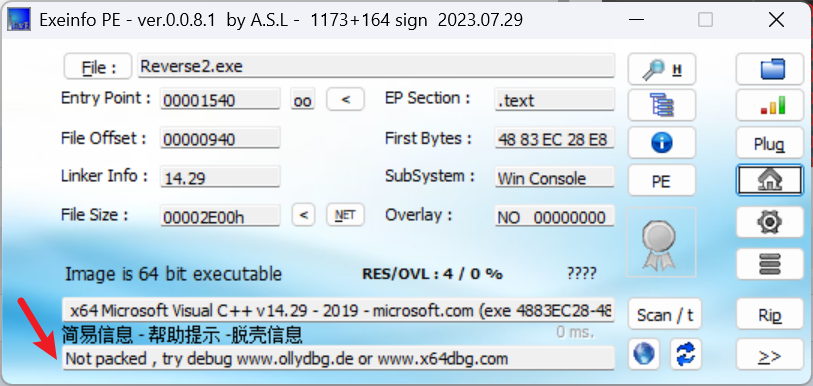
使用IDA64打开
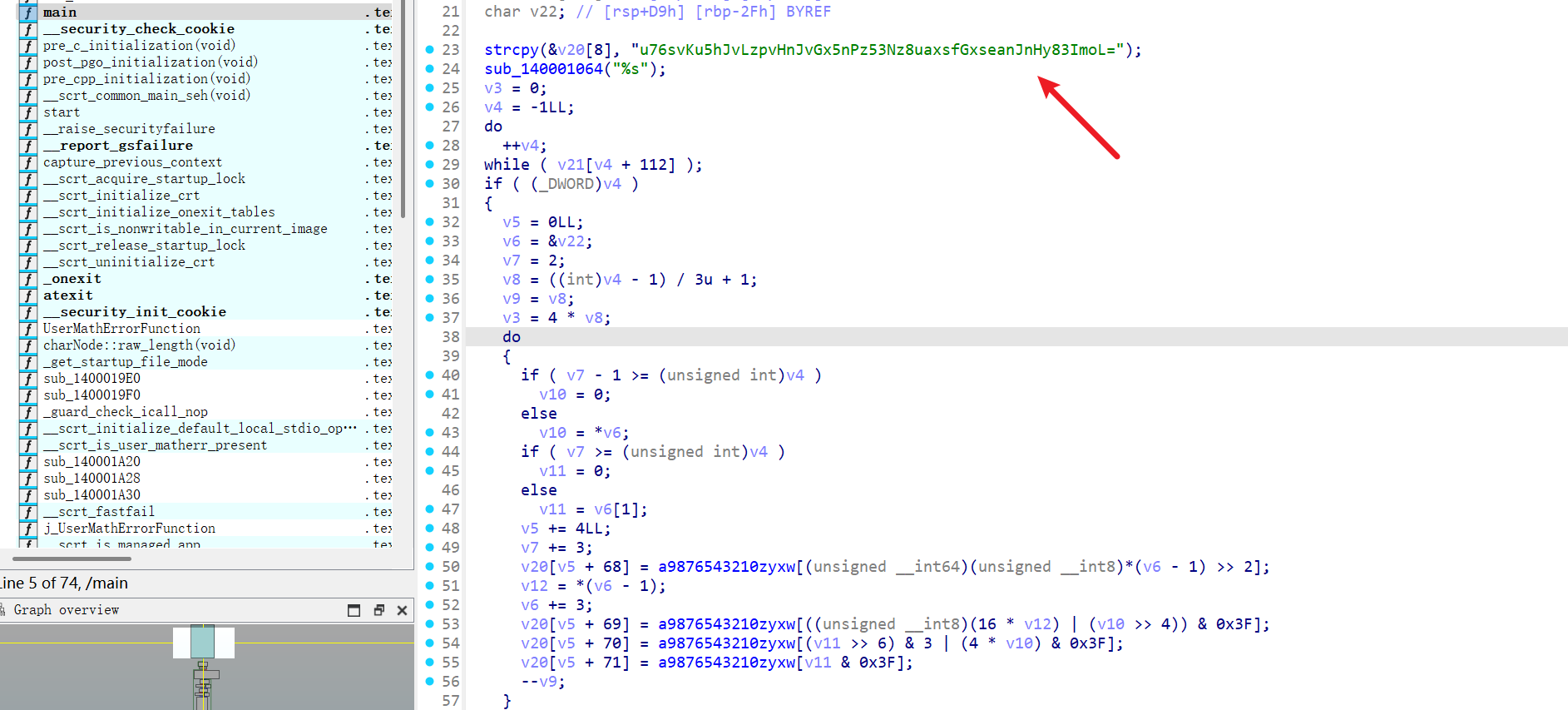
找到密文, 看起来是base64加密, shift+F12打开字符串看到base64编码表, 考察base64变表加密
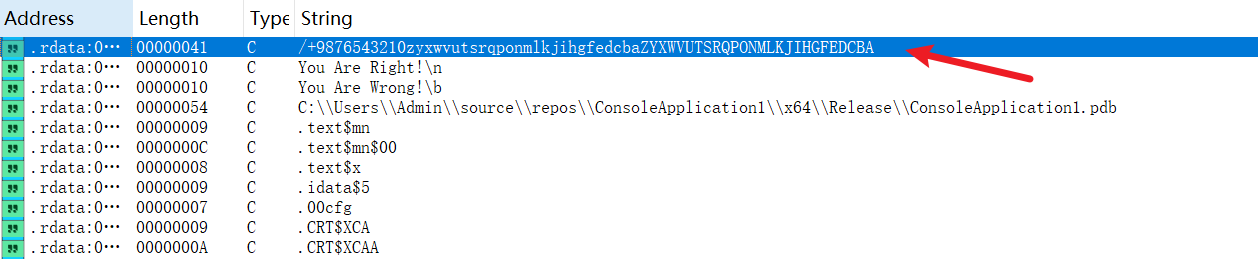
打开厨子即可解密
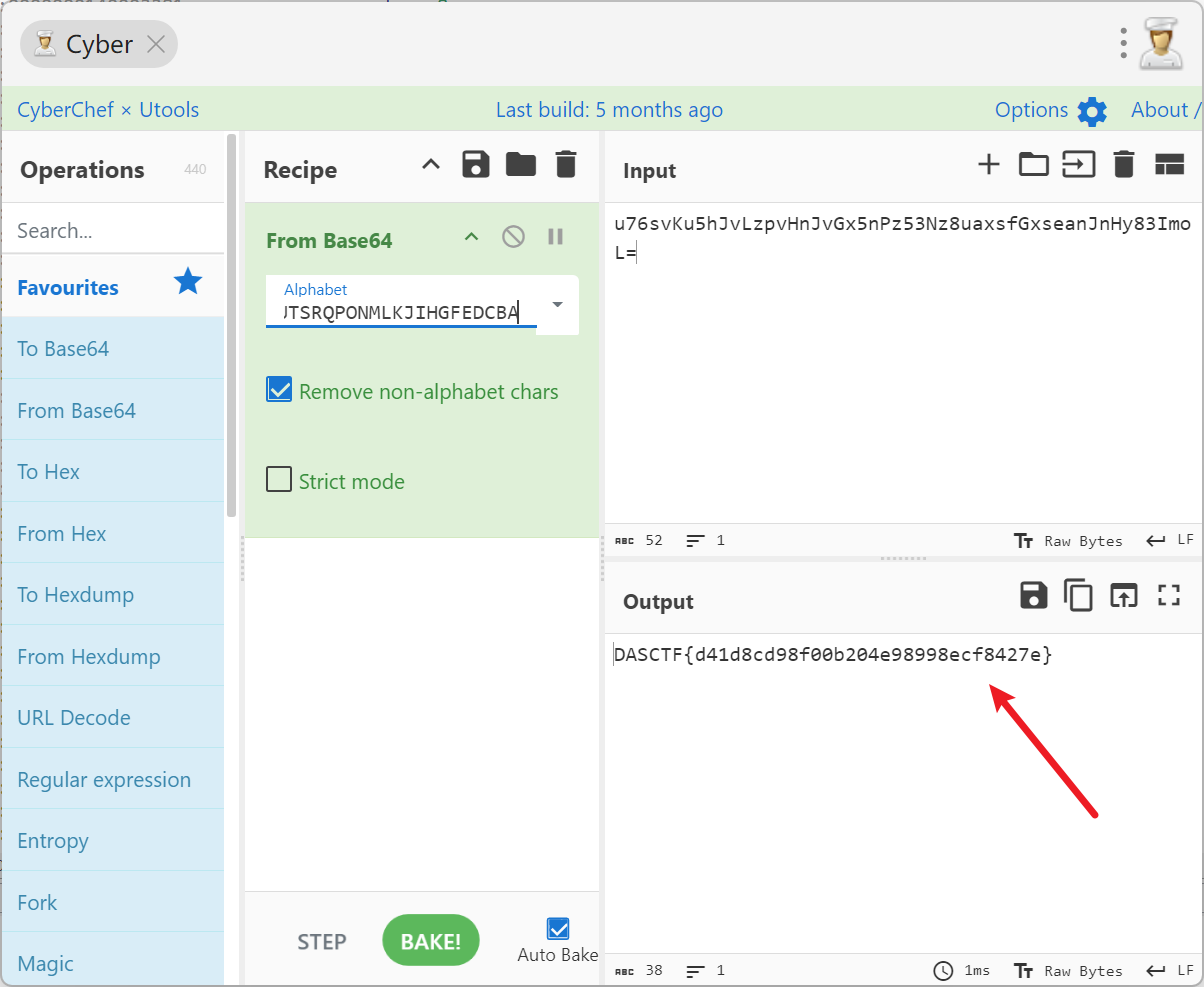
#DASCTF{d41d8cd98f00b204e98998ecf8427e}
Crypto
1. 还是RSA
已知p, q, e, c, 求m
exp
import libnum
p = 9648423029010515676590551740010426534945737639235739800643989352039852507298491399561035009163427050370107570733633350911691280297777160200625281665378483
q = 11874843837980297032092405848653656852760910154543380907650040190704283358909208578251063047732443992230647903887510065547947313543299303261986053486569407
e = 65537
c = 83208298995174604174773590298203639360540024871256126892889661345742403314929861939100492666605647316646576486526217457006376842280869728581726746401583705899941768214138742259689334840735633553053887641847651173776251820293087212885670180367406807406765923638973161375817392737747832762751690104423869019034
n = p * q
phi = (p - 1) * (q - 1)
d = libnum.invmod(e, phi)
m = pow(c, d, n)
print("flag{" + f"{m}" + "}")
#flag{5577446633554466577768879988}
2. 简单密码
已知p, q, e, 求逆元d
exp
import libnum
p = 473398607161
q = 4511491
e = 17
n = p * q
phi = (p - 1) * (q - 1)
d = libnum.invmod(e, phi)
print("flag{" + f"{d}" + "}")
#flag{125631357777427553}
3. babyrsa
考察pollards_rho_algorithm算法, 已知p, q, alpha, beta都为素数, 且(p-1)和(q-1)有共同的因子2g
exp
import libnum
n = 7291079313308676175175230422086906986296185082644647473960832422555800048359693211245839442369670028931769993263140869765778275923238998260803976729216289550292957705978682342093105097819370971295310860873669725515021912668386895781458555148835312190129315078660321668053910979825522489767263648850838063570709547440063938943646651772164530633522199339380882021
c = 6852815582847351113509942128109481399896904701205184324498219416217713791422045750671866168086014291595924213741129903103633649030030862155462156567674060259236309618154155879167135323181060411408641918545728735975727426628455883980762998117953708039752390223308664385975029727270659931396150824601346207643504567598401379829379513077614506465772564081039622555
e = 0x10001
'''
#生成p和q
def gcd(a, b):
while b:
a, b = b, a % b
return a
def mapx(x):
x = (pow(x, n - 1, n) + 3) % n # pow(x,n-1,n)是为了减小数值,加速运算,
return x
def pollard_rho(x1, x2):
while True:
x1 = mapx(x1)
x2 = mapx(mapx(x2))
p = gcd(x1 - x2, n)
if (p == n):
print("fail")
return
elif (p != 1):
print("p: " + str(p))
print("q: " + str(n // p))
break
def main():
pollard_rho(1, 1)
return
main()
'''
p = 2948641930262469725989181036958671521254663020227860530233393495537459874852024531666954047492491971602801538914012981613264502670285474838189347278705242650445407848908630163212543
q = 2472690643946608240561292074974644222204317457834288068258816385031871462181573647892577171804047793781795390348807454334484077875356225305957305065441735307518077256890485938747547
phi = (p - 1) * (q - 1)
d = libnum.invmod(e, phi)
m = pow(c, d, n)
flag = libnum.n2s(int(m))
print(flag)
#flag{36e3ac06db2f4b6693b6203b5a7b0c47}
4. ezRSA
用特殊的方法要分解n, 由于这题的n=p*q*r, 所以要二次分离, 用下面的脚本依次求出p和q
这题sagemath通过在线网站:https://sagecell.sagemath.org/
exp1
import sys
sys.setrecursionlimit(10^6)
def QiCheng(n):
R = Integers(n)
attempts = 20
js = [0, (-2^5)^3, (-2^5*3)^3, (-2^5*3*5)^3, (-2^5*3*5*11)^3, (-2^6*3*5*23*29)^3]
for _ in range(attempts):
for j in js:
if j == 0:
a = R.random_element()
E = EllipticCurve([0, a])
else:
a = R(j)/(R(1728)-R(j))
c = R.random_element()
E = EllipticCurve([3*a*c^2, 2*a*c^3])
x = R.random_element()
z = E.division_polynomial(n, x)
g = gcd(z, n)
if g > 1:
return g
n = 9538021751628536852408501286168483813314412735895479739927717141476773667639827957364470036469824080863695016876649430767989493414102438459726995773929432031030711858674010476443470829848881019954364865559786405634110975360603146962905591364077050203611417131319712853488058989616979421086607083508253749107841740805183246095163508729503357644427645551806619877237477506652967793114657161585748011825104957443398546157476609905465434644237382098576123564508081875120447800229615982509540366157404884418246451973549462507557841370664897335482982363052754190858259728676370721643622361513734034132359319207554397899826986064839858882679259437126945956468671697923895447242234231162378527579809374761488089042042372357605061848153824128819513926446389096997922053606332895431573000041370210492719534900204713663983125098567293022461751743252891360699861381370094933791427873060452153432622706509068745004944142594669707821251
p = int(QiCheng(Integer(n)))
print(p)
#p = 13359024722559285282550326061076933199166694977056580088140992627015697239802903302431040957674113267726067821426132611358988463778264497831574600112940763803264872020766051053882791826367069500251456346290430095844021634716250316434904652039400669297620442769482751430158391971439997735232074080800988619219
#q = 37288773955119014430134318532062020064067023074553290748629877676367484720065245223741401567578027915376522193547553463784880890786839600112047345946593965596060583526941972066188065437014108374904767355037823084786177030558268037305001515729117040135822962226882395578474789655538346627440522876175717630333
以上脚本参考博客: https://www.cnblogs.com/SevensNight/p/18766256
接下来就是简单的rsa解密
exp2
import libnum
n = 9538021751628536852408501286168483813314412735895479739927717141476773667639827957364470036469824080863695016876649430767989493414102438459726995773929432031030711858674010476443470829848881019954364865559786405634110975360603146962905591364077050203611417131319712853488058989616979421086607083508253749107841740805183246095163508729503357644427645551806619877237477506652967793114657161585748011825104957443398546157476609905465434644237382098576123564508081875120447800229615982509540366157404884418246451973549462507557841370664897335482982363052754190858259728676370721643622361513734034132359319207554397899826986064839858882679259437126945956468671697923895447242234231162378527579809374761488089042042372357605061848153824128819513926446389096997922053606332895431573000041370210492719534900204713663983125098567293022461751743252891360699861381370094933791427873060452153432622706509068745004944142594669707821251
p = 13359024722559285282550326061076933199166694977056580088140992627015697239802903302431040957674113267726067821426132611358988463778264497831574600112940763803264872020766051053882791826367069500251456346290430095844021634716250316434904652039400669297620442769482751430158391971439997735232074080800988619219
q = 37288773955119014430134318532062020064067023074553290748629877676367484720065245223741401567578027915376522193547553463784880890786839600112047345946593965596060583526941972066188065437014108374904767355037823084786177030558268037305001515729117040135822962226882395578474789655538346627440522876175717630333
c = 8243781365021341186612492054592396383427890072936684035243158841287346560003926505992638553468886116290066804756399060183524696774209011032883381702599391468871118789020601807007698875719472431879626581687479844727454950093287345743783548605024141323386806568251049163223972244347622973095080517297303132449740465668054283295581532467268462237717125345183959801509643840317034839676766370633006938185077193034074556981880142346462710701216201656488835015411558357741449492849820423474575038534680496338168780719053657060351385492716126246241035251982909489197109305155754881260917889857309921900911409653582692603777488289720669749835563928362029646084787931908736767440696465196589571451783360340113134781087943137196008115146673358409080831667383264465236365505571254001720698813228283453555980255403123662646082715574518910522012748840917523128629747604684821654016184589548173592998316905563723893887658301124792507982
e = 0x10001
r = n // p // q
assert p * q * r == n
phi = (p - 1) * (q - 1) * (r - 1)
d = libnum.invmod(e, phi)
m = pow(c, d, n)
flag = libnum.n2s(int(m))
print(flag)
#flag{3a30d70e-baee-44d3-8e63-a45b6785e07e}
Misc
1.你从丹东来还我一场雪白
直接GIF分离得到flag



#flag{he11ohongke}
2. 签到题
双击签到题.html, 查看源代码发现一串base64编码Zmxh开头就是flag
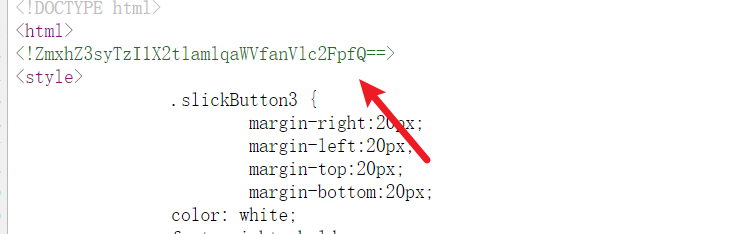
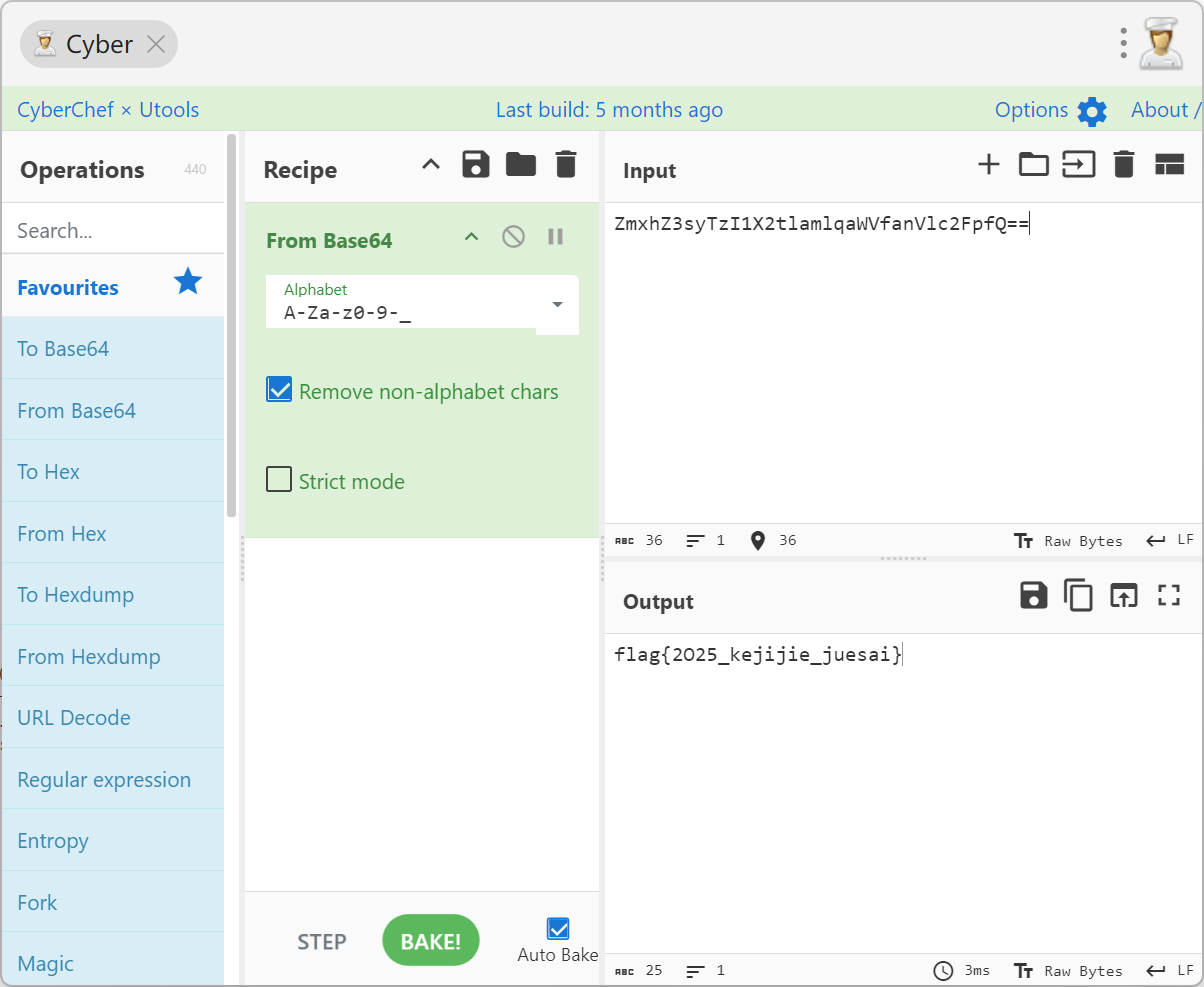
#flag{2O25_kejijie_juesai}
3. 你觉得这题怎么样
暴力破解压缩包密码, 得到密码为123456
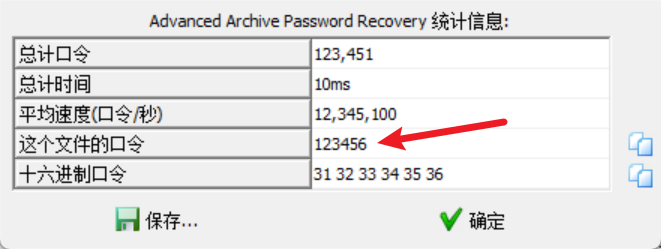
解压得到一张excel表格, 应该是隐藏了flag, 直接Ctrl+F搜索flag{
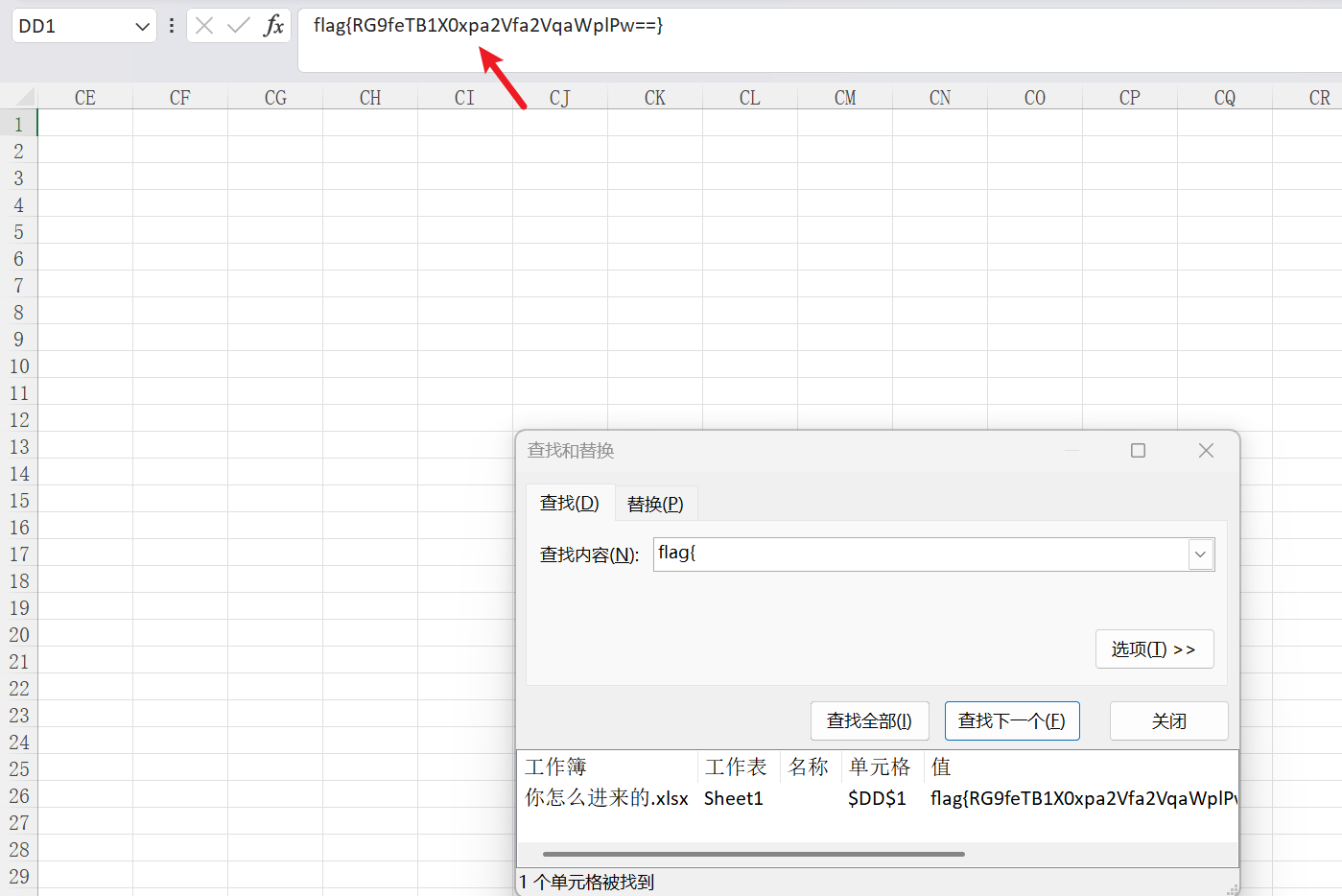
将里面的内容进行base64解码
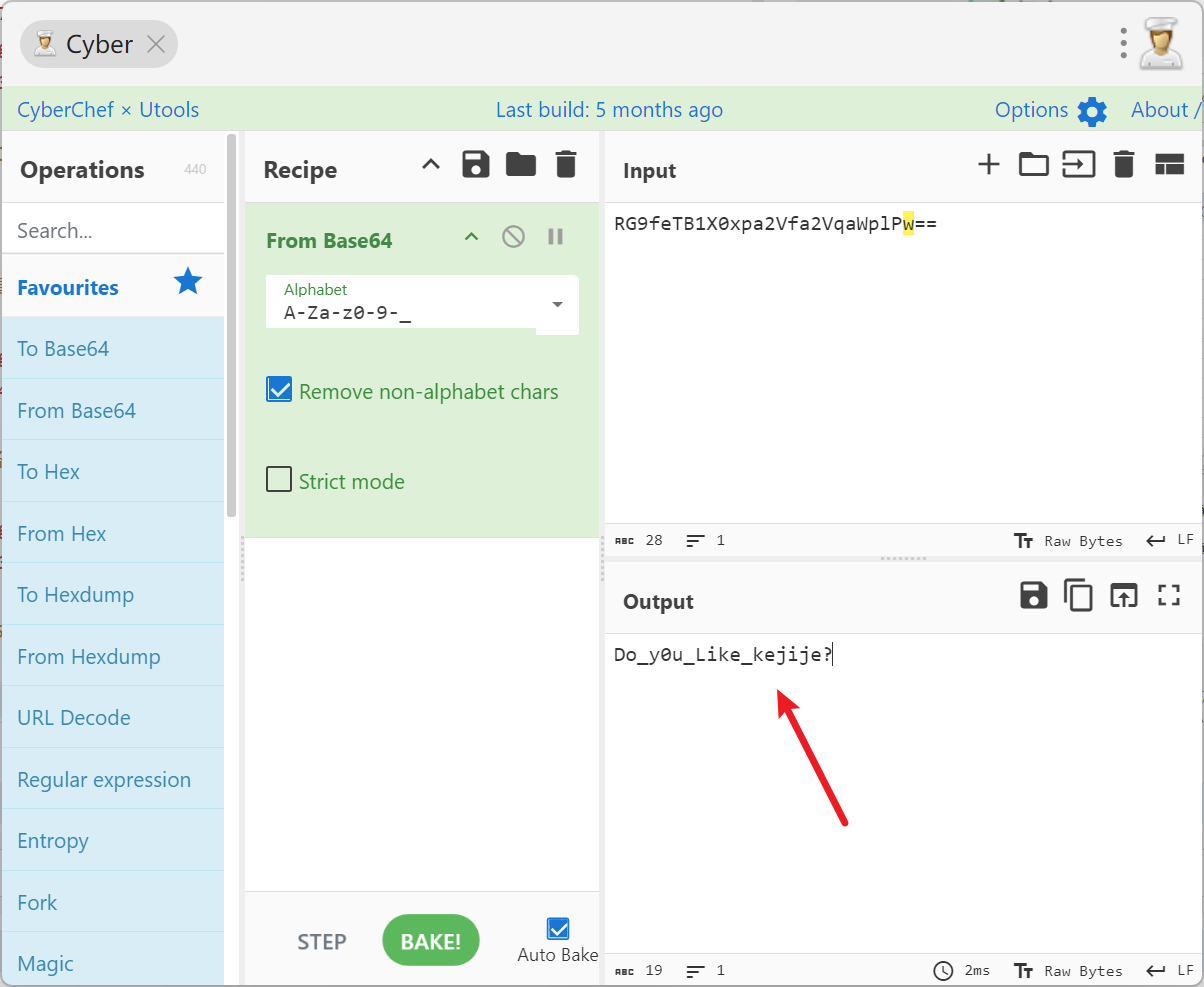
#flag{Do_y0u_Like_kejije?}
4.很传统噢
考察音频隐写, 用DeepSound工具, 密码为弱密码也就是123得到flag.zip
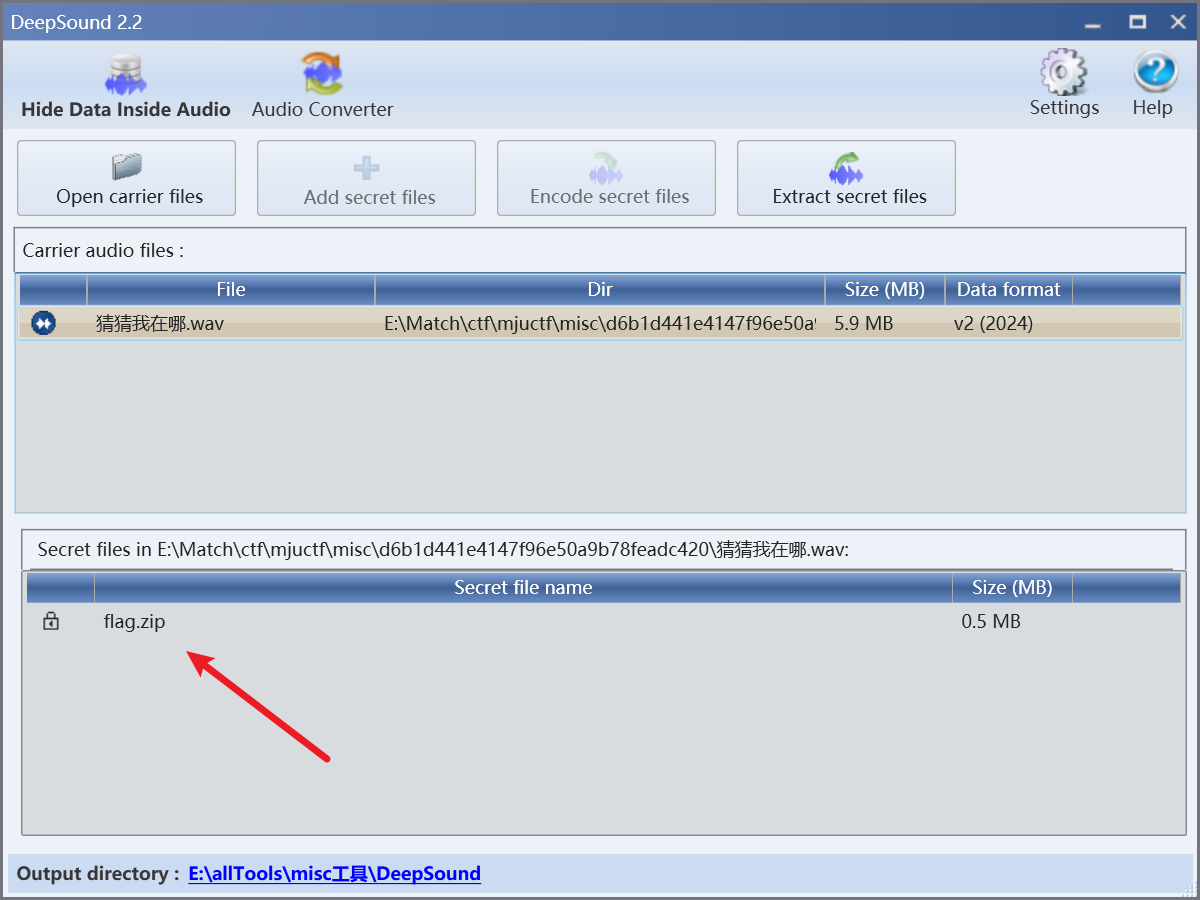
flag.zip被加密了, 里面有张flag.png图片, 考察zip的明文攻击, 使用bkcrack工具
命令:
bkcrack.exe -C flag.zip -c flag.png -x 0 89504E470D0A1A0A0000000D49484452
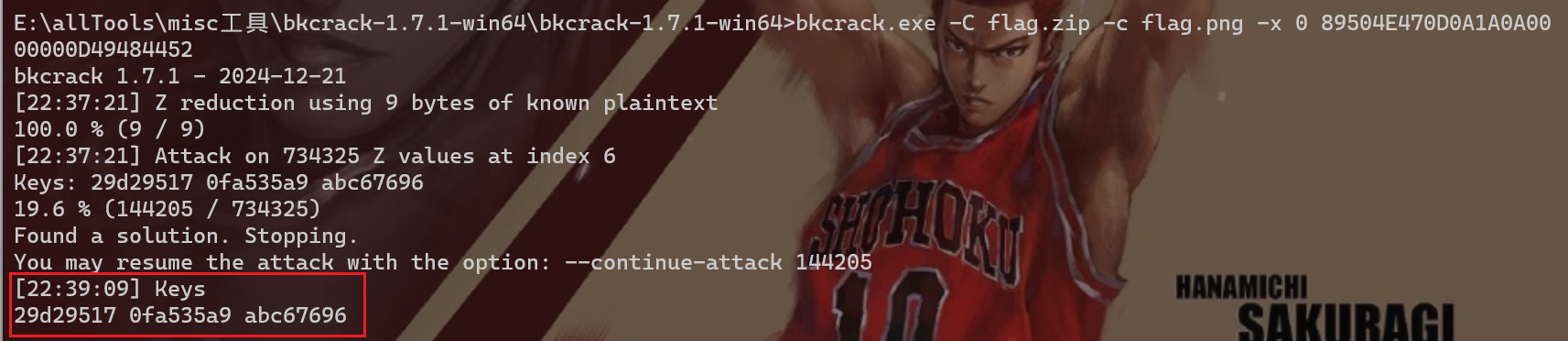
得到key之后, 再导出一个新的zip

得到图片后, 将图片拖入到随波逐流中, 发现flag
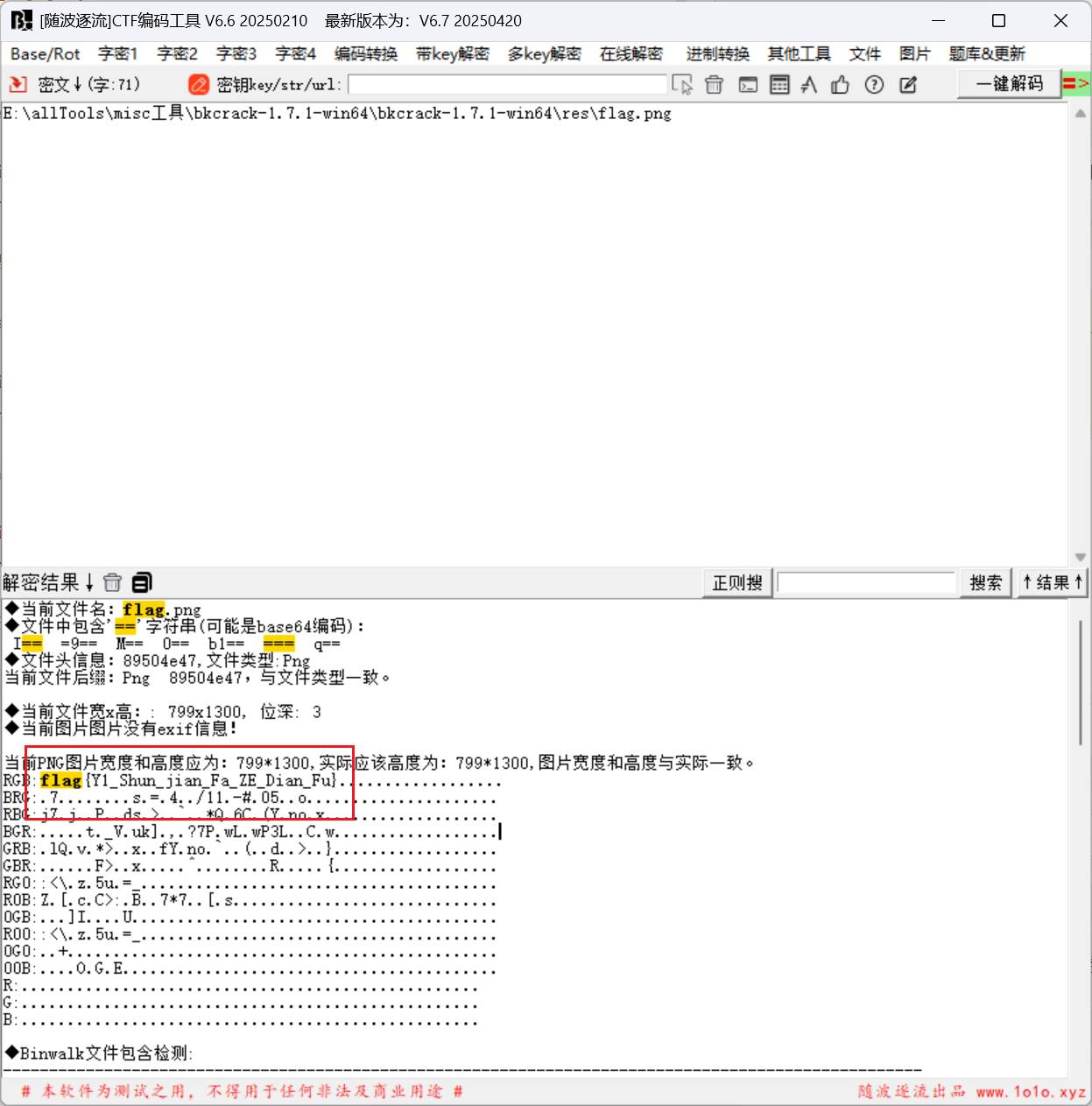
#flag{Y1_Shun_jian_Fa_ZE_Dian_Fu}
5. 太极生两仪
根据八卦图, 编写exp
exp
_hash= {"乾":"111", "兑":"011", "离":"101", "震":"001", "巽":"110", "坎":"010", "艮":"100", "坤":"000"}
encoded_text = "兑兑震兑巽巽震离乾坤坤艮"
a = ""
flag = ""
for i in encoded_text:
a += _hash.get(i)
for i in range(len(a)):
flag += a[i]
print("flag{" + flag + "}")
#flag{011011001011110110001101111000000100}
6. 两仪生四象
首先跟上一题一样, 尝试了二进制提交无果后, 猜测是否为Morse, 断开为., 没断开为-
exp
_hash= {"乾":"---", "兑":".--", "离":"-.-", "震":"..-", "巽":"--.", "坎":".-.", "艮":"-..", "坤":"...", "少阴":"-.-", "太阳":"---", "少阳":"--.", "太阴":"..-"}
encoded_text = "少阴 太阳 兑 乾 艮 震 兑 乾 巽 震 少阳 太阴"
res = ""
for i in encoded_text.split(" "):
res += _hash.get(i)
res += " "
print(res)
#-.- --- .-- --- -.. ..- .-- --- --. ..- --. ..-
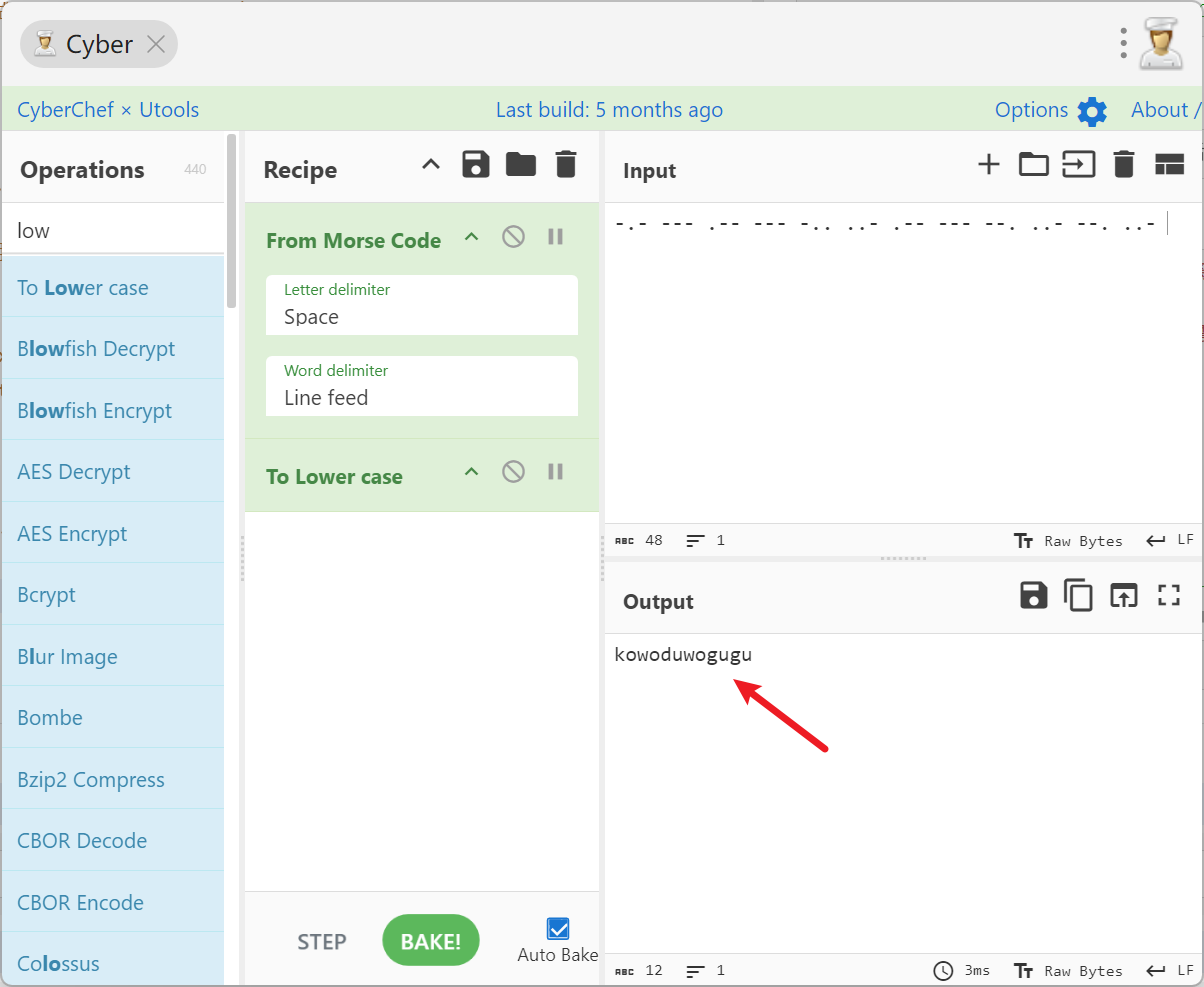
#flag{kowoduwogugu}
7. 鸽鸽
将照片拖入随波逐流, 发现还存在一个png图片(这里也可以使用010手动分离)
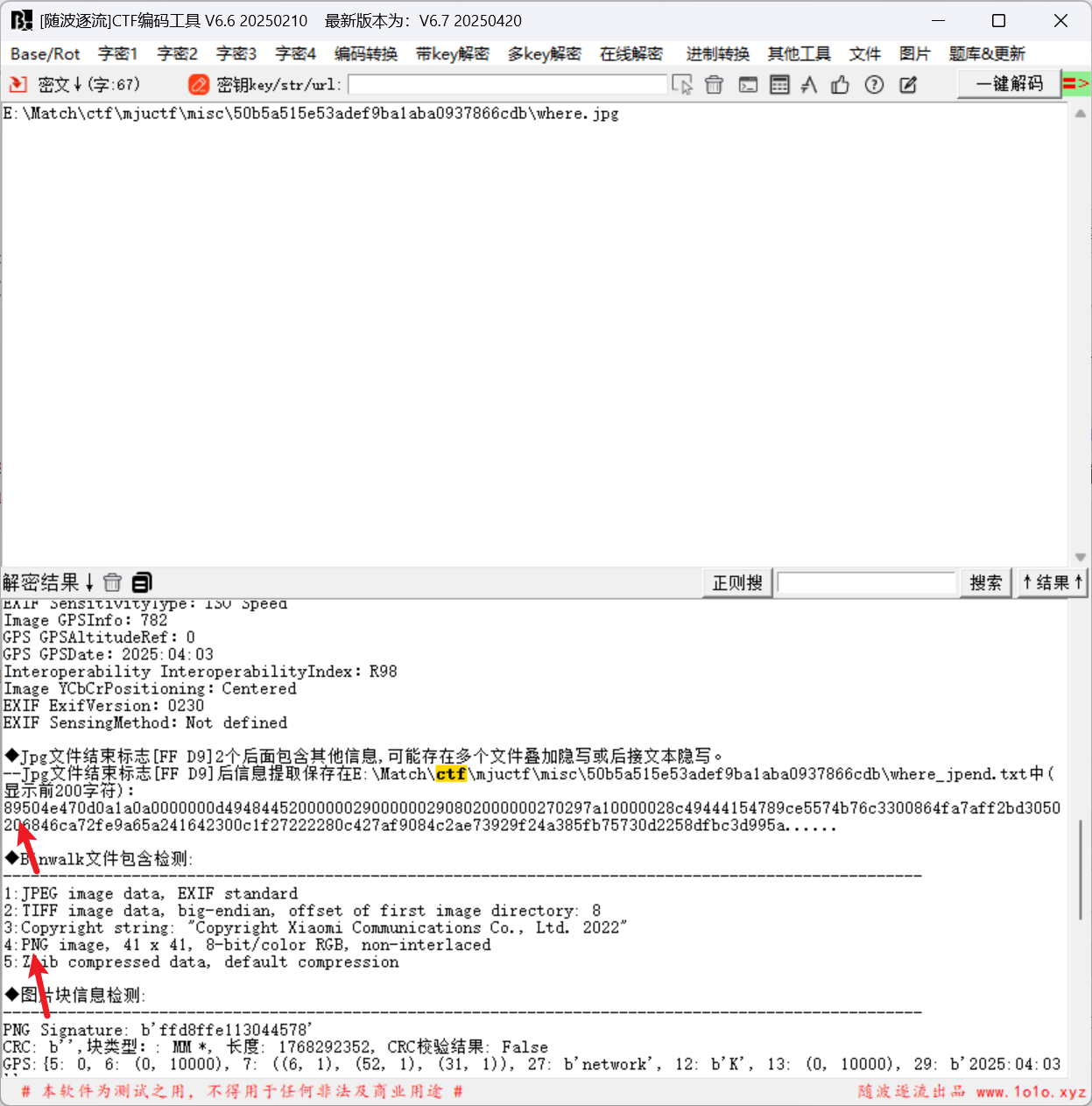
打开010新建十六进制文件, Ctrl+S保存为1.png
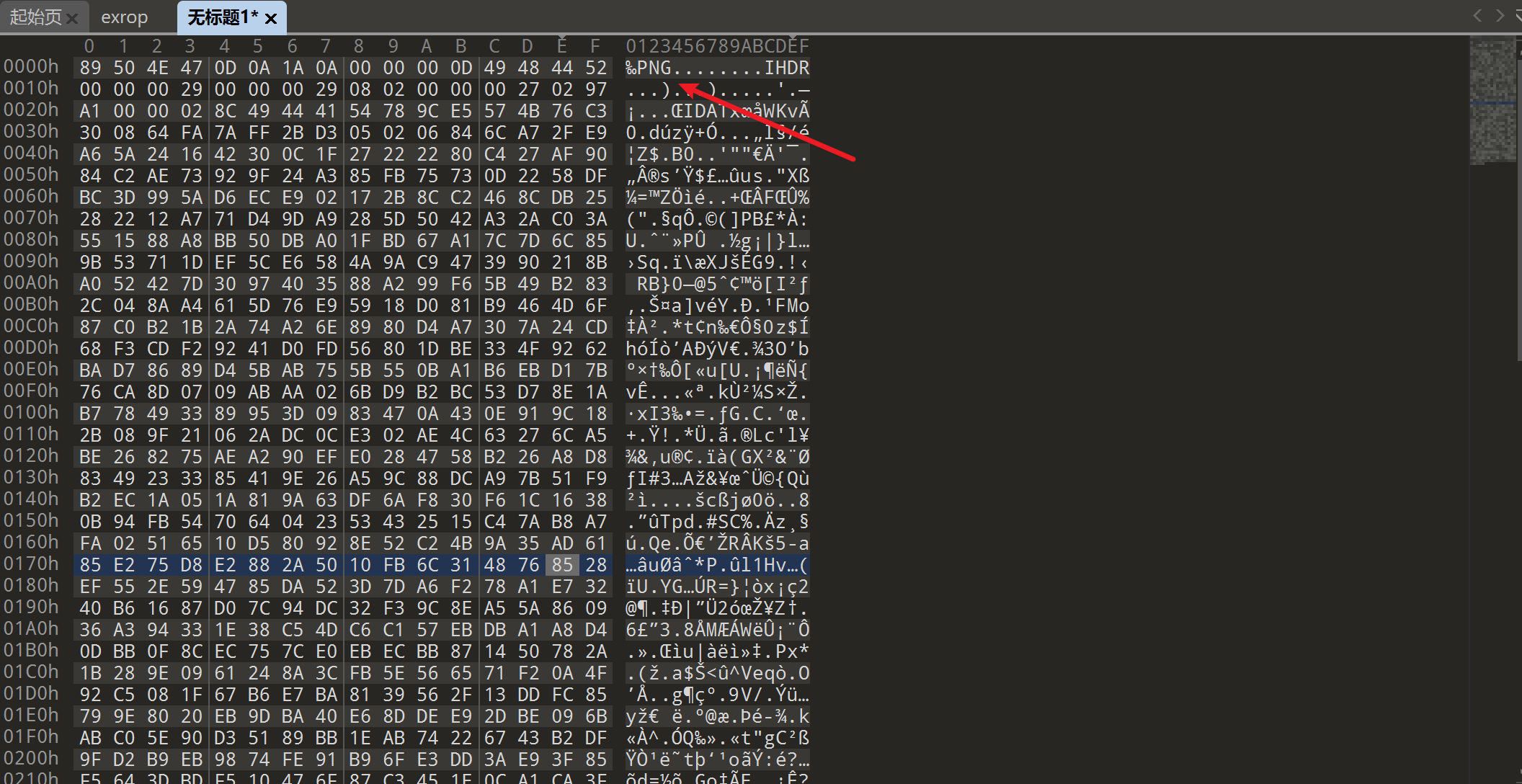
用zsteg查看下图片有隐藏什么信息

发现存在两个压缩包, 分别将其提取出来, 并修复一下压缩包
命令: zsteg -E b1,r,lsb,xy 1.png > 1.zip
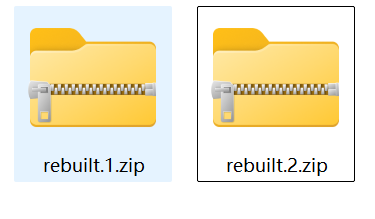
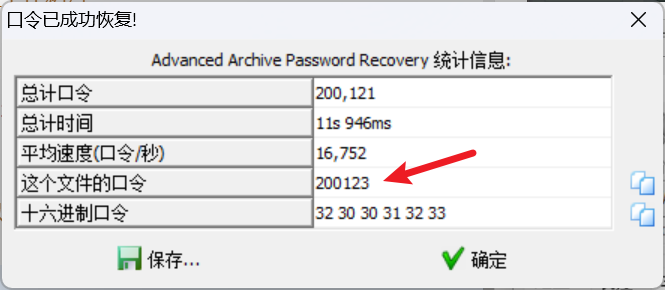
其中rebuilt1.zip存在伪加密, rebuilt2.zip可以通过爆破出密码来
再进行aes解密
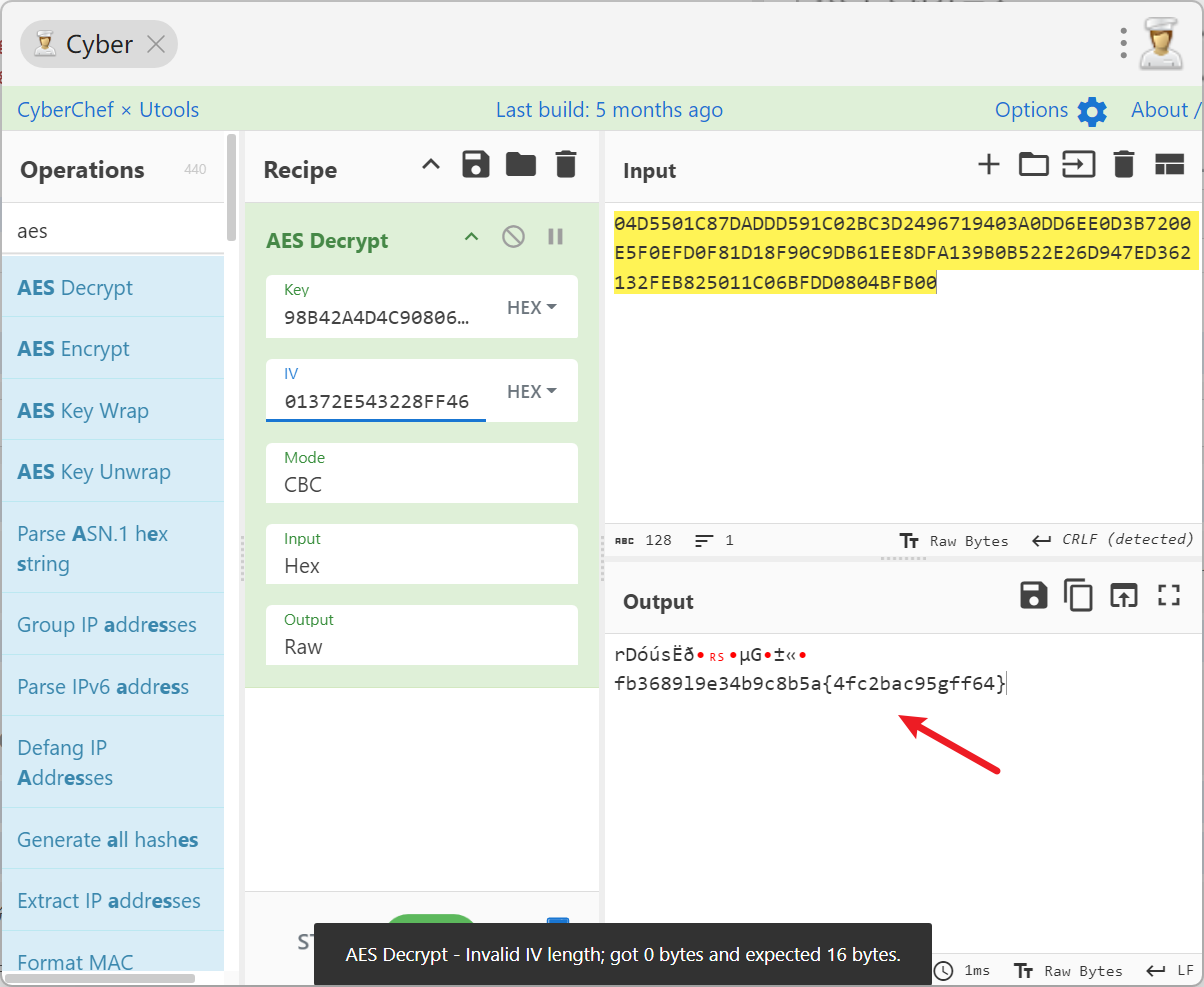
最后栅栏解密得到flag
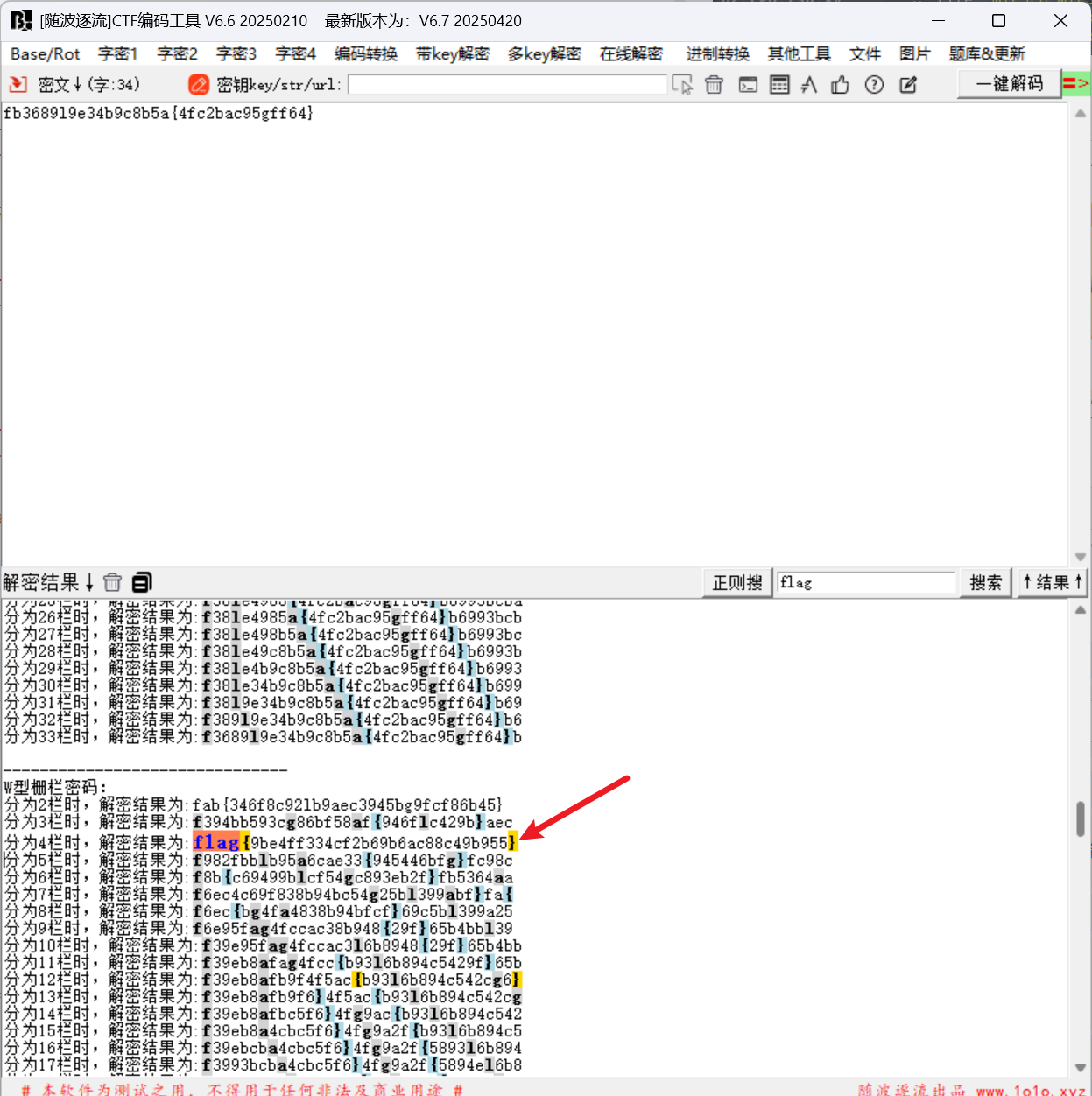
#flag{9be4ff334cf2b69b6ac88c49b955}
8. 混乱的二维码
将文件拖入到010中, 发现89 50 4E 47在尾部, 将其逆序

exp
input = open("E:\\Match\\ctf\\mjuctf\\misc\\混乱的二维码\\混乱的二维码", 'rb')
input_all = input.read()
ss = input_all[::-1]
output = open("E:\\Match\\ctf\\mjuctf\\misc\\混乱的二维码\\res.jpg", 'wb')
output.write(ss)
input.close()
output.close()

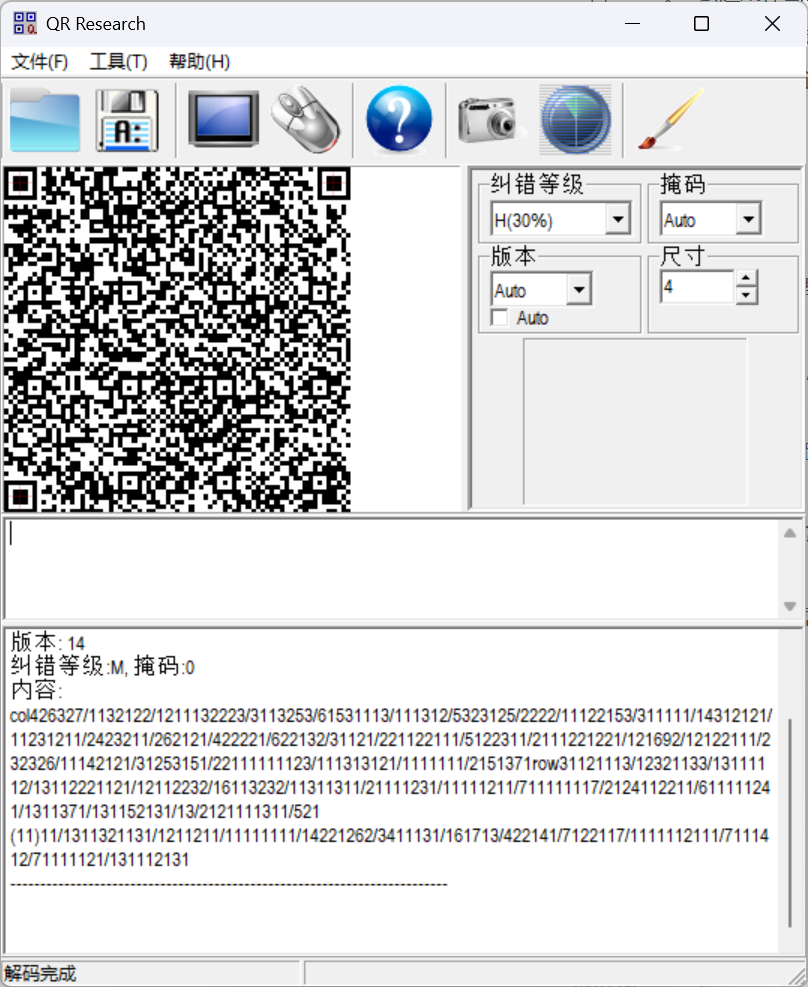
扫描结果:
col426327/1132122/1211132223/3113253/61531113/111312/5323125/2222/11122153/311111/14312121/11231211/2423211/262121/422221/622132/31121/221122111/5122311/2111221221/121692/12122111/232326/11142121/31253151/22111111123/111313121/1111111/2151371
row31121113/12321133/13111112/13112221121/12112232/16113232/11311311/21111231/11111211/711111117/2124112211/611111241/1311371/131152131/13/2121111311/521(11)11/1311321131/1211211/11111111/14221262/3411131/161713/422141/7122117/1111112111/7111412/71111121/131112131
考察数织, https://fedimser.github.io/nonogram.html
参考博客: https://blog.gzti.me/posts/2021/eee18328/index.html#ChieftainsSecret-Misc
使用上面的脚本获得二维码
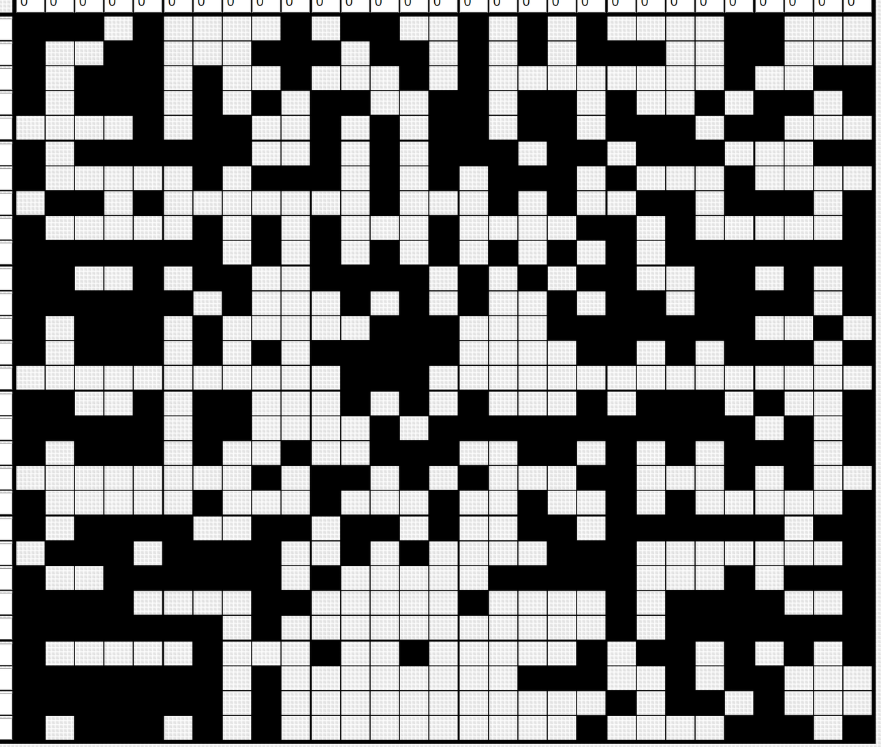
exp
data = [[1,1,1,1,1,1,1,0,1,0,1,1,0,0,1,1,0,1,0,0,1,0,1,1,1,1,1,1,1],
[1,0,0,0,0,0,1,0,1,0,1,0,0,0,1,0,0,0,0,1,1,0,1,0,0,0,0,0,1],
[1,0,1,1,1,0,1,0,1,0,1,1,1,1,1,0,0,0,0,1,1,0,1,0,1,1,1,0,1],
[1,0,1,1,1,0,1,0,0,1,0,0,1,1,1,0,0,1,1,0,1,0,1,0,1,1,1,0,1],
[1,0,1,1,1,0,1,0,1,0,0,0,0,1,0,0,0,0,1,1,0,0,1,0,1,1,1,0,1],
[1,0,0,0,0,0,1,0,0,0,1,0,0,0,1,0,0,1,0,0,1,0,1,0,0,0,0,0,1],
[1,1,1,1,1,1,1,0,1,0,1,0,1,0,1,0,1,0,1,0,1,0,1,1,1,1,1,1,1],
[0,0,0,0,0,0,0,0,0,1,0,1,1,1,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0],
[1,0,0,1,1,1,1,1,1,0,1,0,0,0,0,1,1,1,1,1,1,1,0,0,1,0,1,1,1],
[1,1,1,1,0,0,0,0,1,1,0,0,0,0,0,1,1,0,0,0,1,0,1,1,1,1,0,0,1],
[1,1,0,0,1,0,1,1,0,0,1,1,1,1,0,1,0,1,0,1,1,0,0,1,1,0,1,0,1],
[0,1,1,0,1,0,0,0,0,0,0,0,1,0,0,0,1,0,1,0,0,1,1,0,1,1,1,0,1],
[1,1,0,0,1,0,1,1,0,0,0,1,0,1,0,1,0,0,0,1,0,1,1,1,0,1,0,0,1],
[1,1,1,0,1,0,0,0,0,1,0,1,1,0,0,1,0,1,0,1,0,0,0,1,1,1,0,0,0],
[0,0,0,0,1,0,1,1,0,0,1,0,1,0,1,1,0,1,1,0,1,1,1,0,1,1,0,0,0],
[1,1,1,1,1,1,0,1,0,0,0,1,0,1,0,1,0,0,1,0,1,1,0,1,1,1,1,0,1],
[0,1,1,1,0,1,1,1,1,0,0,1,0,1,0,0,0,0,1,1,1,0,0,0,0,0,0,0,1],
[1,0,0,1,1,0,0,0,1,1,1,0,1,1,0,1,0,1,0,1,1,1,0,0,1,1,1,0,0],
[1,0,1,1,1,1,1,1,0,0,1,0,1,0,1,1,1,0,1,1,0,1,1,1,0,0,0,1,1],
[1,0,1,1,1,1,0,0,1,1,0,1,1,0,1,0,0,1,1,0,1,1,1,1,1,1,0,1,1],
[1,1,1,1,1,0,1,1,0,0,0,0,1,0,1,1,1,1,1,1,1,1,1,1,1,0,1,0,1],
[0,0,0,0,0,0,0,0,1,0,1,1,0,1,0,1,0,0,0,1,1,0,0,0,1,0,1,0,0],
[1,1,1,1,1,1,1,0,1,0,0,1,0,1,0,1,0,1,1,1,1,0,1,0,1,1,0,0,0],
[1,0,0,0,0,0,1,0,1,1,1,0,1,0,1,0,1,1,1,0,1,0,0,0,1,0,0,0,0],
[1,0,1,1,1,0,1,0,1,0,0,0,1,1,1,0,0,0,1,1,1,1,1,1,1,0,0,1,0],
[1,0,1,1,1,0,1,0,1,0,1,1,0,0,1,1,0,1,1,0,1,0,0,1,0,1,1,0,1],
[1,0,1,1,1,0,1,0,0,1,0,0,0,1,0,1,0,0,0,0,0,0,0,0,1,0,0,1,1],
[1,0,0,0,0,0,1,0,0,0,1,0,0,1,0,0,1,0,0,1,0,1,1,0,1,0,1,0,1],
[1,1,1,1,1,1,1,0,1,0,1,0,0,0,0,1,0,0,0,0,1,0,1,1,0,1,0,0,0]]
import pyzbar.pyzbar as pyzbar
from itertools import permutations
from PIL import Image, ImageDraw as draw
import matplotlib.pyplot as plt
from tqdm import tqdm
shuffle_1 = [9, 11, 13, 15, 17, 19]
shuffle_2 = [10, 12, 14, 16, 18]
head = data[:9]
tail = data[20:]
def body(body_1, body_2): # 获取中间部分的一种排列
body = []
for i in range(5):
body.append(body_1[i])
body.append(body_2[i])
body.append(body_1[5])
return [data[i] for i in body]
def draw_img(data): # 生成二维码图片
assert len(data) == 29 and len(data[0]) == 29
img = Image.new('RGB', (31, 31), (255,255,255))
for i, row in enumerate(data):
for j, pixel in enumerate(row):
img.putpixel((j + 1, i + 1), (0,0,0) if pixel == 1 else (255,255,255))
return img
with tqdm(total=720 * 120) as pbar:
for body_1 in permutations(shuffle_1):
for body_2 in permutations(shuffle_2):
im = draw_img(head + body(body_1, body_2) + tail)
barcodes = pyzbar.decode(im)
pbar.update(1)
if(len(barcodes) == 0):
continue
for barcode in barcodes:
barcodeData = barcode.data.decode("utf-8")
print(barcodeData)
plt.imshow(im)
plt.show()
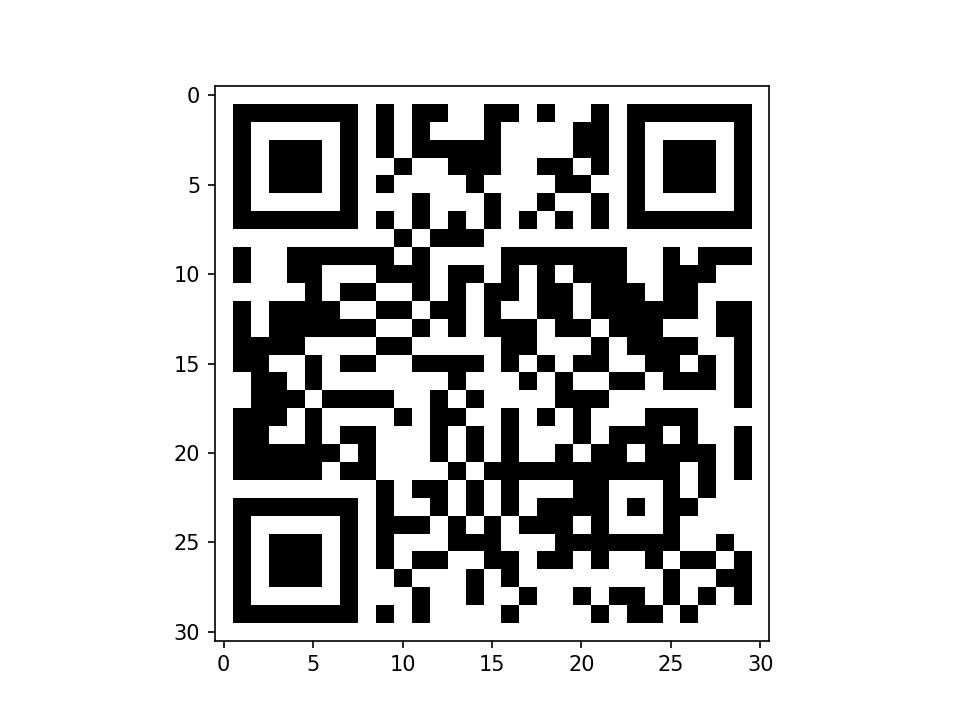
#flag{f31861a9-a753-47d5-8660-a8cada6c599e}
9. onist
社工题, 用谷歌识图得到该建筑在冰岛,再根据搜索冰岛EDITION附近的演唱厅得到答案


再使用地图查看对面的建筑, 发现是一家酒店
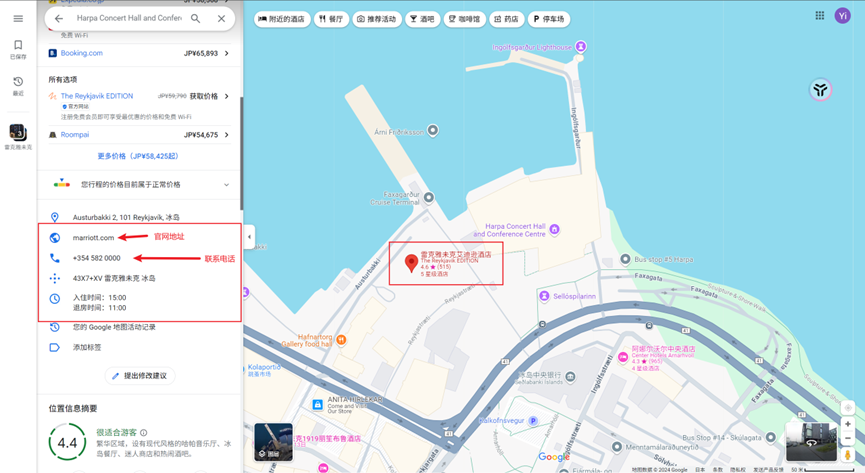
flag{冰岛_雷克雅未克_哈帕音乐厅_雷克雅未克艾迪逊}
10. 蝎子莱莱
逆推key, 找一段较小的返回包, 猜测该密文的明文应该以{"status":"c3VjY2Vzcw==","msg"开头的
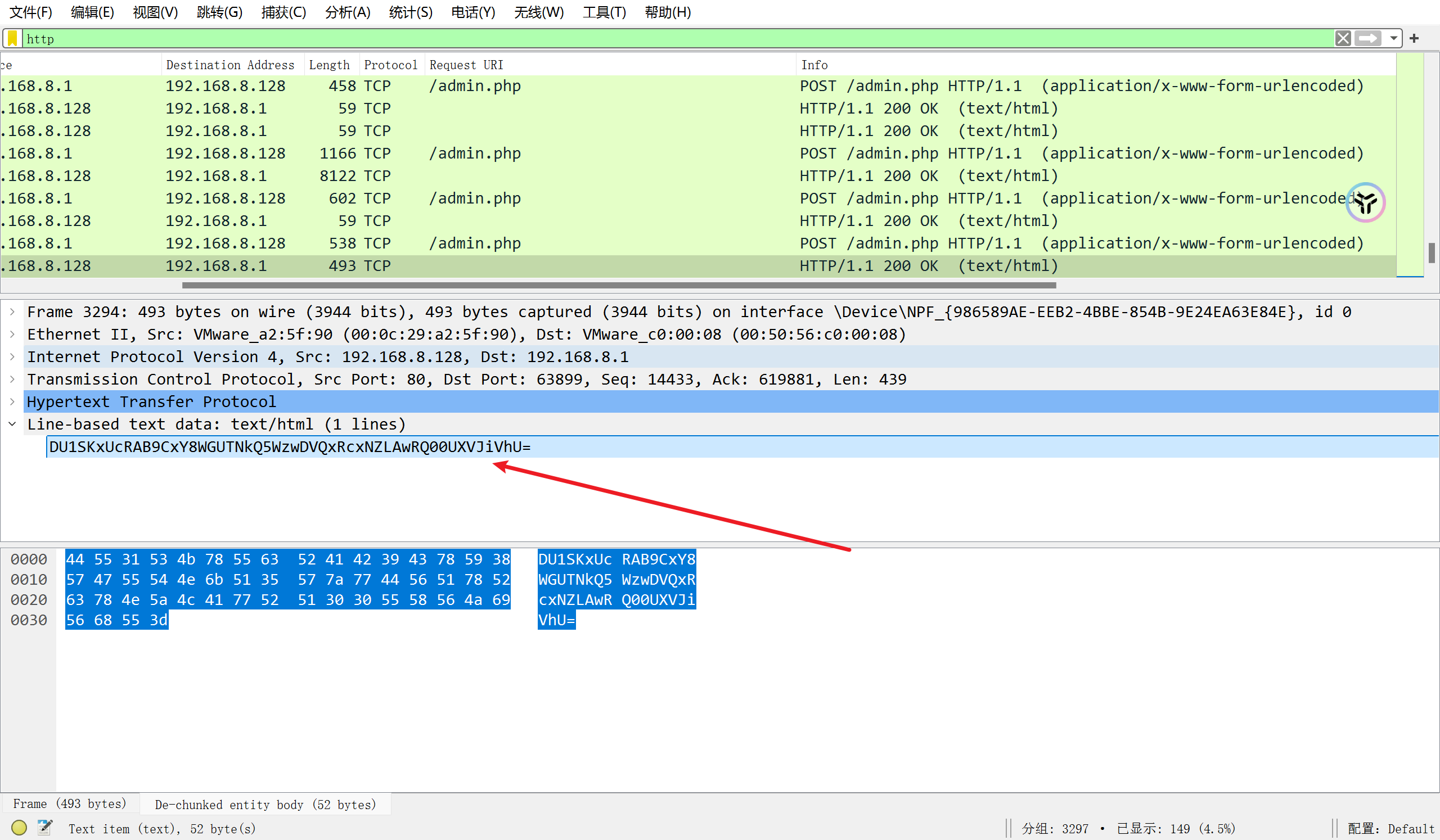
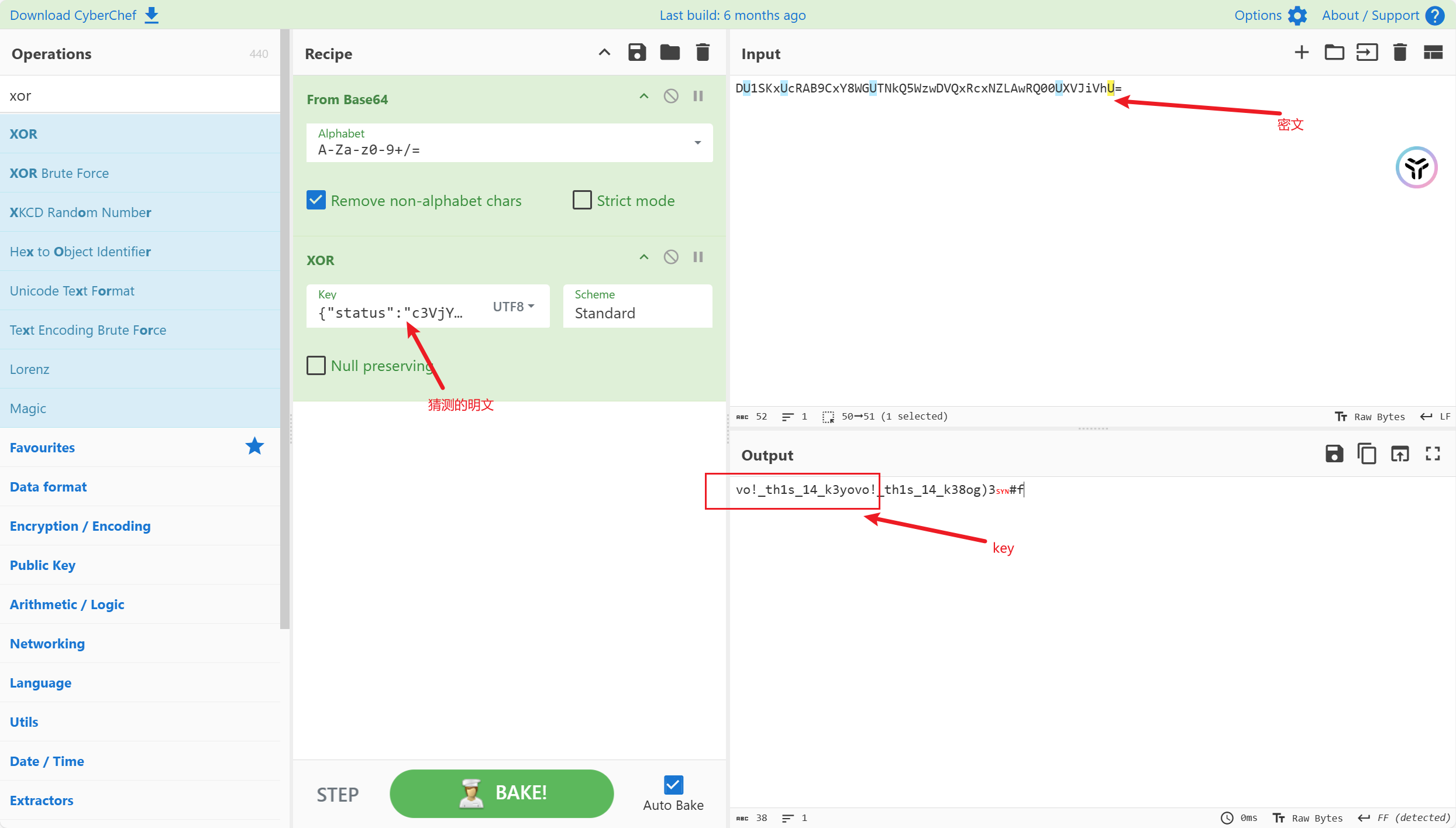
注意冰蝎的xor加密会先将key变形, 也就是将key的第一位放到末尾, 即key=ovo!_th1s_14_k3y
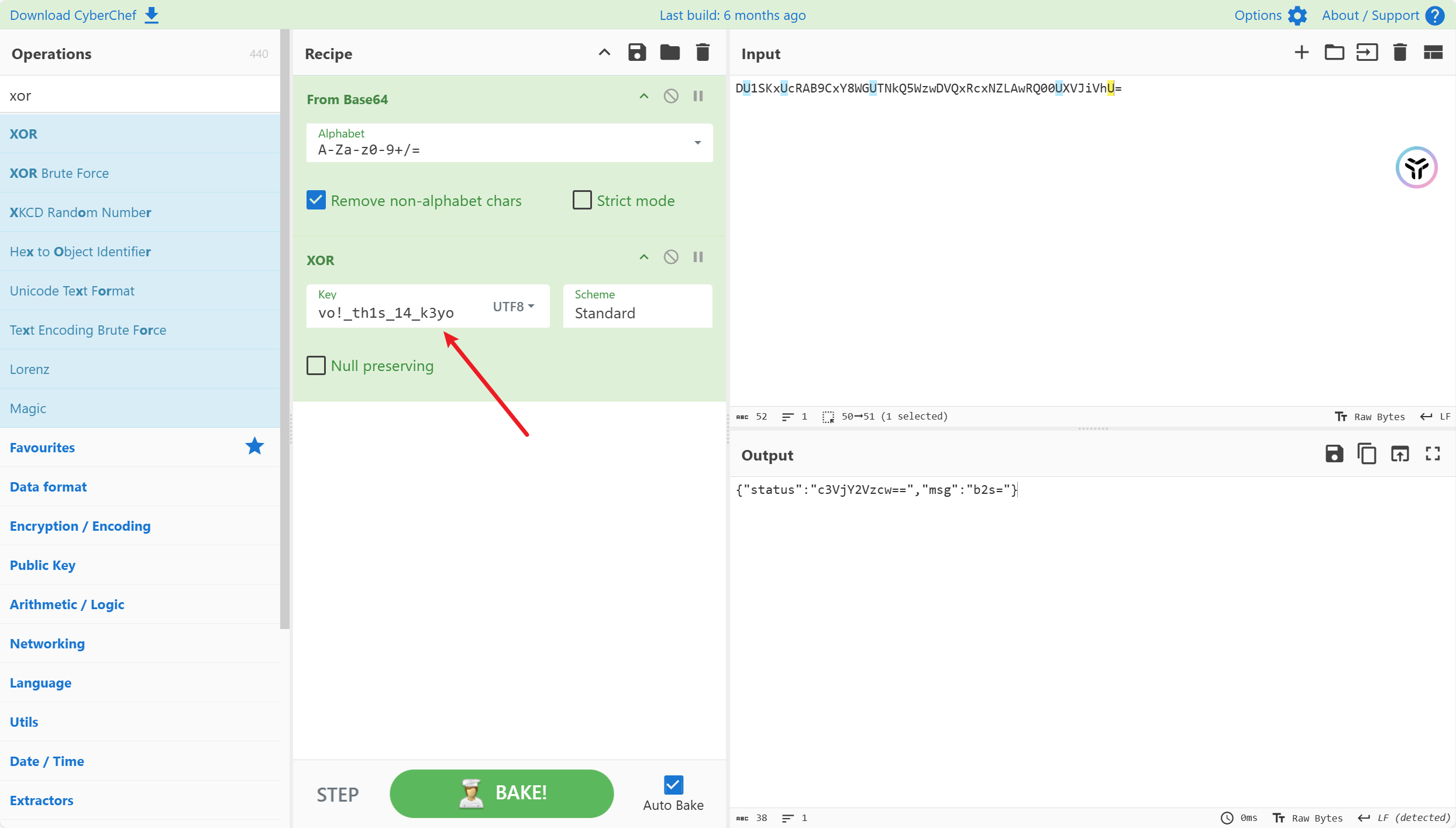
成功解密冰蝎, 接下来翻流量包查找有用的信息, 在2560包中发现存在flag.zip

再在返回包中寻找flag.zip, 在3057流中找到, 先冰蝎解密, 再两重base64得到PK头
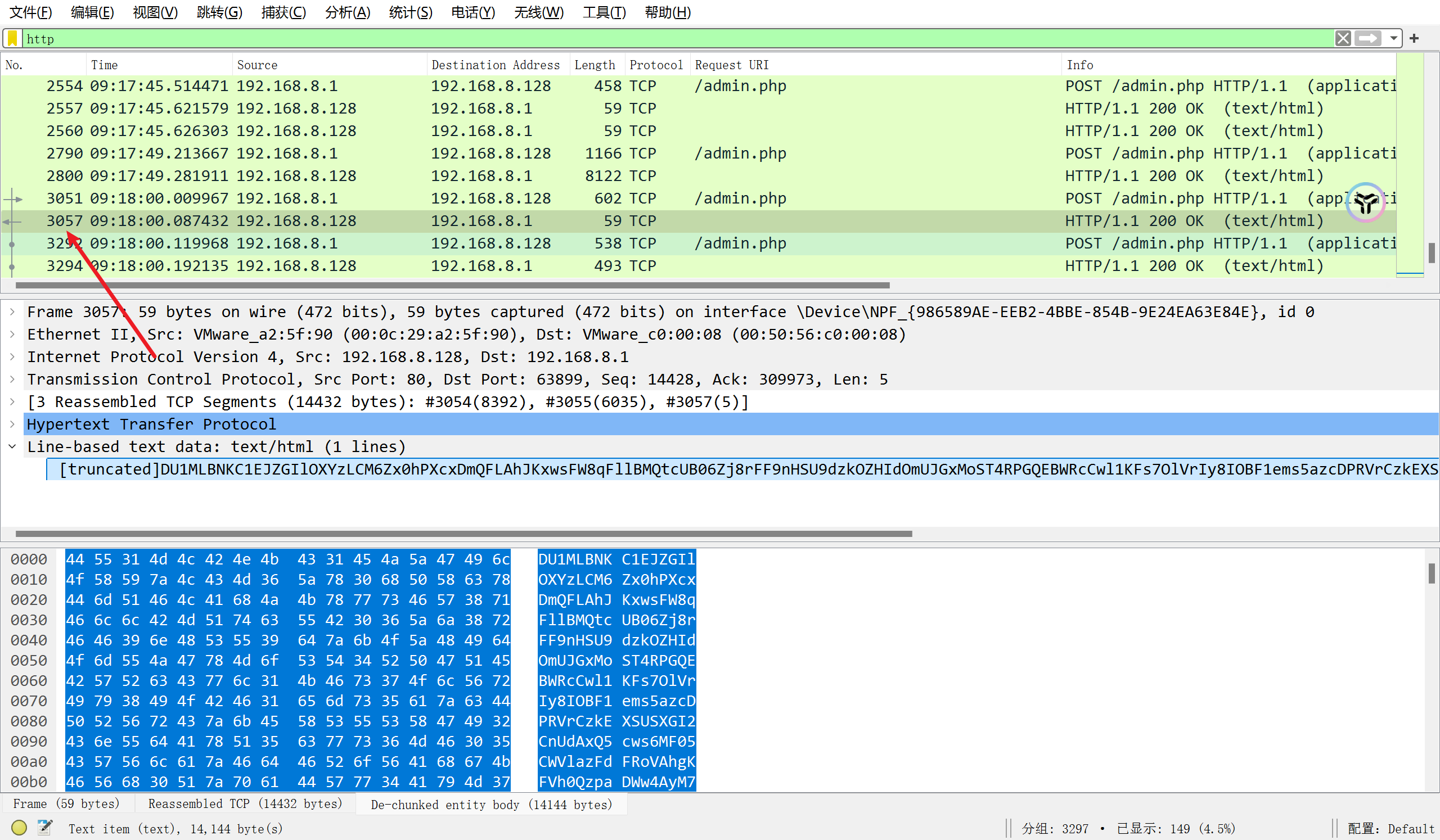
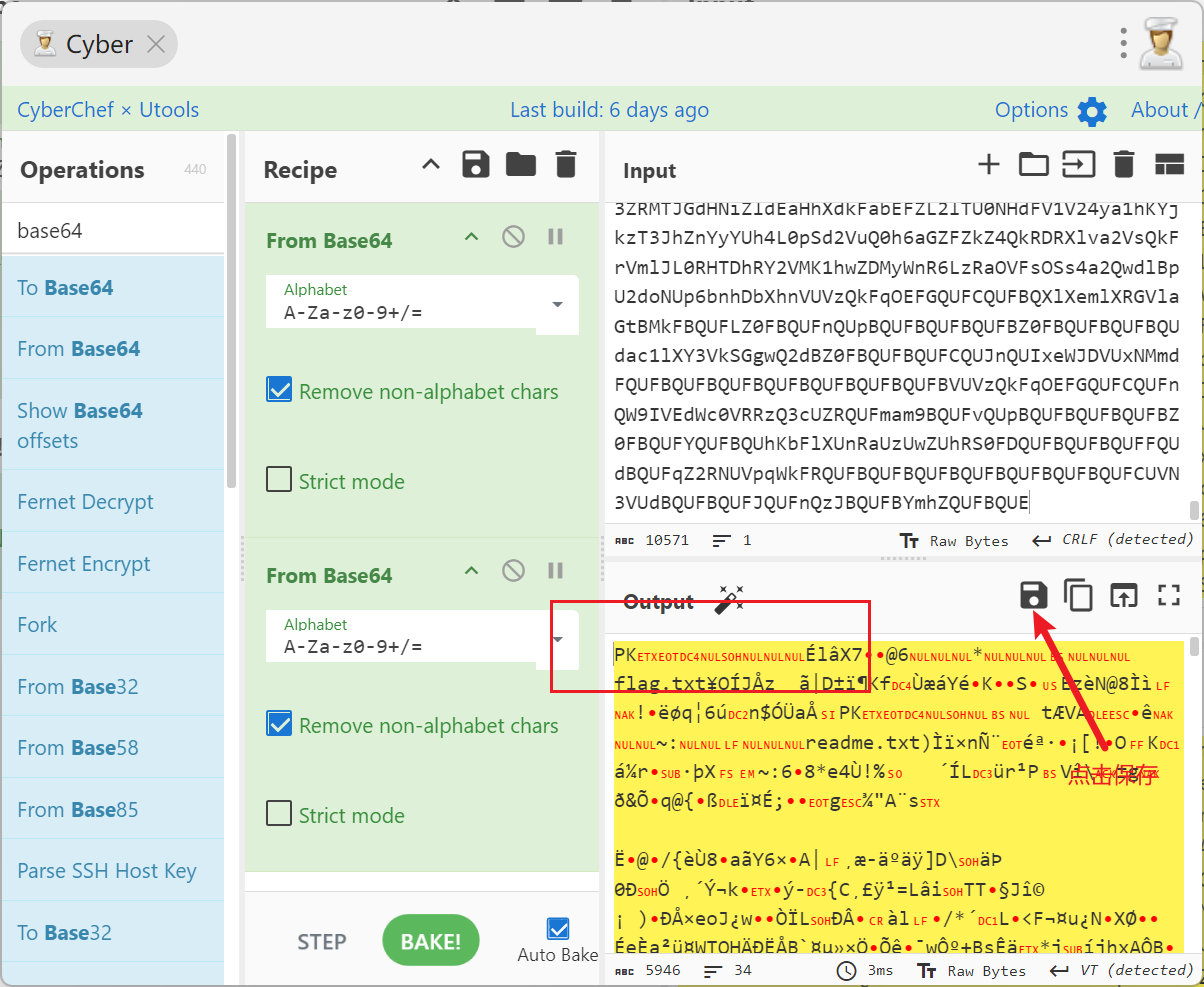
压缩包被加密了, 发现里面存在两个文件, 猜测为明文攻击
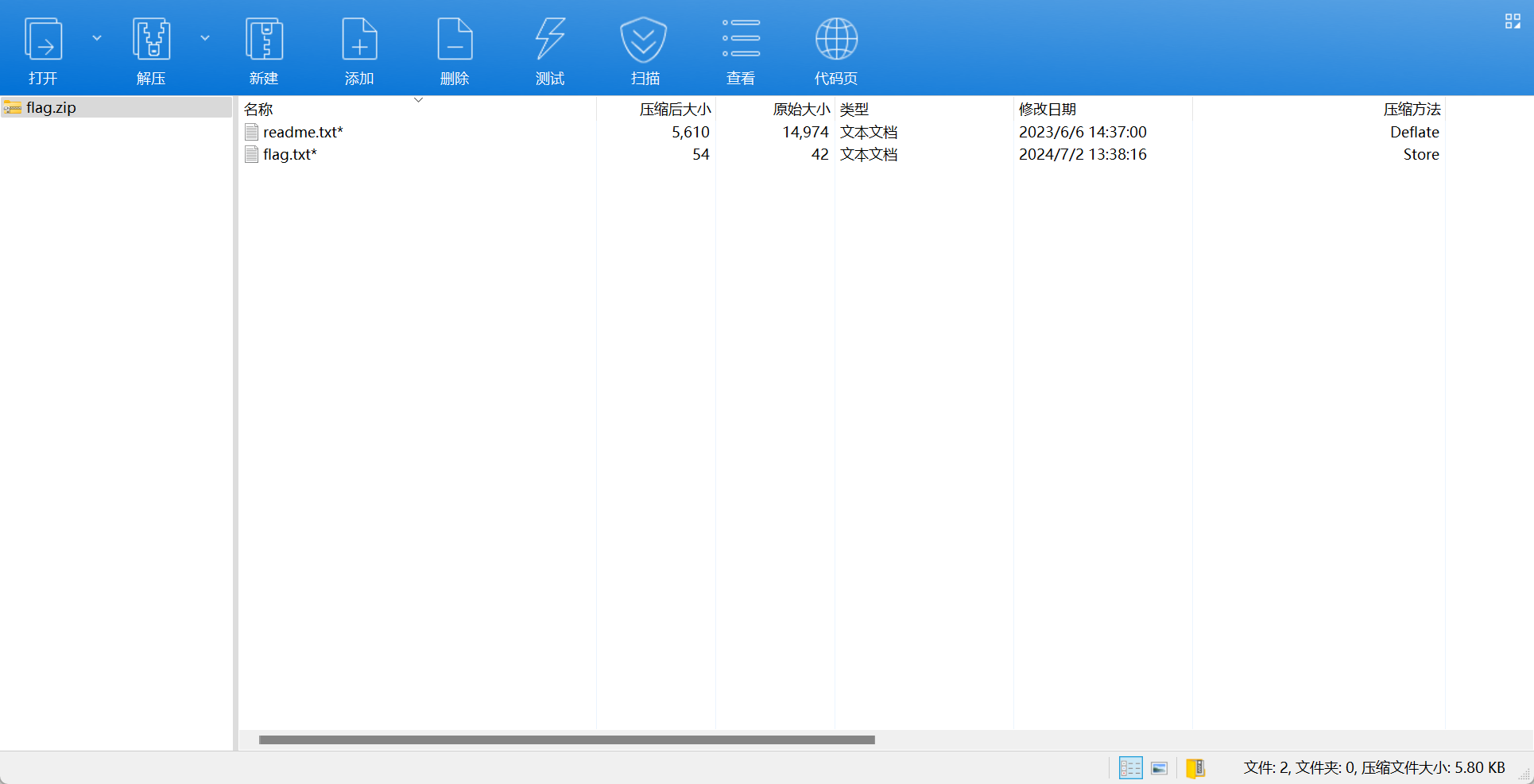
去流量包中找到readme.txt的内容, 在流2800中(猜测肯定是从最长的开始找)
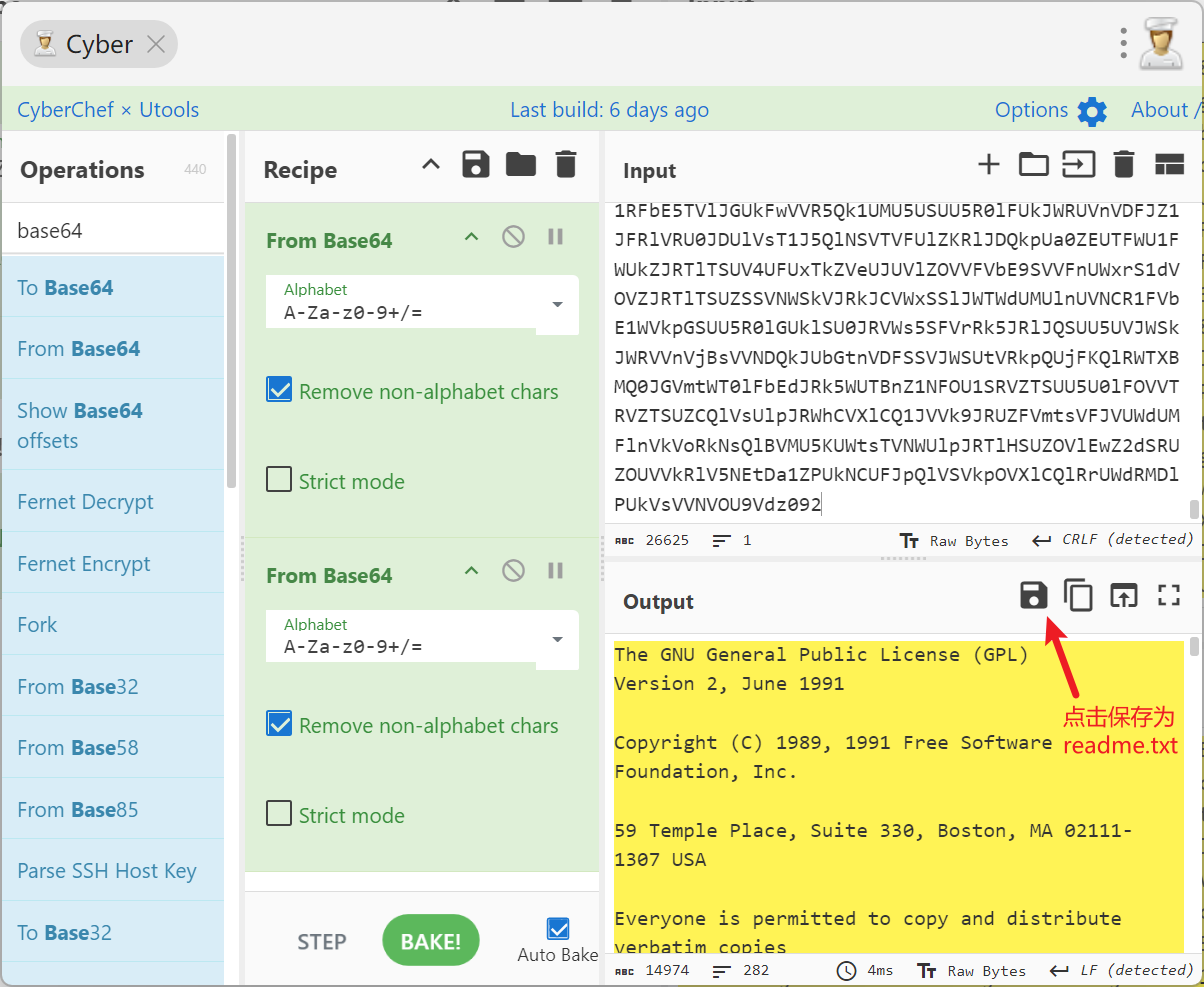
再通过7z进行压缩, 注意明文攻击的坑点就在于两个文件的name和crc是否相同
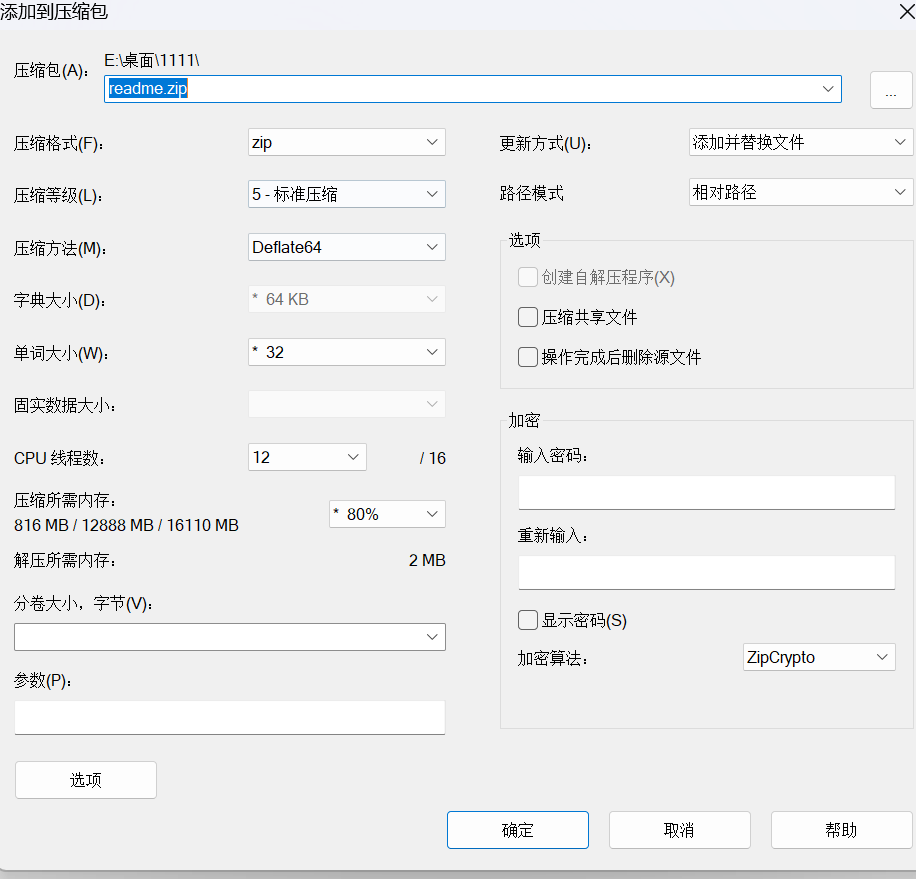
用工具ARCHPR5.4进行明文攻击, 过程不会太久, 如果太久还没显示出来的话直接停止即可
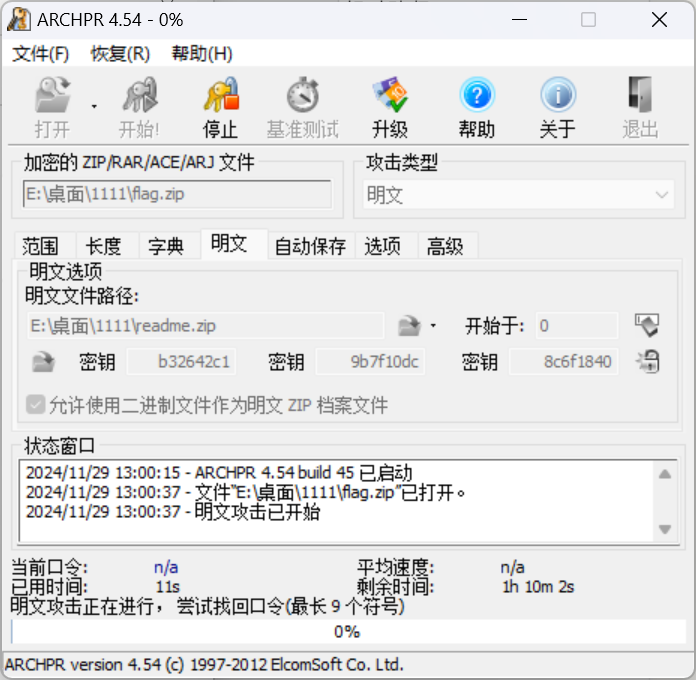
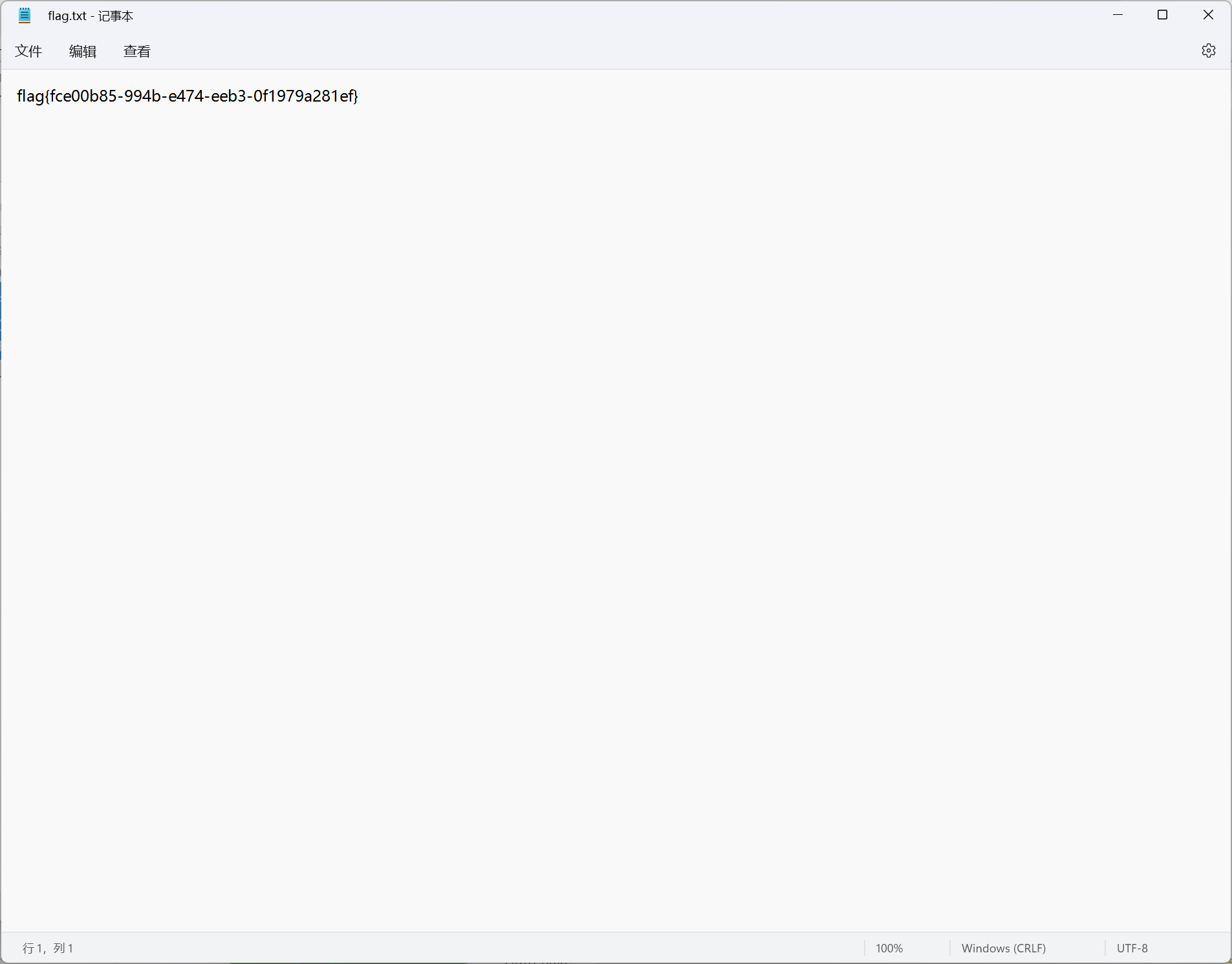
#flag{fce00b85-994b-e474-eeb3-0f1979a281ef}
11. funny_ascii
直接在线工具二进制转ASCII文本
https://www.convertstore.com/number/binarytoascii/zh/%E2%80%9C/home/privacy%E2%80%9D
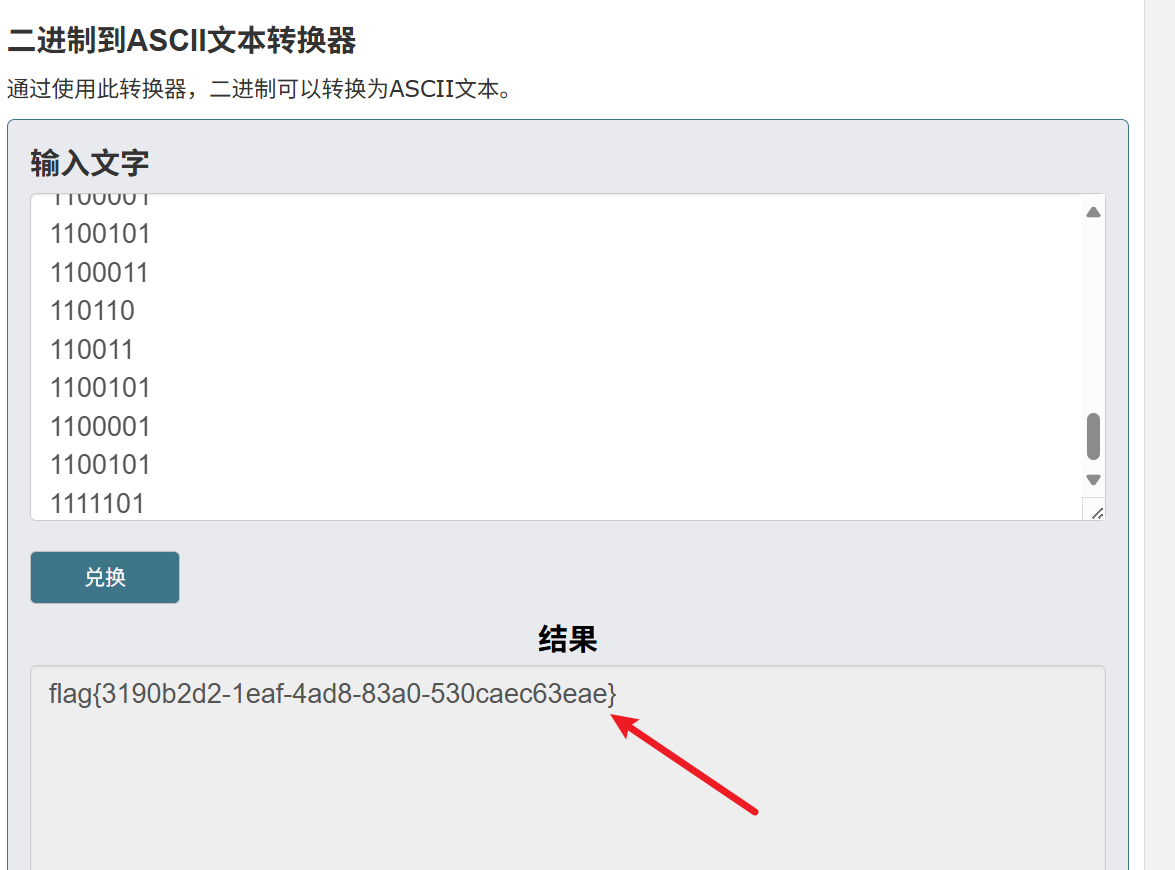
#flag{3190b2d2-1eaf-4ad8-83a0-530caec63eae}

 浙公网安备 33010602011771号
浙公网安备 33010602011771号